fc40772740b2eb8f56e5fd67c043894a.ppt
- Количество слайдов: 26

IBM Banking Industry The transition to active and predictive enterprise-wide risk management, monitoring & control Jonathan Rosenoer June 2004 © Copyright IBM Corporation 2004 Copyright © IBM Corp. 2006

Where there is no risk, there is no reward 2 © Copyright IBM Corporation 2004 © Copyright IBM Corporation 2005
Realized risk • • • • ATM software error inflates 800 customer balances by sum of $763. 9 B $4 M sell order executed as $4 B: all but $622 M orders are cancelled; Dow falls 2% Los Angeles County pension fund loses $1. 2 B over 20 yrs due to programming error $125 million Mars orbiter lost because an engineering team used English units of measurement instead of metric system for key spacecraft operation Half of Norway’s banks driven offline after organization running computer services wipes out data warehouse instead of initializing 280 new disks 22 -state EFT/ATM network disabled when tropical storm floods main and backup power systems 28 hour mainframe failure causes bank to borrow $20 B to manage sale of securities, at an interest cost of $4 M Volkswagen loses $260 M due to computer-based foreign exchange fraud U. S. Treasury issues $160 million in securities to online purchaser before realizing he had no funds. The transaction was reversed and purchaser arrested after attempting to steal $1. 3 billion more five days later. High tech crime team gains access to Sumitomo, London, computer systems and attempts to electronically transfer € 317 M to ten bank accounts around the world. Police subsequently warned financial institutions to be on alert for key-loggers. India BPO call center employees obtained PINs from 4 New York Citigroup account holders and used SWIFT to transfer more than $350 K to their own accounts Vendor of computer database of 19 billion public records, including Social Security numbers and credit reports, discloses that personal data on about 145, 000 people may have been stolen. Bank loses back-up tapes containing information on the customers and accounts of the U. S. government's Smart. Pay charge card program, which has more than 2. 1 million members and annual transactions totaling more than $21 billion. “Mathematically chaos is associated with a nonlinear relationship between inputs and outputs. Software is worse than chaotic; the output is not just nonlinear, it can actually be a discontinuous function because it is built on logic gates. ” 3 © Copyright IBM Corporation 2005

