749b7975791af657f9c72530a84fca69.ppt
- Количество слайдов: 22
 IELM 511: Information System design Introduction Part 1. ISD for well structured data – relational and other DBMS Info storage (modeling, normalization) Info retrieval (Relational algebra, Calculus, SQL) DB integrated API’s Part 2. ISD for systems with non-uniformly structured data Basics of web-based IS (www, web 2. 0, …) Markup’s, HTML, XML Design tools for Info Sys: UML Part III: (subset of) API’s for mobile apps Security, Cryptography IS product lifecycles Algorithm analysis, P, NPC
IELM 511: Information System design Introduction Part 1. ISD for well structured data – relational and other DBMS Info storage (modeling, normalization) Info retrieval (Relational algebra, Calculus, SQL) DB integrated API’s Part 2. ISD for systems with non-uniformly structured data Basics of web-based IS (www, web 2. 0, …) Markup’s, HTML, XML Design tools for Info Sys: UML Part III: (subset of) API’s for mobile apps Security, Cryptography IS product lifecycles Algorithm analysis, P, NPC
 Agenda Basics of secure communications in Information Systems Private key (symmetric key) IS Asymmetric keys and their uses in IS Encryption algorithms and how they work (basics) The mathematical basis for encryption Concluding remarks
Agenda Basics of secure communications in Information Systems Private key (symmetric key) IS Asymmetric keys and their uses in IS Encryption algorithms and how they work (basics) The mathematical basis for encryption Concluding remarks
 Communications basics In many applications, we use a secret ‘password’ to ‘log in’ and communicate securely How does the IS exchange data securely between the client and server? Data encryption transmit encrypted data decrypt data on server How to encrypt/decrypt ? Shared secret password: Symmetric keys Asymmetric keys (uses Secure Sockets Layer protocol), or SSL
Communications basics In many applications, we use a secret ‘password’ to ‘log in’ and communicate securely How does the IS exchange data securely between the client and server? Data encryption transmit encrypted data decrypt data on server How to encrypt/decrypt ? Shared secret password: Symmetric keys Asymmetric keys (uses Secure Sockets Layer protocol), or SSL
