c6e3a1b8529ddff19bae92d66e3c2a76.ppt
- Количество слайдов: 20
 ICN ISA TNA Wireless Certificates PKI Forum, TWG, Munich 2001 Meeting © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 Trusted Networks & Applications
ICN ISA TNA Wireless Certificates PKI Forum, TWG, Munich 2001 Meeting © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 Trusted Networks & Applications
 Contents q M-Business q Wireless PKI © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Conclusions Trusted Networks & Applications - E-Business Security 2
Contents q M-Business q Wireless PKI © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Conclusions Trusted Networks & Applications - E-Business Security 2
 M-Business q Considered as variant of E-Business that is accommodating mobile users: “M-Business = Internet + E-Business + Mobility” [Siemens I&C] q Classical security requirements occur: q Integrity q Authentication q Non-repudiation q Confidentiality q Classical security solutions apply: q Security infrastructure q Information- and/or transport-bound security services q Security token Trusted Networks & Applications - E-Business Security 3 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Intends to supply ubiquitous access to digitally represented business processes.
M-Business q Considered as variant of E-Business that is accommodating mobile users: “M-Business = Internet + E-Business + Mobility” [Siemens I&C] q Classical security requirements occur: q Integrity q Authentication q Non-repudiation q Confidentiality q Classical security solutions apply: q Security infrastructure q Information- and/or transport-bound security services q Security token Trusted Networks & Applications - E-Business Security 3 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Intends to supply ubiquitous access to digitally represented business processes.
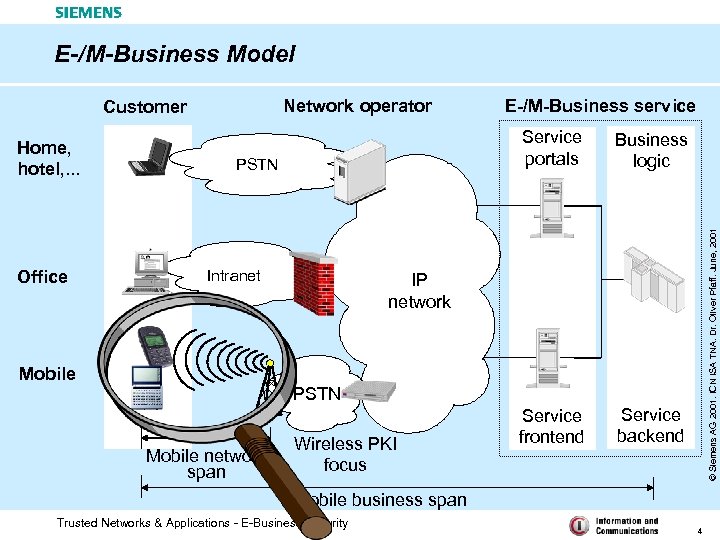 E-/M-Business Model Home, hotel, . . . Office E-/M-Business service Service portals PSTN Intranet Business logic Service frontend Service backend © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 Network operator Customer IP network Mobile PSTN Mobile network span Wireless PKI focus Mobile business span Trusted Networks & Applications - E-Business Security 4
E-/M-Business Model Home, hotel, . . . Office E-/M-Business service Service portals PSTN Intranet Business logic Service frontend Service backend © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 Network operator Customer IP network Mobile PSTN Mobile network span Wireless PKI focus Mobile business span Trusted Networks & Applications - E-Business Security 4
 q Limitations of wireless devices/networks constraint M-Business solutions: q Devices are restricted with respect to battery, display, keyboard, memory, or processor capacity. q Networks are based on narrow-band bearers with high latency. q These limitations apply to mobile security architectures, in particular. But, they are becoming less significant with new device and network generations. q Current approaches to deliver Internet contents/services to wireless devices: q i. Mode Based on HTTP as well as a HTML subset (c. HTML - compact HTML). Services are provided via HTTP proxies. Solution is being developed by NTT Do. Co. Mo (www. nttdocomo. com). q WAP - Wireless Application Protocol Version 1. n specifications are based on an own protocol suite and XML. Services are provided via WAP gateways. Specifications are being developed by the WAP Forum (www. wapforum. org), a global industry consortium. Trusted Networks & Applications - E-Business Security 5 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 M-Business Solutions: Constraints and Approaches
