51241c30bb618ae6cf487a23d6753dd0.ppt
- Количество слайдов: 24

“Identity Management in the Financial and Banking Sector” IAM – From vision to reality A chain is only as strong as its weakest link Konstantin Zografov, AFCEA International Regional Vice President for the Mediterranean and Black Sea Region 3/17/2018 Dr. Mircho Marchev, Ph. D. , Director of the Information Technology Directorate of the Bulgarian National Bank, Member of ECB ITC 1

Agenda • • 27. 10. 2009 Introduction Context Federated Identity Needs Standards Approach Roadmap Examples Identity Management in Federated Environment, Brussels 2

Introduction • IAM (Identity and Access Management) • A broad and complex administrative approach in mitigating the risks of fraud, errors and disclosure of confidential information. • A threefold concept of managing digital identities and access to corporate systems and assets by combining: - Business processes, - Policies and - Technologies • Centralized identity management solutions: the users and the systems they accessed were: - within the same network or - within the same “domain of control”. 27. 10. 2009 Identity Management in Federated Environment, Brussels 3

Introduction • IAM – a growing business necessity reflecting the global economic and society developments. • IAM – constantly evolving over time due to to the continually changing computing environment in which organisations operate. • IAM – Banks are the leaders in the civil sectors in working on and launching information security systems to handle digital identities and access due to the greatest possible impacts of identity breach to the financial community – both clients and corporations. • IAM – grows out of already existing corporate security systems, enterprise administration, single sign-on etc. 27. 10. 2009 Identity Management in Federated Environment, Brussels 4

Context • International – Globalization, Internet access, NATO Alliance • Corporate – Multiple applications, some of those obsolete, increased risk exposure • Financial – ESCB definition: Identity and access management (IAM) enables organisations to handle digital identities, to set and control access to their systems, and to ensure that only authorised users and resources (service accounts and devices) gain the appropriate access to those systems, in accordance with business requirements. 27. 10. 2009 Identity Management in Federated Environment, Brussels 5

Context • Decentralization: – intégration of the Internet into every aspect of personal and business life. • The inevitable separation of users, requiring access to systems and Information Assets • Evolving identity management challenges – cross-company and cross-domain access • A new approach of identity management, known now as “FEDERATED IDENTITY MANAGEMENT”. 27. 10. 2009 Identity Management in Federated Environment, Brussels 6

FEDERATED IDENTITY MANAGEMENT • The Federated Identity (or Identity federation): to enable the portability of identity information across independent security domains. • The concept of Federated identity describes: – The policies, the technologies, the standards and the usecases of the respected industry. • Federation of identities could only be realised by the usage of: – open industry standards, – Agreed specifications, made available to the parties, – Thus achieving interoperability for the common use cases. 27. 10. 2009 Identity Management in Federated Environment, Brussels 7

General Definition • Federated identity: – – • The virtual reunion, or assembled identity, of a person's user information (or principal), stored across multiple distinct identity management systems. Data are joined together by use of the common token, usually the user name. A user's authentication process across multiple IT systems or organizations. The concept: – – the capacity of being able to extend, under a pre-defined circle of trust, the account profile and access management system to a third party who needs to access a specific target resources and applications. The architecture will be based on a federated identity model where authentication could be fully delegated towards trusted members. 27. 10. 2009 Identity Management in Federated Environment, Brussels 8

Principles ESCB: IAM High Level Principles • Individual accountability should be ensured ESCB-wide. • Access rights are task specific and granted on a need to know/do/work basis, and, of a non-permanent nature. • Management (issuing, renewing, revoking, etc) of credentials shall be controlled through a formal management process. • Each CB must inform their staff and relevant third-parties of their roles, obligations and duties. 27. 10. 2009 • Each CB must report IAM security incidents to the IAM System Owner and/or Information Owner. Identity Management in Federated Environment, Brussels 9

The Needs • Risks: – businesses without strict IM procedures risk having attackers use employee passwords to gain illegal access to applications and information, or conflicting with government regulations. Building a consistent IAM system: • improve security • boost worker productivity • cut costs • reduce the "integration friction" • while giving access to internal systems to employees, business partners, customers and suppliers. 27. 10. 2009 Identity Management in Federated Environment, Brussels 10

The Needs • Reduce cost by eliminating the need to scale old or proprietary solutions. • Increase security and lower risk by enabling an organization to identify and authenticate a user once, and then use that identity information across multiple systems, including external partner websites. • Improve privacy compliance by allowing the user to control what information is shared, or by limiting the amount of information shared. • Improve the end-user experience by eliminating the need for new account registration through automatic “federated provisioning” or the need to redundantly login through crossdomain single sign-on. The way to do this is through standards. 27. 10. 2009 Identity Management in Federated Environment, Brussels 11