Risk can have severe impacts if not properly managed Citigroup (3/2005) - Federal Reserve bars major acquisitions until compliance problems are resolved. Adecco (1/2004) - Shares close down 35% following announcement of "material weaknesses in internal controls in the company's North American operations" Parmalat (12/2003) - Parmalat files for bankruptcy after Bank of America verifies forgery of a document purporting to certify that € 3. 9 bn of securities and cash were held in a company account. The company had a market value of € 1. 8 bn before the crisis broke. Food company (9/1999) - Reported 19% drop in 3 rd quarter net earnings due to “computer problems” result in one day 8% drop in stock price § “Analysts didn't fully trust [company]'s ability to deliver [product] until the following fall, when things had long been back to normal. ” Leading e-auction site (6/1999) - 22 hour site outage causes loss of $4 million in fees and $5 billion drop in market capitalization West coast bank (1996) - Following hostile takeover of another bank, “[ c]ustomers left in droves amid computer and processing snafus that included misplaced deposits. ” News reports and analysts call merger a bust, and acquirer is acquired. Review of 100 companies that disclosed internal control problems in 2004 shows most saw their stock prices fall around 5 -10% immediately afterward. Wall St. J. , Nov. 3, 2004 Poorly-governed firms have lower operating performance, lower valuations, and pay out less cash to their shareholders, while better-governed firms have higher operating performance, higher valuations, and pay out more cash to their shareholders. Georgia State U. , Corporate Governance and Firm Performance, Dec. 7, 2004 4 © Copyright IBM Corporation 2005
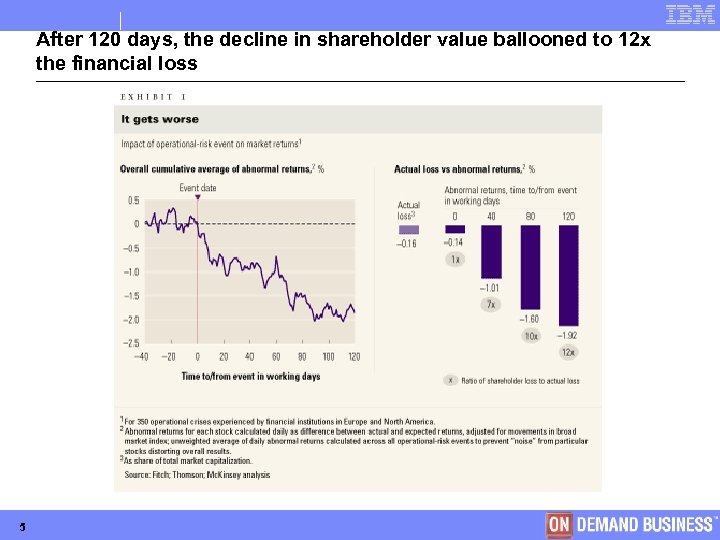
After 120 days, the decline in shareholder value ballooned to 12 x the financial loss 5 © Copyright IBM Corporation 2005

Agenda § § 6 Risk and business Transitioning through risk-based supervision to ERM Operational Risk quantification and modeling Creating a Risk Early Warning / Command Control system © Copyright IBM Corporation 2005
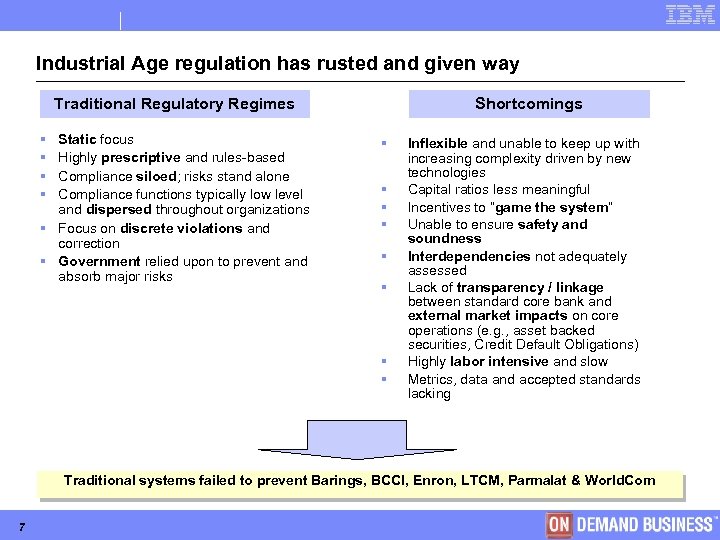
Industrial Age regulation has rusted and given way Traditional Regulatory Regimes § § Static focus Highly prescriptive and rules-based Compliance siloed; risks stand alone Compliance functions typically low level and dispersed throughout organizations § Focus on discrete violations and correction § Government relied upon to prevent and absorb major risks Shortcomings § § § § Inflexible and unable to keep up with increasing complexity driven by new technologies Capital ratios less meaningful Incentives to “game the system” Unable to ensure safety and soundness Interdependencies not adequately assessed Lack of transparency / linkage between standard core bank and external market impacts on core operations (e. g. , asset backed securities, Credit Default Obligations) Highly labor intensive and slow Metrics, data and accepted standards lacking Traditional systems failed to prevent Barings, BCCI, Enron, LTCM, Parmalat & World. Com 7 © Copyright IBM Corporation 2005

