1a34f121379adb0c7954fe9be573e21a.ppt
- Количество слайдов: 18
![IETF NEA WG (NEA = Network Endpoint Assessment) nea[-request]@ietf. org Chairs: Steve Hanna, Juniper IETF NEA WG (NEA = Network Endpoint Assessment) nea[-request]@ietf. org Chairs: Steve Hanna, Juniper](https://present5.com/presentation/1a34f121379adb0c7954fe9be573e21a/image-1.jpg) IETF NEA WG (NEA = Network Endpoint Assessment) nea[-request]@ietf. org Chairs: Steve Hanna, Juniper shanna@juniper. net Susan Thomson, Cisco sethomso@cisco. com IETF 67, Tuesday, November 7, 2006, 3: 20 PM – 5: 20 PM November 7, 2006 IETF NEA WG
IETF NEA WG (NEA = Network Endpoint Assessment) nea[-request]@ietf. org Chairs: Steve Hanna, Juniper shanna@juniper. net Susan Thomson, Cisco sethomso@cisco. com IETF 67, Tuesday, November 7, 2006, 3: 20 PM – 5: 20 PM November 7, 2006 IETF NEA WG
 Agenda Review 3: 20 3: 25 3: 30 3: 40 5: 10 5: 20 Blue Sheets, Jabber & Minutes Scribes Agenda Bashing NEA Milestones Discussion of Requirements I-D Next Steps Adjourn November 7, 2006 IETF NEA WG 2
Agenda Review 3: 20 3: 25 3: 30 3: 40 5: 10 5: 20 Blue Sheets, Jabber & Minutes Scribes Agenda Bashing NEA Milestones Discussion of Requirements I-D Next Steps Adjourn November 7, 2006 IETF NEA WG 2
 NEA Milestones • First Milestones – Prepare NEA Requirements I-D (Nov-Jan) – WGLC on NEA Requirements I-D (Feb ‘ 07) – IETF LC on NEA Requirements I-D (Apr ‘ 07) • Then we’ll add milestones for PA, PB, etc. – Subject to AD approval November 7, 2006 IETF NEA WG 3
NEA Milestones • First Milestones – Prepare NEA Requirements I-D (Nov-Jan) – WGLC on NEA Requirements I-D (Feb ‘ 07) – IETF LC on NEA Requirements I-D (Apr ‘ 07) • Then we’ll add milestones for PA, PB, etc. – Subject to AD approval November 7, 2006 IETF NEA WG 3
 NEA Roles and Responsibilities • NEA Requirements Design Team and Editors – Volunteers solicited on list and at IETF 67 – Selected by NEA WG chairs – Develop initial Requirements I-D – Revise I-D in response to WG rough consensus • NEA WG Participants – Review draft documents – Discuss on email list and at IETF meetings – Reach rough consensus on email list • NEA WG Chairs – – Select Design Teams and Editors Moderate WG discussions Judge rough consensus Manage WG process November 7, 2006 IETF NEA WG 4
NEA Roles and Responsibilities • NEA Requirements Design Team and Editors – Volunteers solicited on list and at IETF 67 – Selected by NEA WG chairs – Develop initial Requirements I-D – Revise I-D in response to WG rough consensus • NEA WG Participants – Review draft documents – Discuss on email list and at IETF meetings – Reach rough consensus on email list • NEA WG Chairs – – Select Design Teams and Editors Moderate WG discussions Judge rough consensus Manage WG process November 7, 2006 IETF NEA WG 4
 Goals for Today • Discuss Requirements I-D – Get feedback on current ideas • Recruit volunteers for NEA Requirements Design Team November 7, 2006 IETF NEA WG 5
