119d5be7514758164b20b6a810c2c83d.ppt
- Количество слайдов: 21
 http: //www. csc. gatech. edu/copeland/jac/6612/ Prof. John A. Copeland john. copeland@ece. gatech. edu 404 894 -5177 fax 404 894 -0035 Office: Klaus 3362 email or call for office visit Chapter 5 b - Secure/Multipurpose Internet Mail Extensions S/MIME
http: //www. csc. gatech. edu/copeland/jac/6612/ Prof. John A. Copeland john. copeland@ece. gatech. edu 404 894 -5177 fax 404 894 -0035 Office: Klaus 3362 email or call for office visit Chapter 5 b - Secure/Multipurpose Internet Mail Extensions S/MIME
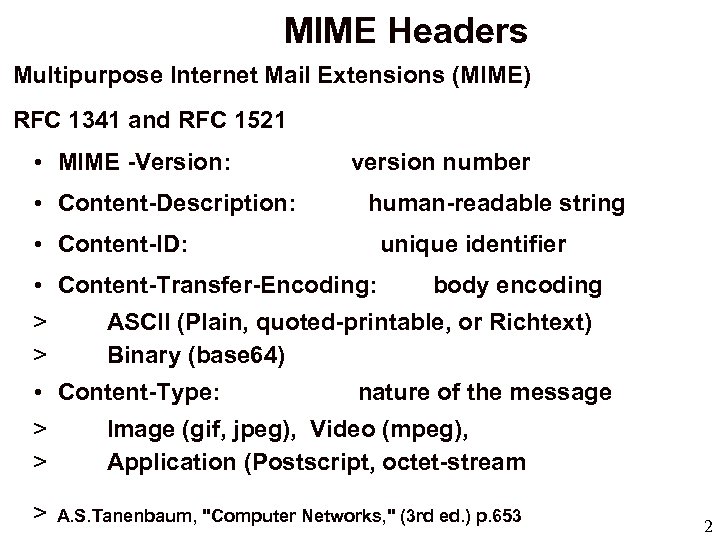 MIME Headers Multipurpose Internet Mail Extensions (MIME) RFC 1341 and RFC 1521 • MIME -Version: • Content-Description: version number human-readable string • Content-ID: unique identifier • Content-Transfer-Encoding: > > body encoding ASCII (Plain, quoted-printable, or Richtext) Binary (base 64) • Content-Type: nature of the message > > Image (gif, jpeg), Video (mpeg), Application (Postscript, octet-stream > A. S. Tanenbaum, "Computer Networks, " (3 rd ed. ) p. 653 2
MIME Headers Multipurpose Internet Mail Extensions (MIME) RFC 1341 and RFC 1521 • MIME -Version: • Content-Description: version number human-readable string • Content-ID: unique identifier • Content-Transfer-Encoding: > > body encoding ASCII (Plain, quoted-printable, or Richtext) Binary (base 64) • Content-Type: nature of the message > > Image (gif, jpeg), Video (mpeg), Application (Postscript, octet-stream > A. S. Tanenbaum, "Computer Networks, " (3 rd ed. ) p. 653 2
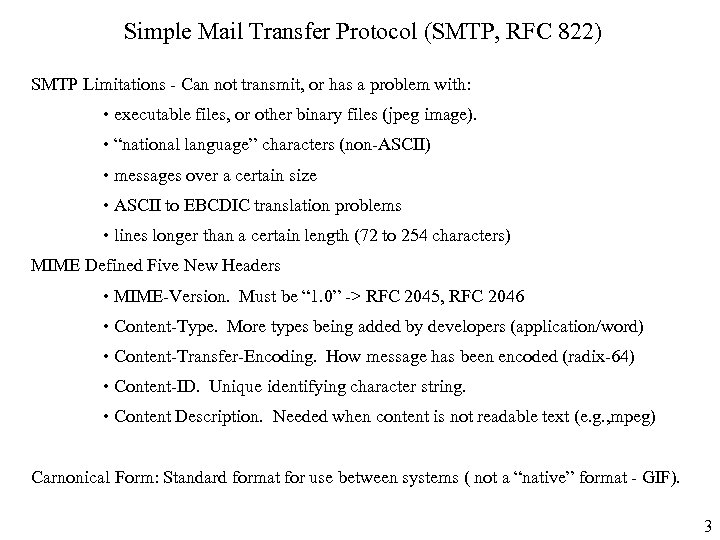 Simple Mail Transfer Protocol (SMTP, RFC 822) SMTP Limitations - Can not transmit, or has a problem with: • executable files, or other binary files (jpeg image). • “national language” characters (non-ASCII) • messages over a certain size • ASCII to EBCDIC translation problems • lines longer than a certain length (72 to 254 characters) MIME Defined Five New Headers • MIME-Version. Must be “ 1. 0” -> RFC 2045, RFC 2046 • Content-Type. More types being added by developers (application/word) • Content-Transfer-Encoding. How message has been encoded (radix-64) • Content-ID. Unique identifying character string. • Content Description. Needed when content is not readable text (e. g. , mpeg) Carnonical Form: Standard format for use between systems ( not a “native” format - GIF). 3
Simple Mail Transfer Protocol (SMTP, RFC 822) SMTP Limitations - Can not transmit, or has a problem with: • executable files, or other binary files (jpeg image). • “national language” characters (non-ASCII) • messages over a certain size • ASCII to EBCDIC translation problems • lines longer than a certain length (72 to 254 characters) MIME Defined Five New Headers • MIME-Version. Must be “ 1. 0” -> RFC 2045, RFC 2046 • Content-Type. More types being added by developers (application/word) • Content-Transfer-Encoding. How message has been encoded (radix-64) • Content-ID. Unique identifying character string. • Content Description. Needed when content is not readable text (e. g. , mpeg) Carnonical Form: Standard format for use between systems ( not a “native” format - GIF). 3
 Secure/MIME Can “sign” and/or encrypt messages Functions: • Enveloped Data: Encrypted content and encrypted session keys for recipients. • Signed Data: Message Digest encrypted with private key of “signer. ” • Clear-Signed Data: Signed but not encrypted. • Signed and Enveloped Data: Various orderings for encrypting and signing. Algorithms Used • Message Digesting: SHA-1 and MDS • Digital Signatures: DSS • Secret-Key Encryption: Triple-DES, RC 2/40 (exportable) • Public-Private Key Encryption: RSA with key sizes of 512 and 1024 bits, and Diffie-Hellman (for session keys). 4
