efc49344184d0f9e32d2f5eb7baf09b3.ppt
- Количество слайдов: 40

IBM System Storage™ IBM Tape Encryption and TKLM v 2. 0. 1 © 2012 IBM Corporation

IBM System Storage® Agenda § Tape Encryption Overview § TKLM – Tivoli Key Lifecycle Manager 4 TKLM v 2. 0. 1 Enhancements § Implementation Considerations § Demo Page 2 © 2012 IBM Corporation
IBM System Storage® IBM Tape Data Encryption § LTO 6 / LTO 5 / LTO 4 Tape Drive 4 Standard feature on all FC & SAS LTO 6/5/4 Tape Drives 4 Supports “traditional” and “encrypted” modes of operation § TS 1140 / TS 1130 / TS 1120 Tape Drive 4 Standard feature on all new TS 11 xx Tape Drives 4 Supports “traditional” and “encrypted” modes of operation § TKLM – Tivoli Key Lifecycle Manager 4 AIX, Sun, Linux, Windows and z/OS 4 Serves keys § ISKLM – IBM Security Key Lifecycle Manager 4 z/OS Page 3 Tivoli Key Lifecycle Manager © 2012 IBM Corporation
IBM System Storage® FIPS 140 -2 Certification § FIPS – Federal Information Processing Standard § Cryptographic Service Providers - certified CE 2 Card 4 IBM Java Cryptographic Extensions (JCE) 4 § Tape Drives TS 1120 – Certified 4 TS 1130 – Certified 4 TS 1140 – In process 4 LTO 4 – Certified 4 LTO 5 - Certified 4 4 Page 4 http: //csrc. nist. gov/groups/STM/cmvp/validation. html © 2012 IBM Corporation
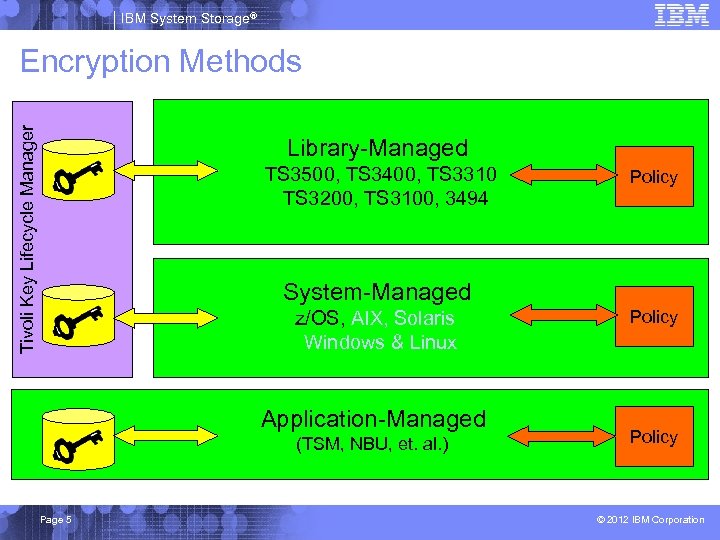
IBM System Storage® Tivoli Key Lifecycle Manager Encryption Methods Library-Managed____ TS 3500, TS 3400, TS 3310_____ TS 3200, TS 3100, 3494____ Policy System-Managed____ z/OS, AIX, Solaris_____ Windows & Linux_____ Application-Managed (TSM, NBU, et. al. ) Page 5 Policy © 2012 IBM Corporation
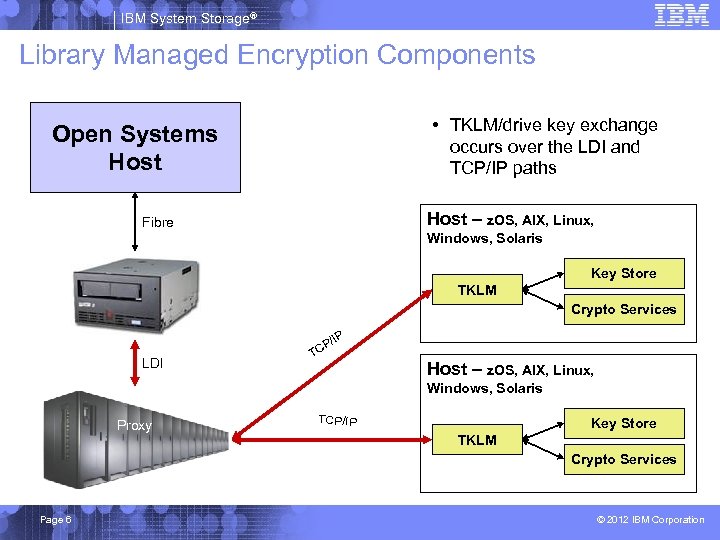
