9263de62c153163596e7172ac312685a.ppt
- Количество слайдов: 19
 Imperva Total Application Security Idan Soen, CISSP Security Engineer Secure. Sphere – The First Dynamic Profiling Firewall
Imperva Total Application Security Idan Soen, CISSP Security Engineer Secure. Sphere – The First Dynamic Profiling Firewall
 Agenda • Imperva • Application Security Landscape • Secure. Sphere 2 Imperva Confidential
Agenda • Imperva • Application Security Landscape • Secure. Sphere 2 Imperva Confidential
 Imperva • Company Focus: Total Application Security • Founded in 2000 by world’s elite application security specialists – Israeli Defense Force cyber warfare team – Private sector penetration testing & app security consultants • Co-Founder, CEO – Shlomo Kramer – Check Point co-founder – Co-developer of Stateful Inspection • Secure. Sphere Product Family – First “Dynamic Profiling Firewall” 3 Imperva Confidential
Imperva • Company Focus: Total Application Security • Founded in 2000 by world’s elite application security specialists – Israeli Defense Force cyber warfare team – Private sector penetration testing & app security consultants • Co-Founder, CEO – Shlomo Kramer – Check Point co-founder – Co-developer of Stateful Inspection • Secure. Sphere Product Family – First “Dynamic Profiling Firewall” 3 Imperva Confidential
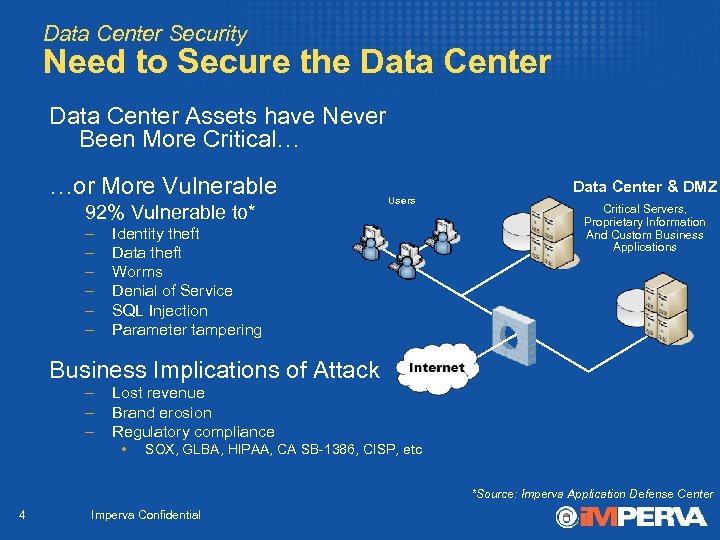 Data Center Security Need to Secure the Data Center Assets have Never Been More Critical… …or More Vulnerable 92% Vulnerable to* – – – Data Center & DMZ Users Identity theft Data theft Worms Denial of Service SQL Injection Parameter tampering Critical Servers, Proprietary Information And Custom Business Applications Business Implications of Attack – – – Lost revenue Brand erosion Regulatory compliance • SOX, GLBA, HIPAA, CA SB-1386, CISP, etc *Source: Imperva Application Defense Center 4 Imperva Confidential
Data Center Security Need to Secure the Data Center Assets have Never Been More Critical… …or More Vulnerable 92% Vulnerable to* – – – Data Center & DMZ Users Identity theft Data theft Worms Denial of Service SQL Injection Parameter tampering Critical Servers, Proprietary Information And Custom Business Applications Business Implications of Attack – – – Lost revenue Brand erosion Regulatory compliance • SOX, GLBA, HIPAA, CA SB-1386, CISP, etc *Source: Imperva Application Defense Center 4 Imperva Confidential
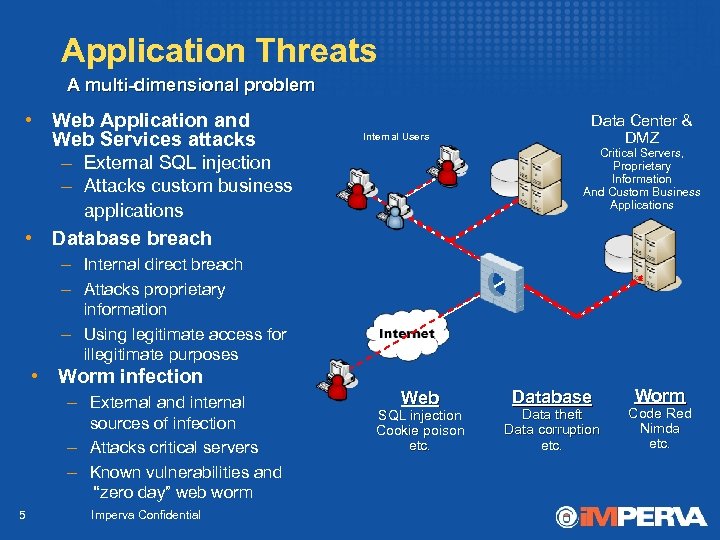 Application Threats A multi-dimensional problem • Web Application and Web Services attacks – External SQL injection – Attacks custom business Internal Users Data Center & DMZ Critical Servers, Proprietary Information And Custom Business Applications applications • Database breach – Internal direct breach – Attacks proprietary information – Using legitimate access for illegitimate purposes • Worm infection – External and internal sources of infection – Attacks critical servers – Known vulnerabilities and “zero day” web worm 5 Imperva Confidential Web SQL injection Cookie poison etc. Database Data theft Data corruption etc. Worm Code Red Nimda etc.
