da567cc1f642da45681d6f166c894b2f.ppt
- Количество слайдов: 38
 IIS 6. 0 SECURITY ARCHITECTURE It’s a Whole New World Michael Muckin Security Architect Microsoft Consulting Services
IIS 6. 0 SECURITY ARCHITECTURE It’s a Whole New World Michael Muckin Security Architect Microsoft Consulting Services
 Agenda Setting the Stage IIS 6. 0 Security design ASP. NET Security Config Scanning & Tools Hardening IIS 6. 0 Demos throughout
Agenda Setting the Stage IIS 6. 0 Security design ASP. NET Security Config Scanning & Tools Hardening IIS 6. 0 Demos throughout
 Setting the Stage No news that IIS is a primary target What is this “Security Push” and Trustworthy Computing? IIS 6. 0 should be tangible evidence of these initiatives
Setting the Stage No news that IIS is a primary target What is this “Security Push” and Trustworthy Computing? IIS 6. 0 should be tangible evidence of these initiatives
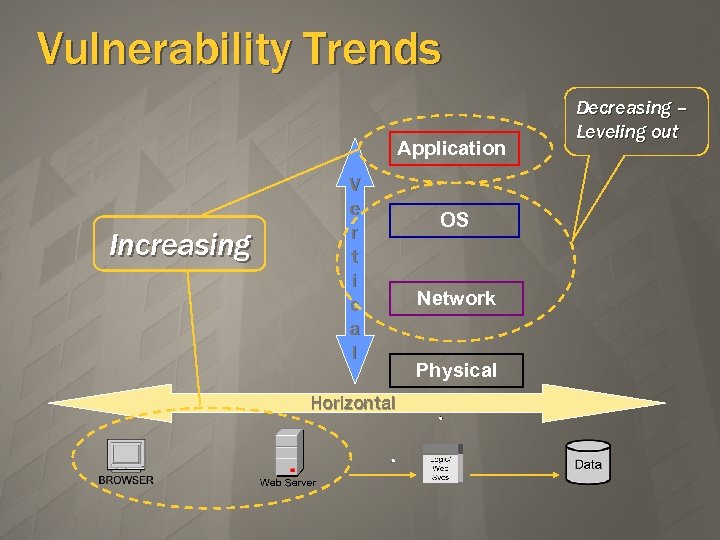 Vulnerability Trends Application Increasing V e r t i c a l Horizontal OS Network Physical Decreasing – Leveling out
Vulnerability Trends Application Increasing V e r t i c a l Horizontal OS Network Physical Decreasing – Leveling out
 IIS 6. 0 Security Design Product quality Improve design, coding, and testing practices Fewer vulnerabilities out of the box Security conscious architecture Reduced attack surface Defense in depth Limit the possible damage should new vulnerabilities be discovered Always up-to-date Make it practical to keep systems up-to-date with the latest software patches
IIS 6. 0 Security Design Product quality Improve design, coding, and testing practices Fewer vulnerabilities out of the box Security conscious architecture Reduced attack surface Defense in depth Limit the possible damage should new vulnerabilities be discovered Always up-to-date Make it practical to keep systems up-to-date with the latest software patches
 Product Quality Security stand-down Development practices /GS Prefix/Prefast runs Single String Class QFE and IIS core team merged Code review for every change External reviews keep us honest Removed legacy code Security design review for every feature Extensive test infrastructure External tools Internal tools IIS tools Buffer overflow scanner Cross-site scripting Fault injection in regular test runs