The Standards • The Liberty Alliance (est. September 2001, now 150 companies) develops open standards, guidelines and best practices for identity management - extending SAML (Security Assertion Markup Language ). • IBM, Microsoft, and Veri. Sign also are pushing their own security specifications. • Iden. Trust, similar to SWIFT, Visa and Master Card, was developed by a consortium of financial institutions to deliver trusted electronic commerce. Those standards don't speak (YET) directly to each other. 27. 10. 2009 Identity Management in Federated Environment, Brussels 12

The Standards • The Basel II accord (Advanced Capital Adequacy Framework– Basel II – November 2, 2007) concerns also access to computer data by physical persons and is an opportunity to Significantly improve identity and access management. • Its overhaul approach can generate important return on investment in terms of productivity among users and IT personnel. • It allows to deploy easily procedures that are critical in a banking environment: De-provisioning, segregation of duties, separation of roles, access rights, independence from technologies. • Among the risk evaluation methods proposed by the accord, the advanced measurement approaches (AMA) authorizes banks to evaluate their operational risks themselves. 27. 10. 2009 Identity Management in Federated Environment, Brussels 13

The Objective Build a series of interconnected systems to allow an employee, logged on to his company's intranet to access a business partner's systems and have those systems automatically trust the employee's digital credentials. 27. 10. 2009 Identity Management in Federated Environment, Brussels 14
The Approach • • Build the Business Case – Educate, stay away from techs (this is not a technical exercise). – Outline benefits and cost reduction, productivity gains for 1. Users; 2. Help desk and 3. System administrators. – Ensure compliance with regulations and to auditors (e. g. Basel II, Sarbanes-Oxley etc. ). Pilot the processes, not just the technology. Plan the customization. Do not struggle to provide automated provisioning to non-standardized, old systems with few users. Industry consolidations – be informed of vendors moves – merges, takes-over etc. , do not “lock” into an obsolete solution. 27. 10. 2009 Identity Management in Federated Environment, Brussels 15

The Roadmap • With IAM, laying down a technology roadmap, usual plan and feasibility study after a business analysis just do not work. • The future landscape is unpredictable from the technology point of view alone. • It takes a consistent and useful shared VISION to develop your ideas as to: – who the future players in the identity and identity management field might be and – how their businesses might work. 27. 10. 2009 Identity Management in Federated Environment, Brussels 16

The Roadmap • Security vision – Executive support and guidance. – Information security principles and values, ISMS scope. • IAM strategy – Internal and External drivers, Requirement definition – IAM value statements, Objectives and success criteria. • Policies and standards – Information management and privacy – Definition of the doctrine – Technology standards 27. 10. 2009 Identity Management in Federated Environment, Brussels 17
The Roadmap • IAM architecture – Conceptual and logical IAM architecture – Control definitions • IAM specifications – Detailed specifications on IAM technology components – Guidelines • The IAM roadmap – Practical steps for Integration of IAM – Deployment of IAM components as per specifications. 27. 10. 2009 Identity Management in Federated Environment, Brussels 18

Example 1 Authentication in SEPA and Cross-Border Payments SEPA (the Single European Payment Area) is developing the legal framework for cross-border payments. • In SEPA the IAM is closely aligned to risk management: having a degree of certainty that the counterparty to a transaction is who they purport to be, based on support by one or more trusted intermediaries, involved in a payment across the SEPA geographies, both from both Initiator’s and Recipient’s side. • This management framework must allow parties to: –Interact in an environment of privacy –Ensure authentication, message integrity, non-repudiation. • SEPA will accomplish this by provisioning credentials which enable authentication, encryption and digital signing. 27. 10. 2009 Identity Management in Federated Environment, Brussels 19

