17f3874e61008549fcbfa47698de5386.ppt
- Количество слайдов: 79

IBM Global Technology Services Network: Proventia Intrusion Prevention & Proventia Anomaly Detection IBM Internet Security Systems Ondrej Kovac Technical Sales Specialist Michael Clark Sr. Solution Expert IBM Internet Security Systems Ahead of the threat. ™ © Copyright IBM Corporation 2007
IBM Internet Security Systems Network: Proventia IPS & Proventia ADS - Agenda § Proventia IPS – Ondrej Kovac – Prehľad trhu – Proventia Network IPS: Čo je nové? – High Speed IPS – Predstavenie Proventia GX 6116 NIPS – Site Protector § Proventia ADS – Michael Clark § Proventia Network Roadmap – Čo je nové? © Copyright IBM Corporation 2007

IBM Internet Security Systems Security Market Overview Companies face sophisticated threats and vulnerabilities, and the pressure to achieve and maintain compliance – all with limited resources, time and budget Security Concerns § Sabotage of business information systems § Theft of information or IT assets § Viruses causing productivity slowdowns § Installation of unauthorized hardware and software § System vulnerabilities, including unauthorized access Compliance Considerations § Cost and legal exposure of non-compliance § Poorly established compliance policies, processes and procedures § Lack of effective policy monitoring and compliance reporting © Copyright IBM Corporation 2007
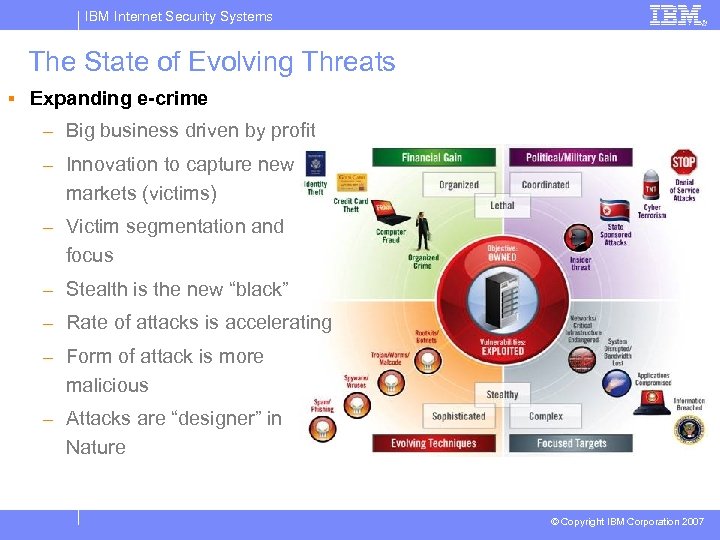
IBM Internet Security Systems The State of Evolving Threats § Expanding e-crime – Big business driven by profit – Innovation to capture new markets (victims) – Victim segmentation and focus – Stealth is the new “black” – Rate of attacks is accelerating – Form of attack is more malicious – Attacks are “designer” in Nature © Copyright IBM Corporation 2007
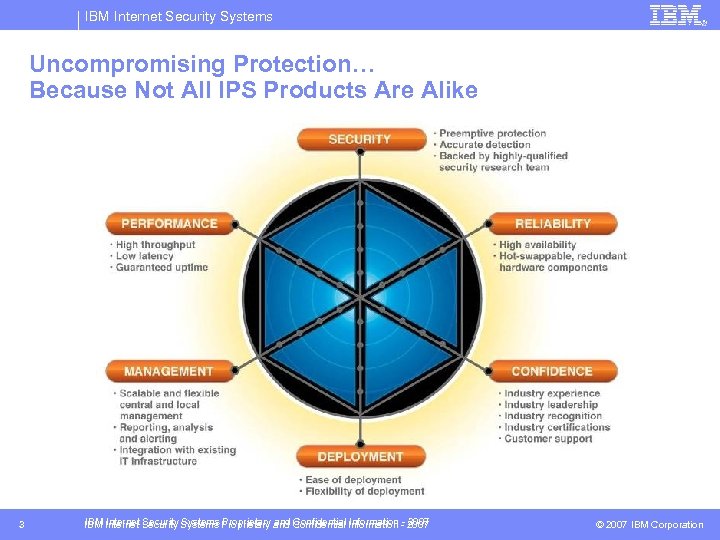
IBM Internet Security Systems Uncompromising Protection… Because Not All IPS Products Are Alike 3 IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
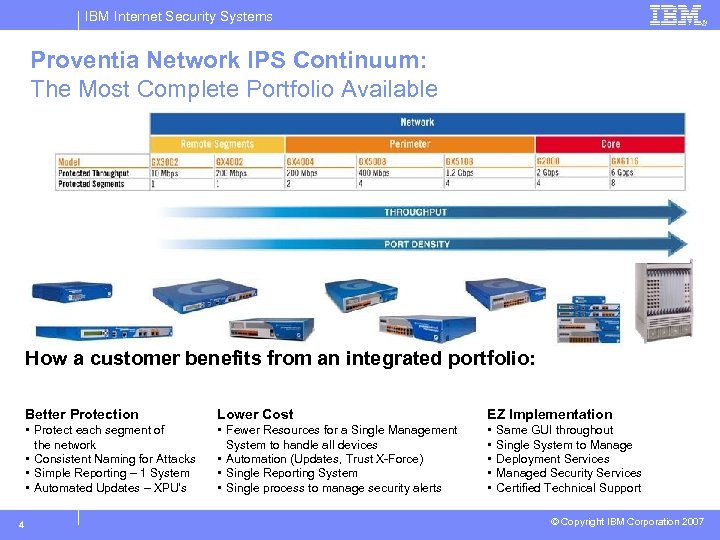
IBM Internet Security Systems Proventia Network IPS Continuum: The Most Complete Portfolio Available How a customer benefits from an integrated portfolio: Better Protection EZ Implementation • Protect each segment of the network • Consistent Naming for Attacks • Simple Reporting – 1 System • Automated Updates – XPU’s 4 Lower Cost • Fewer Resources for a Single Management System to handle all devices • Automation (Updates, Trust X-Force) • Single Reporting System • Single process to manage security alerts • • • Same GUI throughout Single System to Manage Deployment Services Managed Security Services Certified Technical Support © Copyright IBM Corporation 2007

IBM Internet Security Systems Protection for Every Layer of Your Network © Copyright IBM Corporation 2007
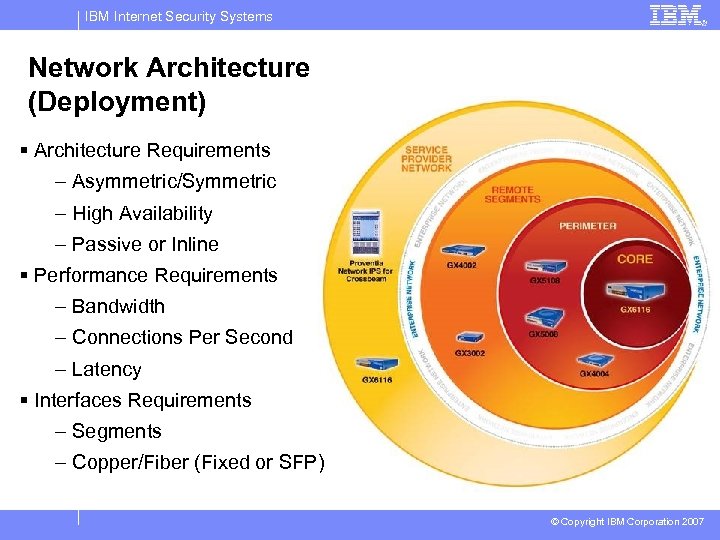
IBM Internet Security Systems Network Architecture (Deployment) § Architecture Requirements – Asymmetric/Symmetric – High Availability – Passive or Inline § Performance Requirements – Bandwidth – Connections Per Second – Latency § Interfaces Requirements – Segments – Copper/Fiber (Fixed or SFP) © Copyright IBM Corporation 2007
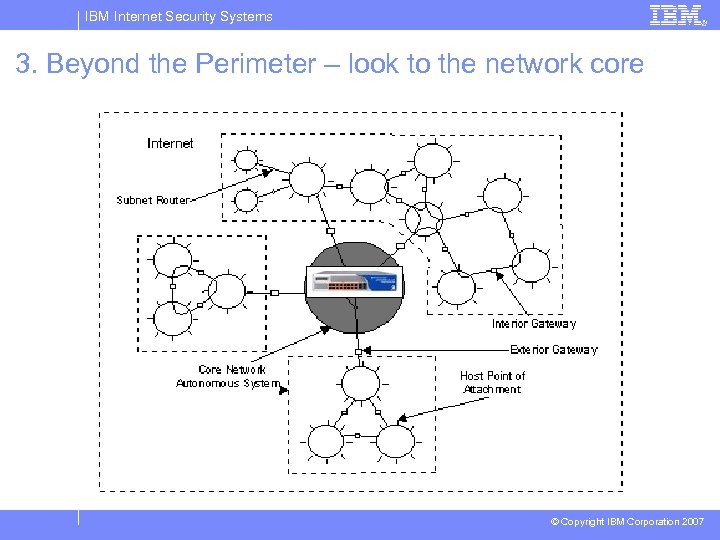
