47901d3a57074fb8c4e957276f1a201f.ppt
- Количество слайдов: 69
 IA&S DARPA Information Security Vision A Look at the Past, Present, and Future Shankar Sastry (Formerly ITO Director, DARPA) Chair, EECS Department University of California, Berkeley With the assistance of Drs. Douglas Maughan, Jaynarayan Lala, Cathy Mc. Collum, Brian Witten. 1
IA&S DARPA Information Security Vision A Look at the Past, Present, and Future Shankar Sastry (Formerly ITO Director, DARPA) Chair, EECS Department University of California, Berkeley With the assistance of Drs. Douglas Maughan, Jaynarayan Lala, Cathy Mc. Collum, Brian Witten. 1
 Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 2
Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 2
 DARPA Mission IA&S Radical Innovation in Support of National Security l l Solve National-level problems Enable Operational Dominance is the Defense Advanced Research Projects Agency u DARPA l High Risk Technology Development and Exploitation --Avoid Surprise 3
DARPA Mission IA&S Radical Innovation in Support of National Security l l Solve National-level problems Enable Operational Dominance is the Defense Advanced Research Projects Agency u DARPA l High Risk Technology Development and Exploitation --Avoid Surprise 3
 Some Current Focus Areas l National-Level Problems u u l Protection from Biological Attack Protection from Information Attack Operational Dominance u Affordable, Precision Moving Target Kill n u Offensive and defensive Dynamic Command & Control n Mobile Networks Near-Real-Time Planning, Replanning Future Warfare Concepts n n l IA&S Hard and Deeply Buried Target Classification Combined Manned, Unmanned Operations High-Risk, High-Payoff Technology Exploitation u u Core Technologies The Intersection of Biology, Information and Microsystems 4
Some Current Focus Areas l National-Level Problems u u l Protection from Biological Attack Protection from Information Attack Operational Dominance u Affordable, Precision Moving Target Kill n u Offensive and defensive Dynamic Command & Control n Mobile Networks Near-Real-Time Planning, Replanning Future Warfare Concepts n n l IA&S Hard and Deeply Buried Target Classification Combined Manned, Unmanned Operations High-Risk, High-Payoff Technology Exploitation u u Core Technologies The Intersection of Biology, Information and Microsystems 4
 Core Technologies l l l l IA&S Microsystems Technology Nanotechnology / Beyond Silicon Biology Math Advanced Materials Information Technology [Bio: Info: Micro] 5
Core Technologies l l l l IA&S Microsystems Technology Nanotechnology / Beyond Silicon Biology Math Advanced Materials Information Technology [Bio: Info: Micro] 5
 DARPA’s Role DARPA Bottom-up, opportunity, event-driven IA&S SERVICE R&D Top-down, requirement, schedule-driven Great process flexibility Highly formalized processes Integrated research 6. 1 - 6. 5 research separated Radical change Central Do. D agency for R&D Tolerant of high risk Planned product obsolescence Reliable, sustainable gains Support Service mission Risk-averse Planned product improvement The Do. D requires both radical innovation and requirements-based R&D 6
DARPA’s Role DARPA Bottom-up, opportunity, event-driven IA&S SERVICE R&D Top-down, requirement, schedule-driven Great process flexibility Highly formalized processes Integrated research 6. 1 - 6. 5 research separated Radical change Central Do. D agency for R&D Tolerant of high risk Planned product obsolescence Reliable, sustainable gains Support Service mission Risk-averse Planned product improvement The Do. D requires both radical innovation and requirements-based R&D 6
 DARPA’s Approach l Strategy u u l IA&S Flexibility, ability to exploit emerging situations is the highest priority Emphasize high technical risk, high focus investments Emphasize competition for ideas, reward for quality performance An investment firm, not R&D lab, no established constituency Operations u u Flat, small organization, no long-term investments in facilities, themes Constant rotation of programs, program managers, directors Continuity provided by industry, other government agencies, customer Highly flexible contracting, hiring capabilities DARPA is Do. D’s Enabler for Radical Innovation – Broader horizon than commercial analogues – More focused than university research – Not bound by military requirements 7
DARPA’s Approach l Strategy u u l IA&S Flexibility, ability to exploit emerging situations is the highest priority Emphasize high technical risk, high focus investments Emphasize competition for ideas, reward for quality performance An investment firm, not R&D lab, no established constituency Operations u u Flat, small organization, no long-term investments in facilities, themes Constant rotation of programs, program managers, directors Continuity provided by industry, other government agencies, customer Highly flexible contracting, hiring capabilities DARPA is Do. D’s Enabler for Radical Innovation – Broader horizon than commercial analogues – More focused than university research – Not bound by military requirements 7
 Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 8
Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 8
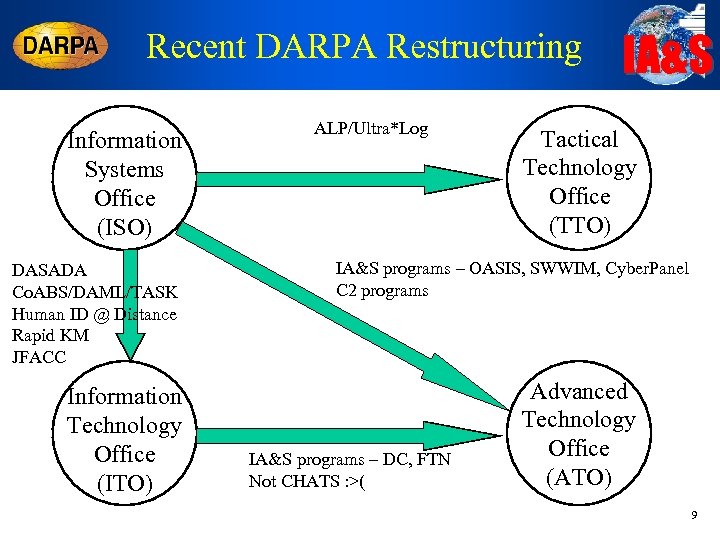 Recent DARPA Restructuring Information Systems Office (ISO) DASADA Co. ABS/DAML/TASK Human ID @ Distance Rapid KM JFACC Information Technology Office (ITO) ALP/Ultra*Log IA&S Tactical Technology Office (TTO) IA&S programs – OASIS, SWWIM, Cyber. Panel C 2 programs IA&S programs – DC, FTN Not CHATS : >( Advanced Technology Office (ATO) 9
Recent DARPA Restructuring Information Systems Office (ISO) DASADA Co. ABS/DAML/TASK Human ID @ Distance Rapid KM JFACC Information Technology Office (ITO) ALP/Ultra*Log IA&S Tactical Technology Office (TTO) IA&S programs – OASIS, SWWIM, Cyber. Panel C 2 programs IA&S programs – DC, FTN Not CHATS : >( Advanced Technology Office (ATO) 9
 Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 11
Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 11
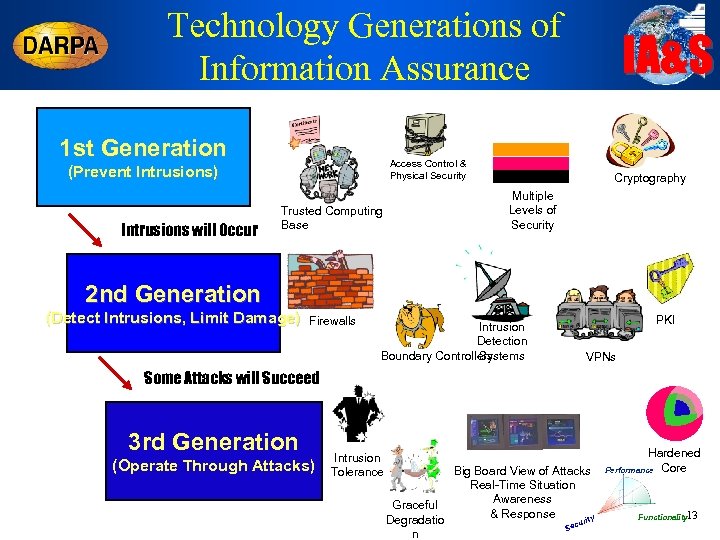 Technology Generations of Information Assurance 1 st Generation Access Control & Physical Security (Prevent Intrusions) Intrusions will Occur IA&S Trusted Computing Base Cryptography Multiple Levels of Security 2 nd Generation (Detect Intrusions, Limit Damage) Firewalls Intrusion Detection Systems Boundary Controllers PKI VPNs Some Attacks will Succeed 3 rd Generation (Operate Through Attacks) Intrusion Tolerance Big Board View of Attacks Real-Time Situation Awareness Graceful & Response ty Degradatio uri Sec n Hardened Performance Core 13 Functionality
Technology Generations of Information Assurance 1 st Generation Access Control & Physical Security (Prevent Intrusions) Intrusions will Occur IA&S Trusted Computing Base Cryptography Multiple Levels of Security 2 nd Generation (Detect Intrusions, Limit Damage) Firewalls Intrusion Detection Systems Boundary Controllers PKI VPNs Some Attacks will Succeed 3 rd Generation (Operate Through Attacks) Intrusion Tolerance Big Board View of Attacks Real-Time Situation Awareness Graceful & Response ty Degradatio uri Sec n Hardened Performance Core 13 Functionality
 Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 14
Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 14