q Limitations of wireless devices/networks constraint M-Business solutions: q Devices are restricted with respect to battery, display, keyboard, memory, or processor capacity. q Networks are based on narrow-band bearers with high latency. q These limitations apply to mobile security architectures, in particular. But, they are becoming less significant with new device and network generations. q Current approaches to deliver Internet contents/services to wireless devices: q i. Mode Based on HTTP as well as a HTML subset (c. HTML - compact HTML). Services are provided via HTTP proxies. Solution is being developed by NTT Do. Co. Mo (www. nttdocomo. com). q WAP - Wireless Application Protocol Version 1. n specifications are based on an own protocol suite and XML. Services are provided via WAP gateways. Specifications are being developed by the WAP Forum (www. wapforum. org), a global industry consortium. Trusted Networks & Applications - E-Business Security 5 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 M-Business Solutions: Constraints and Approaches
 Contents q M-Business q Wireless PKI © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Conclusions Trusted Networks & Applications - E-Business Security 6
Contents q M-Business q Wireless PKI © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Conclusions Trusted Networks & Applications - E-Business Security 6
 WPKI - Wireless PKI: Overview q Public key infrastructure that is designed to support automated identification, authentication, and authorization services in mobile environments. © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Work item of the WAP Forum Security Working Group (WSG). Following PKI specifications are currently available: q WTLS certificate: part of the WTLS specification (status: ‘approved’). Provides a simple, non-ASN. 1 certificate format. q WAPCert: ‘WAP Certificate and CRL Profile’ (status: ‘proposed’). Provides a compact certificate profile on base of PKIX. q WPKI: ‘WAP PKI Definition’ (status: ‘proposed’). Supports WTLS, X. 509 WAPCert, and X. 509 -PKIX certificates. q Basis for efforts of other industry consortiums, including: q Me. T (Mobile Electronic Transactions; www. mobiletransaction. org) q Mobey (promoter of mobile financial services; www. mobeyforum. org) q Mo. Sign (Mobile Signature, a German trial effort; www. mosign. de) q Radicchio (promoter of wireless PKI; www. radicchio. org) Trusted Networks & Applications - E-Business Security 7
WPKI - Wireless PKI: Overview q Public key infrastructure that is designed to support automated identification, authentication, and authorization services in mobile environments. © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Work item of the WAP Forum Security Working Group (WSG). Following PKI specifications are currently available: q WTLS certificate: part of the WTLS specification (status: ‘approved’). Provides a simple, non-ASN. 1 certificate format. q WAPCert: ‘WAP Certificate and CRL Profile’ (status: ‘proposed’). Provides a compact certificate profile on base of PKIX. q WPKI: ‘WAP PKI Definition’ (status: ‘proposed’). Supports WTLS, X. 509 WAPCert, and X. 509 -PKIX certificates. q Basis for efforts of other industry consortiums, including: q Me. T (Mobile Electronic Transactions; www. mobiletransaction. org) q Mobey (promoter of mobile financial services; www. mobeyforum. org) q Mo. Sign (Mobile Signature, a German trial effort; www. mosign. de) q Radicchio (promoter of wireless PKI; www. radicchio. org) Trusted Networks & Applications - E-Business Security 7