IBM System Storage® Library Managed Encryption Components • TKLM/drive key exchange occurs over the LDI and TCP/IP paths Open Systems Host – z. OS, AIX, Linux, Fibre Windows, Solaris Key Store TKLM Crypto Services /IP LDI P TC Host – z. OS, AIX, Linux, Windows, Solaris Proxy TCP/IP Key Store TKLM Crypto Services Page 6 © 2012 IBM Corporation
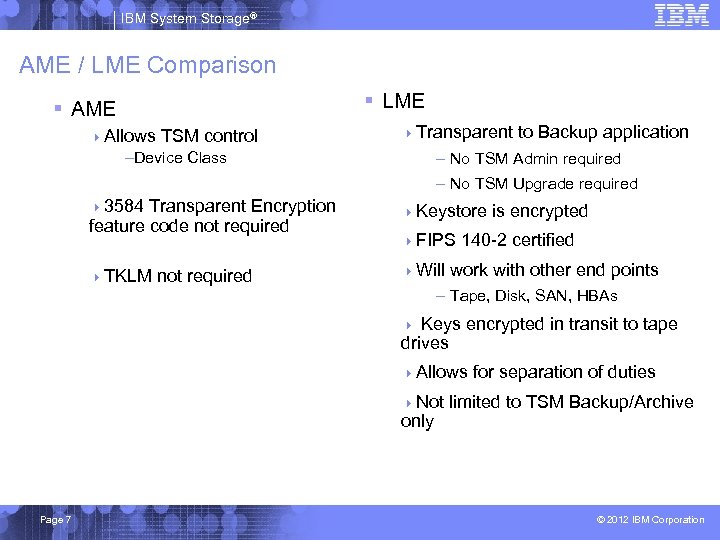
IBM System Storage® AME / LME Comparison § LME § AME 4 Allows TSM control 4 Transparent –Device Class to Backup application – No TSM Admin required – No TSM Upgrade required 43584 Transparent Encryption feature code not required 4 Keystore 4 TKLM 4 Will not required 4 FIPS is encrypted 140 -2 certified work with other end points – Tape, Disk, SAN, HBAs Keys encrypted in transit to tape drives 4 4 Allows 4 Not only Page 7 for separation of duties limited to TSM Backup/Archive © 2012 IBM Corporation
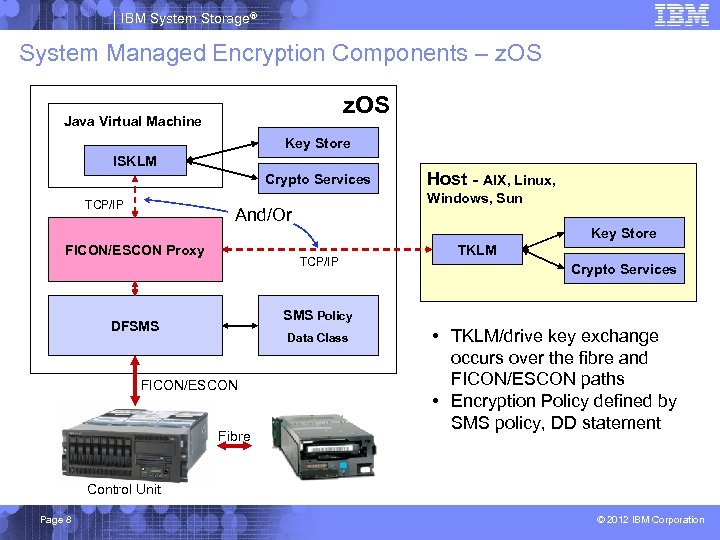
IBM System Storage® System Managed Encryption Components – z. OS Java Virtual Machine Key Store ISKLM Crypto Services TCP/IP Host - AIX, Linux, Windows, Sun And/Or Key Store FICON/ESCON Proxy TCP/IP TKLM Crypto Services SMS Policy DFSMS Data Class FICON/ESCON Fibre • TKLM/drive key exchange occurs over the fibre and FICON/ESCON paths • Encryption Policy defined by SMS policy, DD statement Control Unit Page 8 © 2012 IBM Corporation
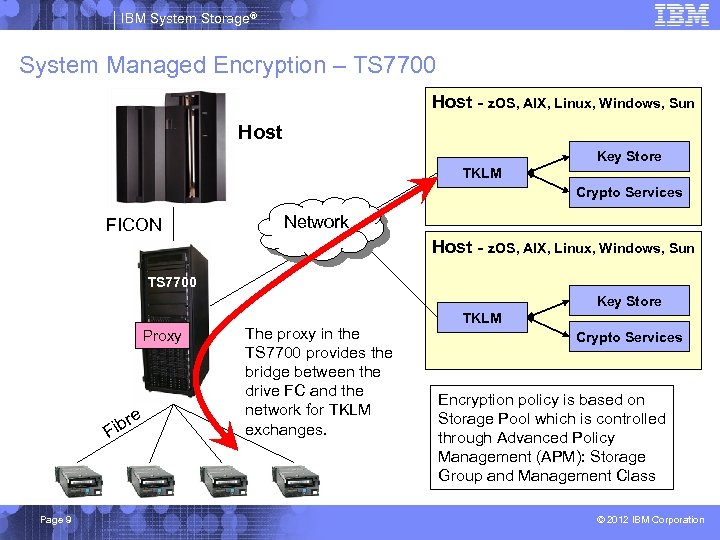
IBM System Storage® System Managed Encryption – TS 7700 Host - z. OS, AIX, Linux, Windows, Sun Host Key Store TKLM Crypto Services FICON Network Host - z. OS, AIX, Linux, Windows, Sun TS 7700 Key Store Proxy e ibr F Page 9 The proxy in the TS 7700 provides the bridge between the drive FC and the network for TKLM exchanges. TKLM Crypto Services Encryption policy is based on Storage Pool which is controlled through Advanced Policy Management (APM): Storage Group and Management Class © 2012 IBM Corporation
