28d5ac13b37b920ad3ab0f4517c01105.ppt
- Количество слайдов: 36
 http: //egee. hu/grid 05/index. php? m=3 Introduction to EGEE and EGEE security Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 1
http: //egee. hu/grid 05/index. php? m=3 Introduction to EGEE and EGEE security Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 1
 Introdution to EGEE and Security Norbert Podhorszki MTA SZTAKI EGEE is funded by the European Union under contract IST-2003 -508833 Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 2
Introdution to EGEE and Security Norbert Podhorszki MTA SZTAKI EGEE is funded by the European Union under contract IST-2003 -508833 Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 2
 Acknowledgement • This tutorial is based on the work of many people: • • • Fabrizio Gagliardi, Flavia Donno and Peter Kunszt (CERN) the EDG developer team the EDG training team the Ne. SC training team the SZTAKI training team Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 3
Acknowledgement • This tutorial is based on the work of many people: • • • Fabrizio Gagliardi, Flavia Donno and Peter Kunszt (CERN) the EDG developer team the EDG training team the Ne. SC training team the SZTAKI training team Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 3
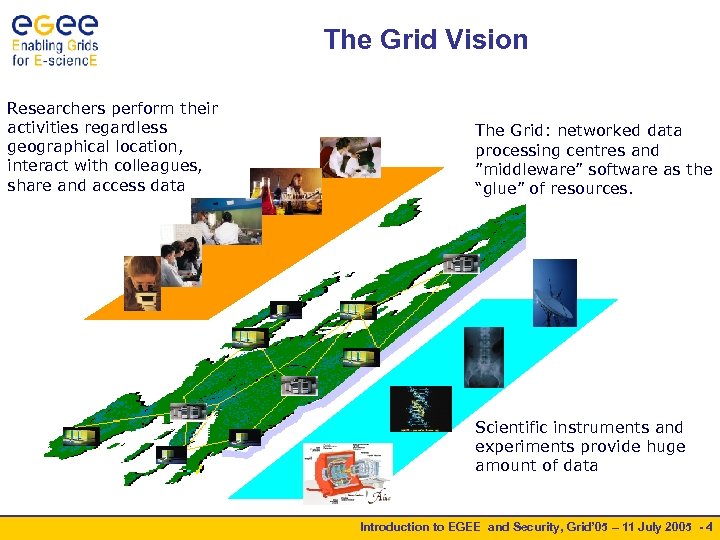 The Grid Vision Researchers perform their activities regardless geographical location, interact with colleagues, share and access data The Grid: networked data processing centres and ”middleware” software as the “glue” of resources. Scientific instruments and experiments provide huge amount of data Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 4
The Grid Vision Researchers perform their activities regardless geographical location, interact with colleagues, share and access data The Grid: networked data processing centres and ”middleware” software as the “glue” of resources. Scientific instruments and experiments provide huge amount of data Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 4
 What do we expect from the Grid? • Access to a world-wide virtual computing laboratory with almost infinite resources • Possibility to organize distributed scientific communities in VOs • Transparent access to distributed data and easy workload management • Easy to use application interfaces Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 5
What do we expect from the Grid? • Access to a world-wide virtual computing laboratory with almost infinite resources • Possibility to organize distributed scientific communities in VOs • Transparent access to distributed data and easy workload management • Easy to use application interfaces Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 5
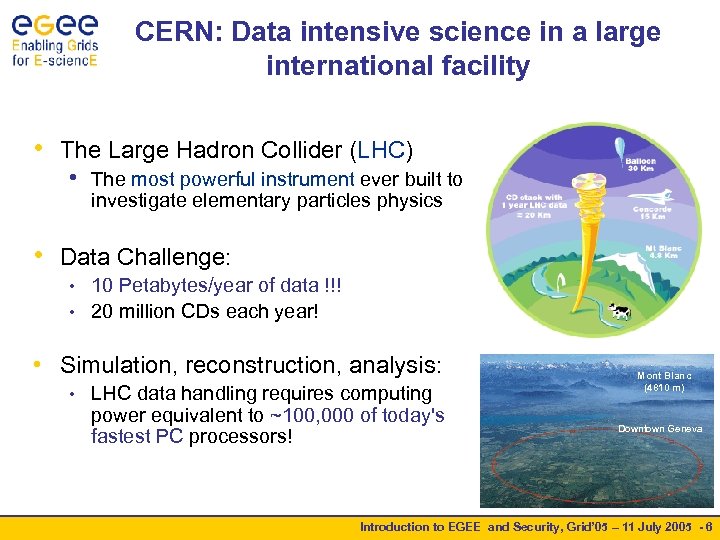 CERN: Data intensive science in a large international facility • The Large Hadron Collider (LHC) • The most powerful instrument ever built to investigate elementary particles physics • Data Challenge: 10 Petabytes/year of data !!! • 20 million CDs each year! • • Simulation, reconstruction, analysis: • LHC data handling requires computing power equivalent to ~100, 000 of today's fastest PC processors! Mont Blanc (4810 m) Downtown Geneva Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 6
