bc21fcaf74a10171cf90c59d2e9ec421.ppt
- Количество слайдов: 106

http: //dl. free. fr/k. FB 3 ljra 4/cours 3 -WAN. pdf Réseau WAN vu de l’entreprise Gilles Clugnac Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 1
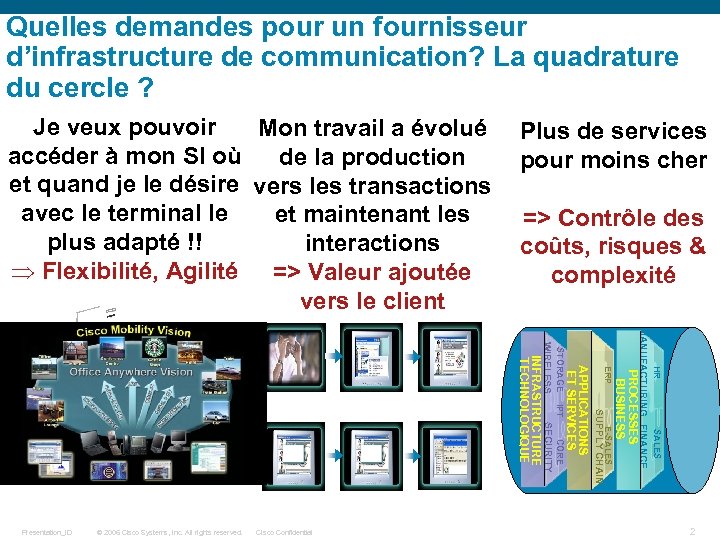
Quelles demandes pour un fournisseur d’infrastructure de communication? La quadrature du cercle ? Je veux pouvoir Mon travail a évolué accéder à mon SI où de la production et quand je le désire vers les transactions avec le terminal le et maintenant les plus adapté !! interactions Þ Flexibilité, Agilité => Valeur ajoutée vers le client Plus de services pour moins cher => Contrôle des coûts, risques & complexité HR SALES MANUFACTURING FINANCE E-SALES SUPPLY CHAIN CORE PROCESSES BUSINESS ERP APPLICATIONS ET SERVICES SECURITY Cisco Confidential IPT © 2006 Cisco Systems, Inc. All rights reserved. STORAGE WIRELESS INFRASTRUCTURE TECHNOLOGIQUE Presentation_ID 2

Convergence des réseaux Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 3

Changement de paradigme Exemple : Vidéosurveillance intégrée Major Segments of Security INTRUSION DETECTION ID CREDENTIAL MANAGEMENT CCTV & DIGITAL VIDEO SURVEILLANCE DATA & NETWORK SECURITY ACCESS CONTROL VISITOR MANAGEMENT Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential FIRE ALARM 4
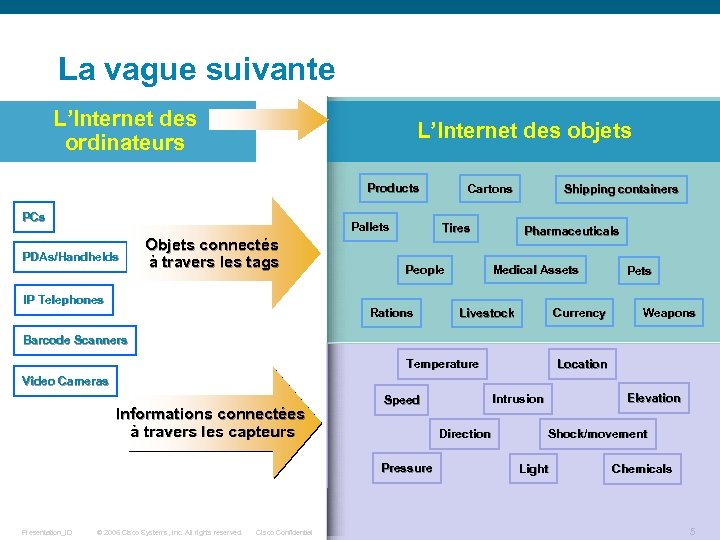
La vague suivante L’Internet des ordinateurs L’Internet des objets Products PCs Pallets PDAs/Handhelds Objets connectés à travers les tags IP Telephones Cartons Tires Pharmaceuticals Medical Assets People Rations Shipping containers Currency Livestock Pets Weapons Barcode Scanners Temperature Location Video Cameras Informations connectées à travers les capteurs Direction Pressure Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Elevation Intrusion Speed Shock/movement Light Chemicals 5
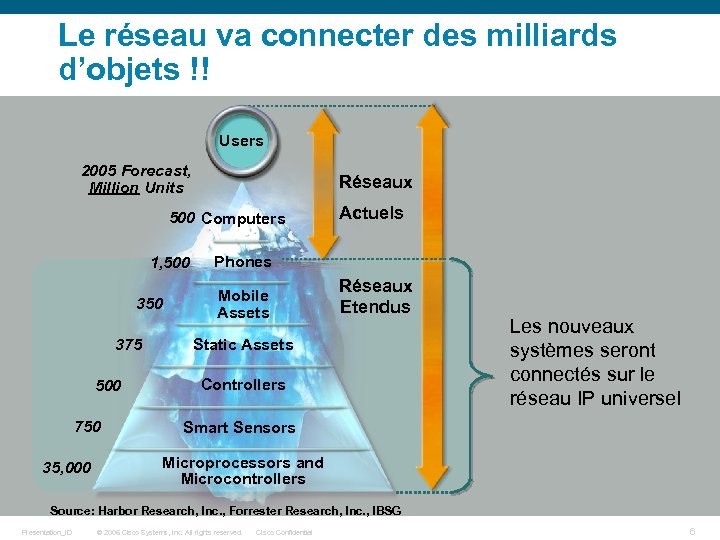
Le réseau va connecter des milliards d’objets !! Users 2005 Forecast, Million Units Réseaux 500 Computers 1, 500 350 375 500 750 35, 000 Actuels Phones Mobile Assets Réseaux Etendus Static Assets Controllers Les nouveaux systèmes seront connectés sur le réseau IP universel Smart Sensors Microprocessors and Microcontrollers Source: Harbor Research, Inc. , Forrester Research, Inc. , IBSG Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 6
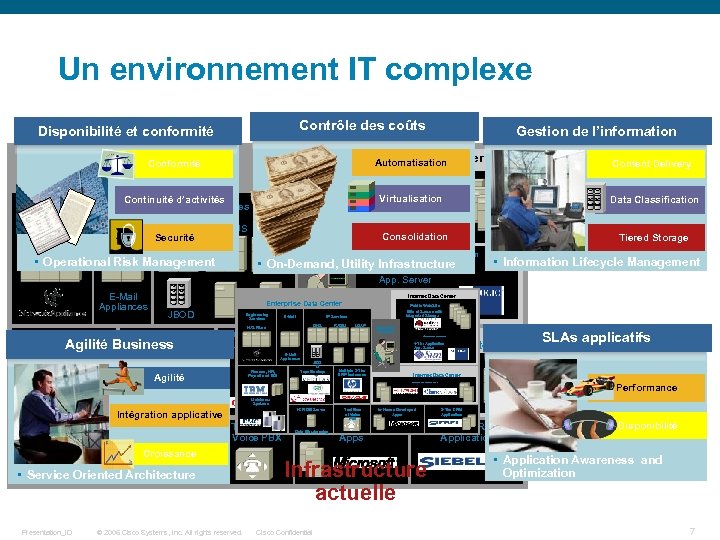
Un environnement IT complexe Contrôle des coûts Disponibilité et conformité Internet Data Center Automatisation Conformité Enterprise Data Center Engineering Services DNS Securité RADIUS LDAP Operations Center Data Classification Consolidation E-Commerce Application • Operational Risk Management Content Delivery Public Web Site 100 s of Servers with Virtualisation Integrated Storage Continuité d’activités E-Mail IP Services NAS Filers Gestion de l’information • On-Demand, Utility Infrastructure 4 -Tier Application Tiered Storage • Information Lifecycle Management App. Server E-Mail Appliances Internet Data Center Enterprise Data Center JBOD Engineering Services E-Mail DNS NAS Filers Finance, HR, Agilité Payroll and EDI Tape Backup Business Multiple 2 -Tier ERP Instances Agilité Mainframe Systems LDAP Operation s Center SLAs applicatifs E-Commerce Application 4 -Tier Application App. Server JBO D Tape Backup Supply-Chain Management Multiple 2 -Tier ERP Instances Internet Data Center Supply-Chain Management Performance Mainframe Systems Intégration applicative Traditional NCR DB Server Voice PBX Croissance • Service Oriented Architecture Data Warehousing Presentation_ID RADIU S Internet Data Center E-Mail Appliances Finance, HR, Payroll and EDI Public Web Site 100 s of Servers with Integrated Storage IP Services © 2006 Cisco Systems, Inc. All rights reserved. NCR DB Server Tradition al Voice PBX In-House Developed Apps Data Warehousing Infrastructure actuelle Cisco Confidential 2 -Tier CRM Application Disponibilité • Application Awareness and Optimization 7
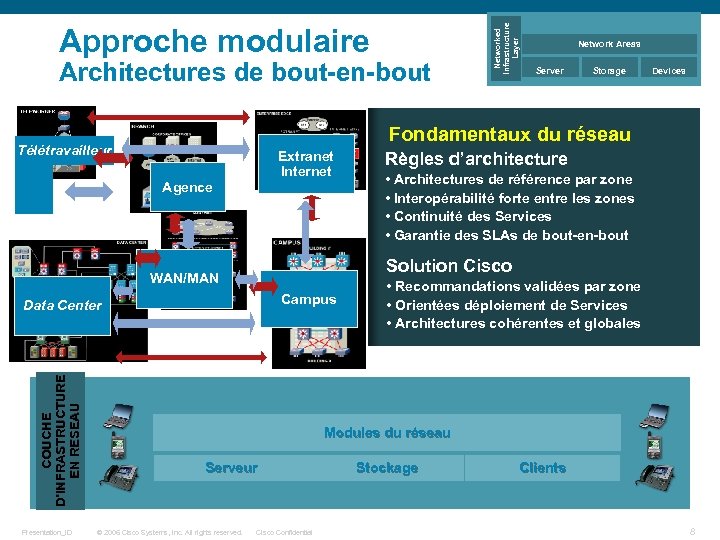
Architectures de bout-en-bout Networked Infrastructure Layer Approche modulaire Network Areas Server Storage Devices Fondamentaux du réseau Télétravailleur Extranet Internet Agence Règles d’architecture • Architectures de référence par zone • Interopérabilité forte entre les zones • Continuité des Services • Garantie des SLAs de bout-en-bout Solution Cisco WAN/MAN Campus Data Center • Recommandations validées par zone • Orientées déploiement de Services • Architectures cohérentes et globales COUCHE D’INFRASTRUCTURE EN RESEAU Site B Presentation_ID Campus Agence Serveur © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Data Extranet Modules du réseau Center Internet Télétravaill WAN/MAN eur Stockage Clients 8
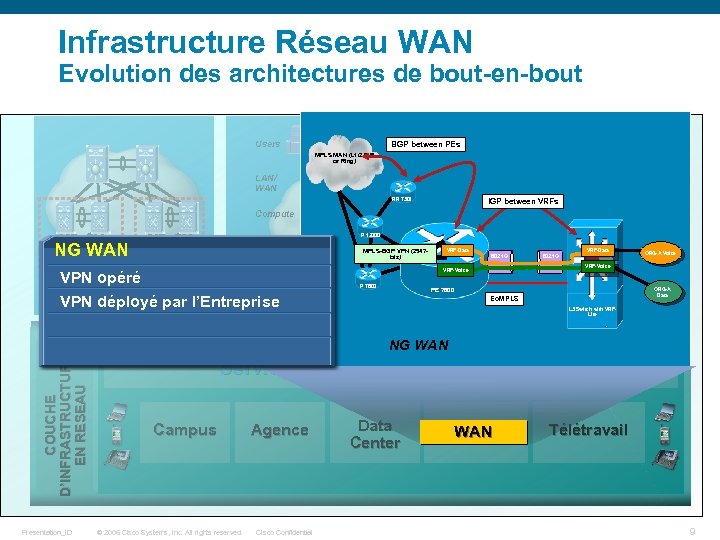
Infrastructure Réseau WAN Evolution des architectures de bout-en-bout Users BGP between PEs MPLS MAN (L 1/2 P-P or Ring) LAN/ WAN RR 7301 Compute SAN NG WAN P 12000 MPLS-BGP VPN (2547 -bis) P 12000 VRF-Data Tape VPN opéré Consolidated Data Center VPN déployé par Adaptable Campusl’Entreprise VRF-Voice RS RS VRF-Data 802. 1 Q Disk/ P 7600 802. 1 Q ORG-A Voice VRF-Voice MPLS-BGP VPN (2547 bis) RS IGP between VRFs RR 7301 PE 7600 802. 1 Q VRF-Data Eo. MPLSVRF-Voice L 3 Switch with VRFLite PE 7600 NG WAN ORGORG-A Voice A Data ORG-A Data Eo. MPLS L 3 Switch with VRFLite COUCHE D’INFRASTRUCTURE EN RESEAU NG WAN Presentation_ID Services de Virtualisation du réseau Campus © 2006 Cisco Systems, Inc. All rights reserved. Agence Cisco Confidential Data Center MAN/WAN Télétravail 9
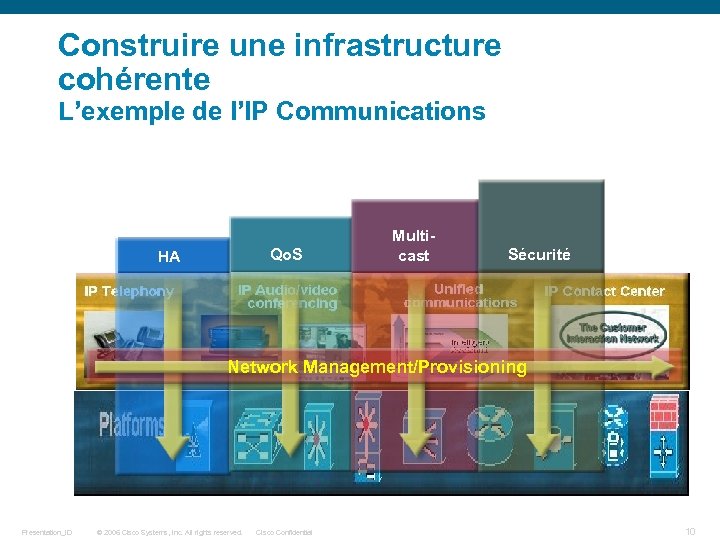
Construire une infrastructure cohérente L’exemple de l’IP Communications Qo. S HA Multicast Sécurité Network Management/Provisioning Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 10
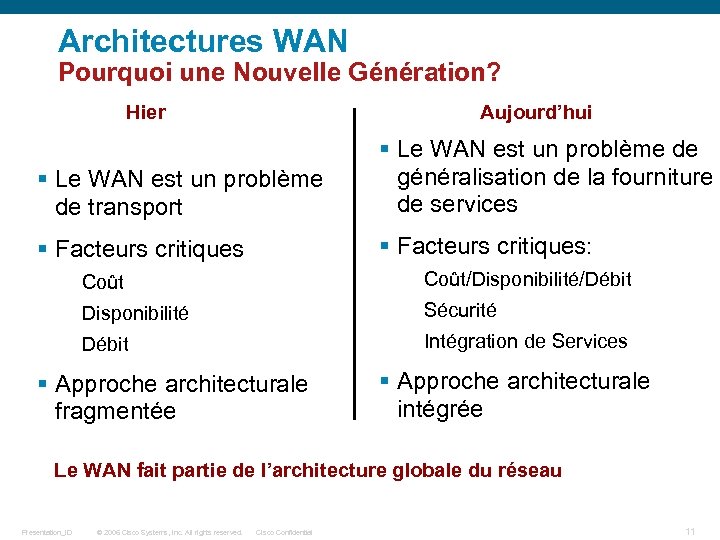
Architectures WAN Pourquoi une Nouvelle Génération? Hier Aujourd’hui § Le WAN est un problème de transport § Le WAN est un problème de généralisation de la fourniture de services § Facteurs critiques: Coût/Disponibilité/Débit Disponibilité Sécurité Débit Intégration de Services § Approche architecturale fragmentée § Approche architecturale intégrée Le WAN fait partie de l’architecture globale du réseau Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 11

Un Besoin de Segmentation § Accès invité Internet access for customers, visitors, etc. § Contrôle d’Accès au Réseau Quarantine and/or isolation during remediation § Accès partenaires Onsite partners, limited server/application access § Séparation Groupes/Départments Closed User Groups for divisions/teams sharing common work locations (e. g. Financial Banking/Trading) L‘isolation des groupes est le principal besoin. Les attaques, virus, vers sont plus facilement confinés. Services Externalisés Participating in multiple client networks (e. g. India ITS model) Ils ne se progagent pas partout § Isolation des Applications/Systèmes Isolating critical applications or devices, such as IPC, factory robots, point-of-sale terminals, etc. § § Filiales / Fusions & Acquisitions Enabling staged network consolidation, while companies are being merged § Entreprise Fournisseur de Services Réseaux (éventuellement source de revenus) Shared service locations (e. g. Munich Airport “virtual” gate access) Retail stores providing kiosk/on-location network access (e. g. Best Buy, Albertson’s, etc. ) Cisco Connected Real Estate (CCRE) (e. g. multi-tenant, strip malls, etc. ) § Dynamique forte de création de projets Closed User Groups between multiple companies during joint-ventures/collaborations Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 12
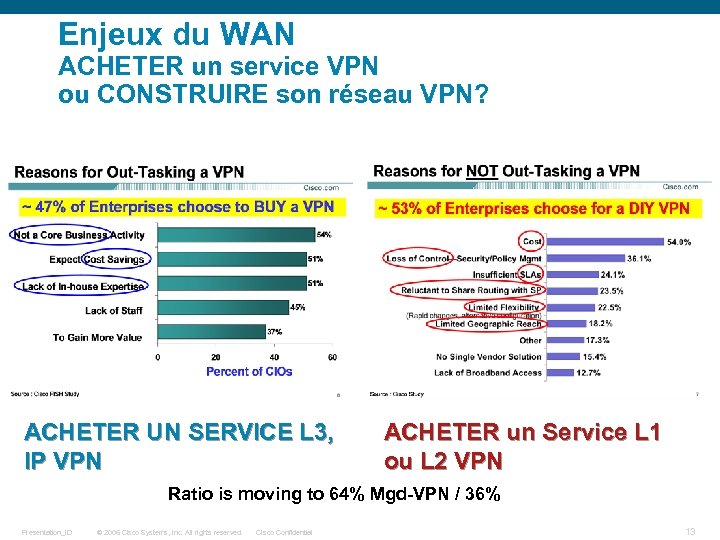
Enjeux du WAN ACHETER un service VPN ou CONSTRUIRE son réseau VPN? ACHETER UN SERVICE L 3, IP VPN ACHETER un Service L 1 ou L 2 VPN Ratio is moving to 64% Mgd-VPN / 36% Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 13