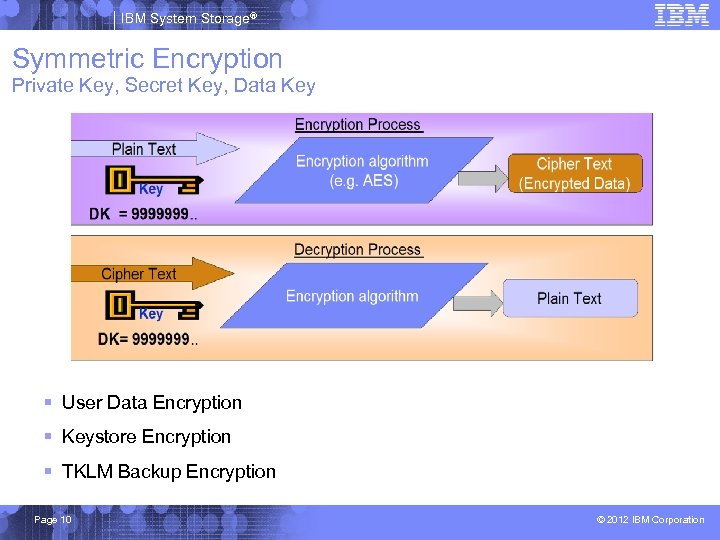
IBM System Storage® Symmetric Encryption Private Key, Secret Key, Data Key § User Data Encryption § Keystore Encryption § TKLM Backup Encryption Page 10 © 2012 IBM Corporation
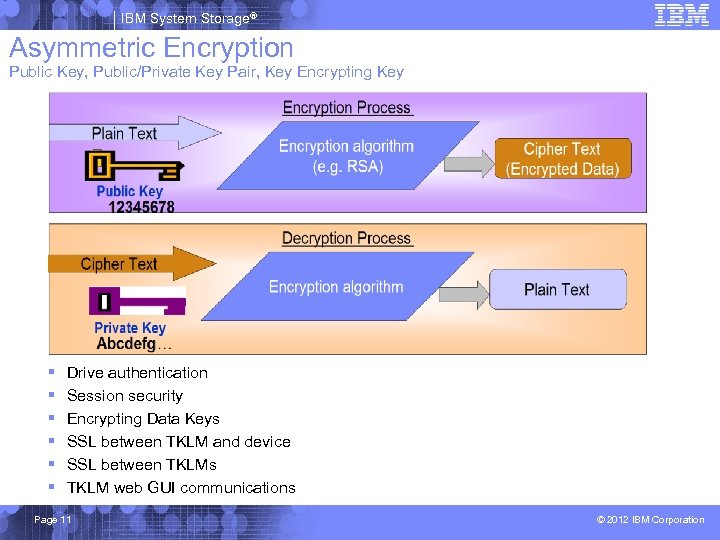
IBM System Storage® Asymmetric Encryption Public Key, Public/Private Key Pair, Key Encrypting Key § § § Drive authentication Session security Encrypting Data Keys SSL between TKLM and device SSL between TKLMs TKLM web GUI communications Page 11 © 2012 IBM Corporation
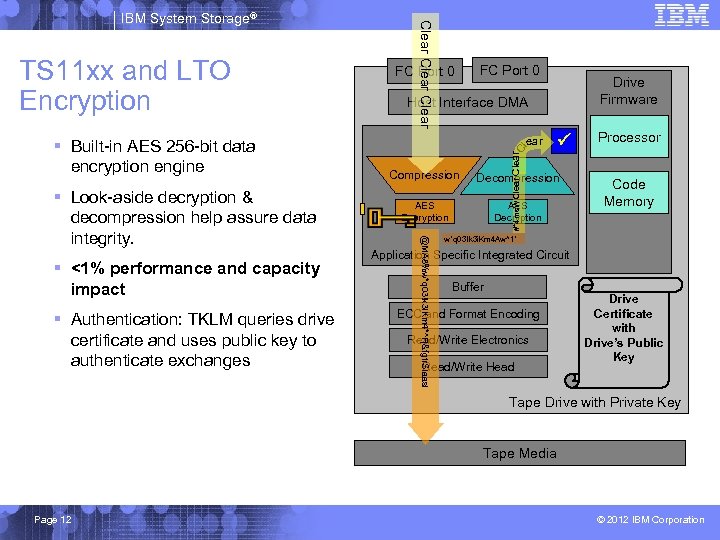
§ <1% performance and capacity impact § Authentication: TKLM queries drive certificate and uses public key to authenticate exchanges Drive Firmware Host Interface DMA l ear Compression Decompression AES Encryption AES Decryption @MA 8%w*q 03!k 3 i. Km 4*^Fj&fgtr. SIaasl § Look-aside decryption & decompression help assure data integrity. FC Port 0 Clear C § Built-in AES 256 -bit data encryption engine FC Port 0 #*4 ms. W Clear TS 11 xx and LTO Encryption Clear IBM System Storage® Processor Code Memory w*q 03!k 3 i. Km 4 Aw^1* Application Specific Integrated Circuit Buffer ECC and Format Encoding Read/Write Electronics Read/Write Head Drive Certificate with Drive’s Public Key Tape Drive with Private Key Tape Media Page 12 © 2012 IBM Corporation
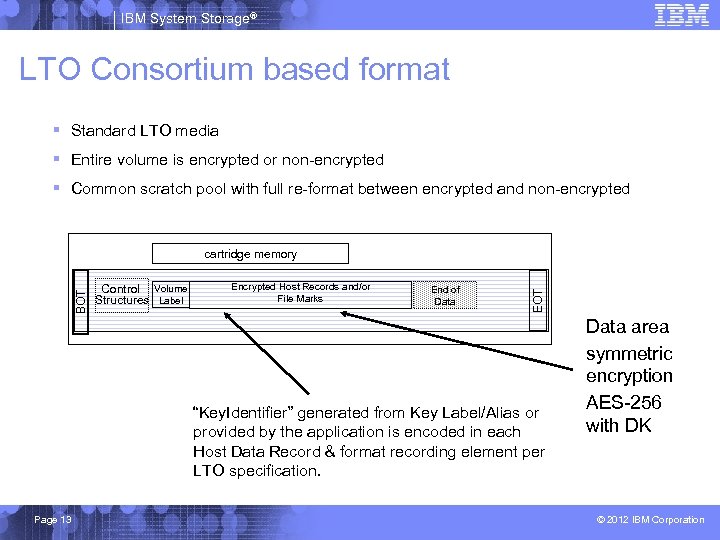
IBM System Storage® LTO Consortium based format § Standard LTO media § Entire volume is encrypted or non-encrypted § Common scratch pool with full re-format between encrypted and non-encrypted Control Volume Structures Label Encrypted Host Records and/or File Marks End of Data EOT BOT cartridge memory “Key. Identifier” generated from Key Label/Alias or provided by the application is encoded in each Host Data Record & format recording element per LTO specification. Page 13 Data area symmetric encryption AES-256 with DK © 2012 IBM Corporation