Regulators are raising the bar with Risk Based Supervision “A deluge of holistic regulatory mandates, including the USA PATRIOT Act, Basel II, and Sarbanes-Oxley, has reinforced the profile of [Enterprise Risk Management] and compliance both internally with financial services executives and externally with regulators, shareholders, auditors, customers, and solution providers. In addition, a flurry of new accounting standards introduced by the Financial Accounting Standards Board (FASB) and other accounting bodies in Europe and the rest of the world are triggering major headaches in financial services firms’ financial control and IT departments. What makes these regulatory mandates so complex is not just the necessary technology investment that must logically occur but also that they demand a transformation of the risk and compliance culture. The holistic requirements of these new regulations demand involvement across many different business lines and product dimensions, which most firms aren’t organizationally or culturally set up to do. ” V. Garcia, The Avant-Garde of Enterprise Risk Management in Financial Services: From Vision to Value, Tower. Group, Aug. 2004 “Large banks assume varied and complex risks that warrant a risk-oriented supervisory approach. Under this approach, examiners do not attempt to restrict risk-taking but rather determine whether banks identify, understand, and control the risks they assume. ” Large Bank Supervision, Comptroller’s Handbook (May 2001) 8 © Copyright IBM Corporation 2005

Information technology is a core regulatory focus “Prior to the 1990 s, the predominant threats to computer security of financial institutions (besides errors and omissions) were physical and environmental, including insider attacks, fire and water damage, theft, and physical damage. … Recent advances in computer hardware, software, and communications technologies have made these infrastructures highly automated and capable. While technological advances have promoted greater efficiency and improved service, they have also made these infrastructures potentially more vulnerable to disruption or incapacitation by a wide range of physical or computer-based (cyber) threats. The infrastructures are much more interdependent than in the past, with the result that the debilitation or destruction of one could have cascading destructive effects on others. Electronic transactions within the financial services infrastructure underpin the entire national economy, as well as the operations of the other infrastructure sectors. ” OCC 99 -9 (March 9, 1999) 9 © Copyright IBM Corporation 2005
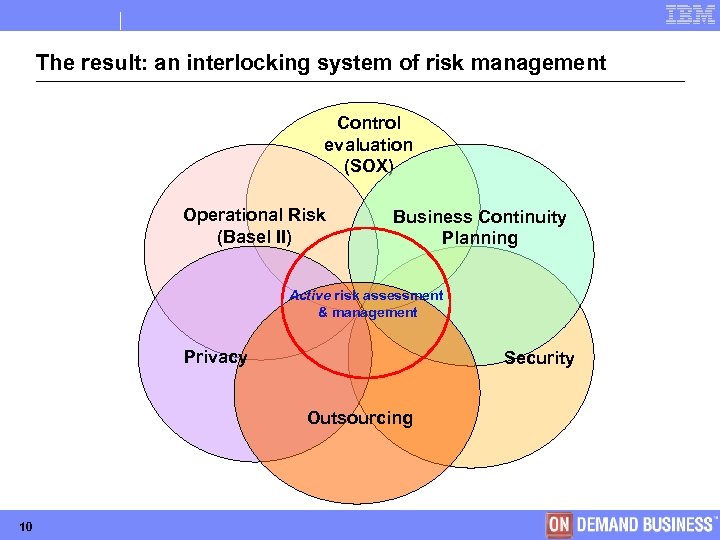
The result: an interlocking system of risk management Control evaluation (SOX) Operational Risk (Basel II) Business Continuity Planning Active risk assessment & management Privacy Security Outsourcing 10 © Copyright IBM Corporation 2005