Secure/MIME Can “sign” and/or encrypt messages Functions: • Enveloped Data: Encrypted content and encrypted session keys for recipients. • Signed Data: Message Digest encrypted with private key of “signer. ” • Clear-Signed Data: Signed but not encrypted. • Signed and Enveloped Data: Various orderings for encrypting and signing. Algorithms Used • Message Digesting: SHA-1 and MDS • Digital Signatures: DSS • Secret-Key Encryption: Triple-DES, RC 2/40 (exportable) • Public-Private Key Encryption: RSA with key sizes of 512 and 1024 bits, and Diffie-Hellman (for session keys). 4
 S/MIME - User Agent Role S/MIME uses Public-Key Certificates - X. 509 version 3 signed by Certification Authority Functions: • Key Generation - Diffie-Hellman, DSS, and RSA key-pairs. • Registration - Public keys must be registered with X. 509 CA. (Thawte (sub. of Veri. Sign), CAcert, . . . ) offer free registration) • Certificate Storage - Local (as in browser application) for different services. • Signed and Enveloped Data: Various orderings for encrypting and signing. Example: Verisign (www. verisign. com) • Class-1 Buyer’s email address confirmed by emailing vital info. • Class-2 Postal address is confirmed as well, and data checked against diectories. • Class-3 Buyer must appear in person, or send notarized documents. 5
S/MIME - User Agent Role S/MIME uses Public-Key Certificates - X. 509 version 3 signed by Certification Authority Functions: • Key Generation - Diffie-Hellman, DSS, and RSA key-pairs. • Registration - Public keys must be registered with X. 509 CA. (Thawte (sub. of Veri. Sign), CAcert, . . . ) offer free registration) • Certificate Storage - Local (as in browser application) for different services. • Signed and Enveloped Data: Various orderings for encrypting and signing. Example: Verisign (www. verisign. com) • Class-1 Buyer’s email address confirmed by emailing vital info. • Class-2 Postal address is confirmed as well, and data checked against diectories. • Class-3 Buyer must appear in person, or send notarized documents. 5
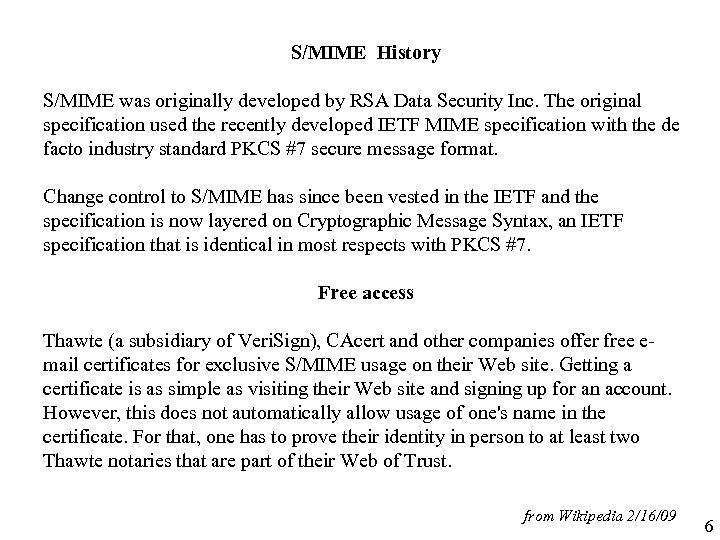 S/MIME History S/MIME was originally developed by RSA Data Security Inc. The original specification used the recently developed IETF MIME specification with the de facto industry standard PKCS #7 secure message format. Change control to S/MIME has since been vested in the IETF and the specification is now layered on Cryptographic Message Syntax, an IETF specification that is identical in most respects with PKCS #7. Free access Thawte (a subsidiary of Veri. Sign), CAcert and other companies offer free email certificates for exclusive S/MIME usage on their Web site. Getting a certificate is as simple as visiting their Web site and signing up for an account. However, this does not automatically allow usage of one's name in the certificate. For that, one has to prove their identity in person to at least two Thawte notaries that are part of their Web of Trust. from Wikipedia 2/16/09 6
