099934bfc9ac575f996f81f2236f8712.ppt
- Количество слайдов: 41
IBM Software Group – Information Management IBM Informix Dynamic Server 10. 00 Security and Column-Level Encryption Jerry Keesee, Director of Informix Lab Jonathan Leffler, STSM, Informix R&D IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Agenda § § § § 2 IBM Informix Dynamic Server 10. 00 What is Column-Level Encryption? Manual Pages Modes of Use Key Management Behind the Scenes Auditing with IDS Questions and Answers IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Announcing IBM Informix Dynamic Server 10. 00 § IDS 10 is IBM’s flagship database for industrialstrength embedded solutions! § IDS 10 is the highest quality and highest performing release ever! § IDS 10 significantly raises the bar for autonomics, availability and low-cost operations! § Generally available since 2005 -02 -28. 3 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Key Features of IDS 10. 00 Safety / High Availability / Reliability ü Table Level Point in Time Restore ü Faster Restart ü Query Plan and Tracing Tool Enhancements ü HDR Setup with External Backup & Restore Partner Enhancements ü Configurable Page Size ü Larger Indexes ü Buffer Pools ü Create or Drop Index Online ü Single or Privileged User Admin Mode ü Rename DBSpace ü Default Roles Security ü Column Level Encryption ü LDAP Support for Windows ü Restricted Datablade Registration 4 Ease of Administration ü Automated Re-Sync of Tables in ER ü BAR Ease of Use Enhancements ü ER Templates / Ease Setup in ISA ü External Optimizer Directives ü Dynamic Set OPTCOMPIND ü ON-Tape Without Involving Backup Media App Development / SWG Integration ü 4 GL / EGL Merge with Web. Sphere ü. Net Native Provider ü Visual Studio Integration ü JDBC 3. 0 Standards Compliance ü Cross DB Built-In UDTs Support ü DRDA in ESQL/C & Server ü WORF and TDPI Bundled Performance & Infrastructure ü Query Processing Improvements ü Load Performance Improvement ü Shared Memory Segments more than 4 GB ü Multiple Fragments of a Table in a Dbspace IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management “To sum it all up, IDS 10. 0 is a DBA’s dream come true. ” Gary Ben-Israel CIO, National Institute for Testing and Evaluation Jerusalem, Israel “Companies that need their data and transaction resources to be available 24 x 7 will be pleased with the release of IDS 10. 0. With this new release, organizations can tune their database and manage index issues online, without interrupting service. ” Gerd Kaluzinski Senior Systems Engineer BYTEC Gmb. H 5 “… Table level restore enables us to implement a BCP plan without the need for duplicate servers. ” David A. Link IS Manager, West Corporation IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management What is Available in Earlier Versions of IDS? § IDS 7. 3 x, 9. 2 x, 9. 30, 9. 40 provides: 4 Auditing q q A powerful and under-appreciated facility Discussed briefly at the end § IDS 9. 40 provides 4 PAM Pluggable Authentication Modules q Configurable authentication mechanism for validating user identities. 4 Encrypted Communications q q Using encryption technology from Open. SSL Client to server communications ER server to server communications – Not HDR server to server communications 6 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management What is Column-Level Encryption? § Data can be stored in encrypted format. 