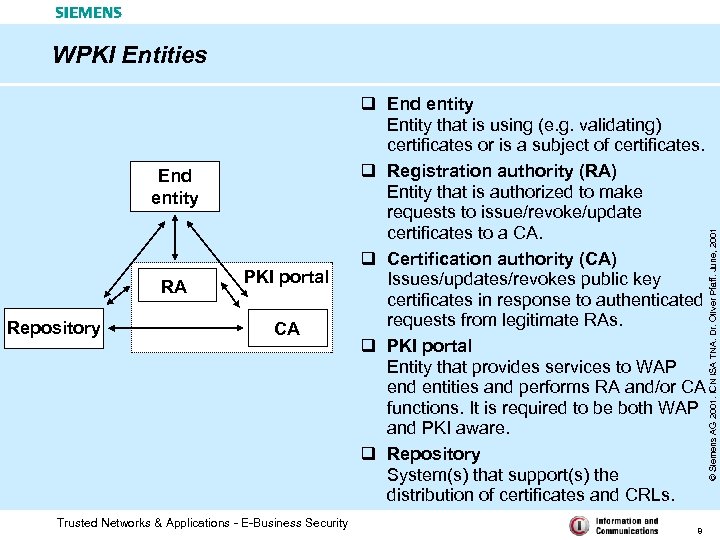 End entity RA Repository PKI portal CA Trusted Networks & Applications - E-Business Security q End entity Entity that is using (e. g. validating) certificates or is a subject of certificates. q Registration authority (RA) Entity that is authorized to make requests to issue/revoke/update certificates to a CA. q Certification authority (CA) Issues/updates/revokes public key certificates in response to authenticated requests from legitimate RAs. q PKI portal Entity that provides services to WAP end entities and performs RA and/or CA functions. It is required to be both WAP and PKI aware. q Repository System(s) that support(s) the distribution of certificates and CRLs. 8 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 WPKI Entities
End entity RA Repository PKI portal CA Trusted Networks & Applications - E-Business Security q End entity Entity that is using (e. g. validating) certificates or is a subject of certificates. q Registration authority (RA) Entity that is authorized to make requests to issue/revoke/update certificates to a CA. q Certification authority (CA) Issues/updates/revokes public key certificates in response to authenticated requests from legitimate RAs. q PKI portal Entity that provides services to WAP end entities and performs RA and/or CA functions. It is required to be both WAP and PKI aware. q Repository System(s) that support(s) the distribution of certificates and CRLs. 8 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 WPKI Entities
 WPKI Applications © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Already specified (and covered by the current ‘WAP PKI Definition’): q Transport-bound security services: q Server authentication (aka: WTLS class 2/3, since WAP 1. 0) q Client authentication (aka: WTLS class 3, since WAP 1. 0) q Information-bound security services: q Signature generation at client-site (via WMLScript ‘sign. Text’, since WAP 1. 2). q Under development (not covered by the current ‘WAP PKI Definition’): q Information-bound security services: q Signature validation at client-site (e. g. signed scripts or active contents such as WTA - Wireless Telephony Application objects) q Encryption at client-site (i. e. wrapping symmetric keys) q Decryption at client-site (i. e. unwrapping symmetric keys) q Remark: WAP security applications are optionally accompanied by a WIM - Wireless Identification Module; WAP includes a WIM specification. Trusted Networks & Applications - E-Business Security 9
WPKI Applications © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Already specified (and covered by the current ‘WAP PKI Definition’): q Transport-bound security services: q Server authentication (aka: WTLS class 2/3, since WAP 1. 0) q Client authentication (aka: WTLS class 3, since WAP 1. 0) q Information-bound security services: q Signature generation at client-site (via WMLScript ‘sign. Text’, since WAP 1. 2). q Under development (not covered by the current ‘WAP PKI Definition’): q Information-bound security services: q Signature validation at client-site (e. g. signed scripts or active contents such as WTA - Wireless Telephony Application objects) q Encryption at client-site (i. e. wrapping symmetric keys) q Decryption at client-site (i. e. unwrapping symmetric keys) q Remark: WAP security applications are optionally accompanied by a WIM - Wireless Identification Module; WAP includes a WIM specification. Trusted Networks & Applications - E-Business Security 9