SOX: ensure strong internal controls and improve disclosure Sarbanes. Oxley (SOX) § Section 302: CEO and CFO personally certify accuracy of financial statements and efficacy of internal disclosure controls § Section 404: Annual assessment of effectiveness of internal controls in financial reporting and attestation from external auditors that controls are effective § Section 409: Disclosure of material events: public companies obliged to disclose "on a rapid and current basis such additional information concerning material changes in the financial condition or operations of the issuer” § Related: - Federal Deposit Insurance Corporation Improvement Act (FDICIA) § FDICIA 112 requires that management report annually on the quality of internal controls and that the outside auditors attest to that control evaluation. § Sec. 39 of the FDI Act: “An institution should have internal controls and information systems that are appropriate to the size of the institution and the nature, scope and risk of its activities…. ” (12 CFR Part 208 App. D-1) - COBIT: Control Objectives for Information and related Technology COSO Enterprise Risk Management Framework "What were the underlying deficiencies in the internal control processes of these companies [Enron, Worldcom, and Health. South] that rendered their governance practices ineffective? " FRB Governor Susan Schmidt Bies, May 7, 2003 11 © Copyright IBM Corporation 2005
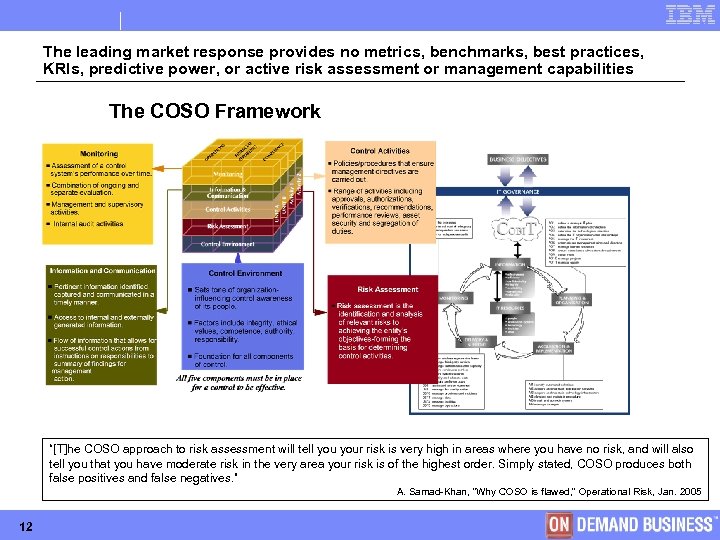
The leading market response provides no metrics, benchmarks, best practices, KRIs, predictive power, or active risk assessment or management capabilities The COSO Framework “[T]he COSO approach to risk assessment will tell your risk is very high in areas where you have no risk, and will also tell you that you have moderate risk in the very area your risk is of the highest order. Simply stated, COSO produces both false positives and false negatives. ” A. Samad-Khan, “Why COSO is flawed, ” Operational Risk, Jan. 2005 12 © Copyright IBM Corporation 2005
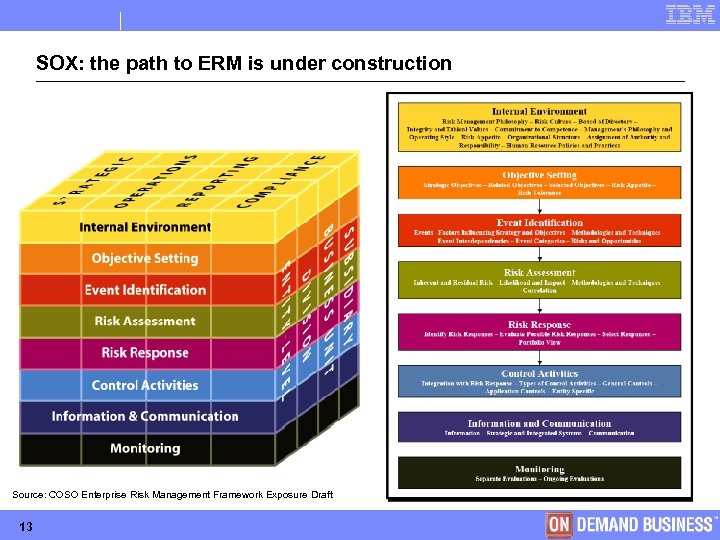
SOX: the path to ERM is under construction Source: COSO Enterprise Risk Management Framework Exposure Draft 13 © Copyright IBM Corporation 2005
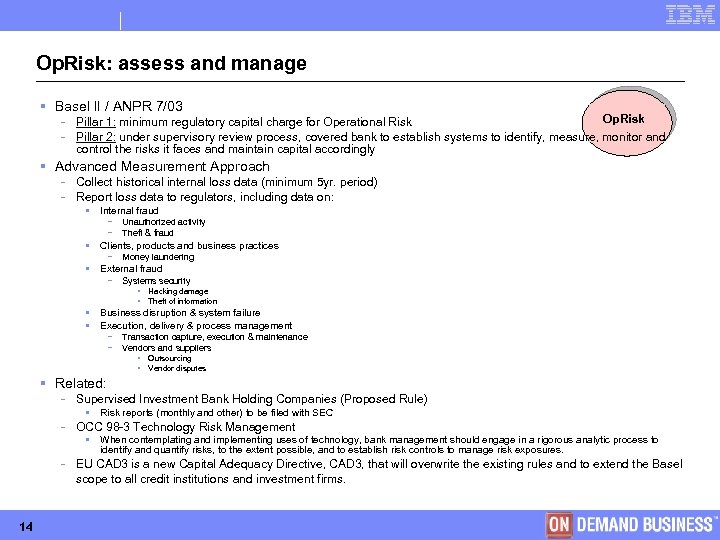
Op. Risk: assess and manage § Basel II / ANPR 7/03 - Op. Risk Pillar 1: minimum regulatory capital charge for Operational Risk Pillar 2: under supervisory review process, covered bank to establish systems to identify, measure, monitor and control the risks it faces and maintain capital accordingly § Advanced Measurement Approach - Collect historical internal loss data (minimum 5 yr. period) Report loss data to regulators, including data on: § Internal fraud - Unauthorized activity Theft & fraud § Clients, products and business practices - Money laundering § External fraud - Systems security § Hacking damage § Theft of information § Business disruption & system failure § Execution, delivery & process management - Transaction capture, execution & maintenance Vendors and suppliers § Outsourcing § Vendor disputes § Related: - Supervised Investment Bank Holding Companies (Proposed Rule) § Risk reports (monthly and other) to be filed with SEC - OCC 98 -3 Technology Risk Management § When contemplating and implementing uses of technology, bank management should engage in a rigorous analytic process to identify and quantify risks, to the extent possible, and to establish risk controls to manage risk exposures. - 14 EU CAD 3 is a new Capital Adequacy Directive, CAD 3, that will overwrite the existing rules and to extend the Basel scope to all credit institutions and investment firms. © Copyright IBM Corporation 2005