Goals for Today • Discuss Requirements I-D – Get feedback on current ideas • Recruit volunteers for NEA Requirements Design Team November 7, 2006 IETF NEA WG 5
 Requirements I-D Outline • • Abstract, Boilerplate Introduction Terminology Applicability Problem Statement Reference Model Use Cases Requirements – Common – Protocol-specific (PA, PB, PT) • Security Analysis/Considerations • References, Editors’ Addresses, Acknowledgements November 7, 2006 IETF NEA WG 6
Requirements I-D Outline • • Abstract, Boilerplate Introduction Terminology Applicability Problem Statement Reference Model Use Cases Requirements – Common – Protocol-specific (PA, PB, PT) • Security Analysis/Considerations • References, Editors’ Addresses, Acknowledgements November 7, 2006 IETF NEA WG 6
 Terminology • Endpoint – A host that can be connected to a network • Laptop, desktop, server, printer, cell phone, any device with an IP address • Posture – Endpoint security-relevant configuration • OS and application version and patch level, security software configuration and status, etc. November 7, 2006 IETF NEA WG 7
Terminology • Endpoint – A host that can be connected to a network • Laptop, desktop, server, printer, cell phone, any device with an IP address • Posture – Endpoint security-relevant configuration • OS and application version and patch level, security software configuration and status, etc. November 7, 2006 IETF NEA WG 7
 Problem Statement • Assess endpoint posture • Various actions may follow – In-scope • Deliver assessment result to endpoint • Deliver remediation instructions to endpoint – Out-of-scope but must be accommodated • • • Evaluate posture policy compliance Monitor compliance Binding to network access control protocols Remediate Identify lying endpoints November 7, 2006 IETF NEA WG 8
Problem Statement • Assess endpoint posture • Various actions may follow – In-scope • Deliver assessment result to endpoint • Deliver remediation instructions to endpoint – Out-of-scope but must be accommodated • • • Evaluate posture policy compliance Monitor compliance Binding to network access control protocols Remediate Identify lying endpoints November 7, 2006 IETF NEA WG 8
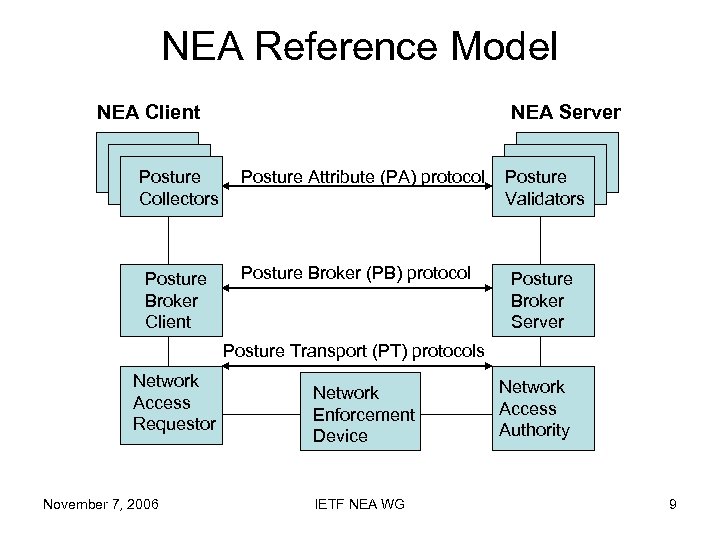 NEA Reference Model NEA Client Posture Collectors Posture Broker Client NEA Server Posture Attribute (PA) protocol Posture Broker (PB) protocol Posture Validators Posture Broker Server Posture Transport (PT) protocols Network Access Requestor November 7, 2006 Network Enforcement Device IETF NEA WG Network Access Authority 9
NEA Reference Model NEA Client Posture Collectors Posture Broker Client NEA Server Posture Attribute (PA) protocol Posture Broker (PB) protocol Posture Validators Posture Broker Server Posture Transport (PT) protocols Network Access Requestor November 7, 2006 Network Enforcement Device IETF NEA WG Network Access Authority 9
