eb280b672b174363579311f6d225e209.ppt
- Количество слайдов: 136

IBM Storage and Technology Group IBM Americas ATS DS 8000 Release 4. 2 Technical Announcement Teleconference February 26 th 2009 Alison Pate - patea@us. ibm. com IBM Americas Advanced Technical Support © 2009 IBM Corporation

IBM Storage and Technology Group Agenda § Announcement Overview/Ordering – Dave Heggen § Encryption – Bob Kern § Flash. Copy/PPRC – Hank Sautter § SSD – Charlie Burger § SATA – Paul Spagnolo § § 2 CLI/GUI enhancements – Paul Spagnolo LDAP – Brian Sherman Performance – Lee La Frese/Carlos Pratt Questions and Answers © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 Release 4. 2 Product Announcement Overview and Ordering Information IBM Advanced Technical Support – Americas Dave Heggen – DHEGGEN@US. IBM. COM © 2009 IBM Corporation

IBM Storage and Technology Group Announcement Summary § DS 8000 R 4. 2 Announcement Date 2/10/2009 § DS 8000 R 4. 2 Generally Available 3/6/2009 (exceptions noted) – 6 new disk options • Full Disk Encryption (FDE) for 146, 300, and 450 GB DDMs • Solid State Drives (SSD) for 73 and 146 GB DDMs • 1 TB 7. 2 K RPM SATA – Remote Pair Flash. Copy – Intelligent Write Caching § New DS 8000 s with R 4 do not need #180 x for TPC-R – IP v 6 is supported on current TPC-R releases § DS 6000 support for System i IOPless adapter for improved performance 4 © 2009 IBM Corporation
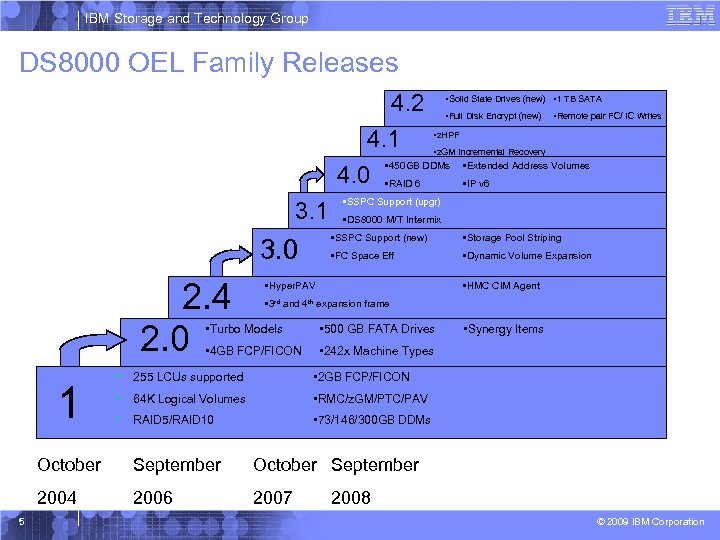
IBM Storage and Technology Group DS 8000 OEL Family Releases 4. 2 4. 1 4. 0 3. 1 • Full Disk Encrypt (new) • z. HPF • z. GM Incremental Recovery • 450 GB DDMs • Extended Address Volumes • RAID 6 • IP v 6 • SSPC Support (upgr) • DS 8000 M/T Intermix • Storage Pool Striping • FC Space Eff • Dynamic Volume Expansion • Hyper. PAV • HMC CIM Agent • 3 rd and 4 th expansion frame • Turbo Models • 500 GB FATA Drives • 4 GB FCP/FICON 1 • 242 x Machine Types § 255 LCUs supported § 64 K Logical Volumes • RMC/z. GM/PTC/PAV § RAID 5/RAID 10 • Synergy Items • 2 GB FCP/FICON • 73/146/300 GB DDMs October September 2004 5 • Remote pair FC/ IC Writes • SSPC Support (new) 3. 0 2. 4 2. 0 • Solid State Drives (new) • 1 TB SATA 2006 2007 2008 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 – R 4. 2 Announcement Summary § Announcing new features codes for 2107 (IBM Announcement 109 -119) – 1 TB SATA Disk Drives § Announcing new features codes for 242 x (IBM Announcement 109 -120) – – – – Full Disk Encryption (146, 300, 450 GB) 15, 000 rpm Fibre Channel Disk Drives Encryption Drive Set Support (#1751) SSD (73, 146 GB) ~150, 000 rpm Disk Drives (April 24 th GA) 1 TB SATA Disk Drives Laptop Management Console Do. D Indicator Release 4. 2 Bundle Family § Announcing new functions for all M/Ts (no new feature codes): – Intelligent Write Caching – Remote Pair Flash. Copy (April 24 th GA) § Lab Based Services Availability (no new feature codes): – Encryption Certification/Activation Service • § Required/Waived for Activation of Licensed Feature for Encryption No Withdrawals with this release 6 © 2009 IBM Corporation
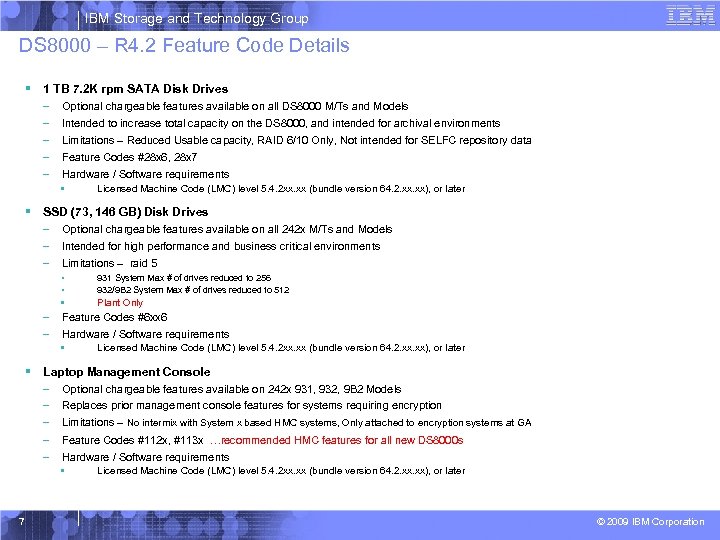
IBM Storage and Technology Group DS 8000 – R 4. 2 Feature Code Details § 1 TB 7. 2 K rpm SATA Disk Drives – – – Optional chargeable features available on all DS 8000 M/Ts and Models Intended to increase total capacity on the DS 8000, and intended for archival environments Limitations – Reduced Usable capacity, RAID 6/10 Only, Not intended for SELFC repository data Feature Codes #28 x 6, 28 x 7 Hardware / Software requirements • Licensed Machine Code (LMC) level 5. 4. 2 xx. xx (bundle version 64. 2. xx), or later § SSD (73, 146 GB) Disk Drives – – – Optional chargeable features available on all 242 x M/Ts and Models Intended for high performance and business critical environments Limitations – raid 5 • • – – 931 System Max # of drives reduced to 256 932/9 B 2 System Max # of drives reduced to 512 • Plant Only Feature Codes #6 xx 6 Hardware / Software requirements • Licensed Machine Code (LMC) level 5. 4. 2 xx. xx (bundle version 64. 2. xx), or later § Laptop Management Console – – – 7 Optional chargeable features available on 242 x 931, 932, 9 B 2 Models Replaces prior management console features for systems requiring encryption Limitations – No intermix with System x based HMC systems, Only attached to encryption systems at GA Feature Codes #112 x, #113 x …recommended HMC features for all new DS 8000 s Hardware / Software requirements • Licensed Machine Code (LMC) level 5. 4. 2 xx. xx (bundle version 64. 2. xx), or later © 2009 IBM Corporation
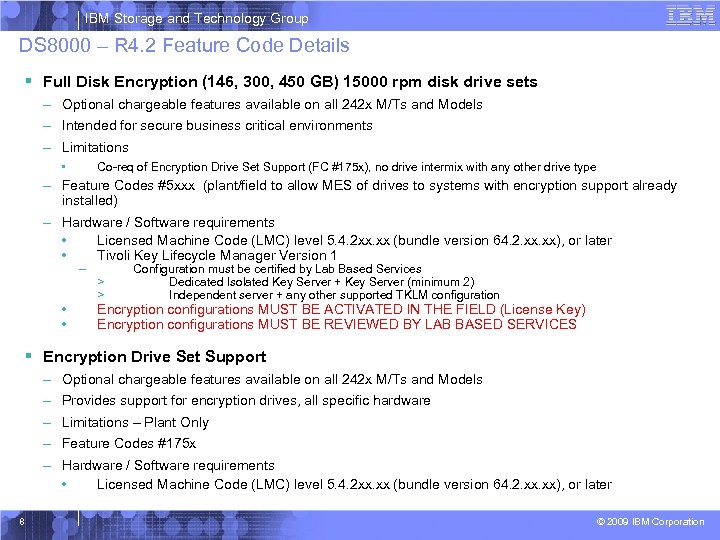
IBM Storage and Technology Group DS 8000 – R 4. 2 Feature Code Details § Full Disk Encryption (146, 300, 450 GB) 15000 rpm disk drive sets – Optional chargeable features available on all 242 x M/Ts and Models – Intended for secure business critical environments – Limitations • Co-req of Encryption Drive Set Support (FC #175 x), no drive intermix with any other drive type – Feature Codes #5 xxx (plant/field to allow MES of drives to systems with encryption support already installed) – Hardware / Software requirements • Licensed Machine Code (LMC) level 5. 4. 2 xx. xx (bundle version 64. 2. xx), or later • Tivoli Key Lifecycle Manager Version 1 – • • > > Configuration must be certified by Lab Based Services Dedicated Isolated Key Server + Key Server (minimum 2) Independent server + any other supported TKLM configuration Encryption configurations MUST BE ACTIVATED IN THE FIELD (License Key) Encryption configurations MUST BE REVIEWED BY LAB BASED SERVICES § Encryption Drive Set Support – Optional chargeable features available on all 242 x M/Ts and Models – Provides support for encryption drives, all specific hardware – Limitations – Plant Only – Feature Codes #175 x – Hardware / Software requirements • Licensed Machine Code (LMC) level 5. 4. 2 xx. xx (bundle version 64. 2. xx), or later 8 © 2009 IBM Corporation