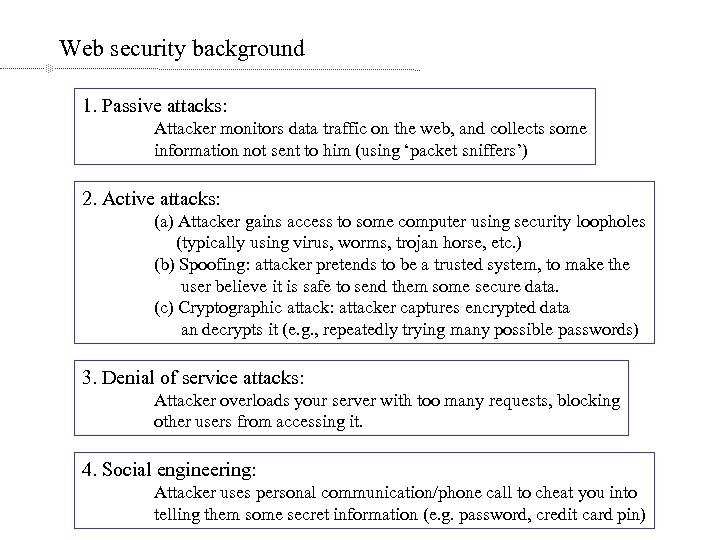 Web security background 1. Passive attacks: Attacker monitors data traffic on the web, and collects some information not sent to him (using ‘packet sniffers’) 2. Active attacks: (a) Attacker gains access to some computer using security loopholes (typically using virus, worms, trojan horse, etc. ) (b) Spoofing: attacker pretends to be a trusted system, to make the user believe it is safe to send them some secure data. (c) Cryptographic attack: attacker captures encrypted data an decrypts it (e. g. , repeatedly trying many possible passwords) 3. Denial of service attacks: Attacker overloads your server with too many requests, blocking other users from accessing it. 4. Social engineering: Attacker uses personal communication/phone call to cheat you into telling them some secret information (e. g. password, credit card pin)
Web security background 1. Passive attacks: Attacker monitors data traffic on the web, and collects some information not sent to him (using ‘packet sniffers’) 2. Active attacks: (a) Attacker gains access to some computer using security loopholes (typically using virus, worms, trojan horse, etc. ) (b) Spoofing: attacker pretends to be a trusted system, to make the user believe it is safe to send them some secure data. (c) Cryptographic attack: attacker captures encrypted data an decrypts it (e. g. , repeatedly trying many possible passwords) 3. Denial of service attacks: Attacker overloads your server with too many requests, blocking other users from accessing it. 4. Social engineering: Attacker uses personal communication/phone call to cheat you into telling them some secret information (e. g. password, credit card pin)
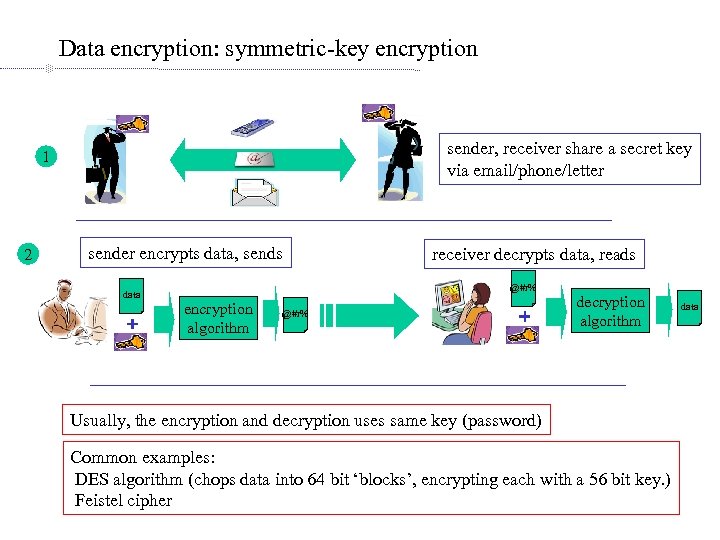 Data encryption: symmetric-key encryption sender, receiver share a secret key via email/phone/letter 1 2 sender encrypts data, sends data receiver decrypts data, reads @#r% encryption algorithm @#r% decryption algorithm Usually, the encryption and decryption uses same key (password) Common examples: DES algorithm (chops data into 64 bit ‘blocks’, encrypting each with a 56 bit key. ) Feistel cipher data
Data encryption: symmetric-key encryption sender, receiver share a secret key via email/phone/letter 1 2 sender encrypts data, sends data receiver decrypts data, reads @#r% encryption algorithm @#r% decryption algorithm Usually, the encryption and decryption uses same key (password) Common examples: DES algorithm (chops data into 64 bit ‘blocks’, encrypting each with a 56 bit key. ) Feistel cipher data