 Cyber Defense & Asymmetric Threat l l IA&S Other nations know that they have fallen behind in (conventional) military muscle, and so need to rely on “Asymmetric” methods, that is, countering an adversary’s strengths by focusing on its weaknesses (see for example, “Unrestricted Warfare” by Qiao and Wang). Both the US military and the “soft underbelly” of commercial and infrastructure networks depend increasingly on information technology making cyber -attack both attractive and potentially effective. THE WEAKNESS OF A SUPERPOWER! 15
Cyber Defense & Asymmetric Threat l l IA&S Other nations know that they have fallen behind in (conventional) military muscle, and so need to rely on “Asymmetric” methods, that is, countering an adversary’s strengths by focusing on its weaknesses (see for example, “Unrestricted Warfare” by Qiao and Wang). Both the US military and the “soft underbelly” of commercial and infrastructure networks depend increasingly on information technology making cyber -attack both attractive and potentially effective. THE WEAKNESS OF A SUPERPOWER! 15
 Moonlight Mayhem and Eligible Receiver l l IA&S Since March 1998, a group of hackers traced to “inoperative telephone numbers” in Russia (but not traced to state-sponsorship) has attacked a number of Do. D networks and installed backdoors for reentering, etc. Since June 1997, the Joint Chiefs have authorized a red team (legal and using tools available on the internet) to attack civilian and Do. D networks in two exercises, Eligible Receiver and Zenith Star. Power networks, logistics networks, national infrastructure networks are vulnerable. 16
Moonlight Mayhem and Eligible Receiver l l IA&S Since March 1998, a group of hackers traced to “inoperative telephone numbers” in Russia (but not traced to state-sponsorship) has attacked a number of Do. D networks and installed backdoors for reentering, etc. Since June 1997, the Joint Chiefs have authorized a red team (legal and using tools available on the internet) to attack civilian and Do. D networks in two exercises, Eligible Receiver and Zenith Star. Power networks, logistics networks, national infrastructure networks are vulnerable. 16
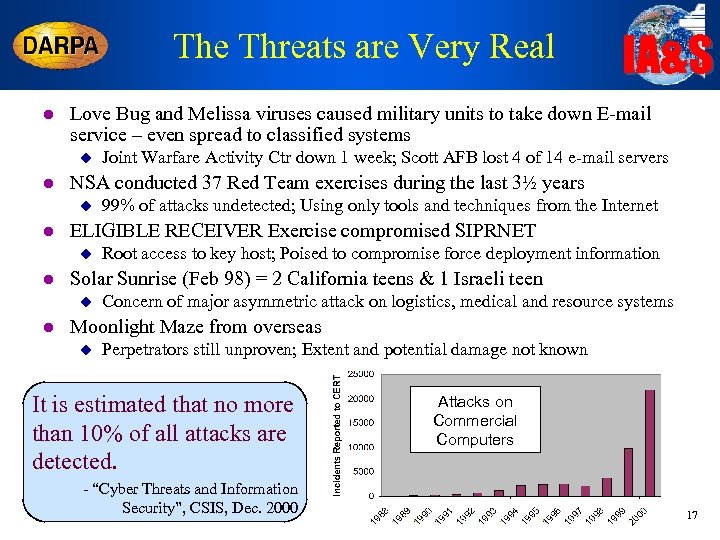 The Threats are Very Real l Love Bug and Melissa viruses caused military units to take down E-mail service – even spread to classified systems u l Root access to key host; Poised to compromise force deployment information Solar Sunrise (Feb 98) = 2 California teens & 1 Israeli teen u l 99% of attacks undetected; Using only tools and techniques from the Internet ELIGIBLE RECEIVER Exercise compromised SIPRNET u l Joint Warfare Activity Ctr down 1 week; Scott AFB lost 4 of 14 e-mail servers NSA conducted 37 Red Team exercises during the last 3½ years u l IA&S Concern of major asymmetric attack on logistics, medical and resource systems Moonlight Maze from overseas u Perpetrators still unproven; Extent and potential damage not known It is estimated that no more than 10% of all attacks are detected. - “Cyber Threats and Information Security”, CSIS, Dec. 2000 Attacks on Commercial Computers 17
The Threats are Very Real l Love Bug and Melissa viruses caused military units to take down E-mail service – even spread to classified systems u l Root access to key host; Poised to compromise force deployment information Solar Sunrise (Feb 98) = 2 California teens & 1 Israeli teen u l 99% of attacks undetected; Using only tools and techniques from the Internet ELIGIBLE RECEIVER Exercise compromised SIPRNET u l Joint Warfare Activity Ctr down 1 week; Scott AFB lost 4 of 14 e-mail servers NSA conducted 37 Red Team exercises during the last 3½ years u l IA&S Concern of major asymmetric attack on logistics, medical and resource systems Moonlight Maze from overseas u Perpetrators still unproven; Extent and potential damage not known It is estimated that no more than 10% of all attacks are detected. - “Cyber Threats and Information Security”, CSIS, Dec. 2000 Attacks on Commercial Computers 17
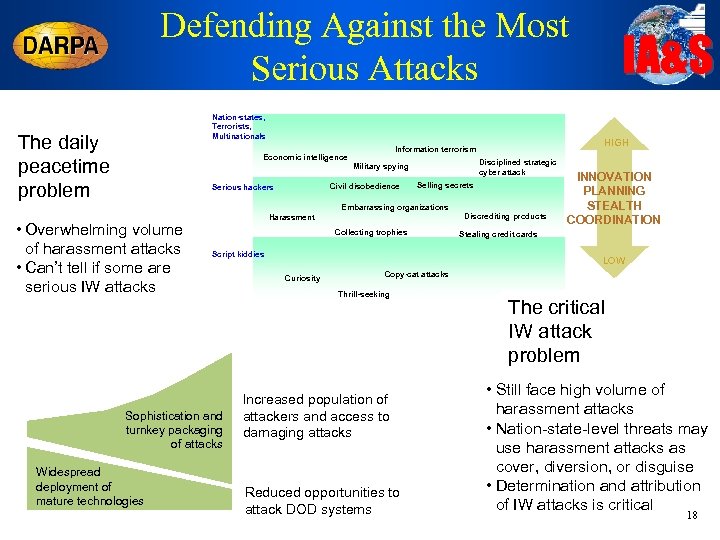 Defending Against the Most Serious Attacks Nation-states, Terrorists, Multinationals The daily peacetime problem Economic intelligence Civil disobedience Serious hackers HIGH Information terrorism Disciplined strategic cyber attack Military spying Selling secrets Embarrassing organizations • Overwhelming volume of harassment attacks • Can’t tell if some are serious IW attacks Collecting trophies Script kiddies Sophistication and turnkey packaging of attacks Widespread deployment of mature technologies Discrediting products Harassment IA&S INNOVATION PLANNING STEALTH COORDINATION Stealing credit cards LOW Curiosity Copy-cat attacks Thrill-seeking Increased population of attackers and access to damaging attacks Reduced opportunities to attack DOD systems The critical IW attack problem • Still face high volume of harassment attacks • Nation-state-level threats may use harassment attacks as cover, diversion, or disguise • Determination and attribution of IW attacks is critical 18
Defending Against the Most Serious Attacks Nation-states, Terrorists, Multinationals The daily peacetime problem Economic intelligence Civil disobedience Serious hackers HIGH Information terrorism Disciplined strategic cyber attack Military spying Selling secrets Embarrassing organizations • Overwhelming volume of harassment attacks • Can’t tell if some are serious IW attacks Collecting trophies Script kiddies Sophistication and turnkey packaging of attacks Widespread deployment of mature technologies Discrediting products Harassment IA&S INNOVATION PLANNING STEALTH COORDINATION Stealing credit cards LOW Curiosity Copy-cat attacks Thrill-seeking Increased population of attackers and access to damaging attacks Reduced opportunities to attack DOD systems The critical IW attack problem • Still face high volume of harassment attacks • Nation-state-level threats may use harassment attacks as cover, diversion, or disguise • Determination and attribution of IW attacks is critical 18
 So Whose Job is it anyway? IA&S During the Cold War, the Government controlled the pace of technology development by direct funding about 70 % of research. Now it is less than 5 %. The shift in funding has been accompanied by the development of a new weapons platfrom: the PC! l National Security today means the ability to protect civilian networks and cooperation between the citizens and government on defense. But there are sometimes legal constraints on the Government on information sharing on threats. l The US defense posture is currently designed around force projection rather than homeland defense. The responsibility must rest with Do. D + reserves + civil defense coordinated by the National Security Council. l 19
So Whose Job is it anyway? IA&S During the Cold War, the Government controlled the pace of technology development by direct funding about 70 % of research. Now it is less than 5 %. The shift in funding has been accompanied by the development of a new weapons platfrom: the PC! l National Security today means the ability to protect civilian networks and cooperation between the citizens and government on defense. But there are sometimes legal constraints on the Government on information sharing on threats. l The US defense posture is currently designed around force projection rather than homeland defense. The responsibility must rest with Do. D + reserves + civil defense coordinated by the National Security Council. l 19