IBM Storage and Technology Group Encryption TKLM Requirements TIVOLI KEY LIFECYCLE MANAGER PLANNING § The DS 8000 series supports: – IBM Tivoli Key Lifecycle Manager V 1. 0, • 5724 -T 60 1. 0. 0 IBM Tivoli Key Lifecycle Manager • 5608 -A 91 1. 0. 0 IBM Tivoli Key Lifecycle Manager (distributed for non-Passport Advantage) – IBM Tivoli Key Lifecycle Manager for z/OS V 1. 0 • 1 5698 -B 35 1. 0. 0 IBM Tivoli Key Lifecycle Manager for z/OS § Isolated key servers – Ordered with feature number 0021, (Machine type 2805 Model MC 3) will have a Linux operating system and TKLM software pre-installed. • Customers will need to acquire a TKLM license for use of the TKLM software, • Ordered separately from the standalone server hardware. § FULL DISK Encryption Activation is a customer responsibility. IBM Full Disk Encryption offerings must be activated prior to use. This activation is part of the installation and configuration steps required for use of the technology. This installation and activation review is performed by the IBM Systems and Technology Lab Services group. • To order: Send email to storsvcs@us. ibm. com 9 © 2009 IBM Corporation
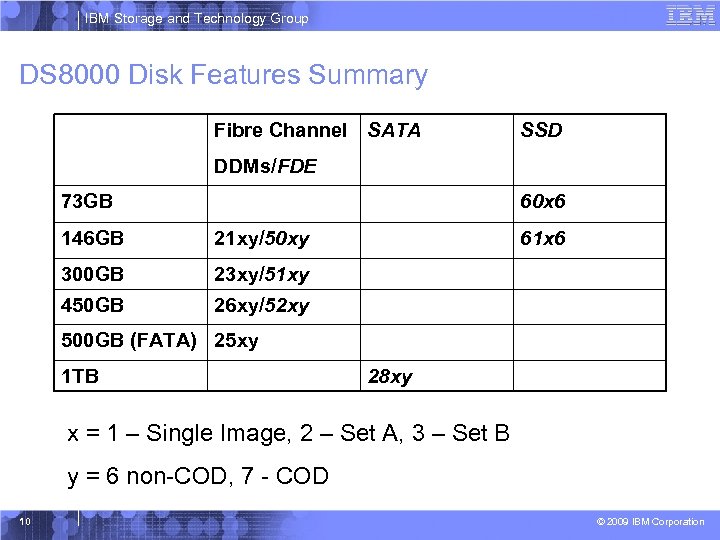
IBM Storage and Technology Group DS 8000 Disk Features Summary Fibre Channel SATA SSD DDMs/FDE 73 GB 60 x 6 146 GB 21 xy/50 xy 300 GB 23 xy/51 xy 450 GB 61 x 6 26 xy/52 xy 500 GB (FATA) 25 xy 1 TB 28 xy x = 1 – Single Image, 2 – Set A, 3 – Set B y = 6 non-COD, 7 - COD 10 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 – R 4. 2 Feature Code Details § Do. D Indicator – Optional features available on 242 x A frames – Indicates Do. D order for label attachment – Feature Codes #0020 § Initial Capacity Indicator – E-config selected, not significant § Release 4. 2 Bundle Family – Optional features available on all 242 x M/Ts and Models – Selects R 4. 2 microcode for function that requires new level microcode – Limitations – none – Feature Codes #1702 – Hardware / Software requirements • 11 Provides Licensed Machine Code (LMC) level 5. 4. 2 xx. xx (bundle version 64. 2. xx), or later © 2009 IBM Corporation
IBM Storage and Technology Group DS 8000 – Function Details § New functions for all M/Ts (no new feature codes): – Intelligent Write Caching • New performance algorithm to maximize our cache performance – Remote Pair Flash. Copy • Improves DR configuration of Flash. Copy and Metro Mirror configurations § Lab Services Availability (no new feature codes): – Encryption Certification/Activation Service • Provides ability to activate encryption on supported DS 8000 systems, while certifying correct configuration of key management software. – Customer can waive service 12 © 2009 IBM Corporation
IBM Storage and Technology Group R 4. 2 Planned Availability Dates § Announce Date Feb 10, 2009 § Planned Availability Date (all features/functions): – March 6, 2009 Plant and Field • • • 1 TB SATA Disk Drives Laptop Management Console Intelligent Write Caching Do. D Indicator FDE Disk Sets – March 6, 2009 • Encrypted Drive Set Support (Plant Only, 242 x only at this time) – April 24 th • • SSD disk drive sets (Plant Only, 242 x only at this time) Remote Pair Flash. Copy (Plant/Field) § MES Planned Availability Date (all features/functions): – March 6, 2009: • • 1 TB 7, 200 rpm SATA disk drive MESs (all DS 8000 Machine Types) Full Disk Encryption disk drive MESs (242 x Machine Types only) – 13 Encryption enabled systems only © 2009 IBM Corporation
IBM Storage and Technology Group Two possible New 242 x Configurations for #1702 § DS 8000 Option 1 – SSD/ENTERPRISE/SATA DDM Features • limit of 128 SSD DDMs/8 features per DA, 2 features optimal • SSD feature order will require i-Listed RPQ – 112 x/113 x HMC (recommended option) § DS 8000 Option 2 – Full Disk Encryption ( FDE DDM feature(s) and #1751) • FDE feature order will require i-Listed RPQ 8 S 1028 – 112 x/113 x required option, Recommend 2 HMCs – TKLM (2 instances), Feature 0021 for Independent Server – Lab Services Review i-Listed RPQs used for review notifications 14 © 2009 IBM Corporation
IBM Storage and Technology Group Innovation that matters IBM Americas ATS DS 8000 R 4. 2 Disk Encryption February 26, 2009 Bob Kern bobkern@us. ibm. com © 2009 IBM Corporation
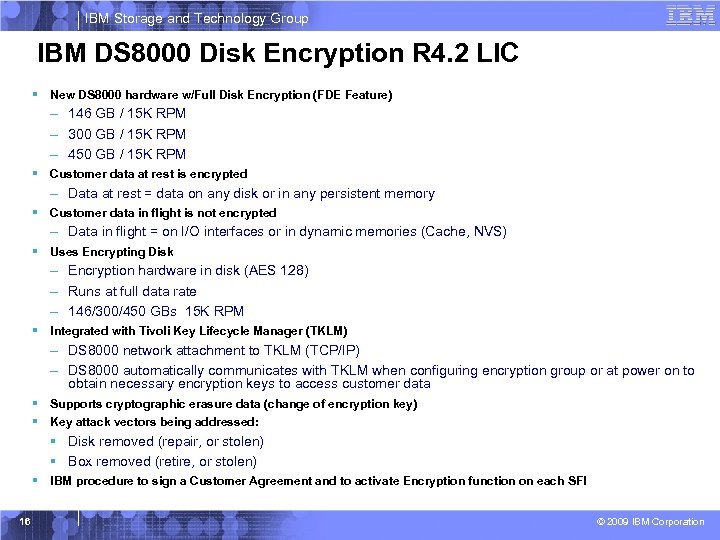
IBM Storage and Technology Group IBM DS 8000 Disk Encryption R 4. 2 LIC § New DS 8000 hardware w/Full Disk Encryption (FDE Feature) – 146 GB / 15 K RPM – 300 GB / 15 K RPM – 450 GB / 15 K RPM § Customer data at rest is encrypted – Data at rest = data on any disk or in any persistent memory § Customer data in flight is not encrypted – Data in flight = on I/O interfaces or in dynamic memories (Cache, NVS) § Uses Encrypting Disk – Encryption hardware in disk (AES 128) – Runs at full data rate – 146/300/450 GBs 15 K RPM § Integrated with Tivoli Key Lifecycle Manager (TKLM) – DS 8000 network attachment to TKLM (TCP/IP) – DS 8000 automatically communicates with TKLM when configuring encryption group or at power on to obtain necessary encryption keys to access customer data § Supports cryptographic erasure data (change of encryption key) § Key attack vectors being addressed: § Disk removed (repair, or stolen) § Box removed (retire, or stolen) § IBM procedure to sign a Customer Agreement and to activate Encryption function on each SFI 16 © 2009 IBM Corporation
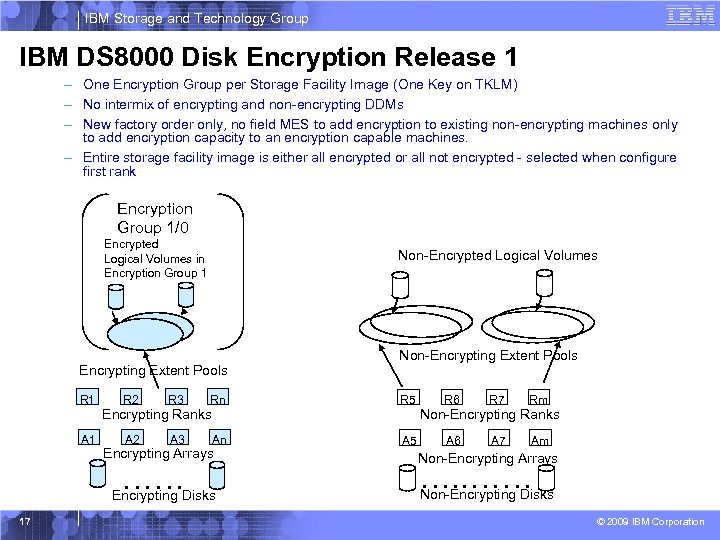
IBM Storage and Technology Group IBM DS 8000 Disk Encryption Release 1 – One Encryption Group per Storage Facility Image (One Key on TKLM) – No intermix of encrypting and non-encrypting DDMs – New factory order only, no field MES to add encryption to existing non-encrypting machines only to add encryption capacity to an encryption capable machines. – Entire storage facility image is either all encrypted or all not encrypted - selected when configure first rank Encryption Group 1/0 Encrypted Logical Volumes in Encryption Group 1 Non-Encrypted Logical Volumes Encrypting Extent Pools R 1 A 1 R 2 R 3 Rn R 5 A 2 A 3 An A 5 Encrypting Ranks Encrypting Arrays …… Encrypting Disks 17 Non-Encrypting Extent Pools R 6 R 7 Rm A 6 A 7 Am Non-Encrypting Ranks Non-Encrypting Arrays …. . …… Non-Encrypting Disks © 2009 IBM Corporation
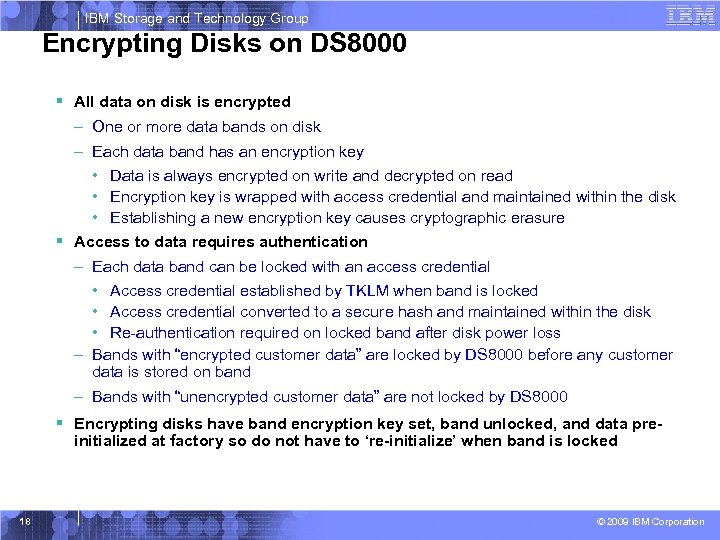
IBM Storage and Technology Group Encrypting Disks on DS 8000 § All data on disk is encrypted – One or more data bands on disk – Each data band has an encryption key • Data is always encrypted on write and decrypted on read • Encryption key is wrapped with access credential and maintained within the disk • Establishing a new encryption key causes cryptographic erasure § Access to data requires authentication – Each data band can be locked with an access credential • Access credential established by TKLM when band is locked • Access credential converted to a secure hash and maintained within the disk • Re-authentication required on locked band after disk power loss – Bands with “encrypted customer data” are locked by DS 8000 before any customer data is stored on band – Bands with “unencrypted customer data” are not locked by DS 8000 § Encrypting disks have band encryption key set, band unlocked, and data preinitialized at factory so do not have to ‘re-initialize’ when band is locked 18 © 2009 IBM Corporation
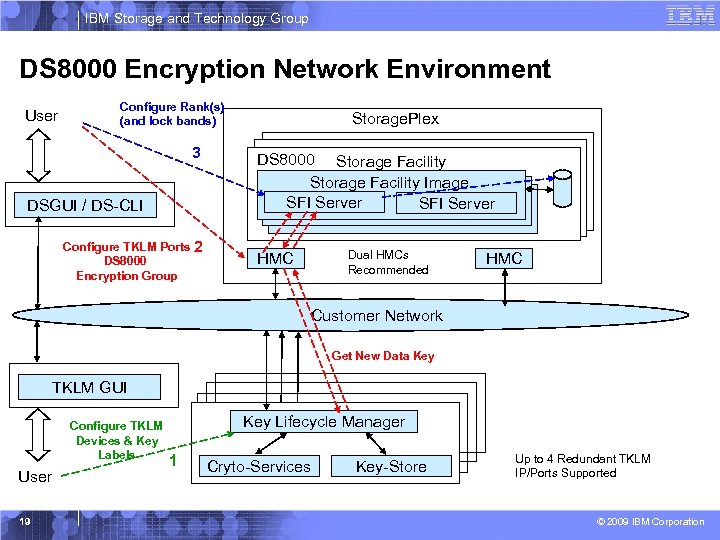
IBM Storage and Technology Group DS 8000 Encryption Network Environment User Configure Rank(s) (and lock bands) 3 DSGUI / DS-CLI Configure TKLM Ports DS 8000 Encryption Group 2 Storage. Plex DS 8000 Storage Facility Image SFI Server Storage. Plex SFI Server Dual HMCs Recommended HMC Customer Network Get New Data Key TKLM GUI Configure TKLM Devices & Key Labels User 19 Key Lifecycle Manager 1 Cryto-Services Key-Store Up to 4 Redundant TKLM IP/Ports Supported © 2009 IBM Corporation
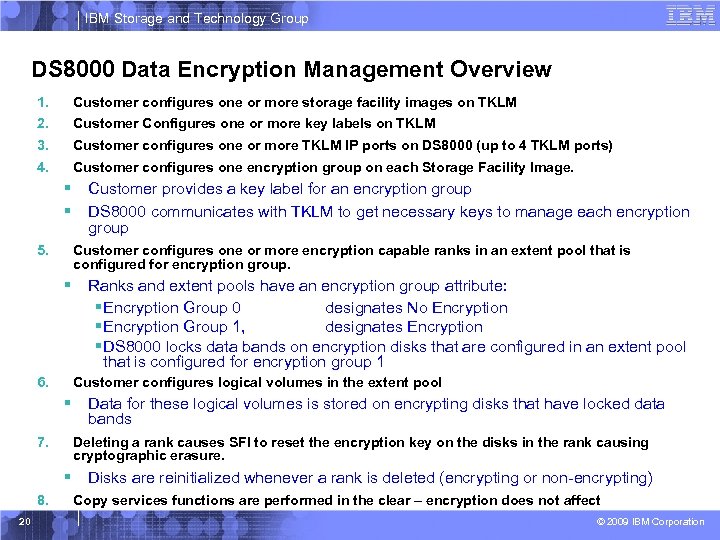
IBM Storage and Technology Group DS 8000 Data Encryption Management Overview 1. Customer configures one or more storage facility images on TKLM 2. Customer Configures one or more key labels on TKLM 3. Customer configures one or more TKLM IP ports on DS 8000 (up to 4 TKLM ports) 4. Customer configures one encryption group on each Storage Facility Image. § § 5. Customer configures one or more encryption capable ranks in an extent pool that is configured for encryption group. § 6. 7. Data for these logical volumes is stored on encrypting disks that have locked data bands Deleting a rank causes SFI to reset the encryption key on the disks in the rank causing cryptographic erasure. § 20 Ranks and extent pools have an encryption group attribute: § Encryption Group 0 designates No Encryption § Encryption Group 1, designates Encryption § DS 8000 locks data bands on encryption disks that are configured in an extent pool that is configured for encryption group 1 Customer configures logical volumes in the extent pool § 8. Customer provides a key label for an encryption group DS 8000 communicates with TKLM to get necessary keys to manage each encryption group Disks are reinitialized whenever a rank is deleted (encrypting or non-encrypting) Copy services functions are performed in the clear – encryption does not affect © 2009 IBM Corporation
IBM Storage and Technology Group IBM Tivoli Key Lifecycle Manager (TKLM) § The TKLM works with IBM encryption-enabled storage components in generating, protecting, storing and maintaining encryption keys that are used to encrypt information being written to and decrypt information being read from storage media. § TKLM executes in the IBM Java run time environment and it uses IBM Java security components for the cryptographic capabilities used. § Supported Operating Systems – AIX 5. 3 and 6. 1 - 64 bit – Red Hat AS 4. 0 x 86 - 32 bit – Suse Linux 9. 0 and 10 x 86 - 32 bit – Solaris 10 Sparc - 64 bit – Windows Server 2003 - 32 bit – z/OS V 1 R 9 (TKLM hosted in the System Services Runtime Environment for z/OS) § Designed to be Easy to use § § Easy backup and restore of TKLM files – § Provide a Graphical User Interface § Initial configuration wizards One button, single jar file Lifecycle functions Notification of certificate expiry – Automated rotation of groups of keys – § Same TKLM can be used with IBM DS 8000 and IBM Tape 21 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 Data Encryption Release 1 Summary § Requires DS 8000 R 4. 2 LIC and TKLM – Initial release requires all disks encryption capable – Enterprise Class Disk Features Supported § Entire Storage Facility is ‘encryption-capable’ or not ‘encryption capable’. § Each Storage Facility Image on encryption-capable Storage Facility can be independently enabled or disabled for encryption. § TKLM unwraps single key stored on DS 8000 to unlock the entire Storage Facility Image. – DS 8000 MUST be connected to at least 2 TKLM Servers. – One of the two TKLM servers must be dedicated/isolated. § Designed to address situations where single disks are removed for repair, and where the entire Storage Facility Image is discontinued or re-purposed 22 © 2009 IBM Corporation

IBM Storage and Technology Group Innovation that matters Remote Pair Flash. Copy Hank Sautter sautter@us. ibm. com © 2009 IBM Corporation
IBM Storage and Technology Group Agenda § Remote Pair Flash Copy –Features and Requirements –How it Works • Establish • Withdraw • Options –Flash. Copy Query 24 © 2009 IBM Corporation
IBM Storage and Technology Group IBM Remote Pair Flash. Copy Features and Requirements 25 © 2009 IBM Corporation

IBM Storage and Technology Group IBM Remote Pair Flash. Copy - Features § Improved Flash. Copy function for Metro Mirror Volumes – Useful for full volume Flash. Copy (FB & CKD) – Dataset Flash. Copy for z/OS § Preserves full duplex – Hyperswap enabled state preserved for z/OS § No additional link bandwidth needed – Flash. Copy commands are sent to the remote site -not the data 26 © 2009 IBM Corporation
IBM Storage and Technology Group IBM Remote Pair Flash. Copy – Features (cont) § Software support – TSO FCESTABL – ANTRQST FCESTABLISH – ICKDSF FLASHCPY ESTABLISH – DSS COPY, CONSOLIDATE, DEFRAG, Virtual Concurrent Copy – HSM FRBACKUP, FRRECOV – ISMF panels for DSS and ICKDSF – DS 8000 DSCLI 27 © 2009 IBM Corporation

IBM Storage and Technology Group IBM Remote Pair Flash. Copy - Requirements § Remote pairs must be in Full Duplex state – Source and Target are Metro Mirror Pairs § Secondary of FLC source and target are in the same subsystem – For best performance they should be in the same cluster as well § Local or remote targets may not be Space Efficient volumes § No cascading configurations MGM / MGC (target volumes) 28 © 2009 IBM Corporation
IBM Storage and Technology Group IBM Remote Pair Flash. Copy How it Works 29 © 2009 IBM Corporation
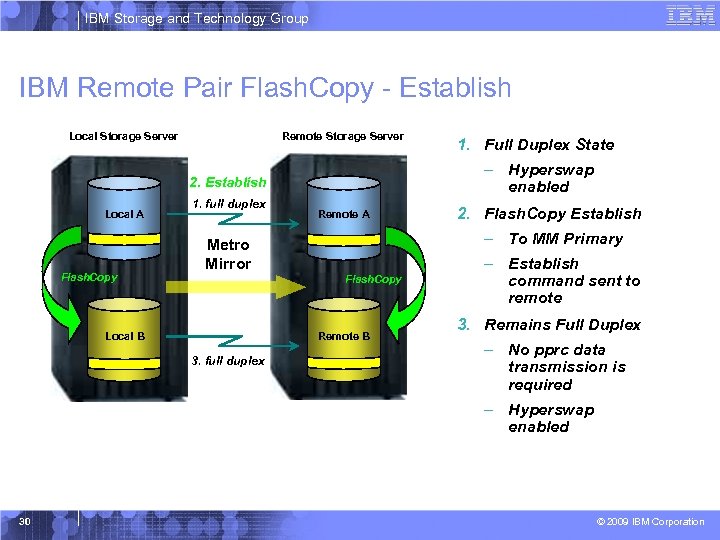
IBM Storage and Technology Group IBM Remote Pair Flash. Copy - Establish Local Storage Server Remote Storage Server – Hyperswap enabled 2. Establish Local A Flash. Copy 1. full duplex Remote A Flash. Copy Remote B 3. full duplex 2. Flash. Copy Establish – To MM Primary Metro Mirror Local B 1. Full Duplex State – Establish command sent to remote 3. Remains Full Duplex – No pprc data transmission is required – Hyperswap enabled 30 © 2009 IBM Corporation
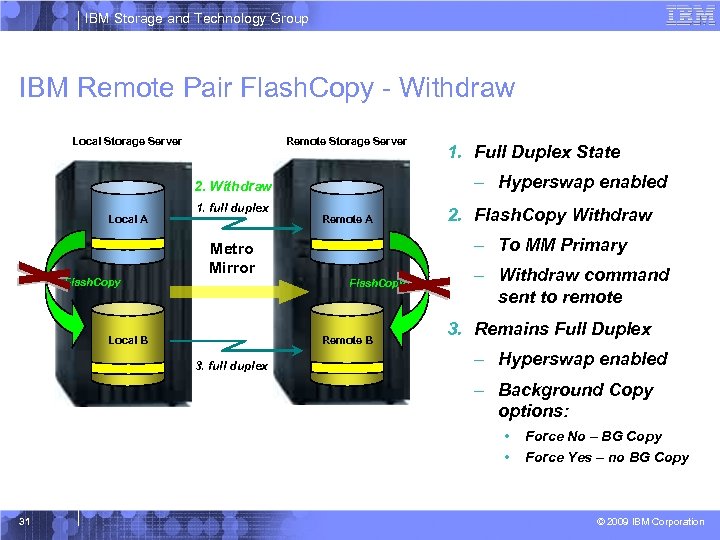
IBM Storage and Technology Group IBM Remote Pair Flash. Copy - Withdraw Local Storage Server Remote Storage Server – Hyperswap enabled 2. Withdraw Local A Flash. Copy 1. full duplex Remote A Flash. Copy Remote B 3. full duplex 2. Flash. Copy Withdraw – To MM Primary Metro Mirror Local B 1. Full Duplex State – Withdraw command sent to remote 3. Remains Full Duplex – Hyperswap enabled – Background Copy options: • • 31 Force No – BG Copy Force Yes – no BG Copy © 2009 IBM Corporation

