 http: //www. engr. uconn. edu/~steve@engr. uconn. edu
http: //www. engr. uconn. edu/~steve@engr. uconn. edu
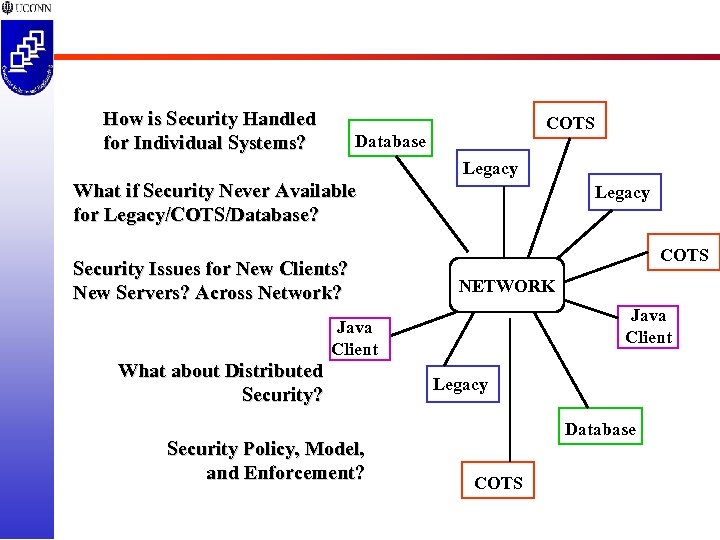 How is Security Handled for Individual Systems? COTS Database Legacy What if Security Never Available for Legacy/COTS/Database? Security Issues for New Clients? New Servers? Across Network? Legacy COTS NETWORK Java Client What about Distributed Security? Security Policy, Model, and Enforcement? Legacy Database COTS
How is Security Handled for Individual Systems? COTS Database Legacy What if Security Never Available for Legacy/COTS/Database? Security Issues for New Clients? New Servers? Across Network? Legacy COTS NETWORK Java Client What about Distributed Security? Security Policy, Model, and Enforcement? Legacy Database COTS
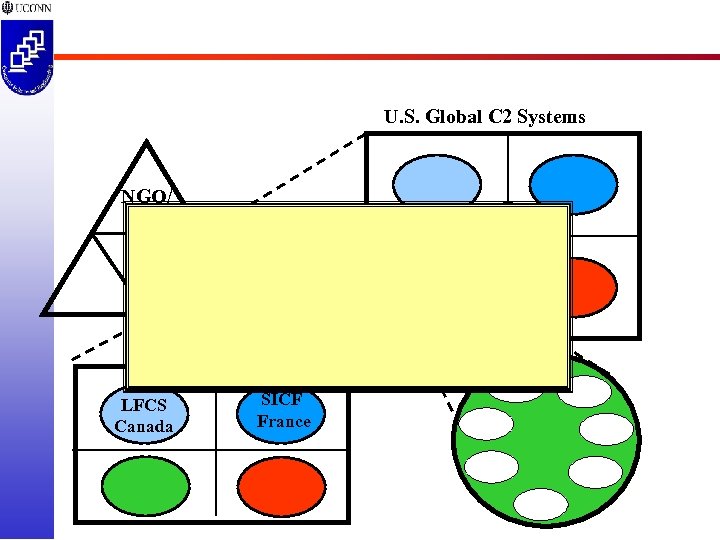 U. S. Global C 2 Systems NGO/ PVO LFCS Canada GCCS SICF France
U. S. Global C 2 Systems NGO/ PVO LFCS Canada GCCS SICF France
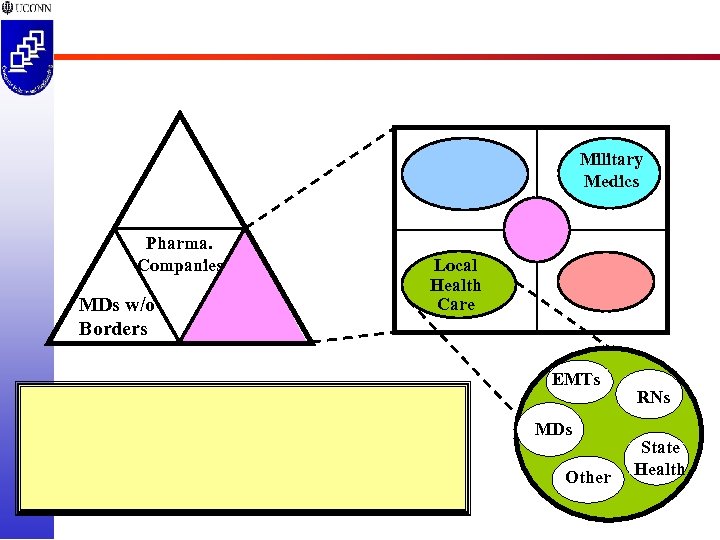 Military Medics Pharma. Companies MDs w/o Borders Local Health Care EMTs MDs Other RNs State Health
Military Medics Pharma. Companies MDs w/o Borders Local Health Care EMTs MDs Other RNs State Health