Product Quality Security stand-down Development practices /GS Prefix/Prefast runs Single String Class QFE and IIS core team merged Code review for every change External reviews keep us honest Removed legacy code Security design review for every feature Extensive test infrastructure External tools Internal tools IIS tools Buffer overflow scanner Cross-site scripting Fault injection in regular test runs
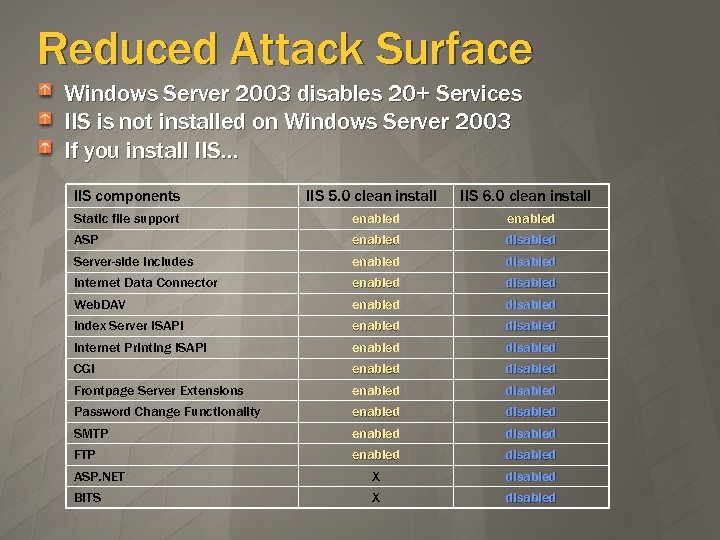 Reduced Attack Surface Windows Server 2003 disables 20+ Services IIS is not installed on Windows Server 2003 If you install IIS… IIS components Static file support IIS 5. 0 clean install IIS 6. 0 clean install enabled enabled disabled disabled enabled disabled enabled disabled ASP. NET X BITS X disabled ASP Server-side includes Internet Data Connector Web. DAV Index Server ISAPI Internet Printing ISAPI CGI Frontpage Server Extensions Password Change Functionality SMTP FTP
Reduced Attack Surface Windows Server 2003 disables 20+ Services IIS is not installed on Windows Server 2003 If you install IIS… IIS components Static file support IIS 5. 0 clean install IIS 6. 0 clean install enabled enabled disabled disabled enabled disabled enabled disabled ASP. NET X BITS X disabled ASP Server-side includes Internet Data Connector Web. DAV Index Server ISAPI Internet Printing ISAPI CGI Frontpage Server Extensions Password Change Functionality SMTP FTP
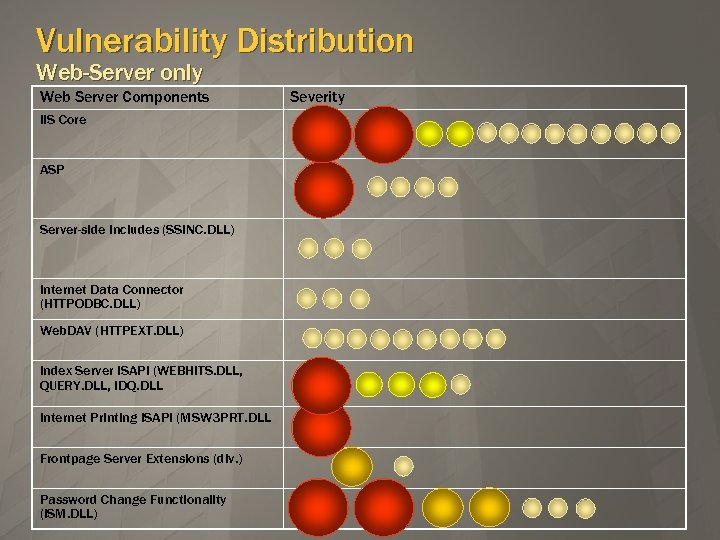 Vulnerability Distribution Web-Server only Web Server Components IIS Core ASP Server-side includes (SSINC. DLL) Internet Data Connector (HTTPODBC. DLL) Web. DAV (HTTPEXT. DLL) Index Server ISAPI (WEBHITS. DLL, QUERY. DLL, IDQ. DLL Internet Printing ISAPI (MSW 3 PRT. DLL Frontpage Server Extensions (div. ) Password Change Functionality (ISM. DLL) Severity
Vulnerability Distribution Web-Server only Web Server Components IIS Core ASP Server-side includes (SSINC. DLL) Internet Data Connector (HTTPODBC. DLL) Web. DAV (HTTPEXT. DLL) Index Server ISAPI (WEBHITS. DLL, QUERY. DLL, IDQ. DLL Internet Printing ISAPI (MSW 3 PRT. DLL Frontpage Server Extensions (div. ) Password Change Functionality (ISM. DLL) Severity
 Defense In Depth Buffer overflows New Low Privilege accts: Network Service (default) and Local Service Default Privileges: Se. Assign. Primary. Token. Privilege Se. Security. Privilege Se. Systemtime. Privilege Se. Audit. Privilege Se. Change. Notify. Privilege Se. Undock. Privilege …vs. the Local. System account – which has almost every system Privilege (21 total)