Application Threats A multi-dimensional problem • Web Application and Web Services attacks – External SQL injection – Attacks custom business Internal Users Data Center & DMZ Critical Servers, Proprietary Information And Custom Business Applications applications • Database breach – Internal direct breach – Attacks proprietary information – Using legitimate access for illegitimate purposes • Worm infection – External and internal sources of infection – Attacks critical servers – Known vulnerabilities and “zero day” web worm 5 Imperva Confidential Web SQL injection Cookie poison etc. Database Data theft Data corruption etc. Worm Code Red Nimda etc.
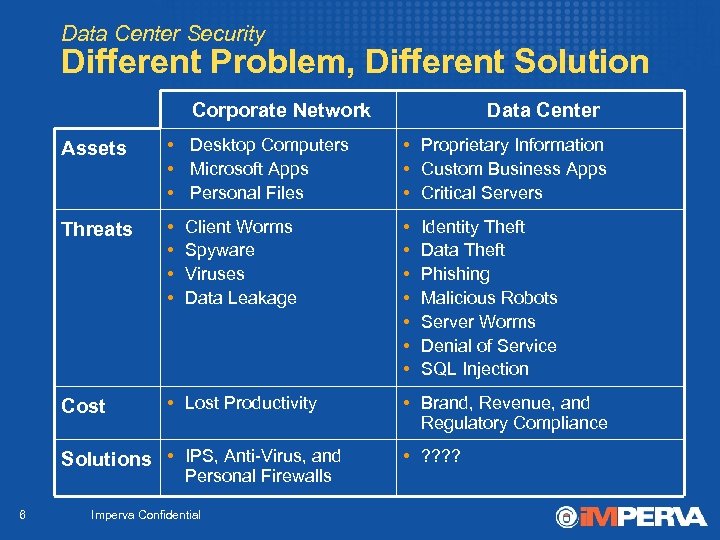 Data Center Security Different Problem, Different Solution Corporate Network Data Center Assets • Desktop Computers • Microsoft Apps • Personal Files • Proprietary Information • Custom Business Apps • Critical Servers Threats • • • Cost • Lost Productivity Client Worms Spyware Viruses Data Leakage Solutions • IPS, Anti-Virus, and Personal Firewalls 6 Imperva Confidential Identity Theft Data Theft Phishing Malicious Robots Server Worms Denial of Service SQL Injection • Brand, Revenue, and Regulatory Compliance • ? ?
Data Center Security Different Problem, Different Solution Corporate Network Data Center Assets • Desktop Computers • Microsoft Apps • Personal Files • Proprietary Information • Custom Business Apps • Critical Servers Threats • • • Cost • Lost Productivity Client Worms Spyware Viruses Data Leakage Solutions • IPS, Anti-Virus, and Personal Firewalls 6 Imperva Confidential Identity Theft Data Theft Phishing Malicious Robots Server Worms Denial of Service SQL Injection • Brand, Revenue, and Regulatory Compliance • ? ?