Enjeux de l’agence Amener les Services aux utilisateurs • Information disponible dans tous les sites de l’entreprise • Besoin de performances dans le Data. Center comme pour l’utilisateur • Fiabilité de tout le système d’information • Architecture et Services réseaux transparents pour l’utilisateur • Les sites distants ou de télétravail ont des besoins audelà de la simple connexion ! Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 14
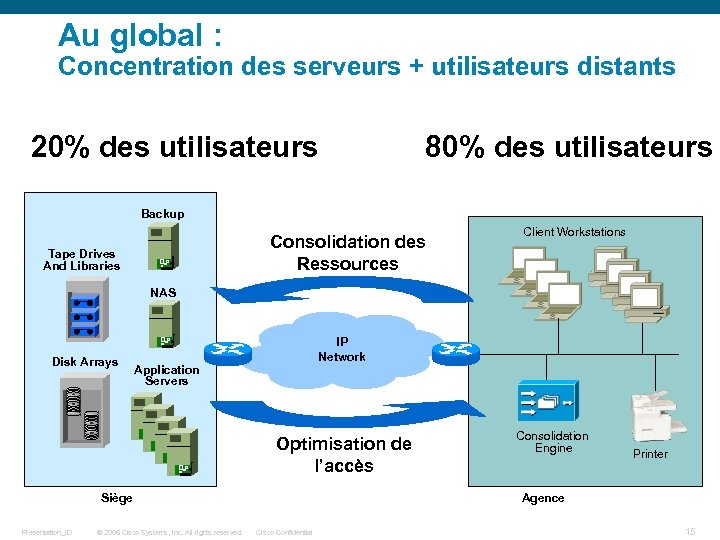
Au global : Concentration des serveurs + utilisateurs distants 20% des utilisateurs 80% des utilisateurs Backup Consolidation des Ressources Tape Drives And Libraries Client Workstations NAS Disk Arrays IP Network Application Servers Optimisation de l’accès Siège Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Consolidation Engine Printer Agence Cisco Confidential 15
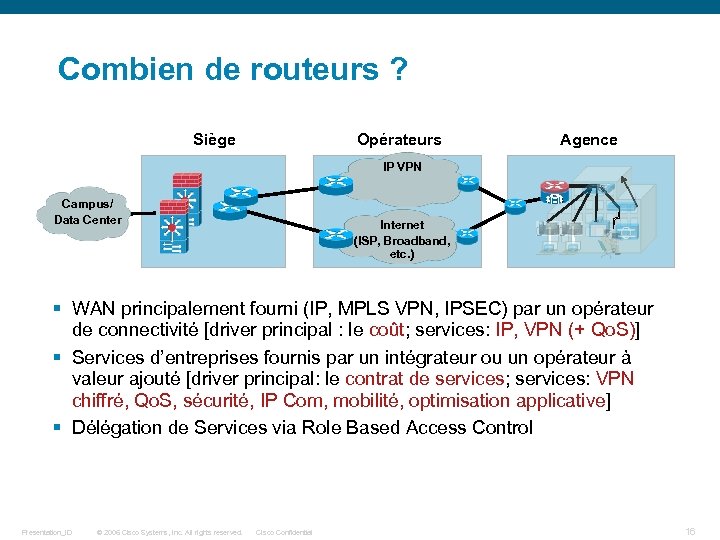
Combien de routeurs ? Siège Opérateurs Agence IP VPN Campus/ Data Center Internet (ISP, Broadband, etc. ) § WAN principalement fourni (IP, MPLS VPN, IPSEC) par un opérateur de connectivité [driver principal : le coût; services: IP, VPN (+ Qo. S)] § Services d’entreprises fournis par un intégrateur ou un opérateur à valeur ajouté [driver principal: le contrat de services; services: VPN chiffré, Qo. S, sécurité, IP Com, mobilité, optimisation applicative] § Délégation de Services via Role Based Access Control Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 16
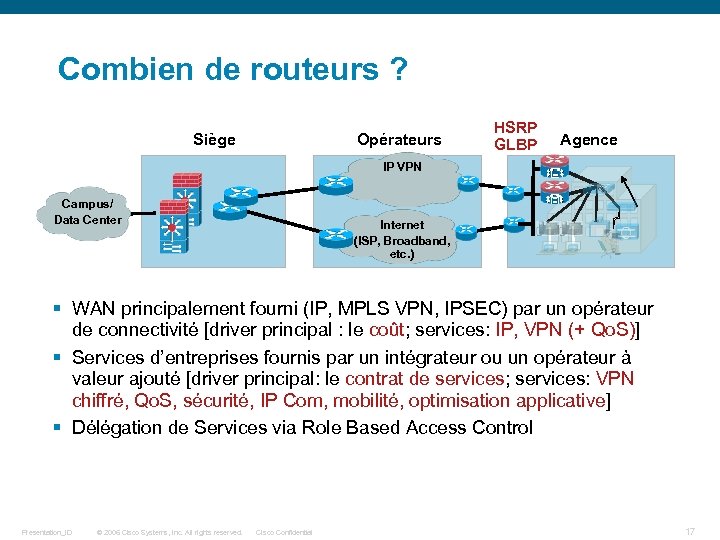
Combien de routeurs ? Siège Opérateurs HSRP GLBP Agence IP VPN Campus/ Data Center Internet (ISP, Broadband, etc. ) § WAN principalement fourni (IP, MPLS VPN, IPSEC) par un opérateur de connectivité [driver principal : le coût; services: IP, VPN (+ Qo. S)] § Services d’entreprises fournis par un intégrateur ou un opérateur à valeur ajouté [driver principal: le contrat de services; services: VPN chiffré, Qo. S, sécurité, IP Com, mobilité, optimisation applicative] § Délégation de Services via Role Based Access Control Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 17

VPN OPERE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 18
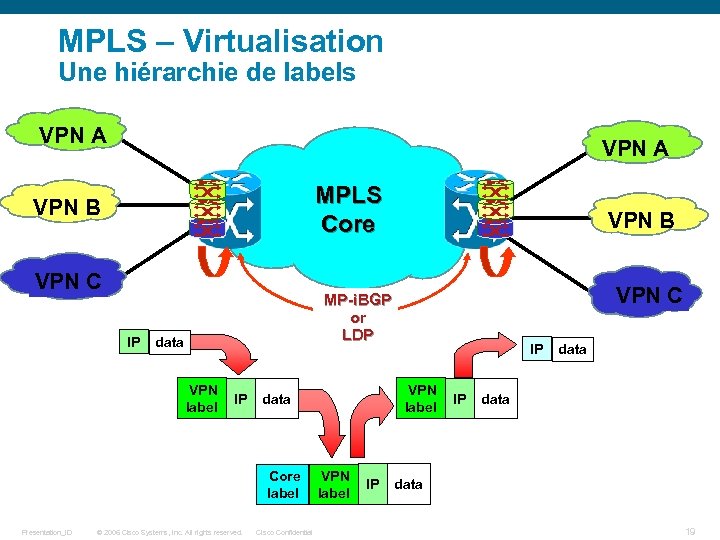
MPLS – Virtualisation Une hiérarchie de labels VPN A MPLS Core VPN B VPN C IP VPN C MP-i. BGP or LDP data VPN label IP © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential IP VPN label data Core label Presentation_ID VPN B VPN label IP IP data 19
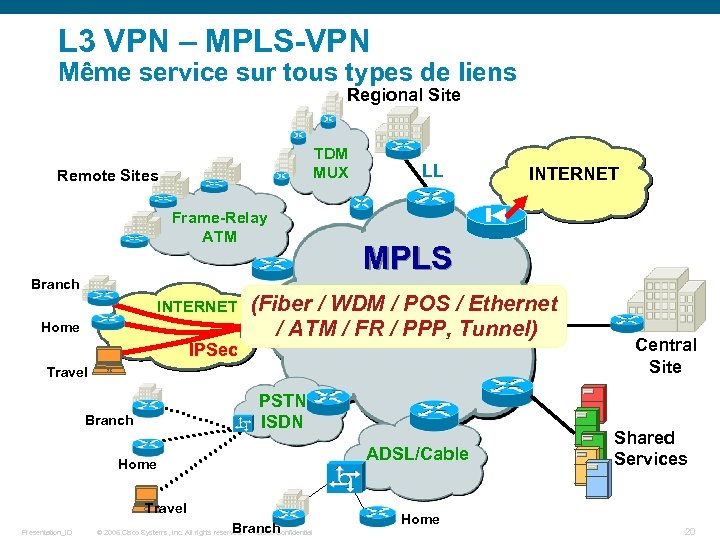
L 3 VPN – MPLS-VPN Même service sur tous types de liens Regional Site TDM MUX Remote Sites Frame-Relay ATM Branch INTERNET Home IPSec LL MPLS (Fiber / WDM / POS / Ethernet / ATM / FR / PPP, Tunnel) Travel PSTN ISDN Branch ADSL/Cable Home Travel Presentation_ID Branch Cisco Confidential © 2006 Cisco Systems, Inc. All rights reserved. INTERNET Home Central Site Shared Services 20
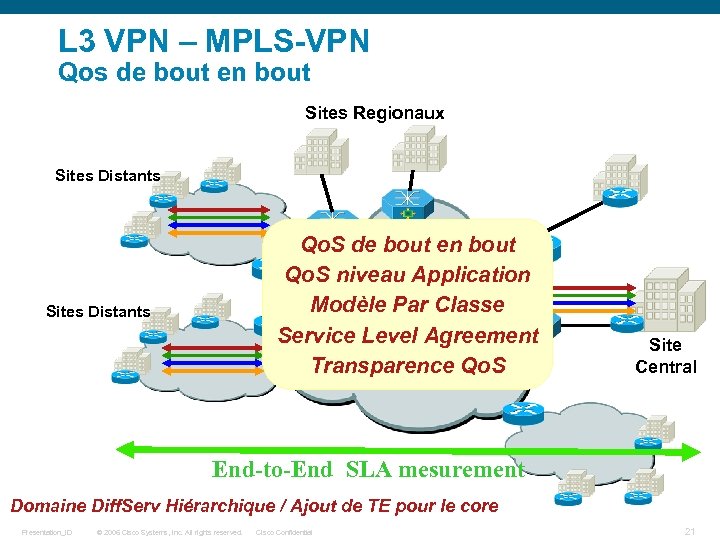
L 3 VPN – MPLS-VPN Qos de bout en bout Sites Regionaux Sites Distants Qo. S de bout en bout MPLS Qo. S niveau Application IP-VPN Modèle Par Classe Service. L 2 VPN Level Agreement Transparence Qo. S Sites Distants Qo. S Site Central End-to-End SLA mesurement Domaine Diff. Serv Hiérarchique / Ajout de TE pour le core Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 21
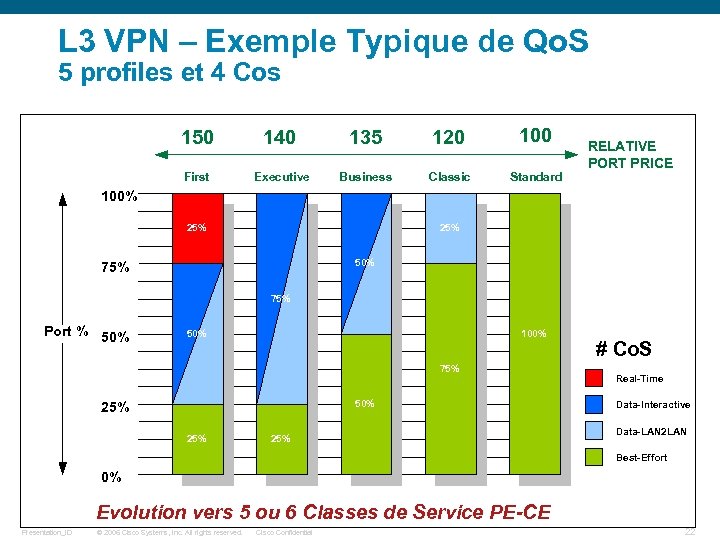
L 3 VPN – Exemple Typique de Qo. S 5 profiles et 4 Cos 150 140 135 120 100 First Executive Business Classic Standard RELATIVE PORT PRICE 100% 25% 50% 75% Port % 50% 100% 75% 50% 25% 25% # Co. S Real-Time Data-Interactive Data-LAN 2 LAN Best-Effort 0% Evolution vers 5 ou 6 Classes de Service PE-CE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 22
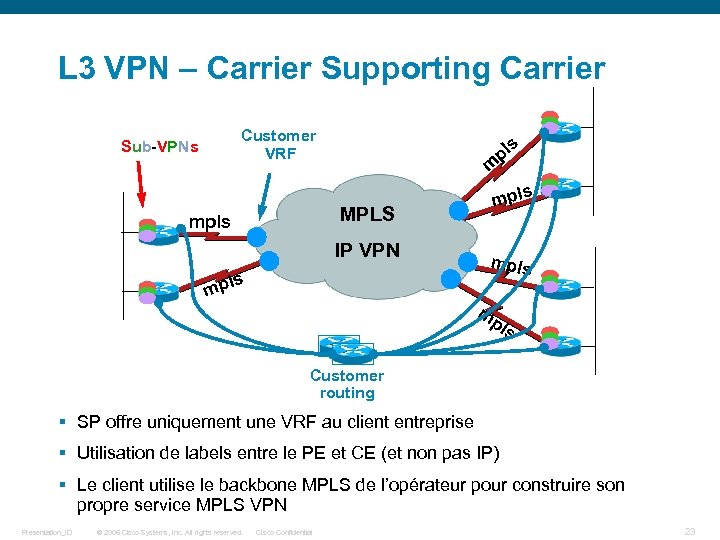
L 3 VPN – Carrier Supporting Carrier Customer VRF Sub-VPNs m MPLS Internet IP VPN mpls mp s pl ls mpls m pl s Customer routing § SP offre uniquement une VRF au client entreprise § Utilisation de labels entre le PE et CE (et non pas IP) § Le client utilise le backbone MPLS de l’opérateur pour construire son propre service MPLS VPN Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 23
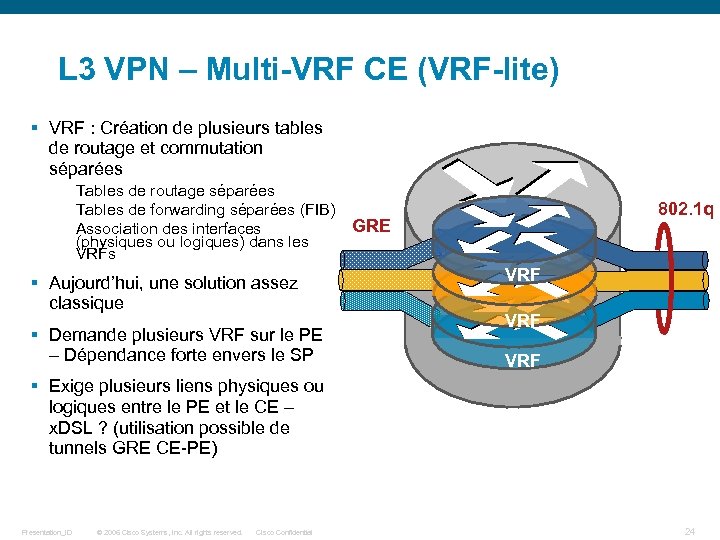
L 3 VPN – Multi-VRF CE (VRF-lite) § VRF : Création de plusieurs tables de routage et commutation séparées Tables de routage séparées Tables de forwarding séparées (FIB) Association des interfaces (physiques ou logiques) dans les VRFs § Aujourd’hui, une solution assez classique § Demande plusieurs VRF sur le PE – Dépendance forte envers le SP 802. 1 q GRE VRF VRF § Exige plusieurs liens physiques ou logiques entre le PE et le CE – x. DSL ? (utilisation possible de tunnels GRE CE-PE) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 24
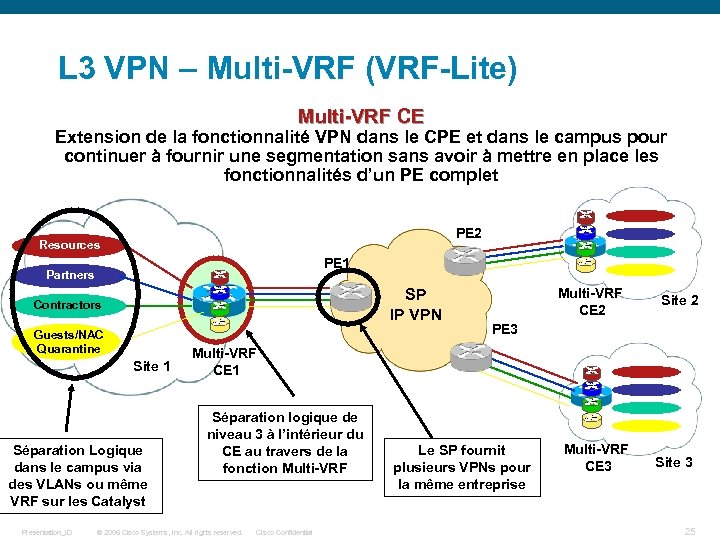
L 3 VPN – Multi-VRF (VRF-Lite) Multi-VRF CE Extension de la fonctionnalité VPN dans le CPE et dans le campus pour continuer à fournir une segmentation sans avoir à mettre en place les fonctionnalités d’un PE complet PE 2 Resources PE 1 Partners SP IP VPN Contractors Guests/NAC Quarantine Site 1 Séparation Logique dans le campus via des VLANs ou même VRF sur les Catalyst Presentation_ID Multi-VRF CE 2 Site 2 PE 3 Multi-VRF CE 1 Séparation logique de niveau 3 à l’intérieur du CE au travers de la fonction Multi-VRF © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Le SP fournit plusieurs VPNs pour la même entreprise Multi-VRF CE 3 Site 3 25
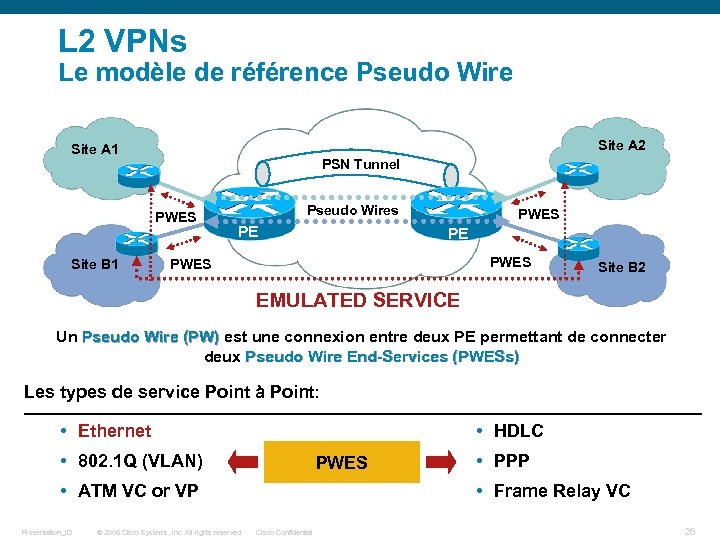
L 2 VPNs Le modèle de référence Pseudo Wire Site A 2 Site A 1 PSN Tunnel PWES Site B 1 Pseudo Wires PE PWES Site B 2 EMULATED SERVICE Un Pseudo Wire (PW) est une connexion entre deux PE permettant de connecter deux Pseudo Wire End-Services (PWESs) Les types de service Point à Point: • Ethernet • HDLC • 802. 1 Q (VLAN) PWES • ATM VC or VP Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. • PPP • Frame Relay VC Cisco Confidential 26
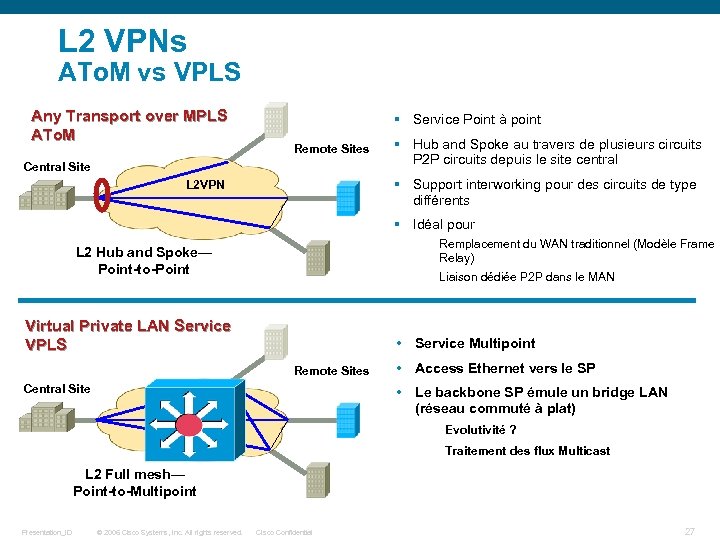
L 2 VPNs ATo. M vs VPLS Any Transport over MPLS ATo. M § Service Point à point Remote Sites Central Site § Hub and Spoke au travers de plusieurs circuits P 2 P circuits depuis le site central § Support interworking pour des circuits de type différents L 2 VPN § Idéal pour Remplacement du WAN traditionnel (Modèle Frame Relay) L 2 Hub and Spoke— Point-to-Point Liaison dédiée P 2 P dans le MAN Virtual Private LAN Service VPLS • Service Multipoint Remote Sites Central Site • Access Ethernet vers le SP • Le backbone SP émule un bridge LAN (réseau commuté à plat) L 2 VPN Evolutivité ? Traitement des flux Multicast L 2 Full mesh— Point-to-Multipoint Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 27