4 Using SQL functions ENCRYPT and DECRYPT. 4 Data encrypted using either Triple-DES or AES. 4 Data encrypted under application control. 4 DBMS is not aware that data is encrypted. 4 Can set password at session level with new SQL statement. § Design based on DB 2 functions. 4 DB 2 supports DES: But, since July 2004, the US Government does not. 4 DB 2 does not support AES: q AES (aka Rijndael) is the replacement for DES. 4 Analogous to Oracle’s DBMS Obfuscation Tool Kit. q 7 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management What is Column-Level Encryption? § Assists in legislative compliance. 4 HIPAA (Health Insurance Portability and Accountability Act), 1996 4 Sarbanes-Oxley (aka Sarbox or Sox), 2002 4 Basel II, 2001 4 Gramm-Leach-Bliley Act (GLBA), 1999 4 California SB 1386 ‘Personal Information: Privacy’, 2002 § Latest cryptographic standards (Open. SSL 0. 9. 7 c) § 128 -bit AES and 112 -bit Triple-DES 8 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Manual Pages – Overview § § § § 9 Passwords and hints ENCRYPT_TDES function ENCRYPT_AES function DECRYPT_CHAR function DECRYPT_BINARY function GETHINT function SET ENCRYPTION PASSWORD statement Data Space Requirements IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Manual Pages – Passwords, Hints § Passwords are necessary. 4 Pass-phrase can be from 6 bytes up to 128 bytes. 4 Cryptographic hash is used to make random-seeming key. 4 Random initialization vector also used (and recorded). § Hints are optional. 4 Hints can be up to 32 bytes of text. § Passwords (and hints) can be set for a session. 4 SET ENCRYPTION PASSWORD statement. 4 Hence, the password and hint parameters are optional. 4 Explicit values override the session default values. 10 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Manual Pages – ENCRYPT_TDES § ENCRYPT_TDES(data [ , password [ , hint ] ]) 4 Input data is encrypted. 4 For character input data: q Output is base-64 encoded. 4 For binary input data (BLOB): q Output is unencoded. § Triple-DES encryption 4 Triple DES uses two 56 -bit keys for 112 -bits overall. § UPDATE Some. Table SET Encrypted. Column = ENCRYPT_TDES(? , ? ) WHERE PK_Column = ? ; § Extremely variant function. 11 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Manual Pages – ENCRYPT_AES § ENCRYPT_AES(data [ , password [ , hint ] ]) 4 Input data is encrypted. 4 For character input data: q Output is base-64 encoded. 4 For binary input data (BLOB): q Output is unencoded. § AES encryption 4 Advanced Encryption System (aka Rijndael). q 128 -bit key size. § INSERT INTO Some. Table VALUES (? , ENCRYPT_AES(? , ? )) § Extremely variant function. 12 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Manual Pages – DECRYPT_CHAR § DECRYPT_CHAR(encrypted_data [ , password ]) § Also known as DECRYPT § Encrypted data in base-64 encoding contains: 4 Information about encryption method. 4 All other data needed to decrypt it. 4 Except the password! § Error if the data is not encrypted. § SELECT DECRYPT_CHAR(Encrypted. Column, ‘password’) FROM Some. Table WHERE PK_Column = ? § Invariant function. 13 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Manual Pages – DECRYPT_BINARY § DECRYPT_BINARY(encrypted_data [, password ]) § Encrypted data contains: 4 Information about encryption method. 