IBM Storage and Technology Group IBM Remote Pair Flash. Copy - options § Flash. Copy Remote Pair Establish Options – None – Use “old way” (primary goes duplex pending, and transfers all target tracks) – Preferred – Use Remote Pair Flash. Copy if possible, otherwise use the “old way” – Required – Fail FLC establish if it does not meet the requirements for Remote pair Flash. Copy (do not cause the FLC target to become duplex pending). § Flash. Copy Remote Pair Withdraw Options – ICKDSF – Force Default is initiate Background copy on withdraw – TSO / DSS / ANTRQST– Force is the default – DSCLI -cprm no other option Background copy initiated (Default fail withdraw) § PPRC Query Changes – PPRC Query shows force withdraw option was initiated – New status codes – Suspend reason -- if establish Flash. Copy at remote fails 32 © 2009 IBM Corporation
IBM Storage and Technology Group IBM Remote Pair Flash. Copy Query 33 © 2009 IBM Corporation
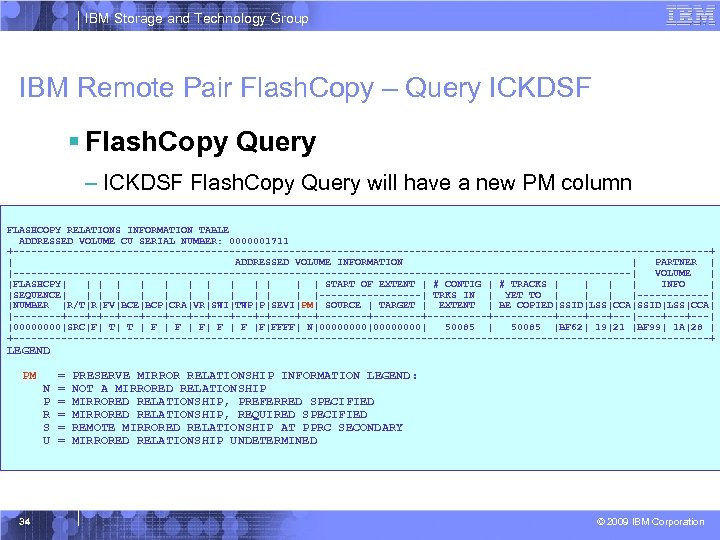
IBM Storage and Technology Group IBM Remote Pair Flash. Copy – Query ICKDSF § Flash. Copy Query – ICKDSF Flash. Copy Query will have a new PM column FLASHCOPY RELATIONS INFORMATION TABLE ADDRESSED VOLUME CU SERIAL NUMBER: 0000001711 +----------------------------------------------------------+ | ADDRESSED VOLUME INFORMATION | PARTNER | |----------------------------------------------------| VOLUME | |FLASHCPY| | | | START OF EXTENT | # CONTIG | # TRACKS | | INFO | |SEQUENCE| | | |---------| TRKS IN | YET TO | |------| |NUMBER |R/T|R|FV|BCE|BCP|CRA|VR|SWI|TWP|P|SEVI|PM| SOURCE | TARGET | EXTENT | BE COPIED|SSID|LSS|CCA| |----+---+-+--+---+--+---+-+----+--+--------+----------+---+---|----+---| |0000|SRC|F| T| T | F | F| F |F|FFFF| N|00000000| 50085 |BF 62| 19|21 |BF 99| 1 A|28 | +----------------------------------------------------------+ LEGEND PM 34 N P R S U = = = PRESERVE MIRROR RELATIONSHIP INFORMATION LEGEND: NOT A MIRRORED RELATIONSHIP, PREFERRED SPECIFIED MIRRORED RELATIONSHIP, REQUIRED SPECIFIED REMOTE MIRRORED RELATIONSHIP AT PPRC SECONDARY MIRRORED RELATIONSHIP UNDETERMINED © 2009 IBM Corporation
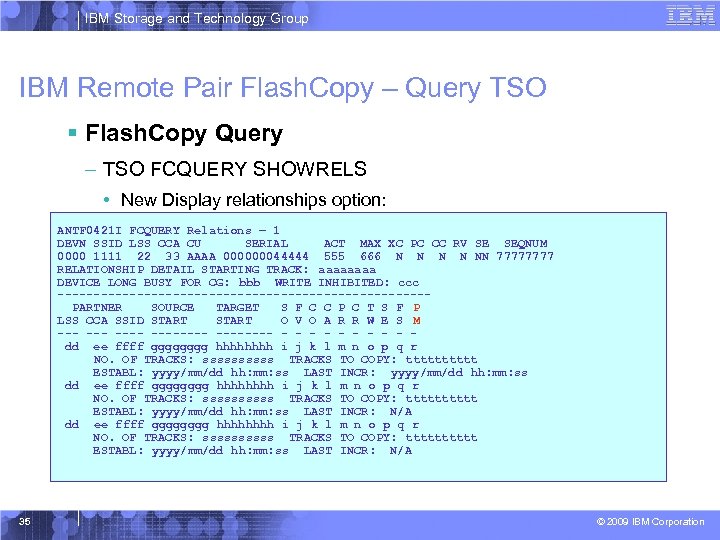
IBM Storage and Technology Group IBM Remote Pair Flash. Copy – Query TSO § Flash. Copy Query – TSO FCQUERY SHOWRELS • New Display relationships option: ANTF 0421 I FCQUERY Relations – 1 DEVN SSID LSS CCA CU SERIAL ACT MAX XC PC CC RV SE SEQNUM 0000 1111 22 33 AAAA 000000044444 555 666 N N NN 7777 RELATIONSHIP DETAIL STARTING TRACK: aaaa DEVICE LONG BUSY FOR CG: bbb WRITE INHIBITED: ccc --------------------------PARTNER SOURCE TARGET S F C C P C T S F P LSS CCA SSID START O V O A R R W E S M --- -------- - - - - - dd ee ffff gggg hhhh i j k l m n o p q r NO. OF TRACKS: sssss TRACKS TO COPY: ttttt ESTABL: yyyy/mm/dd hh: mm: ss LAST INCR: yyyy/mm/dd hh: mm: ss dd ee ffff gggggggg hhhhhhhh i j k l m n o p q r NO. OF TRACKS: ssssssssss TRACKS TO COPY: tttttttttt ESTABL: yyyy/mm/dd hh: mm: ss LAST INCR: N/A 35 © 2009 IBM Corporation

IBM Storage and Technology Group Innovation that matters DS 8000 Solid State Drives Charlie Burger cwburger@us. ibm. com © 2009 IBM Corporation
IBM Storage and Technology Group Agenda § IBM DS 8000 Solid State Drive (SSD) –What are Solid State Drives? –Solid State Drive Considerations –SSD Reliability, Power, Heat –SSD Endurance –SSD Recommended Use –SSD Performance –SSD Awareness –Integrated Tooling –Addendum 37 © 2009 IBM Corporation
IBM Storage and Technology Group What are Solid State Drives? § Not Magnetic § Not Optical § Semiconductor (NAND flash) – Electronically erasable medium – Random access – No mechanical read/write interface (arm/head) – No rotating parts § Packaged with interface just like HDD and function just like HDD 38 © 2009 IBM Corporation
IBM Storage and Technology Group Solid State Drive Considerations § DDM Install Groups – 73 GB – 16 drives – 146 GB – 16 drives § Max 128 SSD per DA – Use 16 SSDs per DA for performance – Max of 256 drives including SSD for Model 931 • Max number of drives possible not recommended for performance for 931 – Max of 512 drives including SSD for Models 932 and 9 B 2 • Consider performance accelerator feature • Max number of drives possible not recommended for performance for either 932 and 9 B 2 § DS 8000 systems with SSD drives installed will have no 3 rd or 4 th expansion frames § RAID-5 only – FB or CKD § Factory only for this release § RPQ to review configuration 39 © 2009 IBM Corporation
IBM Storage and Technology Group SSD Reliability, Power, Heat § Absence of mechanical moving parts – Significantly more reliable • Used in military applications • Used in extreme temperatures (hot/cold) § Green – Power • Fraction of power consumed – Heat • Fraction of heat dissipated 40 © 2009 IBM Corporation

IBM Storage and Technology Group SSD Endurance § Flash program/erase cycles are cumulatively destructive § Current commercial NAND flash varieties – Single level cell (SLC) 105 writes/cell (our SSD is SLC) – Multi level cell (MLC) [ 104 writes/cell (Cameras, i. Pods, etc. ) § Coping strategies – Wear leveling, over-provisioning, bad block management, ECC, compression, write elimination, … § Data stored remain valid for 10 yr without power 41 © 2009 IBM Corporation
IBM Storage and Technology Group SSD Recommended Use § Best suited for cache-unfriendly data – Random read access, high performance data sets • Both FB and CKD environments 42 © 2009 IBM Corporation

IBM Storage and Technology Group SSD Performance § DS 8 K HDD RAID-5 (8 x 15 K 300 GB) – Throughput: 399 MB/s (R), 335 MB/s (W) – IOPS: 1. 9 K (R), 0. 5 K (W) § DS 8 K SSD RAID-5 (8 x 73 GB) – Throughput: 400 MB/s (R), 365 MB/s (W) – IOPS: 21. 3 K (R), 5. 8 K (W) Note the performance improvement for IOPs on SSD! 43 © 2009 IBM Corporation
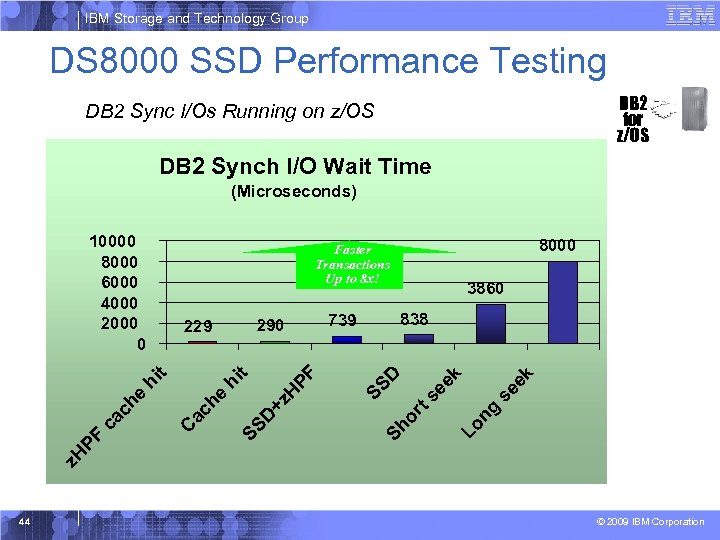
IBM Storage and Technology Group DS 8000 SSD Performance Testing DB 2 for z/OS DB 2 Sync I/Os Running on z/OS DB 2 Synch I/O Wait Time (Microseconds) k se e ng Lo or ts ee k D Sh +z H D 838 739 SS t SS C ac he hi hi e ca ch PF 290 229 3860 z. H PF 8000 Faster Transactions Up to 8 x! t 10000 8000 6000 4000 2000 0 44 © 2009 IBM Corporation

IBM Storage and Technology Group SSD Awareness § SMS volume selection will recognize volumes backed by SSD – Policies implemented by ACS routines can direct allocations to SSD • Consider using a Storage Group with only SSD § New fields for SMF type 42 subtype 5 and 6 records • Average read disconnect time per data set • Total number of read operations to the data set § DEVSERV QDASD – Displays device attributes with new ATTR keyword ds qd, d 300, attr IEE 459 I 16. 59. 01 DEVSERV QDASD 613 C UNIT VOLSER SCUTYPE DEVTYPE CYL SSID SCU-SERIAL DEV-SERIAL EFC ATTRIBUTE/FEATURE YES/NO D 300 TK 9085 2107921 2107900 65520 2401 0175 -02411 *OK SOLID STATE DRIVES Y ENCRYPTION N § DEVTYPE macro – With INFO=DASD, indicates if a volume is backed by solid state drives 45 © 2009 IBM Corporation
IBM Storage and Technology Group Integrated Tooling § DB 2 Online Reorg – Allows non-disruptive migration of data to SSD technology § Omegamon XE – Will identify datasets and volumes that will benefit from migration to SSD – Integrate new instrumentation for Read-Only DISC time – Cache Statistics § Soft. Tek Data Mobility Console – Analyze SMF data in real time – Seamless integration into data migration tools • TDMF • LDMF 46 © 2009 IBM Corporation