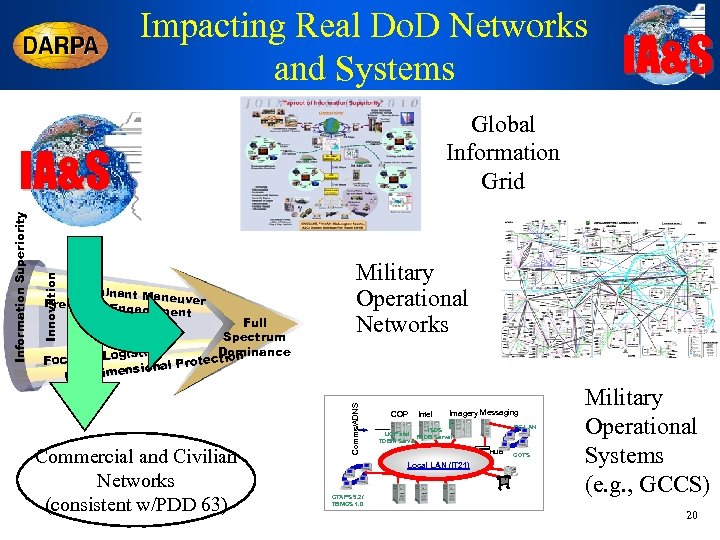 Impacting Real Do. D Networks and Systems Global Information Grid Full Spectrum Dominance cs gisti tion Focused Lo l Protec ensiona Full Dim Commercial and Civilian Networks (consistent w/PDD 63) Military Operational Networks Comms/ADNS Innovation Information Superiority IA&S Dominant M aneuver Precision Eng agement IA&S COP Intel Imagery Messaging ITS HUB Local LAN (IT 21) CTAPS 5. 2/ TBMCS 1. 0 PC LAN ISDS UCP and MIDB Server TDBM Server COTS Military Operational Systems (e. g. , GCCS) 20
Impacting Real Do. D Networks and Systems Global Information Grid Full Spectrum Dominance cs gisti tion Focused Lo l Protec ensiona Full Dim Commercial and Civilian Networks (consistent w/PDD 63) Military Operational Networks Comms/ADNS Innovation Information Superiority IA&S Dominant M aneuver Precision Eng agement IA&S COP Intel Imagery Messaging ITS HUB Local LAN (IT 21) CTAPS 5. 2/ TBMCS 1. 0 PC LAN ISDS UCP and MIDB Server TDBM Server COTS Military Operational Systems (e. g. , GCCS) 20
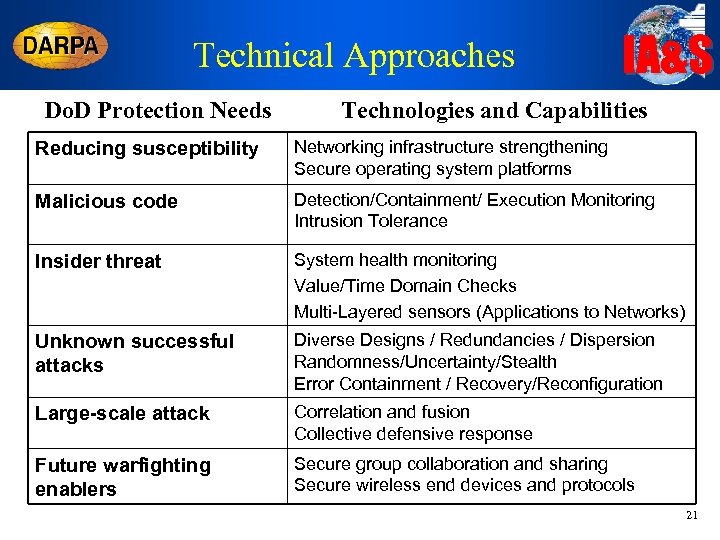 Technical Approaches Do. D Protection Needs IA&S Technologies and Capabilities Reducing susceptibility Networking infrastructure strengthening Secure operating system platforms Malicious code Detection/Containment/ Execution Monitoring Intrusion Tolerance Insider threat System health monitoring Value/Time Domain Checks Multi-Layered sensors (Applications to Networks) Unknown successful attacks Diverse Designs / Redundancies / Dispersion Randomness/Uncertainty/Stealth Error Containment / Recovery/Reconfiguration Large-scale attack Correlation and fusion Collective defensive response Future warfighting enablers Secure group collaboration and sharing Secure wireless end devices and protocols 21
Technical Approaches Do. D Protection Needs IA&S Technologies and Capabilities Reducing susceptibility Networking infrastructure strengthening Secure operating system platforms Malicious code Detection/Containment/ Execution Monitoring Intrusion Tolerance Insider threat System health monitoring Value/Time Domain Checks Multi-Layered sensors (Applications to Networks) Unknown successful attacks Diverse Designs / Redundancies / Dispersion Randomness/Uncertainty/Stealth Error Containment / Recovery/Reconfiguration Large-scale attack Correlation and fusion Collective defensive response Future warfighting enablers Secure group collaboration and sharing Secure wireless end devices and protocols 21
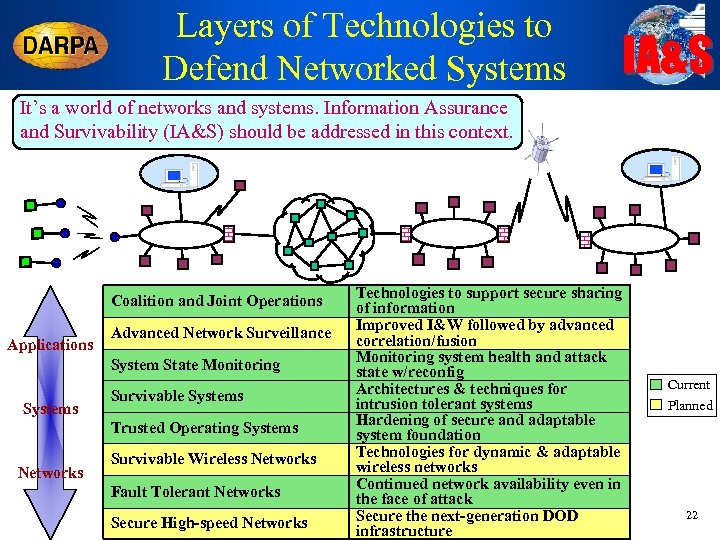 Layers of Technologies to Defend Networked Systems IA&S It’s a world of networks and systems. Information Assurance and Survivability (IA&S) should be addressed in this context. Coalition and Joint Operations Applications Advanced Network Surveillance System State Monitoring Systems Survivable Systems Trusted Operating Systems Networks Survivable Wireless Networks Fault Tolerant Networks Secure High-speed Networks Technologies to support secure sharing of information Improved I&W followed by advanced correlation/fusion Monitoring system health and attack state w/reconfig Architectures & techniques for intrusion tolerant systems Hardening of secure and adaptable system foundation Technologies for dynamic & adaptable wireless networks Continued network availability even in the face of attack Secure the next-generation DOD infrastructure Current Planned 22
Layers of Technologies to Defend Networked Systems IA&S It’s a world of networks and systems. Information Assurance and Survivability (IA&S) should be addressed in this context. Coalition and Joint Operations Applications Advanced Network Surveillance System State Monitoring Systems Survivable Systems Trusted Operating Systems Networks Survivable Wireless Networks Fault Tolerant Networks Secure High-speed Networks Technologies to support secure sharing of information Improved I&W followed by advanced correlation/fusion Monitoring system health and attack state w/reconfig Architectures & techniques for intrusion tolerant systems Hardening of secure and adaptable system foundation Technologies for dynamic & adaptable wireless networks Continued network availability even in the face of attack Secure the next-generation DOD infrastructure Current Planned 22
 Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 23
Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 23
 Current IA&S Program Suite l IA&S Technology Programs u FTN – Fault Tolerant Networks u SWWIM – Survivable Wired & Wireless Infrastructure u CHATS – Composable High Assurance Trusted Systems u OASIS – Organically Assured & Survivable Info Systems u Cyber. Panel u DC – Dynamic Coalitions l Systems Program u Survivable l Global Information Grid (GIG) Technology Transition u Operational Experimentation u Critical Infrastructure Protection 24
Current IA&S Program Suite l IA&S Technology Programs u FTN – Fault Tolerant Networks u SWWIM – Survivable Wired & Wireless Infrastructure u CHATS – Composable High Assurance Trusted Systems u OASIS – Organically Assured & Survivable Info Systems u Cyber. Panel u DC – Dynamic Coalitions l Systems Program u Survivable l Global Information Grid (GIG) Technology Transition u Operational Experimentation u Critical Infrastructure Protection 24
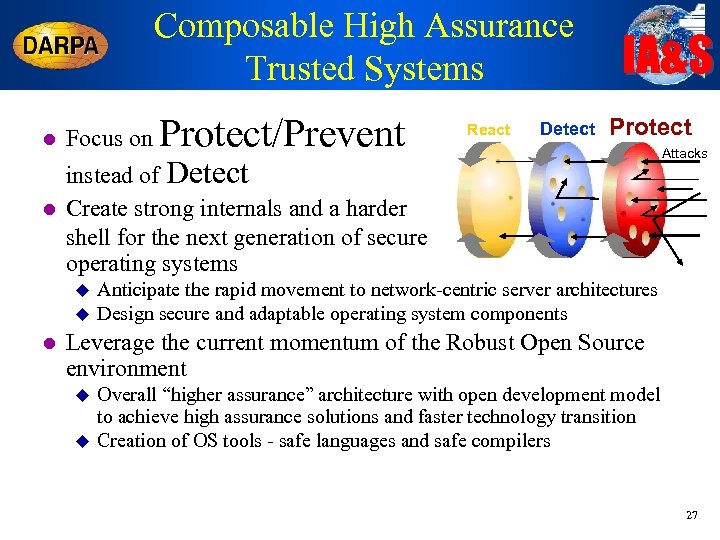 Composable High Assurance Trusted Systems Protect/Prevent l Focus on l React Detect IA&S Protect instead of Detect Create strong internals and a harder shell for the next generation of secure operating systems u u l Attacks Anticipate the rapid movement to network-centric server architectures Design secure and adaptable operating system components Leverage the current momentum of the Robust Open Source environment u u Overall “higher assurance” architecture with open development model to achieve high assurance solutions and faster technology transition Creation of OS tools - safe languages and safe compilers 27
Composable High Assurance Trusted Systems Protect/Prevent l Focus on l React Detect IA&S Protect instead of Detect Create strong internals and a harder shell for the next generation of secure operating systems u u l Attacks Anticipate the rapid movement to network-centric server architectures Design secure and adaptable operating system components Leverage the current momentum of the Robust Open Source environment u u Overall “higher assurance” architecture with open development model to achieve high assurance solutions and faster technology transition Creation of OS tools - safe languages and safe compilers 27
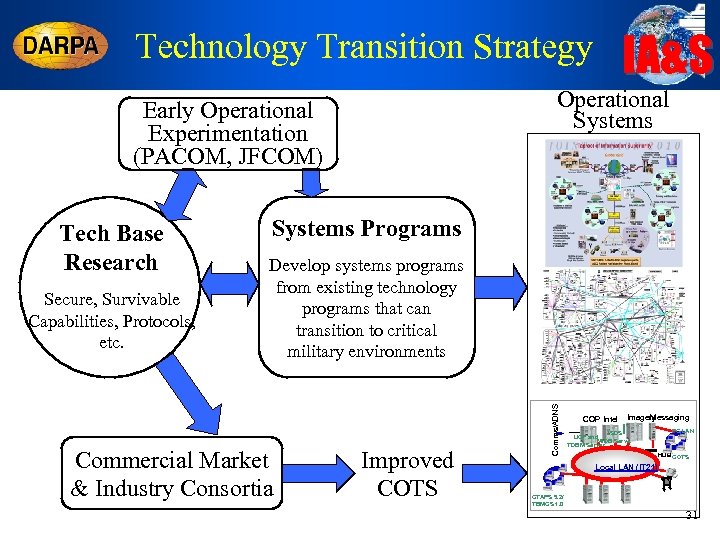 IA&S Technology Transition Strategy Operational Systems Early Operational Experimentation (PACOM, JFCOM) Secure, Survivable Capabilities, Protocols, etc. Systems Programs Develop systems programs from existing technology programs that can transition to critical military environments Commercial Market & Industry Consortia Improved COTS Comms/ADNS Tech Base Research COP Intel Messaging Imagery ITS ISDS UCP and MIDB Server TDBM Server PC LAN HUB COTS Local LAN (IT 21) CTAPS 5. 2/ TBMCS 1. 0 31