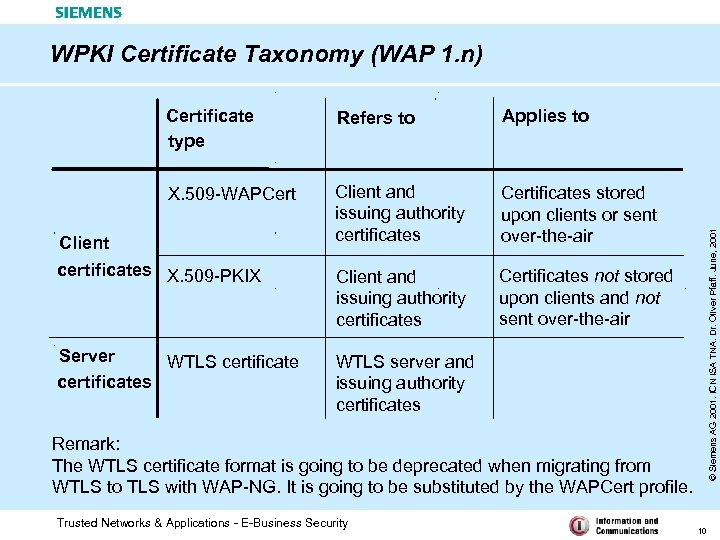 WPKI Certificate Taxonomy (WAP 1. n) Refers to Applies to X. 509 -WAPCert Client and issuing authority certificates Certificates stored upon clients or sent over-the-air Client and issuing authority certificates Certificates not stored upon clients and not sent over-the-air Client certificates X. 509 -PKIX Server WTLS certificates © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 Certificate type WTLS server and issuing authority certificates Remark: The WTLS certificate format is going to be deprecated when migrating from WTLS to TLS with WAP-NG. It is going to be substituted by the WAPCert profile. Trusted Networks & Applications - E-Business Security 10
WPKI Certificate Taxonomy (WAP 1. n) Refers to Applies to X. 509 -WAPCert Client and issuing authority certificates Certificates stored upon clients or sent over-the-air Client and issuing authority certificates Certificates not stored upon clients and not sent over-the-air Client certificates X. 509 -PKIX Server WTLS certificates © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 Certificate type WTLS server and issuing authority certificates Remark: The WTLS certificate format is going to be deprecated when migrating from WTLS to TLS with WAP-NG. It is going to be substituted by the WAPCert profile. Trusted Networks & Applications - E-Business Security 10
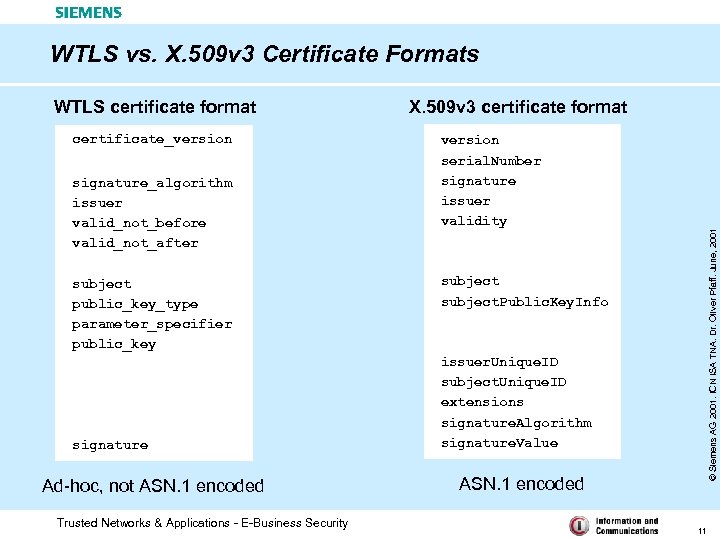 WTLS vs. X. 509 v 3 Certificate Formats certificate_version signature_algorithm issuer valid_not_before valid_not_after subject public_key_type parameter_specifier public_key signature Ad-hoc, not ASN. 1 encoded Trusted Networks & Applications - E-Business Security X. 509 v 3 certificate format version serial. Number signature issuer validity © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 WTLS certificate format subject. Public. Key. Info issuer. Unique. ID subject. Unique. ID extensions signature. Algorithm signature. Value ASN. 1 encoded 11
WTLS vs. X. 509 v 3 Certificate Formats certificate_version signature_algorithm issuer valid_not_before valid_not_after subject public_key_type parameter_specifier public_key signature Ad-hoc, not ASN. 1 encoded Trusted Networks & Applications - E-Business Security X. 509 v 3 certificate format version serial. Number signature issuer validity © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 WTLS certificate format subject. Public. Key. Info issuer. Unique. ID subject. Unique. ID extensions signature. Algorithm signature. Value ASN. 1 encoded 11
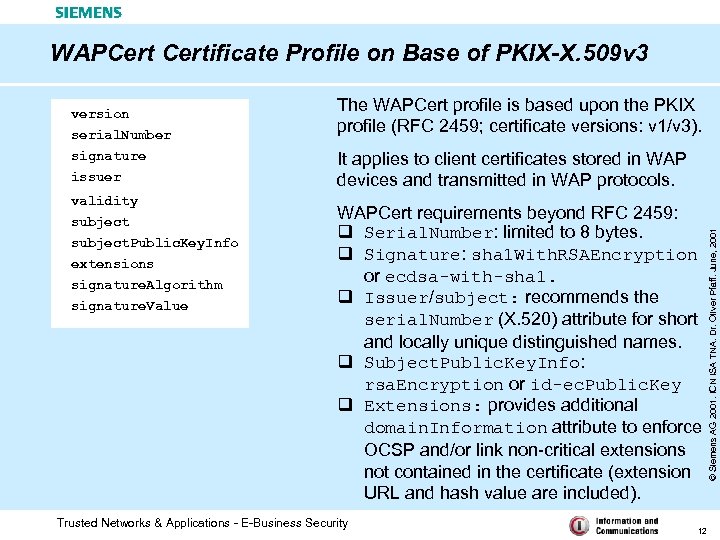 WAPCertificate Profile on Base of PKIX-X. 509 v 3 serial. Number signature issuer validity subject. Public. Key. Info extensions signature. Algorithm signature. Value The WAPCert profile is based upon the PKIX profile (RFC 2459; certificate versions: v 1/v 3). It applies to client certificates stored in WAP devices and transmitted in WAP protocols. WAPCert requirements beyond RFC 2459: q Serial. Number: limited to 8 bytes. q Signature: sha 1 With. RSAEncryption or ecdsa-with-sha 1. q Issuer/subject: recommends the serial. Number (X. 520) attribute for short and locally unique distinguished names. q Subject. Public. Key. Info: rsa. Encryption or id-ec. Public. Key q Extensions: provides additional domain. Information attribute to enforce OCSP and/or link non-critical extensions not contained in the certificate (extension URL and hash value are included). Trusted Networks & Applications - E-Business Security 12 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 version