S/MIME History S/MIME was originally developed by RSA Data Security Inc. The original specification used the recently developed IETF MIME specification with the de facto industry standard PKCS #7 secure message format. Change control to S/MIME has since been vested in the IETF and the specification is now layered on Cryptographic Message Syntax, an IETF specification that is identical in most respects with PKCS #7. Free access Thawte (a subsidiary of Veri. Sign), CAcert and other companies offer free email certificates for exclusive S/MIME usage on their Web site. Getting a certificate is as simple as visiting their Web site and signing up for an account. However, this does not automatically allow usage of one's name in the certificate. For that, one has to prove their identity in person to at least two Thawte notaries that are part of their Web of Trust. from Wikipedia 2/16/09 6
 S/MIME Certificates Before S/MIME can be used in any of the above applications, one must obtain and install an individual key/certificate either from one's in-house certificate authority (CA) or from a public CA such as one of those listed below. Best practice is to use separate private keys (and associated certificates) for Signature and for Encryption, as this permits escrow of the encryption key without compromise to the non-repudiation property of the signature key. Encryption requires having the destination party's certificate on store (which is typically automatic upon receiving a message from the party with a valid signing certificate). While it is technically possible to send a message encrypted (using the destination party certificate) without having one's own certificate to digitally sign, in practice, the S/MIME clients will require you install your own certificate before they allow encrypting to others. from Wikipedia 2/16/09 7
S/MIME Certificates Before S/MIME can be used in any of the above applications, one must obtain and install an individual key/certificate either from one's in-house certificate authority (CA) or from a public CA such as one of those listed below. Best practice is to use separate private keys (and associated certificates) for Signature and for Encryption, as this permits escrow of the encryption key without compromise to the non-repudiation property of the signature key. Encryption requires having the destination party's certificate on store (which is typically automatic upon receiving a message from the party with a valid signing certificate). While it is technically possible to send a message encrypted (using the destination party certificate) without having one's own certificate to digitally sign, in practice, the S/MIME clients will require you install your own certificate before they allow encrypting to others. from Wikipedia 2/16/09 7
 A typical basic personal certificate verifies the owner's identity only in terms of binding them to an email address and does not verify the person's name or business. The latter, if needed (e. g. for signing contracts), can be obtained through CAs that offer further verification (digital notary) services or managed PKI service. For more detail on authentication, see Digital Signature. Depending on the policy of the CA, your certificate and all its contents may be posted publicly for reference and verification. This makes your name and email address available for all to see and possibly search for. Other CAs only post serial numbers and revocation status, which does not include any of the personal information. The latter, at a minimum, is mandatory to uphold the integrity of the public key infrastructure. S/MIME is sometimes considered not properly suited for use via Webmail clients. Though support can be hacked into a browser, some security practices require the private key to be kept accessible to the user but inaccessible from the Webmail server, complicating the key Webmail advantage of providing ubiquitous accessibility. from Wikipedia 2/16/09 8