IBM Internet Security Systems 3. Beyond the Perimeter – look to the network core © Copyright IBM Corporation 2007
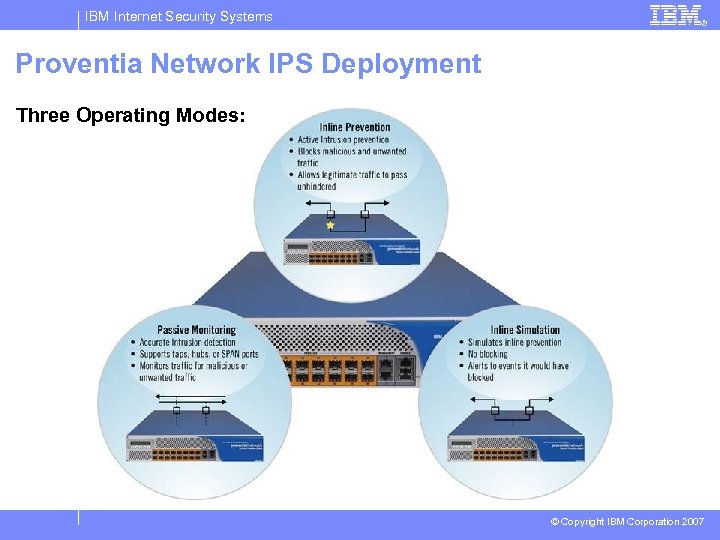
IBM Internet Security Systems Proventia Network IPS Deployment Three Operating Modes: © Copyright IBM Corporation 2007
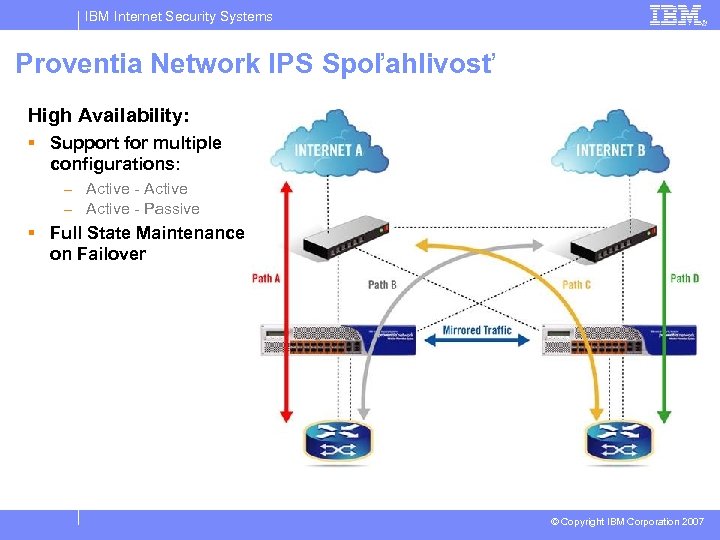
IBM Internet Security Systems Proventia Network IPS Spoľahlivosť High Availability: § Support for multiple configurations: – Active - Active – Active - Passive § Full State Maintenance on Failover © Copyright IBM Corporation 2007
IBM Internet Security Systems Proventia Network IPS Reliability § Active – Active HA – Requires active-active network infrastructure – Maintains your “HA” network design – Supports asymmetrical routing § Will not miss split attacks § Active – Passive HA – Requires active-passive infrastructure – Primary appliance is active and inspecting traffic – If primary is Interrupted secondary appliance becomes active link © Copyright IBM Corporation 2007

IBM Internet Security Systems What’s new? § Proventia GX 3002 – Desktop form factor – 1 protected segment, 10/100 copper ethernet, Integrated bypass – 10 mbps, sub-microsecond latency § Proventia GX 5008 / GX 5108 SFP – Expansion to existing GX 5 product line – 4 protected segments, all SFP interfaces § TX copper, SX / LX fiber § Proventia GX 6116 – NPU powered high speed network IPS – 8 protected segments, all SFP interfaces – 15 gbps throughput, 6 gbps full inspection – Configurable guaranteed maximum latency © Copyright IBM Corporation 2007

IBM Internet Security Systems Helping Enterprises Secure Their Networks § IBM Proventia Network Intrusion Prevention System (IPS) –Transparent, in-line network appliances block attacks while allowing legitimate traffic to flow unhindered –Comprehensive line of models available: § 10 Mbps - 15 Gbps throughput capacity § Up to eight protected network segments § IBM Managed Protection Services Networks for –Deployment –Maintenance –Monitoring –Incident response © Copyright IBM Corporation 2007
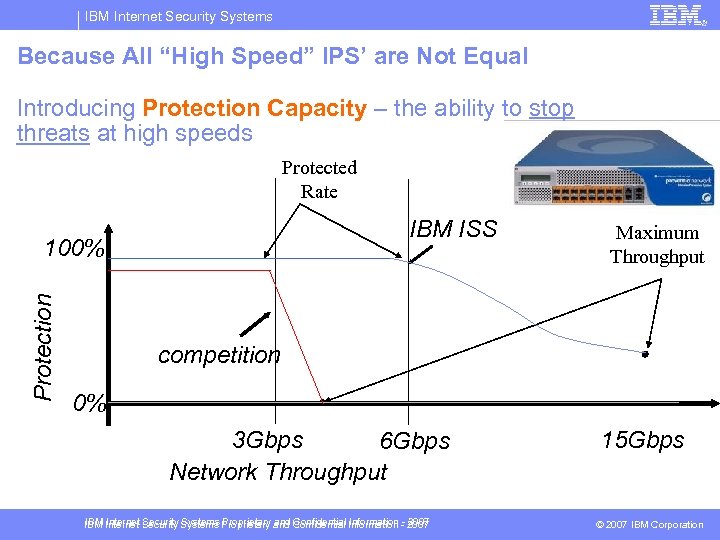
IBM Internet Security Systems Because All “High Speed” IPS’ are Not Equal Introducing Protection Capacity – the ability to stop threats at high speeds Protected Rate IBM ISS Protection 100% Maximum Throughput competition 0% 3 Gbps 6 Gbps Network Throughput IBM Internet Security Systems Proprietary and Confidential Information - 2007 15 Gbps © 2007 IBM Corporation
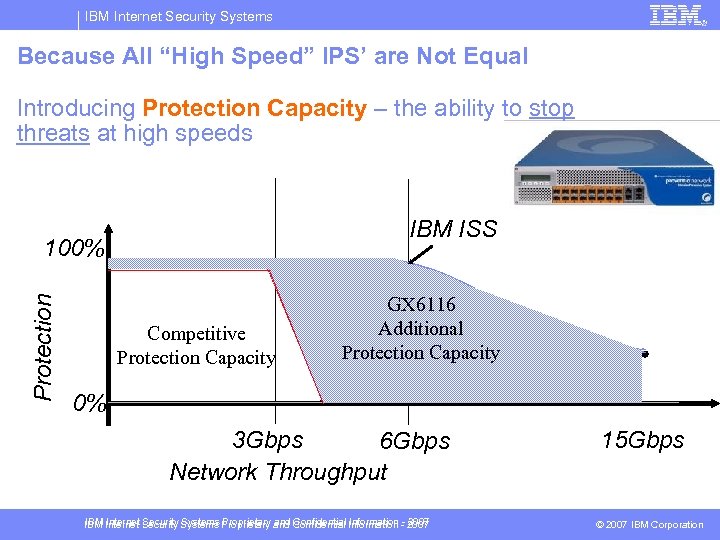
IBM Internet Security Systems Because All “High Speed” IPS’ are Not Equal Introducing Protection Capacity – the ability to stop threats at high speeds IBM ISS Protection 100% Competitive Protection Capacity GX 6116 Additional Protection Capacity 0% 3 Gbps 6 Gbps Network Throughput IBM Internet Security Systems Proprietary and Confidential Information - 2007 15 Gbps © 2007 IBM Corporation
IBM Internet Security Systems Proventia Network IPS Management § Command Control – Site. Protector™ – Proventia Manager (LMI) – Command Line Interface § Policy Management – Do it yourself / Do it for me – Policy per Device – Policy per Port § Intrusion Responses – – – – Block Ignore Log & Log Evidence Email Quarantine SNMP User Defined § Logging – Policy per VLAN Tag – Attack Packet Logging – Policy per IP Address / Range – TCP-Dump – Support for Custom / SNORT Rules TRONS sign. IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