VPN DEPLOYE PAR L’ENTREPRISE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 28
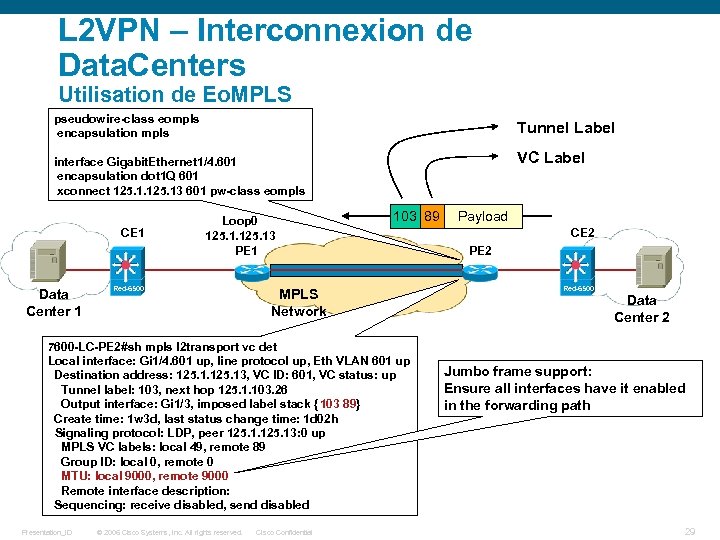
L 2 VPN – Interconnexion de Data. Centers Utilisation de Eo. MPLS pseudowire-class eompls encapsulation mpls Tunnel Label VC Label interface Gigabit. Ethernet 1/4. 601 encapsulation dot 1 Q 601 xconnect 125. 13 601 pw-class eompls CE 1 Data Center 1 Loop 0 125. 13 PE 1 Red-6500 103 89 MPLS Network 7600 -LC-PE 2#sh mpls l 2 transport vc det Local interface: Gi 1/4. 601 up, line protocol up, Eth VLAN 601 up Destination address: 125. 13, VC ID: 601, VC status: up Tunnel label: 103, next hop 125. 1. 103. 26 Output interface: Gi 1/3, imposed label stack {103 89} Create time: 1 w 3 d, last status change time: 1 d 02 h Signaling protocol: LDP, peer 125. 13: 0 up MPLS VC labels: local 49, remote 89 Group ID: local 0, remote 0 MTU: local 9000, remote 9000 Remote interface description: Sequencing: receive disabled, send disabled Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Payload CE 2 PE 2 Red-6500 Data Center 2 Jumbo frame support: Ensure all interfaces have it enabled in the forwarding path 29
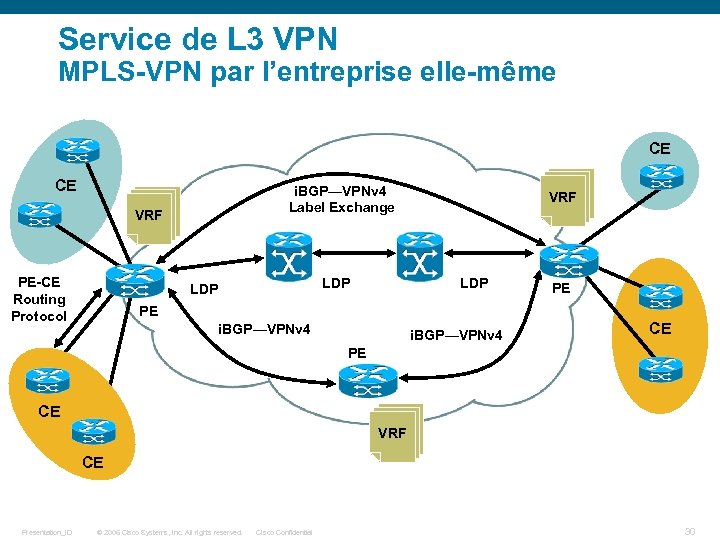
Service de L 3 VPN MPLS-VPN par l’entreprise elle-même CE CE i. BGP—VPNv 4 Label Exchange VRF PE-CE Routing Protocol LDP VRF LDP PE PE i. BGP—VPNv 4 CE PE CE VRF CE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 30

IPSec VPN dans le WAN Enterprise Applications Clients Pourquoi utiliser un VPN IPSec ? § Encryption sur les liens WAN traditionnels (par exemple FR, ATM, LL) § Conformité aux nouvelles législations : HIPAA, Sarbanes-Oxley (SOx), Basel Agreement (Europe), etc. § Migration d’un WAN traditionnel vers un service bas-coût (exemple Internet, broadband) § Utilisation d’un service Internet comme WAN secondaire, comme backup ou comme lien pour le trafic non critique et bande passante importante § Extension des services de sites vers les télétravailleurs Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 31
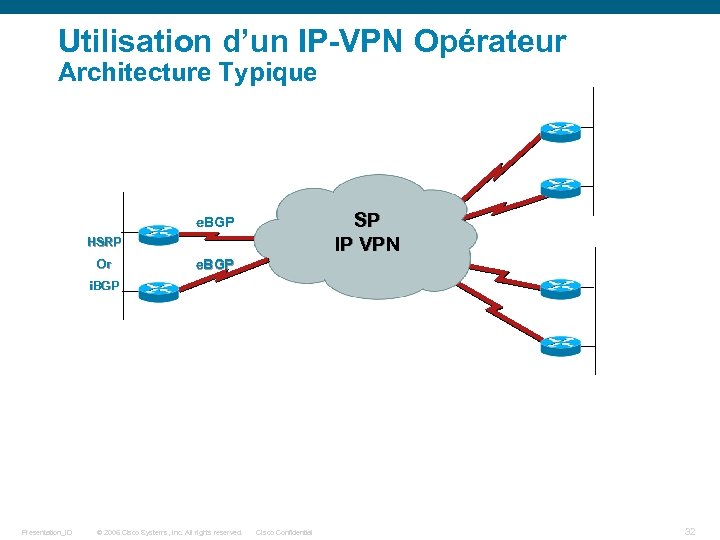
Utilisation d’un IP-VPN Opérateur Architecture Typique SP Internet IP VPN e. BGP HSRP Or e. BGP i. BGP Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 32
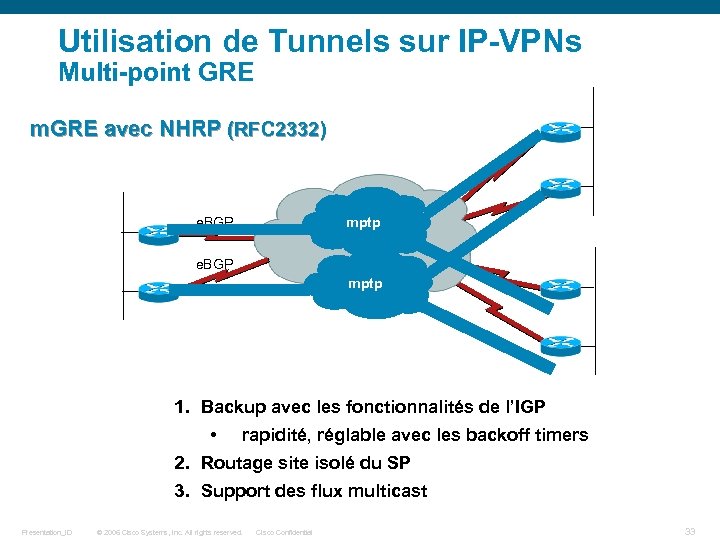
Utilisation de Tunnels sur IP-VPNs Multi-point GRE m. GRE avec NHRP (RFC 2332) IP VPN mptp Internet e. BGP mptp 1. Backup avec les fonctionnalités de l’IGP • rapidité, réglable avec les backoff timers 2. Routage site isolé du SP 3. Support des flux multicast Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 33
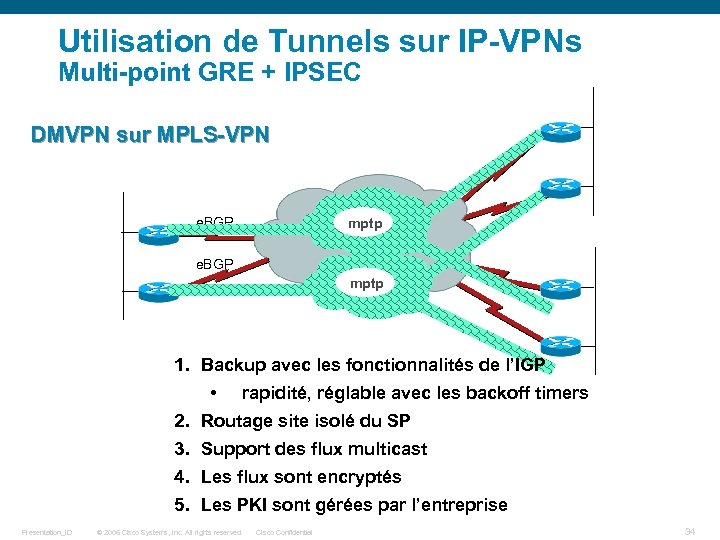
Utilisation de Tunnels sur IP-VPNs Multi-point GRE + IPSEC DMVPN sur MPLS-VPN IP VPN mptp Internet e. BGP mptp 1. Backup avec les fonctionnalités de l’IGP • rapidité, réglable avec les backoff timers 2. Routage site isolé du SP 3. Support des flux multicast 4. Les flux sont encryptés 5. Les PKI sont gérées par l’entreprise Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 34
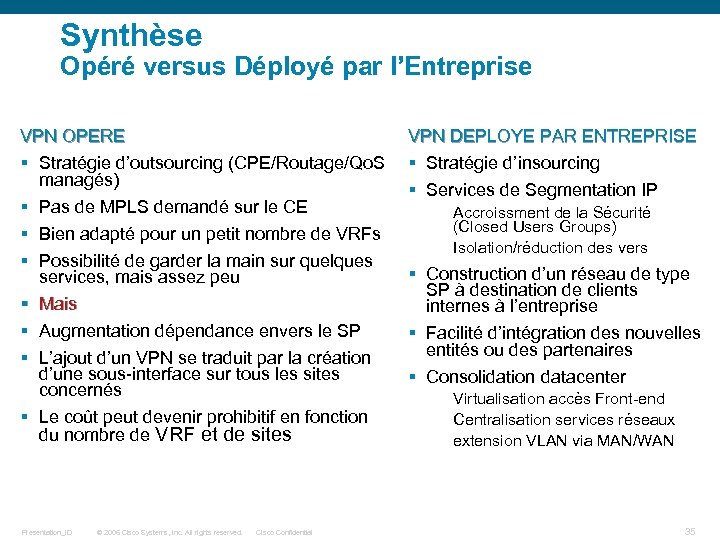
Synthèse Opéré versus Déployé par l’Entreprise VPN OPERE § Stratégie d’outsourcing (CPE/Routage/Qo. S managés) § Pas de MPLS demandé sur le CE § Bien adapté pour un petit nombre de VRFs § Possibilité de garder la main sur quelques services, mais assez peu § Mais § Augmentation dépendance envers le SP § L’ajout d’un VPN se traduit par la création d’une sous-interface sur tous les sites concernés § Le coût peut devenir prohibitif en fonction du nombre de VRF et de sites Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential VPN DEPLOYE PAR ENTREPRISE § Stratégie d’insourcing § Services de Segmentation IP Accroissment de la Sécurité (Closed Users Groups) Isolation/réduction des vers § Construction d’un réseau de type SP à destination de clients internes à l’entreprise § Facilité d’intégration des nouvelles entités ou des partenaires § Consolidation datacenter Virtualisation accès Front-end Centralisation services réseaux extension VLAN via MAN/WAN 35

Qualité de service Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 36
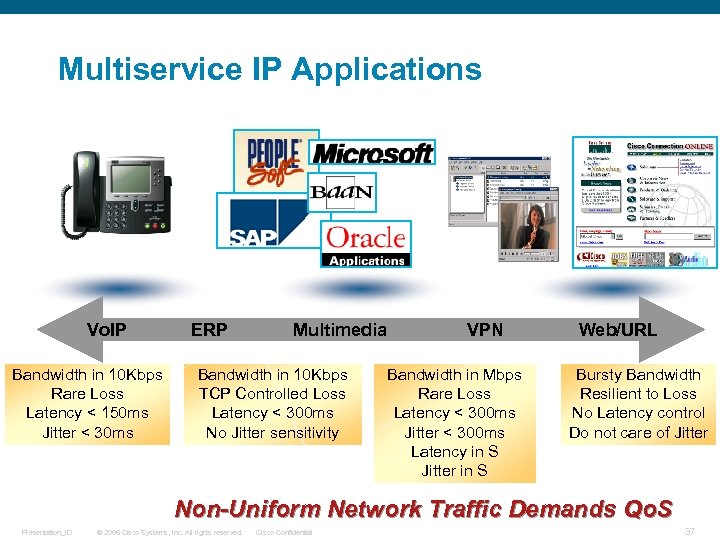
Multiservice IP Applications Vo. IP Bandwidth in 10 Kbps Rare Loss Latency < 150 ms Jitter < 30 ms ERP Multimedia Bandwidth in 10 Kbps TCP Controlled Loss Latency < 300 ms No Jitter sensitivity VPN Bandwidth in Mbps Rare Loss Latency < 300 ms Jitter < 300 ms Latency in S Jitter in S Web/URL Bursty Bandwidth Resilient to Loss No Latency control Do not care of Jitter Non-Uniform Network Traffic Demands Qo. S Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 37

So, What Is Quality of Service? “Collection of technologies which allows applications/users to request and receive predictable service levels in terms of data throughput capacity (bandwidth), latency variations (jitter) and delay” Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 38

