97f4981b706beacaaa488b722999e0ad.ppt
- Количество слайдов: 21

Illinois Security Lab Using Attribute-Based Access Control to Enable Attribute. Based Messaging Rakesh Bobba, Omid Fatemieh, Fariba Khan, Carl A. Gunter and Himanshu Khurana University of Illinois at Urbana-Champaign ACSAC 2006
Introduction to ABM Illinois Security Lab Attribute-Based Messaging (ABM): Targeting messages based on attributes. To: faculty going on sabbatical ACSAC 2006

Introduction to ABM Illinois Security Lab Attribute-Based Messaging (ABM): Targeting messages based on attributes. Examples • Address all faculty going on sabbatical next term • Notify all female CS graduate students who passed qualifying exams of a scholarship opportunity ACSAC 2006

Illinois Why ABM? Security Lab • Attribute-based systems have desirable properties – flexibility, privacy and intuitiveness • Attribute-Based Messaging (ABM) brings these advantages to e-mail messaging – enhances confidentiality by supporting targeted messaging • via dynamic and transient groups – enhances relevance of messages • by reducing unwanted messages ACSAC 2006

Challenges Illinois Security Lab • Access Control – access to such a system should be carefully controlled • potential for spam • privacy of attributes • Deployability – system should be compatible with existing infrastructure • Efficiency – system should have comparable performance to regular e-mail ACSAC 2006
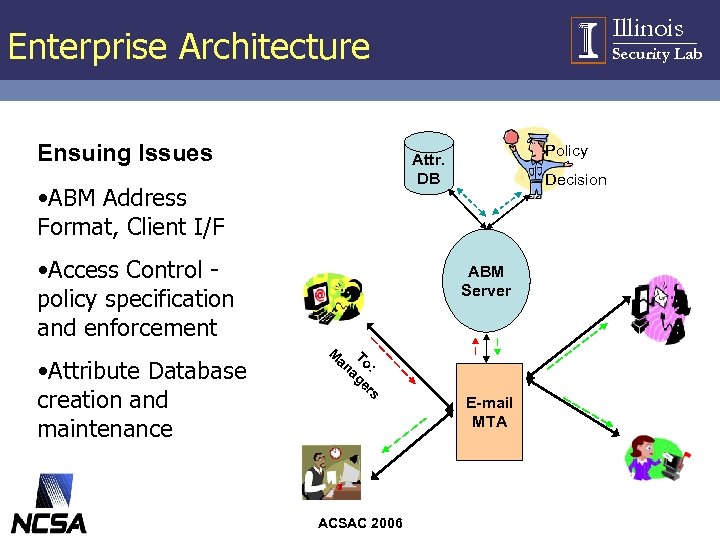
Illinois Enterprise Architecture Ensuing Issues Policy Attr. DB • ABM Address Format, Client I/F • Access Control policy specification and enforcement • Attribute Database creation and maintenance Security Lab Decision ABM Server M an To: ag er s ACSAC 2006 E-mail MTA
Enterprise Architecture cont. Illinois Security Lab • Attribute database – all enterprises have attribute data about their users – data spread over multiple, possibly disparate databases – assume that this attribute data is available to ABM system • “information fabric” , “data services layer” • ABM address format − logical expressions of attribute value pairs − disjunctive normal form ACSAC 2006

Illinois Access Control Security Lab • Access Control Lists (ACLs) – difficult to manage ACSAC 2006

Illinois Access Control Security Lab × Access Control Lists (ACLs) × difficult to manage • Role-Based Access Control (RBAC) – simplified management if roles already exist ACSAC 2006
Illinois Access Control Security Lab × Access Control Lists (ACLs) × difficult to manage × Role-Based Access Control (RBAC) × simplified management if roles already exist • Attribute-Based Access Control (ABAC) − uses same attributes used to target messages − more flexible policies than with RBAC • Access policy − XACML is used to specify access policies − Sun’s XACML engine is used for policy decision ACSAC 2006