4 All other data needed to decrypt it. 4 Except the password! § Error if the data is not encrypted. § SELECT DECRYPT_BINARY(Encrypted. Byte. Column, ? ) FROM Some. Table WHERE PK_Column = ? § Invariant function. 14 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Manual Pages – GETHINT § GETHINT(encrypted_data) § Returns the hint (if any) from the encrypted data. 4 Or an empty string (NULL). § SELECT GETHINT(enc_cc_number) FROM cc_info WHERE user_id = ? ; § Invariant function. § Anybody can get any hint at any time. 15 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Manual Pages – SET ENCRYPTION PASSWORD § New SQL statement 4 SET ENCRYPTION PASSWORD ‘password’ [ WITH HINT ‘hint string’ ]; § Specifies the password that will be used by default. 4 When no password explicitly provided: q q To encryption functions. To decryption functions. § Optionally specifies the hint that will be used by default: 4 When no hint provided to encryption functions. § Session wide password management: 4 For easy programming. 4 Support for views, triggers, SPL. 16 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Manual Pages – Storage Space Requirements § Encrypted data will be stored in character columns. § Needs more space than the unencrypted data. § If input data string is N bytes long: 4 AES = B 64(NGM(N, 16) + H + 8) + 11 4 Triple-DES = B 64(NGM(N, 8) + H + 8) + 11 4 H = 0 with no hint; H = 40 with hint. 4 NGM(x, y) – Next multiple of y that is greater than x. q NGM(x, y) = ((x + y) ÷ y) × y 4 B 64(x) – Base-64 encoding size. q B 64(x) = ((x + 2) ÷ 3) × 4 4 AES can be bigger than Triple-DES, but not by much. § Do not normally encrypt 4 -byte integer numbers. 17 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
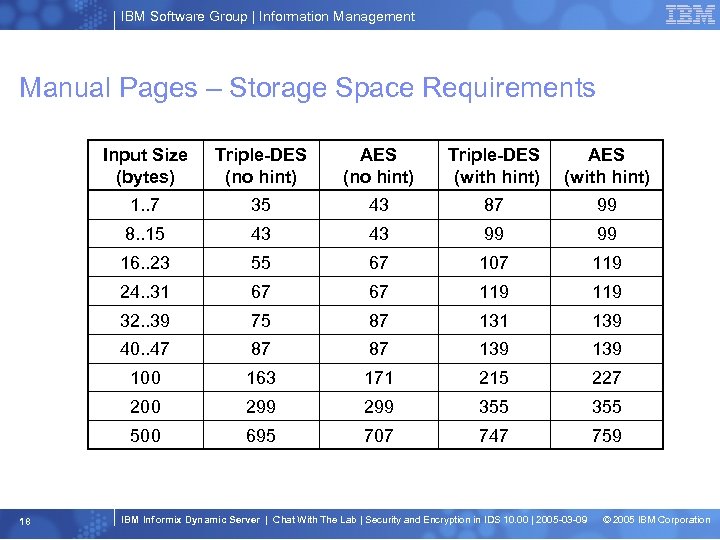
IBM Software Group | Information Management Manual Pages – Storage Space Requirements Input Size (bytes) AES (no hint) Triple-DES (with hint) AES (with hint) 1. . 7 35 43 87 99 8. . 15 43 43 99 99 16. . 23 55 67 107 119 24. . 31 67 67 119 32. . 39 75 87 131 139 40. . 47 87 87 139 100 163 171 215 227 200 299 355 500 18 Triple-DES (no hint) 695 707 747 759 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Performance Impact of Encryption § Comparing ‘apples to apples’ is hard. § An accurate comparison consists of: 4 IDS encrypting and decrypting data sent unencrypted by client q versus 4 Client encrypting and decrypting data sent encrypted to IDS. § Unfortunately, that requires benchmarking an application with cryptography built in. 4 Can be done, but is fiddly. § So, everybody makes an ‘apples to oranges’ comparison: 4 IDS encrypting and decrypting data versus 4 IDS not encrypting and decrypting data. q 19 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Performance Impact of Encryption § The performance impact of encryption is significant. 4 It depends on direction: q Encrypting is slower than decrypting. 4 It does not depend measurably on algorithm: AES performs at the same speed as Triple-DES. 4 It does depend on data size: q q The relative overhead is less when there is more data to encrypt. § Do not use encryption just because it is sexy. 4 Use it where there is a demonstrable business or legal need. 20 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Performance Impact – Credit Card Number § Credit card number plus expiry date 420 digits + 5 punctuators 4“ 4567 -1234 -2345 -3456□ 01/99” 4 Needs 67 characters without hint; 119 with hint. § These comparisons should be repeated for your machine! 