cefaea88d178e96474818b9bcfd7c024.ppt
- Количество слайдов: 18
 Imperva The Leader in Application Data Security and Compliance Eran Cohen EMEA Sale Engineer Eran@imperva. com
Imperva The Leader in Application Data Security and Compliance Eran Cohen EMEA Sale Engineer Eran@imperva. com
 Agenda • Corporate Overview • Application Data Security and Compliance Why is it so difficult? • Introduction to Imperva Solutions • Universal User Tracking • Why Customers Select Imperva 2
Agenda • Corporate Overview • Application Data Security and Compliance Why is it so difficult? • Introduction to Imperva Solutions • Universal User Tracking • Why Customers Select Imperva 2
 Imperva Mission To deliver the industry’s most robust and widely deployed solution for addressing application data security and compliance issues. 3
Imperva Mission To deliver the industry’s most robust and widely deployed solution for addressing application data security and compliance issues. 3
 Imperva Overview • Leader in application data security and compliance – The market leader in Web Application Firewalls – Market leader in Database Audit, Monitoring and Security – Most impressive data security and compliance customer base in the industry • Founded in 2002 • Global Company – US headquarters in California; International headquarters in Israel – Local presence in all major global markets: USA, UK, France, Germany, Japan, China, Taiwan, Israel • 50 active channel partners world-wide • 300+ customers, will double customer base in ’ 07 • Seasoned management team, led by President and CEO Shlomo Kramer, one of 3 founders of Check Point 4
Imperva Overview • Leader in application data security and compliance – The market leader in Web Application Firewalls – Market leader in Database Audit, Monitoring and Security – Most impressive data security and compliance customer base in the industry • Founded in 2002 • Global Company – US headquarters in California; International headquarters in Israel – Local presence in all major global markets: USA, UK, France, Germany, Japan, China, Taiwan, Israel • 50 active channel partners world-wide • 300+ customers, will double customer base in ’ 07 • Seasoned management team, led by President and CEO Shlomo Kramer, one of 3 founders of Check Point 4
 Our Customers by Key Industry Segments Finance Credit Card Media / Telco 5 Healthcare Insurance
Our Customers by Key Industry Segments Finance Credit Card Media / Telco 5 Healthcare Insurance
 Our Customers by Key Industry Segments Government Technology e. Retail / Retail 6 Healthcare Insurance Credit Card Other
Our Customers by Key Industry Segments Government Technology e. Retail / Retail 6 Healthcare Insurance Credit Card Other
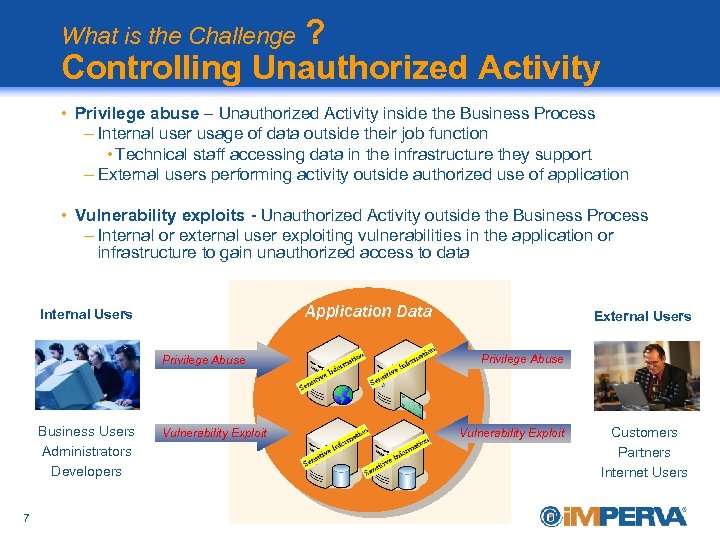 ? Controlling Unauthorized Activity What is the Challenge • Privilege abuse – Unauthorized Activity inside the Business Process – Internal user usage of data outside their job function • Technical staff accessing data in the infrastructure they support – External users performing activity outside authorized use of application • Vulnerability exploits - Unauthorized Activity outside the Business Process – Internal or external user exploiting vulnerabilities in the application or infrastructure to gain unauthorized access to data Application Data Internal Users Privilege Abuse Business Users Administrators Developers 7 Vulnerability Exploit External Users Privilege Abuse Vulnerability Exploit Customers Partners Internet Users