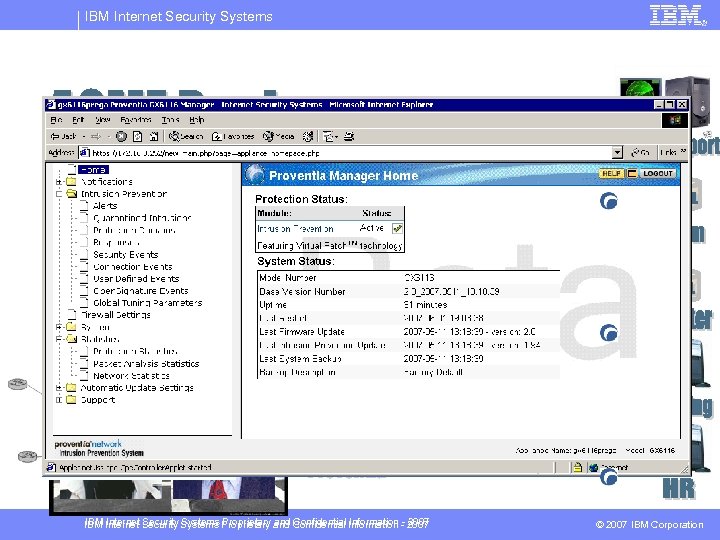
IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
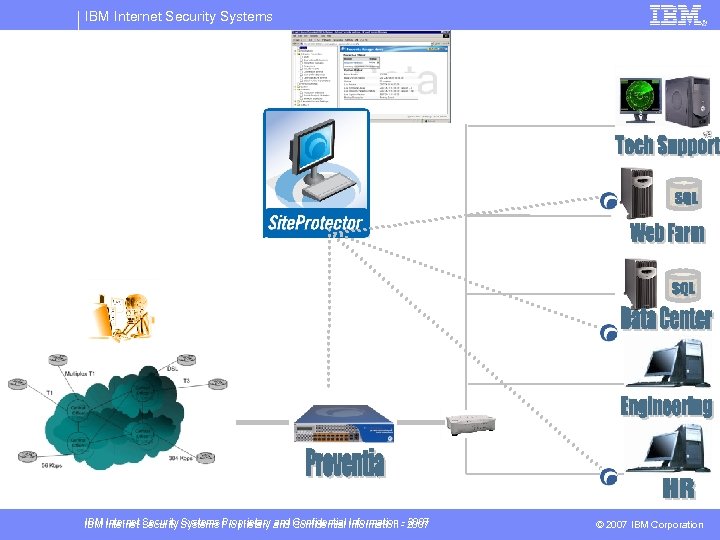
IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
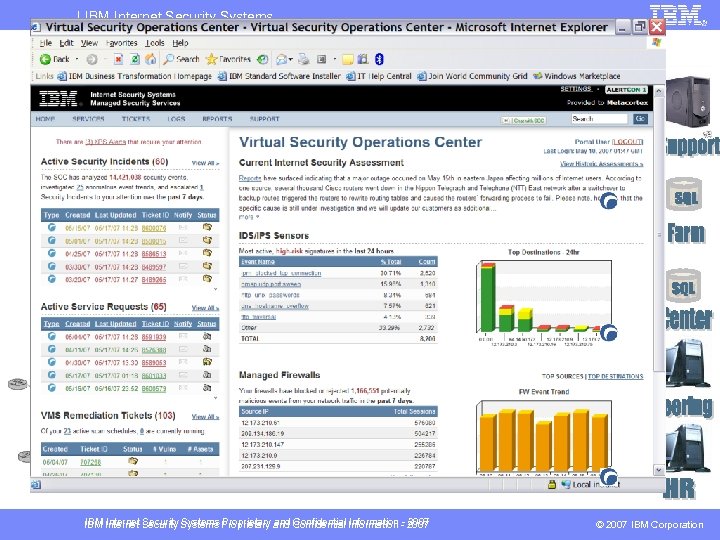
IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
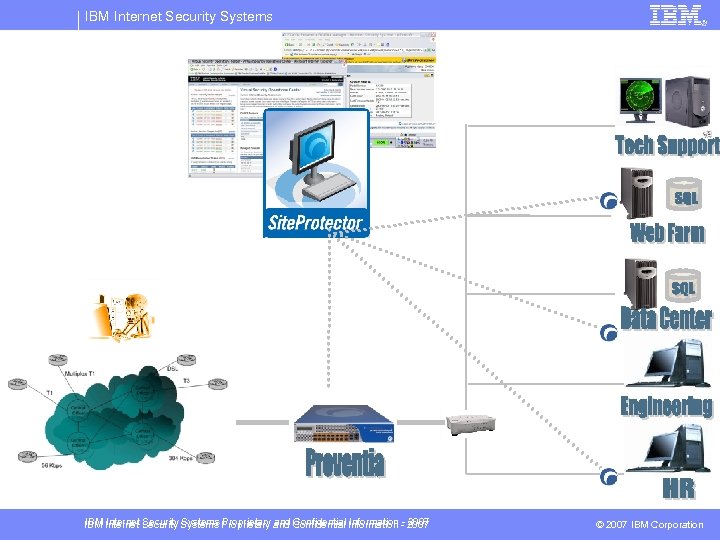
IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Internet Security Systems The GX 6116: Because Your Job Depends Upon the Availability and Reliability of the Network! § Maximum Network Reliability – Configurable maximum latency – Passive Bypass – Active Bypass – High-Availability pairs – IDS and simulation mode – Prioritized network availability Design for The Security Team AND The Network Administrator 7 IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
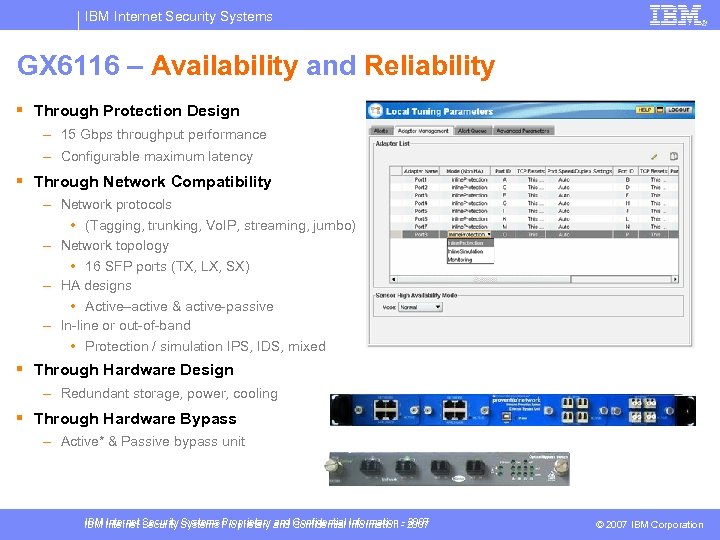
IBM Internet Security Systems GX 6116 – Availability and Reliability § Through Protection Design – 15 Gbps throughput performance – Configurable maximum latency § Through Network Compatibility – Network protocols • (Tagging, trunking, Vo. IP, streaming, jumbo) – Network topology • 16 SFP ports (TX, LX, SX) – HA designs • Active–active & active-passive – In-line or out-of-band • Protection / simulation IPS, IDS, mixed § Through Hardware Design – Redundant storage, power, cooling § Through Hardware Bypass – Active* & Passive bypass unit IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Internet Security Systems GX 6116 – Availability and Reliability § Through Protection Technology – IBM ISS’ Protocol Analysis Module identifies & analyzes more than 173 protocols & data formats – Provide vulnerability-based protection with more than 2, 000 algorithms – Enable Virtual Patching… IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
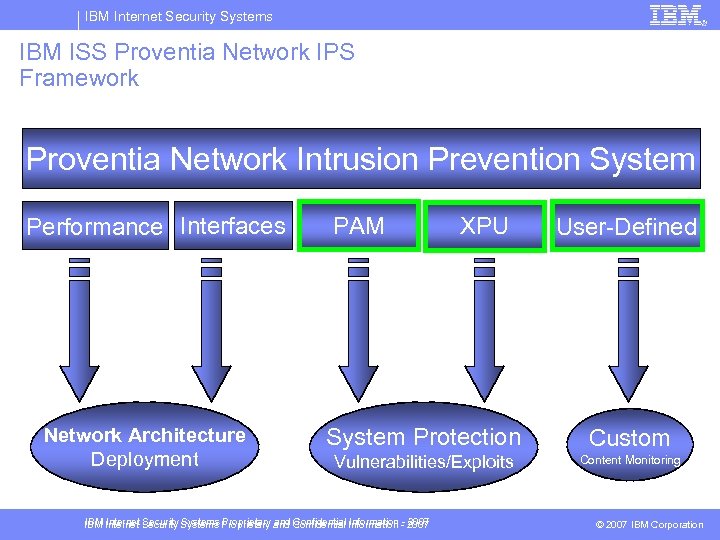
IBM Internet Security Systems IBM ISS Proventia Network IPS Framework Proventia Network Intrusion Prevention System Performance Interfaces Network Architecture Deployment PAM XPU User-Defined System Protection Custom Vulnerabilities/Exploits Content Monitoring IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Reality check – Data Loss Prevention (DLP ) § Employees will transfer data to do their jobs – Whether IT likes it or not – Email / Gmail / IM / You. Send. It. com… § Enterprise IT complexity grows – Planned or unplanned – Wireless routers / notebooks / Starbucks hotspots § Playing “catch up” with security can have devastating results IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
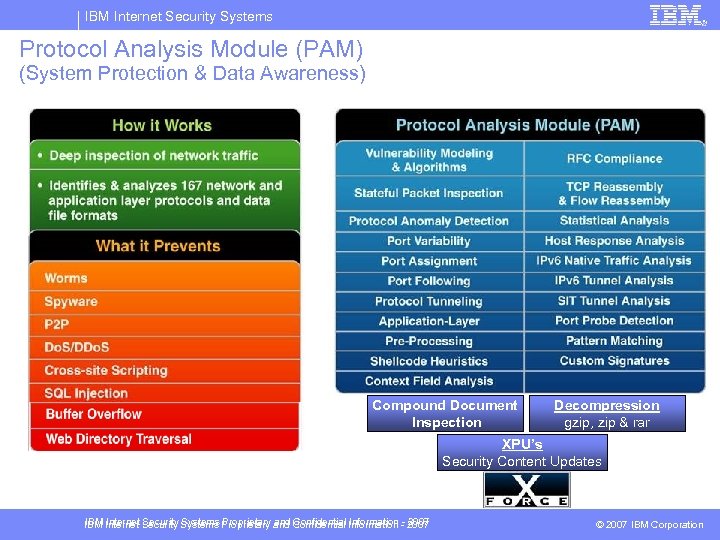
IBM Internet Security Systems Protocol Analysis Module (PAM) (System Protection & Data Awareness) Compound Document Inspection Decompression gzip, zip & rar XPU’s Security Content Updates IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

www. iss. net IBM Global Services Static Demonstration PAM Content Analysis IBM Internet Security Systems ® Ahead of the threat. ™ © 2007 IBM Corporation © 2006 Internet Security Systems. All rights reserved worldwide. Contents are property of Internet Security Systems.