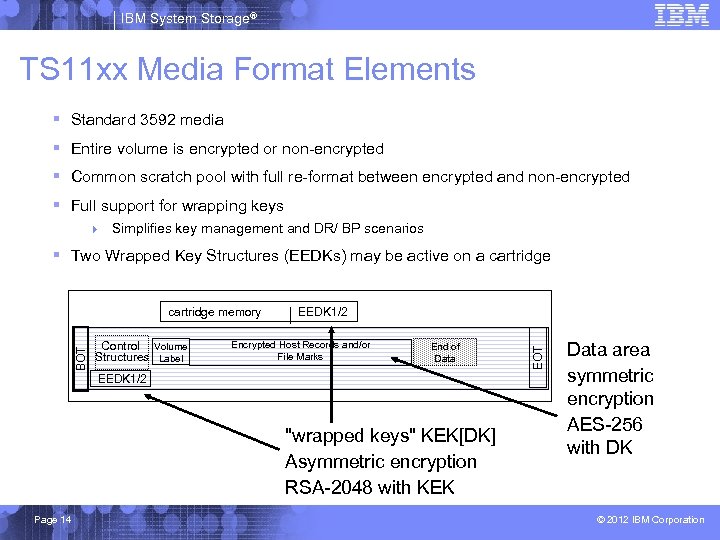
IBM System Storage® TS 11 xx Media Format Elements § Standard 3592 media § Entire volume is encrypted or non-encrypted § Common scratch pool with full re-format between encrypted and non-encrypted § Full support for wrapping keys 4 Simplifies key management and DR/ BP scenarios § Two Wrapped Key Structures (EEDKs) may be active on a cartridge Control Volume Structures Label EEDK 1/2 EEDK 1 Encrypted Host Records and/or File Marks End of Data EEDK 1/2 EEDK 1 "wrapped keys" KEK[DK] Asymmetric encryption RSA-2048 with KEK Page 14 EOT BOT cartridge memory Data area symmetric encryption AES-256 with DK © 2012 IBM Corporation

IBM System Storage® Agenda § Tape Encryption Overview § TKLM – Tivoli Key Lifecycle Manager 4 TKLM v 2. 0. 1 § Implementation Considerations § Demo Page 15 © 2012 IBM Corporation
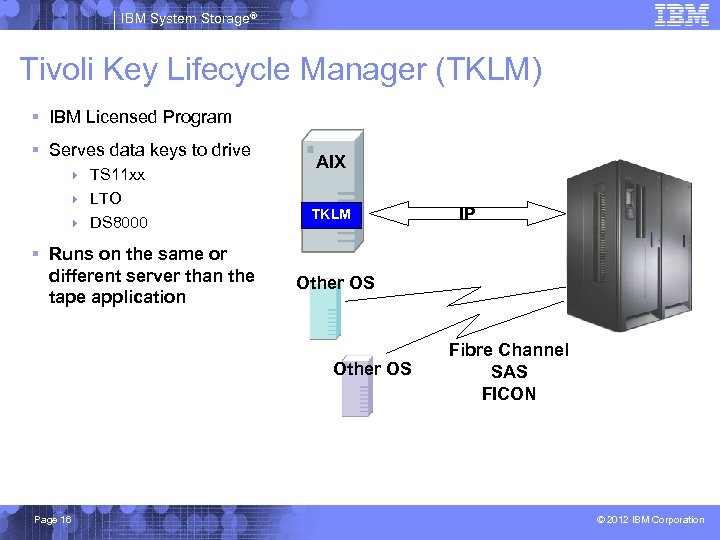
IBM System Storage® Tivoli Key Lifecycle Manager (TKLM) § IBM Licensed Program § Serves data keys to drive 4 TS 11 xx 4 LTO 4 DS 8000 § Runs on the same or different server than the tape application AIX TKLM Other OS Page 16 IP Fibre Channel SAS FICON © 2012 IBM Corporation

IBM System Storage® TKLM OS Support § AIX 5. 3 or later § AIX 6. 1 or later § Red Hat Enterprise Linux 4. 0 (32 bit) § Red Hat Enterprise Linux 5. 0 (32 bit and 64 bit) § Su. SE Linux 9 (32 bit) § Su. SE Linux 10 (32 bit and 64 bit) § Solaris 9 Sparc § Solaris 10 Sparc § Windows Server 2003 (32 bit and 64 bit) § Windows Server 2008 (32 bit and 64 bit) § z/OS 1. 9, 1. 10, 1. 11 (TKLM v 1 only) Page 17 © 2012 IBM Corporation
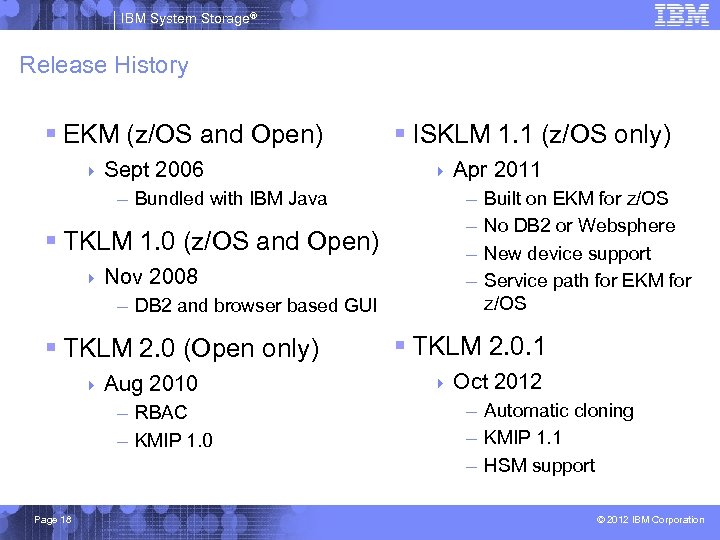