? Controlling Unauthorized Activity What is the Challenge • Privilege abuse – Unauthorized Activity inside the Business Process – Internal user usage of data outside their job function • Technical staff accessing data in the infrastructure they support – External users performing activity outside authorized use of application • Vulnerability exploits - Unauthorized Activity outside the Business Process – Internal or external user exploiting vulnerabilities in the application or infrastructure to gain unauthorized access to data Application Data Internal Users Privilege Abuse Business Users Administrators Developers 7 Vulnerability Exploit External Users Privilege Abuse Vulnerability Exploit Customers Partners Internet Users
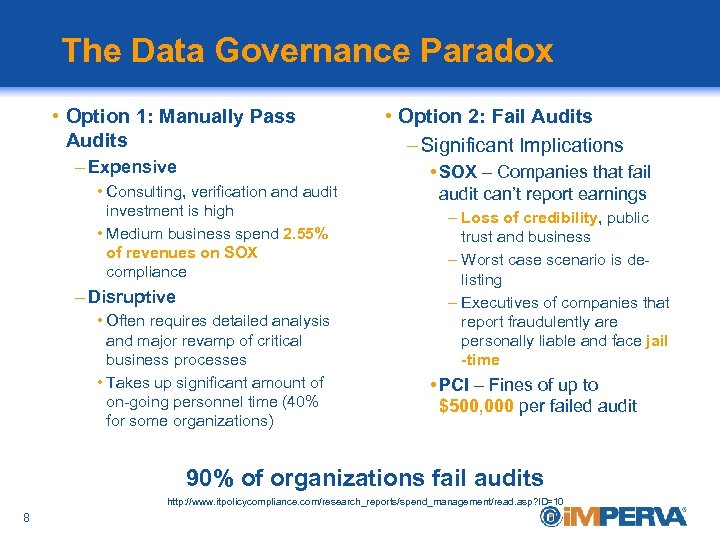 The Data Governance Paradox • Option 1: Manually Pass Audits – Expensive • Consulting, verification and audit investment is high • Medium business spend 2. 55% of revenues on SOX compliance – Disruptive • Often requires detailed analysis and major revamp of critical business processes • Takes up significant amount of on-going personnel time (40% for some organizations) • Option 2: Fail Audits – Significant Implications • SOX – Companies that fail audit can’t report earnings – Loss of credibility, public trust and business – Worst case scenario is delisting – Executives of companies that report fraudulently are personally liable and face jail -time • PCI – Fines of up to $500, 000 per failed audit 90% of organizations fail audits http: //www. itpolicycompliance. com/research_reports/spend_management/read. asp? ID=10 8
The Data Governance Paradox • Option 1: Manually Pass Audits – Expensive • Consulting, verification and audit investment is high • Medium business spend 2. 55% of revenues on SOX compliance – Disruptive • Often requires detailed analysis and major revamp of critical business processes • Takes up significant amount of on-going personnel time (40% for some organizations) • Option 2: Fail Audits – Significant Implications • SOX – Companies that fail audit can’t report earnings – Loss of credibility, public trust and business – Worst case scenario is delisting – Executives of companies that report fraudulently are personally liable and face jail -time • PCI – Fines of up to $500, 000 per failed audit 90% of organizations fail audits http: //www. itpolicycompliance. com/research_reports/spend_management/read. asp? ID=10 8
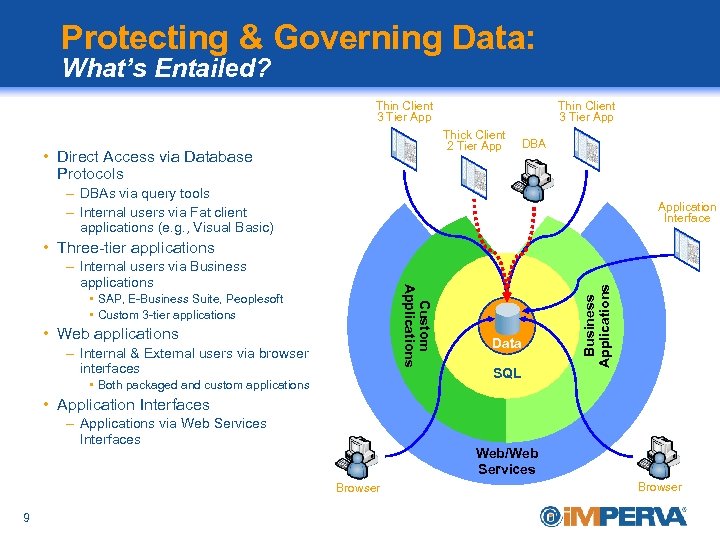 Protecting & Governing Data: What’s Entailed? Thin Client 3 Tier App Thick Client 2 Tier App • Direct Access via Database Protocols DBA – DBAs via query tools – Internal users via Fat client applications (e. g. , Visual Basic) Application Interface Custom Applications – Internal users via Business applications • SAP, E-Business Suite, Peoplesoft • Custom 3 -tier applications • Web applications – Internal & External users via browser interfaces • Both packaged and custom applications Data SQL Business Applications • Three-tier applications • Application Interfaces – Applications via Web Services Interfaces Web/Web Services Browser 9 Browser