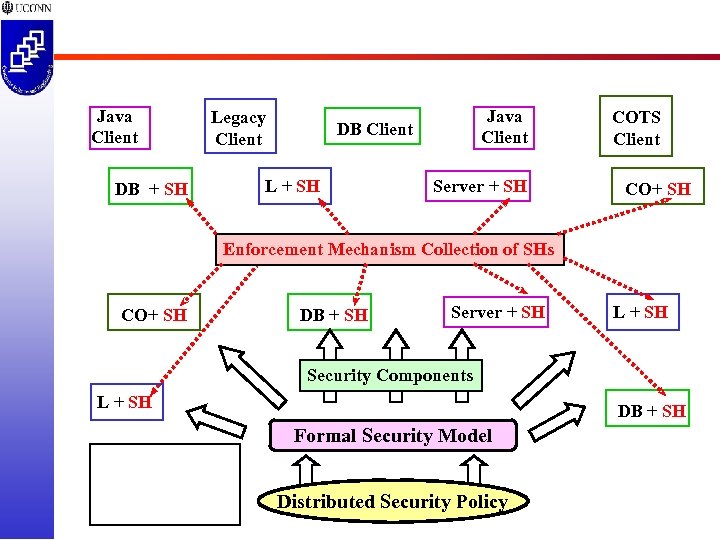 Java Client DB + SH Legacy Client Java Client DB Client L + SH Server + SH COTS Client CO+ SH Enforcement Mechanism Collection of SHs CO+ SH DB + SH Server + SH L + SH Security Components L + SH DB + SH Formal Security Model Distributed Security Policy
Java Client DB + SH Legacy Client Java Client DB Client L + SH Server + SH COTS Client CO+ SH Enforcement Mechanism Collection of SHs CO+ SH DB + SH Server + SH L + SH Security Components L + SH DB + SH Formal Security Model Distributed Security Policy
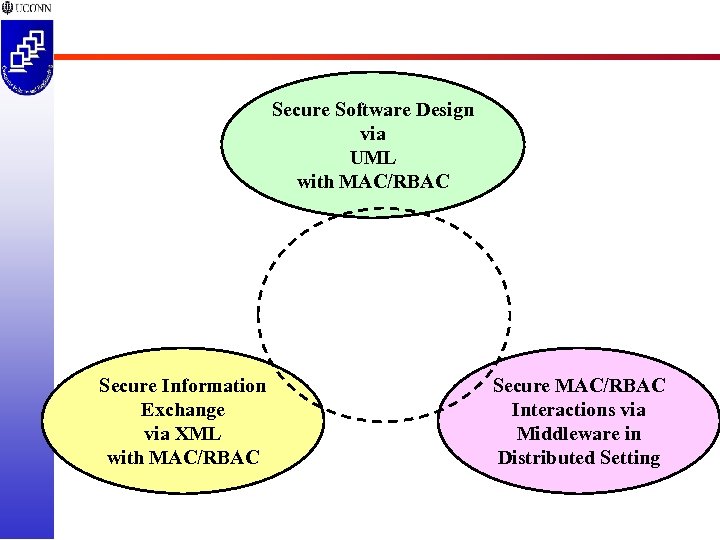 Secure Software Design via UML with MAC/RBAC Secure Information Exchange via XML with MAC/RBAC Secure MAC/RBAC Interactions via Middleware in Distributed Setting
Secure Software Design via UML with MAC/RBAC Secure Information Exchange via XML with MAC/RBAC Secure MAC/RBAC Interactions via Middleware in Distributed Setting
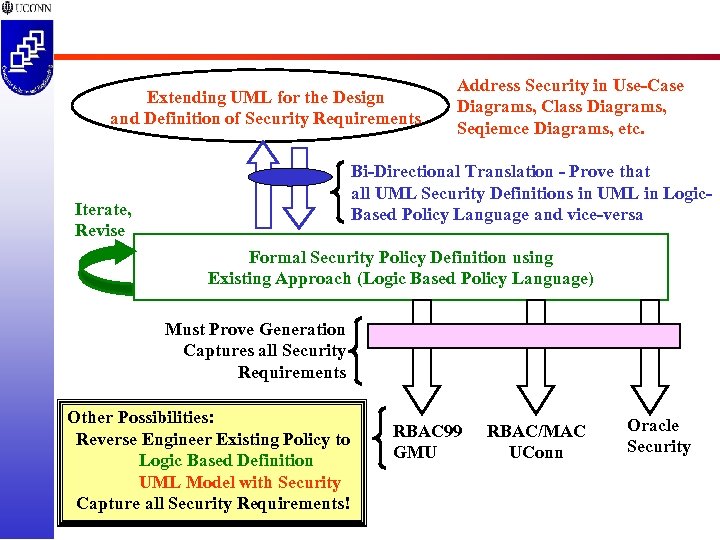 Extending UML for the Design and Definition of Security Requirements Address Security in Use-Case Diagrams, Class Diagrams, Seqiemce Diagrams, etc. Bi-Directional Translation - Prove that all UML Security Definitions in UML in Logic. Based Policy Language and vice-versa Iterate, Revise Formal Security Policy Definition using