Defense In Depth Buffer overflows New Low Privilege accts: Network Service (default) and Local Service Default Privileges: Se. Assign. Primary. Token. Privilege Se. Security. Privilege Se. Systemtime. Privilege Se. Audit. Privilege Se. Change. Notify. Privilege Se. Undock. Privilege …vs. the Local. System account – which has almost every system Privilege (21 total)
 Defense In Depth Canonicalization issues Rigorous and restrictive parsing Default handler is restricted to a list of known extensions Denial-of-service attacks Fault-tolerant infrastructure Limits Cross-site scripting issues ASP. NET data validation controls Executing command-line scripts Secure defaults: don’t allow anonymous account to execute *. exe’s Site defacements No write access for anonymous account in home dir
Defense In Depth Canonicalization issues Rigorous and restrictive parsing Default handler is restricted to a list of known extensions Denial-of-service attacks Fault-tolerant infrastructure Limits Cross-site scripting issues ASP. NET data validation controls Executing command-line scripts Secure defaults: don’t allow anonymous account to execute *. exe’s Site defacements No write access for anonymous account in home dir
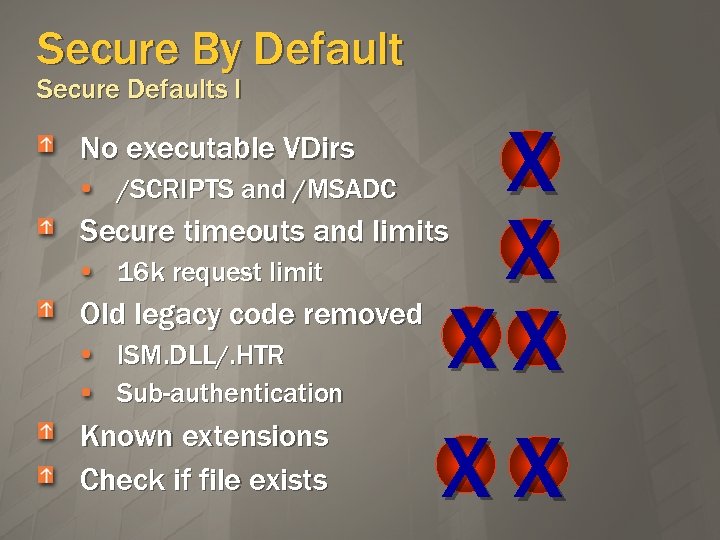 Secure By Default Secure Defaults I No executable VDirs /SCRIPTS and /MSADC X X XX XX Secure timeouts and limits 16 k request limit Old legacy code removed ISM. DLL/. HTR Sub-authentication Known extensions Check if file exists
Secure By Default Secure Defaults I No executable VDirs /SCRIPTS and /MSADC X X XX XX Secure timeouts and limits 16 k request limit Old legacy code removed ISM. DLL/. HTR Sub-authentication Known extensions Check if file exists
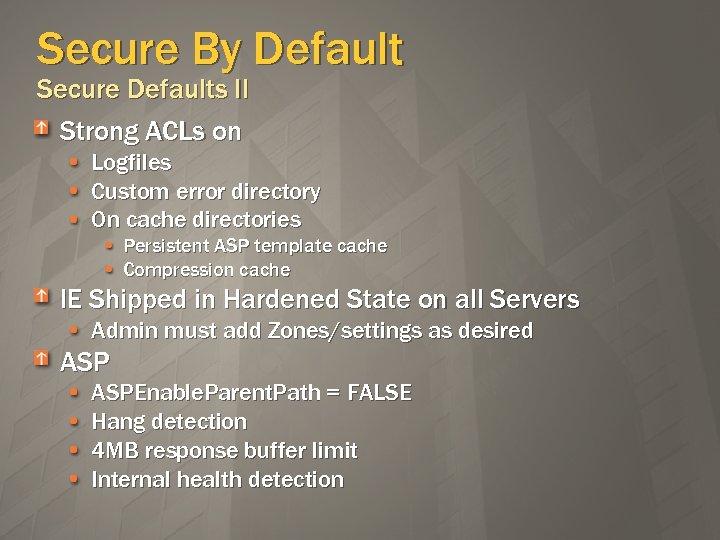 Secure By Default Secure Defaults II Strong ACLs on Logfiles Custom error directory On cache directories Persistent ASP template cache Compression cache IE Shipped in Hardened State on all Servers Admin must add Zones/settings as desired ASPEnable. Parent. Path = FALSE Hang detection 4 MB response buffer limit Internal health detection
Secure By Default Secure Defaults II Strong ACLs on Logfiles Custom error directory On cache directories Persistent ASP template cache Compression cache IE Shipped in Hardened State on all Servers Admin must add Zones/settings as desired ASPEnable. Parent. Path = FALSE Hang detection 4 MB response buffer limit Internal health detection