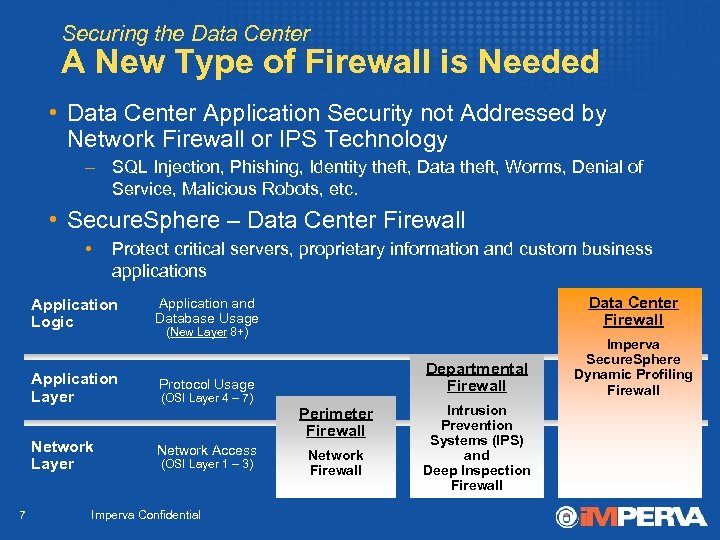 Securing the Data Center A New Type of Firewall is Needed • Data Center Application Security not Addressed by Network Firewall or IPS Technology – SQL Injection, Phishing, Identity theft, Data theft, Worms, Denial of Service, Malicious Robots, etc. • Secure. Sphere – Data Center Firewall • Protect critical servers, proprietary information and custom business applications Application and Database Usage Data Center Firewall Application Layer Protocol Usage Imperva Secure. Sphere Dynamic Profiling Firewall Network Layer Network Access Application Logic 7 (New Layer 8+) (OSI Layer 4 – 7) (OSI Layer 1 – 3) Imperva Confidential Departmental Firewall Perimeter Firewall Network Firewall Intrusion Prevention Systems (IPS) and Deep Inspection Firewall
Securing the Data Center A New Type of Firewall is Needed • Data Center Application Security not Addressed by Network Firewall or IPS Technology – SQL Injection, Phishing, Identity theft, Data theft, Worms, Denial of Service, Malicious Robots, etc. • Secure. Sphere – Data Center Firewall • Protect critical servers, proprietary information and custom business applications Application and Database Usage Data Center Firewall Application Layer Protocol Usage Imperva Secure. Sphere Dynamic Profiling Firewall Network Layer Network Access Application Logic 7 (New Layer 8+) (OSI Layer 4 – 7) (OSI Layer 1 – 3) Imperva Confidential Departmental Firewall Perimeter Firewall Network Firewall Intrusion Prevention Systems (IPS) and Deep Inspection Firewall
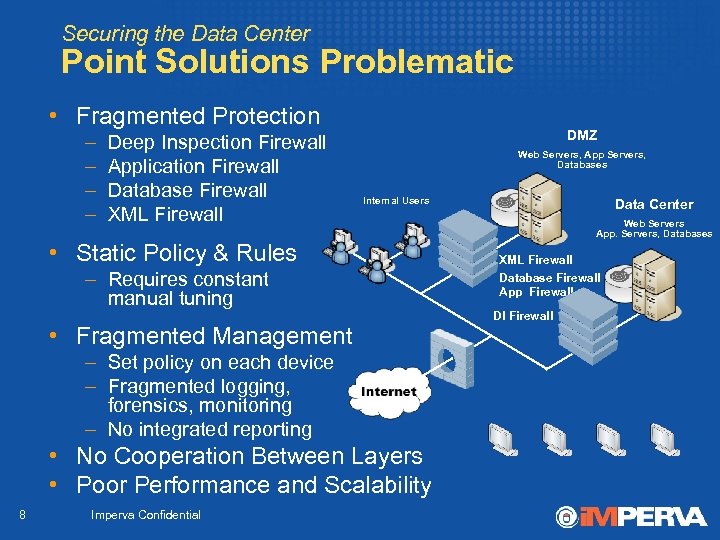 Securing the Data Center Point Solutions Problematic • Fragmented Protection – – Deep Inspection Firewall Application Firewall Database Firewall XML Firewall DMZ Web Servers, App Servers, Databases Internal Users • Static Policy & Rules – Requires constant manual tuning • Fragmented Management – Set policy on each device – Fragmented logging, forensics, monitoring – No integrated reporting • No Cooperation Between Layers • Poor Performance and Scalability 8 Imperva Confidential Data Center Web Servers App. Servers, Databases XML Firewall Database Firewall App Firewall DI Firewall
Securing the Data Center Point Solutions Problematic • Fragmented Protection – – Deep Inspection Firewall Application Firewall Database Firewall XML Firewall DMZ Web Servers, App Servers, Databases Internal Users • Static Policy & Rules – Requires constant manual tuning • Fragmented Management – Set policy on each device – Fragmented logging, forensics, monitoring – No integrated reporting • No Cooperation Between Layers • Poor Performance and Scalability 8 Imperva Confidential Data Center Web Servers App. Servers, Databases XML Firewall Database Firewall App Firewall DI Firewall