4 Mine is an old, small, slow Sun Ultra. Sparc 10: q q q 21 Solaris 8 Single CPU at 333 MHz 256 MB Single user No /dev/random or /dev/urandom Running several IDS servers, Apache, etc. IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Performance Impact – Credit Card Number § Without hints – batch mode processing – 5000 rows. 4 INSERT INTO New. Table SELECT …, ENCRYPT_TDES(Other. Column), … FROM Other. Table; § Encryption performance: 4424 µs per row (without encryption) 43601 µs per row (with Triple-DES encryption) 4 Ratio: 8. 5: 1 4 Cost: 3200 µs per call. 4 Even a trivial SPL procedure called in place of encryption levels the playing field a lot. 22 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Performance Impact – Credit Card Number § Without hints – batch mode processing – 5000 rows. 4 SELECT …, DECRYPT_CHAR(Encrypted. Data), … FROM New. Table; § Decryption performance: 4155 µs per row (without decryption) 41285 µs per row (with Triple-DES decryption) 4 Ratio: 8. 3: 1 4 Cost: 1100 µs per call. § Hence, decryption costs about 1/3 what encryption costs. 4 Major component of encryption cost: Generating cryptographically random number. 4 Just as well you’ll normally do more decryption than encryption. q 23 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Modes of Use § Column-Level Encryption is an enabling technology § You decide how you are going to use it. § Consider reading: 4 Peter Wayner, ‘Translucent Databases’, Flyzone Press, 2002. q ISBN 0 -12 -738671 -8 q Correct URL: http: //www. wayner. org/books/td/ – Not http: //www. flyzone. com/ o As on the inside of the book and original version of this presentation. q Available via Barnes and Noble, or Amazon. § Two main modes of operation: 4 Web mode: q Different keys for each row of data. 4 MIS mode: q Same key for each row of data. 24 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Web Application § § Think of credit card numbers on a web site. Different keys for each row of data. Hints are important. Key management is not a major problem. 4 You do not store the key (password) for the user. 4 If the user forgets their password, the data is re-enterable. 4 Or you get into more fancy schemes: q q Encrypt user’s passwords with known key. But these systems are generally less secure. § SET ENCRYPTION PASSWORD is irrelevant. 25 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management MIS Applications § § Same key for each row of data Hints are irrelevant Key management is critical. SET ENCRYPTION PASSWORD is critical. 4 You might be better off coding with a temporary table: q q q 26 Contains one row of data – the password. Join with that table when you need encrypted data. Avoids revealing the password in SQL. IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Key Management § IDS does not do any key management. § Keys are handled outside the DBMS. § You can store keys in the DBMS if you want to. 4 Securing them is your problem. 4 Probably encrypted with a single high-security password. 27 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Encryption Without Changing Applications § You can do it, 4 But it is not necessarily a good idea. § The application will not work as fast as without encryption, 4 But it will run about as fast as if you rework it with encryption. q So, many people will do it. § The application will use more data space. 