Qo. S Factors Delay (Latency) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Delay. Variation (Jitter) Cisco Confidential Packet Loss 39
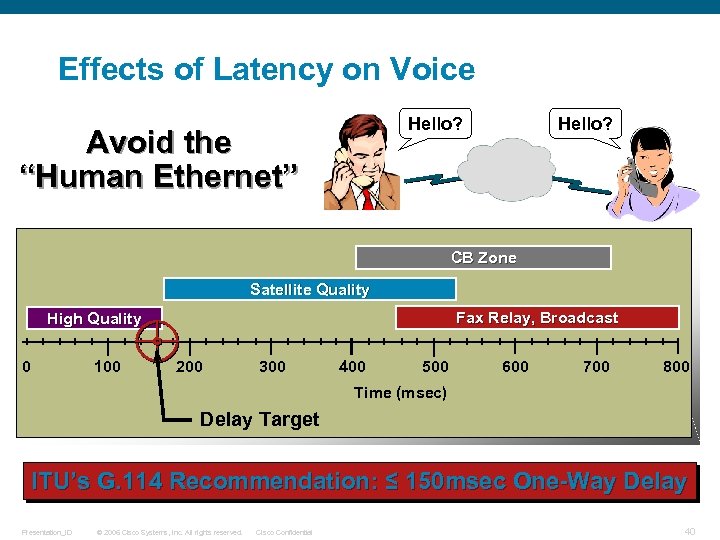
Effects of Latency on Voice Hello? Avoid the “Human Ethernet” Hello? CB Zone Satellite Quality Fax Relay, Broadcast High Quality 0 100 200 300 400 500 600 700 800 Time (msec) Delay Target ITU’s G. 114 Recommendation: ≤ 150 msec One-Way Delay Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 40
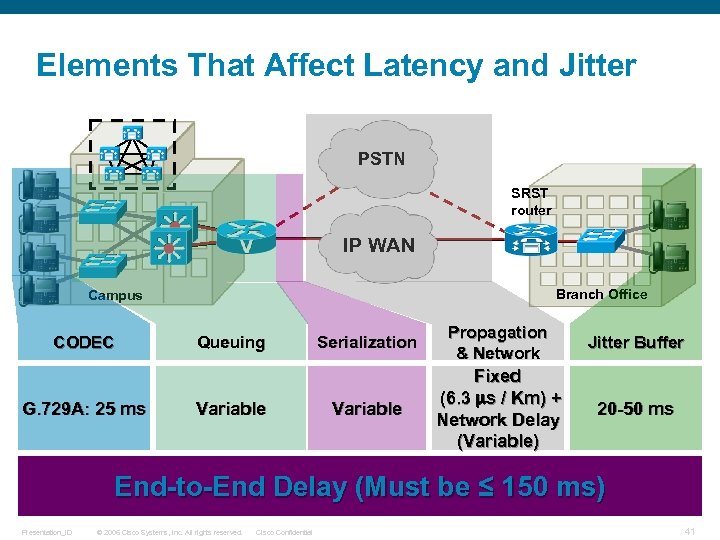
Elements That Affect Latency and Jitter PSTN SRST router IP WAN Branch Office Campus CODEC G. 729 A: 25 ms Queuing Variable Serialization Propagation & Network Jitter Buffer Variable Fixed (6. 3 s / Km) + Network Delay (Variable) 20 -50 ms End-to-End Delay (Must be ≤ 150 ms) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 41
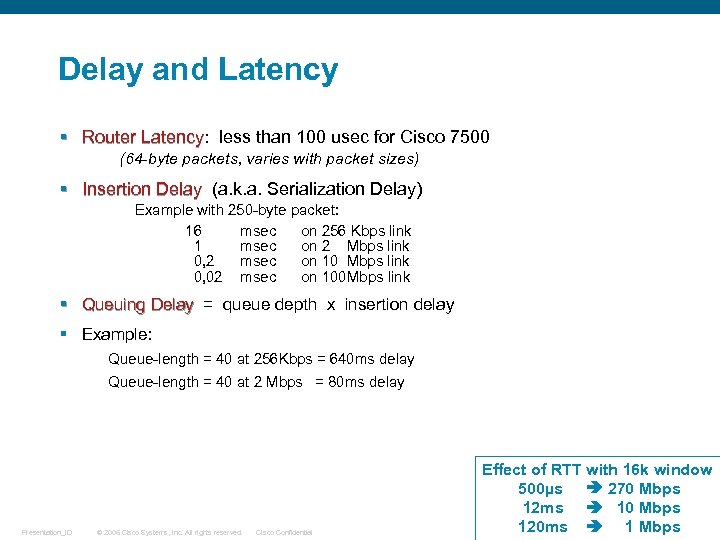
Delay and Latency § Router Latency: less than 100 usec for Cisco 7500 Router Latency (64 -byte packets, varies with packet sizes) § Insertion Delay (a. k. a. Serialization Delay) Insertion Delay Example with 250 -byte packet: 16 msec on 256 Kbps link 1 msec on 2 Mbps link 0, 2 msec on 10 Mbps link 0, 02 msec on 100 Mbps link § Queuing Delay = queue depth x insertion delay § Example: Queue-length = 40 at 256 Kbps = 640 ms delay Queue-length = 40 at 2 Mbps = 80 ms delay Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Effect of RTT with 16 k window 500µs 270 Mbps 12 ms 10 Mbps 120 ms 1 Mbps 42
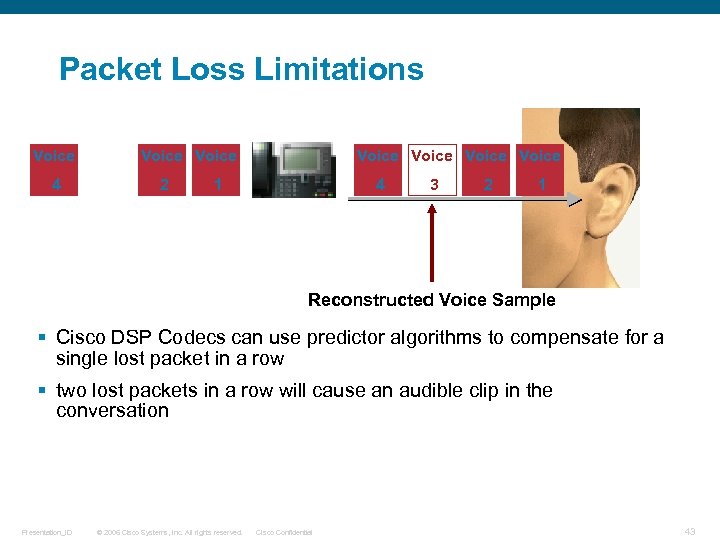
Packet Loss Limitations Voice 4 3 2 Voice 1 4 3 2 1 Voice 3 Reconstructed Voice Sample § Cisco DSP Codecs can use predictor algorithms to compensate for a single lost packet in a row § two lost packets in a row will cause an audible clip in the conversation Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 43
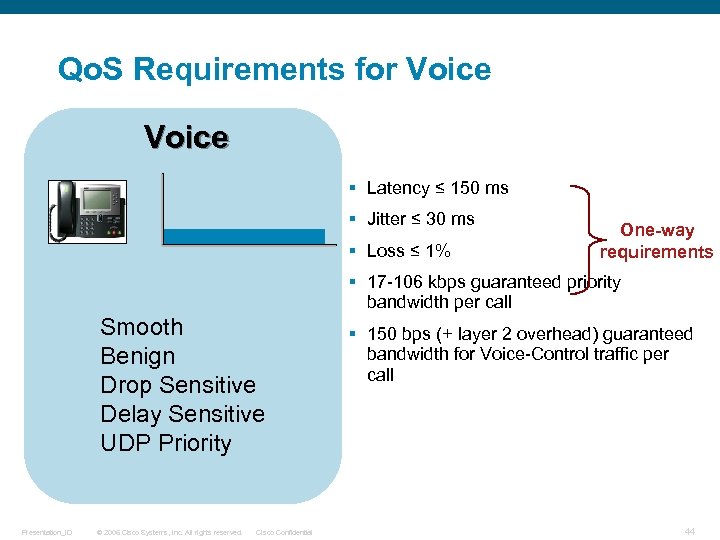
Qo. S Requirements for Voice § Latency ≤ 150 ms § Jitter ≤ 30 ms § Loss ≤ 1% One-way requirements § 17 -106 kbps guaranteed priority bandwidth per call Smooth Benign Drop Sensitive Delay Sensitive UDP Priority Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential § 150 bps (+ layer 2 overhead) guaranteed bandwidth for Voice-Control traffic per call 44
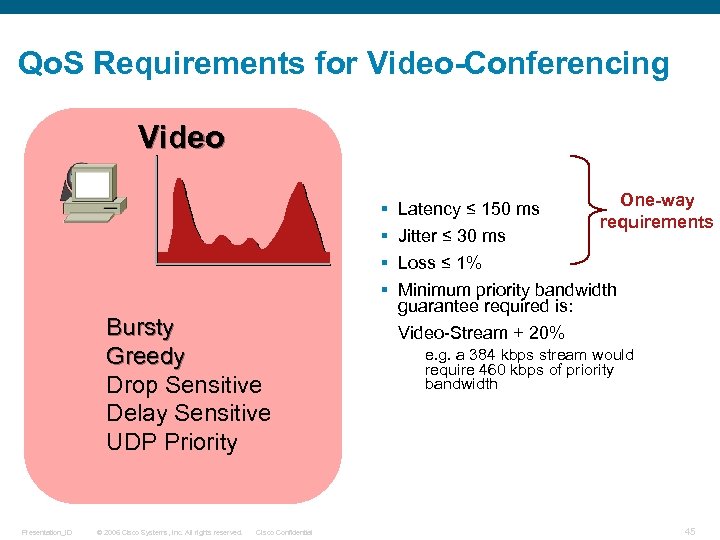
Qo. S Requirements for Video-Conferencing Video § § Bursty Greedy Drop Sensitive Delay Sensitive UDP Priority Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Latency ≤ 150 ms Jitter ≤ 30 ms Loss ≤ 1% One-way requirements Minimum priority bandwidth guarantee required is: Video-Stream + 20% e. g. a 384 kbps stream would require 460 kbps of priority bandwidth 45
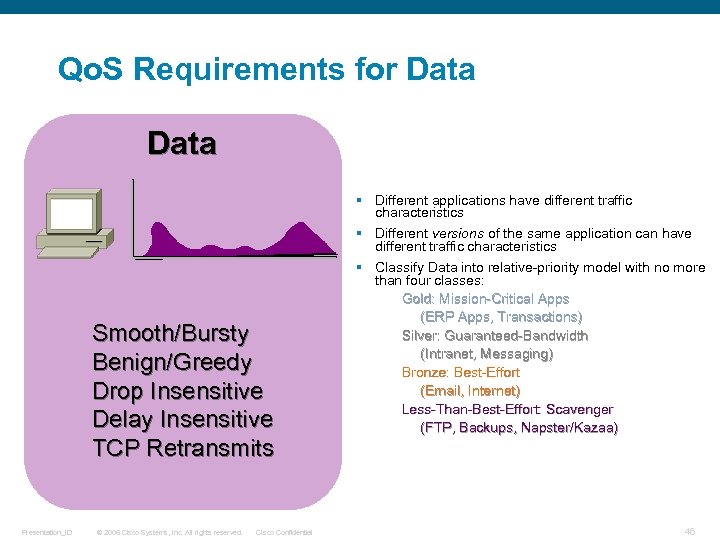
Qo. S Requirements for Data Smooth/Bursty Benign/Greedy Drop Insensitive Delay Insensitive TCP Retransmits Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential § Different applications have different traffic characteristics § Different versions of the same application can have different traffic characteristics § Classify Data into relative-priority model with no more than four classes: Gold: Mission-Critical Apps (ERP Apps, Transactions) Silver: Guaranteed-Bandwidth (Intranet, Messaging) Bronze: Best-Effort (Email, Internet) Less-Than-Best-Effort: Scavenger (FTP, Backups, Napster/Kazaa) 46
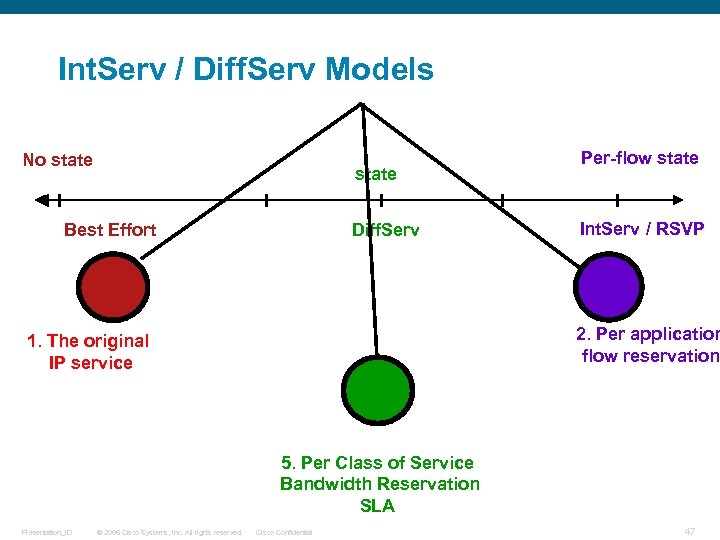
Int. Serv / Diff. Serv Models No state Best Effort Diff. Serv Per-flow state Int. Serv / RSVP 2. Per application flow reservation 1. The original IP service 5. Per Class of Service Bandwidth Reservation SLA Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 47
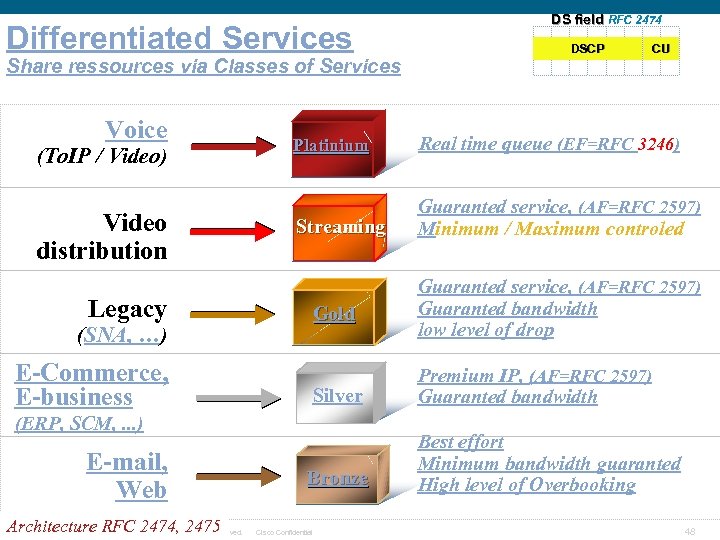
Differentiated Services Share ressources via Classes of Services Voice (To. IP / Video) Video distribution Streaming Guaranted service, (AF=RFC 2597) Minimum / Maximum controled Gold Guaranted service, (AF=RFC 2597) Guaranted bandwidth low level of drop Silver Premium IP, (AF=RFC 2597) Guaranted bandwidth Bronze Best effort Minimum bandwidth guaranted High level of Overbooking (ERP, SCM, . . . ) Architecture RFC 2474, 2475 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. CU Real time queue (EF=RFC 3246) (SNA, …) E-mail, Web DSCP Platinium Legacy E-Commerce, E-business DS field RFC 2474 Cisco Confidential 48
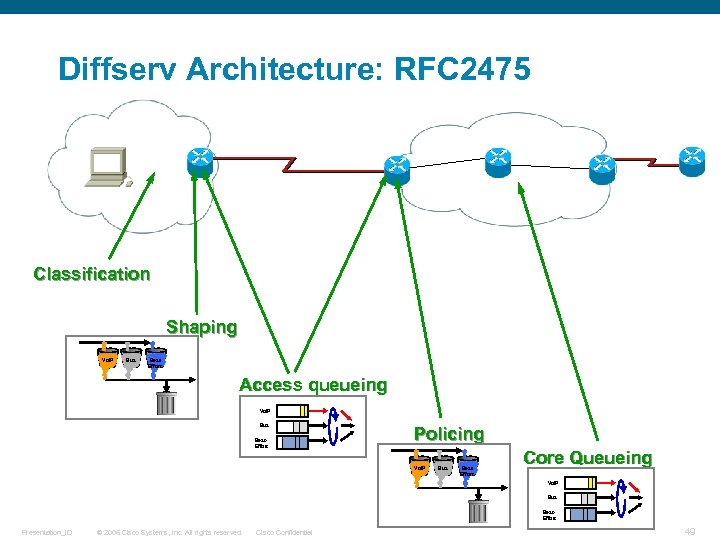
Diffserv Architecture: RFC 2475 Classification Shaping Vo. IP Bus Best. Effort Access queueing Vo. IP Bus Best. Effort Policing Vo. IP Bus Best. Effort Core Queueing Vo. IP Bus Best. Effort Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 49
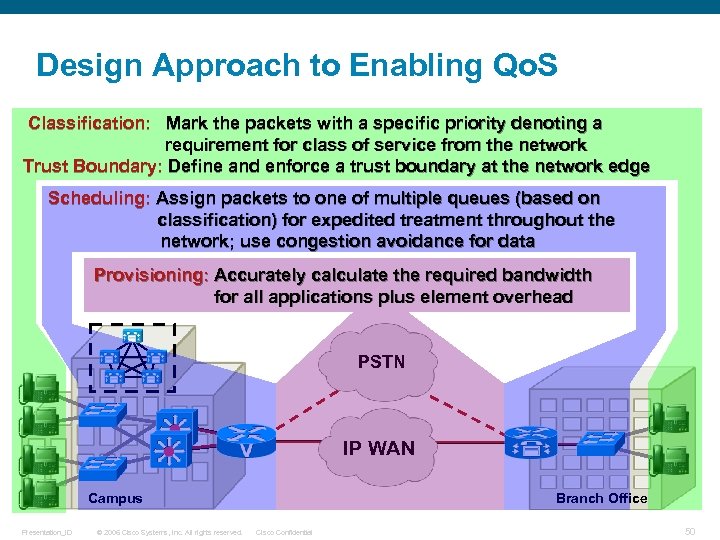
Design Approach to Enabling Qo. S Classification: Mark the packets with a specific priority denoting a requirement for class of service from the network Trust Boundary: Define and enforce a trust boundary at the network edge Scheduling: Assign packets to one of multiple queues (based on classification) for expedited treatment throughout the network; use congestion avoidance for data Provisioning: Accurately calculate the required bandwidth for all applications plus element overhead PSTN IP WAN Branch Office Campus Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 50
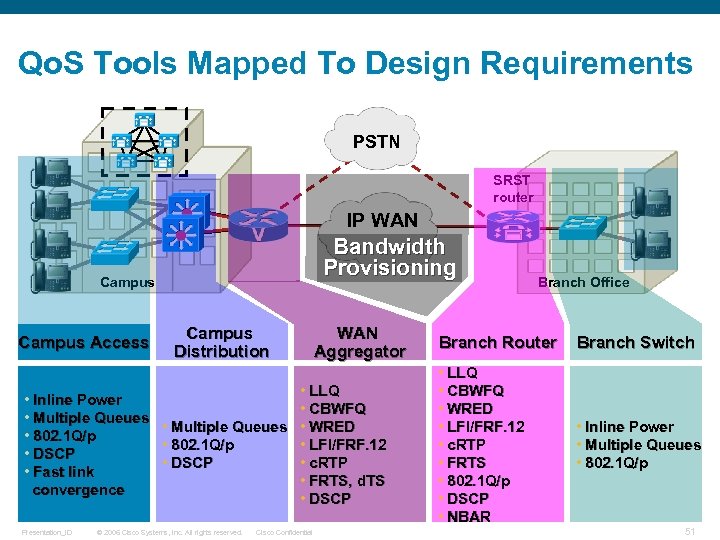
Qo. S Tools Mapped To Design Requirements PSTN SRST router IP WAN Bandwidth Provisioning Campus Access • Inline Power • Multiple Queues • 802. 1 Q/p • DSCP • Fast link convergence Presentation_ID Campus Distribution WAN Aggregator • LLQ • CBWFQ • Multiple Queues • WRED • 802. 1 Q/p • LFI/FRF. 12 • DSCP • c. RTP • FRTS, d. TS • DSCP © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Branch Office Branch Router Branch Switch • LLQ • CBWFQ • WRED • LFI/FRF. 12 • c. RTP • FRTS • 802. 1 Q/p • DSCP • NBAR • Inline Power • Multiple Queues • 802. 1 Q/p 51