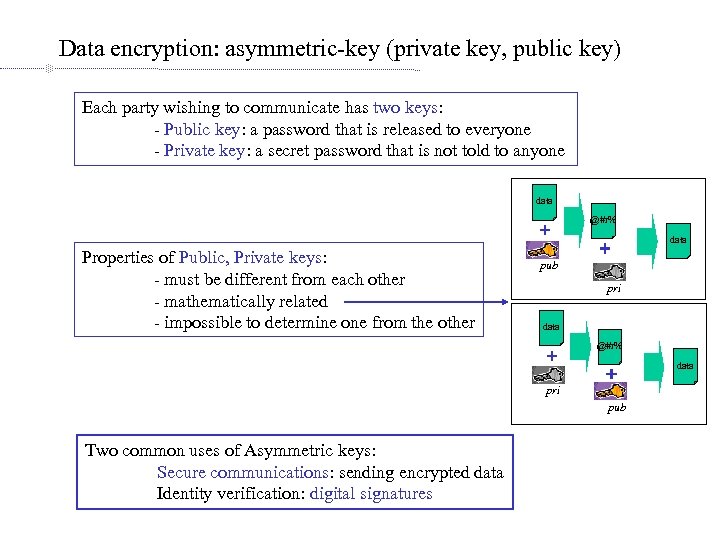 Data encryption: asymmetric-key (private key, public key) Each party wishing to communicate has two keys: - Public key: a password that is released to everyone - Private key: a secret password that is not told to anyone data @#r% data Properties of Public, Private keys: - must be different from each other - mathematically related - impossible to determine one from the other pub pri data @#r% data pri pub Two common uses of Asymmetric keys: Secure communications: sending encrypted data Identity verification: digital signatures
Data encryption: asymmetric-key (private key, public key) Each party wishing to communicate has two keys: - Public key: a password that is released to everyone - Private key: a secret password that is not told to anyone data @#r% data Properties of Public, Private keys: - must be different from each other - mathematically related - impossible to determine one from the other pub pri data @#r% data pri pub Two common uses of Asymmetric keys: Secure communications: sending encrypted data Identity verification: digital signatures
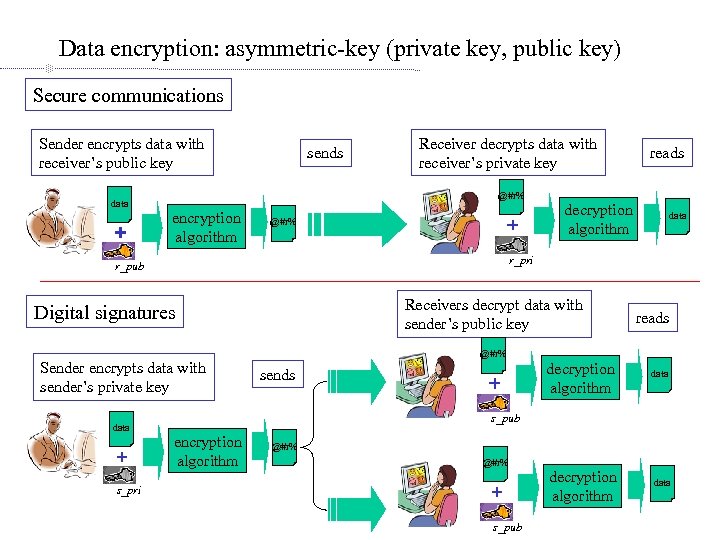 Data encryption: asymmetric-key (private key, public key) Secure communications Sender encrypts data with receiver’s public key data sends Receiver decrypts data with receiver’s private key @#r% encryption algorithm @#r% decryption algorithm data r_pri r_pub Receivers decrypt data with sender’s public key Digital signatures Sender encrypts data with sender’s private key data reads @#r% sends reads decryption algorithm data s_pub encryption algorithm @#r% s_pri s_pub
Data encryption: asymmetric-key (private key, public key) Secure communications Sender encrypts data with receiver’s public key data sends Receiver decrypts data with receiver’s private key @#r% encryption algorithm @#r% decryption algorithm data r_pri r_pub Receivers decrypt data with sender’s public key Digital signatures Sender encrypts data with sender’s private key data reads @#r% sends reads decryption algorithm data s_pub encryption algorithm @#r% s_pri s_pub