A typical basic personal certificate verifies the owner's identity only in terms of binding them to an email address and does not verify the person's name or business. The latter, if needed (e. g. for signing contracts), can be obtained through CAs that offer further verification (digital notary) services or managed PKI service. For more detail on authentication, see Digital Signature. Depending on the policy of the CA, your certificate and all its contents may be posted publicly for reference and verification. This makes your name and email address available for all to see and possibly search for. Other CAs only post serial numbers and revocation status, which does not include any of the personal information. The latter, at a minimum, is mandatory to uphold the integrity of the public key infrastructure. S/MIME is sometimes considered not properly suited for use via Webmail clients. Though support can be hacked into a browser, some security practices require the private key to be kept accessible to the user but inaccessible from the Webmail server, complicating the key Webmail advantage of providing ubiquitous accessibility. from Wikipedia 2/16/09 8
 General Email Problems SMTP Headers • Can be used to check email routing, but not reliable (spoofing, NAT, . . . ) • Can reveal your IP address, mail server to recipients Content Poisons: • Attachments that are executable files (viruses, Worms, Back Doors, . . . ) • HTML encoded mail has all the threats of an untrusted Web site Links can execute code FTP links can give away your email address, if used as password Hidden keys can identify the address of the message, ID of recipient Spammers use unwitting mail servers for exploding and relaying email, hiding their identity • This requires “Relaying Prohibited, ” makes sending email harder from the road 9
General Email Problems SMTP Headers • Can be used to check email routing, but not reliable (spoofing, NAT, . . . ) • Can reveal your IP address, mail server to recipients Content Poisons: • Attachments that are executable files (viruses, Worms, Back Doors, . . . ) • HTML encoded mail has all the threats of an untrusted Web site Links can execute code FTP links can give away your email address, if used as password Hidden keys can identify the address of the message, ID of recipient Spammers use unwitting mail servers for exploding and relaying email, hiding their identity • This requires “Relaying Prohibited, ” makes sending email harder from the road 9
 Email sent with: % telnet mail. ece. gatech. edu 25 >> YOU TYPE THIS. << WAIT FOR THIS REPLY FROM THE SMTP SERVER [COMMENTS] >> HELO c-66 -53 -58 -172. hsd 1. ga. comcast. net [must be actual DNS name of host being used] << 220 mail. ece. gatech. edu ESMTP Sendmail 8. 12. 10/8. 13. 4; Wed, 28 Sep 2005 17: 34: 44 -0400 (EDT) << 250 mail. ece. gatech. edu Hello ecevpn-021. ece-int. gatech. edu [192. 168. 66. 21], pleased to meet you >> MAIL FROM: copeland@ece. gatech. edu [must be an actual user on this server] << 250 2. 1. 0 copeland@ece. gatech. edu. . . Sender ok >> RCPT TO: jacopeland 3@comcast. net [must not violate any anti-relay rule] << 250 2. 1. 5 jacopeland 3@comcast. net. . . Recipient ok [this would be relaying, except for VPN] >> DATA << 354 Enter mail, end with ". " on a line by itself >> 'hw 1/hw 1. graded on * * Sep 28, 2005 16: 49, # = 13 Explanation at bottom. ' >> 'Name on HW return: smith, _john' >> 'Date & Time submitted: Wed, 28 Sep 2005 03: 45: 36 -0400 (EDT)' >> '-Email: gte 014 w@prism. gatech. edu (at line 2) : Break the following ciphertext: ' >> ' #1' >> '1 ok 2 /N=N/ : [n] - Which cipher character' >> '2 ok 2 /THIS_CODE_IS_W=THIS_CODE_IS_W/ : [this_code_is_w] - type in the' >> 'No. Graded = 10, Average Grade = 92' >>. [ends message text] << 250 2. 0. 0 j 8 SLYi. LA 000789 Message accepted for delivery >> QUIT 10