IBM Storage and Technology Group 1 TB SATA Drive Paul Spagnolo pgspagn@us. ibm. com © 2009 IBM Corporation 47
IBM Storage and Technology Group 1 TB SATA 7200 RPM Drive Support § New 1 TB SATA drives will become available on March 6, 2009 § Enabled through new feature code specifications in megapack (16) drive increments (see following chart for list of feature codes) § Scales DS 8000 to 1, 024 TB physical capacity when fully populated with all 1 TB SATA drives (5 frames) § All models of the DS 8000 family are supported (2107, 2421, 2422, 2423 and 2424) 48 © 2009 IBM Corporation
IBM Storage and Technology Group When to Consider SATA § Tier-1 Storage – When looking for low cost per gigabyte with lower expectations of performance – Streaming applications where transfer rate is more important than seek times – Applications with low IOPS performance requirements § Tier-2 Storage – Disk based near-line storage between disk and tape – Disaster recovery target for remote replication – Fixed content / Managed Retention data – Temporary work space for short-term processing – Consolidation of tier-2 subsystems 49 © 2009 IBM Corporation
IBM Storage and Technology Group New Feature Codes § FC #2816 – 1 TB 7200 RPM SATA drive set § FC #2817 – 1 TB 7200 RPM SATA standby COD drive set § FC #2826 – 1 TB 7200 RPM SATA LPAR A drive set § FC #2836 – 1 TB 7200 RPM SATA LPAR B drive set § FC #2827 – 1 TB 7200 RPM SATA LPAR A standby COD drive set § FC #2837 – 1 TB 7200 RPM SATA LPAR B standby COD drive set § Available for both factory (new builds) and field upgrades (MES) at GA 50 © 2009 IBM Corporation
IBM Storage and Technology Group SATA Drive Requirements and Limitations § 1 TB SATA drives will require at a minimum licensed machine code (LMC) level 5. 4. 2 xx. xxx (bundle version 64. 2. xx) § Only RAID-6 or RAID-10 will support the SATA drives – No RAID-5 support at GA – RPQs for RAID-5 support must be submitted through normal channels – RAID-6 requires DA-2 device adapters § Not intended for Space Efficient Flash. Copy repository because of the lower performance and reliability characteristics § A SATA drive will not be used as a spare for FC or FATA drives – Performance of the entire array would be degraded 51 © 2009 IBM Corporation
IBM Storage and Technology Group SATA Design Architecture § SATA architecture uses a 512 byte physical sector size § DS 8000 device adapters require 524 bytes sector size § SATA uses a different protocol compared to fibre channel § IBM elected to utilize a bridge card • Translates fibre channel protocol to SATA protocol and vice versa • Bridge card is an Emulex BRG 436 -I • Connects to Hitachi Gemini-K 1 TB SATA drive • Requires padding to align blocks to sector size • Each SATA drive has its own dedicated bridge card 52 © 2009 IBM Corporation
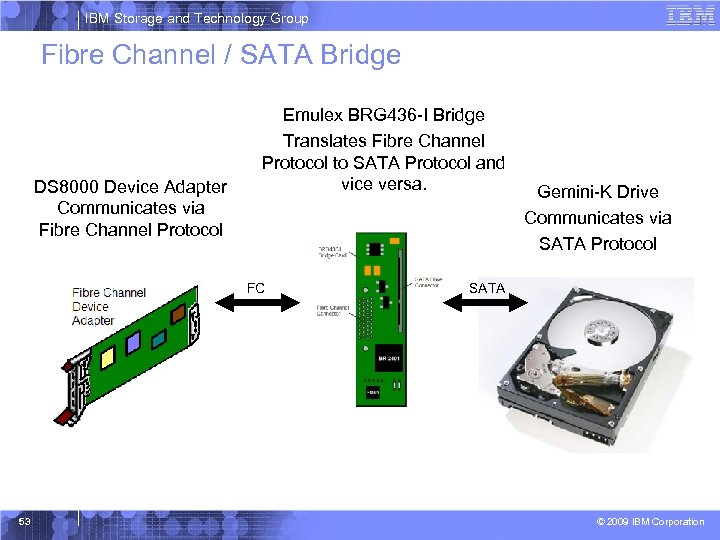
IBM Storage and Technology Group Fibre Channel / SATA Bridge DS 8000 Device Adapter Communicates via Fibre Channel Protocol Emulex BRG 436 -I Bridge Translates Fibre Channel Protocol to SATA Protocol and vice versa. FC 53 Gemini-K Drive Communicates via SATA Protocol SATA © 2009 IBM Corporation
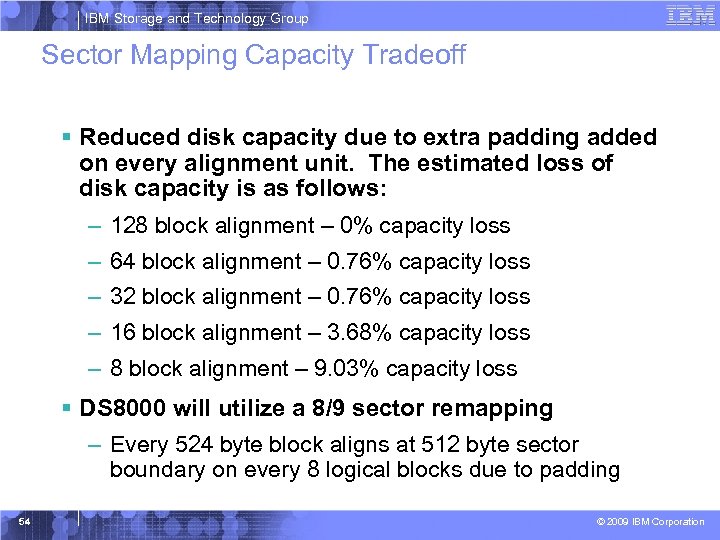
IBM Storage and Technology Group Sector Mapping Capacity Tradeoff § Reduced disk capacity due to extra padding added on every alignment unit. The estimated loss of disk capacity is as follows: – 128 block alignment – 0% capacity loss – 64 block alignment – 0. 76% capacity loss – 32 block alignment – 0. 76% capacity loss – 16 block alignment – 3. 68% capacity loss – 8 block alignment – 9. 03% capacity loss § DS 8000 will utilize a 8/9 sector remapping – Every 524 byte block aligns at 512 byte sector boundary on every 8 logical blocks due to padding 54 © 2009 IBM Corporation
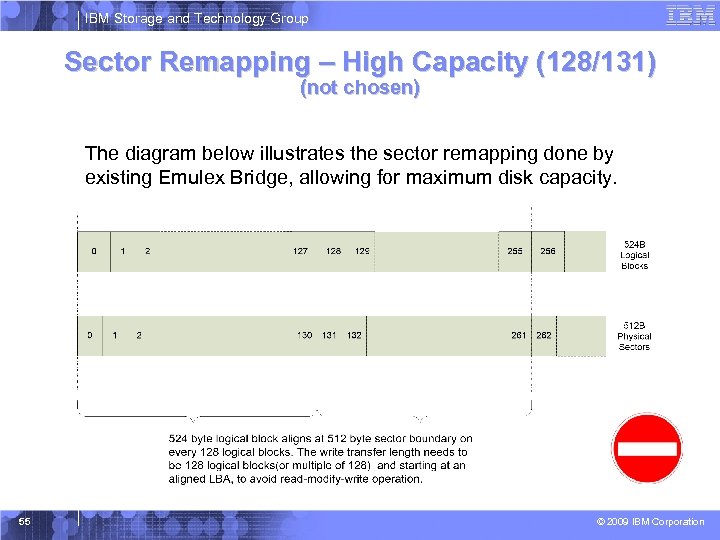
IBM Storage and Technology Group Sector Remapping – High Capacity (128/131) (not chosen) The diagram below illustrates the sector remapping done by existing Emulex Bridge, allowing for maximum disk capacity. 55 © 2009 IBM Corporation
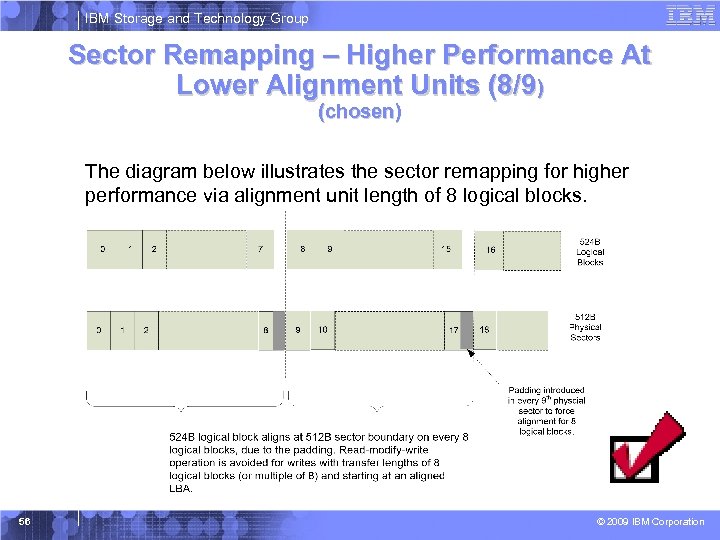
IBM Storage and Technology Group Sector Remapping – Higher Performance At Lower Alignment Units (8/9) (chosen) The diagram below illustrates the sector remapping for higher performance via alignment unit length of 8 logical blocks. 56 © 2009 IBM Corporation
IBM Storage and Technology Group Sector Remapping § Higher performance (8/9) remapping was chosen over higher capacity (128/131). § Results in significantly higher write performance § However 1 TB SATA drives will have about 900 GB of usable capacity § Formatted arrays are quite large 57 © 2009 IBM Corporation
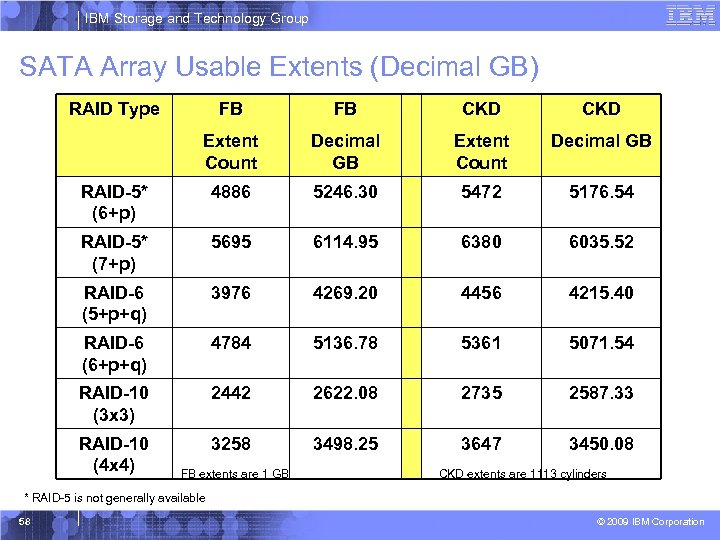
IBM Storage and Technology Group SATA Array Usable Extents (Decimal GB) RAID Type FB FB CKD Extent Count Decimal GB RAID-5* (6+p) 4886 5246. 30 5472 5176. 54 RAID-5* (7+p) 5695 6114. 95 6380 6035. 52 RAID-6 (5+p+q) 3976 4269. 20 4456 4215. 40 RAID-6 (6+p+q) 4784 5136. 78 5361 5071. 54 RAID-10 (3 x 3) 2442 2622. 08 2735 2587. 33 RAID-10 (4 x 4) 3258 3498. 25 3647 3450. 08 FB extents are 1 GB CKD extents are 1113 cylinders * RAID-5 is not generally available 58 © 2009 IBM Corporation
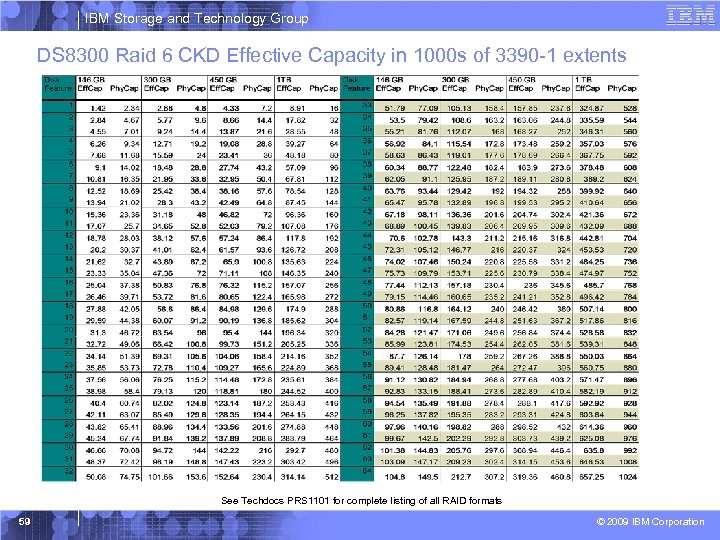
IBM Storage and Technology Group DS 8300 Raid 6 CKD Effective Capacity in 1000 s of 3390 -1 extents See Techdocs PRS 1101 for complete listing of all RAID formats 59 © 2009 IBM Corporation
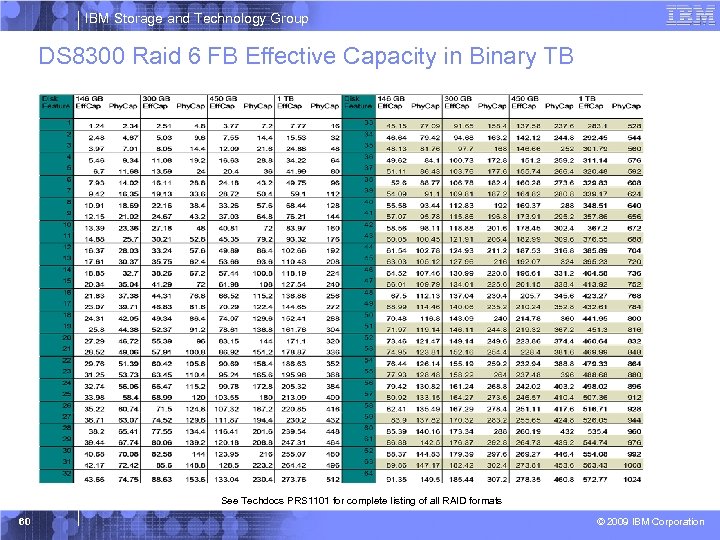
IBM Storage and Technology Group DS 8300 Raid 6 FB Effective Capacity in Binary TB See Techdocs PRS 1101 for complete listing of all RAID formats 60 © 2009 IBM Corporation
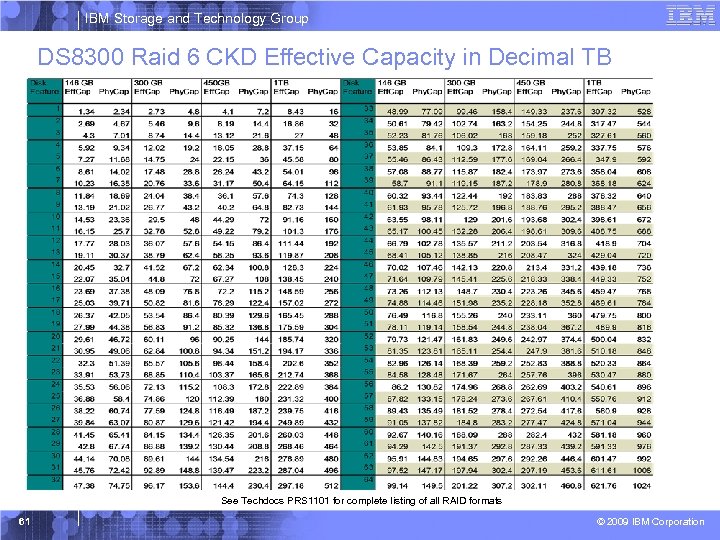
IBM Storage and Technology Group DS 8300 Raid 6 CKD Effective Capacity in Decimal TB See Techdocs PRS 1101 for complete listing of all RAID formats 61 © 2009 IBM Corporation
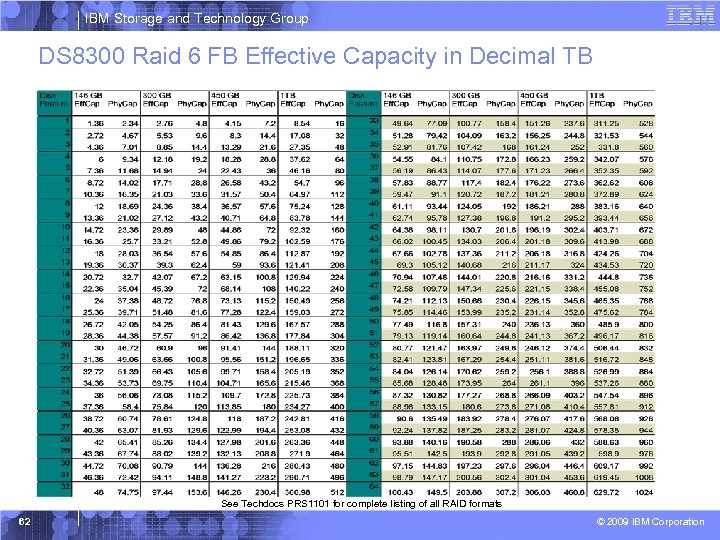
IBM Storage and Technology Group DS 8300 Raid 6 FB Effective Capacity in Decimal TB See Techdocs PRS 1101 for complete listing of all RAID formats 62 © 2009 IBM Corporation
IBM Storage and Technology Group Intermix of 1 TB SATA Drives § The same rules governing intermix of Fibre Channel and FATA drives apply to SATA drives § Intermix of Fibre Channel, FATA or SATA drives on the same DA pair is allowed. § 1 TB SATA drive can not be used as a spare in the event of a failure of FC or FATA drive § If a spare occurs, the rank will take on the attributes of the slowest drive in the rank (no change in how this operates) § Neither Fibre Channel nor FATA drive can serve as a spare for the 1 TB SATA drives due to their smaller size 63 © 2009 IBM Corporation

IBM Storage and Technology Group GUI/CLI Changes 64 © 2009 IBM Corporation
IBM Storage and Technology Group Major GUI Changes § Encryption – Manage encryption key servers – Manage encryption groups (extent pools) § Complete revision to create and maintain volumes – Create multiple LCUs, LSSs and volumes (several new wizards) – New preview panel to review before create process – Improvements for large table scrolling – Performance improvements – New open systems explorer to see relationships between servers and volumes § Support for LDAP functionality § DSCLI – Update to support new R 4. 2 functions – Installer changes from Install. Shield to Install. Anywhere – New platform OS support – Additional performance statistics with showioport -metrics 65 © 2009 IBM Corporation

IBM Storage and Technology Group Innovation that matters IBM Americas ATS DS 8000 R 4. 2 LDAP Overview Brian Sherman Americas Storage ATS bsherman@ca. ibm. com © 2009 IBM Corporation
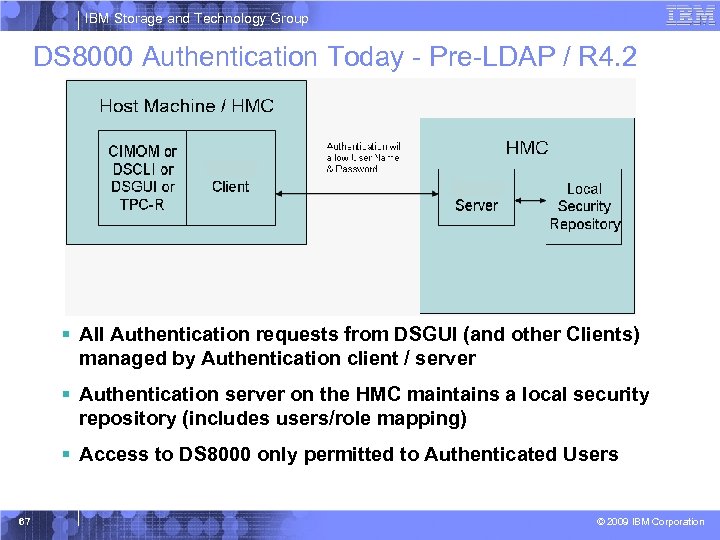
IBM Storage and Technology Group DS 8000 Authentication Today - Pre-LDAP / R 4. 2 § All Authentication requests from DSGUI (and other Clients) managed by Authentication client / server § Authentication server on the HMC maintains a local security repository (includes users/role mapping) § Access to DS 8000 only permitted to Authenticated Users 67 © 2009 IBM Corporation
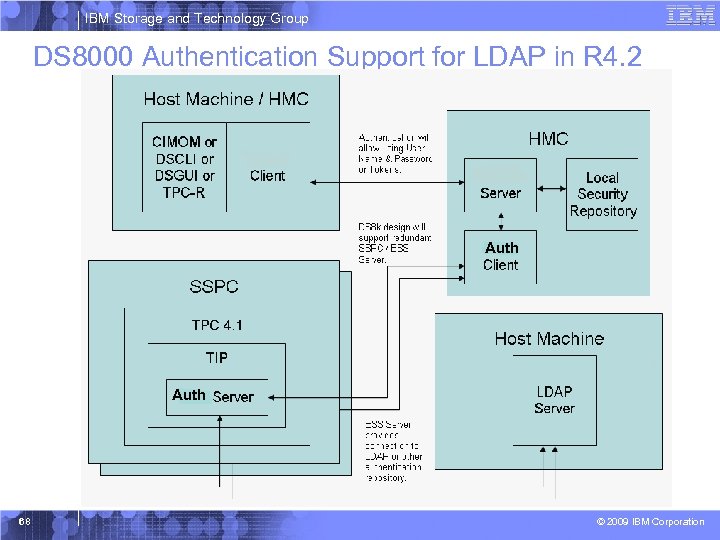
IBM Storage and Technology Group DS 8000 Authentication Support for LDAP in R 4. 2 Auth 68 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 Release 4. 2 Authentication § Authentication Policy: – Defines the criteria / mechanism used to perform authentication – Multiple authentication policies can be defined – Only one active authentication policy § Authentication Policy types: – Basic Authentication policy • Same as Pre R 4. 2 (Authorized users assigned to pre-defined DS 8000 User Groups) • Also commonly called Default or Local policy – Storage Authentication Service (a. k. a. SAS) policy • This is the policy type for LDAP. Need to map External users and/or user groups to DS 8000 User groups in the policy definition 69 © 2009 IBM Corporation