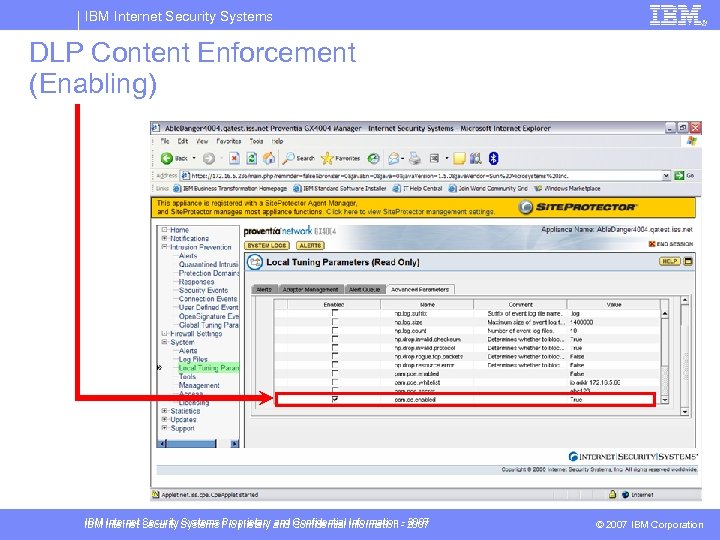
IBM Internet Security Systems DLP Content Enforcement (Enabling) IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
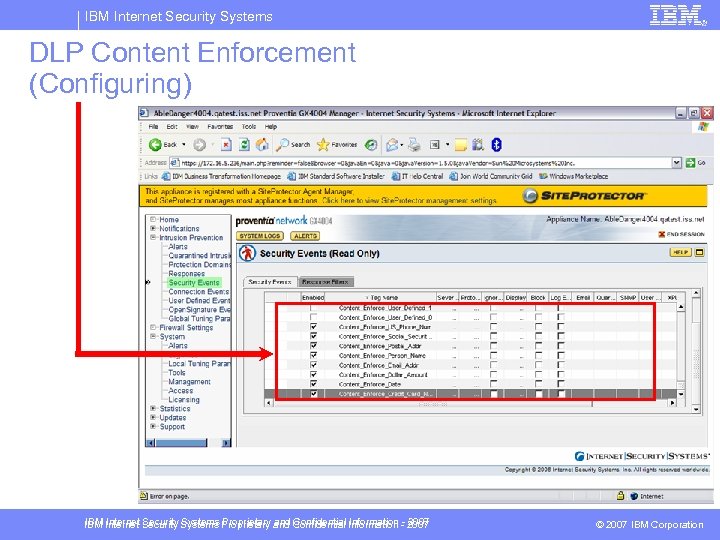
IBM Internet Security Systems DLP Content Enforcement (Configuring) IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Do. S protection from IPS SYN Flood attacks are handled by the Protocol Analysis Module (PAM) and controlled by advanced parameters. Here is the description: § The SYNFlood signature detects a TCP SYN flood attack by monitoring the number and rate of SYN packets that a server receives that do not result in an established connection. You control the triggering connection § rate using two tuning parameters to specify the number of new connection requests and measurement interval. Enabling this signature on Proventia G appliances running in IPS mode will enable SYNFlood protection. § In addition to SYN Floods, we also protect against other forms of Do. S. We also currently have 76 security events related to Do. S § SYNFlood § Stream_Do. S § DNS_Malformed_Flood § ICMP_Flood § Malformed_Packet_Storm IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems MPLS ? § Multiprotocol Label Switching (MPLS) is a data-carrying mechanism which emulates some properties of a circuit-switched network over a packet-switched network. § Our Protocol Analysis Module (PAM) can parse MPLS packets as PAM defined by RFC 3031 and RFC 3032. The MPLS labels are ignored and if the underlying protocols are supported by PAM (such as Ipv 4, IPv 6, etc. ) the attack will be detectet and can be blocked IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems PAM Content Enforcement/Analysis (Frequently Asked Questions) § Does PAM CE replace the need for me to purchase an Enterprise DLP Solution? – No, PAM CE and Network IPS for that matter is a complimentary component of any data security architecture § Does PAM CE index/cache data i. e. ; entire files? – No, we perform packet based inspection targeted for specific Pii and user-defined expressions. However, this type of capability is available in an Enterprise DLP System that is offered by Fidelis (Industry DLP vendor). § Does PAM CE allow inspection for con-joined data-sets i. e. ; User name and SSN? – Yes, we can look for single expressions and con-joined data-sets § Does PAM CE impact performance when enabled? – Yes, there is a cost to running PAM CE and you should expect 15% loss. § Does PAM CE allow me to only monitor for content in HTTP traffic only? – Yes, the interface provides you the capability to target the protocols, content and signatures of your choice. § Does PAM CE provide the capability to inspect attachments that are sent over Yahoo instant messenger? – Yes, PAM CE can inspect the content of the attachment and chat conversation § Does PAM CE provide the capability to alert based on number of signature hits? – Yes, PAM CE provides you the capability to set a minimum match count i. e. ; If I see 8 consecutive SSN then fire an alert IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Internet Security Systems GX 6116 – Availability and reliability § Through Research & Development IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Internet Security Systems The GX 6116: The Task at Hand – Create the Fastest IPS without Compromising Protection 8 IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems The ISS roadmaps drive towards the unification of system security and data security, with full coverage spanning the network, server, and endpoint strategic control points ahead of the threat § Network Protection (IPS, ADS) § Multifunction (UTM) Security § Vulnerability Management § Endpoint and Server Protection § Data and Content Protection …. enabled and enhanced by Enterprise Services “Comprehensive system security and data security delivered and managed through world class services” © Copyright IBM Corporation 2007

IBM Internet Security Systems Network Protection Business Line …. providing world class network protection Client Value – Pre-emptive network security protecting client assets, applications and data § Current Product line – Proventia G § IDS/IPS protecting from SMB to Large Enterprise to Carrier class networks – ADS § Network behavioral analysis to protect against data leakage and the insider threat § Integration with IBM products & services – Integrated with ISS suite of products, services and solutions – Site. Protector management console, Managed Security Services, Tivoli Security Operations Manager (TSOM) – In-process integration – IPS and ADS on Blade. Center § Solutions / Strategy – Data Leakage Protection – ADS to stop the insider threat, IPS with content analysis to stop malicious and accidental compromise – Compliance and Reporting – advanced reporting and business intelligence tools – Carrier and Telco services – products and services geared to enable in the cloud protection § © Copyright IBM Corporation 2007
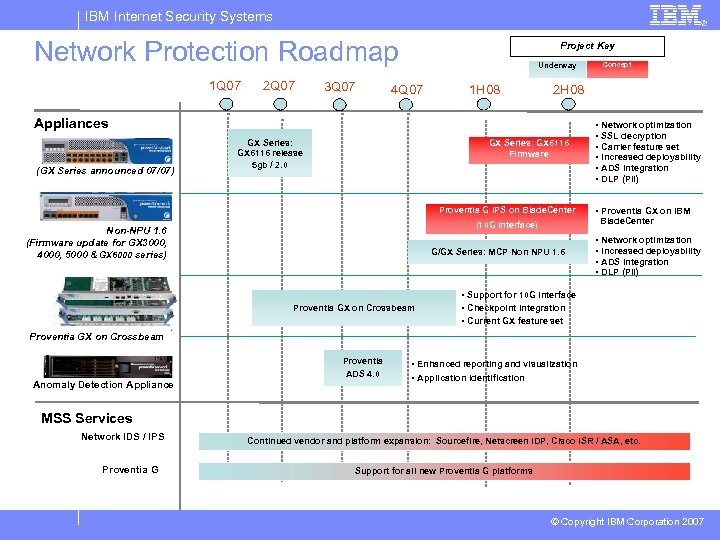
IBM Internet Security Systems Network Protection Roadmap 1 Q 07 2 Q 07 3 Q 07 Project Key Underway 4 Q 07 1 H 08 2 H 08 Appliances (GX Series announced 07/07) GX Series: GX 6116 release 5 gb / 2. 0 GX Series: GX 6116 Firmware Proventia G IPS on Blade. Center G/GX Series: MCP Non NPU 1. 6 Proventia GX on Crossbeam • Network optimization • SSL decryption • Carrier feature set • Increased deployability • ADS integration • DLP (PII) • Proventia GX on IBM Blade. Center (10 G interface) Non-NPU 1. 6 (Firmware update for GX 3000, 4000, 5000 & GX 6000 series) Concept • Network optimization • Increased deployability • ADS integration • DLP (PII) • Support for 10 G interface • Checkpoint integration • Current GX feature set Proventia GX on Crossbeam Proventia ADS 4. 0 Anomaly Detection Appliance • Enhanced reporting and visualization • Application identification MSS Services Network IDS / IPS Proventia G Continued vendor and platform expansion: Sourcefire, Netscreen IDP, Cisco ISR / ASA, etc. Support for all new Proventia G platforms © Copyright IBM Corporation 2007