Qo. S Toolset § Classification § Policing / Shaping § Scheduling / Queueing § Congestion Avoidance Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 52
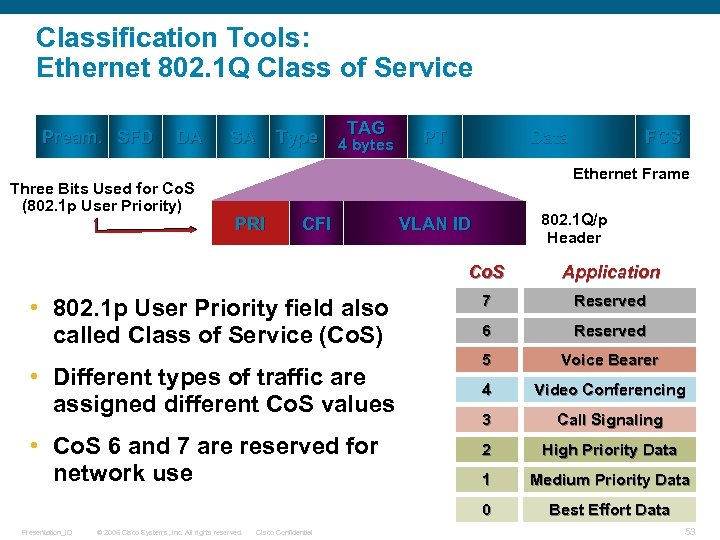
Classification Tools: Ethernet 802. 1 Q Class of Service Pream. SFD DA Three Bits Used for Co. S (802. 1 p User Priority) Type SA TAG 4 bytes PT Data FCS Ethernet Frame PRI CFI 802. 1 Q/p Header VLAN ID Co. S • Different types of traffic are assigned different Co. S values • Co. S 6 and 7 are reserved for network use Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 7 Reserved 6 Reserved 5 Voice Bearer 4 Video Conferencing 3 Call Signaling 2 High Priority Data 1 Medium Priority Data 0 • 802. 1 p User Priority field also called Class of Service (Co. S) Application Best Effort Data 53
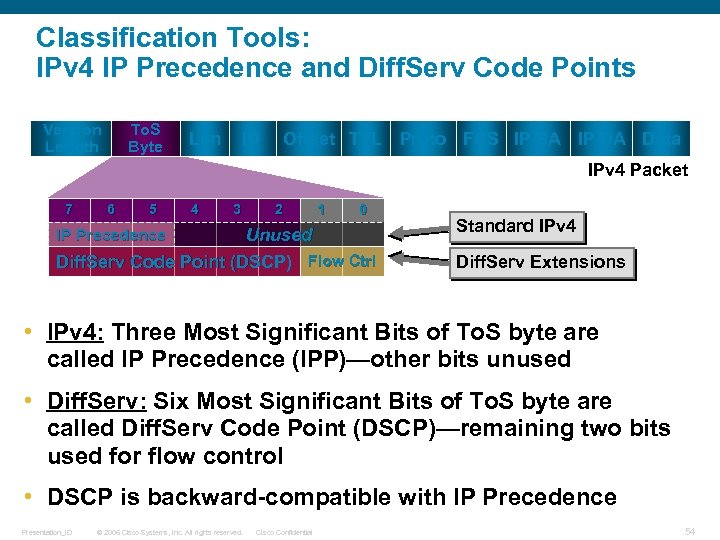
Classification Tools: IPv 4 IP Precedence and Diff. Serv Code Points To. S Byte Version Length Len ID Offset TTL Proto FCS IP SA IP DA Data IPv 4 Packet 7 6 5 4 3 2 1 0 Unused Diff. Serv Code Point (DSCP) Flow Ctrl IP Precedence Standard IPv 4 Diff. Serv Extensions • IPv 4: Three Most Significant Bits of To. S byte are called IP Precedence (IPP)—other bits unused • Diff. Serv: Six Most Significant Bits of To. S byte are called Diff. Serv Code Point (DSCP)—remaining two bits used for flow control • DSCP is backward-compatible with IP Precedence Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 54
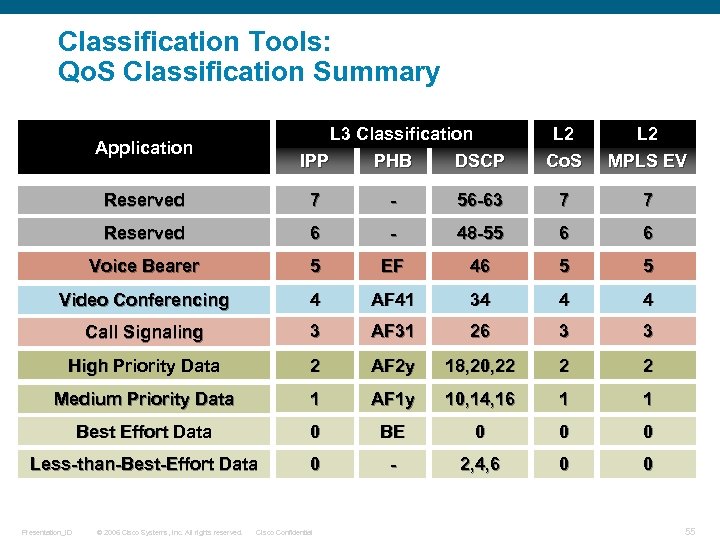
Classification Tools: Qo. S Classification Summary L 3 Classification IPP PHB DSCP Application L 2 Co. S L 2 MPLS EV Reserved 7 - 56 -63 7 7 Reserved 6 - 48 -55 6 6 Voice Bearer 5 EF 46 5 5 Video Conferencing 4 AF 41 34 4 4 Call Signaling 3 AF 31 26 3 3 High Priority Data 2 AF 2 y 18, 20, 22 2 2 Medium Priority Data 1 AF 1 y 10, 14, 16 1 1 Best Effort Data 0 BE 0 0 0 Less-than-Best-Effort Data 0 - 2, 4, 6 0 0 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 55
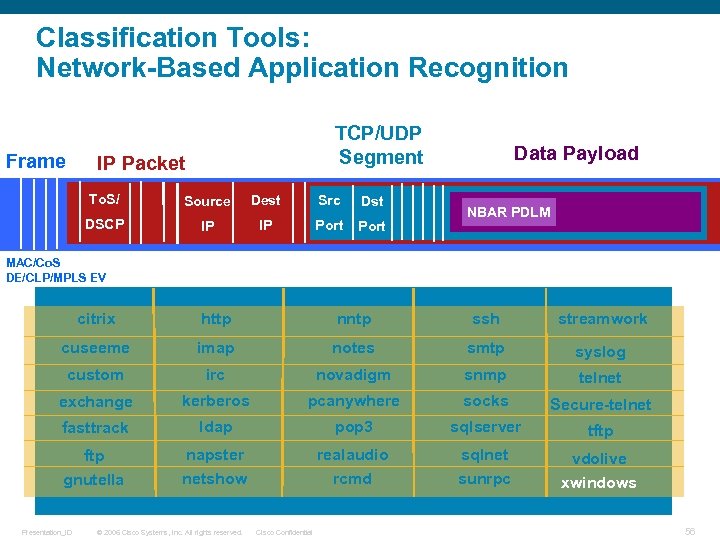
Classification Tools: Network-Based Application Recognition Frame TCP/UDP Segment IP Packet To. S/ Source Dest Src Dst DSCP IP IP Port Data Payload NBAR PDLM DATA MAC/Co. S DE/CLP/MPLS EV citrix http nntp ssh streamwork cuseeme imap notes smtp syslog custom irc novadigm snmp telnet exchange kerberos pcanywhere socks Secure-telnet fasttrack ldap pop 3 sqlserver tftp gnutella napster realaudio sqlnet netshow rcmd sunrpc vdolive xwindows Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 56
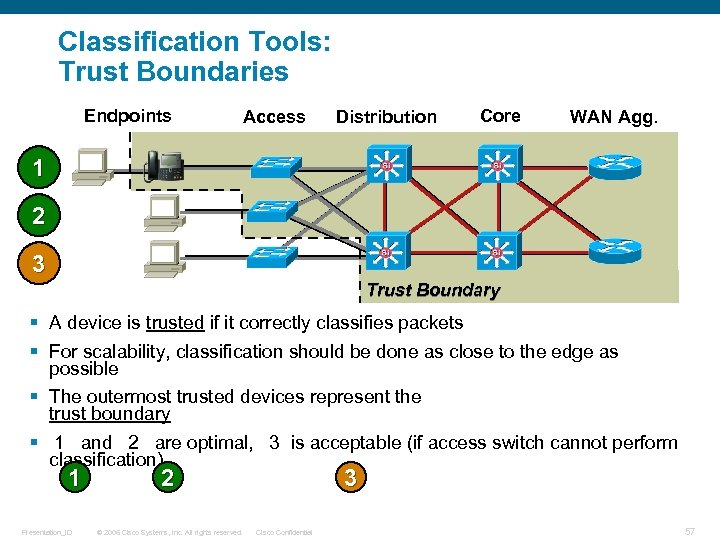
Classification Tools: Trust Boundaries Endpoints Access Distribution Core WAN Agg. 1 2 3 Trust Boundary § A device is trusted if it correctly classifies packets § For scalability, classification should be done as close to the edge as possible § The outermost trusted devices represent the trust boundary § 1 and 2 are optimal, 3 is acceptable (if access switch cannot perform classification) 1 Presentation_ID 2 © 2006 Cisco Systems, Inc. All rights reserved. 3 Cisco Confidential 57
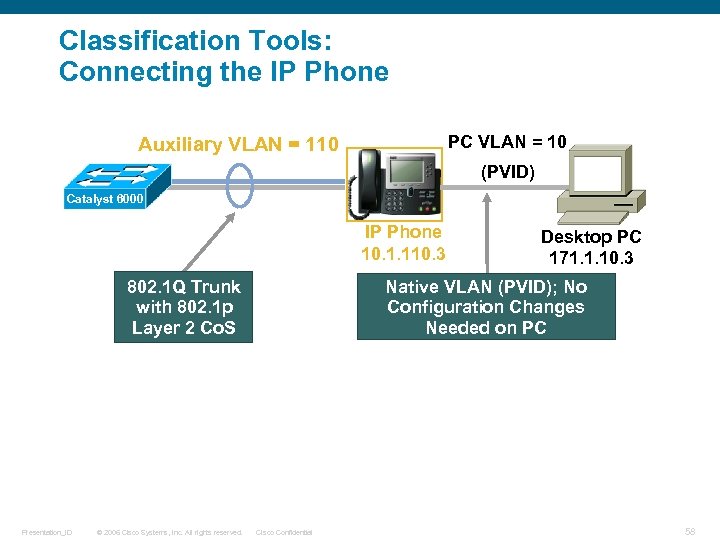
Classification Tools: Connecting the IP Phone PC VLAN = 10 Auxiliary VLAN = 110 (PVID) Catalyst 6000 IP Phone 10. 1. 110. 3 802. 1 Q Trunk with 802. 1 p Layer 2 Co. S Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Desktop PC 171. 1. 10. 3 Native VLAN (PVID); No Configuration Changes Needed on PC Cisco Confidential 58
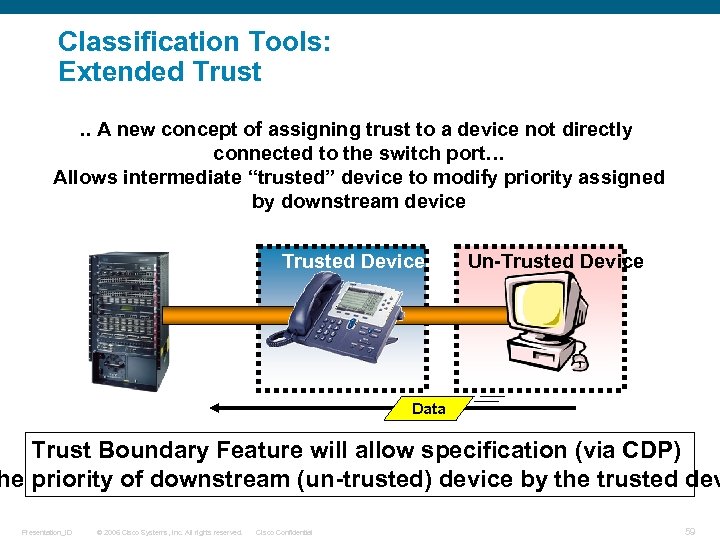
Classification Tools: Extended Trust. . A new concept of assigning trust to a device not directly connected to the switch port… Allows intermediate “trusted” device to modify priority assigned by downstream device Trusted Device Un-Trusted Device Data Trust Boundary Feature will allow specification (via CDP) he priority of downstream (un-trusted) device by the trusted dev Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 59
Classification Tools: PC Co. S Settings Are Not Trusted Co. S=5 Co. S=0 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 60
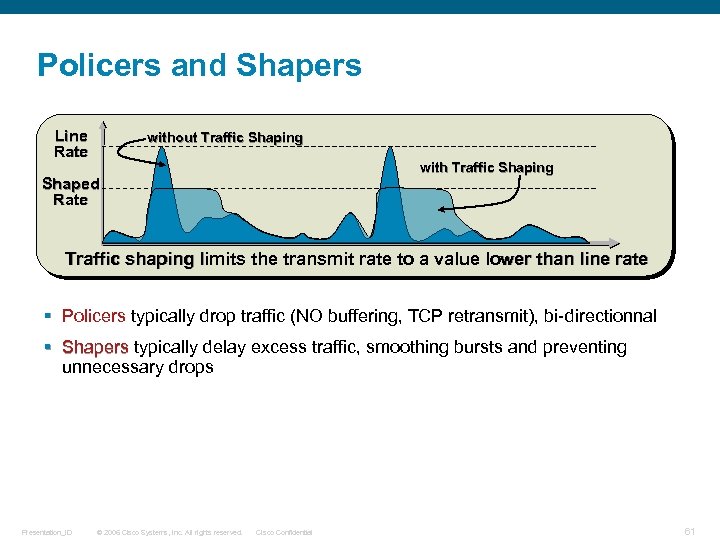
Policers and Shapers Line Rate without Traffic Shaping with Traffic Shaping Shaped Rate Traffic shaping limits the transmit rate to a value lower than line rate § Policers typically drop traffic (NO buffering, TCP retransmit), bi-directionnal Policers § Shapers typically delay excess traffic, smoothing bursts and preventing Shapers unnecessary drops Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 61
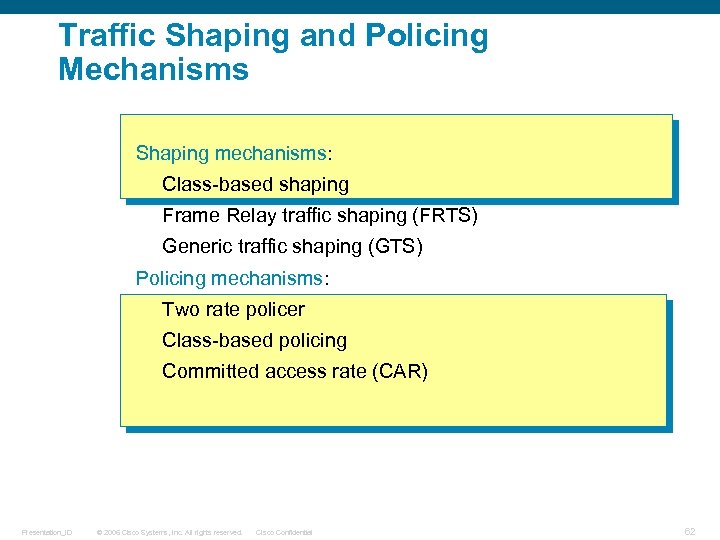
Traffic Shaping and Policing Mechanisms Shaping mechanisms: Class-based shaping Frame Relay traffic shaping (FRTS) Generic traffic shaping (GTS) Policing mechanisms: Two rate policer Class-based policing Committed access rate (CAR) Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 62
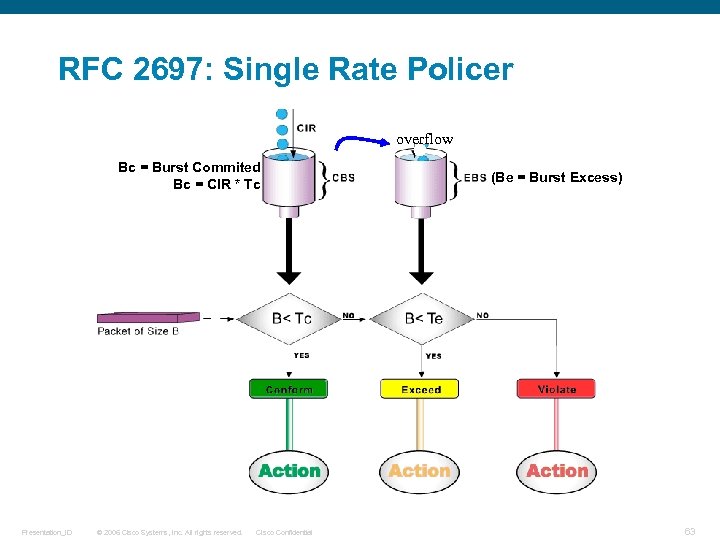
RFC 2697: Single Rate Policer overflow Bc = Burst Commited Bc = CIR * Tc Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential (Be = Burst Excess) 63
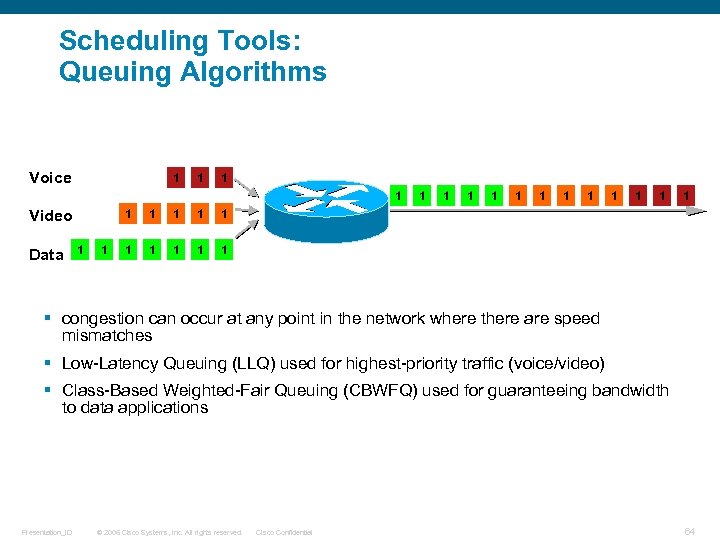
Scheduling Tools: Queuing Algorithms Voice 1 1 1 Video Data 1 1 1 1 1 2 12 1 3 3 13 1 § congestion can occur at any point in the network where there are speed mismatches § Low-Latency Queuing (LLQ) used for highest-priority traffic (voice/video) § Class-Based Weighted-Fair Queuing (CBWFQ) used for guaranteeing bandwidth to data applications Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 64
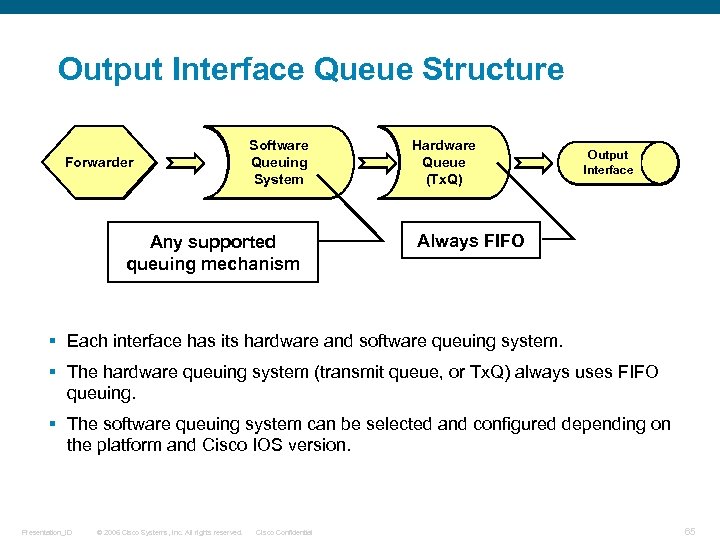
Output Interface Queue Structure Forwarder Software Queuing System Any supported queuing mechanism Hardware Queue (Tx. Q) Output Interface Always FIFO § Each interface has its hardware and software queuing system. § The hardware queuing system (transmit queue, or Tx. Q) always uses FIFO queuing. § The software queuing system can be selected and configured depending on the platform and Cisco IOS version. Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 65
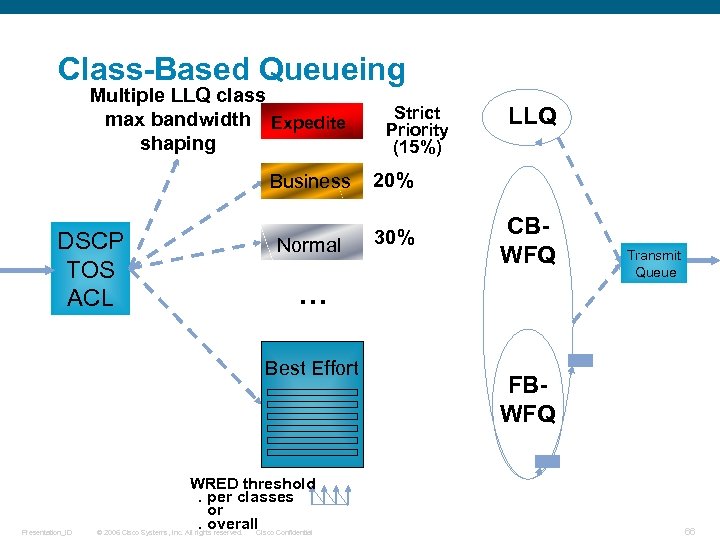
Class-Based Queueing Multiple LLQ class max bandwidth Expedite shaping Strict Priority (15%) Business DSCP TOS ACL 20% Normal 30% CBWFQ . . . Best Effort Presentation_ID LLQ WRED threshold. per classes or. overall. Cisco Confidential © 2006 Cisco Systems, Inc. All rights reserved. Transmit Queue FBWFQ 66
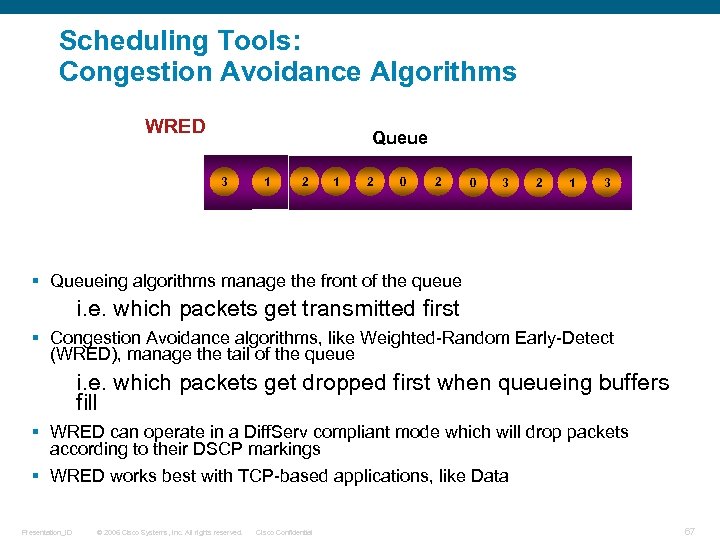
Scheduling Tools: Congestion Avoidance Algorithms TAIL DROP WRED 3 31 3 Queue 1 00 2 1 2 0 3 2 1 3 0 0 § Queueing algorithms manage the front of the queue 3 i. e. which packets get transmitted first § Congestion Avoidance algorithms, like Weighted-Random Early-Detect (WRED), manage the tail of the queue i. e. which packets get dropped first when queueing buffers fill § WRED can operate in a Diff. Serv compliant mode which will drop packets according to their DSCP markings § WRED works best with TCP-based applications, like Data Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 67
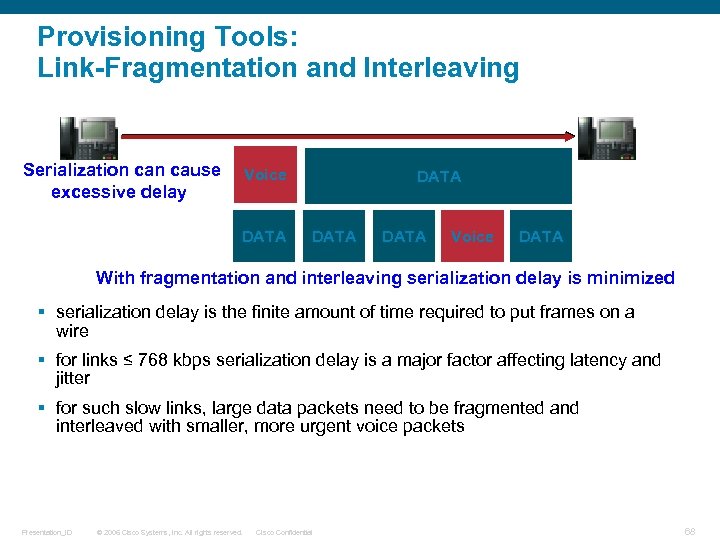
Provisioning Tools: Link-Fragmentation and Interleaving Serialization cause excessive delay Voice DATA Voice DATA With fragmentation and interleaving serialization delay is minimized § serialization delay is the finite amount of time required to put frames on a wire § for links ≤ 768 kbps serialization delay is a major factor affecting latency and jitter § for such slow links, large data packets need to be fragmented and interleaved with smaller, more urgent voice packets Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 68
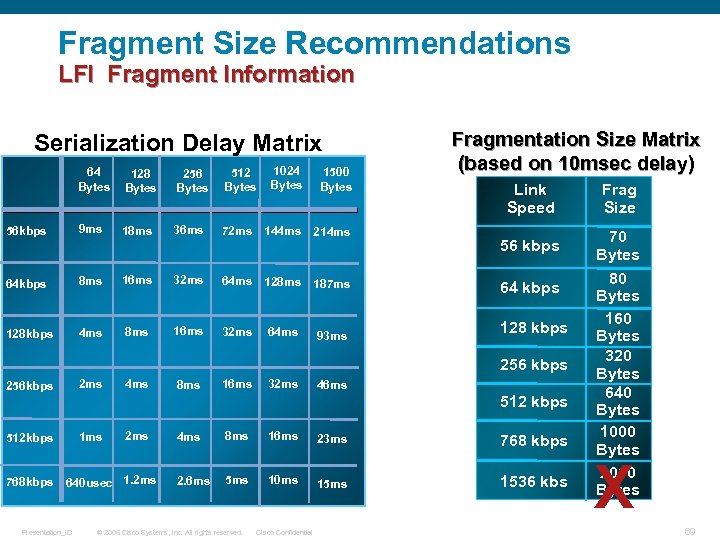
Fragment Size Recommendations LFI Fragment Information Serialization Delay Matrix 1024 Bytes 64 Bytes 128 Bytes 256 Bytes 512 Bytes 56 kbps 9 ms 18 ms 36 ms 72 ms 144 ms 214 ms 64 kbps 8 ms 16 ms 32 ms 64 ms 128 ms 187 ms 128 kbps 4 ms 8 ms 16 ms 32 ms 64 ms 1500 Bytes 93 ms Fragmentation Size Matrix (based on 10 msec delay) Link Speed Frag Size 56 kbps 70 Bytes 64 kbps 128 kbps 256 kbps 2 ms 512 kbps 1 ms 4 ms 16 ms 32 ms 46 ms 512 kbps 2 ms 768 kbps 640 usec 1. 2 ms Presentation_ID 8 ms 4 ms 8 ms 16 ms 23 ms 768 kbps 2. 6 ms 5 ms 10 ms 1536 kbs © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 80 Bytes 160 Bytes 320 Bytes 640 Bytes 1000 Bytes 2000 Bytes X 69
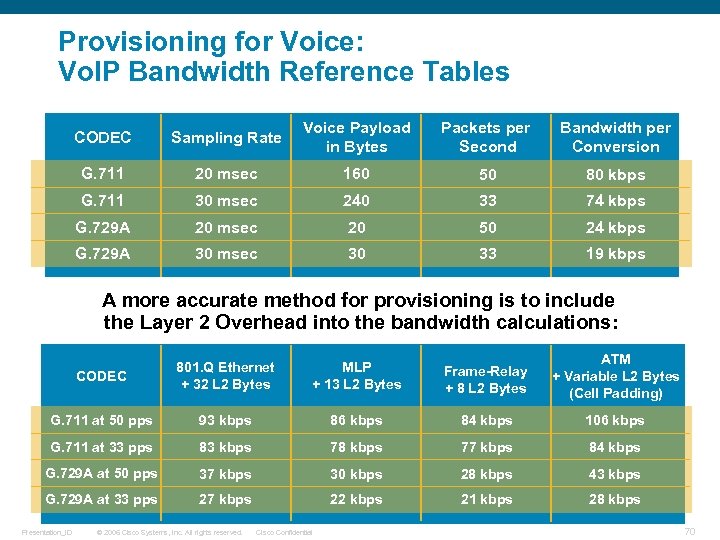
Provisioning for Voice: Vo. IP Bandwidth Reference Tables CODEC Sampling Rate Voice Payload in Bytes Packets per Second Bandwidth per Conversion G. 711 20 msec 160 50 80 kbps G. 711 30 msec 240 33 74 kbps G. 729 A 20 msec 20 50 24 kbps G. 729 A 30 msec 30 33 19 kbps A more accurate method for provisioning is to include the Layer 2 Overhead into the bandwidth calculations: CODEC 801. Q Ethernet + 32 L 2 Bytes MLP + 13 L 2 Bytes Frame-Relay + 8 L 2 Bytes ATM + Variable L 2 Bytes (Cell Padding) G. 711 at 50 pps 93 kbps 86 kbps 84 kbps 106 kbps G. 711 at 33 pps 83 kbps 78 kbps 77 kbps 84 kbps G. 729 A at 50 pps 37 kbps 30 kbps 28 kbps 43 kbps G. 729 A at 33 pps 27 kbps 22 kbps 21 kbps 28 kbps Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 70
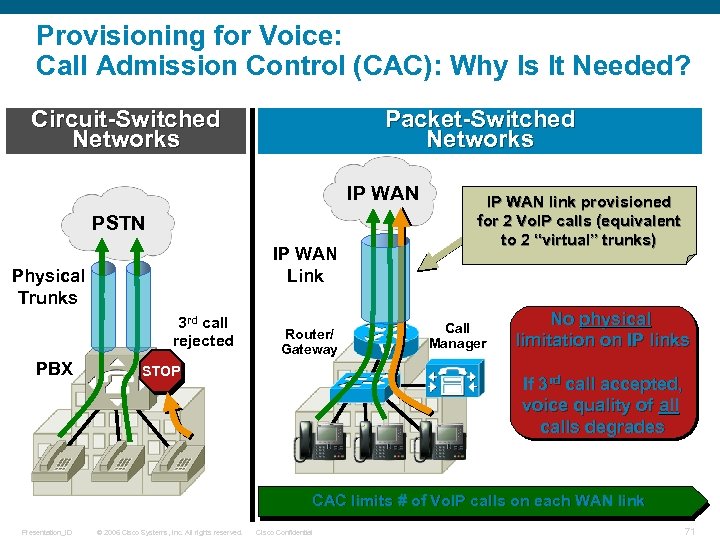
Provisioning for Voice: Call Admission Control (CAC): Why Is It Needed? Circuit-Switched Networks Packet-Switched Networks IP WAN PSTN IP WAN Link Physical Trunks 3 rd call rejected PBX Router/ Gateway STOP IP WAN link provisioned for 2 Vo. IP calls (equivalent to 2 “virtual” trunks) Call Manager No physical limitation on IP links If 3 rd call accepted, voice quality of all calls degrades CAC limits # of Vo. IP calls on each WAN link Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 71
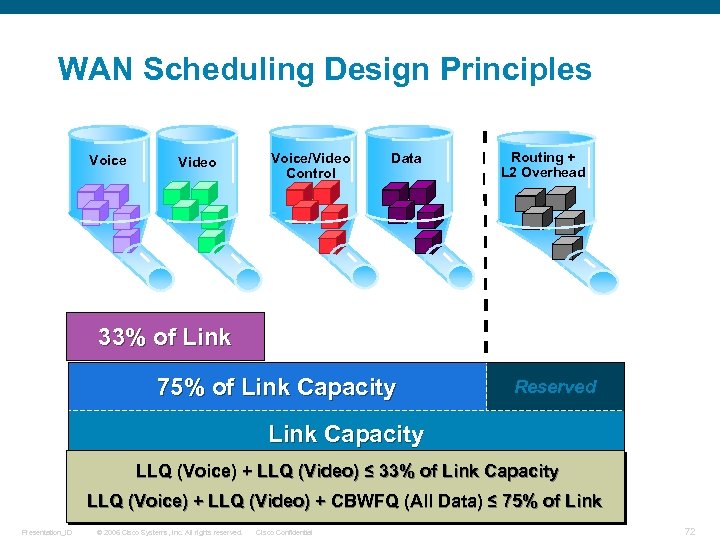
WAN Scheduling Design Principles Voice Video Voice/Video Control Data Routing + L 2 Overhead 33% of Link 75% of Link Capacity Reserved Link Capacity LLQ (Voice) + LLQ (Video) ≤ 33% of Link Capacity LLQ (Voice) + LLQ (Video) + CBWFQ (All Data) ≤ 75% of Link Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 72
Management Tools § Qo. S is efficiently scaled with a centralized management server § Qo. S deployment is best followed by ongoing monitoring to ensure that targeted service-levels are being provided § Qo. S policies need periodic tuning to adjust to changing business needs Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 73
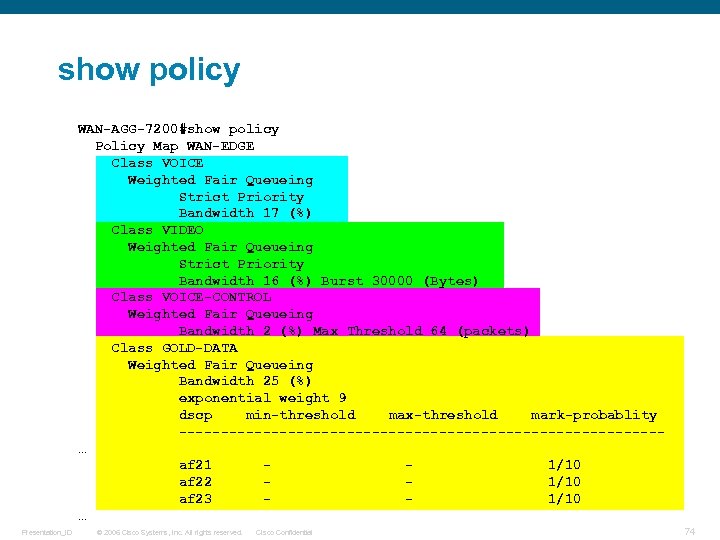
show policy WAN-AGG-7200#show policy Policy Map WAN-EDGE Class VOICE Weighted Fair Queueing Strict Priority Bandwidth 17 (%) Class VIDEO Weighted Fair Queueing Strict Priority Bandwidth 16 (%) Burst 30000 (Bytes) Class VOICE-CONTROL Weighted Fair Queueing Bandwidth 2 (%) Max Threshold 64 (packets) Class GOLD-DATA Weighted Fair Queueing Bandwidth 25 (%) exponential weight 9 dscp min-threshold max-threshold mark-probablity -----------------------------… af 21 1/10 af 22 1/10 af 23 1/10 … Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 74
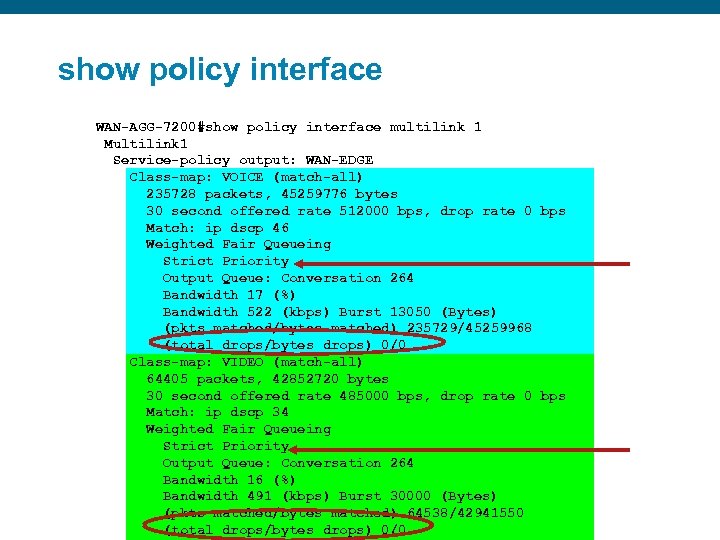
show policy interface Presentation_ID WAN-AGG-7200#show policy interface multilink 1 Multilink 1 Service-policy output: WAN-EDGE Class-map: VOICE (match-all) 235728 packets, 45259776 bytes 30 second offered rate 512000 bps, drop rate 0 bps Match: ip dscp 46 Weighted Fair Queueing Strict Priority Output Queue: Conversation 264 Bandwidth 17 (%) Bandwidth 522 (kbps) Burst 13050 (Bytes) (pkts matched/bytes matched) 235729/45259968 (total drops/bytes drops) 0/0 Class-map: VIDEO (match-all) 64405 packets, 42852720 bytes 30 second offered rate 485000 bps, drop rate 0 bps Match: ip dscp 34 Weighted Fair Queueing Strict Priority Output Queue: Conversation 264 Bandwidth 16 (%) Bandwidth 491 (kbps) Burst 30000 (Bytes) (pkts matched/bytes matched) 64538/42941550 (total drops/bytes drops) 0/0 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 75
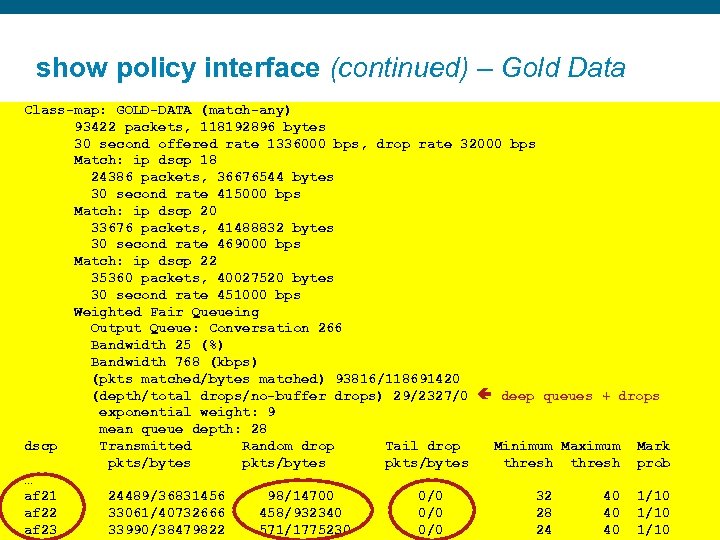
show policy interface (continued) – Gold Data Class-map: GOLD-DATA (match-any) 93422 packets, 118192896 bytes 30 second offered rate 1336000 bps, drop rate 32000 bps Match: ip dscp 18 24386 packets, 36676544 bytes 30 second rate 415000 bps Match: ip dscp 20 33676 packets, 41488832 bytes 30 second rate 469000 bps Match: ip dscp 22 35360 packets, 40027520 bytes 30 second rate 451000 bps Weighted Fair Queueing Output Queue: Conversation 266 Bandwidth 25 (%) Bandwidth 768 (kbps) (pkts matched/bytes matched) 93816/118691420 (depth/total drops/no-buffer drops) 29/2327/0 deep queues + drops exponential weight: 9 mean queue depth: 28 dscp Transmitted Random drop Tail drop Minimum Maximum Mark pkts/bytes thresh prob … af 21 24489/36831456 98/14700 0/0 32 40 1/10 af 22 33061/40732666 458/932340 0/0 28 40 1/10 af 23 33990/38479822 571/1775230 0/0 24 40 1/10 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 76

