 ICT Strategy Identity Management and Enterprise Single Sign-On (ESSO)
ICT Strategy Identity Management and Enterprise Single Sign-On (ESSO)
 Introduction • Follows on from other related themes: • • Unified Operator Interface (UOI) Network Convergence Network Security and Domains Circles of Trust Federated Identities Security as a Service Location transparency Virtualisation
Introduction • Follows on from other related themes: • • Unified Operator Interface (UOI) Network Convergence Network Security and Domains Circles of Trust Federated Identities Security as a Service Location transparency Virtualisation
 Identity Management Business Value “Identity management projects are much more than technology implementations — they drive real business value by reducing direct costs, improving operational efficiency and enabling regulatory compliance. ”
Identity Management Business Value “Identity management projects are much more than technology implementations — they drive real business value by reducing direct costs, improving operational efficiency and enabling regulatory compliance. ”
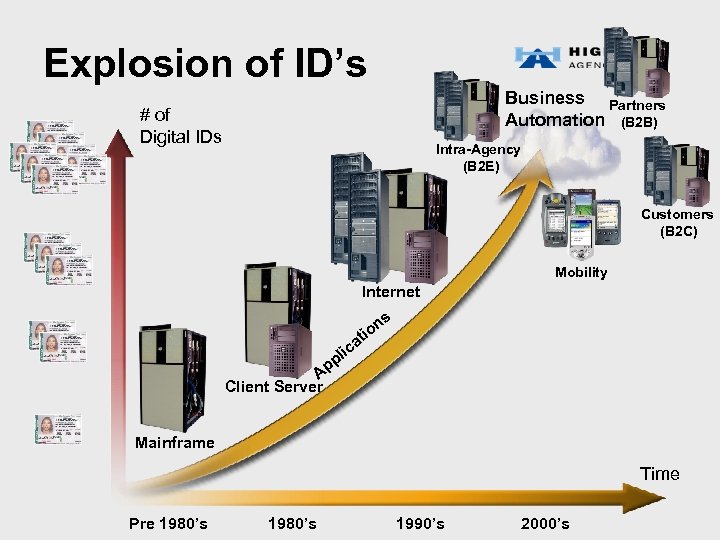 Explosion of ID’s Business Partners Automation (B 2 B) # of Digital IDs Intra-Agency (B 2 E) Customers (B 2 C) Mobility Internet ns o i at c i pl p A Client Server Mainframe Time Pre 1980’s 1990’s 2000’s
Explosion of ID’s Business Partners Automation (B 2 B) # of Digital IDs Intra-Agency (B 2 E) Customers (B 2 C) Mobility Internet ns o i at c i pl p A Client Server Mainframe Time Pre 1980’s 1990’s 2000’s