IA&S Technology Transition Strategy Operational Systems Early Operational Experimentation (PACOM, JFCOM) Secure, Survivable Capabilities, Protocols, etc. Systems Programs Develop systems programs from existing technology programs that can transition to critical military environments Commercial Market & Industry Consortia Improved COTS Comms/ADNS Tech Base Research COP Intel Messaging Imagery ITS ISDS UCP and MIDB Server TDBM Server PC LAN HUB COTS Local LAN (IT 21) CTAPS 5. 2/ TBMCS 1. 0 31
 Background - Critical Infrastructure Protection l l IA&S October 97 - Report of the President’s Commission on Critical Infrastructure Protection (PCCIP) ==> http: //www. pccip. ncr. gov/ May 22, 1998 - President Clinton announced two new directives designed to strengthen the Nation's defenses against terrorism and other unconventional threats u u PDD-62 highlights the growing range of unconventional threats that we face, including "cyber terrorism" and chemical, radiological, and biological weapons, and creates a new and more systematic approach to defending against them. PDD-63 focuses specifically on protecting the Nation's critical infrastructures from both physical and "cyber" attack. These attacks may come from foreign governments, foreign and domestic terrorist organizations, and foreign and domestic criminal organizations. 32
Background - Critical Infrastructure Protection l l IA&S October 97 - Report of the President’s Commission on Critical Infrastructure Protection (PCCIP) ==> http: //www. pccip. ncr. gov/ May 22, 1998 - President Clinton announced two new directives designed to strengthen the Nation's defenses against terrorism and other unconventional threats u u PDD-62 highlights the growing range of unconventional threats that we face, including "cyber terrorism" and chemical, radiological, and biological weapons, and creates a new and more systematic approach to defending against them. PDD-63 focuses specifically on protecting the Nation's critical infrastructures from both physical and "cyber" attack. These attacks may come from foreign governments, foreign and domestic terrorist organizations, and foreign and domestic criminal organizations. 32
 Critical Infrastructures IA&S l Physical and cyber-based systems essential to the minimum operations of the economy and government. These systems are so vital, that their incapacity or destruction would have a debilitating impact on the defense or economic security of the United States. u u u u Information and Telecommunications Banking and Finance Water Supply Systems Electrical Power, Oil and Gas Production and Storage Transportation - Aviation, Rail System, Roads and Highways, Waterways Emergency Services Public Health Services Continuity of Government Services 33
Critical Infrastructures IA&S l Physical and cyber-based systems essential to the minimum operations of the economy and government. These systems are so vital, that their incapacity or destruction would have a debilitating impact on the defense or economic security of the United States. u u u u Information and Telecommunications Banking and Finance Water Supply Systems Electrical Power, Oil and Gas Production and Storage Transportation - Aviation, Rail System, Roads and Highways, Waterways Emergency Services Public Health Services Continuity of Government Services 33
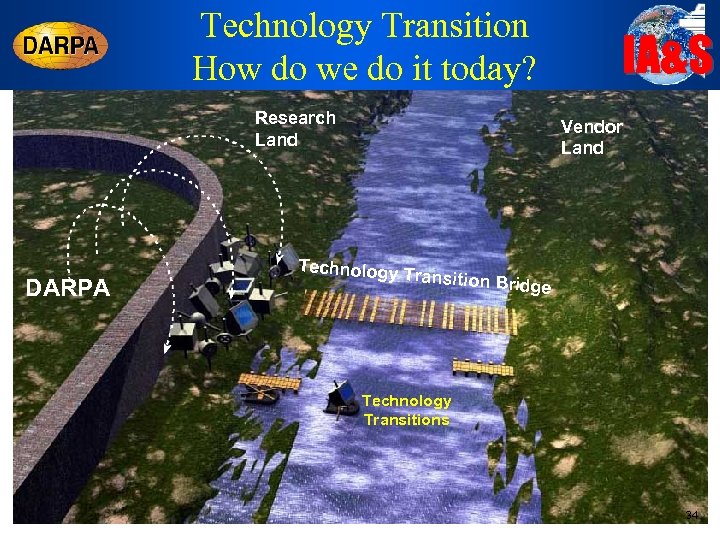 Technology Transition How do we do it today? Research Land DARPA IA&S Vendor Land Technology Transition B ridge Technology Transitions 34
Technology Transition How do we do it today? Research Land DARPA IA&S Vendor Land Technology Transition B ridge Technology Transitions 34
 Technology Transition What can we do to improve? Research Land DARPA IA&S Vendor Land Technology Transition B ridge P C -BG ting S ou SSE R DN Technology Transitions 35
Technology Transition What can we do to improve? Research Land DARPA IA&S Vendor Land Technology Transition B ridge P C -BG ting S ou SSE R DN Technology Transitions 35
 What we have done l Scheduled and held “Forum on Technology Transition for Internet Infrastructure Security” u u l IA&S Date: June 21, 2000 Joint sponsorship with WH/OSTP & NSC and NCO CIC Attendees (Total present: 48) u u u Router Vendors: Cisco, Nortel, Nexabit/Lucent, Extreme Networks, Avici ISPs: MCI/World. Com, UUNet, AT&T, GTE-I (aka Genuity), Qwest, PSInet, @Home, Merit Networks Internet: IESG, ARIN Government: DARPA, DDR&E, WH/OSTP/NSC, DISA, NIST, NSF, AFRL, SSC-SD Others: BBN, NAI Labs, Boeing, University of Michigan 36
What we have done l Scheduled and held “Forum on Technology Transition for Internet Infrastructure Security” u u l IA&S Date: June 21, 2000 Joint sponsorship with WH/OSTP & NSC and NCO CIC Attendees (Total present: 48) u u u Router Vendors: Cisco, Nortel, Nexabit/Lucent, Extreme Networks, Avici ISPs: MCI/World. Com, UUNet, AT&T, GTE-I (aka Genuity), Qwest, PSInet, @Home, Merit Networks Internet: IESG, ARIN Government: DARPA, DDR&E, WH/OSTP/NSC, DISA, NIST, NSF, AFRL, SSC-SD Others: BBN, NAI Labs, Boeing, University of Michigan 36
 Committed Technology Transition Participants IA&S l Agreed to experimentation and incremental deployment on “non-operational” networks with plans for transition to real networks l Researchers Router Vendors l u u u l ISPs u u u l Avici - as originally proposed by BBN Lucent/Nexabit - willing to put S-BGP in next generation routers Nortel - previously committed; unable to attend due to family death MCI/World. Com - willing to do experimentation on “peering” networks AT&T - similar to MCI/World. Com; will peer with several others Genuity - full participant; trying to get ISP consortium off the ground @Home Networks - similar to MCI/World. Com; willing to do experiments Merit Networks - willing to do non-operational experiments Registries - ARIN 37
Committed Technology Transition Participants IA&S l Agreed to experimentation and incremental deployment on “non-operational” networks with plans for transition to real networks l Researchers Router Vendors l u u u l ISPs u u u l Avici - as originally proposed by BBN Lucent/Nexabit - willing to put S-BGP in next generation routers Nortel - previously committed; unable to attend due to family death MCI/World. Com - willing to do experimentation on “peering” networks AT&T - similar to MCI/World. Com; will peer with several others Genuity - full participant; trying to get ISP consortium off the ground @Home Networks - similar to MCI/World. Com; willing to do experiments Merit Networks - willing to do non-operational experiments Registries - ARIN 37
 Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 38
Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 38
 Networks and Systems IA&S Vision IA&S NGI 43
Networks and Systems IA&S Vision IA&S NGI 43
 Secure High Speed IP Networking (SHIPN) IA&S SHIPN 44
Secure High Speed IP Networking (SHIPN) IA&S SHIPN 44
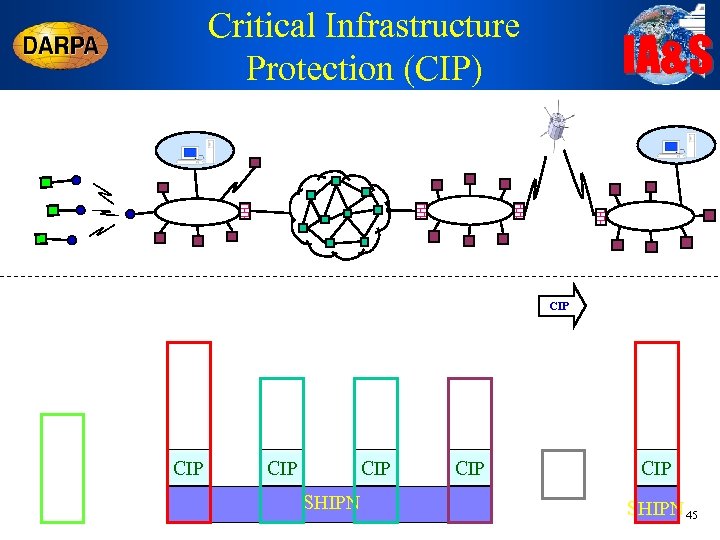 Critical Infrastructure Protection (CIP) IA&S CIP CIP SHIPN 45
Critical Infrastructure Protection (CIP) IA&S CIP CIP SHIPN 45
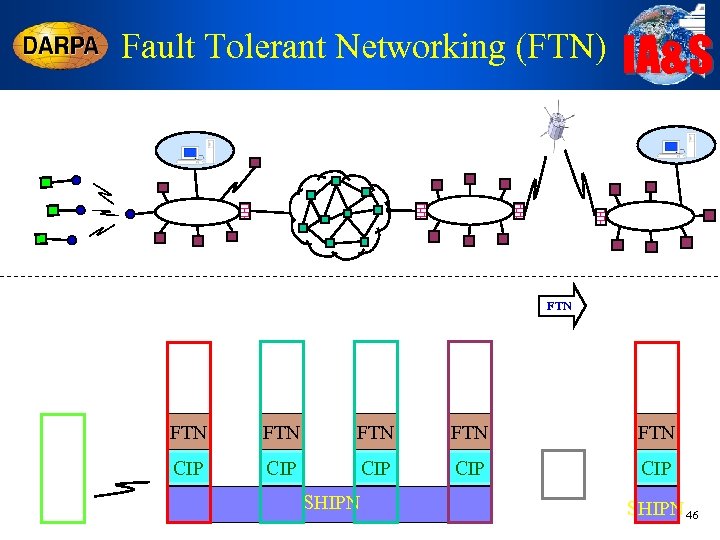 Fault Tolerant Networking (FTN) IA&S FTN FTN FTN CIP CIP CIP SHIPN 46
Fault Tolerant Networking (FTN) IA&S FTN FTN FTN CIP CIP CIP SHIPN 46
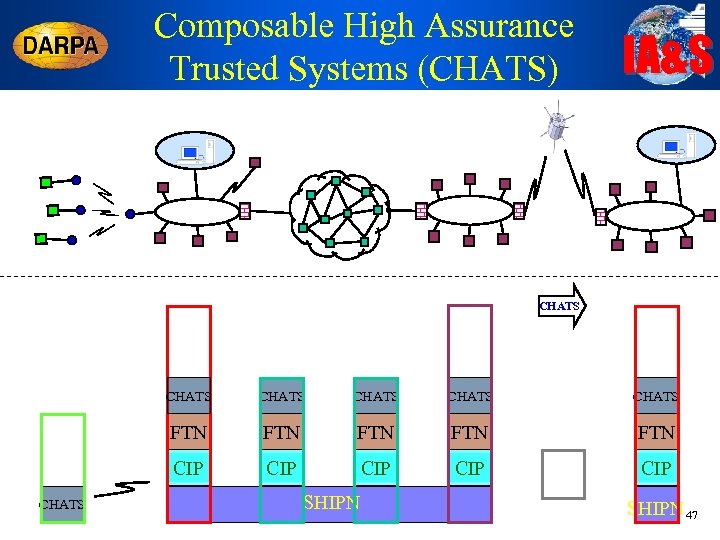 Composable High Assurance Trusted Systems (CHATS) IA&S CHATS CHATS FTN FTN FTN CIP CHATS CIP CIP SHIPN 47