Business Continuity Planning: process orientation BCP § FFIEC, Business Continuity Planning Booklet (3/03) - Financial institutions encouraged to adopt a process-oriented approach to business continuity planning that involves: § § 1. Business impact analysis (BIA); 2. Risk assessment; 3. Risk management; and 4. Risk monitoring. § Interagency White Paper on Sound Practices to Strengthen the Resilience of the U. S. Financial System (April 11, 2003) - Geographic diversity § “The agencies expect that, as technology and business processes supporting back-up arrangements continue to improve and become increasingly cost effective, firms will take advantage of these developments to increase the geographic diversification of their back-up sites. § “Core clearing and settlement organizations should continue their accelerated efforts to develop, approve, and implement plans that substantially achieve the sound practices by the end of 2004. ” - “Plans should provide for back-up facilities that are well outside of the current synchronous range that can meet the withinthe-business-day recovery targets. ” - Recovery time objectives § Core clearing and settlement organizations to recover and resume within the business day - Overall goal of 2 hours after the event § Firms that play a significant role in financial markets to recover within the business day - Overall goal of 4 hours after the event § Related - 15 NASD Rule 3500 Series: requires members to establish emergency preparedness plans and procedures © Copyright IBM Corporation 2005

Outsourcing: equivalent controls Outsourcing § FFIEC, Outsourcing Technology Services (IT Examination Handbook June 2004) - - Management is responsible for managing risk in all outsourcing relationships Outsourced relationships should be subject to the same risk management, security, privacy, and other policies that would be expected if the financial institution were conducting the activities in-house. Management should consider SLAs to address the following issues: § Availability and timeliness of services; § Confidentiality and integrity of data; § Change control; § Security standards compliance, including vulnerability and penetration management; § Business continuity compliance; and § Help desk support. To help ensure financial institutions operate in a safe and sound manner, the services performed by technology service providers are subject to regulation and examination. § The federal financial regulators have the statutory authority to supervise all