 Asymmetric keys: user verification Problem: how will the a user know whether the public key they ‘fetch’ over the internet is really from the party they are communicating, or it’s been altered by some malicious party? Solution: use of a “trusted” intermediary (third party), who is in charge of (a) providing keys to all interacting parties (b) physically checking that the each party is who they claim to be Implementation - Use of a Public Key Infrastructure (PKI), which usually involves a - 3 rd party Certificate Authority (CA) who issues and manages key’s to the applications that are communicating. Some common CA’s - Veri. Sign, Co. Modo, Go. Daddy, Digi. Cert, …
Asymmetric keys: user verification Problem: how will the a user know whether the public key they ‘fetch’ over the internet is really from the party they are communicating, or it’s been altered by some malicious party? Solution: use of a “trusted” intermediary (third party), who is in charge of (a) providing keys to all interacting parties (b) physically checking that the each party is who they claim to be Implementation - Use of a Public Key Infrastructure (PKI), which usually involves a - 3 rd party Certificate Authority (CA) who issues and manages key’s to the applications that are communicating. Some common CA’s - Veri. Sign, Co. Modo, Go. Daddy, Digi. Cert, …
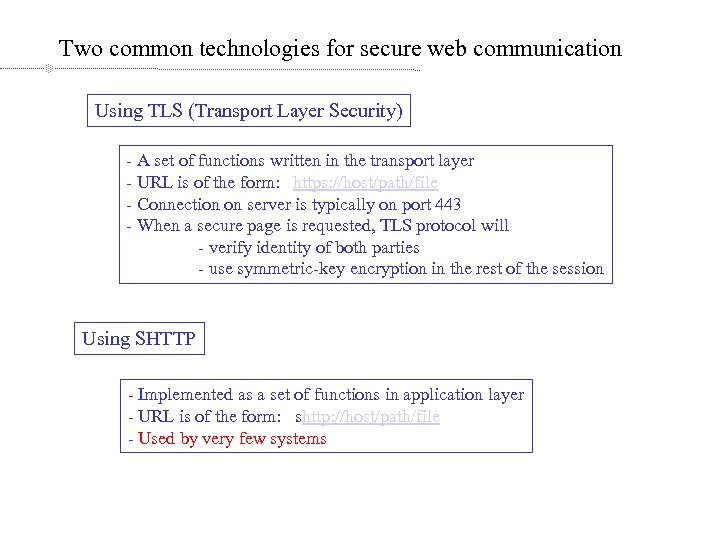 Two common technologies for secure web communication Using TLS (Transport Layer Security) - A set of functions written in the transport layer - URL is of the form: https: //host/path/file - Connection on server is typically on port 443 - When a secure page is requested, TLS protocol will - verify identity of both parties - use symmetric-key encryption in the rest of the session Using SHTTP - Implemented as a set of functions in application layer - URL is of the form: shttp: //host/path/file - Used by very few systems
Two common technologies for secure web communication Using TLS (Transport Layer Security) - A set of functions written in the transport layer - URL is of the form: https: //host/path/file - Connection on server is typically on port 443 - When a secure page is requested, TLS protocol will - verify identity of both parties - use symmetric-key encryption in the rest of the session Using SHTTP - Implemented as a set of functions in application layer - URL is of the form: shttp: //host/path/file - Used by very few systems