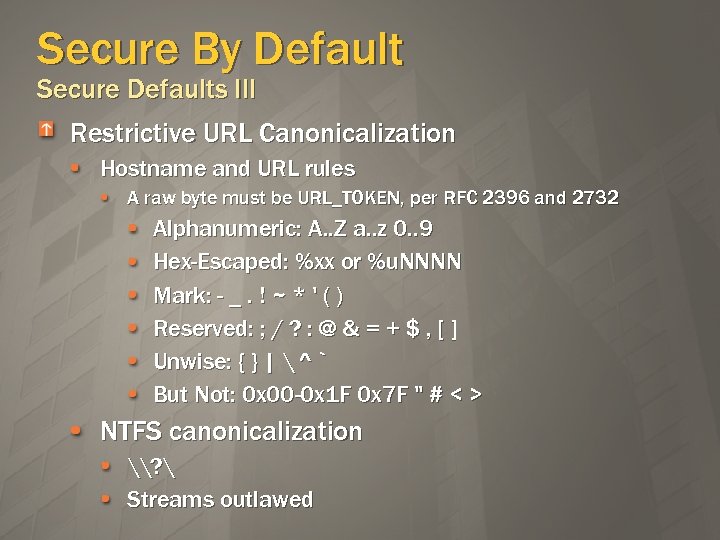 Secure By Default Secure Defaults III Restrictive URL Canonicalization Hostname and URL rules A raw byte must be URL_TOKEN, per RFC 2396 and 2732 Alphanumeric: A. . Z a. . z 0. . 9 Hex-Escaped: %xx or %u. NNNN Mark: - _. ! ~ * ' ( ) Reserved: ; / ? : @ & = + $ , [ ] Unwise: { } | ^ ` But Not: 0 x 00 -0 x 1 F 0 x 7 F " # < > NTFS canonicalization \? Streams outlawed
Secure By Default Secure Defaults III Restrictive URL Canonicalization Hostname and URL rules A raw byte must be URL_TOKEN, per RFC 2396 and 2732 Alphanumeric: A. . Z a. . z 0. . 9 Hex-Escaped: %xx or %u. NNNN Mark: - _. ! ~ * ' ( ) Reserved: ; / ? : @ & = + $ , [ ] Unwise: { } | ^ ` But Not: 0 x 00 -0 x 1 F 0 x 7 F " # < > NTFS canonicalization \? Streams outlawed
 Security Conscious Architecture Compartmentalization Third-Party code runs only in Worker Processes Powerful sandboxing HTTP pre-request logging
Security Conscious Architecture Compartmentalization Third-Party code runs only in Worker Processes Powerful sandboxing HTTP pre-request logging
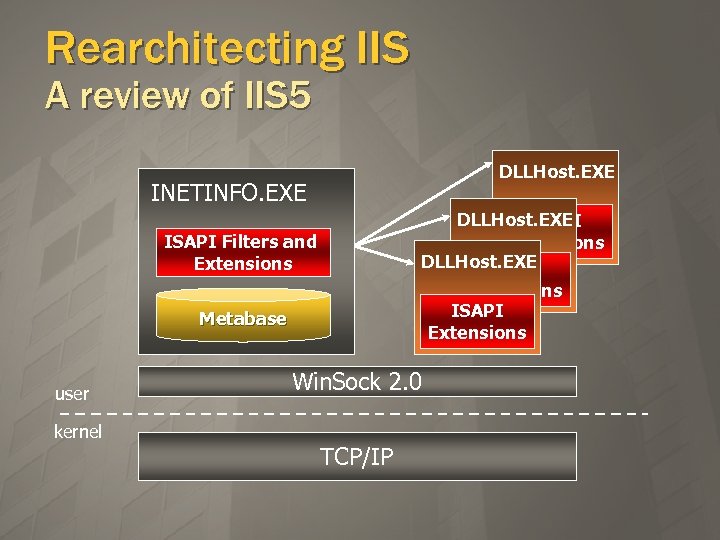 Rearchitecting IIS A review of IIS 5 DLLHost. EXE INETINFO. EXE DLLHost. EXE ISAPI Extensions ISAPI Filters and Extensions Metabase user kernel Win. Sock 2. 0 TCP/IP
Rearchitecting IIS A review of IIS 5 DLLHost. EXE INETINFO. EXE DLLHost. EXE ISAPI Extensions ISAPI Filters and Extensions Metabase user kernel Win. Sock 2. 0 TCP/IP
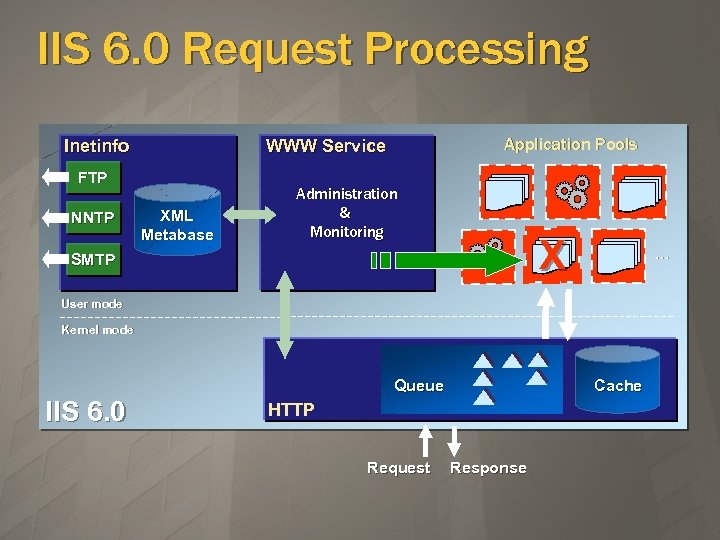 IIS 6. 0 Request Processing Inetinfo FTP NNTP Application Pools WWW Service XML Metabase Administration & Monitoring X SMTP … User mode Kernel mode Queue IIS 6. 0 Cache HTTP Request Response
IIS 6. 0 Request Processing Inetinfo FTP NNTP Application Pools WWW Service XML Metabase Administration & Monitoring X SMTP … User mode Kernel mode Queue IIS 6. 0 Cache HTTP Request Response
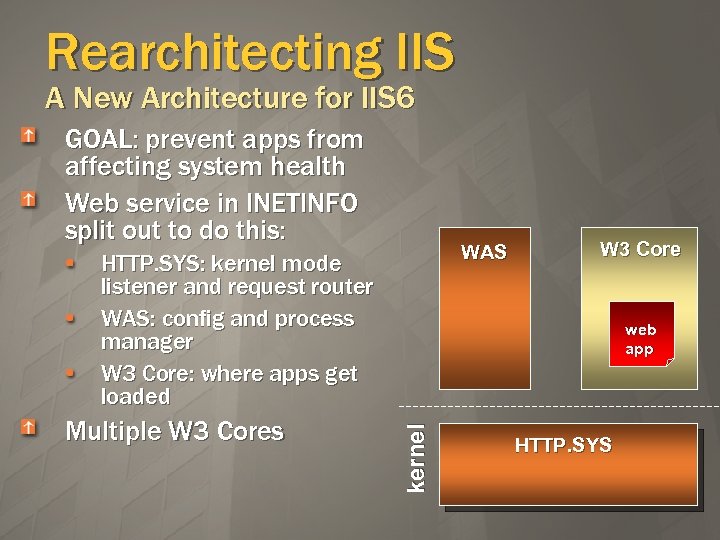 Rearchitecting IIS A New Architecture for IIS 6 GOAL: prevent apps from affecting system health Web service in INETINFO split out to do this: WAS HTTP. SYS: kernel mode listener and request router WAS: config and process manager W 3 Core: where apps get loaded web app kernel Multiple W 3 Cores W 3 Core HTTP. SYS