of the activities and records of the financial institution whether performed or maintained by the institution or by a third party on or off of the premises of the financial institution. § FFIEC, Supervision of Technology Service Providers (IT Examination Handbook March 2003) - 16 Examiners should consider the following factors in evaluating the quality of transaction/operational risk: § The quality of the Technology Service Provider (TSP) policies; § The adequacy of the TSP’s control and operational processes; § The extent of the TSP’s technical and managerial expertise; § Directorate oversight; and § The timeliness and completeness of management information systems that are used to measure performance, make decisions about risk, and assess the effectiveness of processes © Copyright IBM Corporation 2005

Outsourcing: equivalent controls, cont. Outsourcing § Bank Service Company Act, Section 7(c)(2) - Any FDIC-supervised institution that has services performed by a third party "shall notify such agency of the existence of the service relationship within 30 days after the making of such service contract or the performance of the service, whichever occurs first. " § Related: - 17 Basel Comm. (Joint Forum), Outsourcing in Financial Services, February 2005 FDIC, Offshore Outsourcing of Data Services by Insured Institutions and Associated Consumer Privacy Risks, June 2004 Committee of European Banking Supervisors, Consultation Paper on High Level Principles on Outsourcing, CP 02, April 2004 Monetary Authority of Singapore, Public Consultation: Guidelines on Outsourcing, P 002 - 2004, March 2004 OCC Bulletin 2002 -16, Bank Use of Foreign-Based Third-Party Service Providers (May 2002) § 25 a (2) of the KWG (German Banking Act) and associated circular 11/2001 © Copyright IBM Corporation 2005

Security: AML and Anti-Terrorist Financing Security § Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and Obstruct Terrorism (US PATRIOT) Act of 2001. - - Adoption of regulations setting forth minimum standards for “financial institutions” regarding the identification and verification of customers in connection with the opening of accounts. (Section 326) The establishment of anti-money laundering programs by “financial institutions” by April 24, 2002, unless exempted by the Secretary of the Treasury. At a minimum, these programs are to include: § § - 1. The development of internal policies, procedures and controls; 2. The designation of a compliance officer; 3. An ongoing employee training program; and 4. An independent audit function to test programs. (Section 352) Regulations requiring SEC-registered brokers and dealers to submit suspicious activity reports. (Section 356(a)). § Related: - 18 Money Laundering Control Act and the Bank Secrecy Act (BSA) 1996 Antiterrorism and Effective Death Penalty Act Executive Order 13224 © Copyright IBM Corporation 2005