CERN: Data intensive science in a large international facility • The Large Hadron Collider (LHC) • The most powerful instrument ever built to investigate elementary particles physics • Data Challenge: 10 Petabytes/year of data !!! • 20 million CDs each year! • • Simulation, reconstruction, analysis: • LHC data handling requires computing power equivalent to ~100, 000 of today's fastest PC processors! Mont Blanc (4810 m) Downtown Geneva Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 6
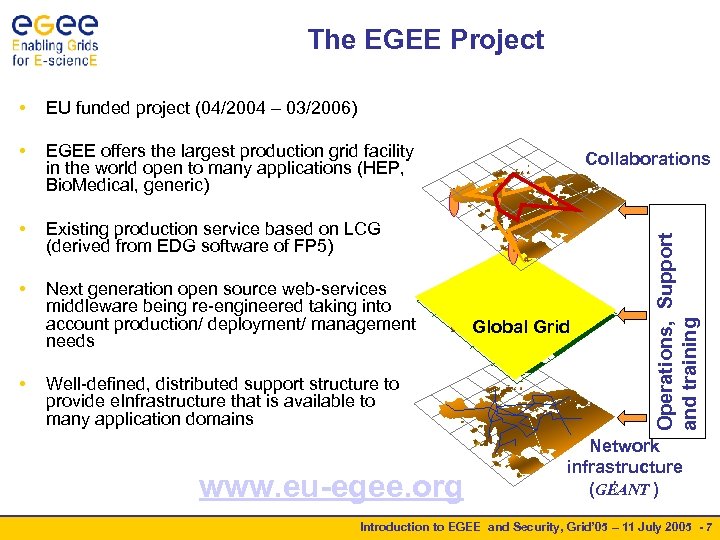 The EGEE Project EU funded project (04/2004 – 03/2006) • EGEE offers the largest production grid facility in the world open to many applications (HEP, Bio. Medical, generic) • Existing production service based on LCG (derived from EDG software of FP 5) • Next generation open source web-services middleware being re-engineered taking into account production/ deployment/ management needs • Well-defined, distributed support structure to provide e. Infrastructure that is available to many application domains www. eu-egee. org Collaborations Global Grid Operations, Support and training • Network infrastructure (GÉANT ) Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 7
The EGEE Project EU funded project (04/2004 – 03/2006) • EGEE offers the largest production grid facility in the world open to many applications (HEP, Bio. Medical, generic) • Existing production service based on LCG (derived from EDG software of FP 5) • Next generation open source web-services middleware being re-engineered taking into account production/ deployment/ management needs • Well-defined, distributed support structure to provide e. Infrastructure that is available to many application domains www. eu-egee. org Collaborations Global Grid Operations, Support and training • Network infrastructure (GÉANT ) Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 7
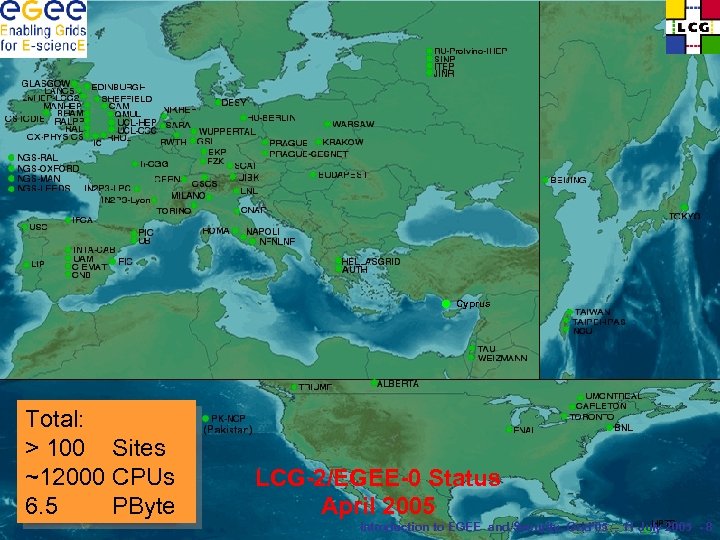 Cyprus Total: > 100 Sites ~12000 CPUs 6. 5 PByte LCG-2/EGEE-0 Status April 2005 Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 8
Cyprus Total: > 100 Sites ~12000 CPUs 6. 5 PByte LCG-2/EGEE-0 Status April 2005 Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 8
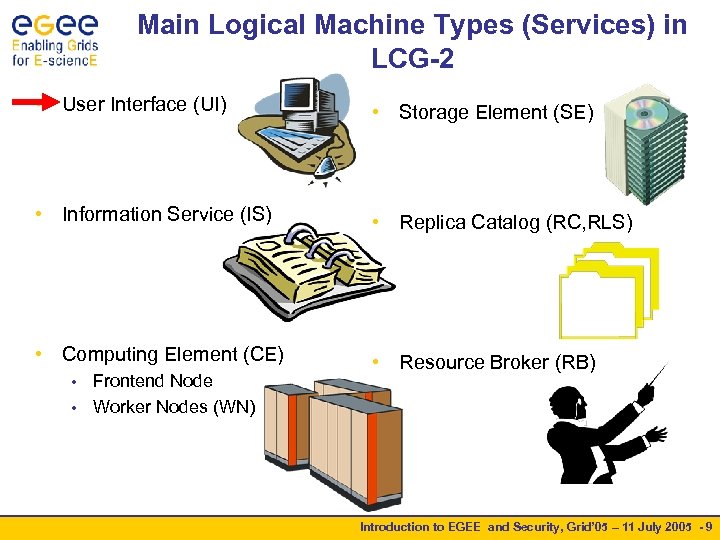 Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 9
Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 9
 User Interface • The initial point of access to the LCG-2 Grid is the User Interface • This is a machine where LCG users have a personal account • The user’s certificate is installed • • The UI is the gateway to Grid services • It provides a Command Line Interface to perform the following basic Grid operations: • • • list all the resources suitable to execute a given job; replicate and copy files; submit a job for execution on a Computing Element; show the status of one or more submitted jobs. retrieve the output of one or more finished jobs; cancel one or more jobs; • One or more UIs are available at each site part of the LCG-2 Grid Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 10
User Interface • The initial point of access to the LCG-2 Grid is the User Interface • This is a machine where LCG users have a personal account • The user’s certificate is installed • • The UI is the gateway to Grid services • It provides a Command Line Interface to perform the following basic Grid operations: • • • list all the resources suitable to execute a given job; replicate and copy files; submit a job for execution on a Computing Element; show the status of one or more submitted jobs. retrieve the output of one or more finished jobs; cancel one or more jobs; • One or more UIs are available at each site part of the LCG-2 Grid Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 10