Un élément CLE : L’administration du réseau § Objectifs 1. Faciliter la configuration des équipements – Management embarqué – Déploiement à grande échelle 2. Gérer les SLA 3. Apporter la visibilité : instrumentation NBAR, Netflow § Moyens 1. L’instrumentation : – SLA : IOS IPSLA , CBQOS, Corvi. L – Visibilité : NBAR, Netflow, RMON 2 et extensions 2. Les outils intégrés 3. Plateformes logicielles Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 77
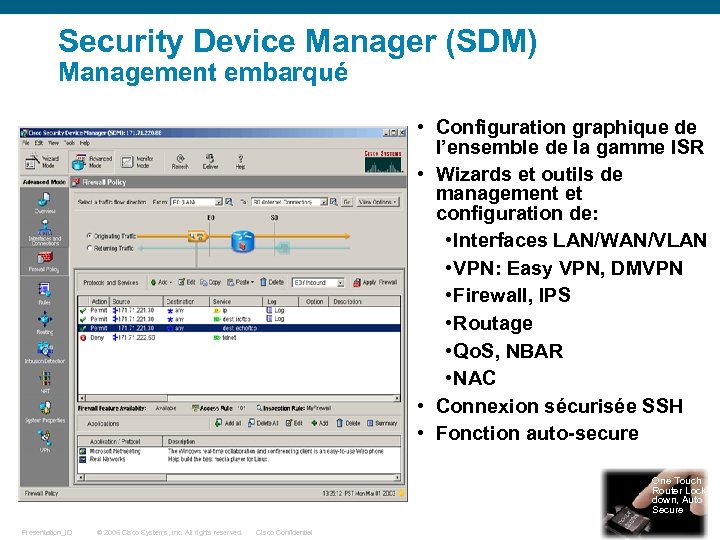
Security Device Manager (SDM) Management embarqué • Configuration graphique de l’ensemble de la gamme ISR • Wizards et outils de management et configuration de: • Interfaces LAN/WAN/VLAN • VPN: Easy VPN, DMVPN • Firewall, IPS • Routage • Qo. S, NBAR • NAC • Connexion sécurisée SSH • Fonction auto-secure One Touch Router Lockdown, Auto Secure Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 78

Déploiement à grande échelle Agents CNS et CNS configuration Engine § Cisco Configuration Engine Solution de configuration et provisionning réseau supportant jusqu’à 5000 CPE Cisco par appliance. Communications sécurisées entre les agents CNS embarqués dans l’IOS des devices et le Configuration Engine. § Distribution des upgrades ou de modifications sur un parc de routeurs Cisco ISR quelque soit la technologie d’accès. § Application embarquée (GUI web) § Technologie flexible pour génération de template de configuration (Velocity template) § Interface de programmation XML-SOAP et Java/C++ based Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 79
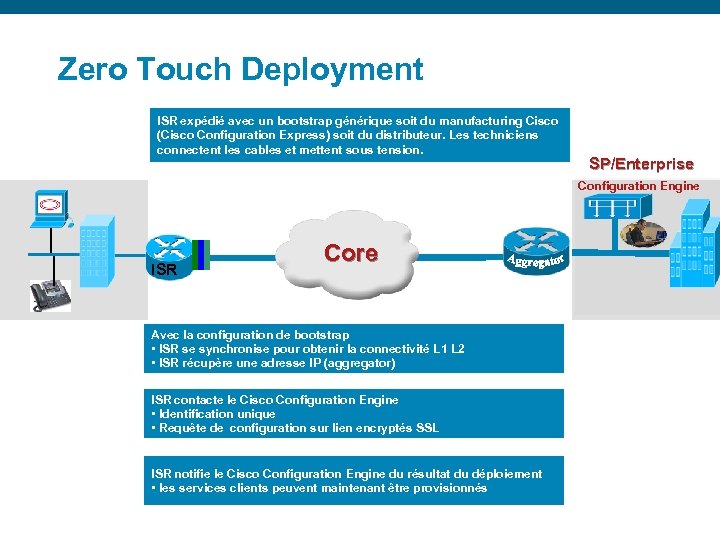
Zero Touch Deployment ISR expédié avec un bootstrap générique soit du manufacturing Cisco (Cisco Configuration Express) soit du distributeur. Les techniciens connectent les cables et mettent sous tension. SP/Enterprise Configuration Engine Core ISR Avec la configuration de bootstrap • ISR se synchronise pour obtenir la connectivité L 1 L 2 • ISR récupère une adresse IP (aggregator) ISR contacte le Cisco Configuration Engine • Identification unique • Requête de configuration sur lien encryptés SSL ISR notifie le Cisco Configuration Engine du résultat du déploiement • les services clients peuvent maintenant être provisionnés Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 80