Rearchitecting IIS A New Architecture for IIS 6 GOAL: prevent apps from affecting system health Web service in INETINFO split out to do this: WAS HTTP. SYS: kernel mode listener and request router WAS: config and process manager W 3 Core: where apps get loaded web app kernel Multiple W 3 Cores W 3 Core HTTP. SYS
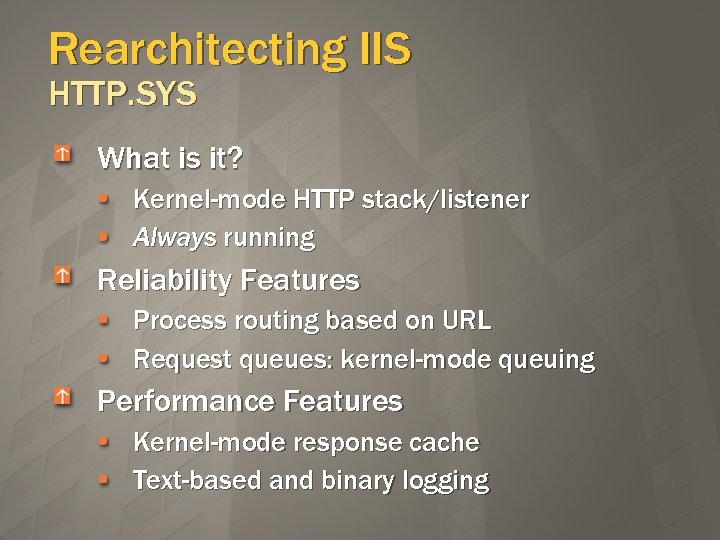 Rearchitecting IIS HTTP. SYS What is it? Kernel-mode HTTP stack/listener Always running Reliability Features Process routing based on URL Request queues: kernel-mode queuing Performance Features Kernel-mode response cache Text-based and binary logging
Rearchitecting IIS HTTP. SYS What is it? Kernel-mode HTTP stack/listener Always running Reliability Features Process routing based on URL Request queues: kernel-mode queuing Performance Features Kernel-mode response cache Text-based and binary logging
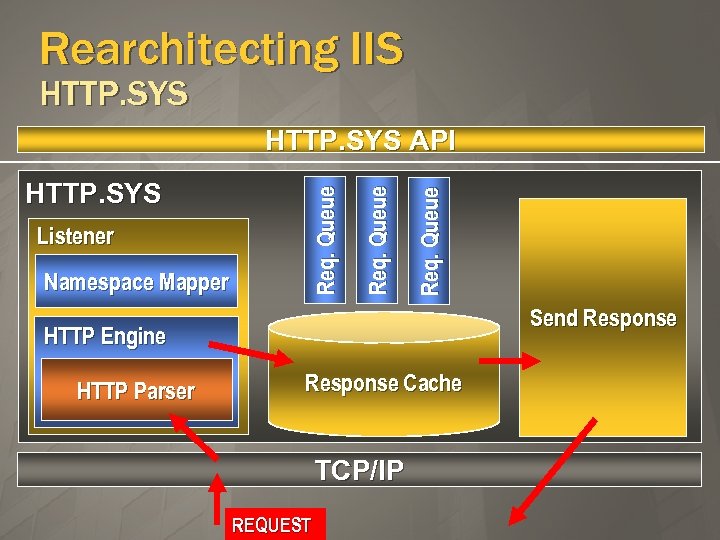 Rearchitecting IIS HTTP. SYS Namespace Mapper Req. Queue Listener Req. Queue HTTP. SYS API Send Response HTTP Engine HTTP Parser Response Cache TCP/IP REQUEST
Rearchitecting IIS HTTP. SYS Namespace Mapper Req. Queue Listener Req. Queue HTTP. SYS API Send Response HTTP Engine HTTP Parser Response Cache TCP/IP REQUEST
 Rearchitecting IIS Web Admin Service (WAS) Application Manager Manages lifetime of W 3 Core(s) Configuration Manager Configures HTTP. SYS No application code Ensures reliability Easier to identify problems Hosted in SVCHOST. exe
Rearchitecting IIS Web Admin Service (WAS) Application Manager Manages lifetime of W 3 Core(s) Configuration Manager Configures HTTP. SYS No application code Ensures reliability Easier to identify problems Hosted in SVCHOST. exe
 Rearchitecting IIS W 3 Core What is it? Main web processing DLL responsible for processing web requests Mini-web server Contains all web request processing functionality Loads ISAPI’s – filters and extensions Separates request processing from rest of web server
Rearchitecting IIS W 3 Core What is it? Main web processing DLL responsible for processing web requests Mini-web server Contains all web request processing functionality Loads ISAPI’s – filters and extensions Separates request processing from rest of web server
 Application Pools Application Isolation in Processes Can create 1 or more application pools Each served by 1 or more processes. Each worker process serves only 1 pool. Reqs routed directly to pool by HTTP. sys Isolate apps based on: Site/Customer Functionality Reliability