IBM System Storage® Release History § EKM (z/OS and Open) 4 Sept 2006 – Bundled with IBM Java § TKLM 1. 0 (z/OS and Open) 4 Nov 2008 – DB 2 and browser based GUI § TKLM 2. 0 (Open only) 4 Aug 2010 – RBAC – KMIP 1. 0 Page 18 § ISKLM 1. 1 (z/OS only) 4 Apr – – 2011 Built on EKM for z/OS No DB 2 or Websphere New device support Service path for EKM for z/OS § TKLM 2. 0. 1 4 Oct 2012 – Automatic cloning – KMIP 1. 1 – HSM support © 2012 IBM Corporation

IBM System Storage® Automated clone replication § Up to 5 Clones § Clones 4 Keystore 4 DB 2 tables 4 Config file § Replication is encrypted § Master and clone systems must be identical Page 19 © 2012 IBM Corporation

IBM System Storage® KMIP v 1. 1 support Device Credentials – how does a consumer of keys identify itself 4 Serial number identifying the client or device 4 Network address 4 Instance or volume identifier 4 Group 4 Shared secret Device Credentials are used: • To help with PCI-DSS compliance, only serve keys to known devices • Ease of use for deployment – can use certificates as a right to connect rather than managing a certificate per device Improved asymmetric key support • Major contributions from PGP and RSA • Will be the basis for managing the key material in certificates Grouping of keys • Default and fresh attributes now supported • Useful for pools of shared media • Useful for key rotation Page 20 © 2012 IBM Corporation
IBM System Storage® TKLM Resources § TKLM Website: www. ibm. com/software/tivoli/products/key-lifecycle-mgr 4 TKLM Info Center 4 TKLM Installation and Configuration Guide 4 Flash Demos – Information Infrastructure Security with IBM – TKLM GUI demo § TKLM Data Sheet 4 ftp: //ftp. software. ibm. com/common/ssi/pm/sp/n/tid 14031 usen/TID 14031 US EN. PDF § White Paper: Simplifying Key Management with Tivoli Key Lifecycle Manager 