Email sent with: % telnet mail. ece. gatech. edu 25 >> YOU TYPE THIS. << WAIT FOR THIS REPLY FROM THE SMTP SERVER [COMMENTS] >> HELO c-66 -53 -58 -172. hsd 1. ga. comcast. net [must be actual DNS name of host being used] << 220 mail. ece. gatech. edu ESMTP Sendmail 8. 12. 10/8. 13. 4; Wed, 28 Sep 2005 17: 34: 44 -0400 (EDT) << 250 mail. ece. gatech. edu Hello ecevpn-021. ece-int. gatech. edu [192. 168. 66. 21], pleased to meet you >> MAIL FROM: copeland@ece. gatech. edu [must be an actual user on this server] << 250 2. 1. 0 copeland@ece. gatech. edu. . . Sender ok >> RCPT TO: jacopeland 3@comcast. net [must not violate any anti-relay rule] << 250 2. 1. 5 jacopeland 3@comcast. net. . . Recipient ok [this would be relaying, except for VPN] >> DATA << 354 Enter mail, end with ". " on a line by itself >> 'hw 1/hw 1. graded on * * Sep 28, 2005 16: 49, # = 13 Explanation at bottom. ' >> 'Name on HW return: smith, _john' >> 'Date & Time submitted: Wed, 28 Sep 2005 03: 45: 36 -0400 (EDT)' >> '-Email: gte 014 w@prism. gatech. edu (at line 2) : Break the following ciphertext: ' >> ' #1' >> '1 ok 2 /N=N/ : [n] - Which cipher character' >> '2 ok 2 /THIS_CODE_IS_W=THIS_CODE_IS_W/ : [this_code_is_w] - type in the' >> 'No. Graded = 10, Average Grade = 92' >>. [ends message text] << 250 2. 0. 0 j 8 SLYi. LA 000789 Message accepted for delivery >> QUIT 10
![Received: from gatech. edu (gatech. edu [130. 207. 244]) by mail. ee. gatech. edu Received: from gatech. edu (gatech. edu [130. 207. 244]) by mail. ee. gatech. edu](https://present5.com/presentation/119d5be7514758164b20b6a810c2c83d/image-11.jpg) Received: from gatech. edu (gatech. edu [130. 207. 244]) by mail. ee. gatech. edu (8. 12. 9/8. 12. 9) with ESMTP id h 7 JMHl. Yk 014613 for
Received: from gatech. edu (gatech. edu [130. 207. 244]) by mail. ee. gatech. edu (8. 12. 9/8. 12. 9) with ESMTP id h 7 JMHl. Yk 014613 for
 Return-Path:
Return-Path:
![# nslookup 22. 239. 60. 151 [IP address from “Rcvd: ” header] *** eeserv. # nslookup 22. 239. 60. 151 [IP address from “Rcvd: ” header] *** eeserv.](https://present5.com/presentation/119d5be7514758164b20b6a810c2c83d/image-13.jpg) # nslookup 22. 239. 60. 151 [IP address from “Rcvd: ” header] *** eeserv. ee. gatech. edu can't find 22. 239. 60. 151: Non-existent host/domain [from www. geektools. com] Final results for 22. 239. 201. 237 obtained from whois. arin. net. Org. Name: Do. D Network Information Center Org. ID: DNIC Address: 7990 Science Applications Ct Address: M/S CV 50 City: Vienna State. Prov: VA [false email source address] ------------------------------------# nslookup www. broadcastemailing. com [from content] Name: www. broadcastemailing. com Address: 202. 63. 201. 237 inetnum: 202. 63. 192. 0 - 202. 63. 223. 255 descr: Cube. XS Private Limited descr: Internet Service Provider descr: Data Entry descr: Software House descr: 310 -311 Kassam Court descr: B. C. 9, Block 5, Clifton descr: Karachi, Pakistan [actual Web location] 13