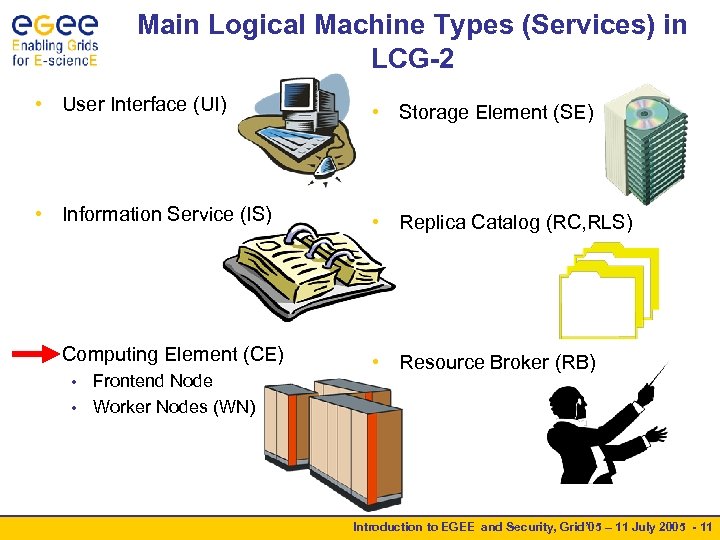 Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 11
Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 11
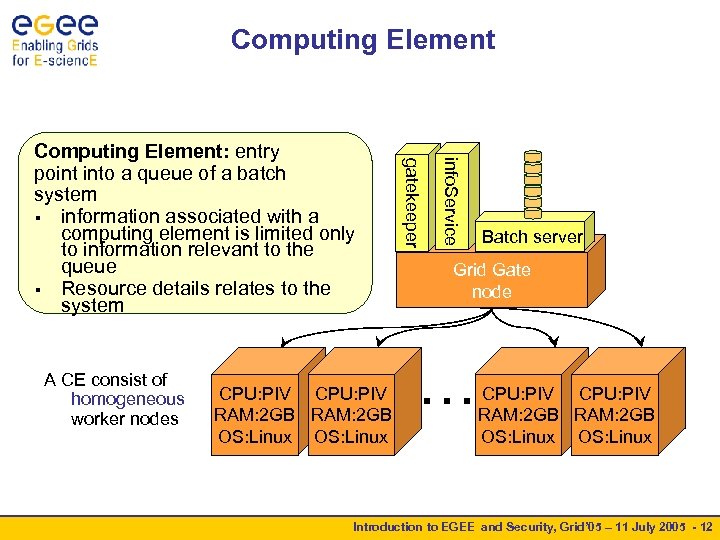 Computing Element CPU: PIV RAM: 2 GB OS: Linux info. Service A CE consist of homogeneous worker nodes gatekeeper Computing Element: entry point into a queue of a batch system § information associated with a computing element is limited only to information relevant to the queue § Resource details relates to the system Batch server Grid Gate node … CPU: PIV RAM: 2 GB OS: Linux Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 12
Computing Element CPU: PIV RAM: 2 GB OS: Linux info. Service A CE consist of homogeneous worker nodes gatekeeper Computing Element: entry point into a queue of a batch system § information associated with a computing element is limited only to information relevant to the queue § Resource details relates to the system Batch server Grid Gate node … CPU: PIV RAM: 2 GB OS: Linux Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 12
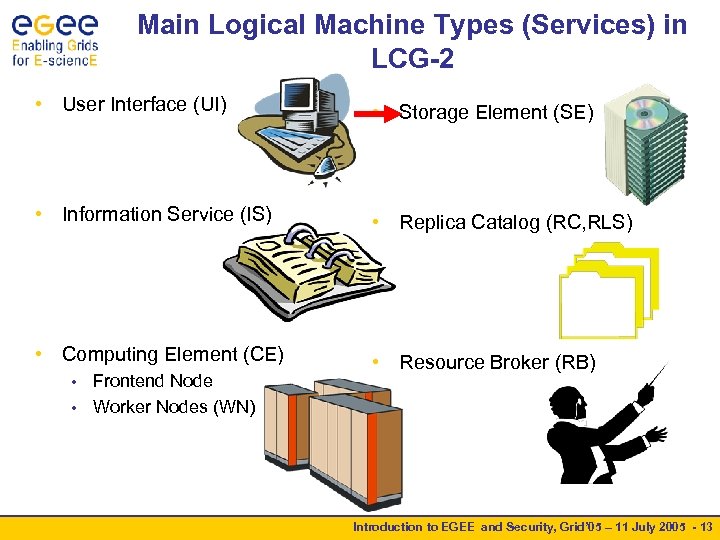 Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 13
Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 13
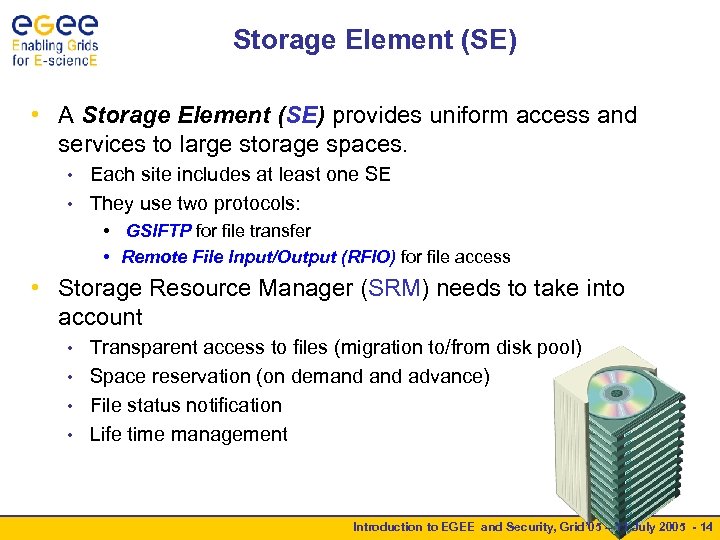 Storage Element (SE) • A Storage Element (SE) provides uniform access and services to large storage spaces. Each site includes at least one SE • They use two protocols: • • GSIFTP for file transfer • Remote File Input/Output (RFIO) for file access • Storage Resource Manager (SRM) needs to take into account Transparent access to files (migration to/from disk pool) • Space reservation (on demand advance) • File status notification • Life time management • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 14
Storage Element (SE) • A Storage Element (SE) provides uniform access and services to large storage spaces. Each site includes at least one SE • They use two protocols: • • GSIFTP for file transfer • Remote File Input/Output (RFIO) for file access • Storage Resource Manager (SRM) needs to take into account Transparent access to files (migration to/from disk pool) • Space reservation (on demand advance) • File status notification • Life time management • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 14
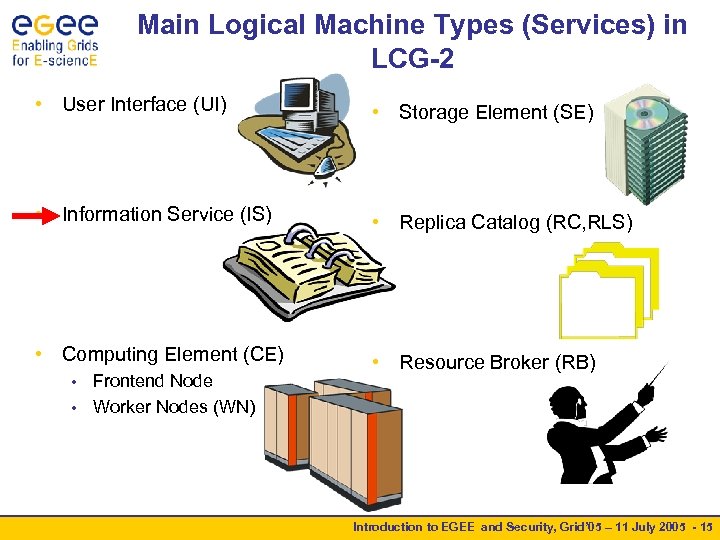 Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 15
Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 15
 Information System (IS) • The Information System (IS) provides information about the LCG -2 Grid resources and their status • The current IS is based on LDAP (Lightweight Directory Access Protocol): a directory service infrastructure which is a specialized database optimized for reading, • browsing and • searching information. • • the LDAP schema used in LCG-2 implements the GLUE (Grid Laboratory for a Uniform Environment) Schema Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 16