Security: General Security § 12 CFR part 21 - Within 30 days after the opening of a new bank, the Bank's board of directors shall designate a security officer § OCC Alert 2000 -1, Internet Security: Distributed Denial of Service Attacks - Management can reduce a bank’s risk exposure by adopting and regularly reviewing its risk assessment plan, risk mitigation controls, intrusion response policies and procedures, and testing processes. § OCC Bulletin 2000 -14, Infrastructure Risks – Intrusion Threats - - The OCC encourages management to participate in information-sharing mechanisms as part of an effort to detect and respond to intrusions and vulnerabilities. National banks are required to report intrusions and other computer crimes to the OCC and law enforcement by filing a Suspicious Activity Report (SAR) form and submitting it to the Financial Crimes Enforcement Network (Fin. CEN), in accordance with 12 USC 21. 11. The first step in managing the risks of intrusions is to assess the effects that intrusions could have on the institution. Effects may include direct dollar loss, damaged reputation, improper disclosure, lawsuits, or regulatory sanctions. § OCC 99 -9, Infrastructure Threats from Cyber-Terrorists - Any intrusion, attempted intrusion, or suspicious activity should be immediately reported to a central source (compliance officer, auditor, etc. ) for disposition regarding the action the bank should take, and whether a Suspicious Activity Report should be filed. § Related: - 19 OCC Bulletin 98 -38, Technology Risk Management: PC Banking FFIEC, E-Banking (IT Examination Handbook August 2003) ISO 17799; NIST 800 -30; British Standard BS 7799 -2 © Copyright IBM Corporation 2005

Privacy § GLBA - § 501(a): Each financial institution has an affirmative and continuing obligation to respect the privacy of its customers and to protect the security and confidentiality of those customers' nonpublic personal information § Interagency Safeguards for Protecting Customer Information (21 CFR part 30 et al, Implementing GLBA): - A financial institution is required to take appropriate steps to protect customer information provided to a service provider. When outsourcing is used, the financial institution continues to bear responsibility for safeguarding customer information § Federal Banking Agencies (FBAs) guidelines implementing § 501(b) (12 CFR 364. 101, App. B ¶ III. D. ) - Each financial institution shall: § (1) exercise appropriate due diligence in selecting service providers; § (2) require them by contract to implement appropriate measures designed to meet the objectives of the Guidelines; and § (3) where indicated based upon the institution's risk assessment, monitor the service providers to confirm that they implement the procedures required by the Guidelines. § Offshore Outsourcing of Data Services by Insured Institutions and Associated Consumer Privacy Risks (FDIC) - "For each form of offshoring (captive, joint venture, direct third party, and indirect third party) nothing precludes the offshore transfer of customer data by a financial institution or one of its service providers. “ § Related: - California Security Breach Law (aka Bill 1386) § Notify CA resident of any security breach, or use encryption - 20 Fair and Accurate Credit Transactions Act of 2003 © Copyright IBM Corporation 2005