4 ftp: //ftp. software. ibm. com/common/ssi/sa/wh/n/tiw 14026 usen/TIW 14026 US EN. PDF § Red Book: IBM System Storage Tape Encryption Solutions 4 http: //www. redbooks. ibm. com/abstracts/sg 247320. html? Open § Red Paper: ISKLM for z/OS 4 http: //www. redbooks. ibm. com/redpapers/abstracts/redp 4646. html? Open Page 21 © 2012 IBM Corporation
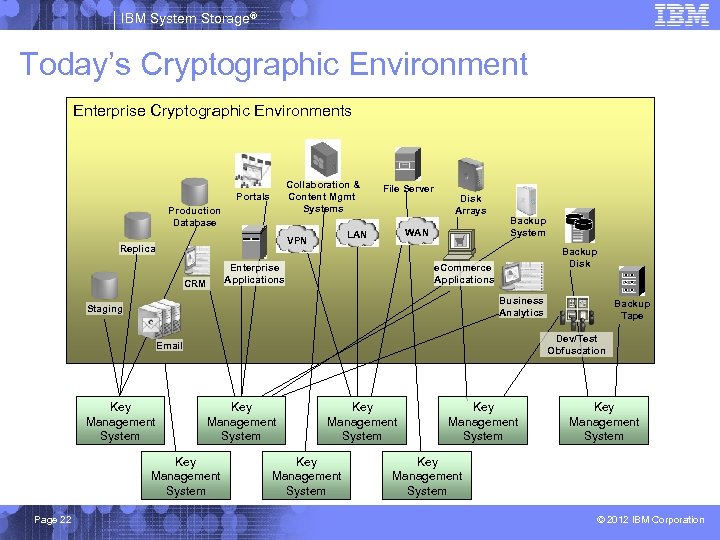
IBM System Storage® Today’s Cryptographic Environment Enterprise Cryptographic Environments Collaboration & Content Mgmt Systems Portals Production Database Enterprise Applications CRM Disk Arrays WAN LAN VPN Replica File Server Backup System Backup Disk e. Commerce Applications Business Analytics Staging Dev/Test Obfuscation Email Key Management System Page 22 Backup Tape Key Management System Key Management System © 2012 IBM Corporation
IBM System Storage® KMIP Overview n Key Management Interoperability Protocol (KMIP) n Key-management to encryption client protocol n Enables key lifecycle management n Generation, submission, retrieval, and deletion n Supports Symmetric keys n Asymmetric keys n Digital certificates n n http: //www. oasisopen. org/committees/tc_home. php? wg_abbrev=kmip Page 23 © 2012 IBM Corporation
IBM System Storage® TKLM v 2 Supported Devices § IBM Tape Drives 4 LTO 4 / LTO 5 / LTO 6 4 TS 1120 / TS 1130 / TS 1140 § IBM Tape Libraries 43494 4 DS 5000 4 DS 3000 4 Emulex – One. Secure HBAs 4 TS 3400 4 Brocade 4 TS 3310 / TS 3100 4 TS 2900 § Non-IBM Tape Libraries 4 Quantum (ADIC) i 2000 4 Quantum (ADIC) i 500 Page 24 4 DS 8000 § KMIP Supported Devices 4 TS 3500 4 TS 3200 § IBM Disk Drives (IBM OEM) – IBM SAN 32 B-E 4 (2498 -E 32) – FC: 3895 - Encryption Blade 4 Net. App –FAS 2040 –FAS 3200 –FAS 6200 © 2012 IBM Corporation