Gestion des SLAs Enterprise and Small/Medium Business Understand Network Performance and Ease Deployment Verify Service Levels Verify Outsourced SLAs § Métriques Disponibilité Mean Time to diagnose (MTD) Mean Time To Repair (MTTR) Mean Time Between Failure (MTBF) Performance des services différenciés Bande passante Latence Perte de paquets Variation de latence(Gigue) MOS Presentation_ID Service Providers © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Measure and Provide SLAs • Process de prise en compte des anomalies • Engagements de retour à la normale • Pénalités 81
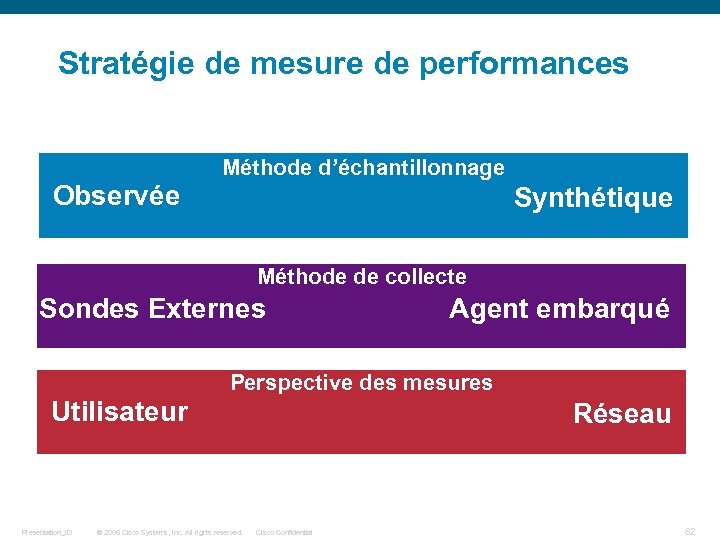
Stratégie de mesure de performances Observée Méthode d’échantillonnage Synthétique Méthode de collecte Sondes Externes Agent embarqué Perspective des mesures Utilisateur Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Réseau Cisco Confidential 82
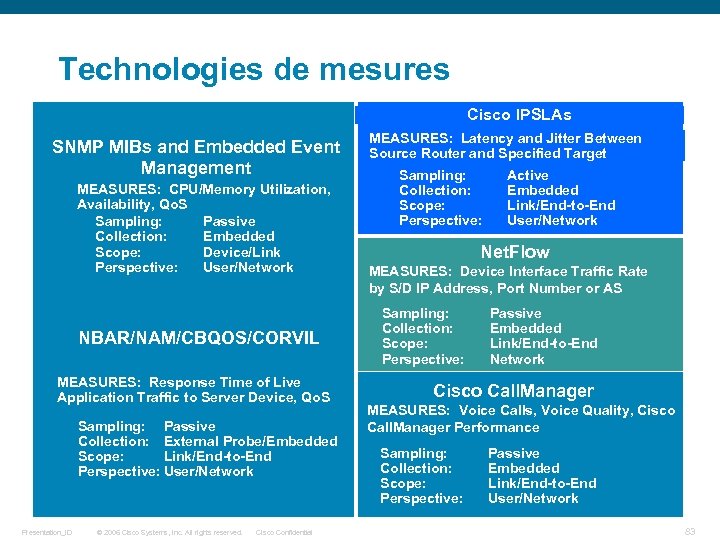
Technologies de mesures Cisco IPSLAs SNMP MIBs and Embedded Event Management MEASURES: CPU/Memory Utilization, Availability, Qo. S Sampling: Passive Collection: Embedded Scope: Device/Link Perspective: User/Network NBAR/NAM/CBQOS/CORVIL MEASURES: Response Time of Live Application Traffic to Server Device, Qo. S Sampling: Passive Collection: External Probe/Embedded Scope: Link/End-to-End Perspective: User/Network Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential MEASURES: Latency and Jitter Between Source Router and Specified Target Sampling: Collection: Scope: Perspective: Active Embedded Link/End-to-End User/Network Net. Flow MEASURES: Device Interface Traffic Rate by S/D IP Address, Port Number or AS Sampling: Collection: Scope: Perspective: Passive Embedded Link/End-to-End Network Cisco Call. Manager MEASURES: Voice Calls, Voice Quality, Cisco Call. Manager Performance Sampling: Collection: Scope: Perspective: Passive Embedded Link/End-to-End User/Network 83
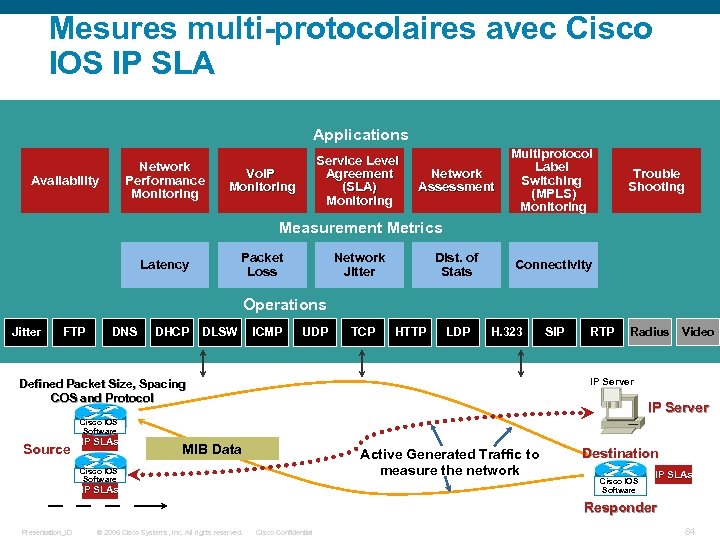
Mesures multi-protocolaires avec Cisco IOS IP SLA Applications Network Performance Monitoring Availability Service Level Agreement (SLA) Monitoring Vo. IP Monitoring Network Assessment Multiprotocol Label Switching (MPLS) Monitoring Trouble Shooting Measurement Metrics Packet Loss Latency Network Jitter Dist. of Stats Connectivity Operations Jitter FTP DNS DHCP DLSW ICMP UDP TCP HTTP LDP H. 323 SIP RTP Radius Video IP Server Defined Packet Size, Spacing COS and Protocol IP Server Cisco IOS Software Source IP SLAs MIB Data Active Generated Traffic to measure the network Cisco IOS Software IP SLAs Destination Cisco IOS Software IP SLAs Responder Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 84
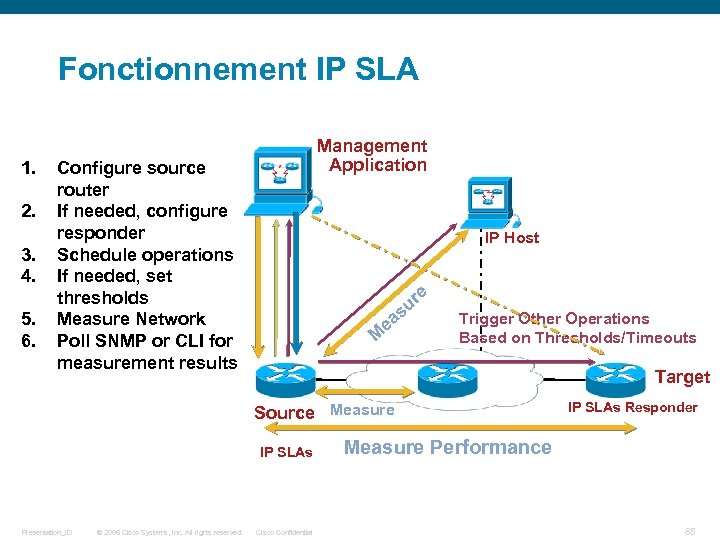
Fonctionnement IP SLA 1. 2. 3. 4. 5. 6. Management Application Configure source router If needed, configure responder Schedule operations If needed, set thresholds Measure Network Poll SNMP or CLI for measurement results IP Host e ea M r su Trigger Other Operations Based on Thresholds/Timeouts Target Source Measure IP SLAs Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential IP SLAs Responder Measure Performance 85
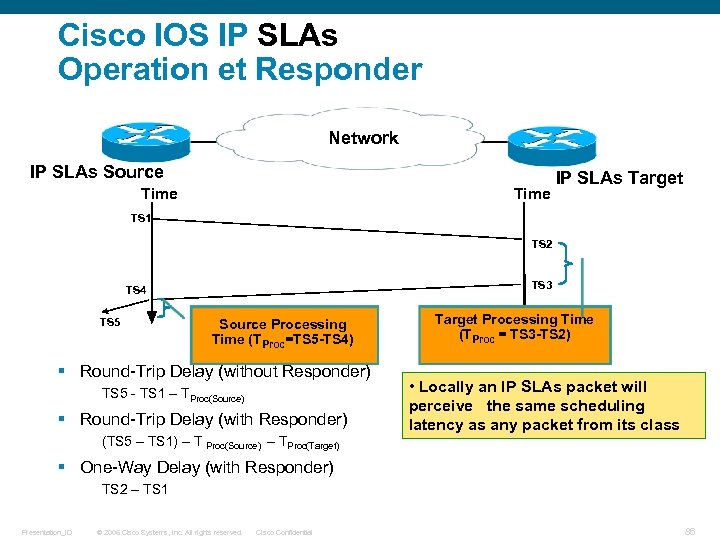
Cisco IOS IP SLAs Operation et Responder Network IP SLAs Source Time IP SLAs Target TS 1 TS 2 TS 3 TS 4 TS 5 Source Processing Time (TProc=TS 5 -TS 4) § Round-Trip Delay (without Responder) TS 5 - TS 1 – TProc(Source) § Round-Trip Delay (with Responder) (TS 5 – TS 1) – T Proc(Source) – TProc(Target) Target Processing Time (TProc = TS 3 -TS 2) • Locally an IP SLAs packet will perceive the same scheduling latency as any packet from its class § One-Way Delay (with Responder) TS 2 – TS 1 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 86
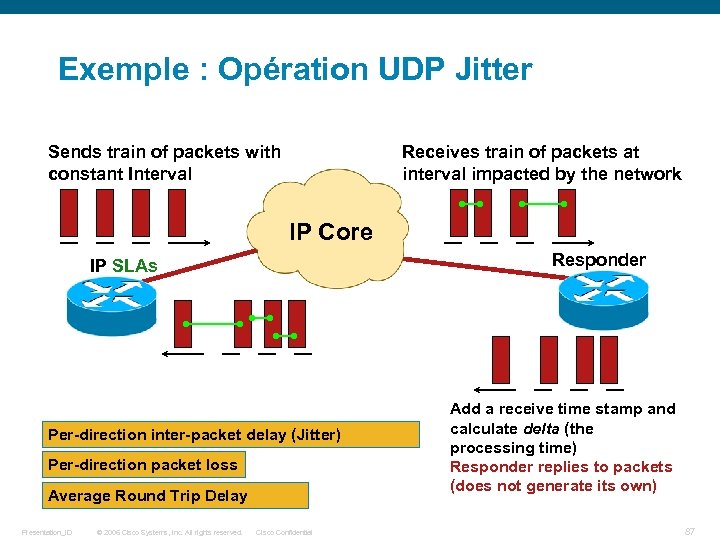
Exemple : Opération UDP Jitter Sends train of packets with constant Interval Receives train of packets at interval impacted by the network IP Core Responder IP SLAs Per-direction inter-packet delay (Jitter) Per-direction packet loss Average Round Trip Delay Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential Add a receive time stamp and calculate delta (the processing time) Responder replies to packets (does not generate its own) 87
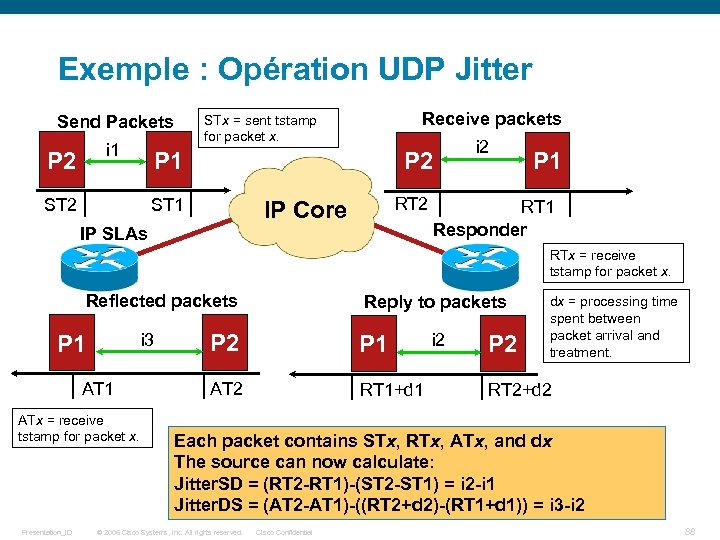
Exemple : Opération UDP Jitter Send Packets i 1 P 2 Receive packets STx = sent tstamp for packet x. P 1 ST 2 P 2 ST 1 RT 2 IP Core IP SLAs i 2 P 1 RT 1 Responder RTx = receive tstamp for packet x. Reflected packets i 3 P 1 ATx = receive tstamp for packet x. Presentation_ID Reply to packets P 2 P 1 AT 2 RT 1+d 1 i 2 P 2 dx = processing time spent between packet arrival and treatment. RT 2+d 2 Each packet contains STx, RTx, ATx, and dx The source can now calculate: Jitter. SD = (RT 2 -RT 1)-(ST 2 -ST 1) = i 2 -i 1 Jitter. DS = (AT 2 -AT 1)-((RT 2+d 2)-(RT 1+d 1)) = i 3 -i 2 © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 88
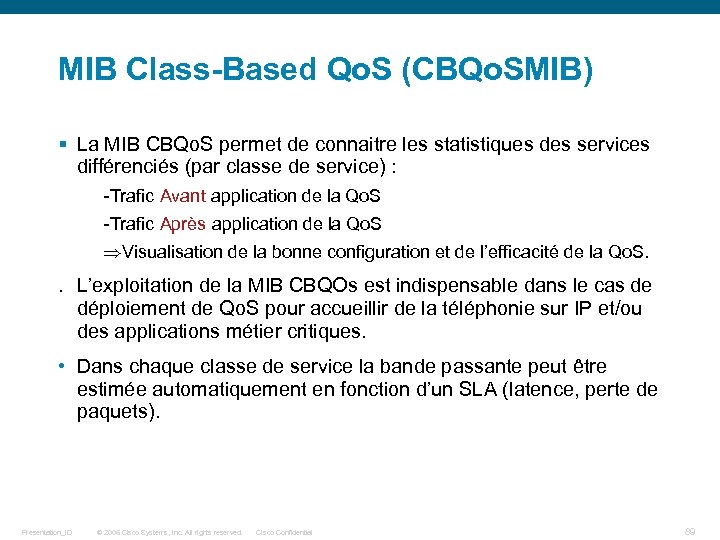
MIB Class-Based Qo. S (CBQo. SMIB) § La MIB CBQo. S permet de connaitre les statistiques des services différenciés (par classe de service) : -Trafic Avant application de la Qo. S -Trafic Après application de la Qo. S ÞVisualisation de la bonne configuration et de l’efficacité de la Qo. S. . L’exploitation de la MIB CBQOs est indispensable dans le cas de déploiement de Qo. S pour accueillir de la téléphonie sur IP et/ou des applications métier critiques. • Dans chaque classe de service la bande passante peut être estimée automatiquement en fonction d’un SLA (latence, perte de paquets). Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 89
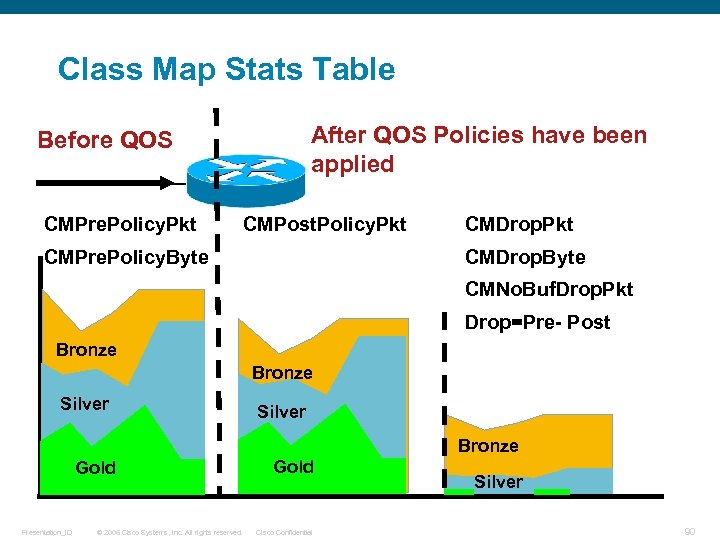
Class Map Stats Table After QOS Policies have been applied Before QOS CMPre. Policy. Pkt CMPost. Policy. Pkt CMPre. Policy. Byte CMDrop. Pkt CMDrop. Byte CMNo. Buf. Drop. Pkt Drop=Pre- Post Bronze Silver Bronze Gold Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Gold Cisco Confidential Silver 90
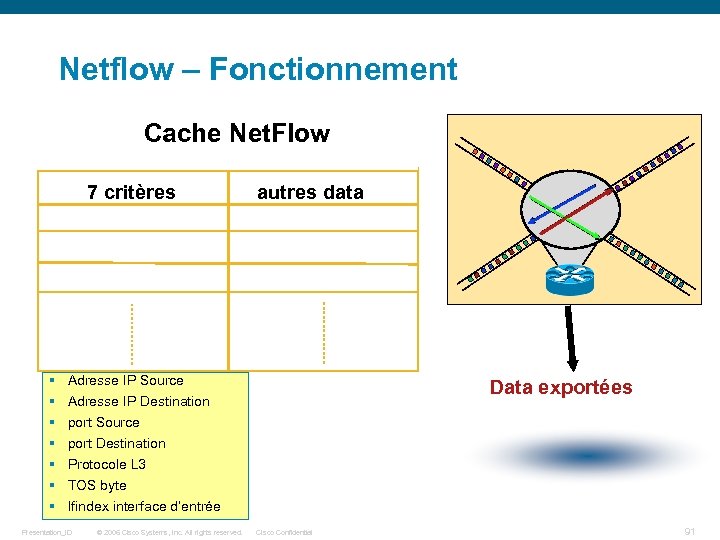
Netflow – Fonctionnement Cache Net. Flow 77 critères identifiers autres data Other data Flow identifiers Flow data Flow identifiers § § § § Flow data update Flow data Adresse IP Source Data exportées Adresse IP Destination port Source port Destination Protocole L 3 TOS byte Ifindex interface d’entrée Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 91
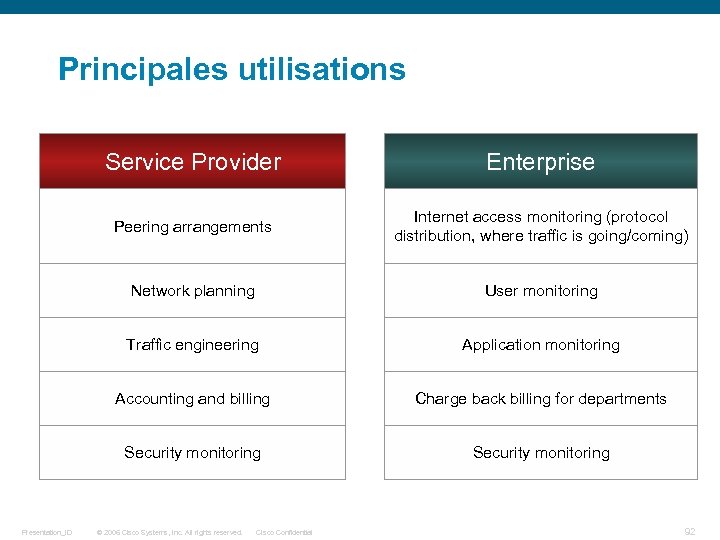
Principales utilisations Service Provider Peering arrangements Internet access monitoring (protocol distribution, where traffic is going/coming) Network planning User monitoring Traffic engineering Application monitoring Accounting and billing Charge back billing for departments Security monitoring Presentation_ID Enterprise Security monitoring © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 92
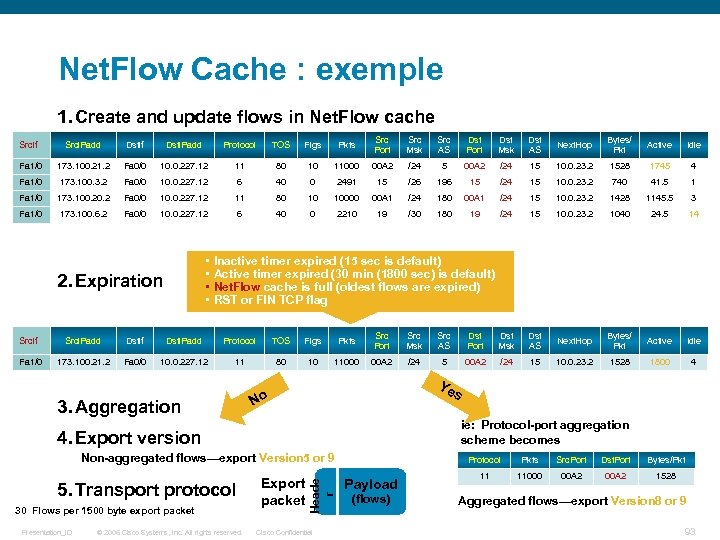