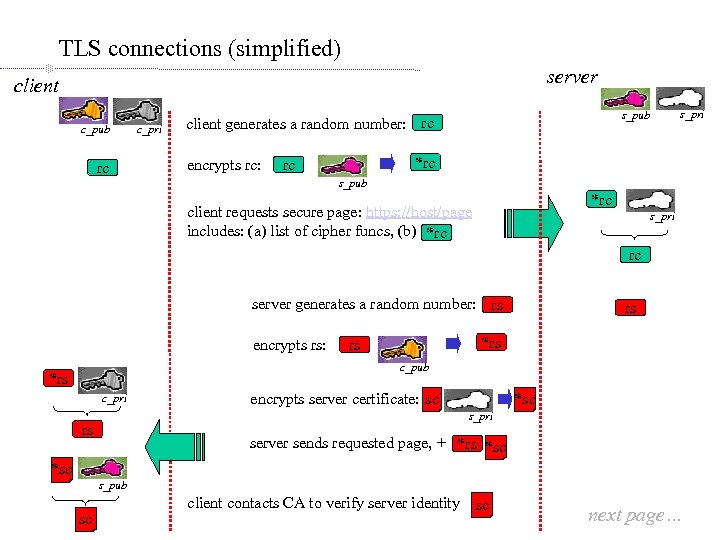 TLS connections (simplified) server client c_pub rc c_pri s_pub client generates a random number: rc encrypts rc: s_pri *rc rc s_pub *rc client requests secure page: https: //host/page includes: (a) list of cipher funcs, (b) *rc s_pri rc server generates a random number: rs encrypts rs: rs *rs rs c_pub *rs c_pri *sc encrypts server certificate: sc s_pri rs server sends requested page, + *rs *sc s_pub sc client contacts CA to verify server identity sc next page…
TLS connections (simplified) server client c_pub rc c_pri s_pub client generates a random number: rc encrypts rc: s_pri *rc rc s_pub *rc client requests secure page: https: //host/page includes: (a) list of cipher funcs, (b) *rc s_pri rc server generates a random number: rs encrypts rs: rs *rs rs c_pub *rs c_pri *sc encrypts server certificate: sc s_pri rs server sends requested page, + *rs *sc s_pub sc client contacts CA to verify server identity sc next page…
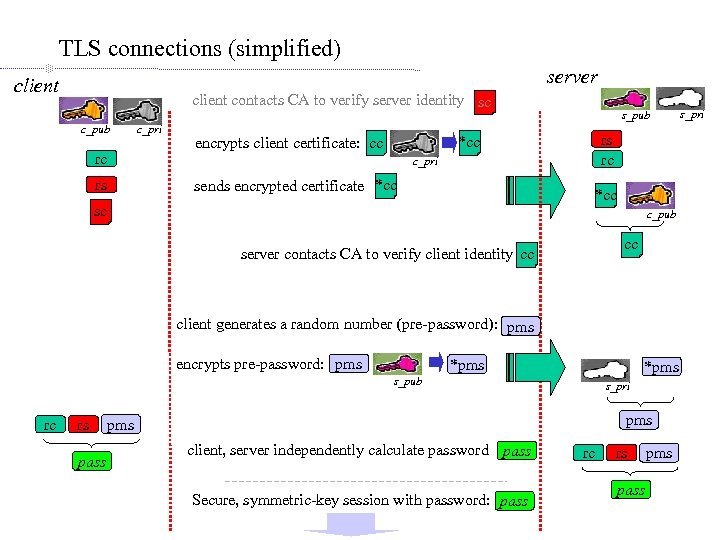 TLS connections (simplified) server client contacts CA to verify server identity sc c_pub rc c_pri rs rc *cc encrypts client certificate: cc c_pri sends encrypted certificate *cc rs s_pub *cc sc c_pub cc server contacts CA to verify client identity cc client generates a random number (pre-password): pms encrypts pre-password: pms *pms s_pub rc rs pass s_pri pms client, server independently calculate password pass Secure, symmetric-key session with password: pass rc rs pass pms s_pri
TLS connections (simplified) server client contacts CA to verify server identity sc c_pub rc c_pri rs rc *cc encrypts client certificate: cc c_pri sends encrypted certificate *cc rs s_pub *cc sc c_pub cc server contacts CA to verify client identity cc client generates a random number (pre-password): pms encrypts pre-password: pms *pms s_pub rc rs pass s_pri pms client, server independently calculate password pass Secure, symmetric-key session with password: pass rc rs pass pms s_pri
 Basics of encryption Encryption is essential for many IS applications. How do encryption algorithms work ?
Basics of encryption Encryption is essential for many IS applications. How do encryption algorithms work ?