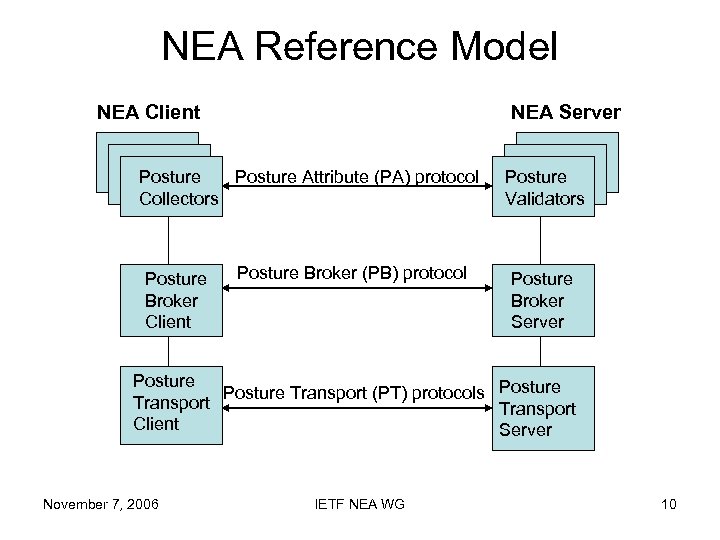 NEA Reference Model NEA Client NEA Server Posture Attribute (PA) protocol Collectors Posture Broker Client Posture Broker (PB) protocol Posture Validators Posture Broker Server Posture Transport (PT) protocols Posture Transport Client Server November 7, 2006 IETF NEA WG 10
NEA Reference Model NEA Client NEA Server Posture Attribute (PA) protocol Collectors Posture Broker Client Posture Broker (PB) protocol Posture Validators Posture Broker Server Posture Transport (PT) protocols Posture Transport Client Server November 7, 2006 IETF NEA WG 10
 Use Cases • Goals – Span the problem space – Drive requirements • Non-Goals – List all use cases – Describe details of PT protocols November 7, 2006 IETF NEA WG 11
Use Cases • Goals – Span the problem space – Drive requirements • Non-Goals – List all use cases – Describe details of PT protocols November 7, 2006 IETF NEA WG 11
 Types of Flows • Initial assessment of endpoint – Triggered by Network Connection – Triggered by Service Request • Re-assessment of endpoint – Triggered by NEA Server (timer, event, etc. ) – Triggered by NEA Client (timer, event, etc. ) November 7, 2006 IETF NEA WG 12
Types of Flows • Initial assessment of endpoint – Triggered by Network Connection – Triggered by Service Request • Re-assessment of endpoint – Triggered by NEA Server (timer, event, etc. ) – Triggered by NEA Client (timer, event, etc. ) November 7, 2006 IETF NEA WG 12
 Types of Attributes • Endpoint Data (client to server) – By value – By reference • Compliance Policy (server to client) • Compliance Policy Evaluation Results (client to server) • Cryptographic Protocols (multiple round trips) – Proof of possession – Replay protection mechanisms • Compliance Result (server to client) • Remediation Instructions (server to client) November 7, 2006 IETF NEA WG 13
Types of Attributes • Endpoint Data (client to server) – By value – By reference • Compliance Policy (server to client) • Compliance Policy Evaluation Results (client to server) • Cryptographic Protocols (multiple round trips) – Proof of possession – Replay protection mechanisms • Compliance Result (server to client) • Remediation Instructions (server to client) November 7, 2006 IETF NEA WG 13
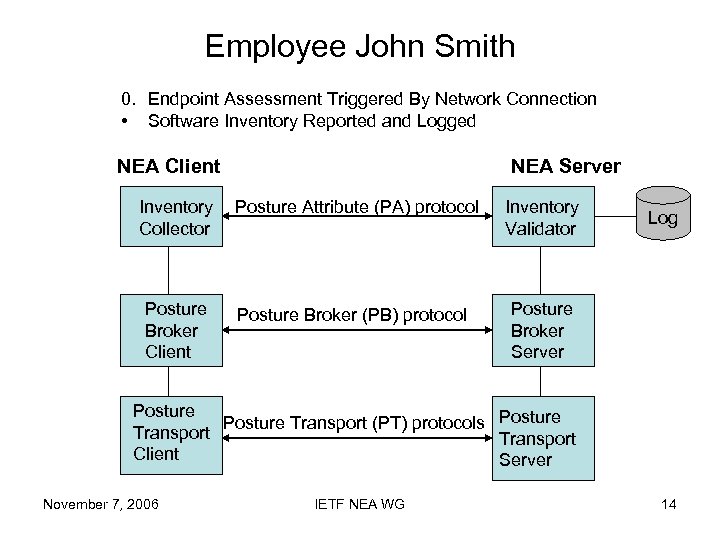 Employee John Smith 0. Endpoint Assessment Triggered By Network Connection • Software Inventory Reported and Logged NEA Client Inventory Collector Posture Broker Client NEA Server Posture Attribute (PA) protocol Posture Broker (PB) protocol Inventory Validator Log Posture Broker Server Posture Transport (PT) protocols Posture Transport Client Server November 7, 2006 IETF NEA WG 14