What is needed: § § § § § 21 Governance: commitment and oversight Organization, management and accountability Threat analysis, risk assessment and control evaluation Process mapping KRI identification Workflow Risk data management Common risk language Risk quantification V. Garcia, The Avant-Garde of Enterprise Risk Management in Financial Services: From Vision to Value, Tower. Group, Aug. 2004 Transparency Active risk monitoring and management Change management Record retention Testing and improvement Business continuity (vs. disaster recovery) Education and training Compliance reporting New technology for improved controls Risk management maturity process “A unified view of risk is needed. ” © Copyright IBM Corporation 2005

Resiliency The ability of an enterprise to sense and respond to any internal or external adverse, fast changing or unexpected condition, as well as opportunities, in order to maintain continuous business operations, be a more trusted partner, and enable growth. 22 © Copyright IBM Corporation 2005
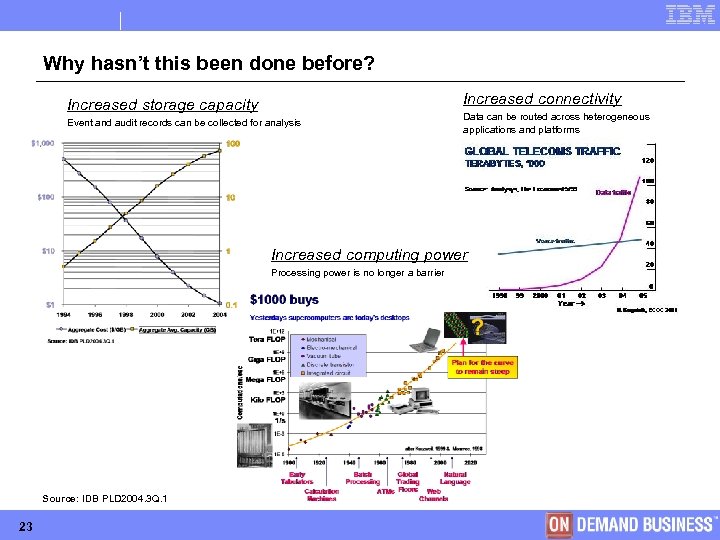
Why hasn’t this been done before? Increased connectivity Increased storage capacity Event and audit records can be collected for analysis Data can be routed across heterogeneous applications and platforms Increased computing power Processing power is no longer a barrier Source: IDB PLD 2004. 3 Q. 1 23 © Copyright IBM Corporation 2005
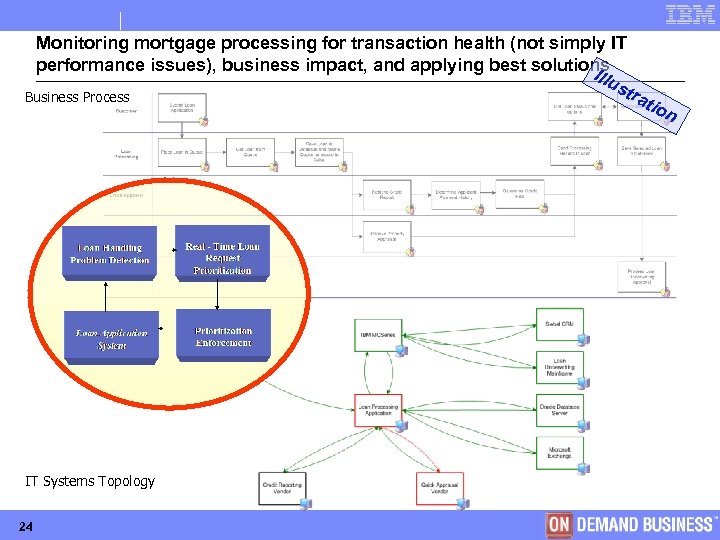
Monitoring mortgage processing for transaction health (not simply IT performance issues), business impact, and applying best solutions Illu str Business Process a tio n IT Systems Topology 24 © Copyright IBM Corporation 2005
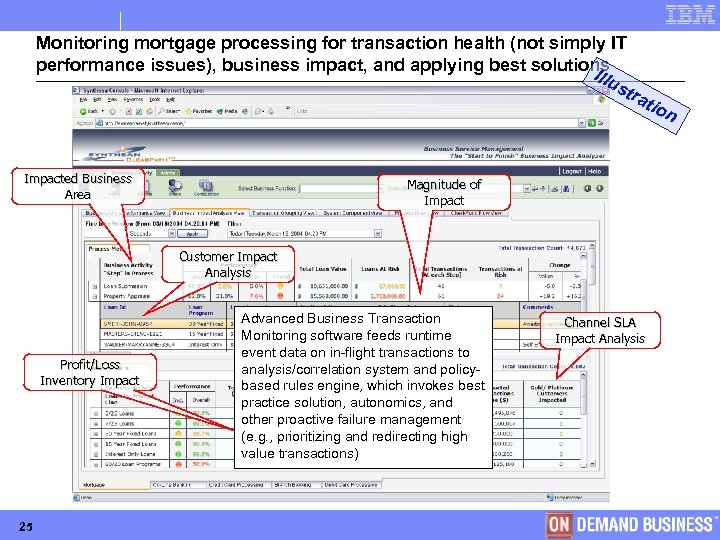
Monitoring mortgage processing for transaction health (not simply IT performance issues), business impact, and applying best solutions Illu str a tio Impacted Business Area n Magnitude of Impact Customer Impact Analysis Profit/Loss Inventory Impact 25 Advanced Business Transaction Monitoring software feeds runtime event data on in-flight transactions to analysis/correlation system and policybased rules engine, which invokes best practice solution, autonomics, and other proactive failure management (e. g. , prioritizing and redirecting high value transactions) Channel SLA Impact Analysis © Copyright IBM Corporation 2005
Thank You! IBM Financial Services Sector Global Risk Officer Global Banking Risk & Compliance Solutions Executive Jonathan Rosenoer – 415. 762. 2798 - rosenoer@us. ibm. com/industries/financialservices 26 © Copyright IBM Corporation 2005
fc40772740b2eb8f56e5fd67c043894a.ppt