WAPCertificate Profile on Base of PKIX-X. 509 v 3 serial. Number signature issuer validity subject. Public. Key. Info extensions signature. Algorithm signature. Value The WAPCert profile is based upon the PKIX profile (RFC 2459; certificate versions: v 1/v 3). It applies to client certificates stored in WAP devices and transmitted in WAP protocols. WAPCert requirements beyond RFC 2459: q Serial. Number: limited to 8 bytes. q Signature: sha 1 With. RSAEncryption or ecdsa-with-sha 1. q Issuer/subject: recommends the serial. Number (X. 520) attribute for short and locally unique distinguished names. q Subject. Public. Key. Info: rsa. Encryption or id-ec. Public. Key q Extensions: provides additional domain. Information attribute to enforce OCSP and/or link non-critical extensions not contained in the certificate (extension URL and hash value are included). Trusted Networks & Applications - E-Business Security 12 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 version
 q Key generation q May be upon devices (such as WIM) or externally; may be local or central. q Required are different keys with respect to different PKI applications (esp. for client authentication and digitally signing). q Certification request Processed by a RA. PKI registration may be part of device/service provisioning or performed upon user request. Formats/protocols to transfer public keys and to provide proof of private key possession (POP): q Server certificates: PKCS#10 q Client certificates (authentication): WTLS q Client certificates (digital signature): sign. Text format PKI registration may be assisted by devices delivered with initial key pairs and pre-installed ‘device certificates’ (allowing manufacturers to make statements regarding key quality, device properties, and related procedures). q Certificate issuance Performed by a CA upon legitimate request by a RA. Binding of a specific key usage (e. g. client authentication and digitally signing) is recommended. Due to storage limitations, multiple certificates may be issued per client key pair. Trusted Networks & Applications - E-Business Security 13 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 WPKI Operations
q Key generation q May be upon devices (such as WIM) or externally; may be local or central. q Required are different keys with respect to different PKI applications (esp. for client authentication and digitally signing). q Certification request Processed by a RA. PKI registration may be part of device/service provisioning or performed upon user request. Formats/protocols to transfer public keys and to provide proof of private key possession (POP): q Server certificates: PKCS#10 q Client certificates (authentication): WTLS q Client certificates (digital signature): sign. Text format PKI registration may be assisted by devices delivered with initial key pairs and pre-installed ‘device certificates’ (allowing manufacturers to make statements regarding key quality, device properties, and related procedures). q Certificate issuance Performed by a CA upon legitimate request by a RA. Binding of a specific key usage (e. g. client authentication and digitally signing) is recommended. Due to storage limitations, multiple certificates may be issued per client key pair. Trusted Networks & Applications - E-Business Security 13 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 WPKI Operations