IBM Storage and Technology Group Steps for LDAP Implementation § TPC / SSPC Steps – Configure Access to LDAP Repository – Extract certificate – Create a truststore § DS 8000 Steps – Create an SAS Authentication policy with information collected from TPC and LDAP Server – Test the SAS policy using a valid LDAP user mapped to a DS 8000 User role in the policy – Activate the SAS policy using a valid LDAP user mapped to the DS 8000 Administrative User role in the policy 70 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 LDAP Recommendations § Recommendations – If using SAS authentication, use multiple SSPCs / instances of TPC 4. 1 and LDAP • If only using a single instance and it goes down, customers cannot logon to DS 8000 – Must fix SSPC/TPC 4. 1, or Call IBM Service to reset authentication back to Basic – If using SAS authentication, map groups not users • Users can be added/removed without changing any policies – Do not modify the active policy • Copy the active policy, make changes to it, test it, then activate it – Maintain consistency of policies on multiple DS 8000 s • • Can use GUI to copy one policy to multiple DS 8000 s Can create the same copy on multiple DS 8000 s at the same time DSCLI only copies policies to same DS 8000 Can use scripts to make same change with the DSCLI on multiple DS 8000 s – dscli –hmc 1 ds 8 k_A … chauthpol –activate … my. Policy – dscli –hmc 1 ds 8 k_B … chauthpol –activate … my. Policy – dscli –hmc 1 ds 8 k_C … chauthpol –activate … my. Policy 71 © 2009 IBM Corporation
IBM Storage and Technology Group DS 8000 LDAP Support Requirements § DS 8000 with R 4. 2 LIC – Includes DSCLI and GUI support § TPC 4. 1 – SSPC future release will include TPC 4. 1 – Any or other supported TPC server • http: //www 01. ibm. com/support/docview. wss? rs=1133&uid=ssg 1 S 1003119 – Preview announce on 02/09 • planned announcement 04/07 with GA 04/10 § Planned Supported LDAP Servers – IBM Directory Server – MS Active Directory – Sun One 72 © 2009 IBM Corporation

IBM Storage and Technology Group Backup Material © 2009 IBM Corporation
IBM Storage and Technology Group IBM Remote Pair Flash. Copy Addendum 74 © 2009 IBM Corporation
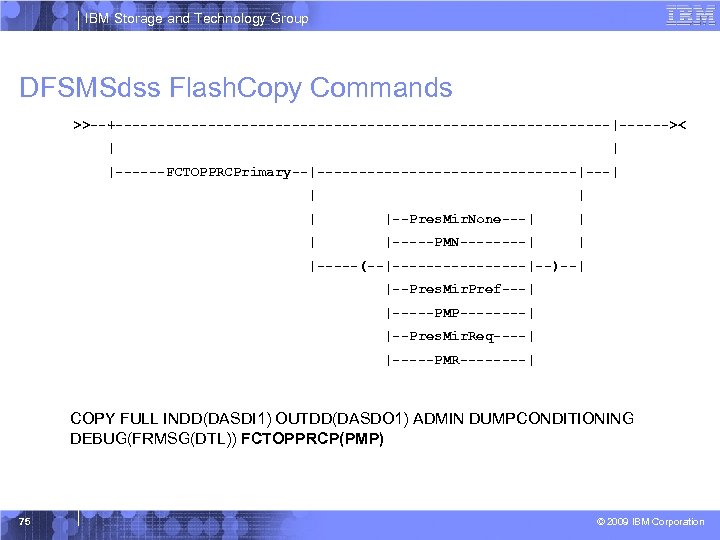
IBM Storage and Technology Group DFSMSdss Flash. Copy Commands >>--+------------------------------|------>< | | |------FCTOPPRCPrimary--|----------------|---| | |--Pres. Mir. None---| | | |-----PMN----| | |-----(--|--------|--)--| |--Pres. Mir. Pref---| |-----PMP----| |--Pres. Mir. Req----| |-----PMR----| COPY FULL INDD(DASDI 1) OUTDD(DASDO 1) ADMIN DUMPCONDITIONING DEBUG(FRMSG(DTL)) FCTOPPRCP(PMP) 75 © 2009 IBM Corporation
IBM Storage and Technology Group DFSMSdss ADRUFO Parameter List ADRUFO parameter list is used in the interface between DFSMSdss and the installation-wide options exit routine (ADRUIXIT), and between DFSMSdss and the user interaction module (UIM). New bits will be defined in the ADRUFO mapping macro for the new FCTOPPRCPRIMARY(PRESMIRREQ|PRESMIRPREF|PRESMIRNONE) keyword: 1. Define new fields, UFO 8 FLGS, at offset 33 (X’ 21’) in the UFOFUNCT mapping. 2. Define the UFOPMREQ bit in UFO 8 FLGS flags for the new FCTOPPRCPRIMARY(PRESMIRREQ) option. 3. Define the UFOPMPRE bit in UFO 8 FLGS flags for the new FCTOPPRCPRIMARY(PRESMIRPREF) option. 4. Define the UFOPMNON bit in UFO 8 FLGS flags for the new FCTOPPRCPRIMARY(PRESMIRNONE) option. 76 © 2009 IBM Corporation
IBM Storage and Technology Group DFSMSdss Virtual Concurrent Copy (VCC) ALLOWPPRCONWSDS(YES|NO|PMREQ|PMPREF) In z/OS 1. 10 Virtual Concurrent Copy using Flash. Copy function was added. As part of this function, the ability to use a working space dataset (WSDS) allocated on a PPRC primary device was enabled using a value in the ANTMIN 00 member of PARMLIB. In order to allow the Flash. Copy function within VCC to use a WSDS allocated on a PPRC primary device, ALLOWPPRCONWSDS(YES) must be specified. 77 © 2009 IBM Corporation
IBM Storage and Technology Group ICKDSF Flash. Copy Commands PRESERVEMIRROR(REQUIRED|PREFERRED| NO) FLASHCPY ESTABLISH DDNAME(ddname) TARGETVOL(lss, cca, cuuu) TGTOKASPPRCPRIM(YES) PRESERVEMIRROR(PREFERRED) FORCE(NO|YES) FLASHCPY WITHDRAW DDNAME(ddname) TARGETVOL(lss, cca, cuuu) FORCE(YES) 78 © 2009 IBM Corporation
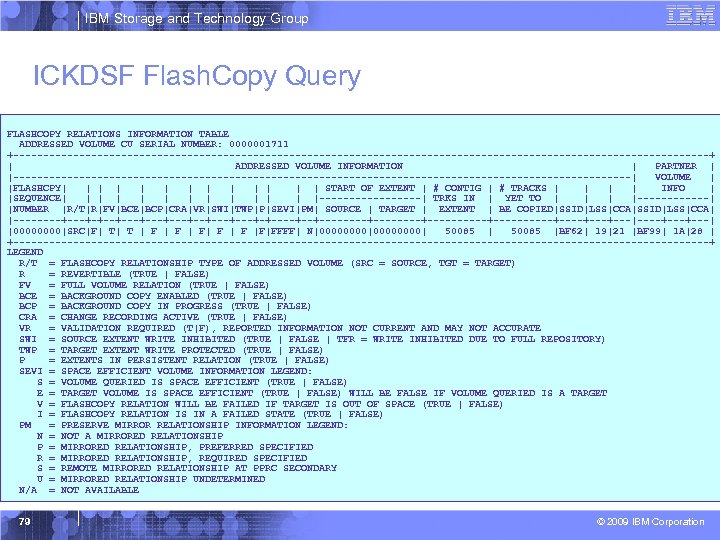
IBM Storage and Technology Group ICKDSF Flash. Copy Query FLASHCOPY RELATIONS INFORMATION TABLE ADDRESSED VOLUME CU SERIAL NUMBER: 0000001711 +----------------------------------------------------------+ | ADDRESSED VOLUME INFORMATION | PARTNER | |----------------------------------------------------| VOLUME | |FLASHCPY| | | | START OF EXTENT | # CONTIG | # TRACKS | | INFO | |SEQUENCE| | | |---------| TRKS IN | YET TO | |------| |NUMBER |R/T|R|FV|BCE|BCP|CRA|VR|SWI|TWP|P|SEVI|PM| SOURCE | TARGET | EXTENT | BE COPIED|SSID|LSS|CCA| |----+---+-+--+---+--+---+-+----+--+--------+----------+---+---|----+---| |0000|SRC|F| T| T | F | F| F |F|FFFF| N|00000000| 50085 |BF 62| 19|21 |BF 99| 1 A|28 | +----------------------------------------------------------+ LEGEND R/T = FLASHCOPY RELATIONSHIP TYPE OF ADDRESSED VOLUME (SRC = SOURCE, TGT = TARGET) R = REVERTIBLE (TRUE | FALSE) FV = FULL VOLUME RELATION (TRUE | FALSE) BCE = BACKGROUND COPY ENABLED (TRUE | FALSE) BCP = BACKGROUND COPY IN PROGRESS (TRUE | FALSE) CRA = CHANGE RECORDING ACTIVE (TRUE | FALSE) VR = VALIDATION REQUIRED (T|F), REPORTED INFORMATION NOT CURRENT AND MAY NOT ACCURATE SWI = SOURCE EXTENT WRITE INHIBITED (TRUE | FALSE | TFR = WRITE INHIBITED DUE TO FULL REPOSITORY) TWP = TARGET EXTENT WRITE PROTECTED (TRUE | FALSE) P = EXTENTS IN PERSISTENT RELATION (TRUE | FALSE) SEVI = SPACE EFFICIENT VOLUME INFORMATION LEGEND: S = VOLUME QUERIED IS SPACE EFFICIENT (TRUE | FALSE) E = TARGET VOLUME IS SPACE EFFICIENT (TRUE | FALSE) WILL BE FALSE IF VOLUME QUERIED IS A TARGET V = FLASHCOPY RELATION WILL BE FAILED IF TARGET IS OUT OF SPACE (TRUE | FALSE) I = FLASHCOPY RELATION IS IN A FAILED STATE (TRUE | FALSE) PM = PRESERVE MIRROR RELATIONSHIP INFORMATION LEGEND: N = NOT A MIRRORED RELATIONSHIP P = MIRRORED RELATIONSHIP, PREFERRED SPECIFIED R = MIRRORED RELATIONSHIP, REQUIRED SPECIFIED S = REMOTE MIRRORED RELATIONSHIP AT PPRC SECONDARY U = MIRRORED RELATIONSHIP UNDETERMINED N/A = NOT AVAILABLE 79 © 2009 IBM Corporation

IBM Storage and Technology Group TSO Flash. Copy Commands PRESERVEMIRROR(REQUIRED|PREFERRED| NO) FCESTABL SDEVN(X’uadd’) TDEVN(X’uadd’) MODE(NOCOPY) PRESERVEMIRROR(PREFERRED) For FCWITHDR, SDM will automatically set the force bit on the withdraw CCW, indicating that if the relationship is a mirrored relation, the withdraw should be immediate. This will also cause a bit to be set for the target PPRC pair, indicating that it was previously the target of a preserve mirror relationship that was withdrawn. FCWITHDR SDEVN(X’uadd’) TDEVN(X’uadd’) 80 © 2009 IBM Corporation
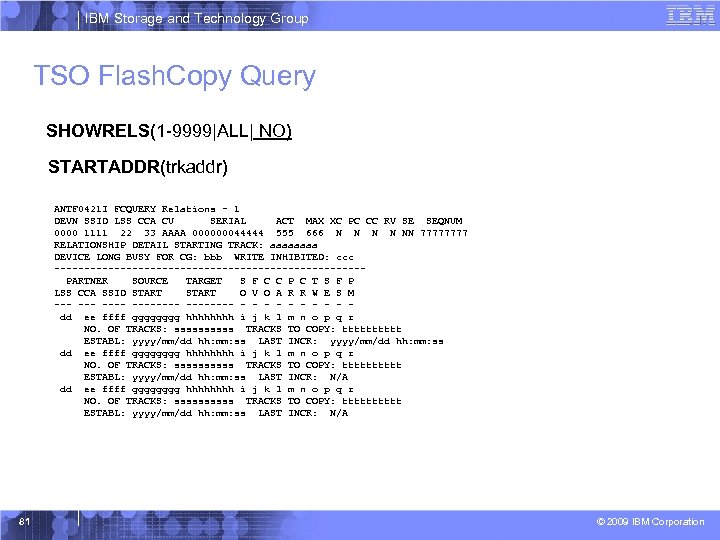
IBM Storage and Technology Group TSO Flash. Copy Query SHOWRELS(1 -9999|ALL| NO) STARTADDR(trkaddr) ANTF 0421 I FCQUERY Relations – 1 DEVN SSID LSS CCA CU SERIAL ACT MAX XC PC CC RV SE SEQNUM 0000 1111 22 33 AAAA 000000044444 555 666 N N NN 7777 RELATIONSHIP DETAIL STARTING TRACK: aaaa DEVICE LONG BUSY FOR CG: bbb WRITE INHIBITED: ccc --------------------------PARTNER SOURCE TARGET S F C C P C T S F P LSS CCA SSID START O V O A R R W E S M --- -------- - - - - - dd ee ffff gggg hhhh i j k l m n o p q r NO. OF TRACKS: sssss TRACKS TO COPY: ttttt ESTABL: yyyy/mm/dd hh: mm: ss LAST INCR: yyyy/mm/dd hh: mm: ss dd ee ffff gggggggg hhhhhhhh i j k l m n o p q r NO. OF TRACKS: ssssssssss TRACKS TO COPY: tttttttttt ESTABL: yyyy/mm/dd hh: mm: ss LAST INCR: N/A 81 © 2009 IBM Corporation
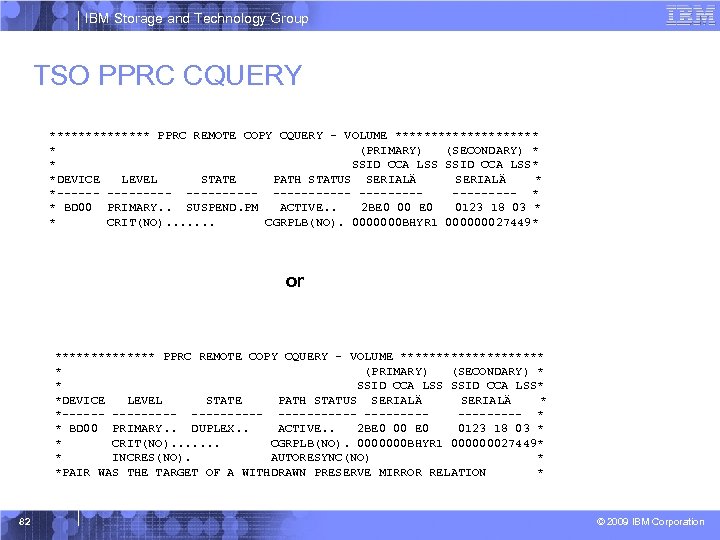
IBM Storage and Technology Group TSO PPRC CQUERY ******* PPRC REMOTE COPY CQUERY - VOLUME ********** * (PRIMARY) (SECONDARY) * * SSID CCA LSS* *DEVICE LEVEL STATE PATH STATUS SERIALÄ * *----------------- * * BD 00 PRIMARY. . SUSPEND. PM ACTIVE. . 2 BE 0 00 E 0 0123 18 03 * * CRIT(NO). . . . CGRPLB(NO). 0000000 BHYR 1 000000027449* or ******* PPRC REMOTE COPY CQUERY - VOLUME ********** * (PRIMARY) (SECONDARY) * * SSID CCA LSS* *DEVICE LEVEL STATE PATH STATUS SERIALÄ * *----------------- * * BD 00 PRIMARY. . DUPLEX. . ACTIVE. . 2 BE 0 00 E 0 0123 18 03 * * CRIT(NO). . . . CGRPLB(NO). 0000000 BHYR 1 000000027449* * INCRES(NO). AUTORESYNC(NO) * *PAIR WAS THE TARGET OF A WITHDRAWN PRESERVE MIRROR RELATION * 82 © 2009 IBM Corporation
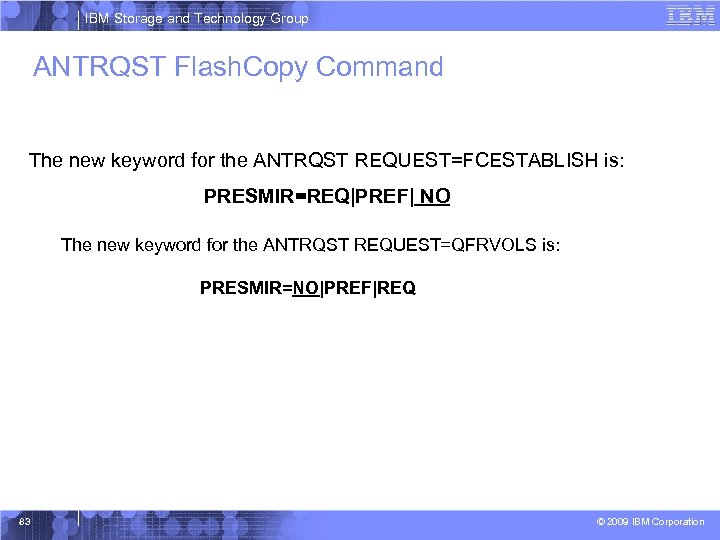
IBM Storage and Technology Group ANTRQST Flash. Copy Command The new keyword for the ANTRQST REQUEST=FCESTABLISH is: PRESMIR=REQ|PREF| NO The new keyword for the ANTRQST REQUEST=QFRVOLS is: PRESMIR=NO|PREF|REQ 83 © 2009 IBM Corporation
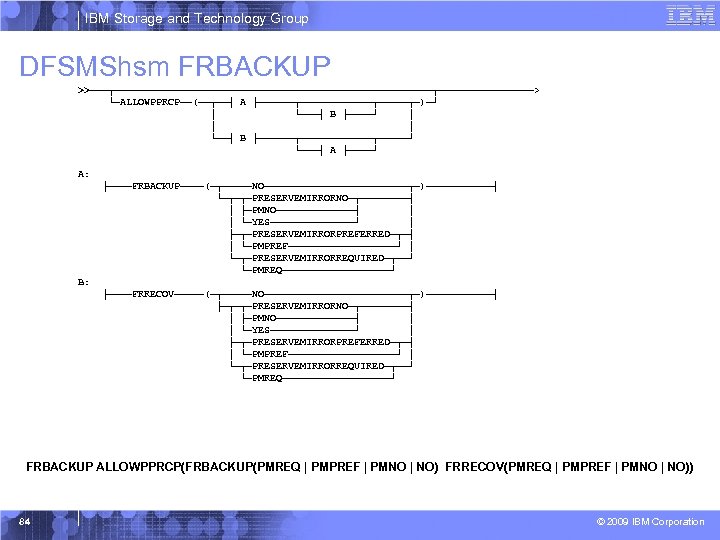
IBM Storage and Technology Group DFSMShsm FRBACKUP >>───┬───────────────────────────┬────────> └─ALLOWPPRCP──(──┬──┤ A ├──────┬──────┬─────┬─)─┘ │ └───┤ B ├────┘ │ │ │ └──┤ B ├──────┬──────┬─────┘ └───┤ A ├────┘ A: ├────FRBACKUP────(─┬─────NO────────────┬─)──────┤ └─┬─┬─PRESERVEMIRRORNO─┬────┤ │ ├─PMNO───────┤ │ │ └─YES───────┘ │ ├─┬─PRESERVEMIRRORPREFERRED─┬─┤ │ └─PMPREF─────────┘ │ └─┬─PRESERVEMIRRORREQUIRED─┬──┘ └─PMREQ─────────┘ B: ├────FRRECOV─────(─┬─────NO────────────┬─)──────┤ ├─┬─┬─PRESERVEMIRRORNO─┬────┤ │ ├─PMNO───────┤ │ │ └─YES───────┘ │ ├─┬─PRESERVEMIRRORPREFERRED─┬─┤ │ └─PMPREF─────────┘ │ └─┬─PRESERVEMIRRORREQUIRED─┬──┘ └─PMREQ─────────┘ FRBACKUP ALLOWPPRCP(FRBACKUP(PMREQ | PMPREF | PMNO | NO) FRRECOV(PMREQ | PMPREF | PMNO | NO)) 84 © 2009 IBM Corporation
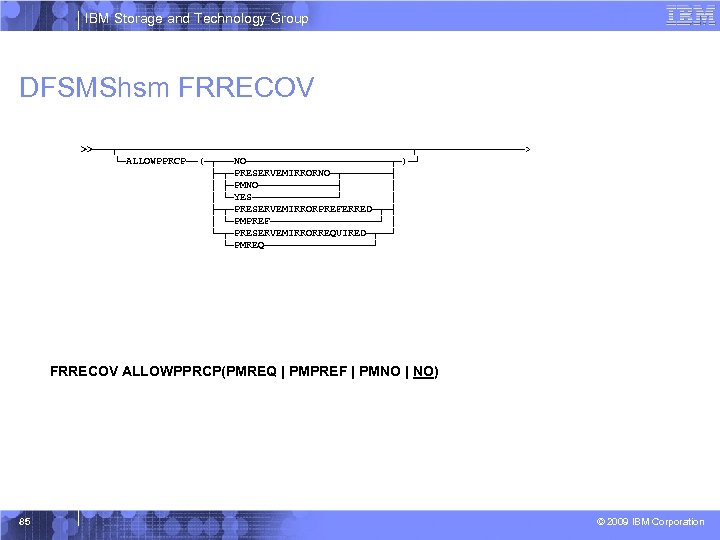
IBM Storage and Technology Group DFSMShsm FRRECOV >>───┬─────────────────────────┬─────────> └─ALLOWPPRCP──(─┬───NO────────────┬─)─┘ ├─┬─PRESERVEMIRRORNO─┬────┤ │ ├─PMNO───────┤ │ │ └─YES───────┘ │ ├─┬─PRESERVEMIRRORPREFERRED─┬─┤ │ └─PMPREF─────────┘ │ └─┬─PRESERVEMIRRORREQUIRED─┬──┘ └─PMREQ─────────┘ FRRECOV ALLOWPPRCP(PMREQ | PMPREF | PMNO | NO) 85 © 2009 IBM Corporation