Application Pools Application Isolation in Processes Can create 1 or more application pools Each served by 1 or more processes. Each worker process serves only 1 pool. Reqs routed directly to pool by HTTP. sys Isolate apps based on: Site/Customer Functionality Reliability
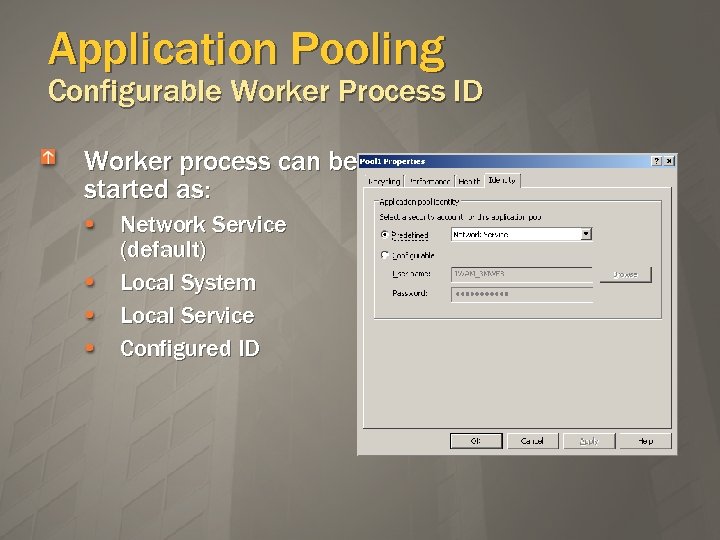 Application Pooling Configurable Worker Process ID Worker process can be started as: Network Service (default) Local System Local Service Configured ID
Application Pooling Configurable Worker Process ID Worker process can be started as: Network Service (default) Local System Local Service Configured ID
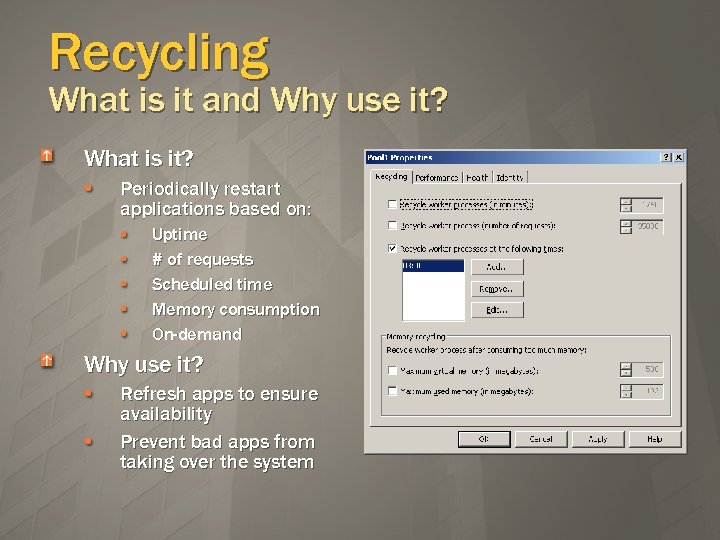 Recycling What is it and Why use it? What is it? Periodically restart applications based on: Uptime # of requests Scheduled time Memory consumption On-demand Why use it? Refresh apps to ensure availability Prevent bad apps from taking over the system
Recycling What is it and Why use it? What is it? Periodically restart applications based on: Uptime # of requests Scheduled time Memory consumption On-demand Why use it? Refresh apps to ensure availability Prevent bad apps from taking over the system
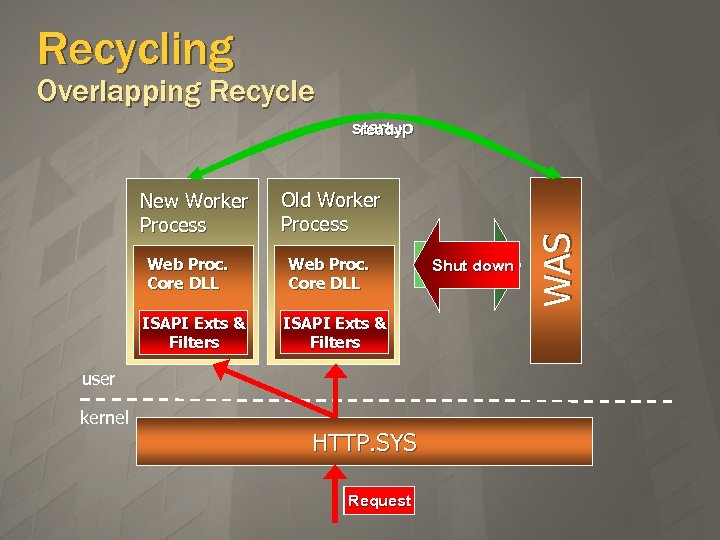 Recycling Overlapping Recycle New Worker Process Web Proc. Core DLL ISAPI Exts & Filters Old Worker Process Web Proc. Core DLL ISAPI Exts & Filters user kernel HTTP. SYS Request Ready for Shut down Recycle WAS startup ready
Recycling Overlapping Recycle New Worker Process Web Proc. Core DLL ISAPI Exts & Filters Old Worker Process Web Proc. Core DLL ISAPI Exts & Filters user kernel HTTP. SYS Request Ready for Shut down Recycle WAS startup ready
 Countering Do. S ISAPI Interaction – REPORT_UNHEALTHY HSE_REQ_REPORT_UNHEALTHY Goal: allow an ISAPI to report to IIS that it needs to be recycled. b. Result = p. ECB-> Server. Support. Function( p. ECB->Conn. ID, HSE_REQ_REPORT_UNHEALTHY, psz_reason_unhealthy, NULL ); ASP Hang Detection Used to detect when ASP threads block in components
Countering Do. S ISAPI Interaction – REPORT_UNHEALTHY HSE_REQ_REPORT_UNHEALTHY Goal: allow an ISAPI to report to IIS that it needs to be recycled. b. Result = p. ECB-> Server. Support. Function( p. ECB->Conn. ID, HSE_REQ_REPORT_UNHEALTHY, psz_reason_unhealthy, NULL ); ASP Hang Detection Used to detect when ASP threads block in components