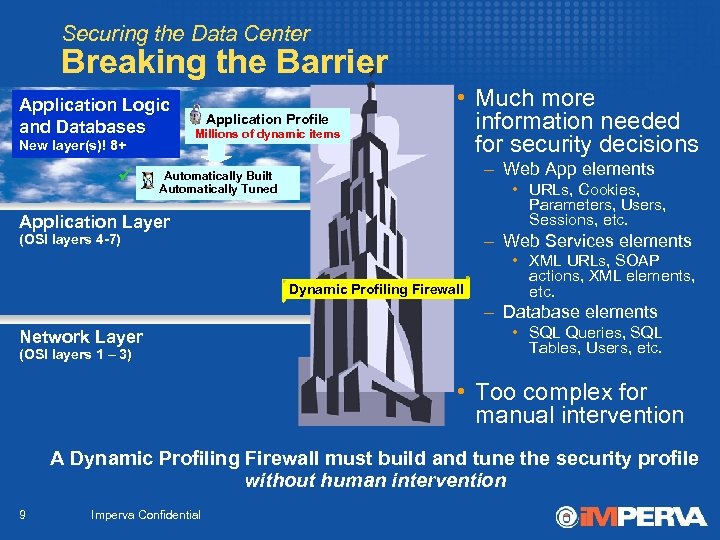 Securing the Data Center Breaking the Barrier Application Logic and Databases New layer(s)! 8+ Application Profile Millions of dynamic items • Much more information needed for security decisions – Web App elements Automatically Built Automatically Tuned • URLs, Cookies, Parameters, Users, Sessions, etc. Application Layer – Web Services elements (OSI layers 4 -7) Dynamic Profiling Firewall • XML URLs, SOAP actions, XML elements, etc. – Database elements Network Layer (OSI layers 1 – 3) • SQL Queries, SQL Tables, Users, etc. • Too complex for manual intervention A Dynamic Profiling Firewall must build and tune the security profile without human intervention 9 Imperva Confidential
Securing the Data Center Breaking the Barrier Application Logic and Databases New layer(s)! 8+ Application Profile Millions of dynamic items • Much more information needed for security decisions – Web App elements Automatically Built Automatically Tuned • URLs, Cookies, Parameters, Users, Sessions, etc. Application Layer – Web Services elements (OSI layers 4 -7) Dynamic Profiling Firewall • XML URLs, SOAP actions, XML elements, etc. – Database elements Network Layer (OSI layers 1 – 3) • SQL Queries, SQL Tables, Users, etc. • Too complex for manual intervention A Dynamic Profiling Firewall must build and tune the security profile without human intervention 9 Imperva Confidential
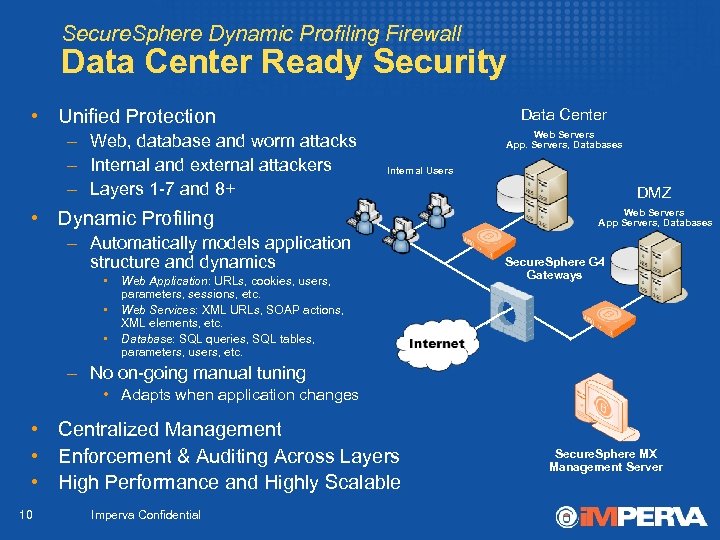 Secure. Sphere Dynamic Profiling Firewall Data Center Ready Security • Unified Protection – Web, database and worm attacks – Internal and external attackers – Layers 1 -7 and 8+ Data Center Web Servers App. Servers, Databases Internal Users • Dynamic Profiling – Automatically models application structure and dynamics • • • Web Application: URLs, cookies, users, parameters, sessions, etc. Web Services: XML URLs, SOAP actions, XML elements, etc. Database: SQL queries, SQL tables, parameters, users, etc. DMZ Web Servers App Servers, Databases Secure. Sphere G 4 Gateways – No on-going manual tuning • Adapts when application changes • Centralized Management • Enforcement & Auditing Across Layers • High Performance and Highly Scalable 10 Imperva Confidential Secure. Sphere MX Management Server