IBM Storage and Technology Group DS CLI Remote Pair Flash. Copy § -pmir flag added to mkflash/resyncflash/reverseflash – pmir parameter requires one of three values: • no – Do not create a Remote Pair Flash. Copy • preferred – Create remote FLC, may go Duplex Pending • required – Create remote FLC, but no Duplex Pending – If –pmir is not specified, behavior defaults to no § Both lsflash/lsremoteflash display a new “Pmir” column with –l parameter – The Pmir column has five values: • • • 86 No – The -pmir parameter was not specified Preferred – The –pmir parameter was specified and will preserve the target Metro Mirror relationship’s “Full Duplex” state if possible Required – The –pmir parameter was specified and will preserve the target Metro Mirror relationship’s “Full Duplex” state Remote – The –pmir parameter was specified on a different FLC relationship and this FLC relationship is the remote pair FLC that was established automatically Unknown – The Remote Pair Copy status can not be determined due to a conflict in the source and/or target Metro Mirror status © 2009 IBM Corporation

IBM Storage and Technology Group DS CLI Remote Pair Flash. Copy § Normally, removing the FLC relationship on the Metro Mirror Primary volumes will automatically remove the remote FLC relationship on the Secondary Metro Mirror volumes § If there are communications problems, however, the remote FLC relationship on the Secondary Metro Mirror volumes may not be removed § Normally, using rmflash on a FLC relationship with a Remote Pair Copy status of ‘Remote’ will fail, leaving the FLC relationship intact § The rmflash command added an optional –cprm parameter to solve this problem § The cprm stands for Initiate Background Copy and Terminate Relationship § Using rmflash on a FLC relationship with a Remote Pair Copy status of ‘Remote’ and the new –cprm parameter will behave as follows: – If specified on a non-persistent FLC, the -cprm parameter will do the following: • Copy any remaining tracks from the source volume to the target volume • Terminate the Flash. Copy relationship – If specified on a persistent FLC, the -cprm parameter will do the following: • Change the FLC relationship from persistent to non-persistent • Copy any remaining tracks from the source volume to the target volume • Terminate the Flash. Copy relationship 87 © 2009 IBM Corporation

IBM Storage and Technology Group Remote Pair Flash. Copy Do’s and Don’ts § Remote Pair Flash. Copy operations can be full volume or dataset (track) level. Remote Pair Flash. Copy can be used in combination with the following: – Incremental Flash. Copy (unless the request is attempting to take an increment using preserve mirror on a relationship that was established without preserve mirror) – copy, nocopy, or nocopy to copy – Flash. Copy Consistency Groups – Fixed Block § Remote Pair Flash. Copy cannot be used in combination with the following: – Commit – Revert – Fast Reverse Restore – Global Mirror – Global Copy – Existing copy services conflicts still apply (the remote target cannot be a source, local B cannot be an XRC primary, etc. ) – PPRC Incremental Resynchronization started on the PPRC primary that is the target of the relationship. – Taking an incremental on an existing incremental relationship that is not a preserve mirror relationship. – Cascading PPRC (Metro/Global Mirror or Metro/Global Copy) – Space Efficient Volumes 88 © 2009 IBM Corporation

IBM Storage and Technology Group Remote Pair Flash. Copy Operation Requirements § Both Local A and Local B must be Metro Mirror primary devices in full duplex mode with links established and available § Remote A and Remote B must reside in the same Storage Facility Image (SFI) § The required microcode level must be installed in both the local and the remote storage control units 89 © 2009 IBM Corporation

IBM Storage and Technology Group Remote Pair Flash. Copy and SMS Volume Selection § CASE A) Volume is non-FR capable. This case will be handled as before. If FAST REPLICATION was REQUIRED then this volume is rejected. If FAST REPLICATION was PREFERRED then this volume is ranked lower than a FR capable volume. The associated message text in the volume entry may be externalized in the IGD 17268 I or IGD 17279 I message. § CASE B) Volume is FR capable. – PRESERVE MIRROR was either not specified or specified as NO. This case will be handled as before. The volume will be eligible for volume selection and will be ranked higher than a similar non-FR capable volume. – PRESERVE MIRROR was specified as PREFERRED. This case will also be handled as before. The ‘preserve mirror’ capability of this volume will be IGNORED. The volume will be eligible for volume selection and will be ranked higher than a similar non-FR capable volume. – PRESERVE MIRROR was specified as REQUIRED. This volume will be considered eligible for volume selection if any one of the following conditions is met. • • • Volume is marked PRESERVE MIRROR capable VOLUME is marked NOT PRESERVE MIRROR capable because it is not a PPRC volume VOLUME is marked NOT PRESERVE MIRROR capable because it does not have the new feature installed The volume will be REJECTED if none of the above conditions are met. The message text associated with a rejected volume will be preserved in an internal table that also includes a count of the number of volumes rejected for each particular reason. The count and the message text may be externalized in a IGD 17268 I or IGD 17279 I message. 90 © 2009 IBM Corporation

IBM Storage and Technology Group ISMF and Remote Pair Flash. Copy Changes will be made in the DFSMSdss/ISMF line operators to support 3 new values for the keyword FCTOPPRCPrimary : 1. Pres. Mir. No 2. Pres. Mir. Pref 3. Pres. Mir. Req. Updates are made to COPY, CONSOLIDate and DEFRAG in the volume application. 91 © 2009 IBM Corporation
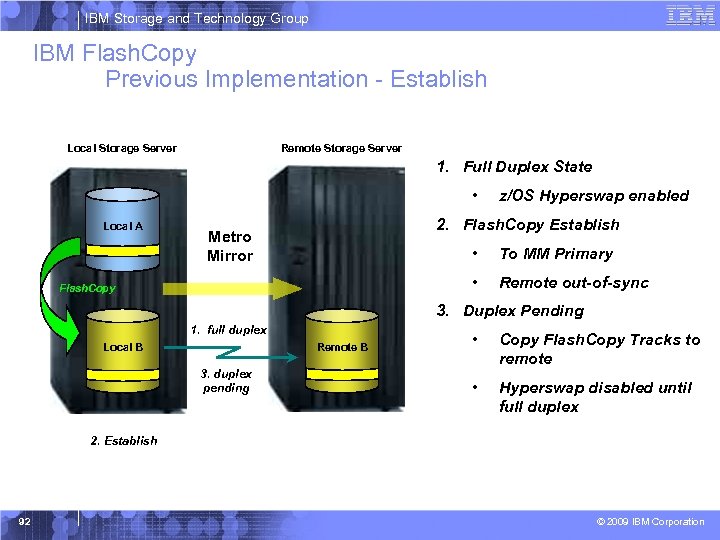
IBM Storage and Technology Group IBM Flash. Copy Previous Implementation - Establish Local Storage Server Remote Storage Server 1. Full Duplex State • Local A z/OS Hyperswap enabled 2. Flash. Copy Establish Metro Mirror • • Flash. Copy To MM Primary Remote out-of-sync 3. Duplex Pending 1. full duplex Local B Remote B 3. duplex pending • Copy Flash. Copy Tracks to remote • Hyperswap disabled until full duplex 2. Establish 92 © 2009 IBM Corporation
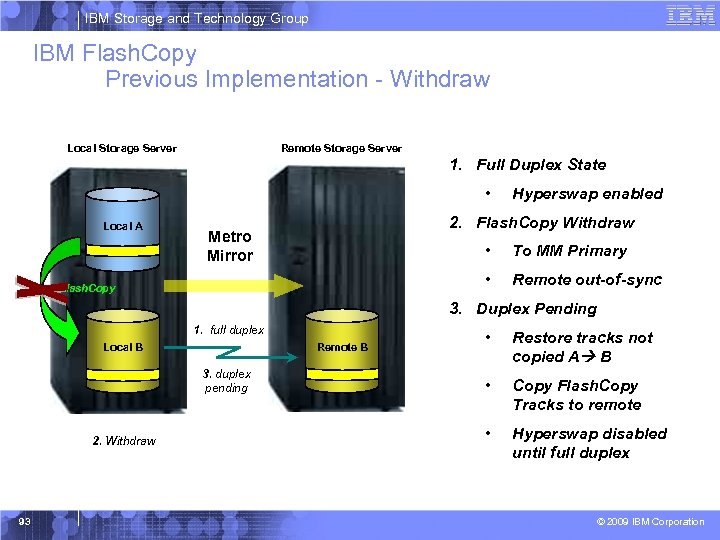
IBM Storage and Technology Group IBM Flash. Copy Previous Implementation - Withdraw Local Storage Server Remote Storage Server 1. Full Duplex State • Local A Hyperswap enabled 2. Flash. Copy Withdraw Metro Mirror • • Flash. Copy To MM Primary Remote out-of-sync 3. Duplex Pending 1. full duplex Local B Remote B 3. duplex pending 2. Withdraw 93 • Restore tracks not copied A B • Copy Flash. Copy Tracks to remote • Hyperswap disabled until full duplex © 2009 IBM Corporation
IBM Storage and Technology Group IBM DS 8000 Solid State Drives Addendum 94 © 2009 IBM Corporation
IBM Storage and Technology Group DFSMS Solid State Device Support § Dependencies: – DS 8000 SSD microcode and hardware § Behavioral Changes: – New I/O statistics in SMF records can help customer to identify good candidates for placement on SSD drives – Users can exploit performance advantages of SSD drives using SMS policy for storage management – DEVSERV command DEVTYPE macro identify volumes backed by SSD 95 © 2009 IBM Corporation
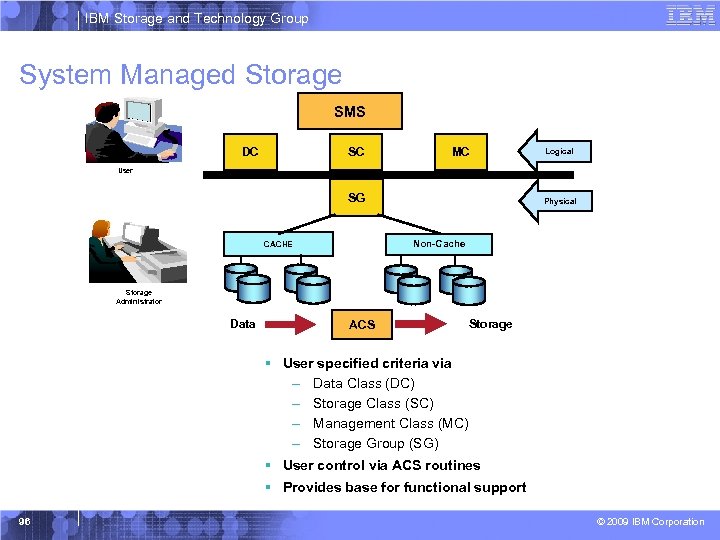
IBM Storage and Technology Group System Managed Storage SMS SC DC MC Logical User SG Physical Non-Cache CACHE Storage Administrator Data ACS Storage § User specified criteria via – Data Class (DC) – Storage Class (SC) – Management Class (MC) – Storage Group (SG) § User control via ACS routines § Provides base for functional support 96 © 2009 IBM Corporation
IBM Storage and Technology Group Defining Data Set Service Levels 97 © 2009 IBM Corporation
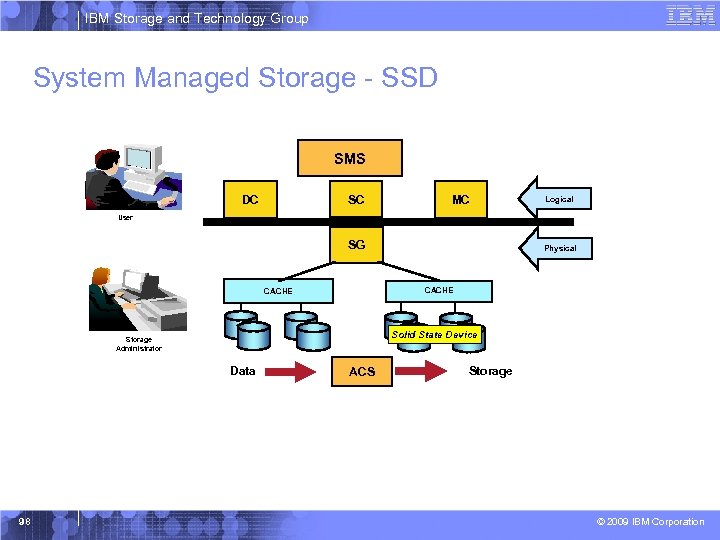
IBM Storage and Technology Group System Managed Storage - SSD SMS SC DC MC Logical User SG CACHE Solid State Device Storage Administrator Data 98 Physical ACS Storage © 2009 IBM Corporation
IBM Storage and Technology Group Storage Class § Performance Objectives – Direct bias – Direct millisecond response – Initial access response – Sequential millisecond response – Sustained data rate § Availability Objectives – Accessibility – Availability – Guaranteed space – Guaranteed synchronous write § Coupling Facility Caching Attributes – Coupling facility cache set name – Coupling facility direct weight – Coupling facility sequential weight 99 © 2009 IBM Corporation
IBM Storage and Technology Group DFSMS Policy Based Storage Management § DFSMS maintains a table for each supported device of performance capabilities – Each entry is in units of millisecond response time (MSR) – A set of MSR values is assigned for random access read and writes, and sequential reads and writes. – Separate MSR values are provided for cache access and disk access – DFSMS takes the MSR values (0 to 999) provided by each device table and inserts each into one of 28 discrete bands. – When a data set allocation request is made, SMS attempts to match the requesting MSR of the storage class associated with the data set with one of the 28 MSR bands. 100 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 Policy Based Storage Management for SSD § New MSR value for cache read and native read for volumes backed by SSD § All other MSR values remain the same as 2107 HDD § How to favor to SSD Selection over non-SSD – Assign a storage class with Direct MSR of 1, DIRECT Bias of R (and not specify any values for sequential MSR or sequential Bias). § To direct storage allocation away from SSD, specify: – DIRECT MSR = 6, DIRECT BIAS = R § Or, create a Storage Group consisting of only SSD backed volumes 101 © 2009 IBM Corporation
IBM Storage and Technology Group When are ACS Routines Invoked for Data Sets? § &ACSENVIR – ALLOC default) for new data set allocations (this is the – ALLOCTST for a pre-allocation or allocation test environment. – CONVERT for data set convert in place operations – RECALL for data set recall operations – RECOVER for data set recover operations – RENAME 102 for data set alter rename operations © 2009 IBM Corporation
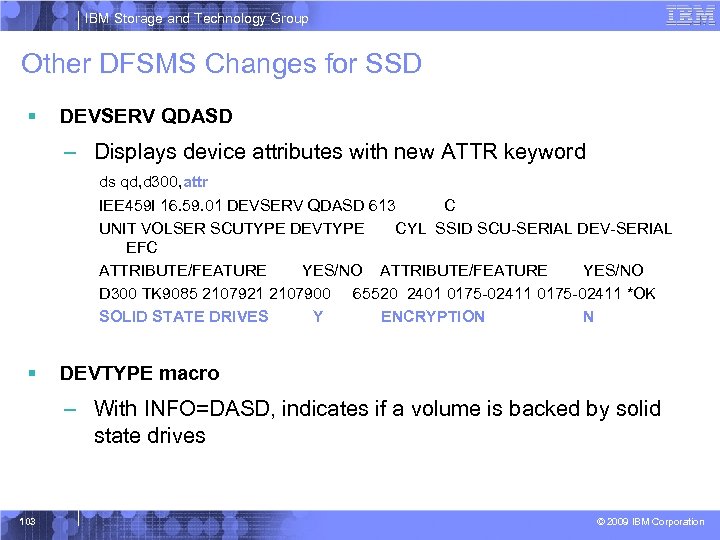
IBM Storage and Technology Group Other DFSMS Changes for SSD § DEVSERV QDASD – Displays device attributes with new ATTR keyword ds qd, d 300, attr IEE 459 I 16. 59. 01 DEVSERV QDASD 613 C UNIT VOLSER SCUTYPE DEVTYPE CYL SSID SCU-SERIAL DEV-SERIAL EFC ATTRIBUTE/FEATURE YES/NO D 300 TK 9085 2107921 2107900 65520 2401 0175 -02411 *OK SOLID STATE DRIVES Y ENCRYPTION N § DEVTYPE macro – With INFO=DASD, indicates if a volume is backed by solid state drives 103 © 2009 IBM Corporation