 WPKI Operations (cont’d) Trusted Networks & Applications - E-Business Security © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Certificate delivery/distribution q CA certificates: may be provisioned as part of device/service supply as well as downloaded. Authentication of self-signed CA certificates may be provided out-of-band by a fingerprint mechanism or in-band by an additional signature (verification key certified by another CA instance). q End entity certificates: client-certificate IDs allow to avoid client-site storage as well as over-the-air distribution of client certificates. Such client certificates are provided by repository services. q Certificate validation Performed by end entities. It is intended to mark trusted certificates upon clients (e. g. ‘telephony service provider root’) in order to be able to control certain applications such as download of WTA objects. q Certificate revocation In order to obviate revocation services upon clients, short-lived WTLS server certificates are suggested (CAs simply stop issuance). q Certificate update Currently specified for CA certificates: employs the signature variant for the distribution of self-signed certificates (cf. above). 14
WPKI Operations (cont’d) Trusted Networks & Applications - E-Business Security © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Certificate delivery/distribution q CA certificates: may be provisioned as part of device/service supply as well as downloaded. Authentication of self-signed CA certificates may be provided out-of-band by a fingerprint mechanism or in-band by an additional signature (verification key certified by another CA instance). q End entity certificates: client-certificate IDs allow to avoid client-site storage as well as over-the-air distribution of client certificates. Such client certificates are provided by repository services. q Certificate validation Performed by end entities. It is intended to mark trusted certificates upon clients (e. g. ‘telephony service provider root’) in order to be able to control certain applications such as download of WTA objects. q Certificate revocation In order to obviate revocation services upon clients, short-lived WTLS server certificates are suggested (CAs simply stop issuance). q Certificate update Currently specified for CA certificates: employs the signature variant for the distribution of self-signed certificates (cf. above). 14
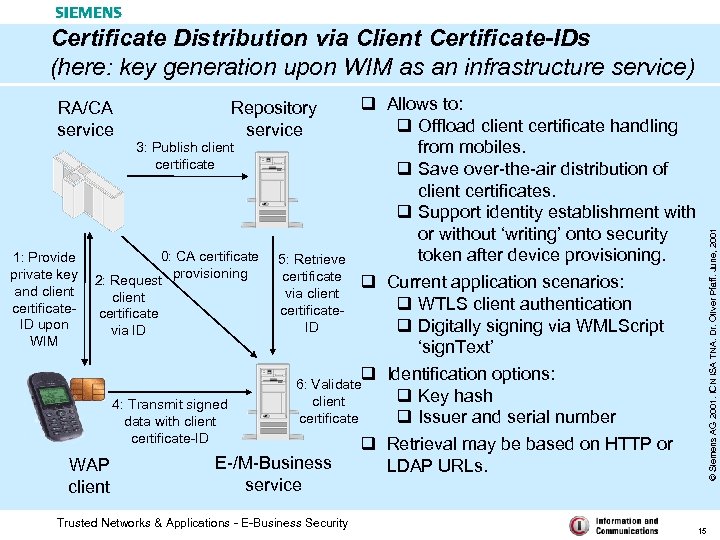 Certificate Distribution via Client Certificate-IDs (here: key generation upon WIM as an infrastructure service) q Allows to: q Offload client certificate handling 3: Publish client from mobiles. certificate q Save over-the-air distribution of client certificates. q Support identity establishment with or without ‘writing’ onto security 0: CA certificate 5: Retrieve token after device provisioning. 1: Provide private key 2: Request provisioning certificate q Current application scenarios: and client via client q WTLS client authentication certificatecertificate ID upon q Digitally signing via WMLScript ID via ID WIM ‘sign. Text’ q Identification options: 6: Validate q Key hash client 4: Transmit signed certificate q Issuer and serial number data with client certificate-ID q Retrieval may be based on HTTP or E-/M-Business WAP LDAP URLs. service client Repository service Trusted Networks & Applications - E-Business Security © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 RA/CA service 15
