613811b471496750b7a212943f0baa31.ppt
- Количество слайдов: 22

IBM’s Cryptolopes http: //www-4. ibm. com/software/security/cryptolope/

Overview • A technology for securing intellectual property rights in a distributed environment • Emphasizes security at the document level, not the channel level • Developed for e-commerce settings, IBM has tuned cryptolopes for the digital library market

History • Developers • Developed at IBM. • Proposed by Jeff Crigler and Marc Kaplan [Benton 1996] • Implemented by Kaplan, Josh Auerbach and Chee-Seng Chow • Pursued by Ulrich Kohl, Jeffrey Lotspiech, and Marc A. Kaplan [Kohl et al. 1997]

History • Time line • 1994) Crigler proposes cryptolopes in the context of IBM’s Info. Market service (now defunct? ). i. e. e-commerce origins: The info. Market service is using Cryptolopes to obtain both service revenue, through reselling a wide range of premium business information by the document, and licensing revenue, from companies that set up Cryptolope clearinghouses for defined uses. [Benton 1996] • • 1995) Kaplan delivers initial prototype 1996? ) IBM licenses Xerox PARC’s Digital Property Rights Language (DPRL) for use in Cryptolopes 1997 -98) “Safeguarding Digital Content” series appears in Dlib magazine, describing the motivation and architecture of cryptolopes. Current) Cryptolopes have been integrated into IBM’s digital library management software. • •

Motivation • Superdistribution • Since distributing info is cheap, we should be able to broadcast it in bulk. i. e. Give information away, then charge for the rights to use it. • e. g. Partially functional software downloads • The idea of superdistribution is due to Ryoichi Mori. See Kaplan, Cox [1994].

Motivation • 4 goals of rights management for digital content – Authentication of both provider & reader – Authentication of content – Reader privacy – Superdistribution [Kohl et al. (1997)]

Motivation • Secure documents, open channels • Traditional intellectual property protection invovles secure channels (SSL/SHHTP) • This is fine for purposes of transmission • But doesn’t protect against illegal copying after legal transmission

Motivation • Secure documents, open channels • Instead of protecting the channel, Cryptolopes protect at the document level. • Getting the document is free, but getting access to the document costs. • So give the documents away! i. e. superdistribution!

Motivation • Customizability • Successful rights management depends on the context in which transactions take place. • Content protection must be easily customizable. • Rights management must be automated, and must scale well.
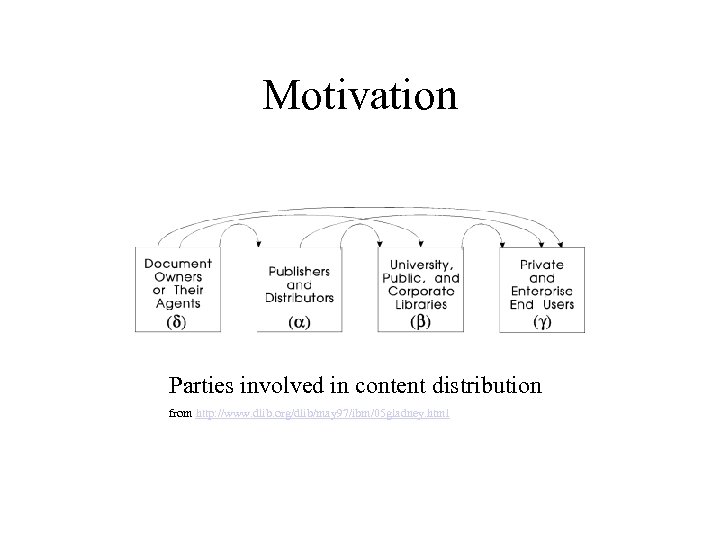
Motivation Parties involved in content distribution from http: //www. dlib. org/dlib/may 97/ibm/05 gladney. html

Analysis • Basic idea of a cryptolope (cryptographic envelope): – Digital content is encrypted by the creator – Encrypted content is bundled into a cryptolope with non -encrypted (clear) metadata and associated authentication material – Encrypted content is freely distributed – Using clear metadata, users decide if they want to “license” the material – If so, users “purchase” decryption key from publisher
Architecture • 3 -tiers • Kohl et al. (1997) and Gladney et al. (1997) describe rights management software utilizing 3 parties • Creator • Publisher • Customer
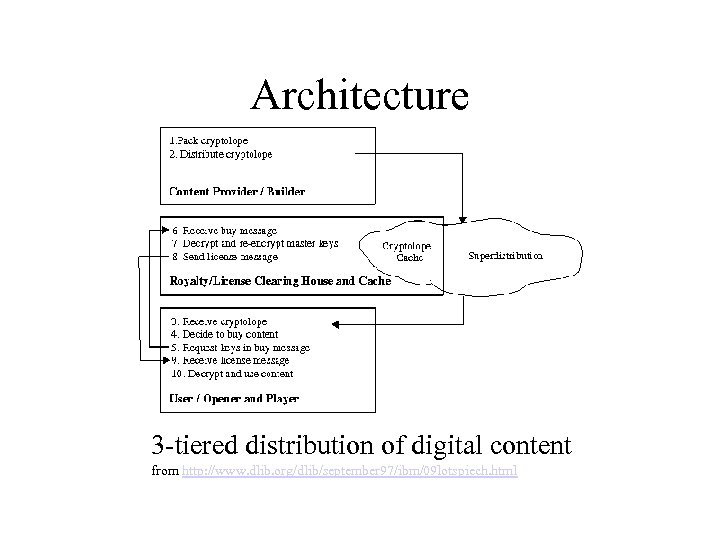
Architecture 3 -tiered distribution of digital content from http: //www. dlib. org/dlib/september 97/ibm/09 lotspiech. html