Secure. Sphere Dynamic Profiling Firewall Data Center Ready Security • Unified Protection – Web, database and worm attacks – Internal and external attackers – Layers 1 -7 and 8+ Data Center Web Servers App. Servers, Databases Internal Users • Dynamic Profiling – Automatically models application structure and dynamics • • • Web Application: URLs, cookies, users, parameters, sessions, etc. Web Services: XML URLs, SOAP actions, XML elements, etc. Database: SQL queries, SQL tables, parameters, users, etc. DMZ Web Servers App Servers, Databases Secure. Sphere G 4 Gateways – No on-going manual tuning • Adapts when application changes • Centralized Management • Enforcement & Auditing Across Layers • High Performance and Highly Scalable 10 Imperva Confidential Secure. Sphere MX Management Server
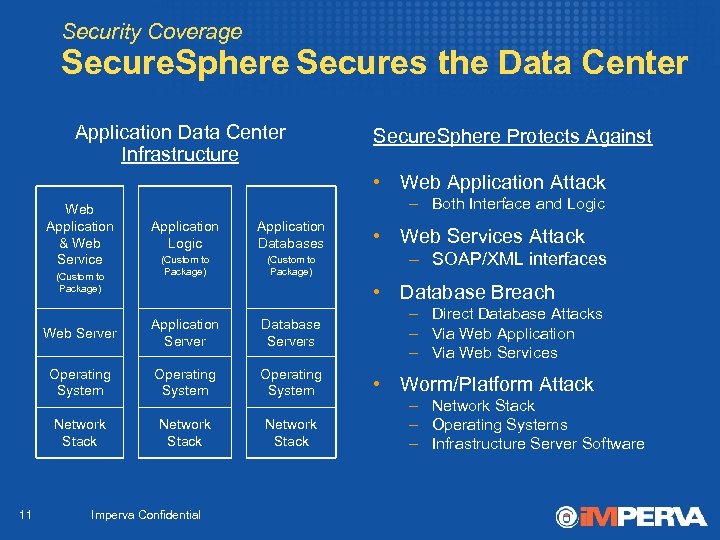 Security Coverage Secure. Sphere Secures the Data Center Application Data Center Infrastructure Secure. Sphere Protects Against • Web Application Attack Web Application & Web Service (Custom to Package) – Both Interface and Logic Application Databases (Custom to Package) – SOAP/XML interfaces • Database Breach Web Server Application Server Database Servers Operating System Network Stack 11 • Web Services Attack Network Stack Imperva Confidential – Direct Database Attacks – Via Web Application – Via Web Services • Worm/Platform Attack – Network Stack – Operating Systems – Infrastructure Server Software
Security Coverage Secure. Sphere Secures the Data Center Application Data Center Infrastructure Secure. Sphere Protects Against • Web Application Attack Web Application & Web Service (Custom to Package) – Both Interface and Logic Application Databases (Custom to Package) – SOAP/XML interfaces • Database Breach Web Server Application Server Database Servers Operating System Network Stack 11 • Web Services Attack Network Stack Imperva Confidential – Direct Database Attacks – Via Web Application – Via Web Services • Worm/Platform Attack – Network Stack – Operating Systems – Infrastructure Server Software
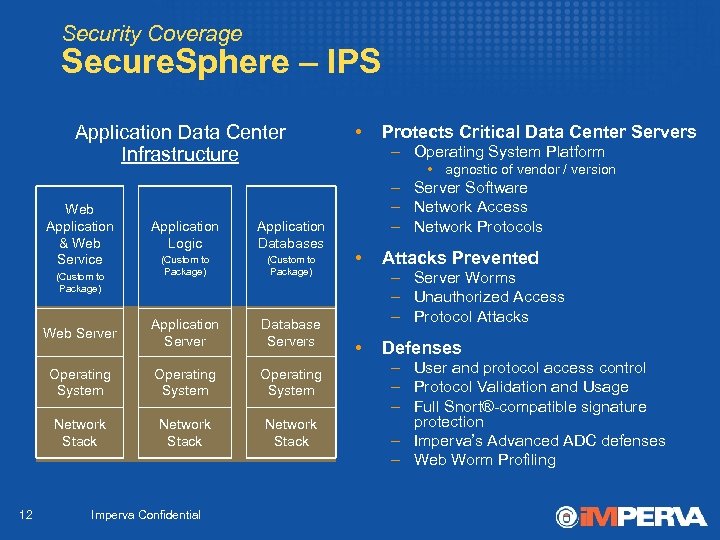 Security Coverage Secure. Sphere – IPS Application Data Center Infrastructure Web Application & Web Service Application Logic Application Databases (Custom to Package) Web Server Application Server Database Servers Operating System Network Stack (Custom to Package) 12 Imperva Confidential • Protects Critical Data Center Servers – Operating System Platform • agnostic of vendor / version – Server Software – Network Access – Network Protocols • Attacks Prevented – Server Worms – Unauthorized Access – Protocol Attacks • Defenses – User and protocol access control – Protocol Validation and Usage – Full Snort®-compatible signature protection – Imperva’s Advanced ADC defenses – Web Worm Profiling