Example 1 Authentication in SEPA and Cross-Border Payments • Financial institutions are to meet this challenge by: – multiple forms of identification before transacting payments or opening any account. – mandated processes, namely Know Your Customer (KYC), applied to both individuals and corporations with a stringent controls for levels of trust. • Iden. Trust validates the identities used by the customers, not the data associated with the transaction. The messages with the transaction data are exchanged between the banks on either ends. • A key part of the solution – the End-to-End activity tracking. • The natural providers of this service are the world’s financial institutions, which will remain active on the market in the transaction processing. 27. 10. 2009 Identity Management in Federated Environment, Brussels 20
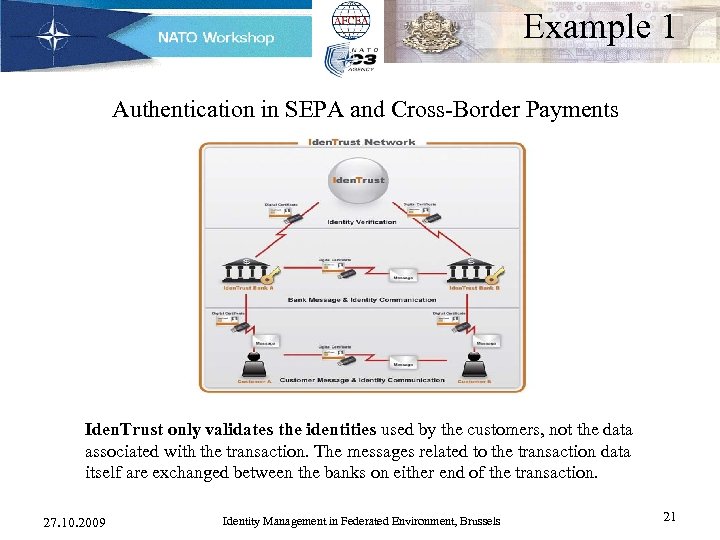
Example 1 Authentication in SEPA and Cross-Border Payments Iden. Trust only validates the identities used by the customers, not the data associated with the transaction. The messages related to the transaction data itself are exchanged between the banks on either end of the transaction. 27. 10. 2009 Identity Management in Federated Environment, Brussels 21

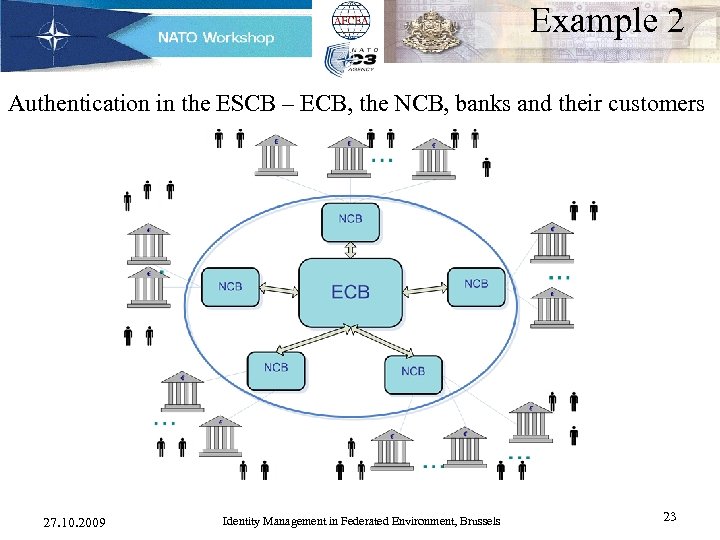
Example 2 Authentication in the ESCB – ECB, the NCB, banks and their customers • Lack of mandatory security components in the ESCB network - authentication, authorization, security logging, SSO etc. • Increase of ESCB-wide applications and the extension to new countries: hundreds of end-users are managed often on “ad hoc”. • The interim solution - ESCB-wide user repository for identity and privilege management. • The objective: a project to enlarge the scope from a centralized directory service to a security infrastructure aligned with its long-term vision for security: – open IT systems to external partners and customers (Credit Institutions, Central Securities Repository, Intern. Institutions and Third parties). – efficient distribution of tasks and applications in the ESCB, new collaboration models. – greater collaboration between NCBs by the re-use of IAM security services regardless location or implementation details. 27. 10. 2009 Identity Management in Federated Environment, Brussels 22
Example 2 Authentication in the ESCB – ECB, the NCB, banks and their customers 27. 10. 2009 Identity Management in Federated Environment, Brussels 23

CONTACTS THANK YOU FOR YOUR ATTENTION ! Dr. Mircho Marchev, Ph. D. , Konstantin Zografov, AFCEA International RVP for the MT&BS Region, Deputy Chairman of the Supervisory Board of Industrial Holding Bulgaria AD 47, Vassil Levski Blvd. Sofia 1000, Bulgaria Tel. ++359 2 980 71 01 Fax: ++ 359 2 980 70 72 Mobile: ++ 359 888 70 82 81 e-mail: zografov@bulgariaholding. com www. bulgariaholding. com 27. 10. 2009 Director of the Information Technology Directorate of the Bulgarian National Bank, Member of ECB ITC 1, Knjaz Alexander I Str. , Sofia 1000, Bulgaria Tel. ++ 359 2 91459 Fax. ++ 359 2 980 2425 e-mail: m. marchev@gmail. bg Identity Management in Federated Environment, Brussels 24
51241c30bb618ae6cf487a23d6753dd0.ppt