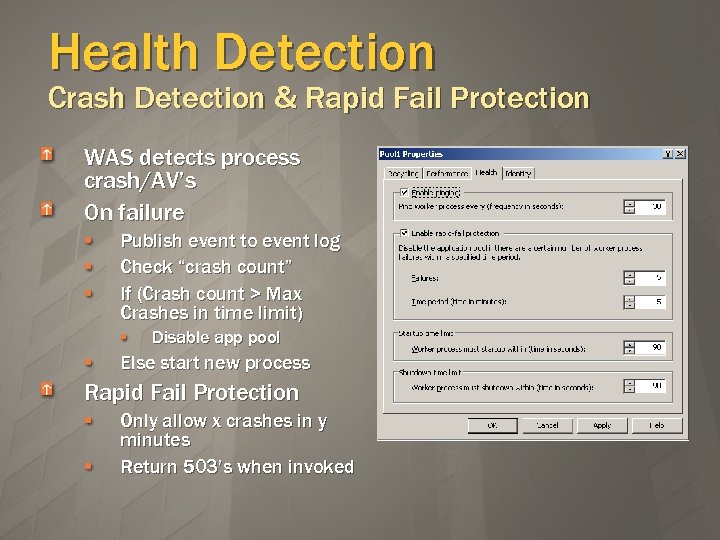 Health Detection Crash Detection & Rapid Fail Protection WAS detects process crash/AV’s On failure Publish event to event log Check “crash count” If (Crash count > Max Crashes in time limit) Disable app pool Else start new process Rapid Fail Protection Only allow x crashes in y minutes Return 503’s when invoked
Health Detection Crash Detection & Rapid Fail Protection WAS detects process crash/AV’s On failure Publish event to event log Check “crash count” If (Crash count > Max Crashes in time limit) Disable app pool Else start new process Rapid Fail Protection Only allow x crashes in y minutes Return 503’s when invoked
 ASP. NET Secure Config ASP. NET Security Layers Configuring ASP. NET Security Server-side Input Validation
ASP. NET Secure Config ASP. NET Security Layers Configuring ASP. NET Security Server-side Input Validation
 ASP. NET Security Layers IIS Authentication URLScan (not specific to ASP. NET) Static file ACLs ASP. NET Web Service Extensions Authorization by Role and URL File access by ASP mapped extensions
ASP. NET Security Layers IIS Authentication URLScan (not specific to ASP. NET) Static file ACLs ASP. NET Web Service Extensions Authorization by Role and URL File access by ASP mapped extensions
 ASP. NET Accounts When ASP. NET is enabled – a new account is created: “ASPNET” – and a new Group “IIS_WPG” Configurable in IIS Service Manager MMC For multiple Pools requiring complete isolation: Create low-priv accounts for each Pool Add to IIS_WPG group Config each Pool with appropriate Identity Both ASPNET and the IUSR_xxxx accounts need Read and Execute (ntfs) access to ASP. NET files (. aspx, . asmx, etc. ) Careful of “code-behind” files that are being accessed – set ACLs appropriately – (aspx. cs, aspx. vb)
ASP. NET Accounts When ASP. NET is enabled – a new account is created: “ASPNET” – and a new Group “IIS_WPG” Configurable in IIS Service Manager MMC For multiple Pools requiring complete isolation: Create low-priv accounts for each Pool Add to IIS_WPG group Config each Pool with appropriate Identity Both ASPNET and the IUSR_xxxx accounts need Read and Execute (ntfs) access to ASP. NET files (. aspx, . asmx, etc. ) Careful of “code-behind” files that are being accessed – set ACLs appropriately – (aspx. cs, aspx. vb)