Security Coverage Secure. Sphere – IPS Application Data Center Infrastructure Web Application & Web Service Application Logic Application Databases (Custom to Package) Web Server Application Server Database Servers Operating System Network Stack (Custom to Package) 12 Imperva Confidential • Protects Critical Data Center Servers – Operating System Platform • agnostic of vendor / version – Server Software – Network Access – Network Protocols • Attacks Prevented – Server Worms – Unauthorized Access – Protocol Attacks • Defenses – User and protocol access control – Protocol Validation and Usage – Full Snort®-compatible signature protection – Imperva’s Advanced ADC defenses – Web Worm Profiling
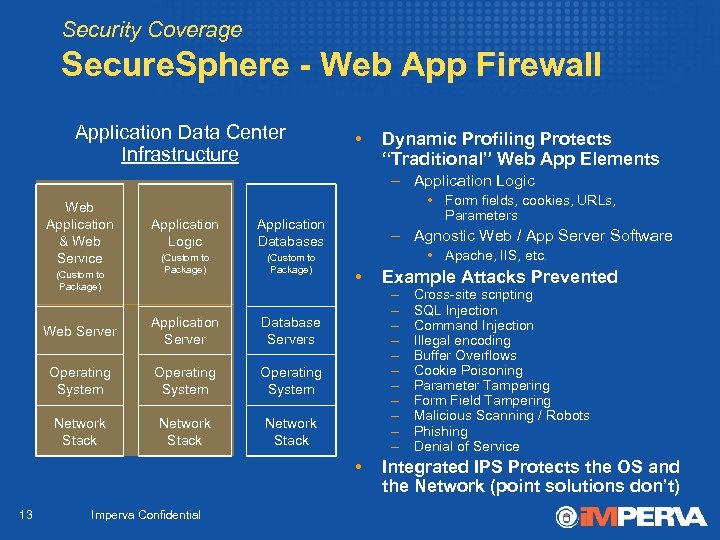 Security Coverage Secure. Sphere - Web App Firewall Application Data Center Infrastructure • Dynamic Profiling Protects “Traditional” Web App Elements – Application Logic Web Application & Web Service (Custom to Package) Application Logic Application Databases (Custom to Package) • Form fields, cookies, URLs, Parameters Web Server Application Server Operating System Network Stack • Apache, IIS, etc. Database Servers Operating System – Agnostic Web / App Server Software Network Stack • 13 Imperva Confidential Example Attacks Prevented – – – Cross-site scripting SQL Injection Command Injection Illegal encoding Buffer Overflows Cookie Poisoning Parameter Tampering Form Field Tampering Malicious Scanning / Robots Phishing Denial of Service Integrated IPS Protects the OS and the Network (point solutions don’t)
Security Coverage Secure. Sphere - Web App Firewall Application Data Center Infrastructure • Dynamic Profiling Protects “Traditional” Web App Elements – Application Logic Web Application & Web Service (Custom to Package) Application Logic Application Databases (Custom to Package) • Form fields, cookies, URLs, Parameters Web Server Application Server Operating System Network Stack • Apache, IIS, etc. Database Servers Operating System – Agnostic Web / App Server Software Network Stack • 13 Imperva Confidential Example Attacks Prevented – – – Cross-site scripting SQL Injection Command Injection Illegal encoding Buffer Overflows Cookie Poisoning Parameter Tampering Form Field Tampering Malicious Scanning / Robots Phishing Denial of Service Integrated IPS Protects the OS and the Network (point solutions don’t)
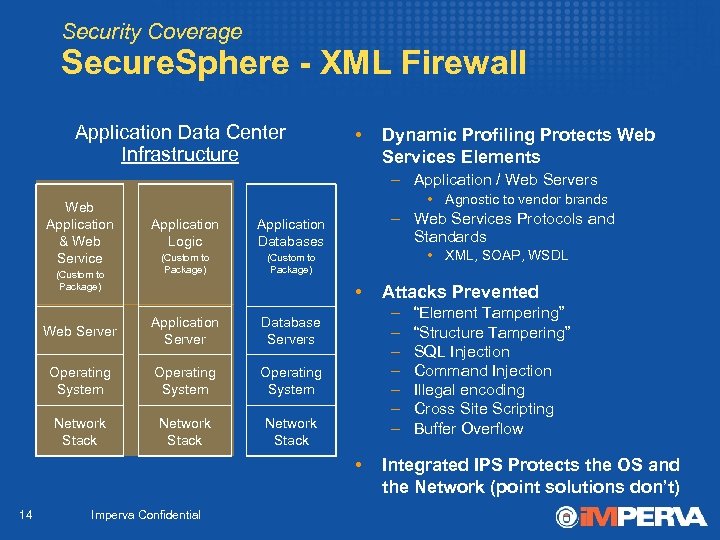 Security Coverage Secure. Sphere - XML Firewall Application Data Center Infrastructure • Dynamic Profiling Protects Web Services Elements – Application / Web Servers Web Application & Web Service (Custom to Package) • Agnostic to vendor brands Application Logic (Custom to Package) – Web Services Protocols and Standards Application Databases (Custom to Package) • XML, SOAP, WSDL • Web Server Application Server Operating System Network Stack – – – – Database Servers Operating System Network Stack • 14 Imperva Confidential Attacks Prevented “Element Tampering” “Structure Tampering” SQL Injection Command Injection Illegal encoding Cross Site Scripting Buffer Overflow Integrated IPS Protects the OS and the Network (point solutions don’t)