Protecting & Governing Data: What’s Entailed? Thin Client 3 Tier App Thick Client 2 Tier App • Direct Access via Database Protocols DBA – DBAs via query tools – Internal users via Fat client applications (e. g. , Visual Basic) Application Interface Custom Applications – Internal users via Business applications • SAP, E-Business Suite, Peoplesoft • Custom 3 -tier applications • Web applications – Internal & External users via browser interfaces • Both packaged and custom applications Data SQL Business Applications • Three-tier applications • Application Interfaces – Applications via Web Services Interfaces Web/Web Services Browser 9 Browser
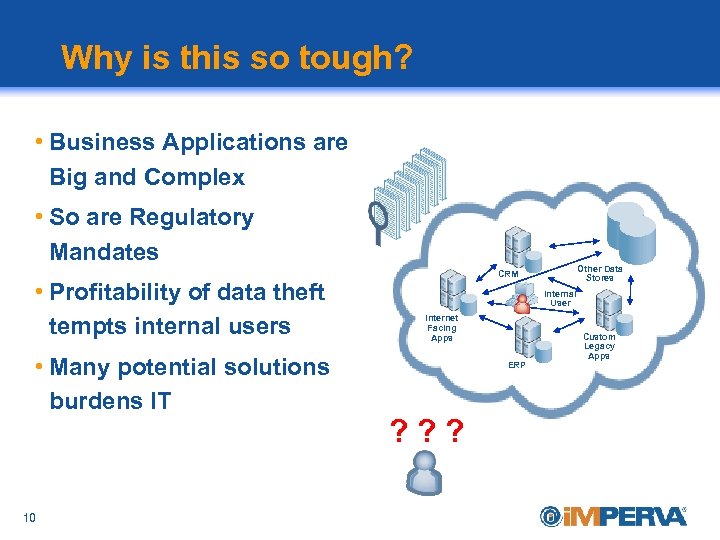 Why is this so tough? • Business Applications are Big and Complex • So are Regulatory Mandates • Profitability of data theft tempts internal users • Many potential solutions burdens IT 10 Other Data Stores CRM Internal User Internet Facing Apps ERP ? ? ? Custom Legacy Apps
Why is this so tough? • Business Applications are Big and Complex • So are Regulatory Mandates • Profitability of data theft tempts internal users • Many potential solutions burdens IT 10 Other Data Stores CRM Internal User Internet Facing Apps ERP ? ? ? Custom Legacy Apps
 Introducing Secure. Sphere • Industry’s only complete solution for security and compliance of enterprise data. • Activity monitoring, audit and security for business applications and databases. • Offers full visibility into data usage – From end user through application and into database – Hybrid network and host-based architecture • Visibility and controls for all data access points • >300 customers, 1000’s of sites and 10, 000’s of applications protected “Database monitoring and auditing is one of the most promising new categories of data security, and one with particular appeal to internal and external auditors. ” Rich Mogull, Research Vice President, Gartner 11
Introducing Secure. Sphere • Industry’s only complete solution for security and compliance of enterprise data. • Activity monitoring, audit and security for business applications and databases. • Offers full visibility into data usage – From end user through application and into database – Hybrid network and host-based architecture • Visibility and controls for all data access points • >300 customers, 1000’s of sites and 10, 000’s of applications protected “Database monitoring and auditing is one of the most promising new categories of data security, and one with particular appeal to internal and external auditors. ” Rich Mogull, Research Vice President, Gartner 11
 Easing Regulatory and Security Compliance Meet Business and Technical Needs Complete Data Governance and Protection • Assess the IT environment • Set Controls and Policies • Monitor Activity and Enforce the Rules • Measure against regulatory requirements and security policies Seamless Deployment, Unrivaled Operational Efficiency • • • No Impact on Database Server No Impact on Applications or Network No On-going Tuning Hierarchical Object Oriented definition of Users, Roles, Applications Task Oriented Workflow Covers all WEB traffic and WEB Services • Covers all major databases – Oracle, SQL Server, Sybase, IBM DB 2 (including z/OS) and Informix 12