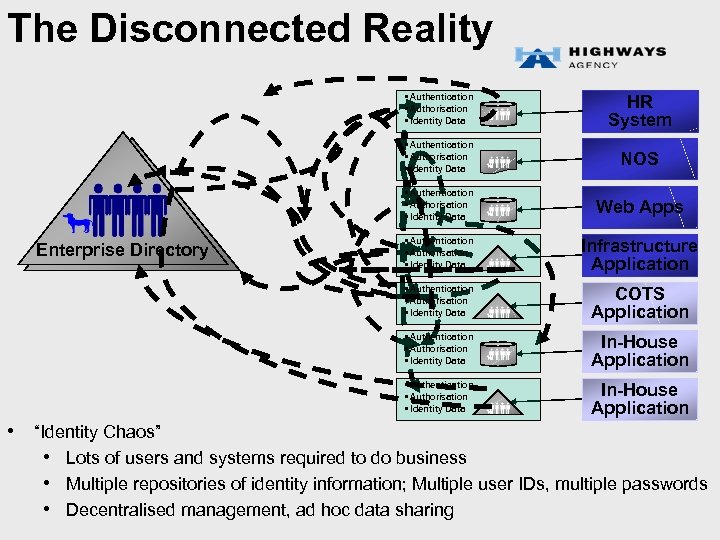 The Disconnected Reality • Authentication • Authorisation • Identity Data NOS • Authentication • Authorisation • Identity Data Web Apps • Authentication • Authorisation • Identity Data Infrastructure Application • Authentication • Authorisation • Identity Data COTS Application • Authentication • Authorisation • Identity Data In-House Application • Authentication • Authorisation • Identity Data Enterprise Directory HR System In-House Application • “Identity Chaos” • Lots of users and systems required to do business • Multiple repositories of identity information; Multiple user IDs, multiple passwords • Decentralised management, ad hoc data sharing
The Disconnected Reality • Authentication • Authorisation • Identity Data NOS • Authentication • Authorisation • Identity Data Web Apps • Authentication • Authorisation • Identity Data Infrastructure Application • Authentication • Authorisation • Identity Data COTS Application • Authentication • Authorisation • Identity Data In-House Application • Authentication • Authorisation • Identity Data Enterprise Directory HR System In-House Application • “Identity Chaos” • Lots of users and systems required to do business • Multiple repositories of identity information; Multiple user IDs, multiple passwords • Decentralised management, ad hoc data sharing
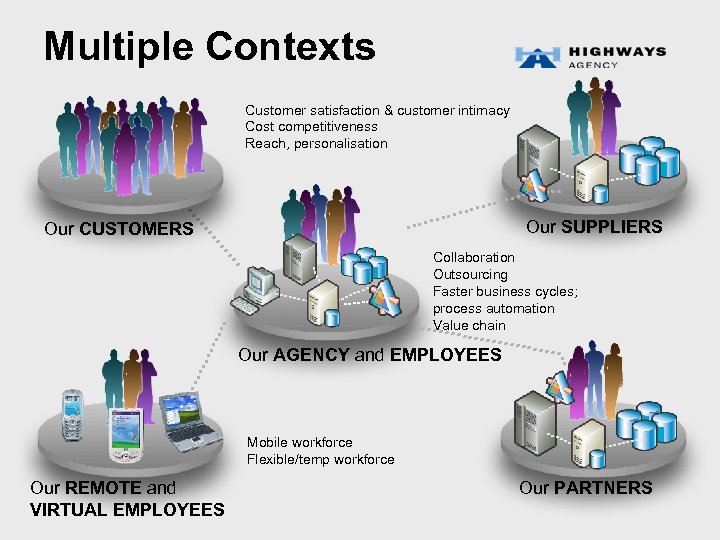 Multiple Contexts Customer satisfaction & customer intimacy Cost competitiveness Reach, personalisation Our SUPPLIERS Our CUSTOMERS Collaboration Outsourcing Faster business cycles; process automation Value chain Our AGENCY and EMPLOYEES Mobile workforce Flexible/temp workforce Our REMOTE and VIRTUAL EMPLOYEES Our PARTNERS
Multiple Contexts Customer satisfaction & customer intimacy Cost competitiveness Reach, personalisation Our SUPPLIERS Our CUSTOMERS Collaboration Outsourcing Faster business cycles; process automation Value chain Our AGENCY and EMPLOYEES Mobile workforce Flexible/temp workforce Our REMOTE and VIRTUAL EMPLOYEES Our PARTNERS
