ba78cfee517a3cd7c9c4e2d5cf22dbea.ppt
- Количество слайдов: 20

HP UX 11 Security Products Jacob Shaaltiel • HP Consulting Israel July 15, 2001
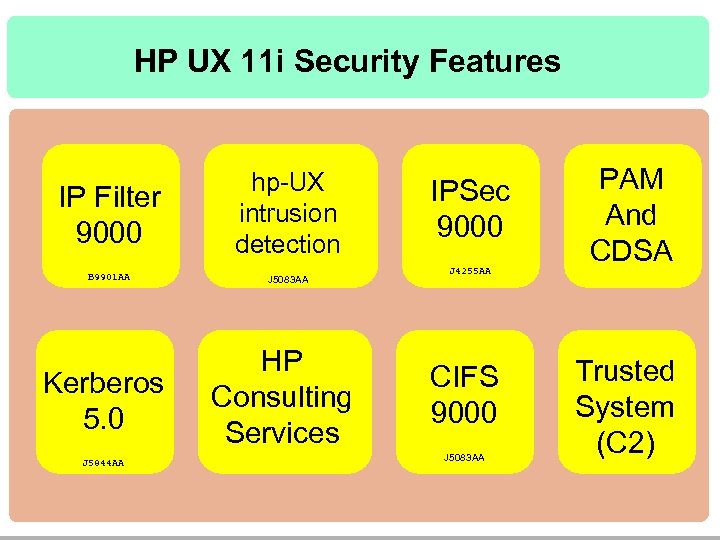
HP UX 11 i Security Features IP Filter 9000 hp-UX intrusion detection B 9901 AA J 5083 AA Kerberos 5. 0 J 5844 AA HP Consulting Services IPSec 9000 J 4255 AA CIFS 9000 J 5083 AA PAM And CDSA Trusted System (C 2)

HP-UX 11 Is The Most Secure Commercial Unix Server Industry standard security easily integrates in end-to-end security solutions • IPSec • CDSA • Kerberos • LDAP • C 2 Compliance High Performance Security • HP Praesideum Speedcard • HP-UX software encryption acceleration Broad portfolio of security products and solutions to meet the demanding requirements of integrated OS, network and application security • Virtual Vault • Domain. Guard • Extranet VPN • e-Firewall • Node Sentry • Intrusion The server is the final line of Detection defense