Information System (IS) • The Information System (IS) provides information about the LCG -2 Grid resources and their status • The current IS is based on LDAP (Lightweight Directory Access Protocol): a directory service infrastructure which is a specialized database optimized for reading, • browsing and • searching information. • • the LDAP schema used in LCG-2 implements the GLUE (Grid Laboratory for a Uniform Environment) Schema Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 16
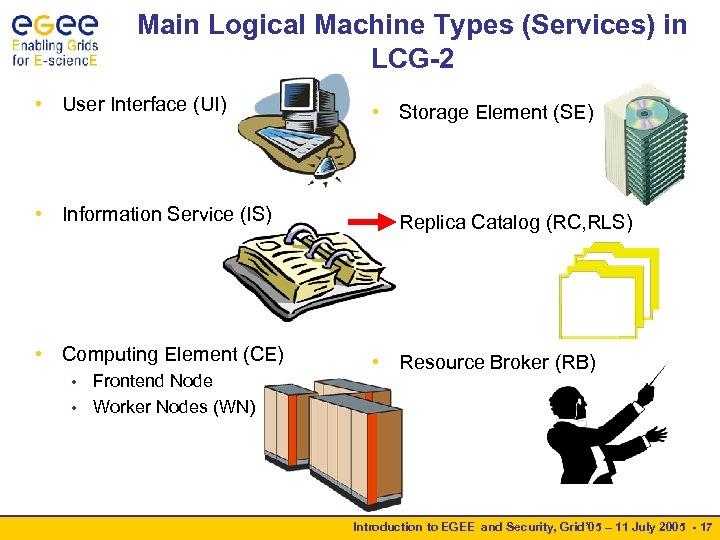 Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 17
Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 17
 Data Management • In LCG, the data files are replicated: on a temporary basis, • to many different sites depending on • where the data is needed. • • The users or applications do not need to know where the data is located, they use logical files names • the Data Management services are responsible for locating and accessing the data. Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 18
Data Management • In LCG, the data files are replicated: on a temporary basis, • to many different sites depending on • where the data is needed. • • The users or applications do not need to know where the data is located, they use logical files names • the Data Management services are responsible for locating and accessing the data. Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 18
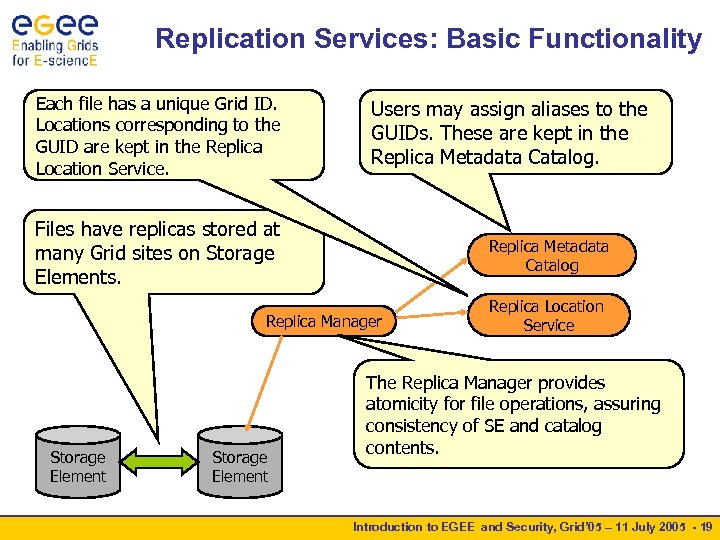 Replication Services: Basic Functionality Each file has a unique Grid ID. Locations corresponding to the GUID are kept in the Replica Location Service. Users may assign aliases to the GUIDs. These are kept in the Replica Metadata Catalog. Files have replicas stored at many Grid sites on Storage Elements. Replica Metadata Catalog Replica Manager Storage Element Replica Location Service The Replica Manager provides atomicity for file operations, assuring consistency of SE and catalog contents. Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 19
Replication Services: Basic Functionality Each file has a unique Grid ID. Locations corresponding to the GUID are kept in the Replica Location Service. Users may assign aliases to the GUIDs. These are kept in the Replica Metadata Catalog. Files have replicas stored at many Grid sites on Storage Elements. Replica Metadata Catalog Replica Manager Storage Element Replica Location Service The Replica Manager provides atomicity for file operations, assuring consistency of SE and catalog contents. Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 19
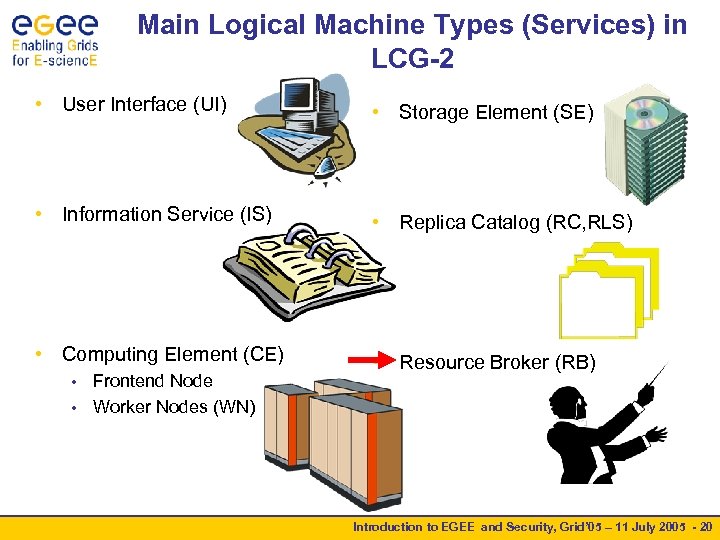 Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 20
Main Logical Machine Types (Services) in LCG-2 • User Interface (UI) • Storage Element (SE) • Information Service (IS) • Replica Catalog (RC, RLS) • Computing Element (CE) • Resource Broker (RB) Frontend Node • Worker Nodes (WN) • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 20
 Job Management • The user interacts with Grid via a Workload Management System (WMS) • The Goal of WMS is the distributed scheduling and resource management in a Grid environment. • What does it allow Grid users to do? To submit their jobs • To execute them on the “best resources” • • The WMS tries to optimize the usage of resources To get information about their status • To retrieve their output • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 21