IBM Storage and Technology Group DFSMS Externals for SSD Support § Vendor exposure/utilization: – No changes needed to benefit from improved performance § Communications to other z/OS platform products and/or vendors: – IGWSMF macro (new I/O statistics added to SMF record 42 subtypes 5 & 6) – DEVTYPE macro (identifying SSD) § Publication Changes: distributed in R 10 refresh – – 104 DFSMS Storage Admin Reference SC 26 -7402 z/OS MVS System Management Facilities (SMF) SA 22 -7630 z/OS MVS System Commands SA 22 -7627 -18 z/OS MVS System Messages VOL 7 (IEB-IEE) SA 22 -7637 -16 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 Authentication Policies and Implementation Steps 105 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 Basic Authentication Policy § Features: – Only one instance – Cannot be copied or deleted – Legacy User Administration § Actions: – Activate Authentication policy – Test Authentication policy – Properties 106 © 2009 IBM Corporation

IBM Storage and Technology Group DS 8000 Storage Authentication Service Policy § Features: – Uses a proxy to contact the external repository (for example: LDAP Server) – Proxy used is a Tivoli Component (Embedded Security Services a. k. a. Authentication Service) – is part of TPC 4. 1 – Multiple instances of SAS policies supported, but only 1 active at a time § Actions: – Create a SAS policy – Activate Authentication policy – Test Authentication policy – Delete Authentication policy – Copy Authentication policy – Properties 107 © 2009 IBM Corporation

IBM Storage and Technology Group Information Required for SAS Policy § Authentication Service URL – https: //<tpc_server_host>: 16311/Token. Service/services/Trust – Example: https: //mdm-b 26 w 2 k 3. storage. usca. ibm. com: 16311/Token. Service/services/Tr ust § Authentication Service Client User ID/Pwd – Example: TPCSuper. User, DSUser, etc § Truststore file with Certificate for SSL/Pwd § LDAP users and/or user groups to map to DS 8000 User Roles 108 © 2009 IBM Corporation
IBM Storage and Technology Group SSPC (TPC) Steps for LDAP Authentication 1. Configure access to LDAP repository 2. Extract Certificate – Used for securing communication between Authentication Client on HMC and Authentication Service (server component) on SSPC 3. Create a truststore which includes the certificate from #2 109 © 2009 IBM Corporation
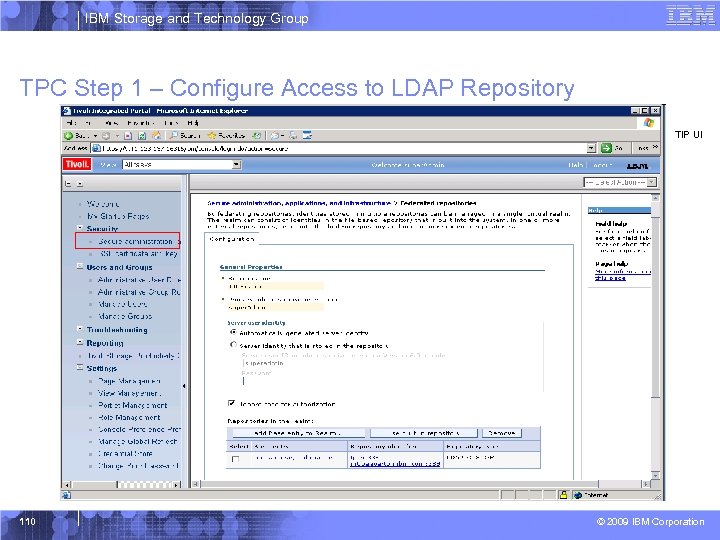
IBM Storage and Technology Group TPC Step 1 – Configure Access to LDAP Repository TIP UI 110 © 2009 IBM Corporation
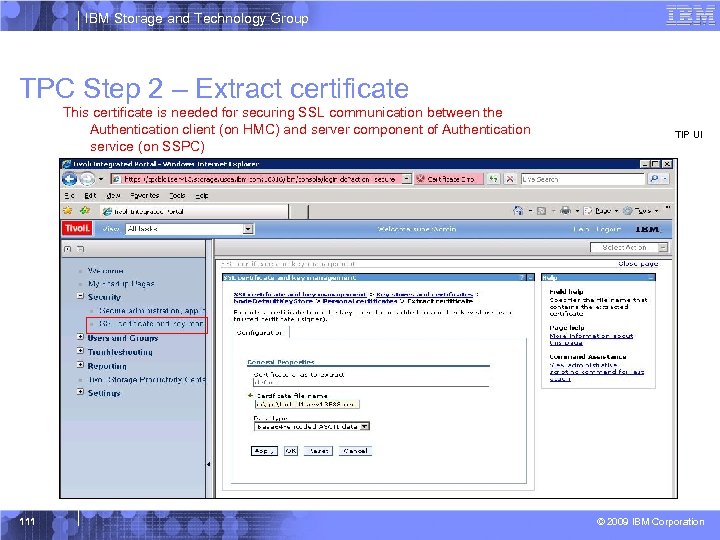
IBM Storage and Technology Group TPC Step 2 – Extract certificate This certificate is needed for securing SSL communication between the Authentication client (on HMC) and server component of Authentication service (on SSPC) 111 TIP UI © 2009 IBM Corporation
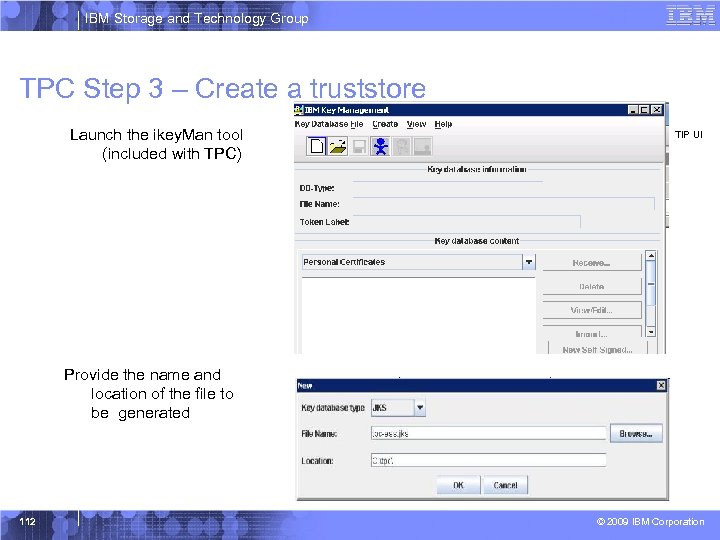
IBM Storage and Technology Group TPC Step 3 – Create a truststore Launch the ikey. Man tool (included with TPC) TIP UI Provide the name and location of the file to be generated 112 © 2009 IBM Corporation
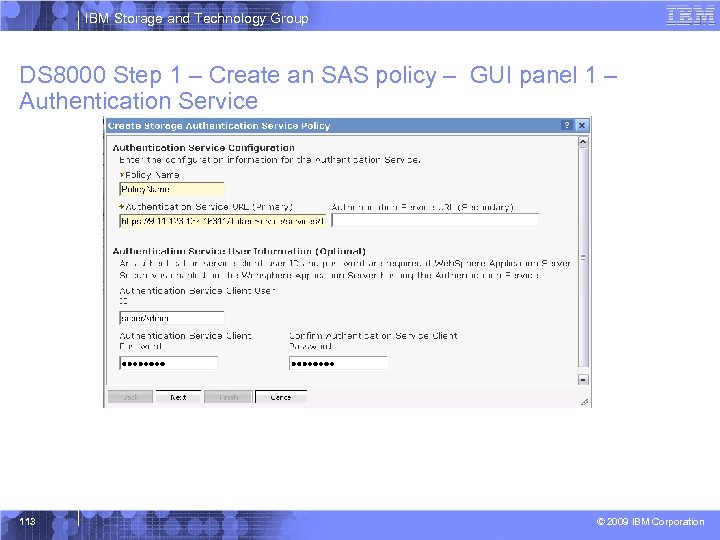
IBM Storage and Technology Group DS 8000 Step 1 – Create an SAS policy – GUI panel 1 – Authentication Service 113 © 2009 IBM Corporation
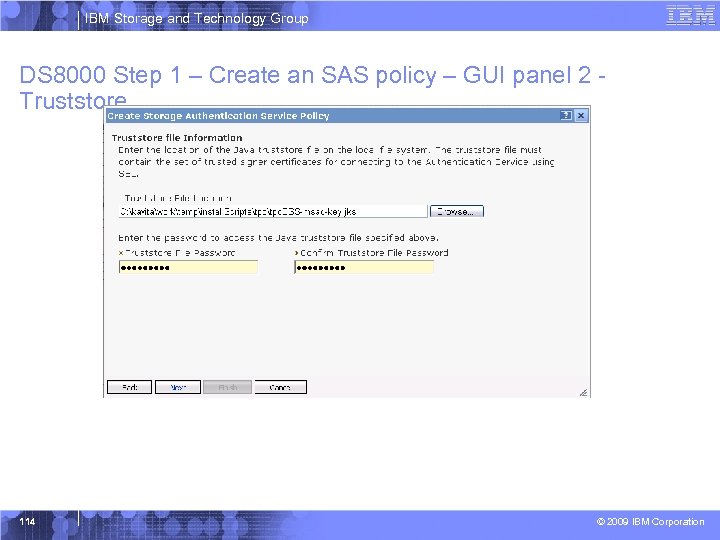
IBM Storage and Technology Group DS 8000 Step 1 – Create an SAS policy – GUI panel 2 Truststore 114 © 2009 IBM Corporation
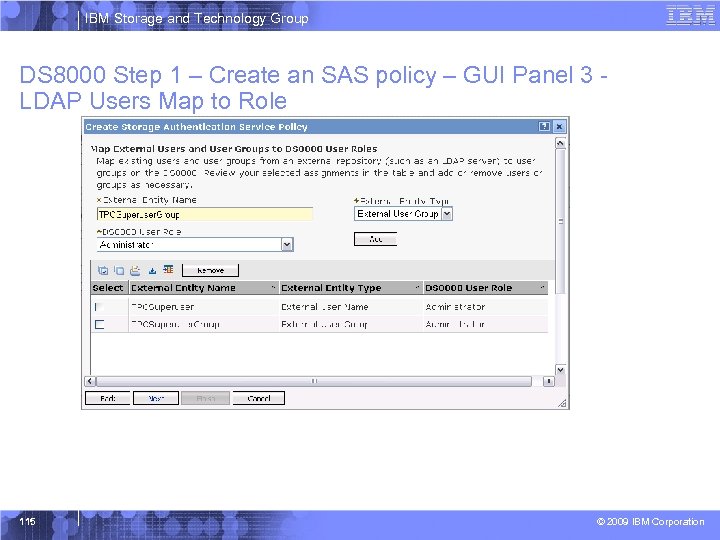
IBM Storage and Technology Group DS 8000 Step 1 – Create an SAS policy – GUI Panel 3 LDAP Users Map to Role 115 © 2009 IBM Corporation
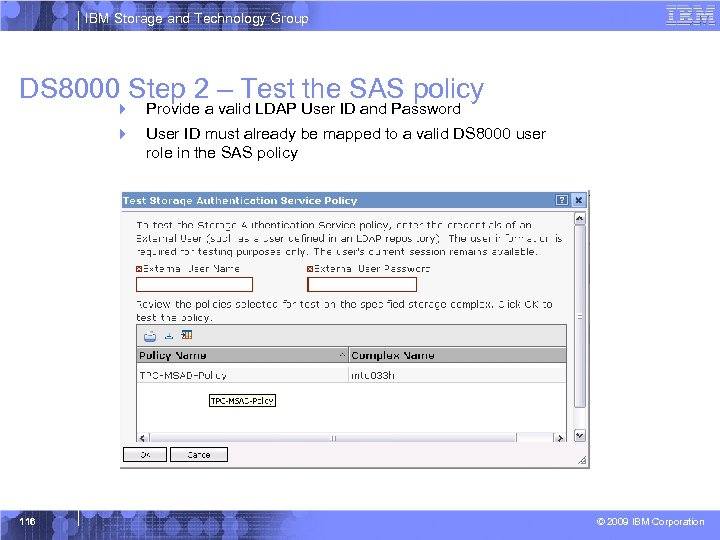
IBM Storage and Technology Group DS 8000 Step 2 – Test the SAS policy 4 Provide a valid LDAP User ID and Password 4 User ID must already be mapped to a valid DS 8000 user role in the SAS policy 116 © 2009 IBM Corporation
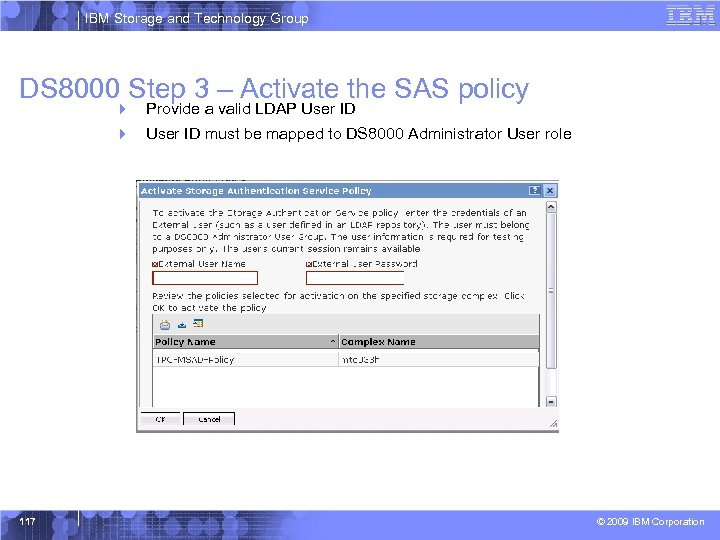
IBM Storage and Technology Group DS 8000 Step 3 – Activate the SAS policy 4 Provide a valid LDAP User ID 4 User ID must be mapped to DS 8000 Administrator User role 117 © 2009 IBM Corporation