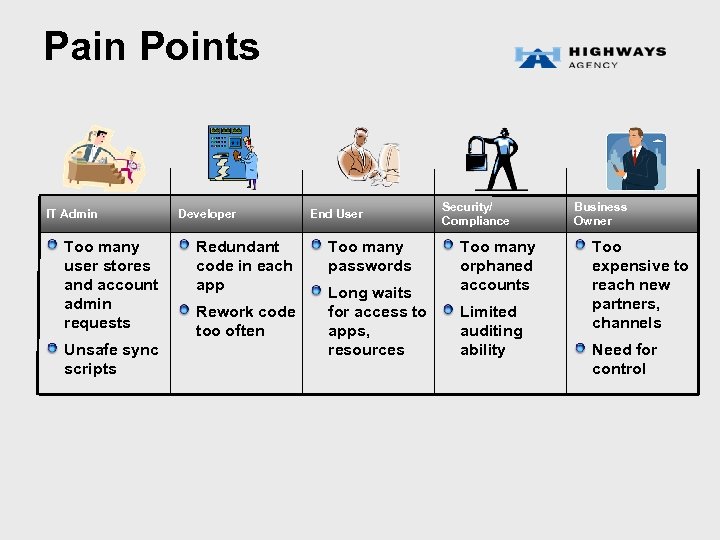 Pain Points IT Admin Too many user stores and account admin requests Unsafe sync scripts Developer Redundant code in each app Rework code too often End User Too many passwords Long waits for access to apps, resources Security/ Compliance Too many orphaned accounts Limited auditing ability Business Owner Too expensive to reach new partners, channels Need for control
Pain Points IT Admin Too many user stores and account admin requests Unsafe sync scripts Developer Redundant code in each app Rework code too often End User Too many passwords Long waits for access to apps, resources Security/ Compliance Too many orphaned accounts Limited auditing ability Business Owner Too expensive to reach new partners, channels Need for control
 To-Be Authentication • Should only have to • • • login once Identity is federated across domains Access permissions determined by Role(s), Groups and Policies Automated provisioning linked to ERP Systems • Employees • joining/leaving (HR) Contractors (Procurement)
To-Be Authentication • Should only have to • • • login once Identity is federated across domains Access permissions determined by Role(s), Groups and Policies Automated provisioning linked to ERP Systems • Employees • joining/leaving (HR) Contractors (Procurement)
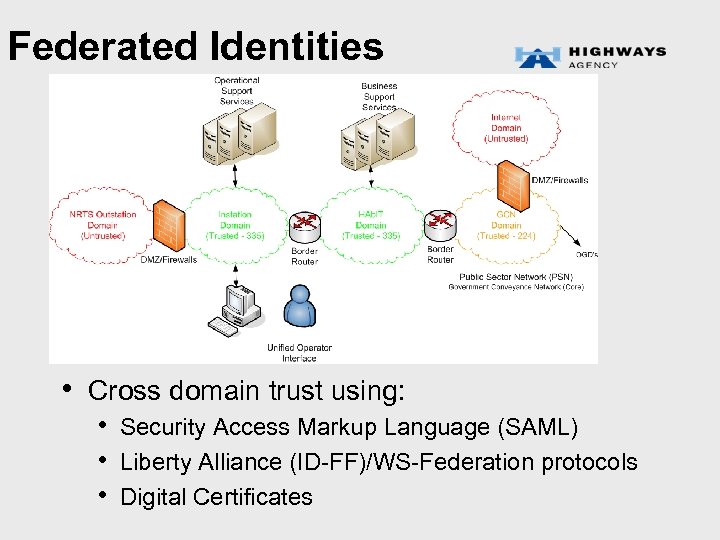 Federated Identities • Cross domain trust using: • Security Access Markup Language (SAML) • Liberty Alliance (ID-FF)/WS-Federation protocols • Digital Certificates
Federated Identities • Cross domain trust using: • Security Access Markup Language (SAML) • Liberty Alliance (ID-FF)/WS-Federation protocols • Digital Certificates
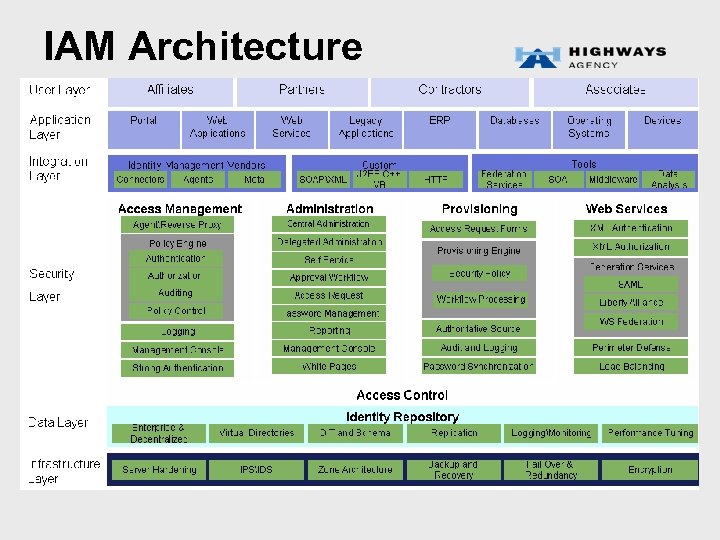 IAM Architecture
IAM Architecture