# nslookup 22. 239. 60. 151 [IP address from “Rcvd: ” header] *** eeserv. ee. gatech. edu can't find 22. 239. 60. 151: Non-existent host/domain [from www. geektools. com] Final results for 22. 239. 201. 237 obtained from whois. arin. net. Org. Name: Do. D Network Information Center Org. ID: DNIC Address: 7990 Science Applications Ct Address: M/S CV 50 City: Vienna State. Prov: VA [false email source address] ------------------------------------# nslookup www. broadcastemailing. com [from content] Name: www. broadcastemailing. com Address: 202. 63. 201. 237 inetnum: 202. 63. 192. 0 - 202. 63. 223. 255 descr: Cube. XS Private Limited descr: Internet Service Provider descr: Data Entry descr: Software House descr: 310 -311 Kassam Court descr: B. C. 9, Block 5, Clifton descr: Karachi, Pakistan [actual Web location] 13
To: "Jacom"
 Note the lack of the “Padlock” symbol. HTTPS (TLS) is not being used because they have no X 509 certificate. Look at Page Source Code - check links: (note directory named “scam”)
Note the lack of the “Padlock” symbol. HTTPS (TLS) is not being used because they have no X 509 certificate. Look at Page Source Code - check links: (note directory named “scam”)
HOME | ACCOUNTS | PAYMENTS & TRANSFERS | INVESTMENTS | ACCOUNT SERVICING
 whois. apnic. net. Results: % Whois data copyright terms http: //www. apnic. net/db/dbcopyright. html inetnum: 219. 138. 0. 0 - 219. 140. 255 netname: CHINANET-HB descr: CHINANET hubei province network descr: China Telecom descr: A 12, Xin-Jie-Kou-Wai Street descr: Beijing 100088 country: CN admin-c: CH 93 -AP tech-c: CHA 1 -AP mnt-by: MAINT-CHINANET mnt-lower: MAINT-CN-CHINANET-HB changed: hostmaster@ns. chinanet. cn. net 20020521 status: ALLOCATED NON-PORTABLE source: APNIC role: CHINANET HB ADMIN address: 8 th floor of Jin. Guang Building address: #232 of Macao Road address: Han. Kou Wuhan Hubei Province address: P. R. China country: CN phone: +86 27 82862199 fax-no: +86 27 82861499 e-mail: ip_admin_hb@public. wh. hb. cn trouble: send spam reports to spam_hb@public. wh. hb. cn trouble: and abuse reports to abuse_hb@public. wh. hb. cn trouble: Please include detailed information and trouble: times in GMT+8
whois. apnic. net. Results: % Whois data copyright terms http: //www. apnic. net/db/dbcopyright. html inetnum: 219. 138. 0. 0 - 219. 140. 255 netname: CHINANET-HB descr: CHINANET hubei province network descr: China Telecom descr: A 12, Xin-Jie-Kou-Wai Street descr: Beijing 100088 country: CN admin-c: CH 93 -AP tech-c: CHA 1 -AP mnt-by: MAINT-CHINANET mnt-lower: MAINT-CN-CHINANET-HB changed: hostmaster@ns. chinanet. cn. net 20020521 status: ALLOCATED NON-PORTABLE source: APNIC role: CHINANET HB ADMIN address: 8 th floor of Jin. Guang Building address: #232 of Macao Road address: Han. Kou Wuhan Hubei Province address: P. R. China country: CN phone: +86 27 82862199 fax-no: +86 27 82861499 e-mail: ip_admin_hb@public. wh. hb. cn trouble: send spam reports to spam_hb@public. wh. hb. cn trouble: and abuse reports to abuse_hb@public. wh. hb. cn trouble: Please include detailed information and trouble: times in GMT+8
![Received: from capitalgroup. ru ([221. 192. 242. 56]) Date: Wed, 22 Sep 2004 15: Received: from capitalgroup. ru ([221. 192. 242. 56]) Date: Wed, 22 Sep 2004 15:](https://present5.com/presentation/119d5be7514758164b20b6a810c2c83d/image-17.jpg) Received: from capitalgroup. ru ([221. 192. 242. 56]) Date: Wed, 22 Sep 2004 15: 01: 44 +0000 To: jacopeland 3@mindspring. com From: "Lillie Haywood"
Received: from capitalgroup. ru ([221. 192. 242. 56]) Date: Wed, 22 Sep 2004 15: 01: 44 +0000 To: jacopeland 3@mindspring. com From: "Lillie Haywood" Notice that the serial code “ 02025” or system “TNIKHMCY” could be codes which may validate your IP address. The random words in the text are to get past a Basian spam filter. They could not actually “scan” my Macintosh computer, which has no spyware.