Access Control cont. • Problem – need policy per logical expression – policy explosion • Solution? – one policy per <attribute, value> ACSAC 2006 Illinois Security Lab
Illinois Deployability Security Lab • Use existing e-mail infrastructure (SMTP) – address ABM messages to the ABM server (MUA) and add ABM address as a MIME attachment • No modification to client – use a web server to aid the sender in composing the ABM address via a thin client (web browser) • E-mail like semantics – policy specialization ACSAC 2006
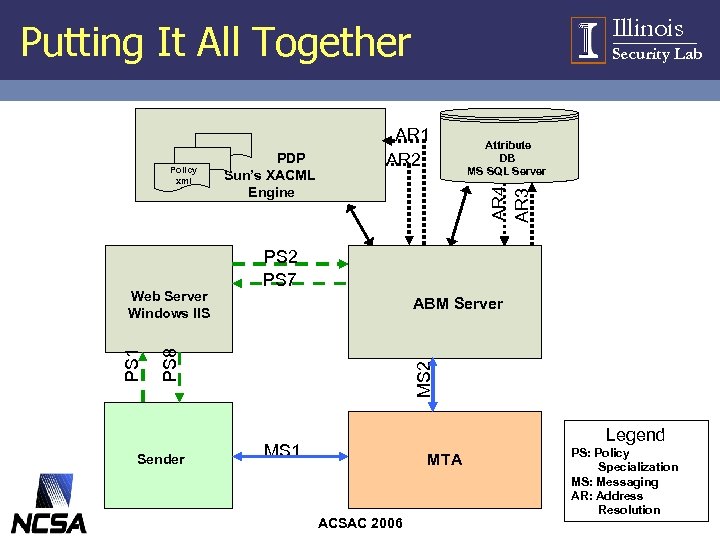
Illinois Putting It All Together Sender Attribute DB MS SQL Server PS 2 PS 7 ABM Server MS 2 PS 8 PS 1 Web Server Windows IIS AR 1 AR 2 AR 4 AR 3 Policy xml PDP Sun’s XACML Engine Security Lab Legend MS 1 MTA ACSAC 2006 PS: Policy Specialization MS: Messaging AR: Address Resolution
Illinois Security Analysis Security Lab • Problem – open to replay attacks • Solution – MTA configured with SMTP authentication • with additional message specific checks ACSAC 2006
Experimental Setup • Measured – latency over regular e-mail • with and without access control – latency of Policy Specialization • Setup – up to 60 K users – 100 attributes in the system • 20% of attributes common to most users • 80% of attributes sparsely distributed ACSAC 2006 Illinois Security Lab
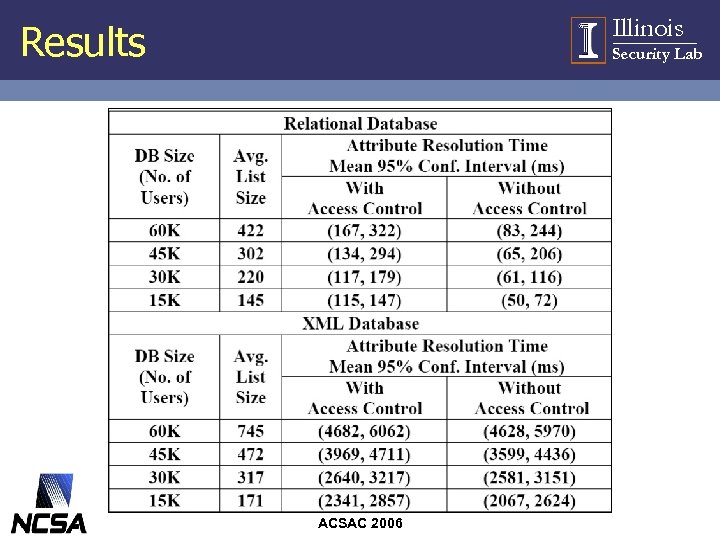
Illinois Results Security Lab ACSAC 2006
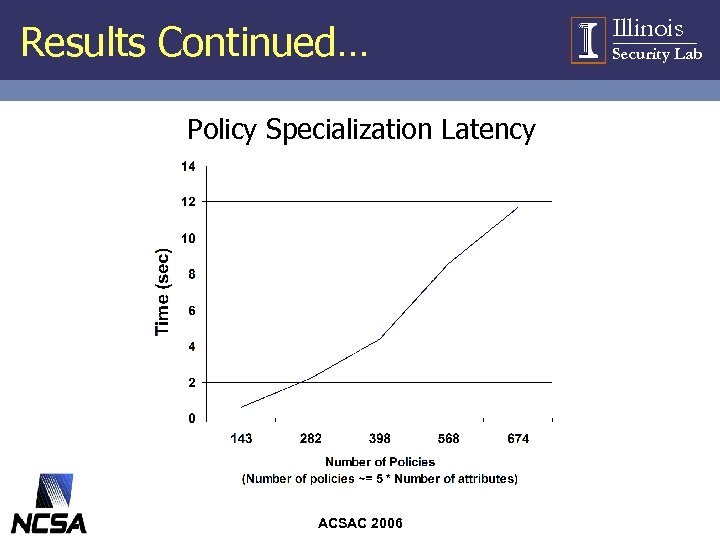
Results Continued… Policy Specialization Latency ACSAC 2006 Illinois Security Lab

Other Considerations Illinois Security Lab • Policy Administration – one policy per <attribute , value> not per address – further be reduced to one policy per attribute • Privacy – of sender and receivers – of ABM address • Usability – user interfaces ACSAC 2006

Illinois Related Work Security Lab • Technologies – List Servers – Customer Relationship Management (CRM) • Secure role-based messaging • WSEmail ACSAC 2006
Illinois Future Work Security Lab • Inter-domain ABM – e. g. , address doctors in the tri-state area who have expertise in a specific kind of surgical procedure – challenge – “attribute mapping” – application in ‘emergency communications’ • Encrypted ABM ACSAC 2006

Illinois Security Lab ACSAC 2006
97f4981b706beacaaa488b722999e0ad.ppt