Architecture • IBM (info. Market) acts as a potential clearing house • Creators may set up their own clearing house servers • [Kohl, et al. (1997)] casts digital libraries as the clearing houses for publishers’ cryptolopes
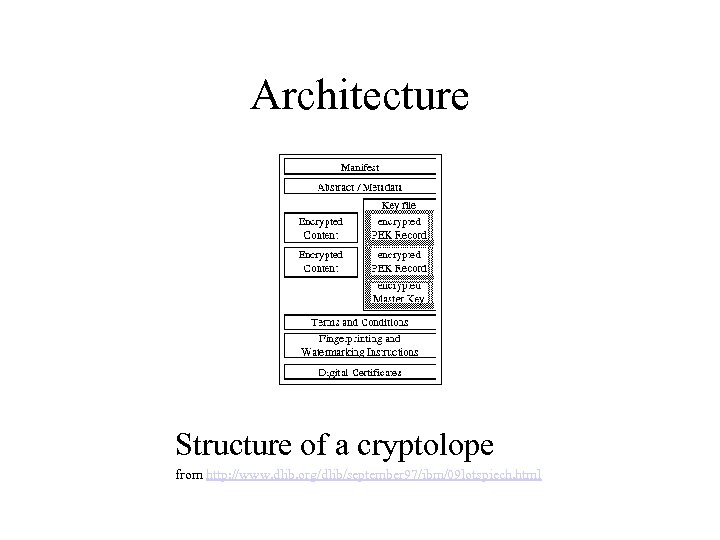
Architecture Structure of a cryptolope from http: //www. dlib. org/dlib/september 97/ibm/09 lotspiech. html

Architecture • Cryptolope structure: important points – Cryptolope contains the keys to its own content – These keys are themselves encoded – Users buy keys for these keys from clearing house – i. e. clearing house only maintains keys for keys, not keys for content – Checksums assure authenticity of content

How does this work? • If a user satisfies T/Cs, he is given the key • Content is decrypted, shown in “special viewer” • Content is authenticated using digital watermark • Content is stamped with a user-specific digital fingerprint

Technical Details • A cryptolope is a *. jar file • Authentication via “X. 509” certificates, a la Verisign…or you can create your own “lightweight certificates. Emphasis on providing just enough security for the distribution context. [See http: //www-4. ibm. com/software/security/cryptolope/about. html for description]

System Requirements • Cryptolope viewer application is available for Win 32 (only successful under NT) • The IBM Digital Library software runs under AIX, Mac. OS, and Win 32. Presumably cryptolope server software does, too…but no mention in IBM docs • IBM Info. Market appears to be defunct (i. e. no readymade clearing house)

Summary • Strengths • Rights management that is flexible regarding: – Level of security – Terms and conditions • Protecting at the document level allows liberal distribution

Summary • Weaknesses • Proprietary viewing software • Reliance on long-term viability of clearing houses • Lack of IBM support

References Benton, P. (1996). “Packaging Information for Superdistribution” IBM Research Magazine. http: //www. research. ibm. com/resources/magazine/1996/issue_3/packinginfo 396. html Cox, Brad. (1994). “Superdistribution. ” Wired. http: //www. wired. com/wired/archive/2. 09/superdis. html Gladney, H. M. and Lotspiech, J. B. “Safeguarding Digital Library Contents and Users: Assuring Convenient Security and Data Quality. ” In D-Lib Magazine, May 1997. http: //www. dlib. org/dlib/may 97/ibm/05 gladney. html Kaplan, Marc A. IBM Cryptolopes, Superdistribution and Digital Rights Management. http: //www. research. ibm. com/people/k/kaplan/cryptolope-docs/crypap. html Ulrich Kohl, Jeffrey Lotspiech, and Marc A. Kaplan, "Safeguarding Digital Library Contents and Users: Protecting Documents Rather Than Channels", in D-lib Magazine, September, 1997. http: //www. dlib. org/dlib/september 97/ibm/09 lotspiech. html
613811b471496750b7a212943f0baa31.ppt