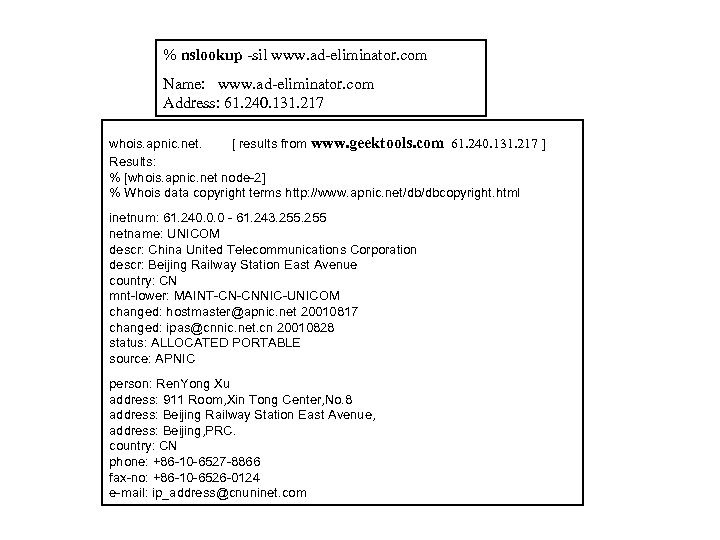 % nslookup -sil www. ad-eliminator. com Name: www. ad-eliminator. com Address: 61. 240. 131. 217 whois. apnic. net. [ results from www. geektools. com 61. 240. 131. 217 ] Results: % [whois. apnic. net node-2] % Whois data copyright terms http: //www. apnic. net/db/dbcopyright. html inetnum: 61. 240. 0. 0 - 61. 243. 255 netname: UNICOM descr: China United Telecommunications Corporation descr: Beijing Railway Station East Avenue country: CN mnt-lower: MAINT-CN-CNNIC-UNICOM changed: hostmaster@apnic. net 20010817 changed: ipas@cnnic. net. cn 20010828 status: ALLOCATED PORTABLE source: APNIC person: Ren. Yong Xu address: 911 Room, Xin Tong Center, No. 8 address: Beijing Railway Station East Avenue, address: Beijing, PRC. country: CN phone: +86 -10 -6527 -8866 fax-no: +86 -10 -6526 -0124 e-mail: ip_address@cnuninet. com
% nslookup -sil www. ad-eliminator. com Name: www. ad-eliminator. com Address: 61. 240. 131. 217 whois. apnic. net. [ results from www. geektools. com 61. 240. 131. 217 ] Results: % [whois. apnic. net node-2] % Whois data copyright terms http: //www. apnic. net/db/dbcopyright. html inetnum: 61. 240. 0. 0 - 61. 243. 255 netname: UNICOM descr: China United Telecommunications Corporation descr: Beijing Railway Station East Avenue country: CN mnt-lower: MAINT-CN-CNNIC-UNICOM changed: hostmaster@apnic. net 20010817 changed: ipas@cnnic. net. cn 20010828 status: ALLOCATED PORTABLE source: APNIC person: Ren. Yong Xu address: 911 Room, Xin Tong Center, No. 8 address: Beijing Railway Station East Avenue, address: Beijing, PRC. country: CN phone: +86 -10 -6527 -8866 fax-no: +86 -10 -6526 -0124 e-mail: ip_address@cnuninet. com
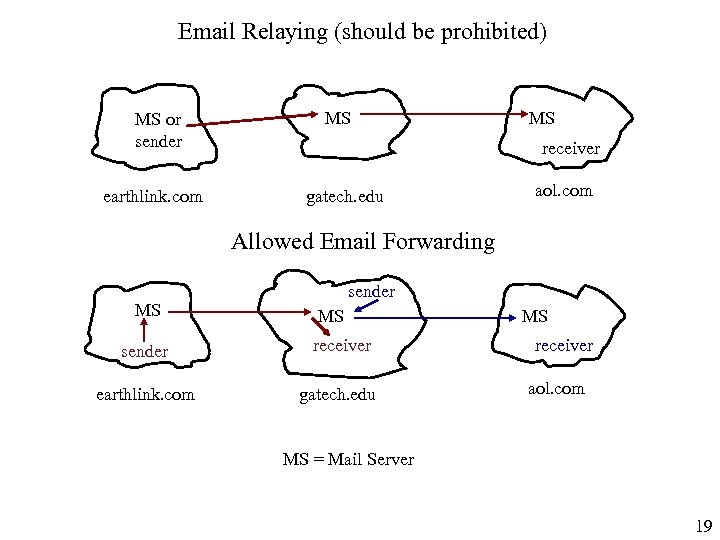 Email Relaying (should be prohibited) MS or sender earthlink. com MS MS receiver gatech. edu aol. com Allowed Email Forwarding MS sender receiver earthlink. com gatech. edu MS receiver aol. com MS = Mail Server 19
Email Relaying (should be prohibited) MS or sender earthlink. com MS MS receiver gatech. edu aol. com Allowed Email Forwarding MS sender receiver earthlink. com gatech. edu MS receiver aol. com MS = Mail Server 19
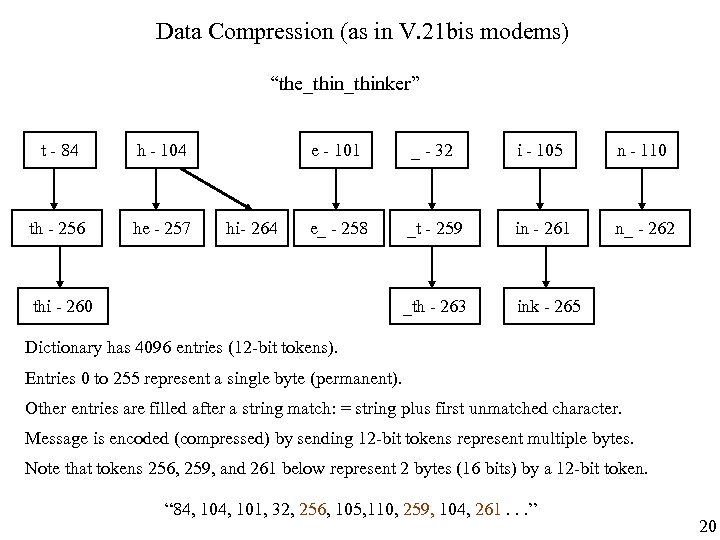 Data Compression (as in V. 21 bis modems) “the_thinker” t - 84 h - 104 th - 256 he - 257 e - 101 i - 105 n - 110 e_ - 258 _t - 259 in - 261 n_ - 262 _th - 263 hi- 264 _ - 32 ink - 265 thi - 260 Dictionary has 4096 entries (12 -bit tokens). Entries 0 to 255 represent a single byte (permanent). Other entries are filled after a string match: = string plus first unmatched character. Message is encoded (compressed) by sending 12 -bit tokens represent multiple bytes. Note that tokens 256, 259, and 261 below represent 2 bytes (16 bits) by a 12 -bit token. “ 84, 101, 32, 256, 105, 110, 259, 104, 261. . . ” 20