Existing Approach (Logic Based Policy Language) Must Prove Generation Captures all Security Requirements Other Possibilities: Reverse Engineer Existing Policy to Logic Based Definition UML Model with Security Capture all Security Requirements! RBAC 99 GMU RBAC/MAC UConn Oracle Security
Extending UML for the Design and Definition of Security Requirements Address Security in Use-Case Diagrams, Class Diagrams, Seqiemce Diagrams, etc. Bi-Directional Translation - Prove that all UML Security Definitions in UML in Logic. Based Policy Language and vice-versa Iterate, Revise Formal Security Policy Definition using Existing Approach (Logic Based Policy Language) Must Prove Generation Captures all Security Requirements Other Possibilities: Reverse Engineer Existing Policy to Logic Based Definition UML Model with Security Capture all Security Requirements! RBAC 99 GMU RBAC/MAC UConn Oracle Security
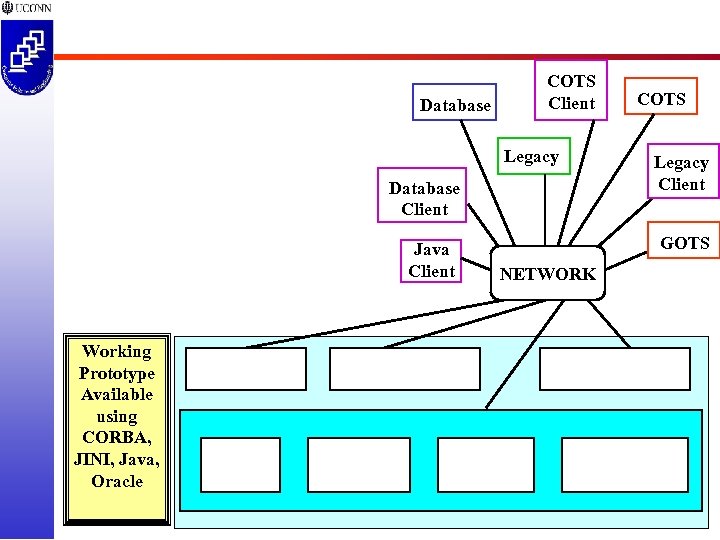 Database COTS Client Legacy Database Client Java Client Working Prototype Available using CORBA, JINI, Java, Oracle COTS Legacy Client GOTS NETWORK
Database COTS Client Legacy Database Client Java Client Working Prototype Available using CORBA, JINI, Java, Oracle COTS Legacy Client GOTS NETWORK