4 But you won’t be using hints. § The easiest approach uses more space than necessary. 4 And more encryption and decryption operations. § It is a bad idea to use encrypted data as keys. 4 Does the SSN get used as a key? 4 Encrypted keys are very much more difficult to handle. 4 Can you use a hash checksum instead? 28 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Encryption Without Changing Applications: Techniques § Changes to database schema: 4 Rename all tables containing encrypted data. 4 Change data types for columns that must be encrypted. CHAR data type. q Expanded size. 4 Create views with the old table names: q CREATE VIEW oldname(key, col 2, col 3) AS SELECT key, DECRYPT(col 2): : type 1, DECRYPT(col 3): : type 2 FROM newname; § The hard part is setting the encryption password! q 29 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
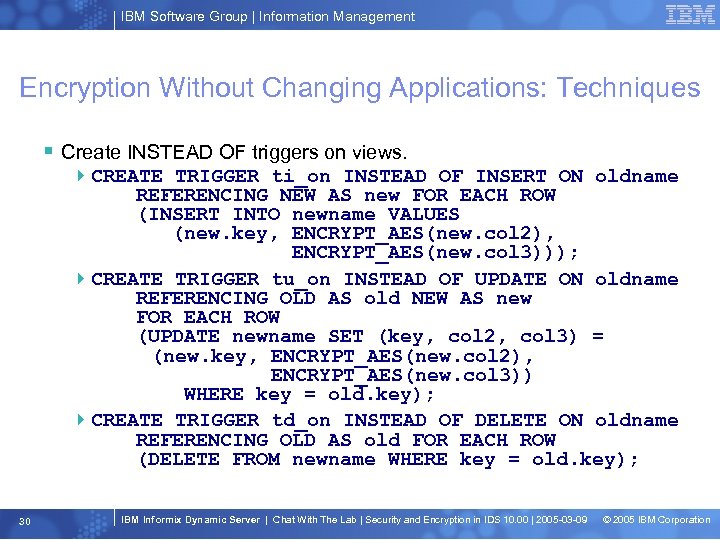
IBM Software Group | Information Management Encryption Without Changing Applications: Techniques § Create INSTEAD OF triggers on views. 4 CREATE TRIGGER ti_on INSTEAD OF INSERT ON oldname REFERENCING NEW AS new FOR EACH ROW (INSERT INTO newname VALUES (new. key, ENCRYPT_AES(new. col 2), ENCRYPT_AES(new. col 3))); 4 CREATE TRIGGER tu_on INSTEAD OF UPDATE ON oldname REFERENCING OLD AS old NEW AS new FOR EACH ROW (UPDATE newname SET (key, col 2, col 3) = (new. key, ENCRYPT_AES(new. col 2), ENCRYPT_AES(new. col 3)) WHERE key = old. key); 4 CREATE TRIGGER td_on INSTEAD OF DELETE ON oldname REFERENCING OLD AS old FOR EACH ROW (DELETE FROM newname WHERE key = old. key); 30 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
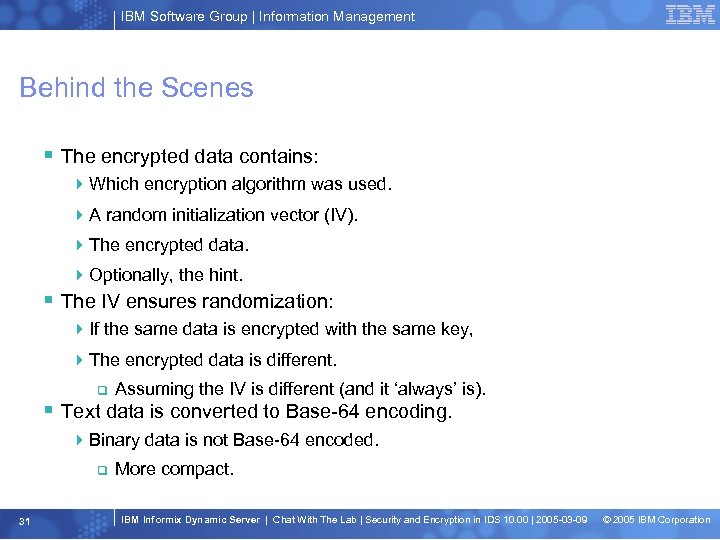
IBM Software Group | Information Management Behind the Scenes § The encrypted data contains: 4 Which encryption algorithm was used. 4 A random initialization vector (IV). 4 The encrypted data. 4 Optionally, the hint. § The IV ensures randomization: 4 If the same data is encrypted with the same key, 4 The encrypted data is different. q Assuming the IV is different (and it ‘always’ is). § Text data is converted to Base-64 encoding. 4 Binary data is not Base-64 encoded. q 31 More compact. IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
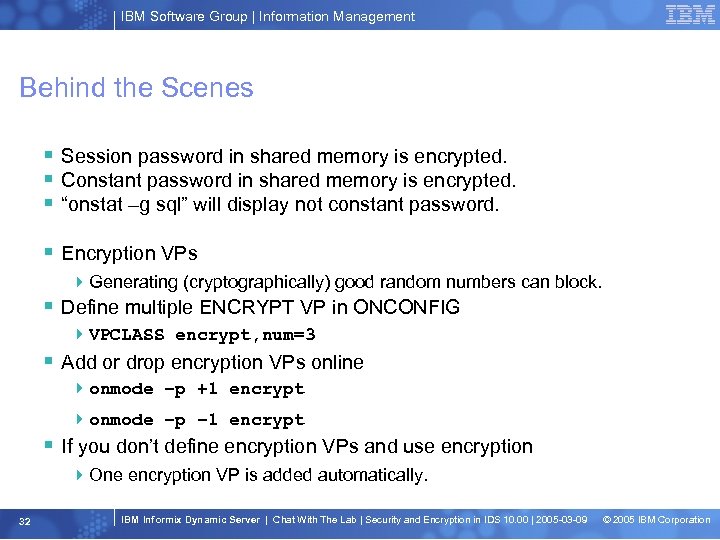
IBM Software Group | Information Management Behind the Scenes § Session password in shared memory is encrypted. § Constant password in shared memory is encrypted. § “onstat –g sql” will display not constant password. § Encryption VPs 4 Generating (cryptographically) good random numbers can block. § Define multiple ENCRYPT VP in ONCONFIG 4 VPCLASS encrypt, num=3 § Add or drop encryption VPs online 4 onmode –p +1 encrypt 4 onmode –p – 1 encrypt § If you don’t define encryption VPs and use encryption 4 One encryption VP is added automatically. 32 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Gotchas § Encrypting BLOB data requires the correct configuration 4 SBSPACE set in ONCONFIG file 4(SYSSBSPACE set in ONCONFIG file, too) 4 If omitted, the errors returned in the initial release are unhelpful. q 33 B 171117 addresses the poor error messages. IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
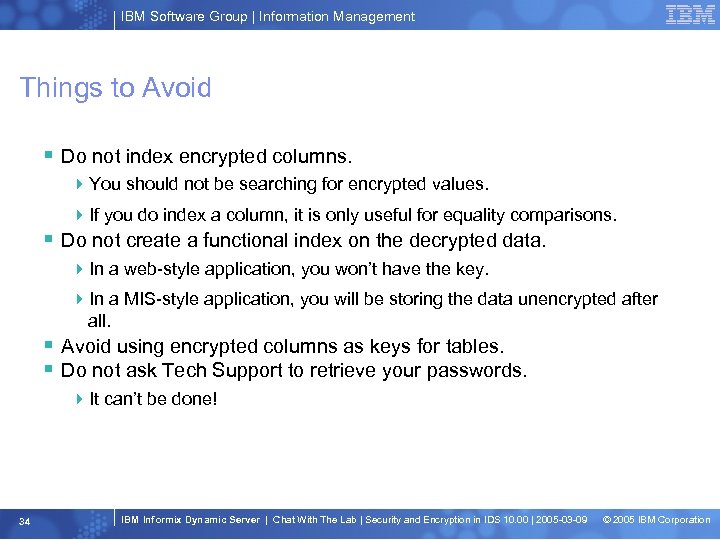