Composable High Assurance Trusted Systems (CHATS) IA&S CHATS CHATS FTN FTN FTN CIP CHATS CIP CIP SHIPN 47
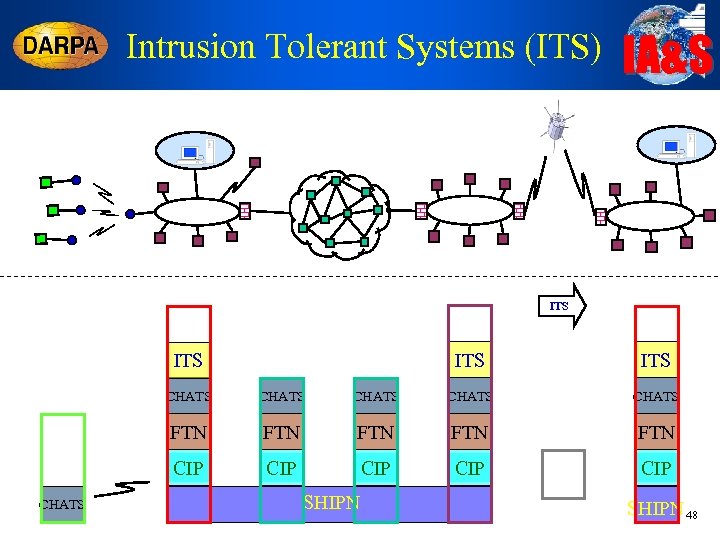 Intrusion Tolerant Systems (ITS) IA&S ITS ITS CHATS FTN FTN FTN CIP CHATS CIP CIP SHIPN 48
Intrusion Tolerant Systems (ITS) IA&S ITS ITS CHATS FTN FTN FTN CIP CHATS CIP CIP SHIPN 48
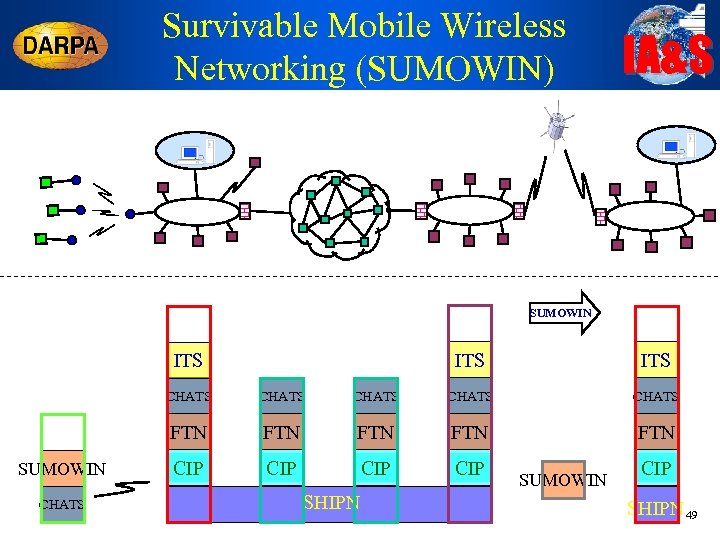 Survivable Mobile Wireless Networking (SUMOWIN) IA&S SUMOWIN ITS ITS CHATS CHATS FTN SUMOWIN CHATS FTN FTN CIP CIP SHIPN SUMOWIN CIP SHIPN 49
Survivable Mobile Wireless Networking (SUMOWIN) IA&S SUMOWIN ITS ITS CHATS CHATS FTN SUMOWIN CHATS FTN FTN CIP CIP SHIPN SUMOWIN CIP SHIPN 49
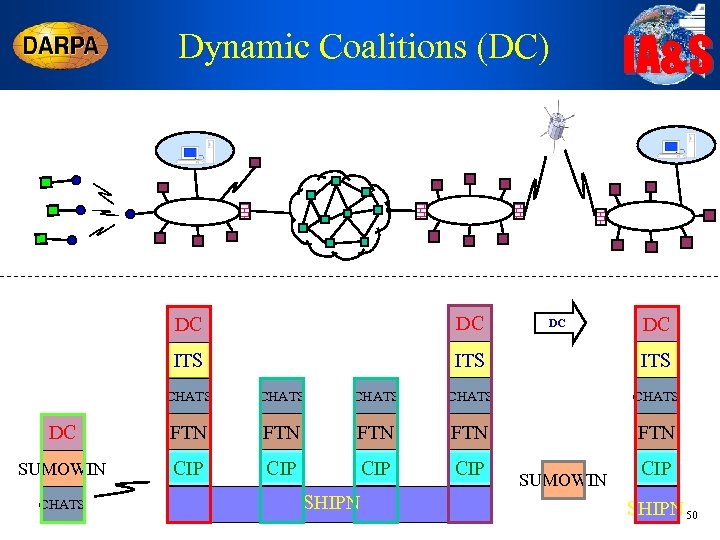 Dynamic Coalitions (DC) IA&S DC DC ITS ITS DC DC CHATS CHATS DC FTN FTN FTN SUMOWIN CIP CIP CHATS SHIPN SUMOWIN CIP SHIPN 50
Dynamic Coalitions (DC) IA&S DC DC ITS ITS DC DC CHATS CHATS DC FTN FTN FTN SUMOWIN CIP CIP CHATS SHIPN SUMOWIN CIP SHIPN 50
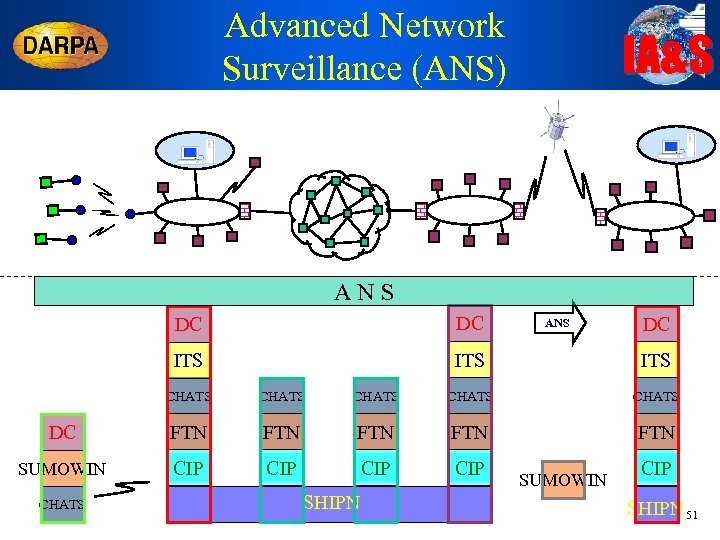 Advanced Network Surveillance (ANS) IA&S ANS DC DC ITS ITS ANS DC CHATS CHATS DC FTN FTN FTN SUMOWIN CIP CIP CHATS SHIPN SUMOWIN CIP SHIPN 51
Advanced Network Surveillance (ANS) IA&S ANS DC DC ITS ITS ANS DC CHATS CHATS DC FTN FTN FTN SUMOWIN CIP CIP CHATS SHIPN SUMOWIN CIP SHIPN 51
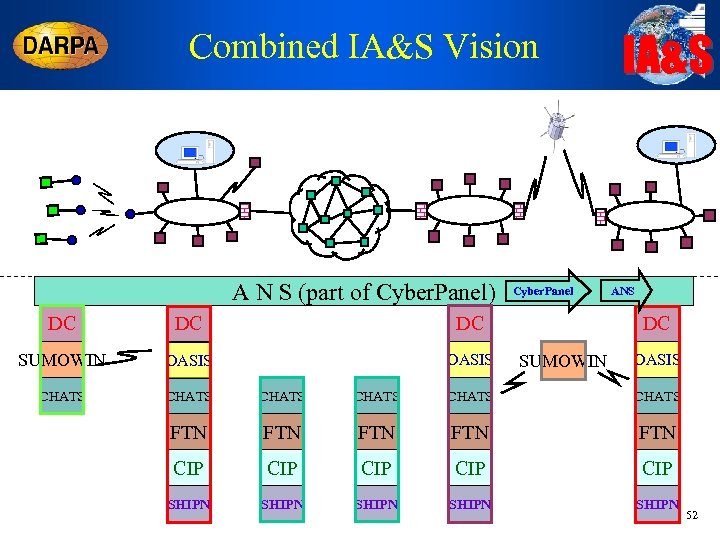 Combined IA&S Vision A N S (part of Cyber. Panel) Cyber. Panel IA&S ANS DC DC SUMOWIN OASIS CHATS CHATS FTN FTN FTN CIP CIP CIP SHIPN SHIPN SUMOWIN OASIS 52
Combined IA&S Vision A N S (part of Cyber. Panel) Cyber. Panel IA&S ANS DC DC SUMOWIN OASIS CHATS CHATS FTN FTN FTN CIP CIP CIP SHIPN SHIPN SUMOWIN OASIS 52
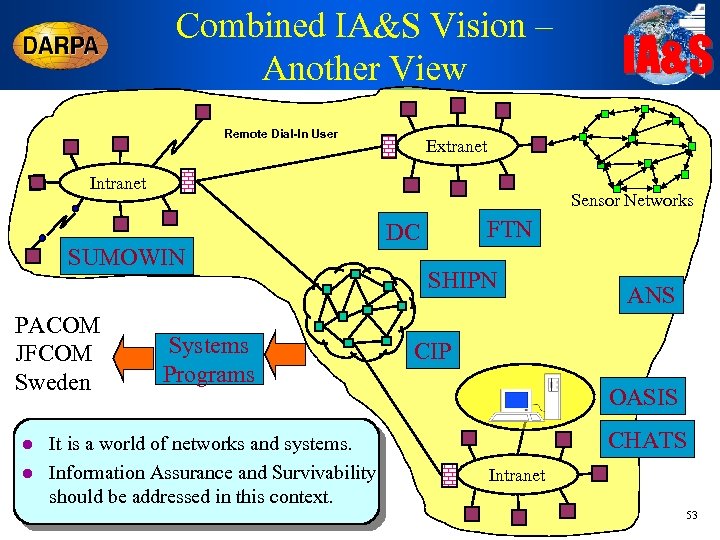 Combined IA&S Vision – Another View Remote Dial-In User Extranet Intranet Sensor Networks SUMOWIN PACOM JFCOM Sweden l l IA&S Systems Programs It is a world of networks and systems. Information Assurance and Survivability should be addressed in this context. FTN DC SHIPN ANS CIP OASIS CHATS Intranet 53
Combined IA&S Vision – Another View Remote Dial-In User Extranet Intranet Sensor Networks SUMOWIN PACOM JFCOM Sweden l l IA&S Systems Programs It is a world of networks and systems. Information Assurance and Survivability should be addressed in this context. FTN DC SHIPN ANS CIP OASIS CHATS Intranet 53
 Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 54
Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 54
 Other security and survivability research investments l IA&S Government-sponsored u NSA: n n u Services: Roughly $5 M/year each n n n u CIA counting on In-Q-Tel – dismantled OR&D; ARDA just getting started in Infosec NSF: n u Commercial-grade security focus; roughly $8 M/yr funding Other Intel: n u Main emphasis on intrusion detection, sanitization; Not focused on warfighting systems NIST: n u Focus on firewall, IDS deployments, operations; Not in the R&D business Do. E: n u Army: Main IA R&D focus is biometrics initiative Navy: Focusing on NMCI; pilot widespread rollout of 2 GS technologies Air Force: Thrusts in Computer/Network Forensics, Active Response DISA: n u Small fraction of RDT&E line is on security/survivability Focused on its own systems and COTS; weak links to services Focus on Critical Infrastructure Protection; spread over many small programs European Union: Multi-country projects in reliability and security n Relatively small investment 55
Other security and survivability research investments l IA&S Government-sponsored u NSA: n n u Services: Roughly $5 M/year each n n n u CIA counting on In-Q-Tel – dismantled OR&D; ARDA just getting started in Infosec NSF: n u Commercial-grade security focus; roughly $8 M/yr funding Other Intel: n u Main emphasis on intrusion detection, sanitization; Not focused on warfighting systems NIST: n u Focus on firewall, IDS deployments, operations; Not in the R&D business Do. E: n u Army: Main IA R&D focus is biometrics initiative Navy: Focusing on NMCI; pilot widespread rollout of 2 GS technologies Air Force: Thrusts in Computer/Network Forensics, Active Response DISA: n u Small fraction of RDT&E line is on security/survivability Focused on its own systems and COTS; weak links to services Focus on Critical Infrastructure Protection; spread over many small programs European Union: Multi-country projects in reliability and security n Relatively small investment 55
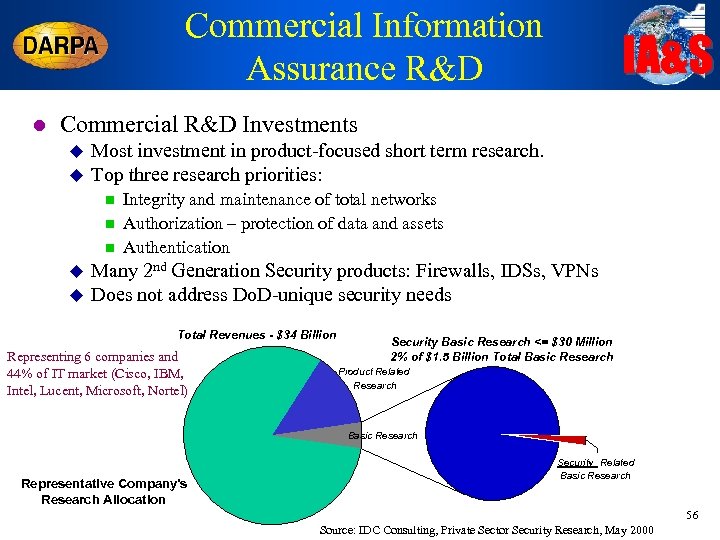 Commercial Information Assurance R&D l IA&S Commercial R&D Investments u u Most investment in product-focused short term research. Top three research priorities: n n n u u Integrity and maintenance of total networks Authorization – protection of data and assets Authentication Many 2 nd Generation Security products: Firewalls, IDSs, VPNs Does not address Do. D-unique security needs Total Revenues - $34 Billion Representing 6 companies and 44% of IT market (Cisco, IBM, Intel, Lucent, Microsoft, Nortel) Security Basic Research <= $30 Million 2% of $1. 5 Billion Total Basic Research Product Related Research Basic Research Representative Company's Research Allocation Security Related Basic Research 56 Source: IDC Consulting, Private Sector Security Research, May 2000
Commercial Information Assurance R&D l IA&S Commercial R&D Investments u u Most investment in product-focused short term research. Top three research priorities: n n n u u Integrity and maintenance of total networks Authorization – protection of data and assets Authentication Many 2 nd Generation Security products: Firewalls, IDSs, VPNs Does not address Do. D-unique security needs Total Revenues - $34 Billion Representing 6 companies and 44% of IT market (Cisco, IBM, Intel, Lucent, Microsoft, Nortel) Security Basic Research <= $30 Million 2% of $1. 5 Billion Total Basic Research Product Related Research Basic Research Representative Company's Research Allocation Security Related Basic Research 56 Source: IDC Consulting, Private Sector Security Research, May 2000
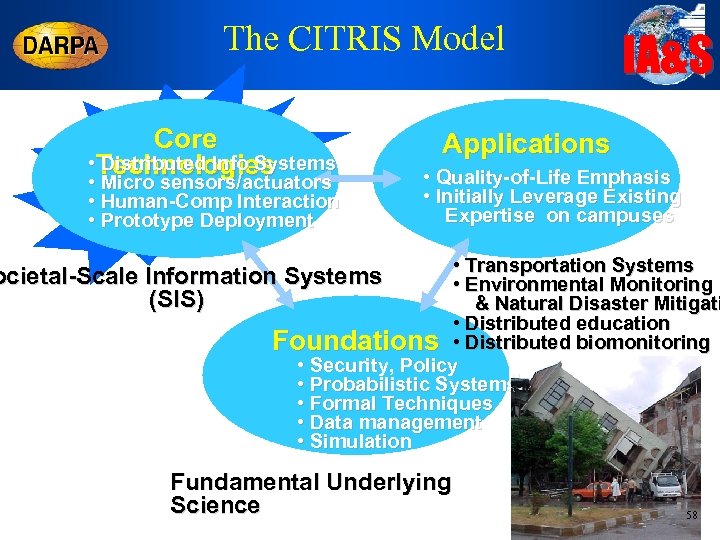
 IA&S Center For Information Technology Research In The Interest Of Society So what about what goes in Universities? CITRIS is a major new undertaking as a State + Industry + University partnership l l Major new initiative within the College of Engineering and on the Berkeley Campus Basis of a proposal to the State of California under the new California Institutes for Science and Innovation (Cal ISI) program Joint with UC Santa Cruz, UC Davis, UC Merced Over 90 faculty from 21 departments 57
IA&S Center For Information Technology Research In The Interest Of Society So what about what goes in Universities? CITRIS is a major new undertaking as a State + Industry + University partnership l l Major new initiative within the College of Engineering and on the Berkeley Campus Basis of a proposal to the State of California under the new California Institutes for Science and Innovation (Cal ISI) program Joint with UC Santa Cruz, UC Davis, UC Merced Over 90 faculty from 21 departments 57
 The CITRIS Model Core • Technologies Distributed Info Systems • Micro sensors/actuators • Human-Comp Interaction • Prototype Deployment IA&S Applications • Quality-of-Life Emphasis • Initially Leverage Existing Expertise on campuses • Transportation Systems ocietal-Scale Information Systems • Environmental Monitoring (SIS) & Natural Disaster Mitigati • Distributed education Foundations • Distributed biomonitoring • Security, Policy • Probabilistic Systems • Formal Techniques • Data management • Simulation Fundamental Underlying Science 58