Easing Regulatory and Security Compliance Meet Business and Technical Needs Complete Data Governance and Protection • Assess the IT environment • Set Controls and Policies • Monitor Activity and Enforce the Rules • Measure against regulatory requirements and security policies Seamless Deployment, Unrivaled Operational Efficiency • • • No Impact on Database Server No Impact on Applications or Network No On-going Tuning Hierarchical Object Oriented definition of Users, Roles, Applications Task Oriented Workflow Covers all WEB traffic and WEB Services • Covers all major databases – Oracle, SQL Server, Sybase, IBM DB 2 (including z/OS) and Informix 12
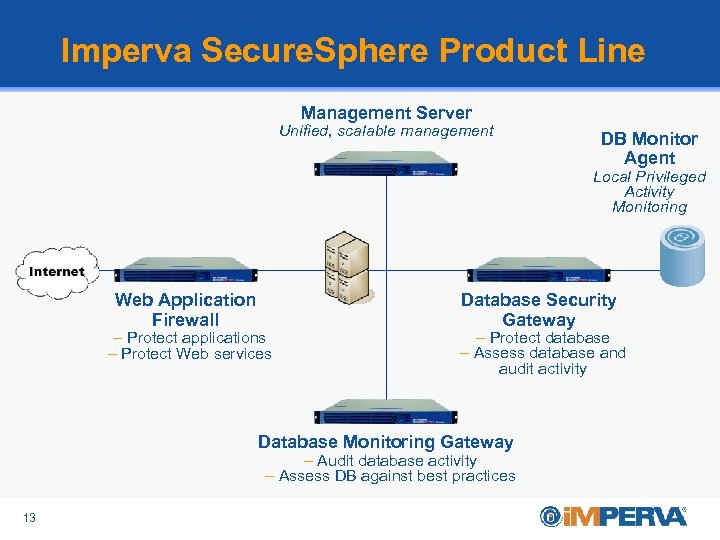 Imperva Secure. Sphere Product Line • MX Management Server Unified, scalable management – Centralized operations • Web Application Firewall (WAF) – Role-based Administration – Automated, efficient application security – Hierarchical management for – Starting point for some enterprises • Database Security Gateway (DSG) large organizations • Most customers expand to DSG in second– Adds preventative controls to DMG phase • Active security enforcement Web Application • Database Monitoring Gateway (DMG) Firewall – Protect applications – Full DB Audit and security lifecycle – Protect Web services • • Assessment Policies Monitoring Measurement – Full visibility to the end (application) user – Full compliance policy and reporting suite 13 DB Monitor Agent Local Privileged Activity Monitoring Database Security Gateway – Protect database • DBA Monitor Agents – Assess database and – Provides full visibility into local activity audit activity on database servers – Complementary to Database Appliances Database Monitoring Gateway – Audit database activity – Assess DB against best practices
Imperva Secure. Sphere Product Line • MX Management Server Unified, scalable management – Centralized operations • Web Application Firewall (WAF) – Role-based Administration – Automated, efficient application security – Hierarchical management for – Starting point for some enterprises • Database Security Gateway (DSG) large organizations • Most customers expand to DSG in second– Adds preventative controls to DMG phase • Active security enforcement Web Application • Database Monitoring Gateway (DMG) Firewall – Protect applications – Full DB Audit and security lifecycle – Protect Web services • • Assessment Policies Monitoring Measurement – Full visibility to the end (application) user – Full compliance policy and reporting suite 13 DB Monitor Agent Local Privileged Activity Monitoring Database Security Gateway – Protect database • DBA Monitor Agents – Assess database and – Provides full visibility into local activity audit activity on database servers – Complementary to Database Appliances Database Monitoring Gateway – Audit database activity – Assess DB against best practices
 Imperva Application Defense Center • Application Data Security and Compliance Experts – Researches latest threats and compliance best practices • Applications (SAP, Oracle EBS, PHP, Perl, OWA & others) • Databases (Oracle, DB 2, SQL-Server & others) • Compliance mandates (SOX, PCI, HIPAA & others) – Provides weekly & on demand updates via ADC Insight Services 14