 ASP. NET Config Files Understanding the “. Config” files XML files with Web and App settings ACL these files tightly Remove “Users” and “Power Users” Hierarchical application of security settings Machine. config Web. config (For all ASP. NET apps) App 1 -> Web. config (Individual App settings) Resultant = inherited settings Settings: Auth. N, Auth. Z by Users, Roles (Domain and Forms) HTTP Verbs Allowed/Disallowed URLs File access Don’t put Connection Strings or User/Pwds in here !!
ASP. NET Config Files Understanding the “. Config” files XML files with Web and App settings ACL these files tightly Remove “Users” and “Power Users” Hierarchical application of security settings Machine. config Web. config (For all ASP. NET apps) App 1 -> Web. config (Individual App settings) Resultant = inherited settings Settings: Auth. N, Auth. Z by Users, Roles (Domain and Forms) HTTP Verbs Allowed/Disallowed URLs File access Don’t put Connection Strings or User/Pwds in here !!
" src="https://present5.com/presentation/da567cc1f642da45681d6f166c894b2f/image-34.jpg" alt="ASP. NET Server-side Validation C# Example (1) – The Control <%@ Page Language="C#" %>" />
ASP. NET Server-side Validation C# Example (1) – The Control <%@ Page Language="C#" %>
 Scanning an IIS 6 Default Box Scanning an ASP. NET enabled Box Log Parser IISLock. Down/URLScan Web Extensions
Scanning an IIS 6 Default Box Scanning an ASP. NET enabled Box Log Parser IISLock. Down/URLScan Web Extensions
 Summary Completely new Architecture Kernel mode request handling Complete Application Isolation Secure Defaults At the Code Level Deployment – Default IIS box is only a static web server – Admin must turn on what is needed IIS/ASP. NET focus on App-layer security Web Service Extensions URLScan ASP. Net. config files Server-side Controls > 10, 000 sites already live on IIS 6. 0 microsoft. com running production since RC 1
Summary Completely new Architecture Kernel mode request handling Complete Application Isolation Secure Defaults At the Code Level Deployment – Default IIS box is only a static web server – Admin must turn on what is needed IIS/ASP. NET focus on App-layer security Web Service Extensions URLScan ASP. Net. config files Server-side Controls > 10, 000 sites already live on IIS 6. 0 microsoft. com running production since RC 1
 Questions ? ? ?
Questions ? ? ?