HP UX 11 i Kernel Level intrusion detection
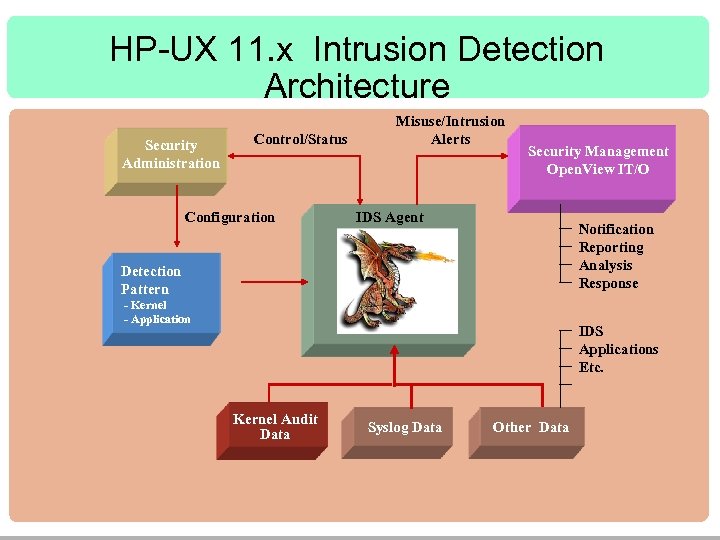
HP-UX 11. x Intrusion Detection Architecture Security Administration Control/Status Configuration Misuse/Intrusion Alerts Security Management Open. View IT/O IDS Agent Notification Reporting Analysis Response Detection Pattern - Kernel - Application IDS Applications Etc. Kernel Audit Data Syslog Data Other Data
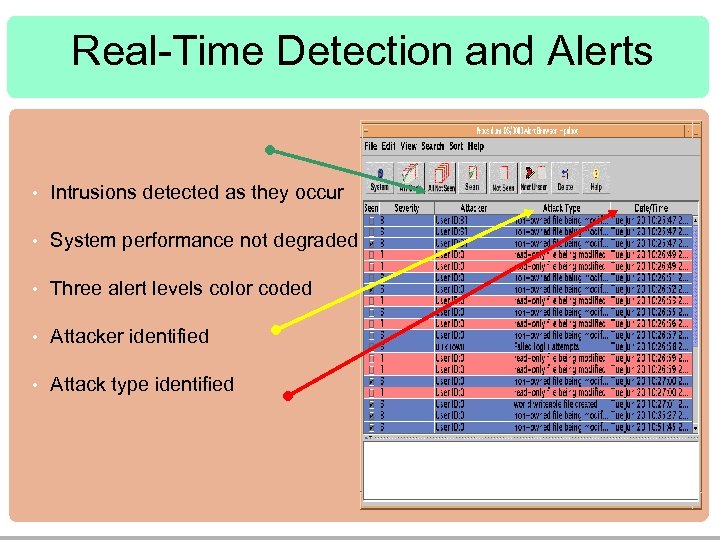
Real-Time Detection and Alerts • Intrusions detected as they occur • System performance not degraded • Three alert levels color coded • Attacker identified • Attack type identified
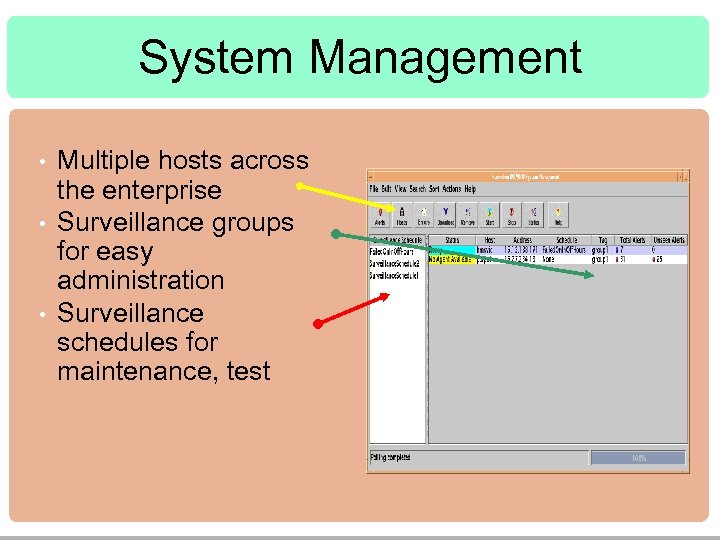
System Management • • • Multiple hosts across the enterprise Surveillance groups for easy administration Surveillance schedules for maintenance, test

HP UX 11 i Security IP Filter 9000
IP Filter 9000 • IPFilter/9000 is the same as the IP Filter Version 3. 5 Alpha 5 from the public domain (authored by Darren Reed) with stronger quality. It contains all functionality in the public domain code including the unsupported perimeter firewall features, such as NAT and firewall stealth. The customers using the unsupported features may request f support from the public domain, at the URL: http: //caligula. anu. edu. au/~avalon/ • IPFilter/9000 is not supported in an MC/SG environment. • IPFilter is offered for free on the application disk HP has positioned IP Filter/9000 as a system firewall and does not support the perimeter firewall features in the product.
IP Filter 9000 • IP Filter/9000 provides the following benefits: · Protect an individual host in intranet against internal attacks · Protect a host in intranet against external attacks that breach perimeter defenses · Protect a bastion host on the perimeter (e. g. web serve · Protect a bastion host in the DMZ (e. g. web server) · Protect an application proxy firewall against attacks tha target the underlying OS · Stop the security hole created by remote access workstation connected to Internet and having VPN access to intranet · Provide restricted configuration of internet services
IP Filter 9000 Example Filtering by Port Number object = addr [ port-comp | port-range ] port-comp = "port" compare port-num port-range = "port" port-num range port-num Only applicable with the TCP and UDP IP Protocols. Example: pass in quick proto tcp from any to 20. 20. 1/32 port = 23