Security Coverage Secure. Sphere - XML Firewall Application Data Center Infrastructure • Dynamic Profiling Protects Web Services Elements – Application / Web Servers Web Application & Web Service (Custom to Package) • Agnostic to vendor brands Application Logic (Custom to Package) – Web Services Protocols and Standards Application Databases (Custom to Package) • XML, SOAP, WSDL • Web Server Application Server Operating System Network Stack – – – – Database Servers Operating System Network Stack • 14 Imperva Confidential Attacks Prevented “Element Tampering” “Structure Tampering” SQL Injection Command Injection Illegal encoding Cross Site Scripting Buffer Overflow Integrated IPS Protects the OS and the Network (point solutions don’t)
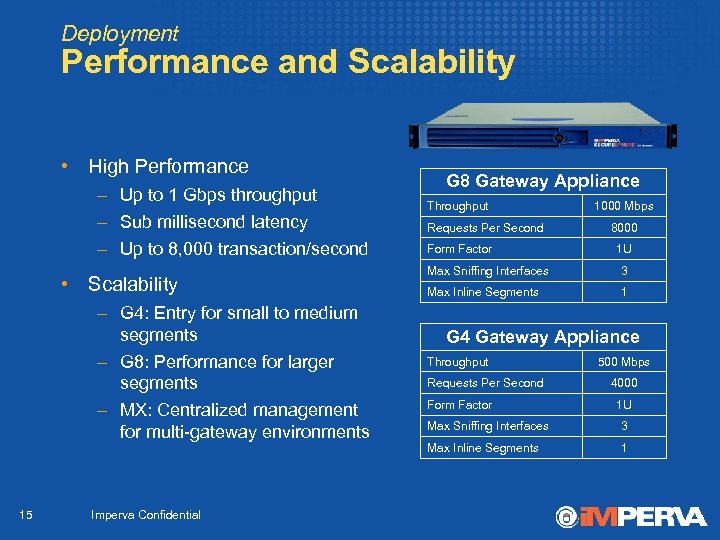 Deployment Performance and Scalability • High Performance – Up to 1 Gbps throughput – Sub millisecond latency – Up to 8, 000 transaction/second • Scalability – G 4: Entry for small to medium segments – G 8: Performance for larger segments – MX: Centralized management for multi-gateway environments 15 Imperva Confidential G 8 Gateway Appliance Throughput Requests Per Second Form Factor 1000 Mbps 8000 1 U Max Sniffing Interfaces 3 Max Inline Segments 1 G 4 Gateway Appliance Throughput Requests Per Second Form Factor 500 Mbps 4000 1 U Max Sniffing Interfaces 3 Max Inline Segments 1
Deployment Performance and Scalability • High Performance – Up to 1 Gbps throughput – Sub millisecond latency – Up to 8, 000 transaction/second • Scalability – G 4: Entry for small to medium segments – G 8: Performance for larger segments – MX: Centralized management for multi-gateway environments 15 Imperva Confidential G 8 Gateway Appliance Throughput Requests Per Second Form Factor 1000 Mbps 8000 1 U Max Sniffing Interfaces 3 Max Inline Segments 1 G 4 Gateway Appliance Throughput Requests Per Second Form Factor 500 Mbps 4000 1 U Max Sniffing Interfaces 3 Max Inline Segments 1
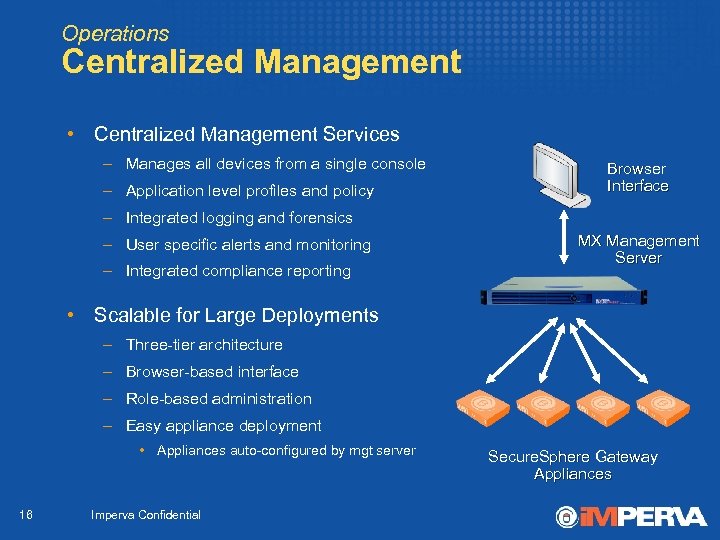 Operations Centralized Management • Centralized Management Services – Manages all devices from a single console – Application level profiles and policy Browser Interface – Integrated logging and forensics – User specific alerts and monitoring – Integrated compliance reporting MX Management Server • Scalable for Large Deployments – Three-tier architecture – Browser-based interface – Role-based administration – Easy appliance deployment • Appliances auto-configured by mgt server 16 Imperva Confidential Secure. Sphere Gateway Appliances