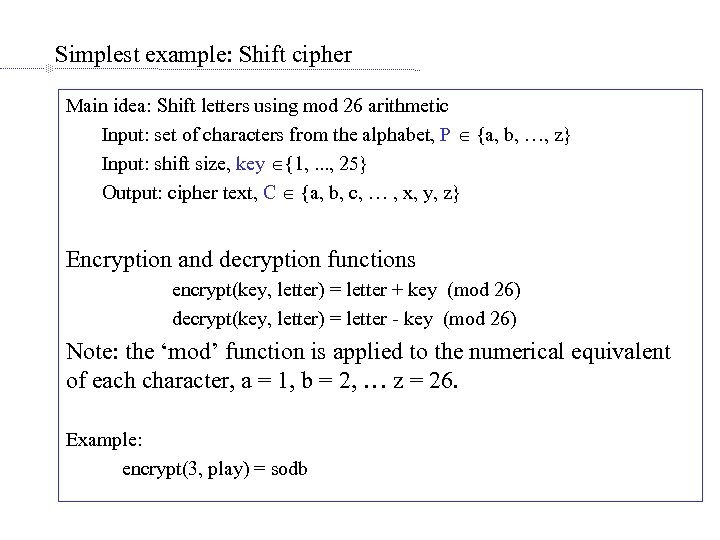 Simplest example: Shift cipher Main idea: Shift letters using mod 26 arithmetic Input: set of characters from the alphabet, P {a, b, …, z} Input: shift size, key {1, . . . , 25} Output: cipher text, C {a, b, c, … , x, y, z} Encryption and decryption functions encrypt(key, letter) = letter + key (mod 26) decrypt(key, letter) = letter - key (mod 26) Note: the ‘mod’ function is applied to the numerical equivalent of each character, a = 1, b = 2, … z = 26. Example: encrypt(3, play) = sodb
Simplest example: Shift cipher Main idea: Shift letters using mod 26 arithmetic Input: set of characters from the alphabet, P {a, b, …, z} Input: shift size, key {1, . . . , 25} Output: cipher text, C {a, b, c, … , x, y, z} Encryption and decryption functions encrypt(key, letter) = letter + key (mod 26) decrypt(key, letter) = letter - key (mod 26) Note: the ‘mod’ function is applied to the numerical equivalent of each character, a = 1, b = 2, … z = 26. Example: encrypt(3, play) = sodb
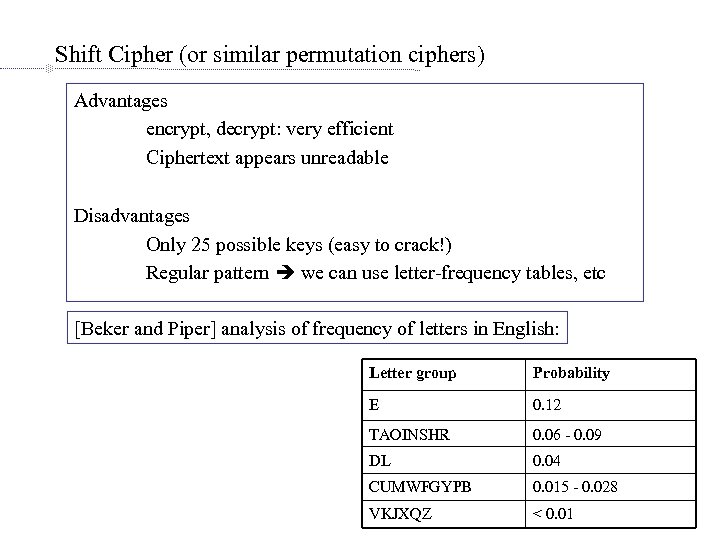 Shift Cipher (or similar permutation ciphers) Advantages encrypt, decrypt: very efficient Ciphertext appears unreadable Disadvantages Only 25 possible keys (easy to crack!) Regular pattern we can use letter-frequency tables, etc [Beker and Piper] analysis of frequency of letters in English: Letter group Probability E 0. 12 TAOINSHR 0. 06 - 0. 09 DL 0. 04 CUMWFGYPB 0. 015 - 0. 028 VKJXQZ < 0. 01
Shift Cipher (or similar permutation ciphers) Advantages encrypt, decrypt: very efficient Ciphertext appears unreadable Disadvantages Only 25 possible keys (easy to crack!) Regular pattern we can use letter-frequency tables, etc [Beker and Piper] analysis of frequency of letters in English: Letter group Probability E 0. 12 TAOINSHR 0. 06 - 0. 09 DL 0. 04 CUMWFGYPB 0. 015 - 0. 028 VKJXQZ < 0. 01