Certificate Distribution via Client Certificate-IDs (here: key generation upon WIM as an infrastructure service) q Allows to: q Offload client certificate handling 3: Publish client from mobiles. certificate q Save over-the-air distribution of client certificates. q Support identity establishment with or without ‘writing’ onto security 0: CA certificate 5: Retrieve token after device provisioning. 1: Provide private key 2: Request provisioning certificate q Current application scenarios: and client via client q WTLS client authentication certificatecertificate ID upon q Digitally signing via WMLScript ID via ID WIM ‘sign. Text’ q Identification options: 6: Validate q Key hash client 4: Transmit signed certificate q Issuer and serial number data with client certificate-ID q Retrieval may be based on HTTP or E-/M-Business WAP LDAP URLs. service client Repository service Trusted Networks & Applications - E-Business Security © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 RA/CA service 15
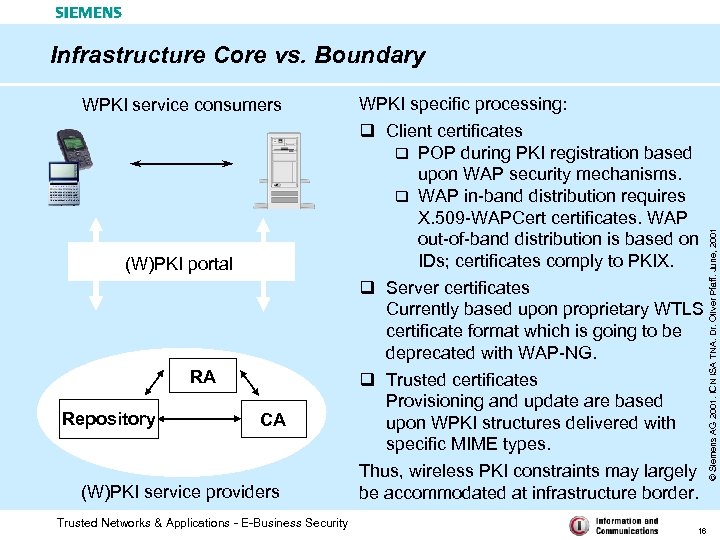 Infrastructure Core vs. Boundary (W)PKI portal RA Repository CA (W)PKI service providers Trusted Networks & Applications - E-Business Security WPKI specific processing: q Client certificates q POP during PKI registration based upon WAP security mechanisms. q WAP in-band distribution requires X. 509 -WAPCert certificates. WAP out-of-band distribution is based on IDs; certificates comply to PKIX. q Server certificates Currently based upon proprietary WTLS certificate format which is going to be deprecated with WAP-NG. q Trusted certificates Provisioning and update are based upon WPKI structures delivered with specific MIME types. Thus, wireless PKI constraints may largely be accommodated at infrastructure border. 16 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 WPKI service consumers
Infrastructure Core vs. Boundary (W)PKI portal RA Repository CA (W)PKI service providers Trusted Networks & Applications - E-Business Security WPKI specific processing: q Client certificates q POP during PKI registration based upon WAP security mechanisms. q WAP in-band distribution requires X. 509 -WAPCert certificates. WAP out-of-band distribution is based on IDs; certificates comply to PKIX. q Server certificates Currently based upon proprietary WTLS certificate format which is going to be deprecated with WAP-NG. q Trusted certificates Provisioning and update are based upon WPKI structures delivered with specific MIME types. Thus, wireless PKI constraints may largely be accommodated at infrastructure border. 16 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 WPKI service consumers
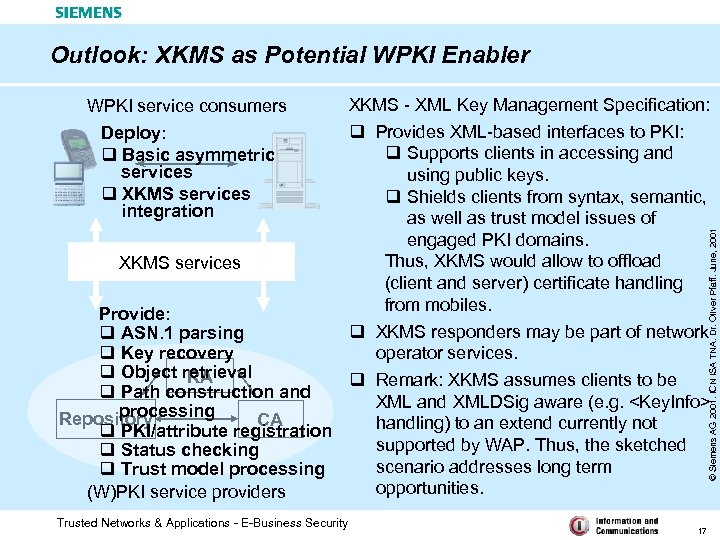 Outlook: XKMS as Potential WPKI Enabler WPKI service consumers Deploy: q Basic asymmetric services q XKMS services integration XKMS - XML Key Management Specification: © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Provides XML-based interfaces to PKI: q Supports clients in accessing and using public keys. q Shields clients from syntax, semantic, as well as trust model issues of engaged PKI domains. Thus, XKMS would allow to offload XKMS services (client and server) certificate handling from mobiles. Provide: q XKMS responders may be part of network q ASN. 1 parsing q Key recovery operator services. q Object retrieval RA q Remark: XKMS assumes clients to be q Path construction and XMLDSig aware (e. g.