The CITRIS Model Core • Technologies Distributed Info Systems • Micro sensors/actuators • Human-Comp Interaction • Prototype Deployment IA&S Applications • Quality-of-Life Emphasis • Initially Leverage Existing Expertise on campuses • Transportation Systems ocietal-Scale Information Systems • Environmental Monitoring (SIS) & Natural Disaster Mitigati • Distributed education Foundations • Distributed biomonitoring • Security, Policy • Probabilistic Systems • Formal Techniques • Data management • Simulation Fundamental Underlying Science 58
 CITRIS Societal Scale Info Systems IA&S l Transportation Systems u u u l Environmental Monitoring & Natural Disaster Mitigation u u l Provide efficient, personalized response in the face of earthquake, fire, flood Must function at maximum performance under very difficult circumstances Distributed Education u l By the use of sensors and advanced networking technology we can improve the efficiency and utility of California highways while reducing pollution levels Improve carpooling efficiency using advanced scheduling Improve freeway utilization by managing traffic flows We are proposing to build a life-long learning center that will be used to implement the first years of the Merced undergraduate CS program and then used for other internal, international, and industrial learning collaborations. Distributed Biomonitoring u u u Wristband biomonitors for chronic illness and the elderly Monitored remotely 24 x 7 x 365 Emergency response and potential remote drug delivery 59
CITRIS Societal Scale Info Systems IA&S l Transportation Systems u u u l Environmental Monitoring & Natural Disaster Mitigation u u l Provide efficient, personalized response in the face of earthquake, fire, flood Must function at maximum performance under very difficult circumstances Distributed Education u l By the use of sensors and advanced networking technology we can improve the efficiency and utility of California highways while reducing pollution levels Improve carpooling efficiency using advanced scheduling Improve freeway utilization by managing traffic flows We are proposing to build a life-long learning center that will be used to implement the first years of the Merced undergraduate CS program and then used for other internal, international, and industrial learning collaborations. Distributed Biomonitoring u u u Wristband biomonitors for chronic illness and the elderly Monitored remotely 24 x 7 x 365 Emergency response and potential remote drug delivery 59
 Societal-Scale Information System (SIS) IA&S l l l A revolutionary, planetary-scale Information Utility, enabling advanced technologies to be exploited by broad communities of users. An SIS learns how it is used and adapts its functions and interfaces to user demands and the context of their activities It achieves this through the provision of ‘fluid technologies’ for plug-andplay component interoperation, introspection, dynamic adaptation, component self-aggregation and self-organization, and ‘extreme personalization. ’ Easily and naturally integrate devices, ranging from tiny sensors and actuators to hand-held information appliances, workstations, and buildingsized cluster supercomputers—‘virtual computers’ Connected by short-range, unreliable wireless networks as well as by very high-bandwidth, high-latency long-haul optical backbones. Data and services must be secure, reliable, and high-performance, even if part of the system is overloaded, down, disconnected, under repair, or under attack 60
Societal-Scale Information System (SIS) IA&S l l l A revolutionary, planetary-scale Information Utility, enabling advanced technologies to be exploited by broad communities of users. An SIS learns how it is used and adapts its functions and interfaces to user demands and the context of their activities It achieves this through the provision of ‘fluid technologies’ for plug-andplay component interoperation, introspection, dynamic adaptation, component self-aggregation and self-organization, and ‘extreme personalization. ’ Easily and naturally integrate devices, ranging from tiny sensors and actuators to hand-held information appliances, workstations, and buildingsized cluster supercomputers—‘virtual computers’ Connected by short-range, unreliable wireless networks as well as by very high-bandwidth, high-latency long-haul optical backbones. Data and services must be secure, reliable, and high-performance, even if part of the system is overloaded, down, disconnected, under repair, or under attack 60
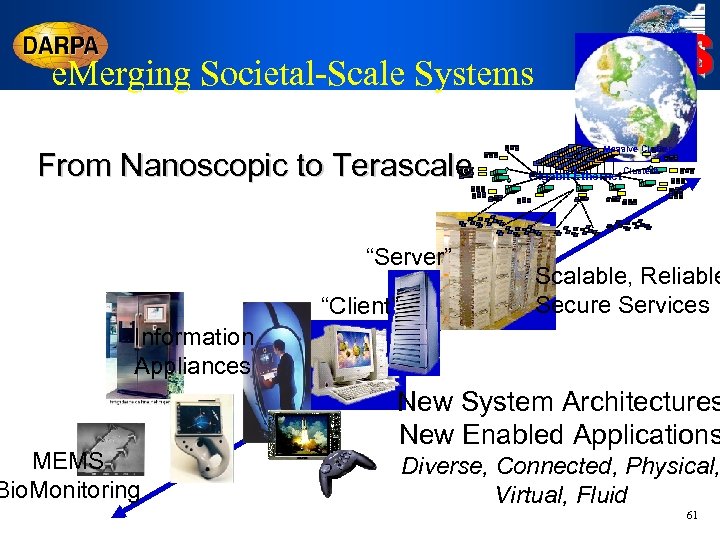 e. Merging Societal-Scale Systems From Nanoscopic to Terascale “Server” “Client” IA&S Massive Cluster Gigabit Ethernet Clusters Scalable, Reliable Secure Services Information Appliances MEMS Bio. Monitoring New System Architectures New Enabled Applications Diverse, Connected, Physical, Virtual, Fluid 61
e. Merging Societal-Scale Systems From Nanoscopic to Terascale “Server” “Client” IA&S Massive Cluster Gigabit Ethernet Clusters Scalable, Reliable Secure Services Information Appliances MEMS Bio. Monitoring New System Architectures New Enabled Applications Diverse, Connected, Physical, Virtual, Fluid 61
 COTS Dust IA&S ATMEL 4 Mhz CPU RFM 916 MHz radio OOK 10 -100 m range 64 KB EEPROM Sensor Bus: 7 Analog sensors u 2 I 2 C buses u 1 SPI bus u l. Runs Tiny OS l 2 weeks on AA batteries l 1% duty w/ solar power (indoors) l. Available from Crossbow (xbow. com) for ~$200 62
COTS Dust IA&S ATMEL 4 Mhz CPU RFM 916 MHz radio OOK 10 -100 m range 64 KB EEPROM Sensor Bus: 7 Analog sensors u 2 I 2 C buses u 1 SPI bus u l. Runs Tiny OS l 2 weeks on AA batteries l 1% duty w/ solar power (indoors) l. Available from Crossbow (xbow. com) for ~$200 62
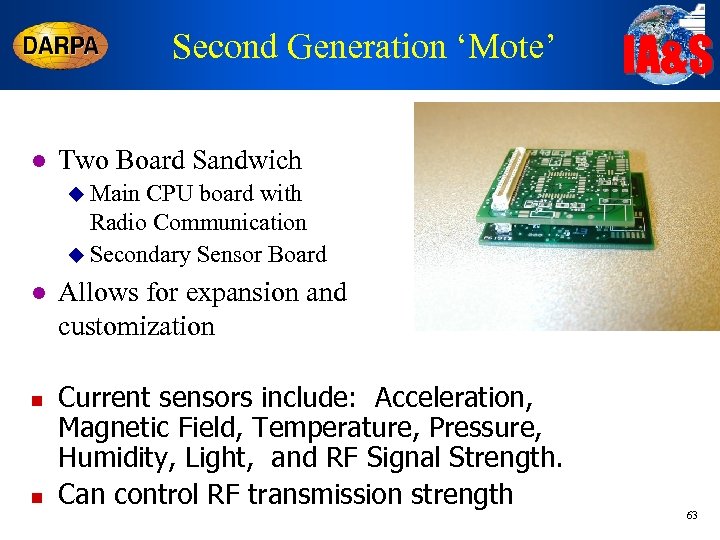 Second Generation ‘Mote’ l IA&S Two Board Sandwich u Main CPU board with Radio Communication u Secondary Sensor Board l n n Allows for expansion and customization Current sensors include: Acceleration, Magnetic Field, Temperature, Pressure, Humidity, Light, and RF Signal Strength. Can control RF transmission strength 63
Second Generation ‘Mote’ l IA&S Two Board Sandwich u Main CPU board with Radio Communication u Secondary Sensor Board l n n Allows for expansion and customization Current sensors include: Acceleration, Magnetic Field, Temperature, Pressure, Humidity, Light, and RF Signal Strength. Can control RF transmission strength 63
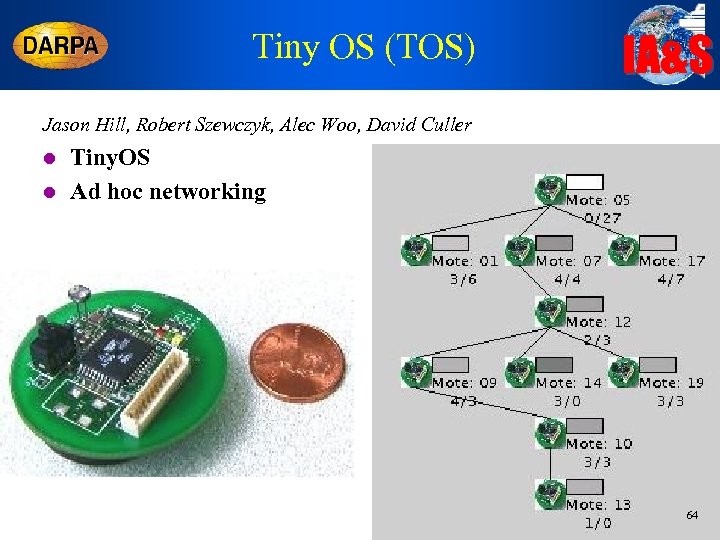 Tiny OS (TOS) IA&S Jason Hill, Robert Szewczyk, Alec Woo, David Culler l l Tiny. OS Ad hoc networking 64
Tiny OS (TOS) IA&S Jason Hill, Robert Szewczyk, Alec Woo, David Culler l l Tiny. OS Ad hoc networking 64
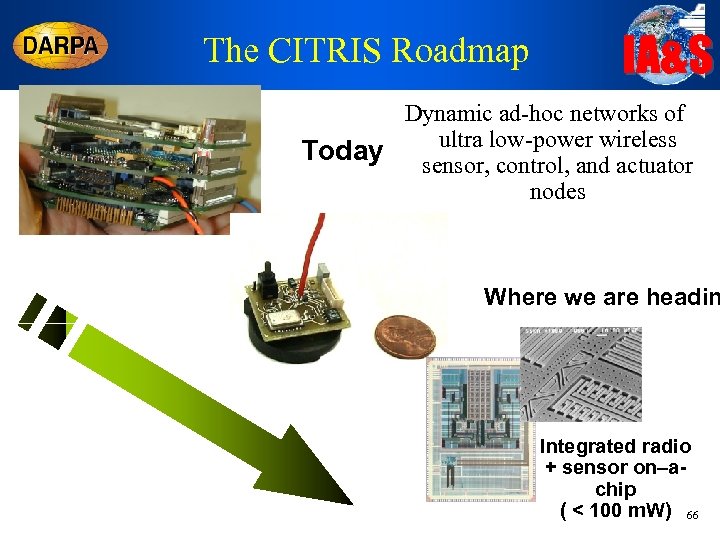 The CITRIS Roadmap IA&S Dynamic ad-hoc networks of ultra low-power wireless Today sensor, control, and actuator nodes Where we are headin Integrated radio + sensor on–achip ( < 100 m. W) 66
The CITRIS Roadmap IA&S Dynamic ad-hoc networks of ultra low-power wireless Today sensor, control, and actuator nodes Where we are headin Integrated radio + sensor on–achip ( < 100 m. W) 66