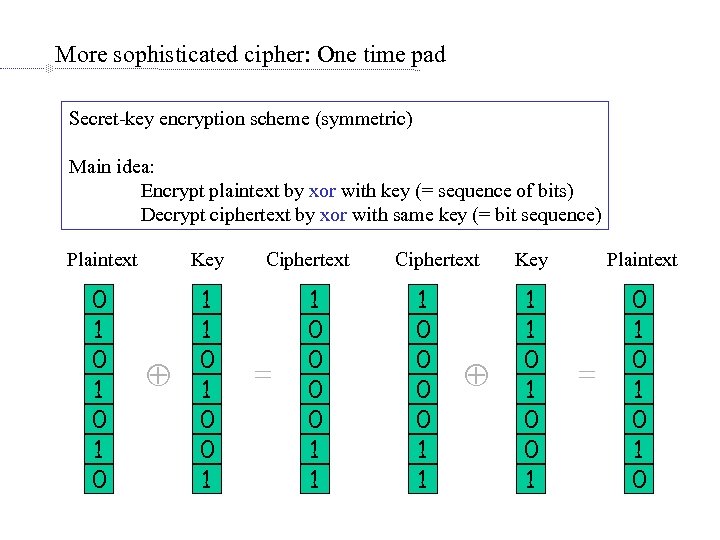 More sophisticated cipher: One time pad Secret-key encryption scheme (symmetric) Main idea: Encrypt plaintext by xor with key (= sequence of bits) Decrypt ciphertext by xor with same key (= bit sequence) Plaintext Key 0 1 0 1 1 0 0 1 Ciphertext = 1 0 0 1 1 Ciphertext 1 0 0 1 1 Key Plaintext 1 1 0 0 1 0 1 0 =
More sophisticated cipher: One time pad Secret-key encryption scheme (symmetric) Main idea: Encrypt plaintext by xor with key (= sequence of bits) Decrypt ciphertext by xor with same key (= bit sequence) Plaintext Key 0 1 0 1 1 0 0 1 Ciphertext = 1 0 0 1 1 Ciphertext 1 0 0 1 1 Key Plaintext 1 1 0 0 1 0 1 0 =
 One time pad Advantages Easy to compute encrypt, decrypt from key, text Secure: Given a plaintext and random key, all possible ciphertexts are equally likely. Disadvantages Key is as long as the plaintext
One time pad Advantages Easy to compute encrypt, decrypt from key, text Secure: Given a plaintext and random key, all possible ciphertexts are equally likely. Disadvantages Key is as long as the plaintext
 Even more sophisticated ciphers: Block ciphers Basic algorithms for Block ciphers were developed at IBM Examples: Feistel: source code is available for many languages; DES (Data Encryption Standard): commonly used. Main idea: 1. Permute input bits 2. Repeat application of a Feistel-style function 3. Apply inverse permutation to produce output Simple, computationally efficient, secure (at least to date!)
Even more sophisticated ciphers: Block ciphers Basic algorithms for Block ciphers were developed at IBM Examples: Feistel: source code is available for many languages; DES (Data Encryption Standard): commonly used. Main idea: 1. Permute input bits 2. Repeat application of a Feistel-style function 3. Apply inverse permutation to produce output Simple, computationally efficient, secure (at least to date!)