Operations Centralized Management • Centralized Management Services – Manages all devices from a single console – Application level profiles and policy Browser Interface – Integrated logging and forensics – User specific alerts and monitoring – Integrated compliance reporting MX Management Server • Scalable for Large Deployments – Three-tier architecture – Browser-based interface – Role-based administration – Easy appliance deployment • Appliances auto-configured by mgt server 16 Imperva Confidential Secure. Sphere Gateway Appliances
 Summary Securing the Data Center • Businesses Vulnerable to New Data Center Threats – Identity theft, data theft, SQL injection, worms, and Do. S – Risking brand, revenue, and regulatory compliance • IPS and Network Firewalls are Not Enough – Do not protect proprietary information and custom business applications • Secure. Sphere - Data Center Ready Protection – Security • Protects proprietary information, custom applications, and critical servers • Blocks even the most sophisticated attacks – Deployment • No change to existing applications and infrastructure • Flexible networking and high availability • Performance and scalability – Operations • No manual tuning • Centralized management Ø Low TCO and High ROI 17
Summary Securing the Data Center • Businesses Vulnerable to New Data Center Threats – Identity theft, data theft, SQL injection, worms, and Do. S – Risking brand, revenue, and regulatory compliance • IPS and Network Firewalls are Not Enough – Do not protect proprietary information and custom business applications • Secure. Sphere - Data Center Ready Protection – Security • Protects proprietary information, custom applications, and critical servers • Blocks even the most sophisticated attacks – Deployment • No change to existing applications and infrastructure • Flexible networking and high availability • Performance and scalability – Operations • No manual tuning • Centralized management Ø Low TCO and High ROI 17
 Thank You Imperva Inc. 950 Tower Lane, Suite 1710 Foster City, CA 94404 Sales: (866) 926 -4678 www. imperva. com 18 Imperva Confidential
Thank You Imperva Inc. 950 Tower Lane, Suite 1710 Foster City, CA 94404 Sales: (866) 926 -4678 www. imperva. com 18 Imperva Confidential
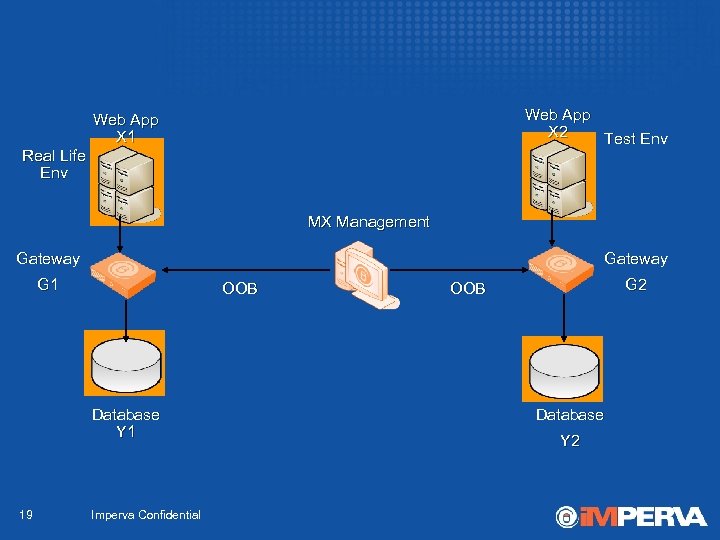 Web App X 2 Test Env Web App X 1 Real Life Env MX Management Gateway G 1 OOB Database Y 1 19 Imperva Confidential G 2 OOB Database Y 2
Web App X 2 Test Env Web App X 1 Real Life Env MX Management Gateway G 1 OOB Database Y 1 19 Imperva Confidential G 2 OOB Database Y 2