 New Building Technologies l IA&S Wireless Sensing and Control u Develop low cost, small wireless devices u Track temperature, humidity, illumination and occupancy, l Underfloor Air Distribution u Thermal and energy performance u Occupant response u Technology transfer to design industry l Task/Ambient Conditioning Systems 67
New Building Technologies l IA&S Wireless Sensing and Control u Develop low cost, small wireless devices u Track temperature, humidity, illumination and occupancy, l Underfloor Air Distribution u Thermal and energy performance u Occupant response u Technology transfer to design industry l Task/Ambient Conditioning Systems 67
 A Proof-of-Concept: IA&S Electric Power Monitoring/Control Leaders: Pister, Culler, Trent, Sastry, Rabaey l “Easy”: u l “Medium”: u u u l Fully instrument a number of buildings on campus with networked light and temperature sensors in every room, and make the data available on a centralized web-site. Make a wireless power monitor with a standard 3 -prong feedthrough receptacle so that people can monitor power consumption of electronic devices as a function of time. Similar device, but passively coupled to high-power wiring to monitor total power consumption through breaker boxes. This would give us a much finer granularity of power-consumption details, and let us look at clusters of rooms, floors, etc. Fully instrument the campus power distribution system “Hard”: u Real-time monitoring and control of hundreds of power systems on campus. Enforce compliance with load reduction. Charge/reward departments according to their use during peak times. 68
A Proof-of-Concept: IA&S Electric Power Monitoring/Control Leaders: Pister, Culler, Trent, Sastry, Rabaey l “Easy”: u l “Medium”: u u u l Fully instrument a number of buildings on campus with networked light and temperature sensors in every room, and make the data available on a centralized web-site. Make a wireless power monitor with a standard 3 -prong feedthrough receptacle so that people can monitor power consumption of electronic devices as a function of time. Similar device, but passively coupled to high-power wiring to monitor total power consumption through breaker boxes. This would give us a much finer granularity of power-consumption details, and let us look at clusters of rooms, floors, etc. Fully instrument the campus power distribution system “Hard”: u Real-time monitoring and control of hundreds of power systems on campus. Enforce compliance with load reduction. Charge/reward departments according to their use during peak times. 68
 Information Technology Research and Development * IA&S * 69
Information Technology Research and Development * IA&S * 69
 HCSS Coordinating Group l IA&S Group Structure and Activities u Agencies currently actively participating: DARPA, NSF, NASA, NIST, FAA, FDA, other Do. D organizations u HCSS Research Agenda developed with input from research community u HCSS Interagency Workshops 70
HCSS Coordinating Group l IA&S Group Structure and Activities u Agencies currently actively participating: DARPA, NSF, NASA, NIST, FAA, FDA, other Do. D organizations u HCSS Research Agenda developed with input from research community u HCSS Interagency Workshops 70
 HCSS Technology Goals IA&S l Provide a sound theoretical, scientific, and technological basis for assured construction of safe, secure systems. l Develop hardware, software, and system engineering tools that incorporate ubiquitous, application-based, domain-based, and risk-based assurance. l Reduce the effort, time, and cost of assurance and quality certification processes. l Provide a technology base of public domain, advancedprototype implementations of high-confidence technologies to enable rapid adoption. l Provide measures of results. 71
HCSS Technology Goals IA&S l Provide a sound theoretical, scientific, and technological basis for assured construction of safe, secure systems. l Develop hardware, software, and system engineering tools that incorporate ubiquitous, application-based, domain-based, and risk-based assurance. l Reduce the effort, time, and cost of assurance and quality certification processes. l Provide a technology base of public domain, advancedprototype implementations of high-confidence technologies to enable rapid adoption. l Provide measures of results. 71
 HCSS Research Agenda l Foundations u u u l Safety Security Assurance Engineering & Experimentation u u u l Technology & Tools u u Programming Languages, tools, environments Systems Software Metrics & Evidence Robust System Design l IA&S Assured PKI Control Systems Hardware Verification Pilot Applications u u Aviation Safety Medical Device Safety Digital Government PKI for Advanced Networks 72
HCSS Research Agenda l Foundations u u u l Safety Security Assurance Engineering & Experimentation u u u l Technology & Tools u u Programming Languages, tools, environments Systems Software Metrics & Evidence Robust System Design l IA&S Assured PKI Control Systems Hardware Verification Pilot Applications u u Aviation Safety Medical Device Safety Digital Government PKI for Advanced Networks 72
 HCSS Basic and Technology Research IA&S HCSS Foundations: l Supporting theory and scientific base for engineering and certifying High Confidence Software & Systems Research areas: u u Theory n Safety n Security n Assurance Specification Interoperability Composition HCSS Tools and Techniques: l Developing the engineering tools, libraries, and techniques required to build and certify large-scale, high confidence systems. Research Areas: u u u u Assurance-bearing programming languages & tools, and correct-byconstruction code synthesis environments Modeling and simulation Robust system design Monitoring and detection Validation Evidence and metrics Process 73
HCSS Basic and Technology Research IA&S HCSS Foundations: l Supporting theory and scientific base for engineering and certifying High Confidence Software & Systems Research areas: u u Theory n Safety n Security n Assurance Specification Interoperability Composition HCSS Tools and Techniques: l Developing the engineering tools, libraries, and techniques required to build and certify large-scale, high confidence systems. Research Areas: u u u u Assurance-bearing programming languages & tools, and correct-byconstruction code synthesis environments Modeling and simulation Robust system design Monitoring and detection Validation Evidence and metrics Process 73
 Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 74
Outline l l l l IA&S DARPA Description DARPA (Re-)Organization and IA-related Impacts Past IA-related Research Programs Motivation - Why Information Assurance Research? Current Research Programs Future Research Programs The Rest of the Community – Do. D and Commercial Concluding Remarks 74
 Concluding Remarks l Joint Vision 2020 requires high assurance networks and systems u u l IA&S Cyber threats are real and growing and, if not countered in time, will prevent Do. D from achieving information superiority Breakthrough technologies must be developed now to neutralize cyber threats, both peacetime harassment and nation-state IW attacks DARPA has created a suite of Information Assurance and Survivability technology and systems programs that will: u Provide a revolutionary technology base to: n n u Reduce adversaries’ opportunities to attack Allow critical systems to withstand operate through cyber attacks Provide commanders means to defend against large scale cyber attacks Create future assured infrastructure components for the Do. D Enable rapid transition to real Do. D networks & systems via pathfinder prototype demonstrations 75