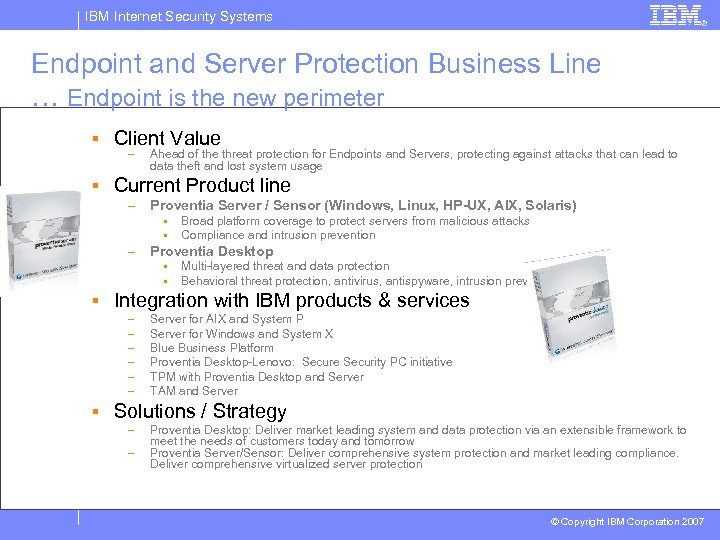
IBM Internet Security Systems Endpoint and Server Protection Business Line … Endpoint is the new perimeter § Client Value – Ahead of the threat protection for Endpoints and Servers, protecting against attacks that can lead to data theft and lost system usage § Current Product line – Proventia Server / Sensor (Windows, Linux, HP-UX, AIX, Solaris) § § – Broad platform coverage to protect servers from malicious attacks Compliance and intrusion prevention Proventia Desktop § § Multi-layered threat and data protection Behavioral threat protection, antivirus, antispyware, intrusion prevention § Integration with IBM products & services – – – Server for AIX and System P Server for Windows and System X Blue Business Platform Proventia Desktop-Lenovo: Secure Security PC initiative TPM with Proventia Desktop and Server TAM and Server § Solutions / Strategy – – Proventia Desktop: Deliver market leading system and data protection via an extensible framework to meet the needs of customers today and tomorrow Proventia Server/Sensor: Deliver comprehensive system protection and market leading compliance. Deliver comprehensive virtualized server protection © Copyright IBM Corporation 2007
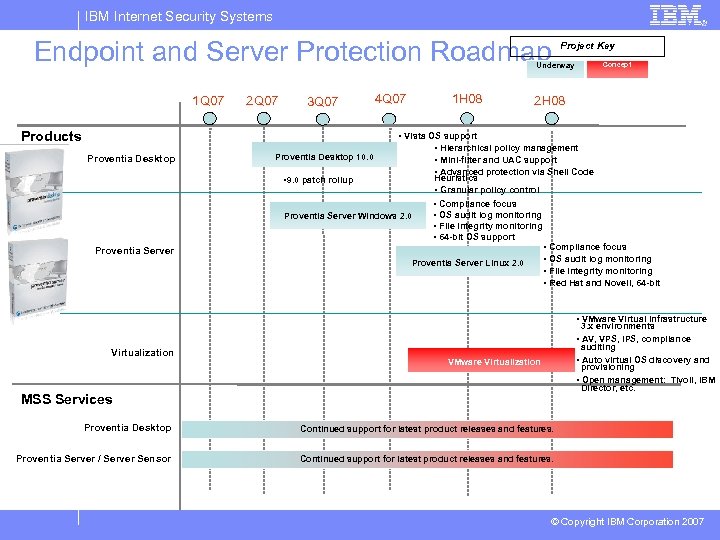
IBM Internet Security Systems Endpoint and Server Protection Roadmap Project Key Concept Underway 1 Q 07 2 Q 07 3 Q 07 Products Proventia Desktop 10. 0 • 9. 0 patch rollup 4 Q 07 1 H 08 2 H 08 • Vista OS support • Hierarchical policy management • Mini-filter and UAC support • Advanced protection via Shell Code Heuristics • Granular policy control Proventia Server Windows 2. 0 • Compliance focus • OS audit log monitoring • File integrity monitoring • 64 -bit OS support Proventia Server Linux 2. 0 • Compliance focus • OS audit log monitoring • File integrity monitoring • Red Hat and Novell, 64 -bit • VMware Virtual Infrastructure 3. x environments • AV, VPS, IPS, compliance Virtualization auditing • Auto virtual OS discovery and VMware Virtualization provisioning • Open management: Tivoli, IBM Director, etc. MSS Services Proventia Desktop Continued support for latest product releases and features. Proventia Server / Server Sensor Continued support for latest product releases and features. © Copyright IBM Corporation 2007
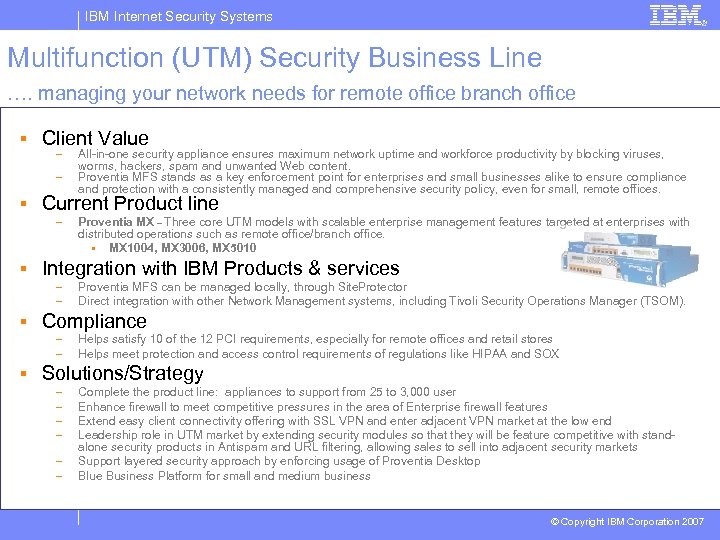
IBM Internet Security Systems Multifunction (UTM) Security Business Line …. managing your network needs for remote office branch office § Client Value – – All-in-one security appliance ensures maximum network uptime and workforce productivity by blocking viruses, worms, hackers, spam and unwanted Web content. Proventia MFS stands as a key enforcement point for enterprises and small businesses alike to ensure compliance and protection with a consistently managed and comprehensive security policy, even for small, remote offices. § Current Product line – Proventia MX – Three core UTM models with scalable enterprise management features targeted at enterprises with distributed operations such as remote office/branch office. § MX 1004, MX 3006, MX 5010 § Integration with IBM Products & services – – Proventia MFS can be managed locally, through Site. Protector Direct integration with other Network Management systems, including Tivoli Security Operations Manager (TSOM). § Compliance – – Helps satisfy 10 of the 12 PCI requirements, especially for remote offices and retail stores Helps meet protection and access control requirements of regulations like HIPAA and SOX § Solutions/Strategy – – – Complete the product line: appliances to support from 25 to 3, 000 user Enhance firewall to meet competitive pressures in the area of Enterprise firewall features Extend easy client connectivity offering with SSL VPN and enter adjacent VPN market at the low end Leadership role in UTM market by extending security modules so that they will be feature competitive with standalone security products in Antispam and URL filtering, allowing sales to sell into adjacent security markets Support layered security approach by enforcing usage of Proventia Desktop Blue Business Platform for small and medium business © Copyright IBM Corporation 2007
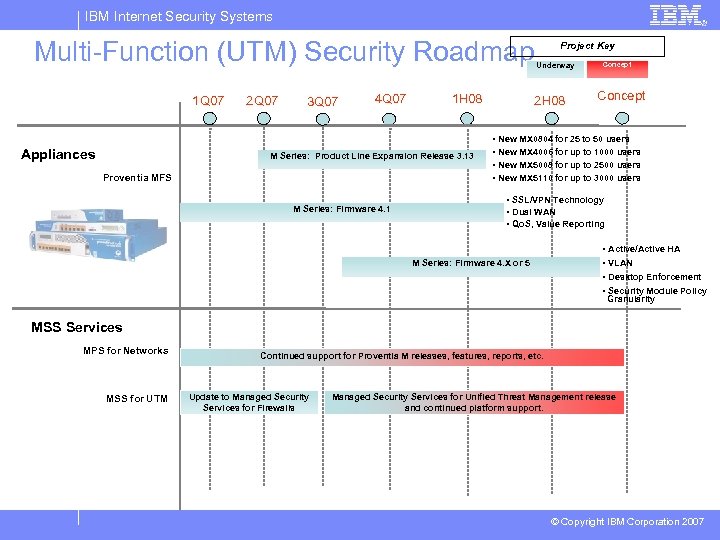
IBM Internet Security Systems Multi-Function (UTM) Security Roadmap 1 Q 07 Appliances 2 Q 07 3 Q 07 4 Q 07 1 H 08 M Series: Product Line Expansion Release 3. 13 Proventia MFS M Series: Firmware 4. 1 Project Key Underway 2 H 08 Concept • New MX 0804 for 25 to 50 users • New MX 4006 for up to 1000 users • New MX 5008 for up to 2500 users • New MX 5110 for up to 3000 users • SSL/VPN Technology • Dual WAN • Qo. S, Value Reporting M Series: Firmware 4. X or 5 • Active/Active HA • VLAN • Desktop Enforcement • Security Module Policy Granularity MSS Services MPS for Networks MSS for UTM Continued support for Proventia M releases, features, reports, etc. Update to Managed Security Services for Firewalls Managed Security Services for Unified Threat Management release and continued platform support. © Copyright IBM Corporation 2007