Outlook: XKMS as Potential WPKI Enabler WPKI service consumers Deploy: q Basic asymmetric services q XKMS services integration XKMS - XML Key Management Specification: © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Provides XML-based interfaces to PKI: q Supports clients in accessing and using public keys. q Shields clients from syntax, semantic, as well as trust model issues of engaged PKI domains. Thus, XKMS would allow to offload XKMS services (client and server) certificate handling from mobiles. Provide: q XKMS responders may be part of network q ASN. 1 parsing q Key recovery operator services. q Object retrieval RA q Remark: XKMS assumes clients to be q Path construction and XMLDSig aware (e. g.
 Contents q M-Business q Wireless PKI © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Conclusions Trusted Networks & Applications - E-Business Security 18
Contents q M-Business q Wireless PKI © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Conclusions Trusted Networks & Applications - E-Business Security 18
 Conclusions q Business development aspects: q Wireless PKI may see truly large consumer PKI domains rapidly due to existing business processes (e. g. device provisioning), available local infrastructure (e. g. network provider outlets), and product properties (e. g. smart card capabilities in GSM/GPRS phones). q Best-of-both-worlds / how to? q Avoid multiple infrastructures when offering E-/M-Business services via multiple distribution channels such as Web and WAP: q Unify infrastructure core. q Accommodate necessary deviations at infrastructure boundary, i. e. as part of service provisioning. q Emerging XKMS services promise adequate support for wireless needs (lean clients) and are becoming a matter of WAP-NG considerations. Trusted Networks & Applications - E-Business Security 19 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Technical aspects: q Compared to classical (i. e. originally wired) PKI efforts, WPKI is no new solution approach; it essentially resembles X. 509 v 3 and PKIX ideas. q In part, WPKI documents define formats, protocols, and procedures that deviate from classical approaches.
Conclusions q Business development aspects: q Wireless PKI may see truly large consumer PKI domains rapidly due to existing business processes (e. g. device provisioning), available local infrastructure (e. g. network provider outlets), and product properties (e. g. smart card capabilities in GSM/GPRS phones). q Best-of-both-worlds / how to? q Avoid multiple infrastructures when offering E-/M-Business services via multiple distribution channels such as Web and WAP: q Unify infrastructure core. q Accommodate necessary deviations at infrastructure boundary, i. e. as part of service provisioning. q Emerging XKMS services promise adequate support for wireless needs (lean clients) and are becoming a matter of WAP-NG considerations. Trusted Networks & Applications - E-Business Security 19 © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 q Technical aspects: q Compared to classical (i. e. originally wired) PKI efforts, WPKI is no new solution approach; it essentially resembles X. 509 v 3 and PKIX ideas. q In part, WPKI documents define formats, protocols, and procedures that deviate from classical approaches.
 Author Information © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 Siemens AG Information and Communication Networks Postal Address: Siemens AG - ICN ISA TNA D-81370 Munich Office Address: Charles-de-Gaulle- Str. 2 Dr. Oliver Pfaff Technology Area Manager E-Business Security Trusted Networks & Applications - E-Business Security Tel. +49. 89. 722. 53227 Fax: +49. 89. 722. 53249 Mobile: +49. 172. 8250805 E-Mail: oliver. pfaff@icn. siemens. de 20
Author Information © Siemens AG 2001. ICN ISA TNA. Dr. Oliver Pfaff. June, 2001 Siemens AG Information and Communication Networks Postal Address: Siemens AG - ICN ISA TNA D-81370 Munich Office Address: Charles-de-Gaulle- Str. 2 Dr. Oliver Pfaff Technology Area Manager E-Business Security Trusted Networks & Applications - E-Business Security Tel. +49. 89. 722. 53227 Fax: +49. 89. 722. 53249 Mobile: +49. 172. 8250805 E-Mail: oliver. pfaff@icn. siemens. de 20