IBM System Storage® Agenda § Tape Encryption Overview § TKLM – Tivoli Key Lifecycle Manager § Implementation Considerations Design Considerations 4 TS 3500 (3584) Implementation 4 § Demo Page 25 © 2012 IBM Corporation
IBM System Storage® TKLM Design Considerations § What Operating System? § Server sizing? § Dedicated Server or LPAR? 4 Dedicated LPAR or Shared LPAR? § TKLM - Local or Remote? § How implement HA? § Moving keys offsite § What to Encrypt? § Key rotation? § Number of Keys? Page 26 © 2012 IBM Corporation
IBM System Storage® What Operating System? § AIX Keystore and Crypto Services § Linux § Solaris § Windows § z/OS TKLM Drive Table Configuration Page 27 © 2012 IBM Corporation
IBM System Storage® What Size Server? § CPU § Memory § Disk Page 28 © 2012 IBM Corporation
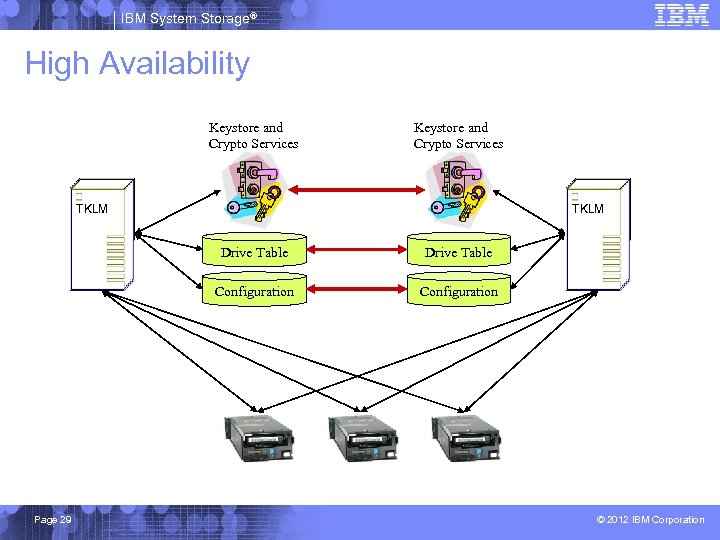
IBM System Storage® High Availability Keystore and Crypto Services TKLM Drive Table Configuration Page 29 Drive Table Configuration © 2012 IBM Corporation
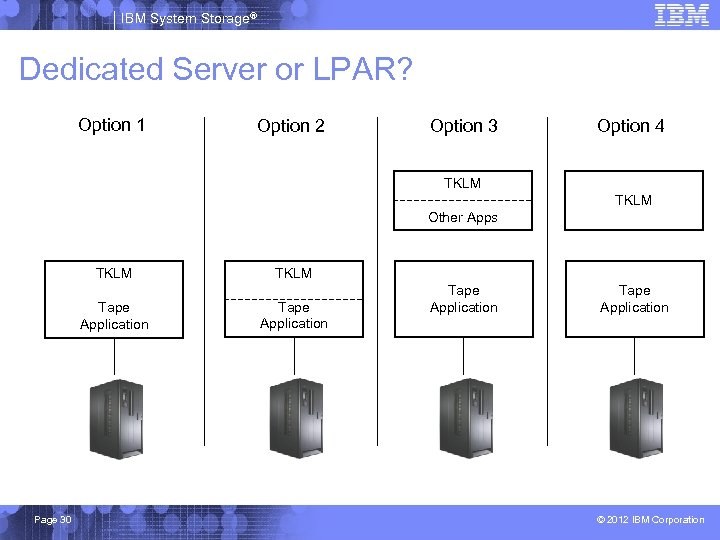
IBM System Storage® Dedicated Server or LPAR? Option 1 Option 2 Option 3 Option 4 TKLM Other Apps TKLM Tape Application Page 30 TKLM Tape Application © 2012 IBM Corporation
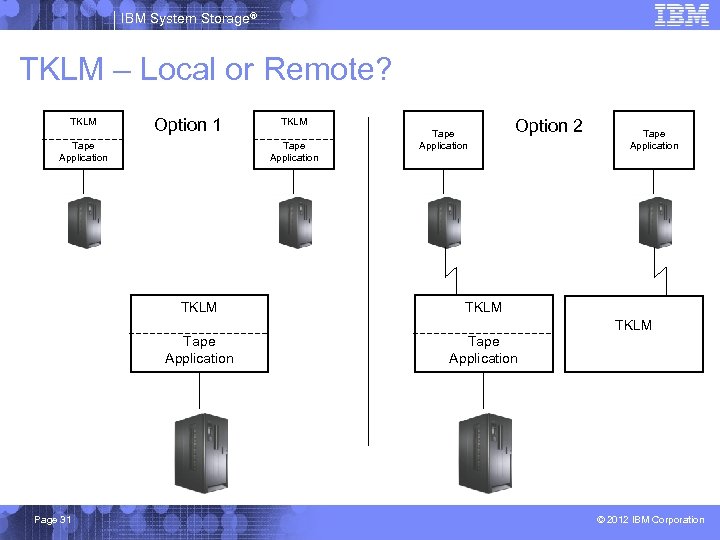
IBM System Storage® TKLM – Local or Remote? TKLM Option 1 Tape Application TKLM Tape Application Option 2 Tape Application TKLM Tape Application Page 31 Tape Application © 2012 IBM Corporation
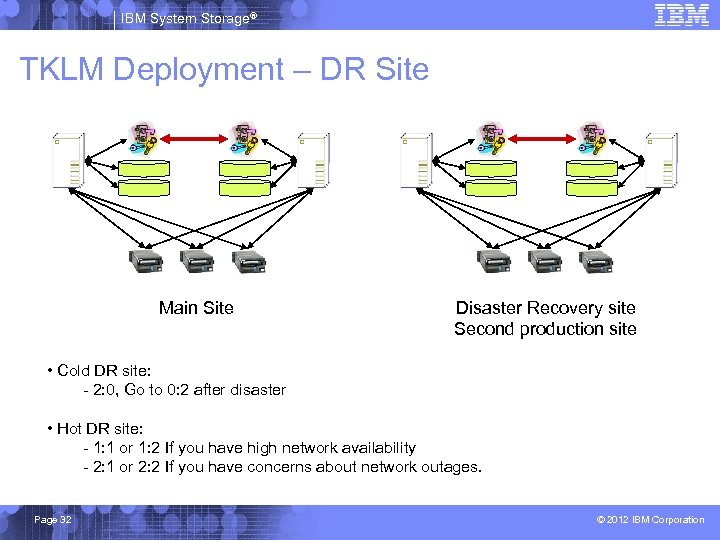
IBM System Storage® TKLM Deployment – DR Site Main Site Disaster Recovery site Second production site • Cold DR site: - 2: 0, Go to 0: 2 after disaster • Hot DR site: - 1: 1 or 1: 2 If you have high network availability - 2: 1 or 2: 2 If you have concerns about network outages. Page 32 © 2012 IBM Corporation
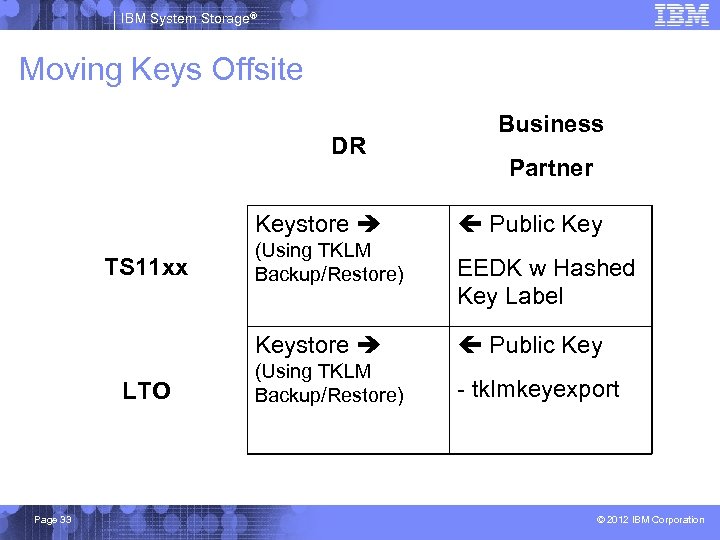