IBM Internet Security Systems Vulnerability Management Business Line …. managing your network vulnerability needs § Client Value – Ensure the availability of IT services, while protecting corporate data by identifying where risk exists, prioritizing and assigning protection activities, and reporting on results. § Current Product line – – Internet Scanner (IS) – Software-based network vulnerability assessment product servicing the Audit and Vulnerability Management markets Enterprise Scanner (ES) – Appliance-based network vulnerability assessment product servicing the Vulnerability Management Markets § ES 750 (Sept 07) § ES 1500 (3 Q 06) § Integration with IBM products & services – Interface to Site Protector which in turn interfaces to Tivoli Security Operations Manager (TSOM) § Strategy / Solutions – – – Competitive enhancements to ES § Added functionality § PCI certification (security checks and reports) Expansion of assessment capabilities to include application and database vulnerability scanners Integration of network, application and database scans to facilitate Overall Risk Management © Copyright IBM Corporation 2007
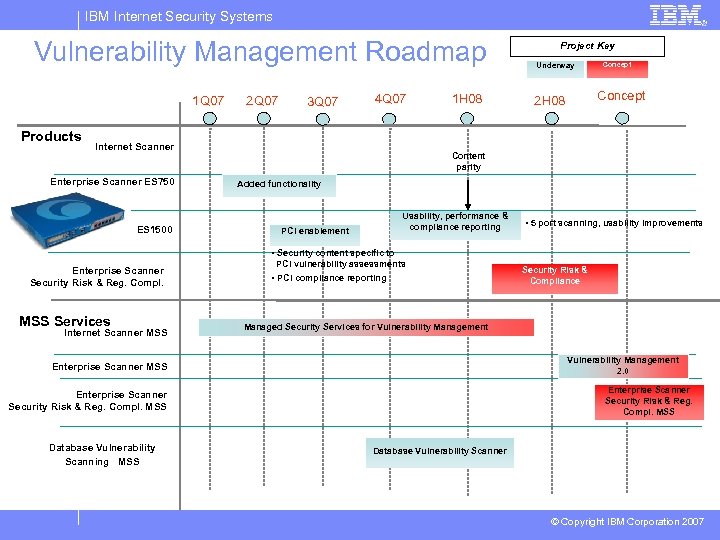
IBM Internet Security Systems Vulnerability Management Roadmap 1 Q 07 Products 2 Q 07 3 Q 07 4 Q 07 Internet Scanner Enterprise Scanner ES 750 ES 1500 1 H 08 Project Key Underway Concept 2 H 08 Content parity Added functionality Usability, performance & compliance reporting PCI enablement • 5 port scanning, usability improvements • Security content specific to Enterprise Scanner Security Risk & Reg. Compl. MSS Services Internet Scanner MSS PCI vulnerability assessments • PCI compliance reporting Managed Security Services for Vulnerability Management 2. 0 Enterprise Scanner MSS Enterprise Scanner Security Risk & Reg. Compl. MSS Database Vulnerability Scanning MSS Security Risk & Compliance Database Vulnerability Scanner © Copyright IBM Corporation 2007

IBM Internet Security Systems Data Security and Content Business Line … enabling collaboration while mitigating risk § Client Value – Safeguarding data across the enterprise, facilitating content awareness, enabling Security & Privacy compliance, monitoring data flows, optimizing control, leveraging industry expertise & best practices to ensure access while preventing data loss § Current Product & Services Line – – Proventia Network Mail § MS 3004 Appliance (launched August 2006) § MS 1002 -VM Virtual Appliance (launched August 2007) Proventia Mail Filter software (July 2004) § Formerly Cobion Orange. Box Mail software (March 2003) Proventia Web Filter software (July 2004) § Formerly Cobion Orange. Box Web software (2002) OEM Business – 30 Active Email and Web content security partners § Includes 5 of the 20 vendors on 2007 Gartner Secure Web Gateway MQ including market leader § Mail Security and UTM vendors also represented in OEM relationships § Integration with other IBM products & services § Solutions/ Strategy – – – Hardware Line Expansion for Mail Security Appliance line – 2008 Secure Browsing – securing transactions regardless of system state Content Protection Appliance – 2008 (HTTP, HTTPS, FTP, IM, P 2 P content gateway inspection) Content Scanning Services and Risk Assessments Brand / Logo Identification Service DLP (Data Loss Prevention Services) including granular controls based on content & context and integration with other components of Enterprise Content Protection such as desktop agents and gateway filters for holistic protection © Copyright IBM Corporation 2007
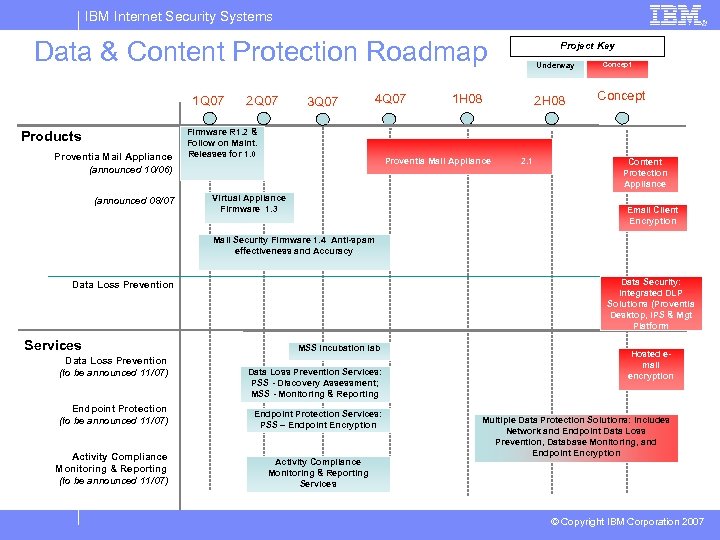
IBM Internet Security Systems Data & Content Protection Roadmap 1 Q 07 Products Proventia Mail Appliance (announced 10/06) (announced 08/07 2 Q 07 3 Q 07 4 Q 07 Firmware R 1. 2 & Follow on Maint. Releases for 1. 0 Underway 1 H 08 Proventia Mail Appliance Virtual Appliance Firmware 1. 3 Project Key 2 H 08 2. 1 Concept Content Protection Appliance Email Client Encryption Mail Security Firmware 1. 4 Anti-spam effectiveness and Accuracy Data Security: Integrated DLP Solutions (Proventia Desktop, IPS & Mgt Platform Data Loss Prevention Services Data Loss Prevention (to be announced 11/07) MSS Incubation lab Data Loss Prevention Services: PSS - Discovery Assessment; MSS - Monitoring & Reporting Endpoint Protection (to be announced 11/07) Endpoint Protection Services: PSS – Endpoint Encryption Activity Compliance Monitoring & Reporting (to be announced 11/07) Activity Compliance Monitoring & Reporting Services Hosted email encryption Multiple Data Protection Solutions: Includes Network and Endpoint Data Loss Prevention, Database Monitoring, and Endpoint Encryption © Copyright IBM Corporation 2007

IBM Internet Security Systems Enterprise Services Business Line …solving business problems through flexible service delivery § Client Value – Comprehensive, adaptable services designed to reduce operational overhead, demonstrate compliance, improve security posture, and guarantee protection at the network, server, and desktop level. § Current Offerings – – – – Managed Protection Services (MPS) – Guaranteed protection offerings based on industry leading IBM ISS technology at the Network, Server, and Desktop. Managed Security Services (MSS) – From fully managed to fully monitored, support for best of breed Firewall, VPS, IPS, AV, AS, from leading vendors – ISS, Cisco, Checkpoint, Juniper, 3 Com, Mc. Afee, Fortinet, Sourcefire, etc. Security Enablement Services – Turn-key solutions delivering on-demand protection when you need it without the need for additional hardware or software deployment. Includes SELM, VMS, and XFTAS. Professional Security Services (PSS) – In