Net. Flow Cache : exemple 1. Create and update flows in Net. Flow cache Srclf Srcl. Padd Dstlf Dstl. Padd Protocol TOS Flgs Pkts Src Port Src Msk Src AS Dst Port Dst Msk Dst AS Next. Hop Bytes/ Pkt Active Idle Fa 1/0 173. 100. 21. 2 Fa 0/0 10. 0. 227. 12 11 80 10 11000 00 A 2 /24 5 00 A 2 /24 15 10. 0. 23. 2 1528 1745 4 Fa 1/0 173. 100. 3. 2 Fa 0/0 10. 0. 227. 12 6 40 0 2491 15 /26 196 15 /24 15 10. 0. 23. 2 740 41. 5 1 Fa 1/0 173. 100. 2 Fa 0/0 10. 0. 227. 12 11 80 10 10000 00 A 1 /24 180 00 A 1 /24 15 10. 0. 23. 2 1428 1145. 5 3 Fa 1/0 173. 100. 6. 2 Fa 0/0 10. 0. 227. 12 6 40 0 2210 19 /30 180 19 /24 15 10. 0. 23. 2 1040 24. 5 14 • • 2. Expiration Inactive timer expired (15 sec is default) Active timer expired (30 min (1800 sec) is default) Net. Flow cache is full (oldest flows are expired) RST or FIN TCP flag Srclf Srcl. Padd Dstlf Dstl. Padd Protocol TOS Flgs Pkts Src Port Src Msk Src AS Dst Port Dst Msk Dst AS Next. Hop Bytes/ Pkt Active Idle Fa 1/0 173. 100. 21. 2 Fa 0/0 10. 0. 227. 12 11 80 10 11000 00 A 2 /24 5 00 A 2 /24 15 10. 0. 23. 2 1528 1800 4 3. Aggregation Ye s No ie: Protocol-port aggregation scheme becomes 4. Export version 5. Transport protocol 30 Flows per 1500 byte export packet Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Export packet Heade r Non-aggregated flows—export Version 5 or 9 Cisco Confidential Protocol Payload (flows) Pkts Src. Port Dst. Port Bytes/Pkt 11 11000 00 A 2 1528 Aggregated flows—export Version 8 or 9 93
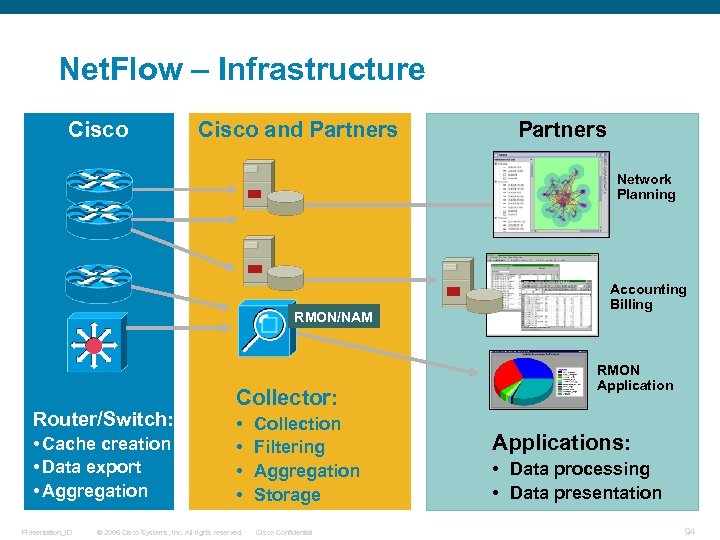
Net. Flow – Infrastructure Cisco and Partners Network Planning RMON/NAM Router/Switch: • Cache creation • Data export • Aggregation Presentation_ID Collector: • • © 2006 Cisco Systems, Inc. All rights reserved. Collection Filtering Aggregation Storage Cisco Confidential Accounting Billing RMON Applications: • Data processing • Data presentation 94
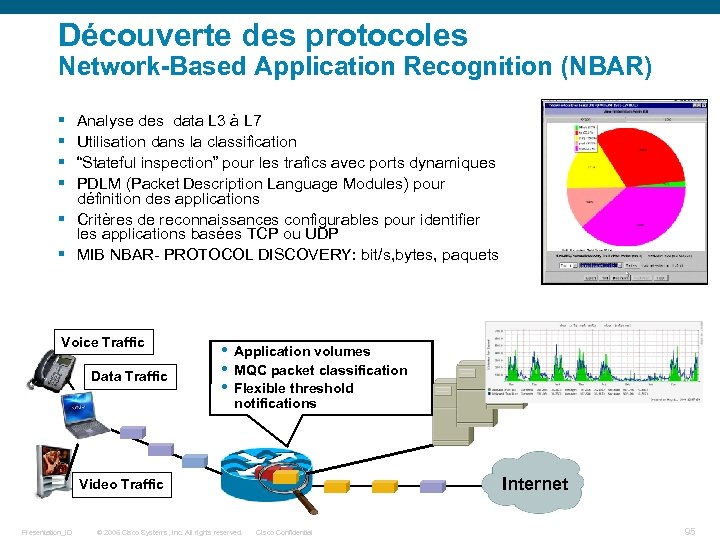
Découverte des protocoles Network-Based Application Recognition (NBAR) § § Analyse des data L 3 à L 7 Utilisation dans la classification “Stateful inspection” pour les trafics avec ports dynamiques PDLM (Packet Description Language Modules) pour définition des applications § Critères de reconnaissances configurables pour identifier les applications basées TCP ou UDP § MIB NBAR- PROTOCOL DISCOVERY: bit/s, bytes, paquets Voice Traffic Data Traffic • • • Application volumes MQC packet classification Flexible threshold notifications Internet Video Traffic Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. P 2 P Cisco Confidential 95
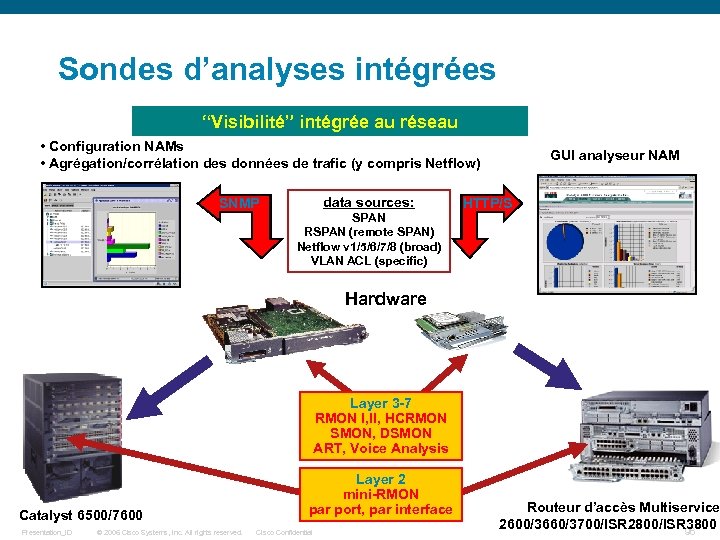
Sondes d’analyses intégrées “Visibilité” intégrée au réseau • Configuration NAMs • Agrégation/corrélation des données de trafic (y compris Netflow) SNMP data sources: SPAN RSPAN (remote SPAN) Netflow v 1/5/6/7/8 (broad) VLAN ACL (specific) GUI analyseur NAM HTTP/S Hardware Layer 3 -7 RMON I, II, HCRMON SMON, DSMON ART, Voice Analysis Catalyst 6500/7600 Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Layer 2 mini-RMON par port, par interface Cisco Confidential Routeur d’accès Multiservice 2600/3660/3700/ISR 2800/ISR 3800 96
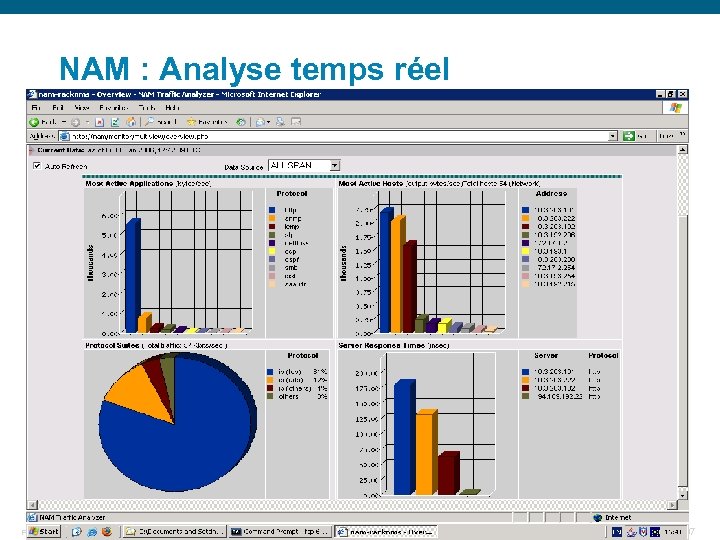
NAM : Analyse temps réel Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 97
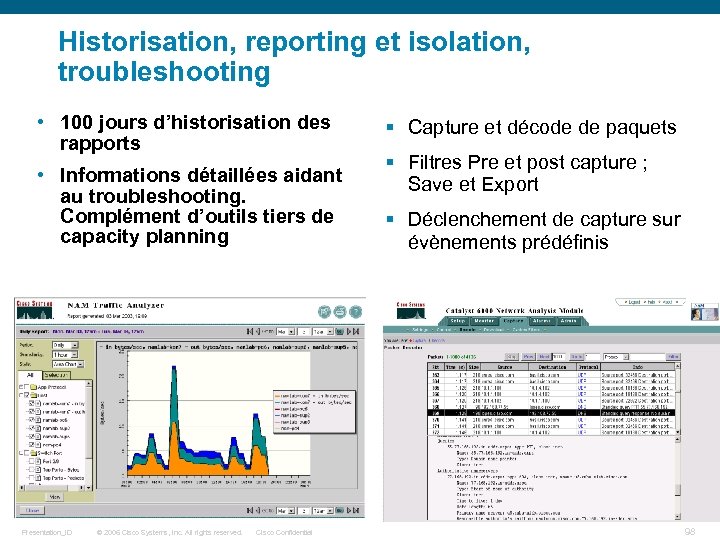
Historisation, reporting et isolation, troubleshooting • 100 jours d’historisation des rapports • Informations détaillées aidant au troubleshooting. Complément d’outils tiers de capacity planning Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential § Capture et décode de paquets § Filtres Pre et post capture ; Save et Export § Déclenchement de capture sur évènements prédéfinis 98
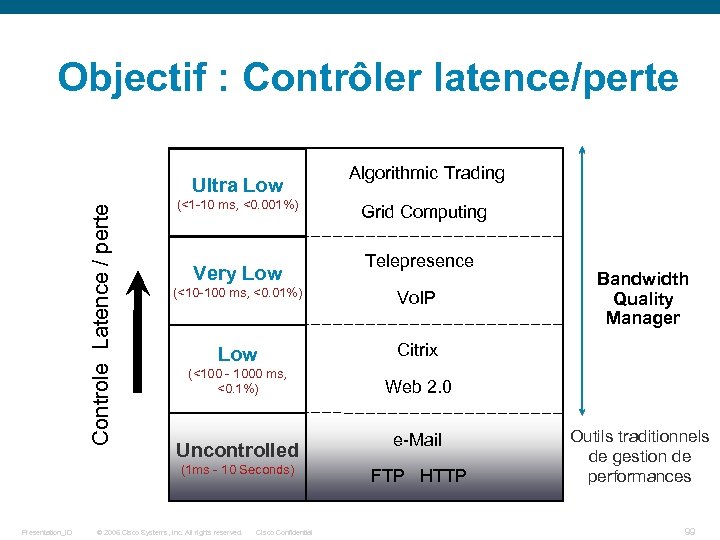
Objectif : Contrôler latence/perte Controle Latence / perte Ultra Low (<1 -10 ms, <0. 001%) Very Low Grid Computing Telepresence (<10 -100 ms, <0. 01%) Vo. IP Low (<100 - 1000 ms, <0. 1%) Bandwidth Quality Manager Citrix Web 2. 0 Uncontrolled (1 ms - 10 Seconds) Presentation_ID Algorithmic Trading © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential e-Mail FTP HTTP Outils traditionnels de gestion de performances 99
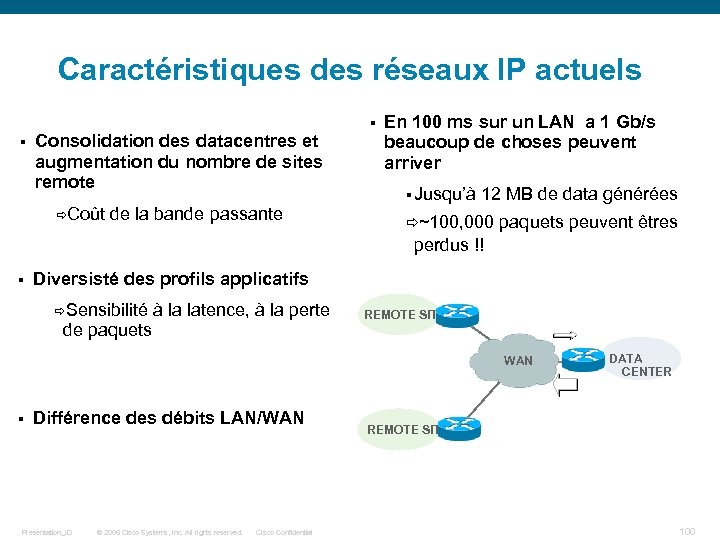
Caractéristiques des réseaux IP actuels § § Consolidation des datacentres et augmentation du nombre de sites remote Coût de la bande passante En 100 ms sur un LAN a 1 Gb/s beaucoup de choses peuvent arriver § Jusqu’à 12 MB de data générées ~100, 000 paquets peuvent êtres perdus !! § Diversisté des profils applicatifs Sensibilité à la latence, à la perte de paquets REMOTE SITE WAN § Différence des débits LAN/WAN Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential DATA CENTER REMOTE SITE 100
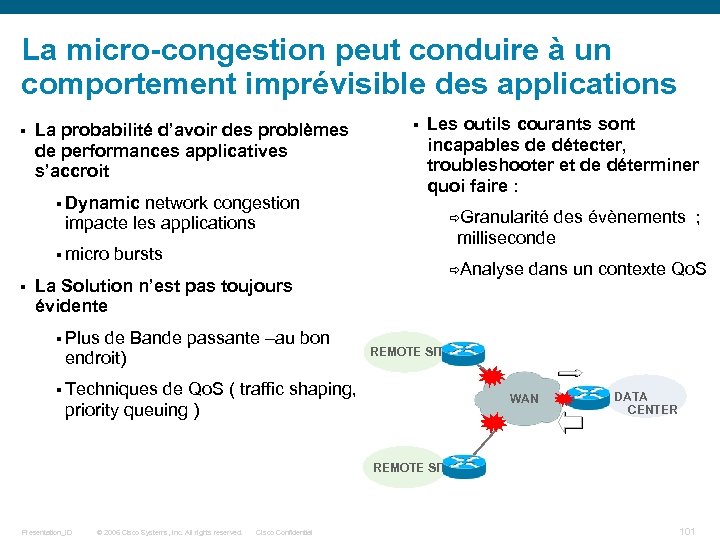
La micro-congestion peut conduire à un comportement imprévisible des applications § La probabilité d’avoir des problèmes de performances applicatives s’accroit § Dynamic network congestion impacte les applications Les outils courants sont incapables de détecter, troubleshooter et de déterminer quoi faire : Granularité des évènements ; milliseconde § micro bursts § § La Solution n’est pas toujours évidente § Plus de Bande passante –au bon endroit) Analyse dans un contexte Qo. S REMOTE SITE § Techniques de Qo. S ( traffic shaping, WAN priority queuing ) DATA CENTER REMOTE SITE Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 101
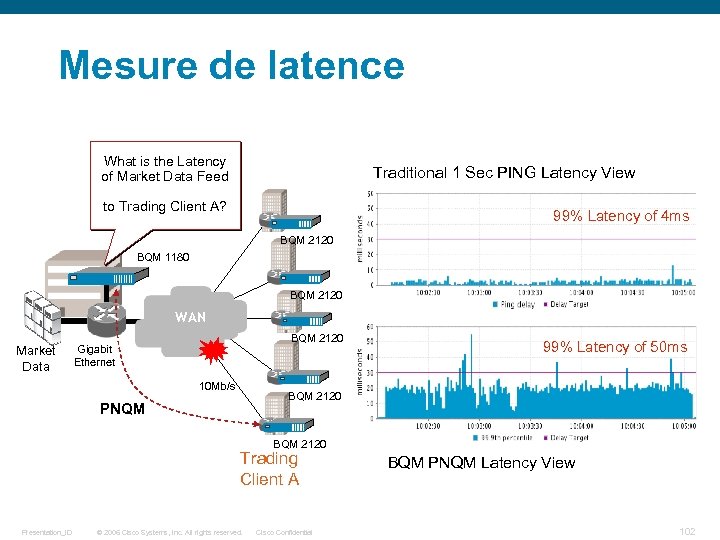
Mesure de latence What is the Latency of Market Data Feed Traditional 1 Sec PING Latency View to Trading Client A? 99% Latency of 4 ms BQM 2120 BQM 1180 BQM 2120 WAN Market Data BQM 2120 Gigabit Ethernet 10 Mb/s 99% Latency of 50 ms BQM 2120 PNQM BQM 2120 Trading Client A Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential BQM PNQM Latency View 102
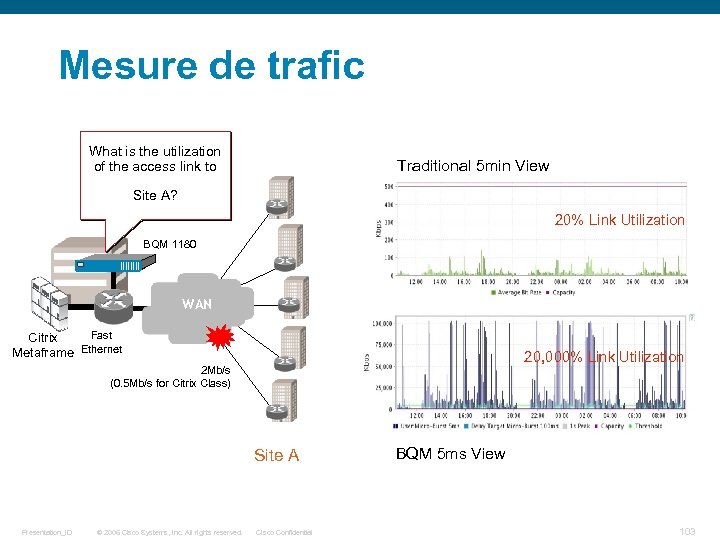
Mesure de trafic What is the utilization of the access link to Traditional 5 min View Site A? 20% Link Utilization BQM 1180 WAN Fast Citrix Metaframe Ethernet 20, 000% Link Utilization 2 Mb/s (0. 5 Mb/s for Citrix Class) Site A Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential BQM 5 ms View 103
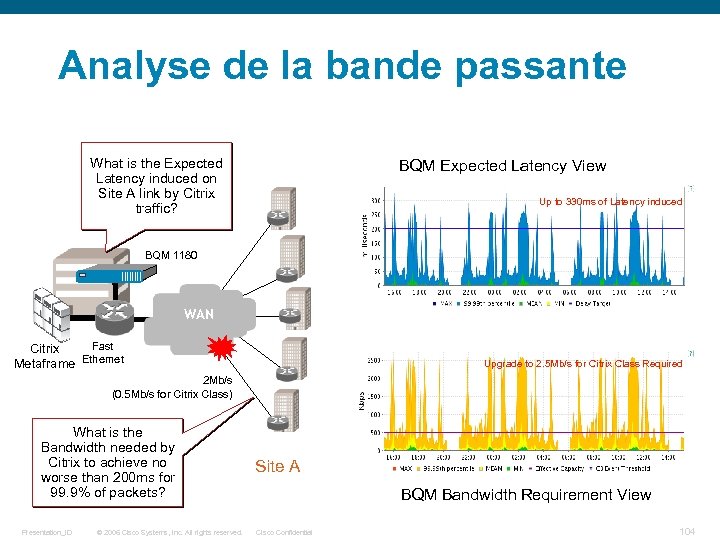
Analyse de la bande passante What is the Expected Latency induced on Site A link by Citrix traffic? BQM Expected Latency View Up to 330 ms of Latency induced BQM 1180 WAN Fast Citrix Ethernet Metaframe Upgrade to 2. 5 Mb/s for Citrix Class Required 2 Mb/s (0. 5 Mb/s for Citrix Class) What is the Bandwidth needed by Citrix to achieve no worse than 200 ms for 99. 9% of packets? Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Site A BQM Bandwidth Requirement View Cisco Confidential 104
Solution de SLM § “Turning a Cisco Network into a powerful SLM solution” § Appliance avec un Portail Web centralisant : Les mesures de performance par les probes IP-SLA L’analyse des MIBs CBQos (classes de service) & NBAR (protocol discovery) Le suivi des trafics Netflow Graphiques détaillés des mesures § Solution évolutive pour : Le suivi des SLA réseaux …. . et des infrastructures Vo. IP Préparer ou améliorer la mise en œuvre d’applications « critiques » Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 105

Presentation_ID © 2006 Cisco Systems, Inc. All rights reserved. Cisco Confidential 106
bc21fcaf74a10171cf90c59d2e9ec421.ppt