IBM Software Group | Information Management Things to Avoid § Do not index encrypted columns. 4 You should not be searching for encrypted values. 4 If you do index a column, it is only useful for equality comparisons. § Do not create a functional index on the decrypted data. 4 In a web-style application, you won’t have the key. 4 In a MIS-style application, you will be storing the data unencrypted after all. § Avoid using encrypted columns as keys for tables. § Do not ask Tech Support to retrieve your passwords. 4 It can’t be done! 34 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Auditing With IDS – The Forgotten Subsystem § § 35 Which Compliance Regulations? Overview of Auditing in IDS Roles: DBSSO versus AAO Summary IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Which Compliance Regulations? § The answer depends on: 4 Industry 4 Country 4 Application § In the USA 4 HIPAA ‘Health Insurance Portability and Accountability Act’ – 1996 4 Sarbanes-Oxley – 2002 4 Gramm-Leach-Bliley – 1999 4 California SB 1386 ‘Personal Information: Privacy’ – 2002 § Worldwide 4 Basel II – 2001 § Disclaimer: I am not a lawyer – I am not giving you legal advice. 36 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management Overview of Auditing in IDS § Many operations can be audited. 4 All auditable operations have a 4 -letter mnemonic. 4 CREATE DATABASE = CRDB 4 SELECT ROW = RDRW – generates voluminous output! § Audit masks are used to dictate which operations are monitored. 4 Different masks for different people. 4 Global masks – default, require, exclude. 4 Template masks 4 User masks. § Audit logging can be done to operating system audit facilities. 4 Requires server running as root – on Unix only. § Audit logging can be done using Informix audit facilities. 37 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Roles: DBSSO versus AAO § DBSSO controls what is audited. 4 Which users are audited. 4 Which operations are audited for each user. 4 Uses ON-Audit command. q Setting auditing masks. § AAO controls whether auditing is active or not. 4 And how the auditing is recorded. 4 Uses ON-Audit command. § AAO monitors the results of auditing. 4 Uses ON-Show. Audit command. § DBSA runs the server. 4 Should not be able to subvert the auditing set up by DBSSO and AAO. 38 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management Summary of Auditing § Many industries and countries require audit trails 4 For compliance with legal regulations. § IDS has a powerful auditing sub-system 4 Very much under-used in the past. § It is important to understand the DBSSO and AAO roles. 4 They are complementary. § Use ON-Audit to control auditing. 4 DBSSO controls which events are audited for each user. 4 AAO controls whether auditing happens, and where the logs are. § Use ON-Showaudit to monitor what happened. 4 AAO analyzes the audit log files. § Control the audit log files. 4 Log retention policies and clean up. 39 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
IBM Software Group | Information Management http: //www. ibm. com/software/data/informix 40 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation

IBM Software Group | Information Management http: //www. ibm. com/software/data/informix 41 IBM Informix Dynamic Server | Chat With The Lab | Security and Encryption in IDS 10. 00 | 2005 -03 -09 © 2005 IBM Corporation
099934bfc9ac575f996f81f2236f8712.ppt