depth Professional Services designed to provide regulatory certification, security assessment / implementation, and full scale penetration testing. Education and Training Services – Comprehensive instructor led training and e-learning offerings designed around IBM ISS technology and security best practices. Emergency Response Services – 24 x 7 emergency response capabilities forensic analysis and investigation, evidence preservation, and expert witnessing. Proventia Management Site. Protector – Provides the industry’s most comprehensive centralized security management tool, designed to simplify management functions while expanding visibility into critical security issues. § Strategy – – – – Service Provider offering portfolio expansion. On-Demand services launch – after hours monitoring for the Security Event and Log Management offering. Security Event and Log Management enhancements for extended regulatory compliance capabilities. Improved Vulnerability Management service with support for Ent. Scanner, PCI compliance, and enhanced usability. Data protection services – Data Loss Prevention, database monitoring, encryption, etc. Enhanced Site. Protector release to include world class business intelligence capabilities. Introduction of new e-learning capabilities delivering IBM ISS education in an always-on, online classroom. © Copyright IBM Corporation 2007
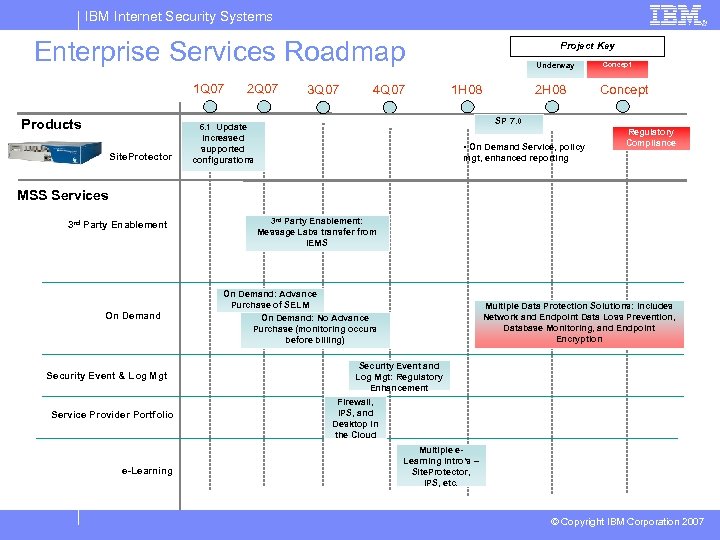
IBM Internet Security Systems Enterprise Services Roadmap 1 Q 07 Products Site. Protector 2 Q 07 3 Q 07 4 Q 07 Project Key Underway 1 H 08 2 H 08 Concept SP 7. 0 6. 1 Update increased supported configurations • On Demand Service, policy Regulatory Compliance mgt, enhanced reporting MSS Services 3 rd Party Enablement On Demand Security Event & Log Mgt Service Provider Portfolio e-Learning 3 rd Party Enablement: Message Labs transfer from IEMS On Demand: Advance Purchase of SELM On Demand: No Advance Purchase (monitoring occurs before billing) Multiple Data Protection Solutions: Includes Network and Endpoint Data Loss Prevention, Database Monitoring, and Endpoint Encryption Security Event and Log Mgt: Regulatory Enhancement Firewall, IPS, and Desktop in the Cloud Multiple e. Learning intro’s – Site. Protector, IPS, etc. © Copyright IBM Corporation 2007
IBM Internet Security Systems More information § Visit us at www. ibm. com Solutions by business need: Security Internet Security Systems (http: //www-935. ibm. com/services/us/index. wss/offerfamily/igs/a 1025846) IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
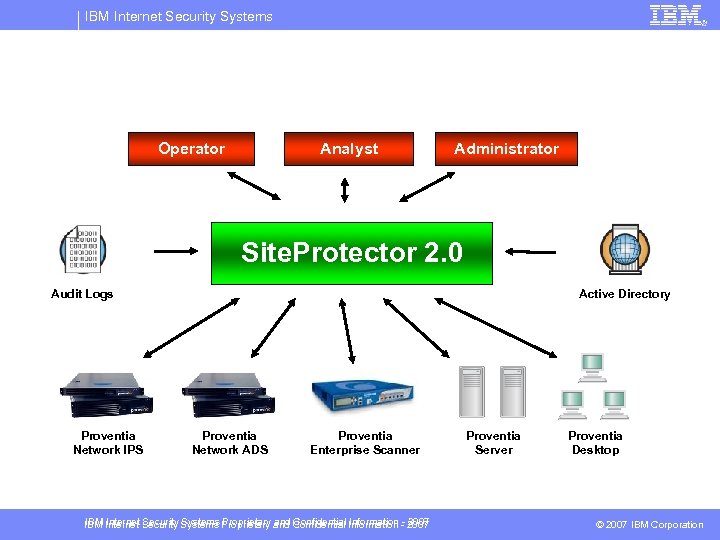
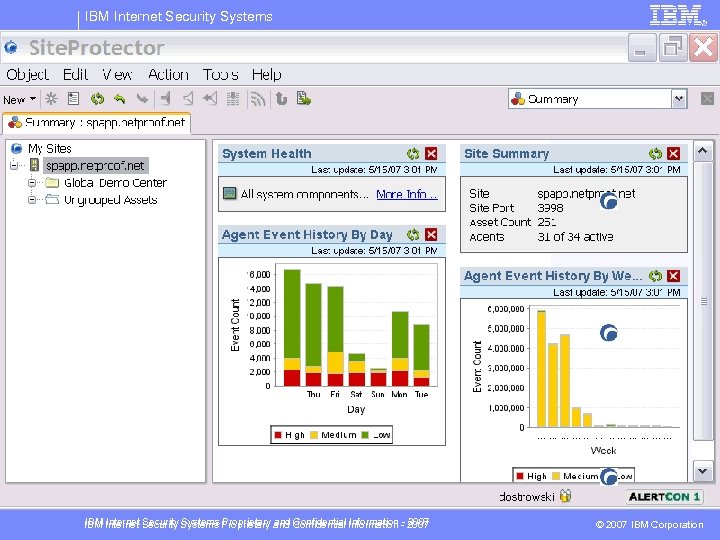
IBM Internet Security Systems Operator Analyst Administrator Site. Protector 2. 0 Audit Logs Proventia Network IPS Active Directory Proventia Network ADS Proventia Enterprise Scanner IBM Internet Security Systems Proprietary and Confidential Information - 2007 Proventia Server Proventia Desktop © 2007 IBM Corporation
IBM Internet Security Systems Real. Secure Site. Protector IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Useful Vulnerability Information IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
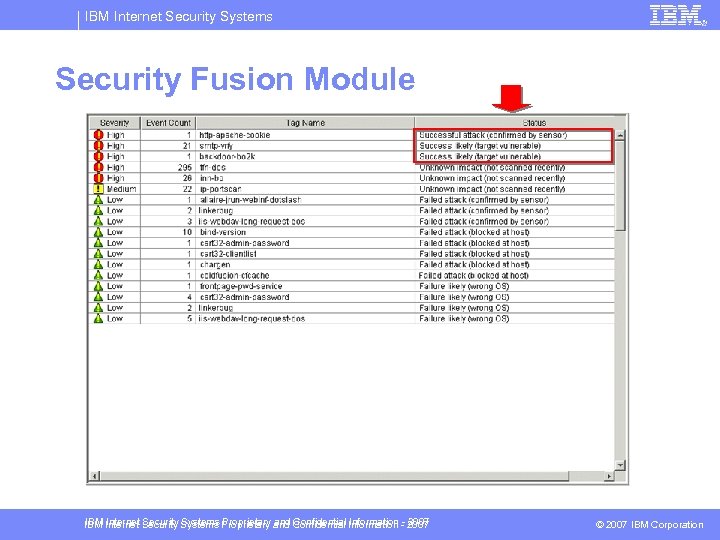
IBM Internet Security Systems Security Fusion Module IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
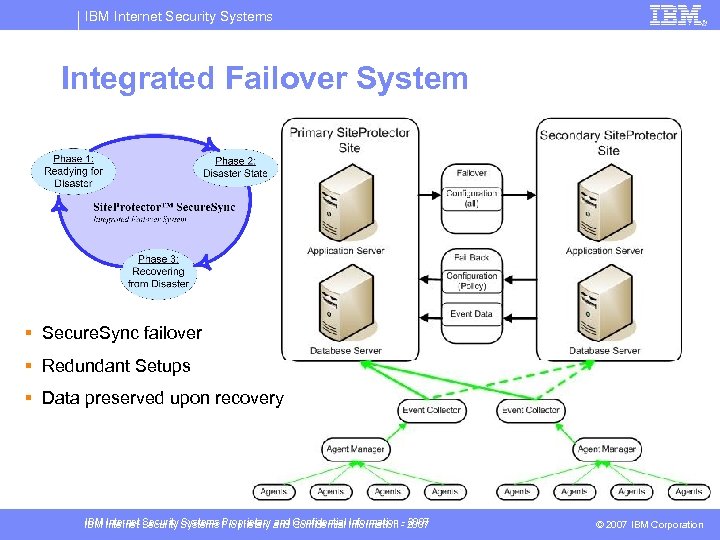
IBM Internet Security Systems Integrated Failover System § Secure. Sync failover § Redundant Setups § Data preserved upon recovery IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
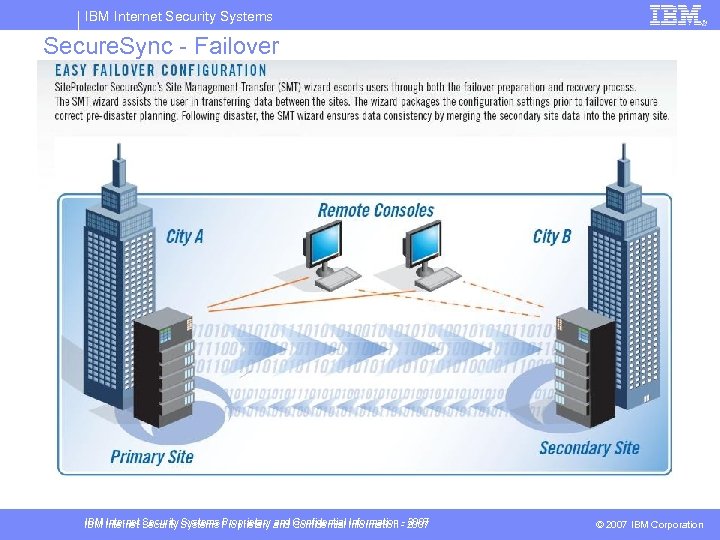
IBM Internet Security Systems Secure. Sync - Failover IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Internet Security Systems Enterprise Security Management § § § § § Built-in ticketing system and API Active Directory import and query, ex. user logged on Forensics – event details, packet capture, and TCPdump Event Filters – based source and destination IP addresses Event Throttling – limit to one event every X seconds Central Responses – based on multi-sensor thresholds Asset orientation – value, owner, department, etc. Customizable Analysis Views can be saved and shared Virtually all operations can be scheduled IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
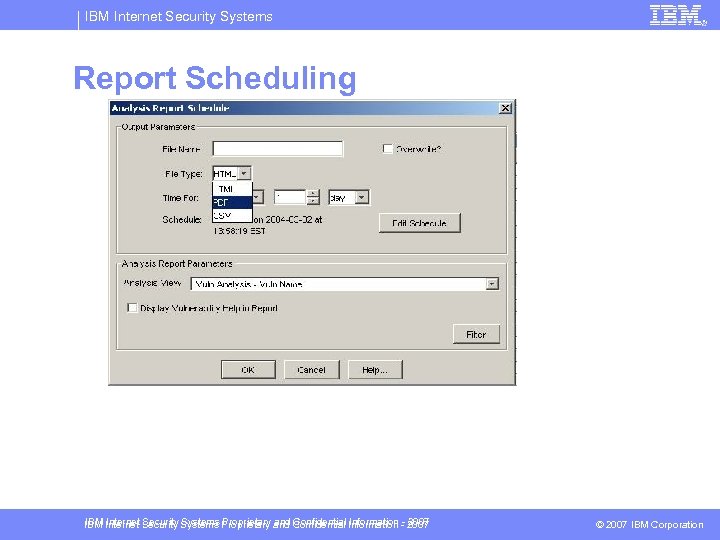
IBM Internet Security Systems Report Scheduling IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
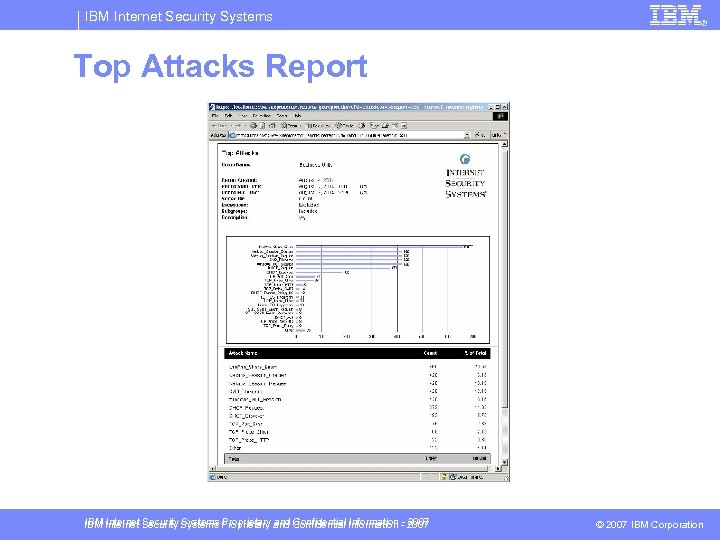
IBM Internet Security Systems Top Attacks Report IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
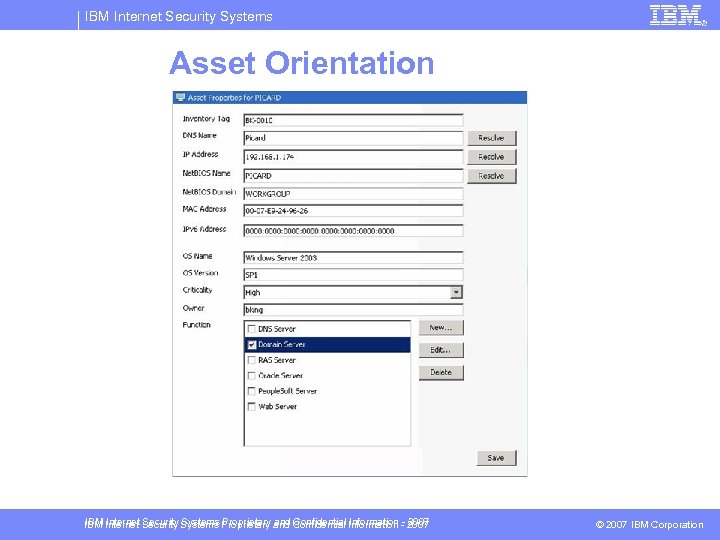
IBM Internet Security Systems Asset Orientation IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
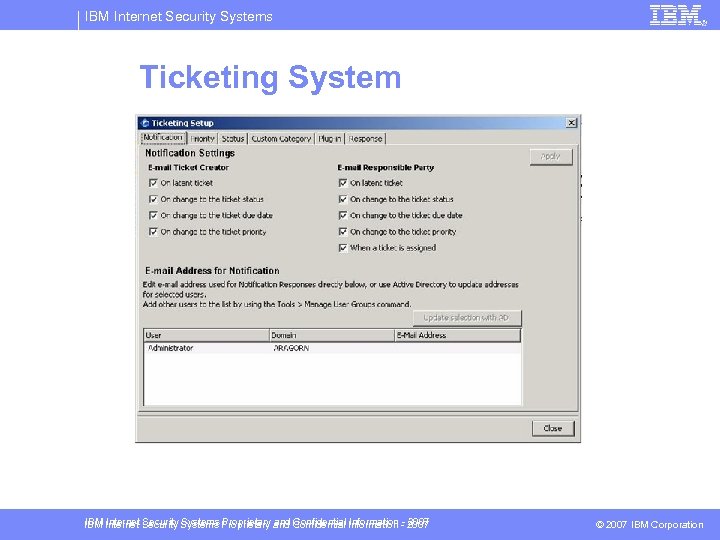
IBM Internet Security Systems Ticketing System IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
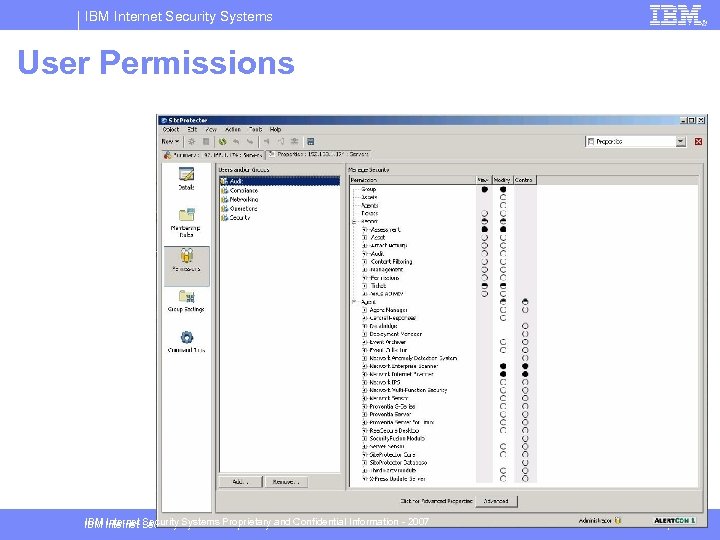
IBM Internet Security Systems User Permissions IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
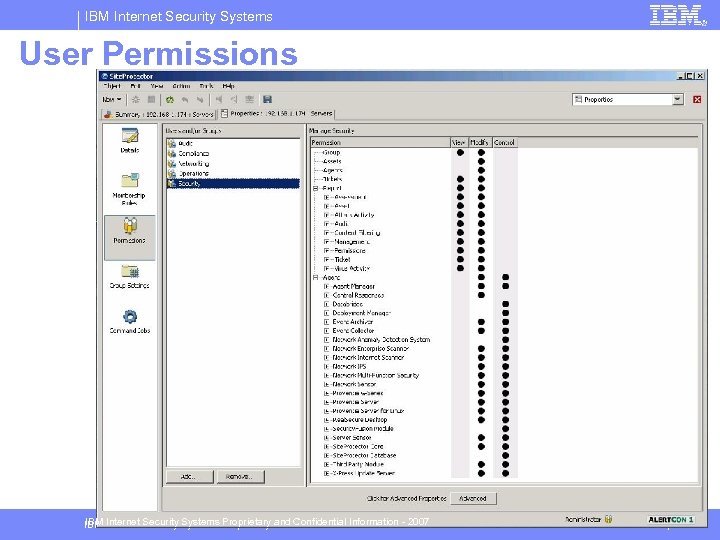
IBM Internet Security Systems User Permissions IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Site. Protector Appliance § Embedded Windows software § LCD for initial setup and configuration § Microsoft updates delivered as firmware XPUs § Full remote system administration IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

www. iss. net IBM Global Services Proventia One. Trust Overview IBM Internet Security Systems ® Ahead of the threat. ™ © 2007 IBM Corporation © 2006 Internet Security Systems. All rights reserved worldwide. Contents are property of Internet Security Systems.