Job Management • The user interacts with Grid via a Workload Management System (WMS) • The Goal of WMS is the distributed scheduling and resource management in a Grid environment. • What does it allow Grid users to do? To submit their jobs • To execute them on the “best resources” • • The WMS tries to optimize the usage of resources To get information about their status • To retrieve their output • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 21
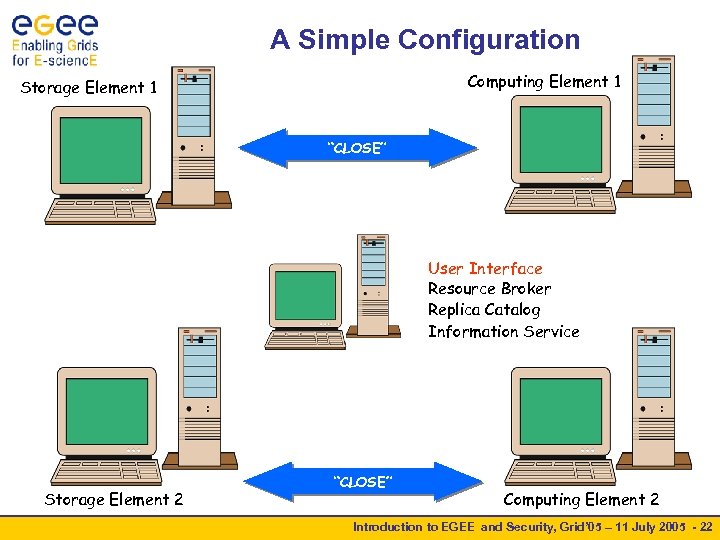 A Simple Configuration Computing Element 1 Storage Element 1 “CLOSE” User Interface Resource Broker Replica Catalog Information Service Storage Element 2 “CLOSE” Computing Element 2 Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 22
A Simple Configuration Computing Element 1 Storage Element 1 “CLOSE” User Interface Resource Broker Replica Catalog Information Service Storage Element 2 “CLOSE” Computing Element 2 Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 22
 Security Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 23
Security Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 23
 Introduction to Security What aspects of security should we be concerned about? • Authentication (Identification) • Confidentiality (Privacy) • Integrity (non-Tampering) • Authorisation Also • Accounting • Delegation • Non-Repudiation Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 24
Introduction to Security What aspects of security should we be concerned about? • Authentication (Identification) • Confidentiality (Privacy) • Integrity (non-Tampering) • Authorisation Also • Accounting • Delegation • Non-Repudiation Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 24
 How do I login on the Grid ? • Distribution of resources: secure access is a basic requirement secure communication • security across organisational boundaries • single “sign-on" for users of the Grid • • Two basic concepts: • Authentication: Who am I? • “Equivalent” to a pass port, ID card etc. • Authorisation: What can I do? • Certain permissions, duties etc. Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 25
How do I login on the Grid ? • Distribution of resources: secure access is a basic requirement secure communication • security across organisational boundaries • single “sign-on" for users of the Grid • • Two basic concepts: • Authentication: Who am I? • “Equivalent” to a pass port, ID card etc. • Authorisation: What can I do? • Certain permissions, duties etc. Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 25
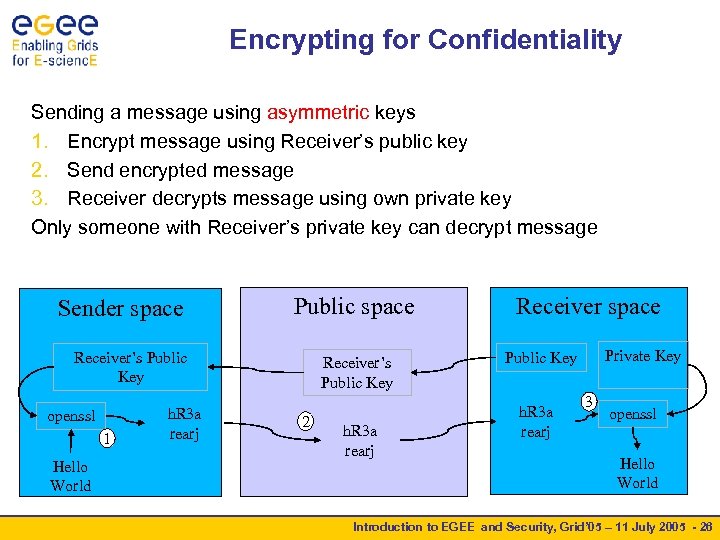 Encrypting for Confidentiality Sending a message using asymmetric keys 1. Encrypt message using Receiver’s public key 2. Send encrypted message 3. Receiver decrypts message using own private key Only someone with Receiver’s private key can decrypt message Sender space Public space Receiver’s Public Key openssl 1 Hello World h. R 3 a rearj Receiver’s Public Key 2 h. R 3 a rearj Receiver space Private Key Public Key h. R 3 a rearj 3 openssl Hello World Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 26
Encrypting for Confidentiality Sending a message using asymmetric keys 1. Encrypt message using Receiver’s public key 2. Send encrypted message 3. Receiver decrypts message using own private key Only someone with Receiver’s private key can decrypt message Sender space Public space Receiver’s Public Key openssl 1 Hello World h. R 3 a rearj Receiver’s Public Key 2 h. R 3 a rearj Receiver space Private Key Public Key h. R 3 a rearj 3 openssl Hello World Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 26