IBM System Storage® Moving Keys Offsite DR Keystore TS 11 xx (Using TKLM Backup/Restore) Business Partner Public Key EEDK w Hashed Key Label Keystore LTO Page 33 Public Key (Using TKLM Backup/Restore) - tklmkeyexport © 2012 IBM Corporation
IBM System Storage® What to Encrypt? § Selective Encryption § Encrypt All § Recovery Page 34 AES x. R%p. W@7 = © 2012 IBM Corporation
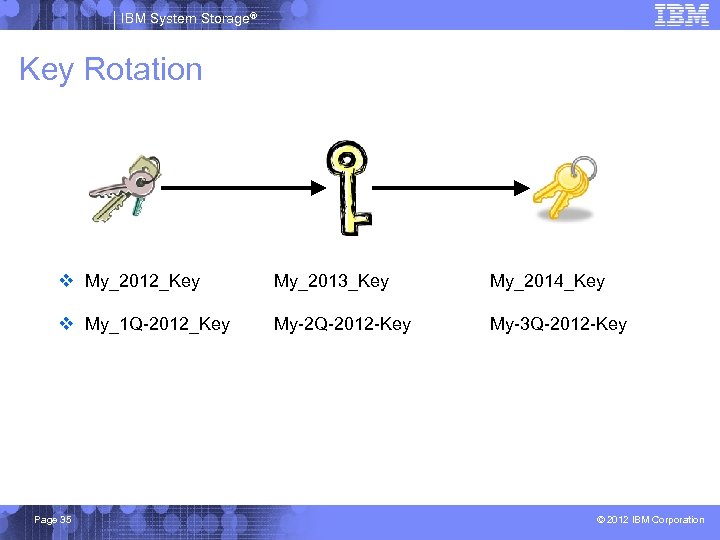
IBM System Storage® Key Rotation v My_2012_Key My_2013_Key My_2014_Key v My_1 Q-2012_Key My-2 Q-2012 -Key My-3 Q-2012 -Key Page 35 © 2012 IBM Corporation

IBM System Storage® Internal or External Perform Resource? § IBM Implementation Services for tape systems - tape encryption and key management § Tasks Performed 4 Planning session meeting 4 Architecture and Design 4 Implementation 4 Procedure Development 4 Skills transfer § IBM Benefits 4 Proven methodology 4 Support from IBM’s dedicated storage specialists 4 Basic skills instruction for client staff 4 Accelerated implementation Page 36 © 2012 IBM Corporation
IBM System Storage® Agenda § Tape Encryption Overview § Tape Encryption Process § Tape Encryption Implementation 4 Design Considerations 4 TS 3500 (3584) Implementation § Demo Page 37 © 2012 IBM Corporation
IBM System Storage® TS 3500 Library Implementation § Install or upgrade tape drives § Upgrade drive firmware § Update TS 3500 firmware § Enable drives for encryption (LME) Set up TKLM IP address 4 Update drive encryption method 4 Setup Barcode Encryption Policy (Optional) 4 Run Key Path Diagnostic Test 4 § Enable drives for encryption (SME) 4 Page 38 Update drive encryption method © 2012 IBM Corporation

IBM System Storage® Questions? Page 39 © 2012 IBM Corporation
IBM System Storage® Demo Page 40 © 2012 IBM Corporation
efc49344184d0f9e32d2f5eb7baf09b3.ppt