![DES basics Plain text (64 bits) Initial permutation IP [0. . 63] Two halves DES basics Plain text (64 bits) Initial permutation IP [0. . 63] Two halves](https://present5.com/presentation/749b7975791af657f9c72530a84fca69/image-18.jpg) DES basics Plain text (64 bits) Initial permutation IP [0. . 63] Two halves L 0 [0. . 31] R 0 [0. . 31] L i-1 R i-1 F F( key, input) x 16 times XOR L 16 [0. . 31] R 16 [0. . 31] Inverse Initial permutation Cipher text (64 bits) L i = Ri-1 Ri Ki Ki = permutation of key K
DES basics Plain text (64 bits) Initial permutation IP [0. . 63] Two halves L 0 [0. . 31] R 0 [0. . 31] L i-1 R i-1 F F( key, input) x 16 times XOR L 16 [0. . 31] R 16 [0. . 31] Inverse Initial permutation Cipher text (64 bits) L i = Ri-1 Ri Ki Ki = permutation of key K
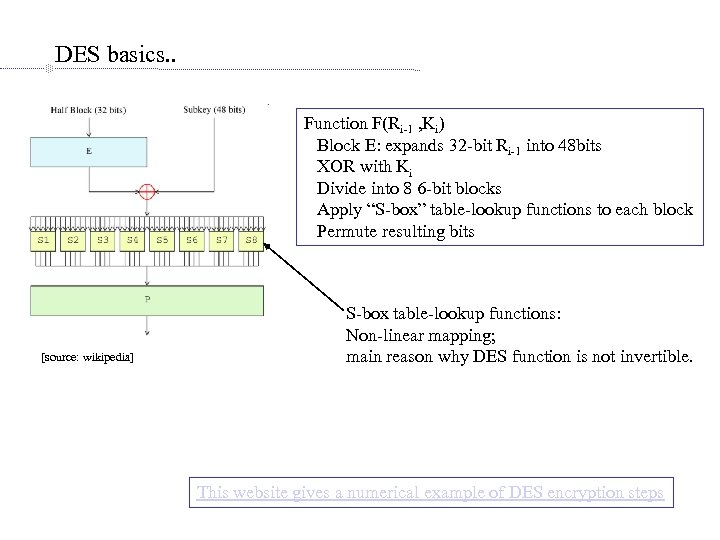 DES basics. . Function F(Ri-1 , Ki) Block E: expands 32 -bit Ri-1 into 48 bits XOR with Ki Divide into 8 6 -bit blocks Apply “S-box” table-lookup functions to each block Permute resulting bits [source: wikipedia] S-box table-lookup functions: Non-linear mapping; main reason why DES function is not invertible. This website gives a numerical example of DES encryption steps
DES basics. . Function F(Ri-1 , Ki) Block E: expands 32 -bit Ri-1 into 48 bits XOR with Ki Divide into 8 6 -bit blocks Apply “S-box” table-lookup functions to each block Permute resulting bits [source: wikipedia] S-box table-lookup functions: Non-linear mapping; main reason why DES function is not invertible. This website gives a numerical example of DES encryption steps
 RSA algorithm DES uses same key for encryption and decryption. The theoretical basis for Public key encryption systems are developed from the RSA algorithm: based on number theory (prime numbers). [an excellent introduction is Prof Deng Xiaotie’s lectures, City U. ]
RSA algorithm DES uses same key for encryption and decryption. The theoretical basis for Public key encryption systems are developed from the RSA algorithm: based on number theory (prime numbers). [an excellent introduction is Prof Deng Xiaotie’s lectures, City U. ]
 Practical matters Private key algorithms: Easy to implement in your own IS Open source code available for many ciphers (Feistel, TEA) Public key algorithms: Requires purchase of service from PKI vendor (e. g. Verisign, …) Expensive to implement, manage, but standard for most businesses
Practical matters Private key algorithms: Easy to implement in your own IS Open source code available for many ciphers (Feistel, TEA) Public key algorithms: Requires purchase of service from PKI vendor (e. g. Verisign, …) Expensive to implement, manage, but standard for most businesses
 References and Further Reading Simon Singh, The Code Book, pub. Anchor press, 2000 PDF article giving brief introduction to RSA maths (Utah State, Prof Moon) Wikipedia cryptography portal Prof Deng Xiaotie/Prof Frances Yao’s lecture notes (City Univ, HK) Next: Mobile Applications Design
References and Further Reading Simon Singh, The Code Book, pub. Anchor press, 2000 PDF article giving brief introduction to RSA maths (Utah State, Prof Moon) Wikipedia cryptography portal Prof Deng Xiaotie/Prof Frances Yao’s lecture notes (City Univ, HK) Next: Mobile Applications Design