IBM Internet Security Systems Proventia Licensing: One. Trust The problem: "Licensing terms and complexity affect us. We have to have an internal person focusing on licensing, so simplification is huge“ "If they can simplify licensing, it will make it easier for customers to buy software through partners. “ Proventia One. Trust reduces the TCO - total cost of ownership for Internet Security Systems’ products by accelerating security deployment and minimizing license management by enabling all ISS products to run using a single token IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
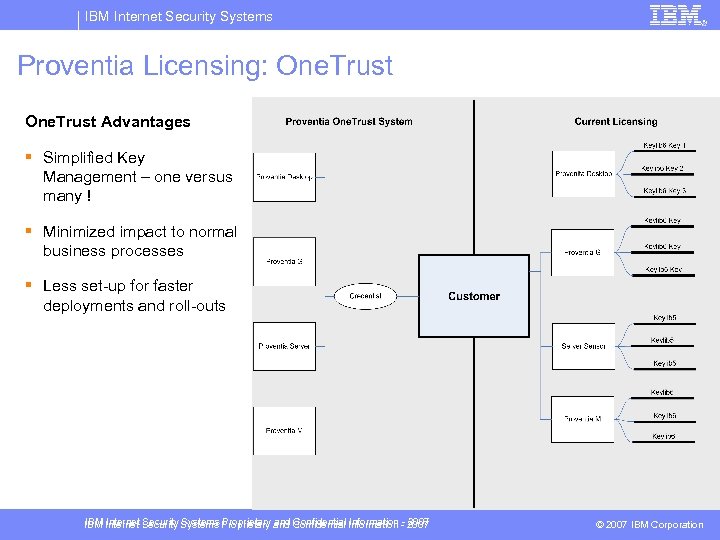
IBM Internet Security Systems Proventia Licensing: One. Trust Advantages § Simplified Key Management – one versus many ! § Minimized impact to normal business processes § Less set-up for faster deployments and roll-outs IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
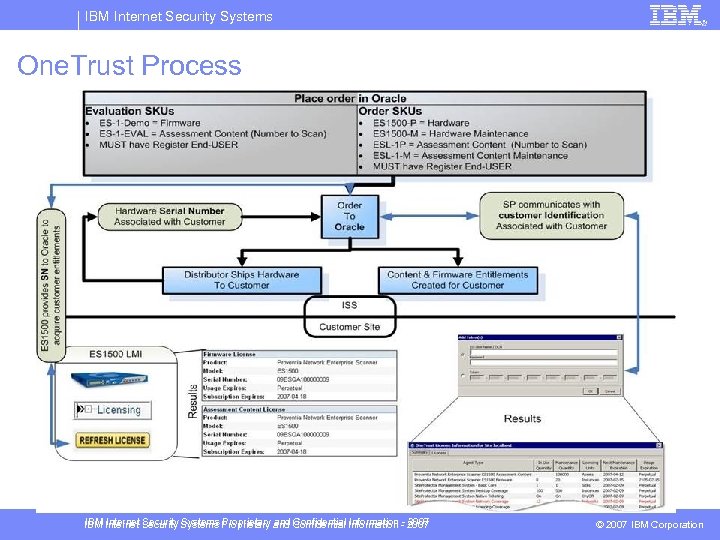
IBM Internet Security Systems One. Trust Process IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
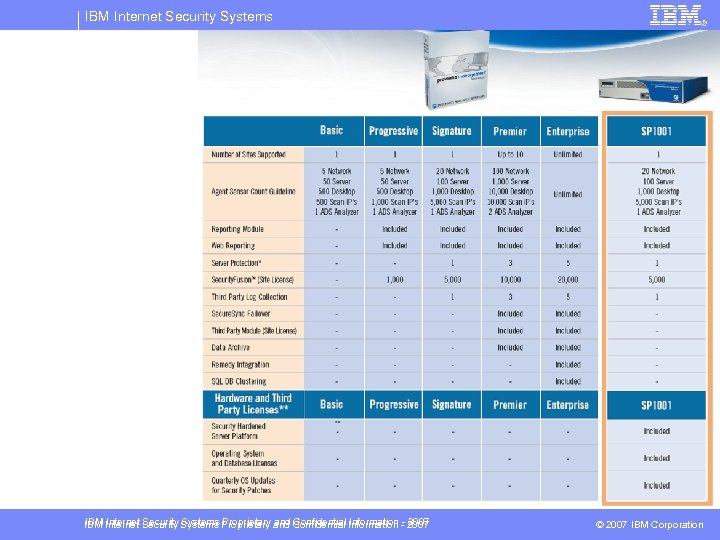
IBM Internet Security Systems Management Roadmap 2007 Products § Site. Protector SP 6. 1: – Scalable Enterprise mgmt, command control, workflow, user roles, reporting, active directory, central alerting, asset centric § Site. Protector Appliance SP 1001 – – Proventia Server protection Fusion Licenses § Fusion 2. 0: Event correlation engine – Included in system packages § Site. Protector Secure Sync: failover solution IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Internet Security Systems Management 2007 § Site. Protector SP 6. 1 enhancements – Extended risk reporting – PCI reporting (available with ES update) – Platform Support (Vista, VMWare, IE 7, Remedy 7. 0, TPMCheck. Point NGX and Cisco PIX 6. 3) § Site. Protector Appliance (tentative) – 1 U appliance – Event. Collector / Agent Manager appliance IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Management 2008 - Site. Protector SP 7 § Business Intelligence Reporting interface extension • Includes drag and drop custom reporting functions • Extended filtering options • Customizable report based dashboards § Policy management enhancements • • Extensive usability studies driving next generation of policy management Designed to flow with customers usage Provides key integrations with other parts of systems (ticketing, audit) Policy versioning § Platform advancement • Extend collaboration between agents - Event based policy changes IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Management § Security. Fusion Module – Must achieve: • Custom correlations developed by user • Correlations based on rules • Multi vendor event correlations – Consider Integration of Network Anomaly system • Network anomaly information with security event IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Internet Security Systems Site. Protector research and design § Enhanced web based interface to Site. Protector § Services based on-demand management § Risk Management perspective § Visualization of network and risk exposures § Ticketing integrations § Asset system integrations § IBM product integrations – Tivoli – Lotus IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Internet Security Systems TSOM & Site. Protector – Complementary Solutions § Tivoli Security Operations Manager (TSOM) – Full featured, multi-vendor Security Information and Event Management (SIEM) platform – Functions • Event aggregation from over 200 unique products & sources • Multi-vendor event correlation engine – 4 correlation techniques, including statistical, across all event types – Pre-built threat & policy correlation rules • Security threat dashboard, visualizations • Incident management ticketing & Investigation tools • Cross product reporting, including compliance focused reports – TSOM not a replacement for Site. Protector • No command control or configuration for any products IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
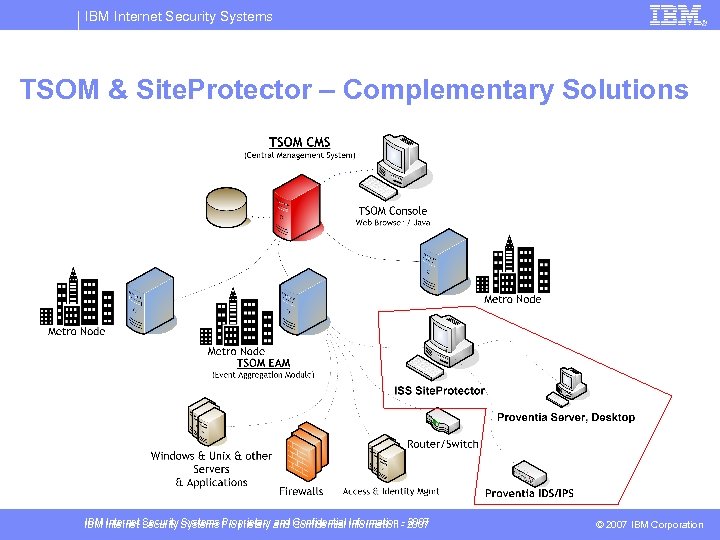
IBM Internet Security Systems TSOM & Site. Protector – Complementary Solutions IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation
IBM Internet Security Systems Site. Protector § Many large ISS shops will have Site. Protector installed. From the TSOM perspective, Site. Protector is an event aggregator that allows us to easily collect events from hundreds or thousands of devices. To collect these events we install an agent called the UCM (Universal Collection Module) on the Site. Protector computer. This agent reads from the MSSql database that stores the events and send them to the TSOM EAM as they are received by Site. Protector. IBM Internet Security Systems Proprietary and Confidential Information - 2007 © 2007 IBM Corporation

IBM Global Technology Services Ďakujem! Po prestávke pokračujeme: Proventia Anomaly Detection IBM Internet Security Systems Ahead of the threat. ™ © Copyright IBM Corporation 2007
www. iss. net IBM Global Services Thank you! § Ondrej KOVAC, § ondrej. kovac@sk. ibm. com § +421 -918 -541975 § Michael Clark, § mclark@fr. ibm. com IBM Internet Security Systems ® Ahead of the threat. ™ © 2007 IBM Corporation © 2006 Internet Security Systems. All rights reserved worldwide. Contents are property of Internet Security Systems.
17f3874e61008549fcbfa47698de5386.ppt