Data Compression (as in V. 21 bis modems) “the_thinker” t - 84 h - 104 th - 256 he - 257 e - 101 i - 105 n - 110 e_ - 258 _t - 259 in - 261 n_ - 262 _th - 263 hi- 264 _ - 32 ink - 265 thi - 260 Dictionary has 4096 entries (12 -bit tokens). Entries 0 to 255 represent a single byte (permanent). Other entries are filled after a string match: = string plus first unmatched character. Message is encoded (compressed) by sending 12 -bit tokens represent multiple bytes. Note that tokens 256, 259, and 261 below represent 2 bytes (16 bits) by a 12 -bit token. “ 84, 101, 32, 256, 105, 110, 259, 104, 261. . . ” 20
 Security Wire Perspectives, Sept 20, 2004 In fact, of the targeted attacks Symantec detected in the last six months, the majority were against e-commerce companies, including financial institutions. Small business received the second highest number of attacks. "We're no longer talking strictly about the male teenager with the low moral compass, or the hactivist, who defaces sites or uses malicious code or worms against those on one side in a political conflict, " said Vincent Weaver, senior director of Symantec Security Response. "These people are targeting e-commerce, and they are often backed by organized crime. ” The average time period between the disclosure of a vulnerability and its first exploit by hackers collapsed from several weeks in past reports to less than six days in the first half of 2004.
Security Wire Perspectives, Sept 20, 2004 In fact, of the targeted attacks Symantec detected in the last six months, the majority were against e-commerce companies, including financial institutions. Small business received the second highest number of attacks. "We're no longer talking strictly about the male teenager with the low moral compass, or the hactivist, who defaces sites or uses malicious code or worms against those on one side in a political conflict, " said Vincent Weaver, senior director of Symantec Security Response. "These people are targeting e-commerce, and they are often backed by organized crime. ” The average time period between the disclosure of a vulnerability and its first exploit by hackers collapsed from several weeks in past reports to less than six days in the first half of 2004.