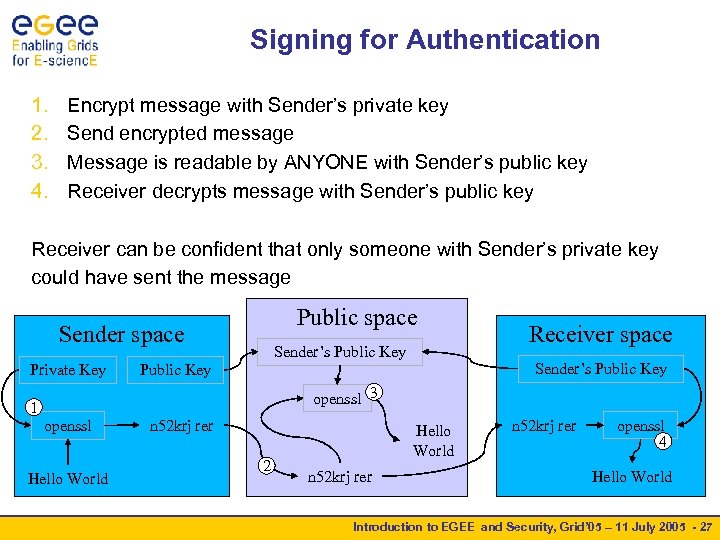 Signing for Authentication 1. 2. 3. 4. Encrypt message with Sender’s private key Send encrypted message Message is readable by ANYONE with Sender’s public key Receiver decrypts message with Sender’s public key Receiver can be confident that only someone with Sender’s private key could have sent the message Public space Sender space Private Key Sender’s Public Key Receiver space Sender’s Public Key openssl 3 1 openssl Hello World n 52 krj rer 2 Hello World n 52 krj rer openssl 4 Hello World Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 27
Signing for Authentication 1. 2. 3. 4. Encrypt message with Sender’s private key Send encrypted message Message is readable by ANYONE with Sender’s public key Receiver decrypts message with Sender’s public key Receiver can be confident that only someone with Sender’s private key could have sent the message Public space Sender space Private Key Sender’s Public Key Receiver space Sender’s Public Key openssl 3 1 openssl Hello World n 52 krj rer 2 Hello World n 52 krj rer openssl 4 Hello World Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 27
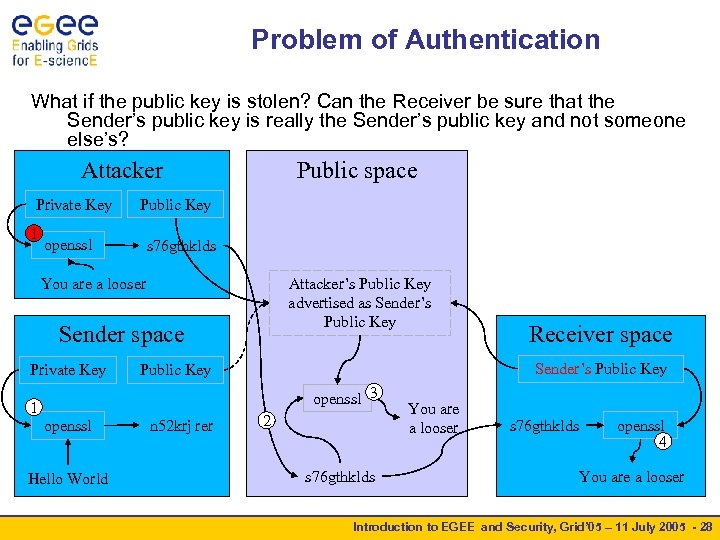 Problem of Authentication What if the public key is stolen? Can the Receiver be sure that the Sender’s public key is really the Sender’s public key and not someone else’s? Attacker Private Key 1 Public space Public Key openssl s 76 gthklds You are a looser Attacker’s Public Key advertised as Sender’s Public Key Sender space Private Key Sender’s Public Key openssl 3 1 openssl Hello World n 52 krj rer Receiver space 2 s 76 gthklds You are a looser s 76 gthklds openssl 4 You are a looser Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 28
Problem of Authentication What if the public key is stolen? Can the Receiver be sure that the Sender’s public key is really the Sender’s public key and not someone else’s? Attacker Private Key 1 Public space Public Key openssl s 76 gthklds You are a looser Attacker’s Public Key advertised as Sender’s Public Key Sender space Private Key Sender’s Public Key openssl 3 1 openssl Hello World n 52 krj rer Receiver space 2 s 76 gthklds You are a looser s 76 gthklds openssl 4 You are a looser Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 28
 Digital Certificates • How can B be sure that A’s public key is really A’s public key and not someone else’s? ● ● A third party guarantees the correspondence between public key and owner’s identity, by signing a document which contains the owner’s identity and his public key (Digital Certificate) Both A and B must trust this third party • Two models: ● X. 509: hierarchical organization; ● PGP: “web of trust”. Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 29
Digital Certificates • How can B be sure that A’s public key is really A’s public key and not someone else’s? ● ● A third party guarantees the correspondence between public key and owner’s identity, by signing a document which contains the owner’s identity and his public key (Digital Certificate) Both A and B must trust this third party • Two models: ● X. 509: hierarchical organization; ● PGP: “web of trust”. Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 29