Concluding Remarks l Joint Vision 2020 requires high assurance networks and systems u u l IA&S Cyber threats are real and growing and, if not countered in time, will prevent Do. D from achieving information superiority Breakthrough technologies must be developed now to neutralize cyber threats, both peacetime harassment and nation-state IW attacks DARPA has created a suite of Information Assurance and Survivability technology and systems programs that will: u Provide a revolutionary technology base to: n n u Reduce adversaries’ opportunities to attack Allow critical systems to withstand operate through cyber attacks Provide commanders means to defend against large scale cyber attacks Create future assured infrastructure components for the Do. D Enable rapid transition to real Do. D networks & systems via pathfinder prototype demonstrations 75
 IA&S BACKUPS 76
IA&S BACKUPS 76
 Foundations - Issues l Theory u Modeling and reasoning n n u l IA&S Physical effects of system actions controlled by software, hybrid discrete/continuous models Assurance and trustworthiness, criticality, uncertainty Event detection and propagation analyses, scalable approaches to evidence and forensics Model validation Domain theories: safety, security, adaptive software and systems; critical properties Composition u Scalability n u Hierarchical model composition: refinement/abstraction, peer hierarchies Interference 77
Foundations - Issues l Theory u Modeling and reasoning n n u l IA&S Physical effects of system actions controlled by software, hybrid discrete/continuous models Assurance and trustworthiness, criticality, uncertainty Event detection and propagation analyses, scalable approaches to evidence and forensics Model validation Domain theories: safety, security, adaptive software and systems; critical properties Composition u Scalability n u Hierarchical model composition: refinement/abstraction, peer hierarchies Interference 77
 Foundations - Issues l IA&S Specification u Notations n n n l General purpose vs. domain-specific, problem-based Usability, soundness, support for analysis Language and logic automation/interaction Interoperability u Mixed n n n strategies and theories Formal/informal; complete/incomplete; deterministic/nondeterministic/stochastic; general/domain-specific; discrete/continuous; abstract/concrete/multilevel; compositional/interfering Software, operating systems, and middleware Layered vs. peer components, sound theoretical frameworks for specialization, staging, adaptation 78
Foundations - Issues l IA&S Specification u Notations n n n l General purpose vs. domain-specific, problem-based Usability, soundness, support for analysis Language and logic automation/interaction Interoperability u Mixed n n n strategies and theories Formal/informal; complete/incomplete; deterministic/nondeterministic/stochastic; general/domain-specific; discrete/continuous; abstract/concrete/multilevel; compositional/interfering Software, operating systems, and middleware Layered vs. peer components, sound theoretical frameworks for specialization, staging, adaptation 78
 Tools & Technologies - Issues l Interoperable robust system design technology u u u g in m Ti u l IA&S Domain and requirements analysis tools End-to-end (system, environment, uncertainty/disturbance) modeling and simulation tools, model-based runtime frameworks Verified design patterns and instantiation support Monitoring, detection, fault identification, tolerance, and adaptation mechanisms Assured software technology u u Language as a carrier for logic Correct-by-construction software n n n u Integrated mathematical design and software generation technology High-confidence middleware and OS components Formal aspect-oriented programming Domain-specific language and tool technology 79
Tools & Technologies - Issues l Interoperable robust system design technology u u u g in m Ti u l IA&S Domain and requirements analysis tools End-to-end (system, environment, uncertainty/disturbance) modeling and simulation tools, model-based runtime frameworks Verified design patterns and instantiation support Monitoring, detection, fault identification, tolerance, and adaptation mechanisms Assured software technology u u Language as a carrier for logic Correct-by-construction software n n n u Integrated mathematical design and software generation technology High-confidence middleware and OS components Formal aspect-oriented programming Domain-specific language and tool technology 79
 Tools & Technologies - Issues l IA&S Evidence and assurance technology u Tools for practical, sound evidence extraction and management n n n l l Coordinated formal, analytic and test-generating tools Lightweight verification and extended type systems Proof-carrying code Assume-guarantee reasoning Testing for validation Next generation hardware/software co-design HCSS Building Blocks u Technology base of components for implementing and checking high-confidence properties 80
Tools & Technologies - Issues l IA&S Evidence and assurance technology u Tools for practical, sound evidence extraction and management n n n l l Coordinated formal, analytic and test-generating tools Lightweight verification and extended type systems Proof-carrying code Assume-guarantee reasoning Testing for validation Next generation hardware/software co-design HCSS Building Blocks u Technology base of components for implementing and checking high-confidence properties 80
 HCSS Technology Evaluation and IA&S Transition HCSS Engineering and Experimentation: u u u Evaluate tools and techniques at realistic scales Derive empirical data about increased confidence and cost effectiveness Provide reference implementations & evidence Experiment in challenging system engineering areas Provide useful building blocks n Software control of physical systems n Hardware /software platforms n High mobility systems n Assured public key infrastructure n Assured middleware HCSS Pilot Applications: u Critical Domain Applications, e. g. , n Aviation, Transportation Safety n Medical/Biological Device Safety n Digital Government n Public Key Infrastructure for Advanced Networks n Others to be Defined 81
HCSS Technology Evaluation and IA&S Transition HCSS Engineering and Experimentation: u u u Evaluate tools and techniques at realistic scales Derive empirical data about increased confidence and cost effectiveness Provide reference implementations & evidence Experiment in challenging system engineering areas Provide useful building blocks n Software control of physical systems n Hardware /software platforms n High mobility systems n Assured public key infrastructure n Assured middleware HCSS Pilot Applications: u Critical Domain Applications, e. g. , n Aviation, Transportation Safety n Medical/Biological Device Safety n Digital Government n Public Key Infrastructure for Advanced Networks n Others to be Defined 81