Employee John Smith 0. Endpoint Assessment Triggered By Network Connection • Software Inventory Reported and Logged NEA Client Inventory Collector Posture Broker Client NEA Server Posture Attribute (PA) protocol Posture Broker (PB) protocol Inventory Validator Log Posture Broker Server Posture Transport (PT) protocols Posture Transport Client Server November 7, 2006 IETF NEA WG 14
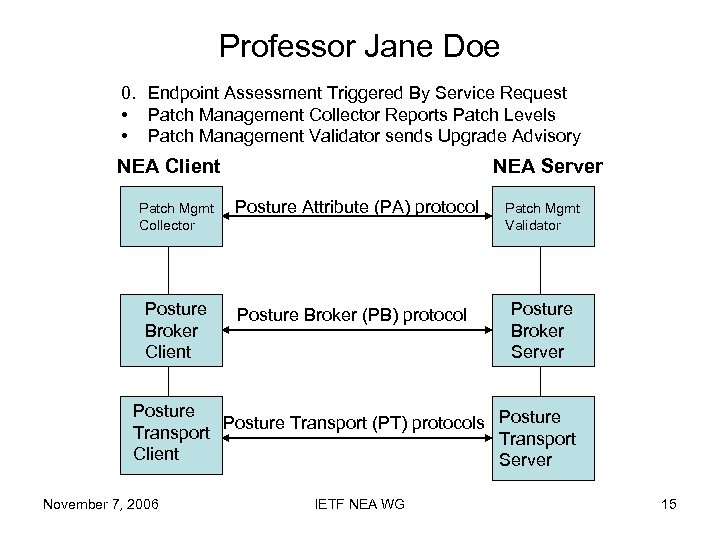 Professor Jane Doe 0. Endpoint Assessment Triggered By Service Request • Patch Management Collector Reports Patch Levels • Patch Management Validator sends Upgrade Advisory NEA Client Patch Mgmt Collector Posture Broker Client NEA Server Posture Attribute (PA) protocol Posture Broker (PB) protocol Patch Mgmt Validator Posture Broker Server Posture Transport (PT) protocols Posture Transport Client Server November 7, 2006 IETF NEA WG 15
Professor Jane Doe 0. Endpoint Assessment Triggered By Service Request • Patch Management Collector Reports Patch Levels • Patch Management Validator sends Upgrade Advisory NEA Client Patch Mgmt Collector Posture Broker Client NEA Server Posture Attribute (PA) protocol Posture Broker (PB) protocol Patch Mgmt Validator Posture Broker Server Posture Transport (PT) protocols Posture Transport Client Server November 7, 2006 IETF NEA WG 15
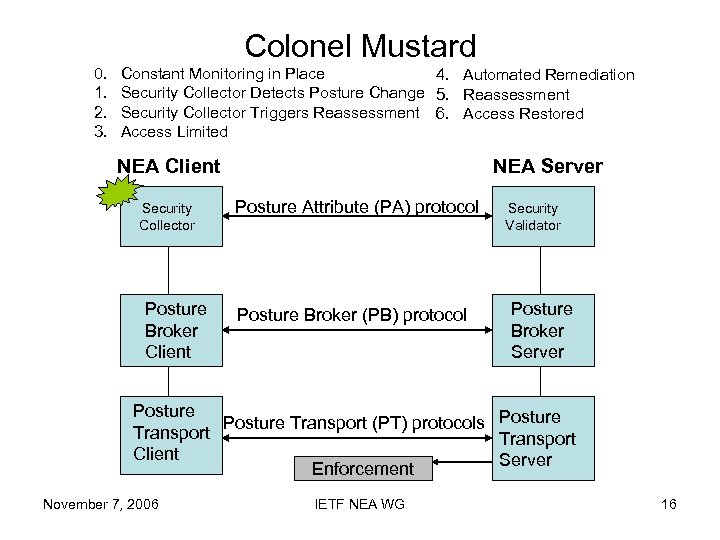 Colonel Mustard 0. 1. 2. 3. Constant Monitoring in Place 4. Automated Remediation Security Collector Detects Posture Change 5. Reassessment Security Collector Triggers Reassessment 6. Access Restored Access Limited NEA Client Security Collector Posture Broker Client NEA Server Posture Attribute (PA) protocol Posture Broker (PB) protocol Security Validator Posture Broker Server Posture Transport (PT) protocols Posture Transport Client Server Enforcement November 7, 2006 IETF NEA WG 16
Colonel Mustard 0. 1. 2. 3. Constant Monitoring in Place 4. Automated Remediation Security Collector Detects Posture Change 5. Reassessment Security Collector Triggers Reassessment 6. Access Restored Access Limited NEA Client Security Collector Posture Broker Client NEA Server Posture Attribute (PA) protocol Posture Broker (PB) protocol Security Validator Posture Broker Server Posture Transport (PT) protocols Posture Transport Client Server Enforcement November 7, 2006 IETF NEA WG 16
 Other Use Cases? • Other use cases that: – Must be addressed by NEA – Drive new PA, PB, or PT requirements November 7, 2006 IETF NEA WG 17
Other Use Cases? • Other use cases that: – Must be addressed by NEA – Drive new PA, PB, or PT requirements November 7, 2006 IETF NEA WG 17
 Next Steps • Solicit Design Team Contributors – Through November 16 • Start Design Team Weekly Concalls – Week of November 27 • First Requirements I-D Posted November 7, 2006 IETF NEA WG 18
Next Steps • Solicit Design Team Contributors – Through November 16 • Start Design Team Weekly Concalls – Week of November 27 • First Requirements I-D Posted November 7, 2006 IETF NEA WG 18