 Certificate contents • The certificate that you present to others contains: • Your distinguished name (DN) • your identifier • Your public key • anyone can send a secret message to you • The identity of the CA who issued the certificate • just a name • Its expiry date • the certificate’s expiry date (usually issued for one year) • Digital signature of the CA which issued it • the certificate encrypted with the CA’s private key Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 30
Certificate contents • The certificate that you present to others contains: • Your distinguished name (DN) • your identifier • Your public key • anyone can send a secret message to you • The identity of the CA who issued the certificate • just a name • Its expiry date • the certificate’s expiry date (usually issued for one year) • Digital signature of the CA which issued it • the certificate encrypted with the CA’s private key Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 30
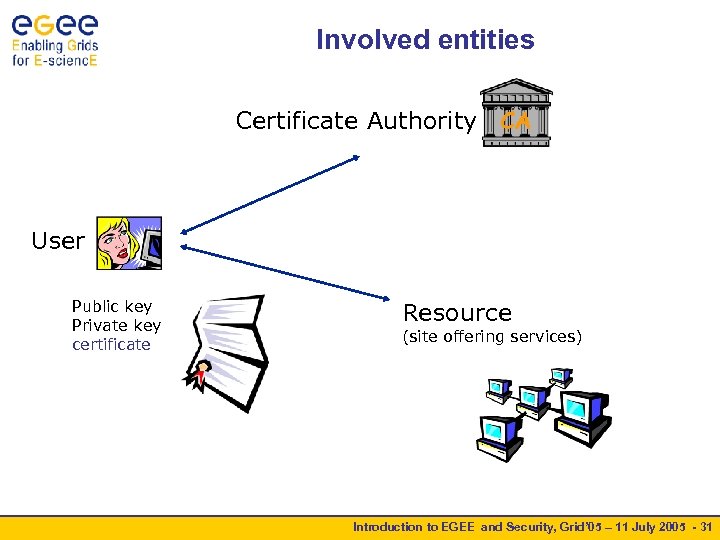 Involved entities Certificate Authority CA User Public key Private key certificate Resource (site offering services) Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 31
Involved entities Certificate Authority CA User Public key Private key certificate Resource (site offering services) Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 31
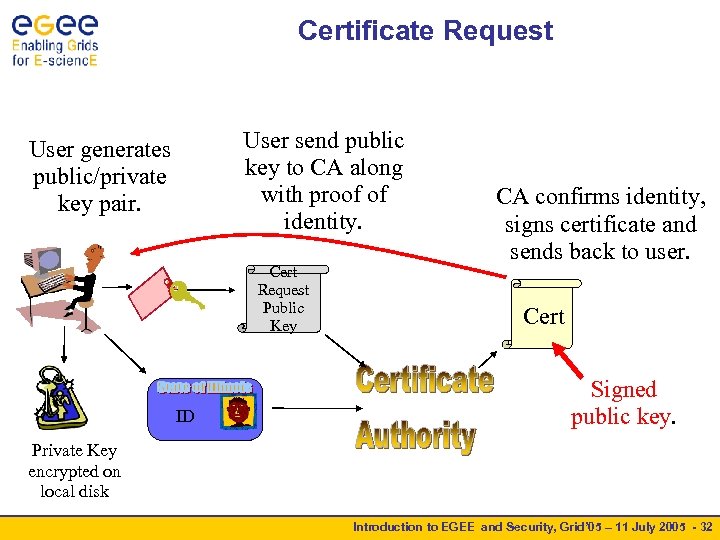 Certificate Request User send public key to CA along with proof of identity. User generates public/private key pair. Cert Request Public Key ID CA confirms identity, signs certificate and sends back to user. Cert Signed public key. Private Key encrypted on local disk Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 32
Certificate Request User send public key to CA along with proof of identity. User generates public/private key pair. Cert Request Public Key ID CA confirms identity, signs certificate and sends back to user. Cert Signed public key. Private Key encrypted on local disk Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 32
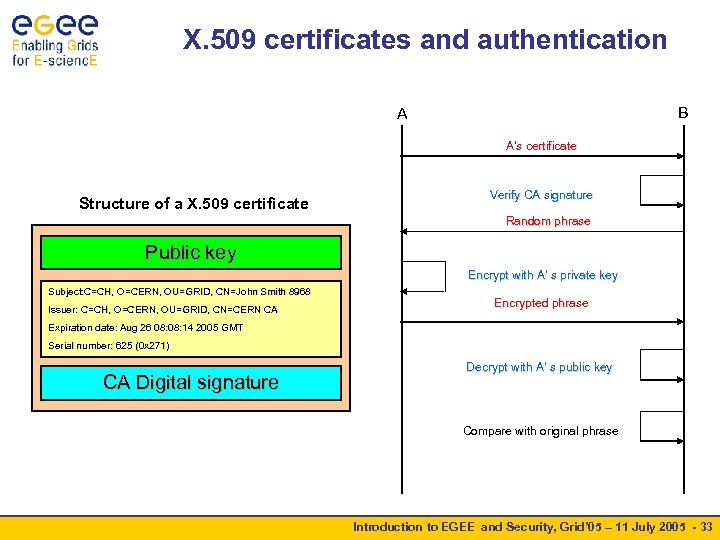 X. 509 certificates and authentication B A A’s certificate Structure of a X. 509 certificate Verify CA signature Random phrase Public key Encrypt with A’ s private key Subject: C=CH, O=CERN, OU=GRID, CN=John Smith 8968 Subject: C=CH, Issuer: C=CH, O=CERN, OU=GRID, CN=CERN CA Encrypted phrase Expiration date: Aug 26 08: 14 2005 GMT Serial number: 625 (0 x 271) CA Digital signature Decrypt with A’ s public key Compare with original phrase Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 33
X. 509 certificates and authentication B A A’s certificate Structure of a X. 509 certificate Verify CA signature Random phrase Public key Encrypt with A’ s private key Subject: C=CH, O=CERN, OU=GRID, CN=John Smith 8968 Subject: C=CH, Issuer: C=CH, O=CERN, OU=GRID, CN=CERN CA Encrypted phrase Expiration date: Aug 26 08: 14 2005 GMT Serial number: 625 (0 x 271) CA Digital signature Decrypt with A’ s public key Compare with original phrase Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 33
 Certificate classification • User certificate issued to a physical person DN= C=CH, O=CERN, OU=GRID, CN =John Smith • the only kind of certificate good for a client, i. e. to send Grid jobs etc. • • • Host certificate • • • issued to a machine (i. e. a secure web server, etc. ) request signed with a user certificate DN= C=CH, O=CERN, OU=GRID, CN=host 1. cern. ch • Grid host certificate • • • issued to a Grid service (i. e. a Resource Broker, a Computing Element, etc. ) request signed with a user certificate DN= C=CH, O=CERN, OU=GRID, CN=host/host 1. cern. ch • Service certificate • • • issued to a program running on a machine request signed with a user certificate DN= C=CH, O=CERN, OU=GRID, CN=ldap/host 1. cern. ch Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 34