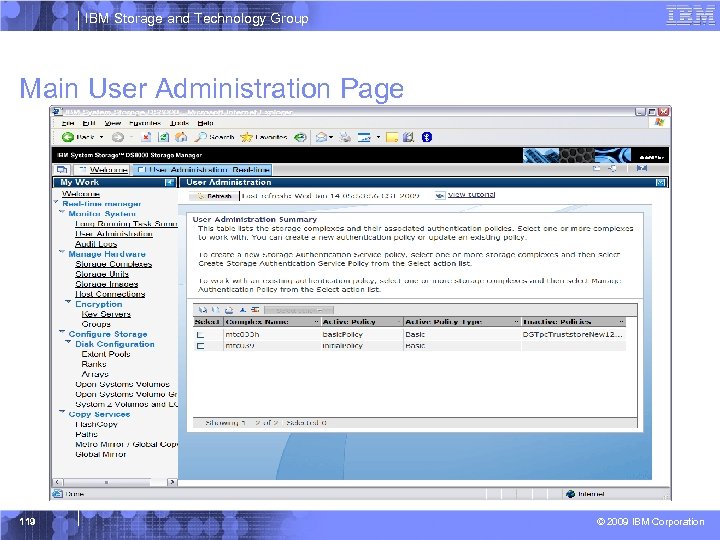
IBM Storage and Technology Group Additional DS 8000 GUI Screenshots 118 © 2009 IBM Corporation
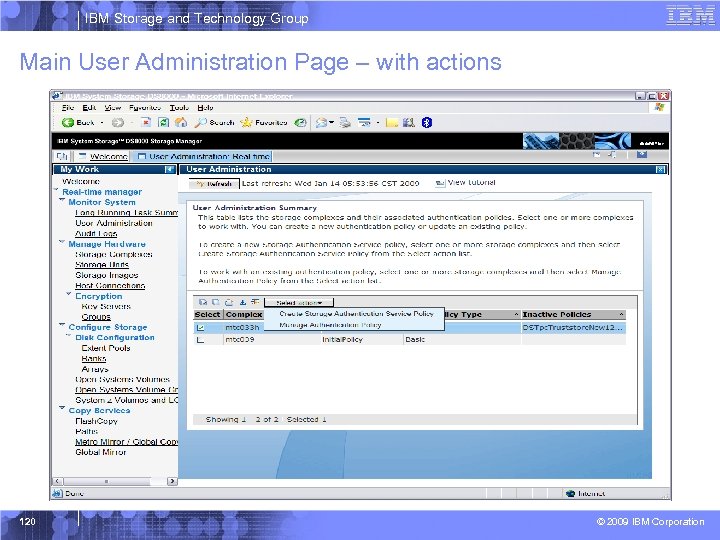
IBM Storage and Technology Group Main User Administration Page 119 © 2009 IBM Corporation
IBM Storage and Technology Group Main User Administration Page – with actions 120 © 2009 IBM Corporation
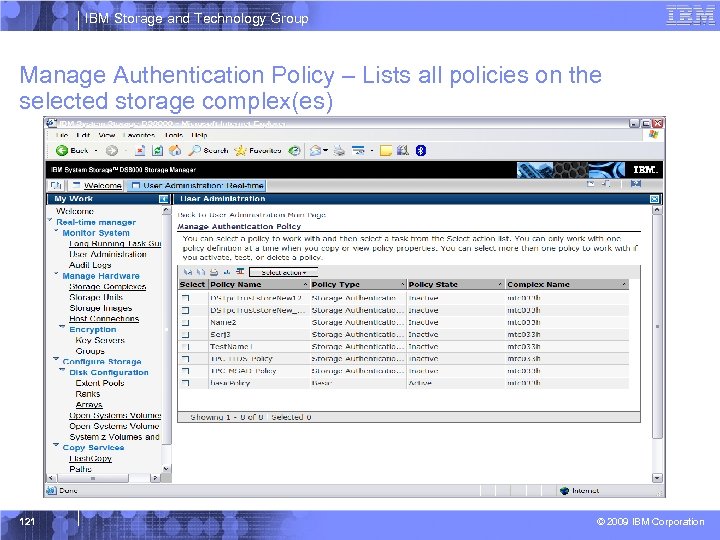
IBM Storage and Technology Group Manage Authentication Policy – Lists all policies on the selected storage complex(es) 121 © 2009 IBM Corporation
IBM Storage and Technology Group Manage Authentication Policy – Actions for Basic (non. LDAP) policy type 122 © 2009 IBM Corporation
IBM Storage and Technology Group Basic Authentication Properties 123 © 2009 IBM Corporation
IBM Storage and Technology Group Basic Authentication Properties – Actions – Launches panels similar to what is in current DS 8 K GUI 124 © 2009 IBM Corporation
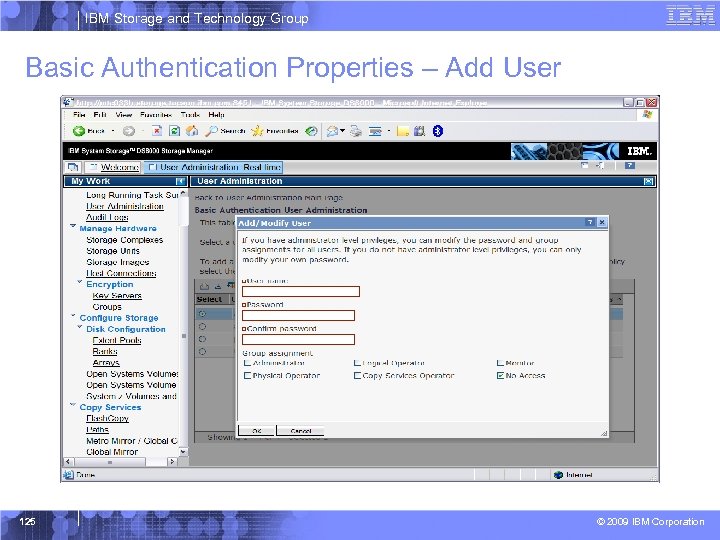
IBM Storage and Technology Group Basic Authentication Properties – Add User 125 © 2009 IBM Corporation
IBM Storage and Technology Group Manage Authentication Policy – Actions for SAS (LDAP) policy type 126 © 2009 IBM Corporation
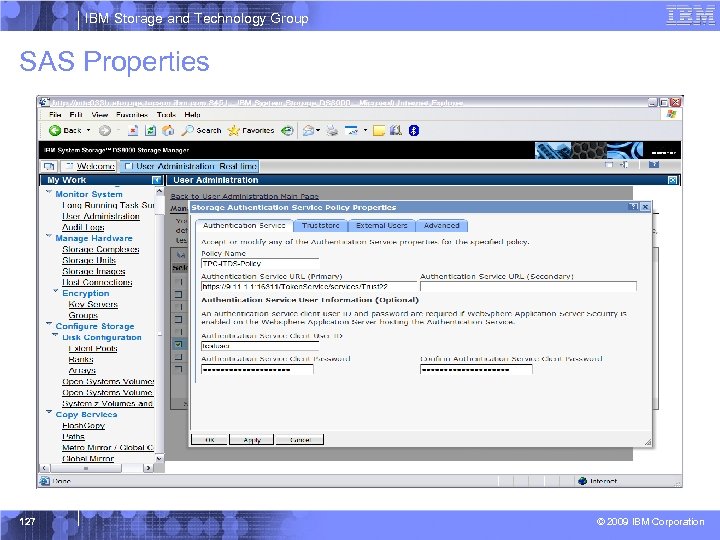
IBM Storage and Technology Group SAS Properties 127 © 2009 IBM Corporation

IBM Storage and Technology Group SAS Copy Authentication Policy § Copy function allows a SAS policy to be copied onto the same storage complex, or onto one or more other storage complexes § The target storage complexes are the same ones as selected from the storage complex list on the main user administration page § Copy function copies all aspects of the SAS policy, including the truststore, making it very simple to activate the same SAS policy on other complexes. – User only has to copy the policy and then activate it (assuming the additional complexes have connectivity to the same SSPC) 128 © 2009 IBM Corporation
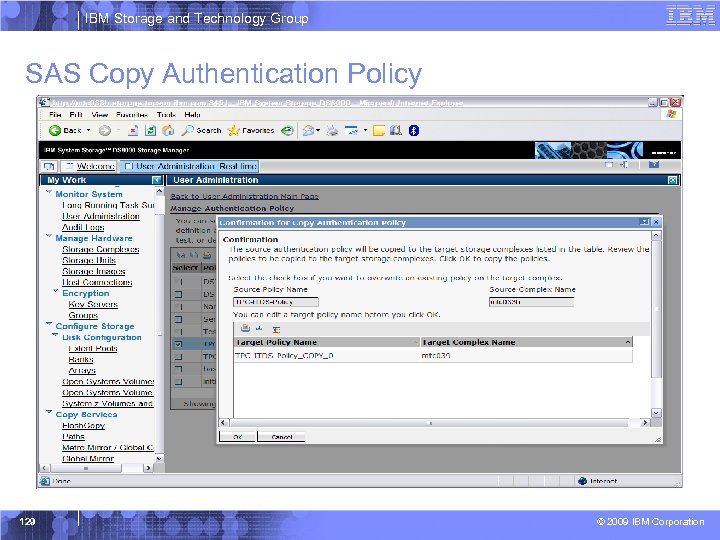
IBM Storage and Technology Group SAS Copy Authentication Policy 129 © 2009 IBM Corporation

IBM Storage and Technology Group Additional TPC Screen Shots 130 © 2009 IBM Corporation
IBM Storage and Technology Group TPC Install Panels for LDAP Info - 1 131 © 2009 IBM Corporation
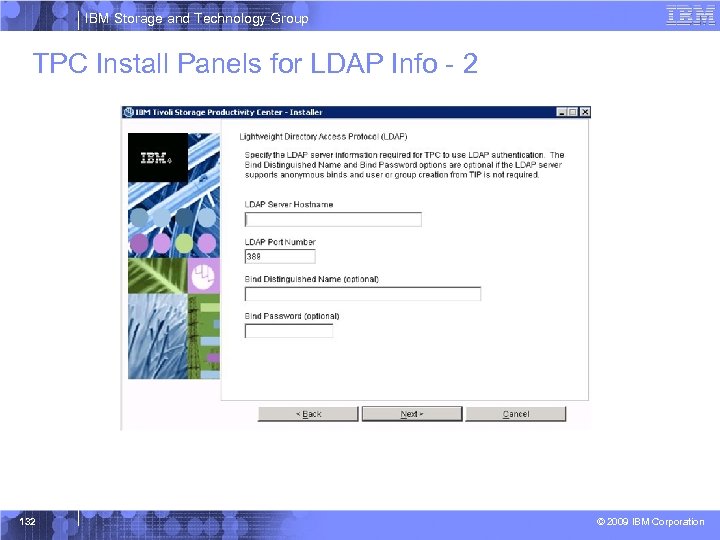
IBM Storage and Technology Group TPC Install Panels for LDAP Info - 2 132 © 2009 IBM Corporation
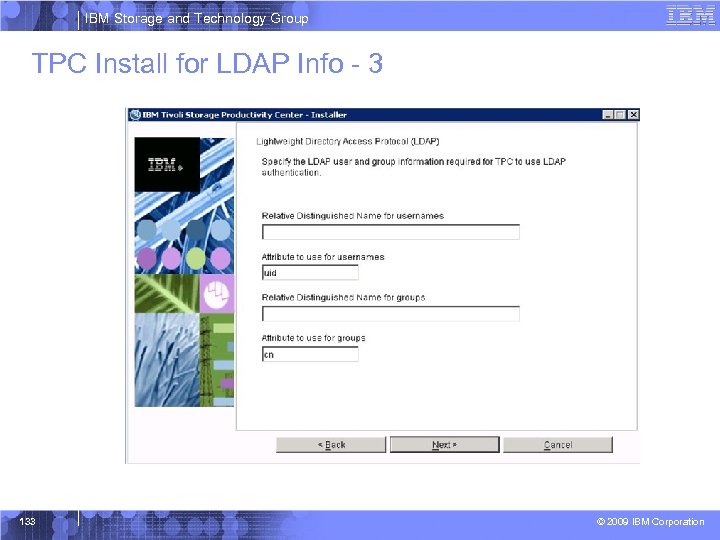
IBM Storage and Technology Group TPC Install for LDAP Info - 3 133 © 2009 IBM Corporation
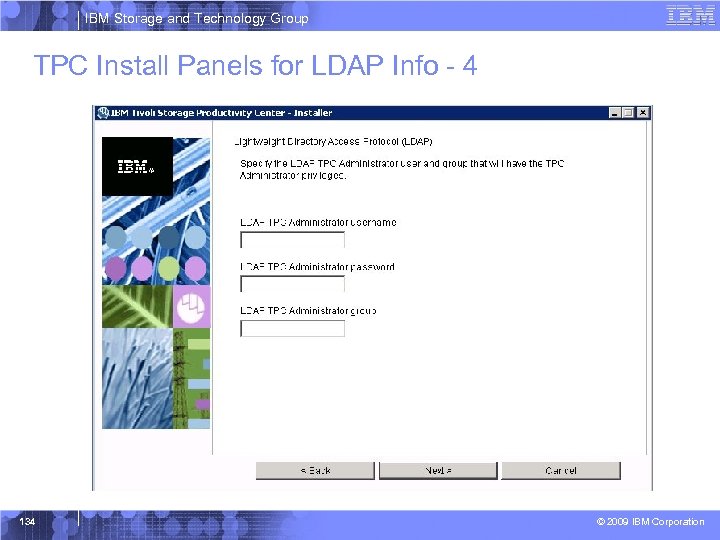
IBM Storage and Technology Group TPC Install Panels for LDAP Info - 4 134 © 2009 IBM Corporation
IBM Storage and Technology Group Disclaimers §Copyright © 2009 by International Business Machines Corporation. §No part of this document may be reproduced or transmitted in any form without written permission from IBM Corporation. §Product data has been reviewed for accuracy as of the date of initial publication. Product data is subject to change without notice. This information could include technical inaccuracies or typographical errors. IBM may make improvements and/or changes in the product(s) and/or programs(s) at any time without notice. §Unless otherwise note, the performance data contained herein was obtained in a controlled, isolated environment. Actual results that may be obtained in other operating environments may vary significantly. While IBM has reviewed each item for accuracy in a specific situation, there is no guarantee that the same or similar results will be obtained elsewhere. Other data may have been obtained from publicly available documents or sources. In such cases, IBM has endeavored to provide comparable measurements for systems being compared. §References in this document to IBM products, programs, or services does not imply that IBM intends to make such products, programs or services available in all countries in which IBM operates or does business. Any reference to an IBM Program Product in this document is not intended to state or imply that only that program product may be used. Any functionally equivalent program, that does not infringe IBM’s intellectually property rights, may be used instead. It is the user’s responsibility to evaluate and verify the operation of any non-IBM product, program or service. §The information provided in this document is distributed "AS IS" without any warranty, either express or implied. IBM EXPRESSLY DISCLAIMS any warranties of merchantability, fitness for a particular purpose OR NONINFRINGEMENT. IBM shall have no responsibility to update this information. IBM products are warranted according to the terms and conditions of the agreements ( e. g. , IBM Customer Agreement, Statement of Limited Warranty, International Program License Agreement, etc. ) under which they are provided. IBM is not responsible for the performance or interoperability of any non. IBM products discussed herein. §Information concerning non-IBM products was obtained from the suppliers of those products, their published announcements or other publicly available sources. IBM has not tested those products in connection with this publication and cannot confirm the accuracy of performance, compatibility or any other claims related to non-IBM products. Questions on the capabilities of non-IBM products should be addressed to the suppliers of those products. §The provision of the information contained herein is not intended to, and does not, grant any right or license under any IBM patents or copyrights. Inquiries regarding patent or copyright licenses should be made, in writing, to: IBM Director of Licensing IBM Corporation North Castle Drive Armonk, NY 10504 -1785 U. S. A. 135 © 2009 IBM Corporation
IBM Storage and Technology Group Trademarks The following terms are trademarks or registered trademarks of the IBM Corporation in either the United States, other countries or both. §IBM, S/390, ES/3090, ES/9000, AS/400, RS/6000, MVS/ESA, OS/390, VM/ESA, VSE, TPF, OS/2, OS/400, AIX, , Flash. Copy, z/VM, z/OS, POWER 5+, DB 2, Universal Database §DFSMS/MVS, DFSMS/VM, , DFSMSdfp, DFSMSdss, DFSMShsm, DFSMSrmm, Blade. Center, §FICON, ESCON, Total. Storage, Enterprise Storage Server, i. Series, p. Series, x. Series, z. Series, System z 9, System i 5, System p 5, System x, System Storage Java and all Java-based trademarks are trademarks of Sun Microsystems, Inc. in the United States, other countries, or both. Microsoft, Windows NT, and the Windows logo are trademarks of Microsoft Corporation in the United States, other countries, or both. Intel, Intel logo, Intel Inside logo, Intel Centrino logo, Celeron, Intel Xeon, Intel Speed. Step, Itanium, and Pentium are trademarks or registered trademarks of Intel Corporation or its subsidiaries in the United States and other countries. UNIX is a registered trademark of The Open Group in the United States and other countries. Linux is a registered trademark of Linus Torvalds in the United States, other countries, or both. Other company, product, or service names may be trademarks or service marks of others. 136 © 2009 IBM Corporation
eb280b672b174363579311f6d225e209.ppt