Imperva Application Defense Center • Application Data Security and Compliance Experts – Researches latest threats and compliance best practices • Applications (SAP, Oracle EBS, PHP, Perl, OWA & others) • Databases (Oracle, DB 2, SQL-Server & others) • Compliance mandates (SOX, PCI, HIPAA & others) – Provides weekly & on demand updates via ADC Insight Services 14
 Universal User Tracking Imperva Secure. Sphere provides the most: • Accurate • Effective • Flexible set of user identification mechanisms to identify the user responsible for each instance of database access 15
Universal User Tracking Imperva Secure. Sphere provides the most: • Accurate • Effective • Flexible set of user identification mechanisms to identify the user responsible for each instance of database access 15
 Application User Tracking • Web Application User Tracking: – Identifies and tracks individual web users and their interactions with web applications • Web to Database User Tracking: – Tracks each web application user’s activities from their interactions with the web application through each of their interactions with the database • SQL Connection User Tracking: – Links each end user’s identity to the SQL commands the user makes to a database in cases of connection pooling 16
Application User Tracking • Web Application User Tracking: – Identifies and tracks individual web users and their interactions with web applications • Web to Database User Tracking: – Tracks each web application user’s activities from their interactions with the web application through each of their interactions with the database • SQL Connection User Tracking: – Links each end user’s identity to the SQL commands the user makes to a database in cases of connection pooling 16
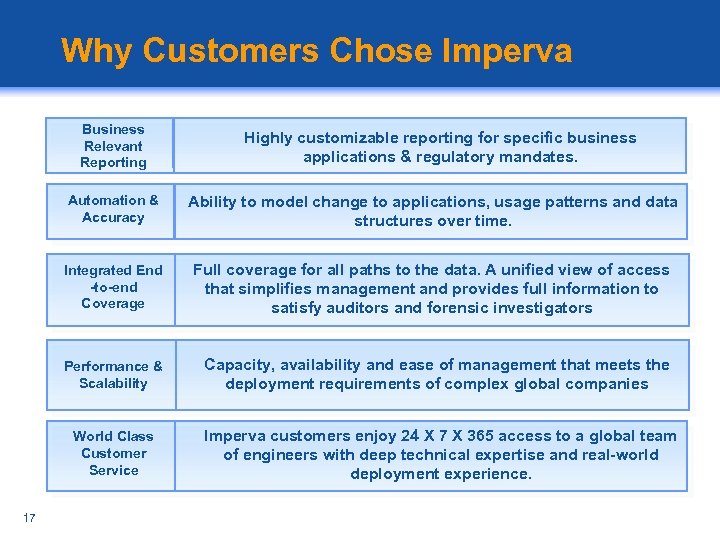 Why Customers Chose Imperva Business Relevant Reporting Highly customizable reporting for specific business applications & regulatory mandates. Automation & Accuracy Integrated End -to-end Coverage Full coverage for all paths to the data. A unified view of access that simplifies management and provides full information to satisfy auditors and forensic investigators Performance & Scalability Capacity, availability and ease of management that meets the deployment requirements of complex global companies World Class Customer Service 17 Ability to model change to applications, usage patterns and data structures over time. Imperva customers enjoy 24 X 7 X 365 access to a global team of engineers with deep technical expertise and real-world deployment experience.
Why Customers Chose Imperva Business Relevant Reporting Highly customizable reporting for specific business applications & regulatory mandates. Automation & Accuracy Integrated End -to-end Coverage Full coverage for all paths to the data. A unified view of access that simplifies management and provides full information to satisfy auditors and forensic investigators Performance & Scalability Capacity, availability and ease of management that meets the deployment requirements of complex global companies World Class Customer Service 17 Ability to model change to applications, usage patterns and data structures over time. Imperva customers enjoy 24 X 7 X 365 access to a global team of engineers with deep technical expertise and real-world deployment experience.
 Thank You Imperva, Inc. www. imperva. com
Thank You Imperva, Inc. www. imperva. com