Certificate classification • User certificate issued to a physical person DN= C=CH, O=CERN, OU=GRID, CN =John Smith • the only kind of certificate good for a client, i. e. to send Grid jobs etc. • • • Host certificate • • • issued to a machine (i. e. a secure web server, etc. ) request signed with a user certificate DN= C=CH, O=CERN, OU=GRID, CN=host 1. cern. ch • Grid host certificate • • • issued to a Grid service (i. e. a Resource Broker, a Computing Element, etc. ) request signed with a user certificate DN= C=CH, O=CERN, OU=GRID, CN=host/host 1. cern. ch • Service certificate • • • issued to a program running on a machine request signed with a user certificate DN= C=CH, O=CERN, OU=GRID, CN=ldap/host 1. cern. ch Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 34
 Grid Security Infrastructure (GSI) • Globus Toolkit. TM proposed and implements the Grid Security Infrastructure (GSI) • Protocols and APIs to address Grid security needs • GSI protocols extend standard public key protocols Standards: X. 509 & SSL/TLS • Extensions: X. 509 Proxy Certificates (single sign-on) & Delegation • • Proxy Certificate: Short term, restricted certificate that is derived form a long-term X. 509 certificate • Signed by the normal end entity cert, or by another proxy • Allows a process to act on behalf of a user • Not encrypted and thus needs to be securely managed by file system • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 35
Grid Security Infrastructure (GSI) • Globus Toolkit. TM proposed and implements the Grid Security Infrastructure (GSI) • Protocols and APIs to address Grid security needs • GSI protocols extend standard public key protocols Standards: X. 509 & SSL/TLS • Extensions: X. 509 Proxy Certificates (single sign-on) & Delegation • • Proxy Certificate: Short term, restricted certificate that is derived form a long-term X. 509 certificate • Signed by the normal end entity cert, or by another proxy • Allows a process to act on behalf of a user • Not encrypted and thus needs to be securely managed by file system • Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 35
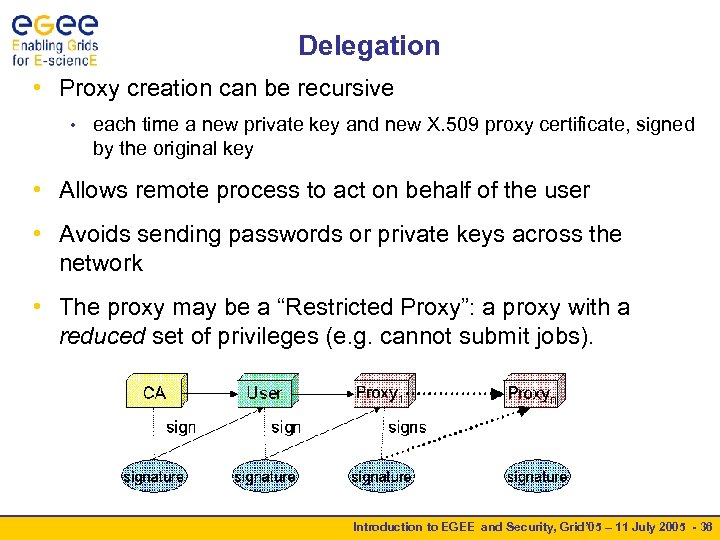 Delegation • Proxy creation can be recursive • each time a new private key and new X. 509 proxy certificate, signed by the original key • Allows remote process to act on behalf of the user • Avoids sending passwords or private keys across the network • The proxy may be a “Restricted Proxy”: a proxy with a reduced set of privileges (e. g. cannot submit jobs). Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 36
Delegation • Proxy creation can be recursive • each time a new private key and new X. 509 proxy certificate, signed by the original key • Allows remote process to act on behalf of the user • Avoids sending passwords or private keys across the network • The proxy may be a “Restricted Proxy”: a proxy with a reduced set of privileges (e. g. cannot submit jobs). Introduction to EGEE and Security, Grid’ 05 – 11 July 2005 - 36