HP UX 11 i Security IPSec 9000
Types of VPNs • Host-to-Host – End-to-End security to protect sensitive data for intra- or internetwork communications • • E-Firewall/VPN Extranet VPN • E-Firewall/VPN – Quick set-up of business-to-business WAN connectivity • • IPSec/9000 Site-to-Site – Replace expensive dedicated leased line WAN charges for site-to-site data connectivity • HP Solution Remote Access – Replace expensive modem pools, ISDN per-minute charges • E-Firewall/VPN
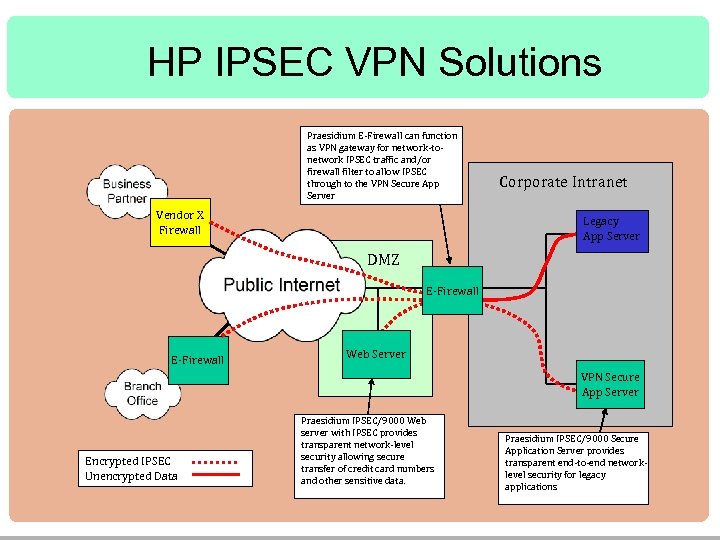
HP IPSEC VPN Solutions Praesidium E-Firewall can function as VPN gateway for network-tonetwork IPSEC traffic and/or firewall filter to allow IPSEC through to the VPN Secure App Server Vendor X Firewall Corporate Intranet Legacy App Server DMZ E-Firewall Web Server VPN Secure App Server Encrypted IPSEC Unencrypted Data Praesidium IPSEC/9000 Web server with IPSEC provides transparent network-level security allowing secure transfer of credit card numbers and other sensitive data. Praesidium IPSEC/9000 Secure Application Server provides transparent end-to-end networklevel security for legacy applications
HP-UX IPSec/9000 Product Overview • IPSec-based standard solutions to provide interoperability and to protect customer’s investment. • Scalable and flexible key management (IKE) for authentication • Easy Integration with existing infrastructure- Pre-shared key support • Scalable Public-key based authentication with PKI - automated certificate and CRL retrieval process • Easy to adopt - allows existing applications to take advantage of IPSec services without modifications. • Flexible rule-based security attribute and access control policy configurations - Allow combinations of IP addresses, subnet mask, ports, protocols and connection-based keying, security attribute configuration and packet filtering - Can be configured to filter both IPSec and clear-text packets • Industry leading high-performance IPSec/VPN Crypto performance is optimized for PA-RISC architecture.

HP-UX IPSec/9000 Product Overview (Continue) • End-to-end IPSec to distribute cryptographic computation cycles among multiple end systems. • Secure and ease-of-use Administration Tools • GUI based IPSec Policy Configuration Console • IPSec Policy Defaults • Diagnostic and Monitoring Tool • Logging and audit trail for accountability and intrusion alerts • Demonstrated multi-vendor interoperability at the ANX and IPSec standards bakeoffs. • Both transport mode and tunnel mode are supported to facilitate flexible VPN scenarios. • No cost.
HP UX 11 i Security Trusted Mode (C 2)
Trusted Mode (C 2) Extensions to Security beyond Standard UNIX The Protected Password Database enables: · System Boot Authentication · Denial of encrypted password access by non-root users · Extending maximum password length beyond eight characters · Forcing all passwords to conform to minimum complexity requirements · Preventing reuse of password once they’ve expired · Establishing minimum and maximum password length requirements · Creation of a unique Audit ID for every user · Automatic user account expiration · Account login restrictions (time of day, day of week) · Account disabling after a number of failed login attempts · Login device restrictions (by tty) Trusted Mode also has a C 2 -compliant auditing system which audits system activity at a low ‘system call’ level.
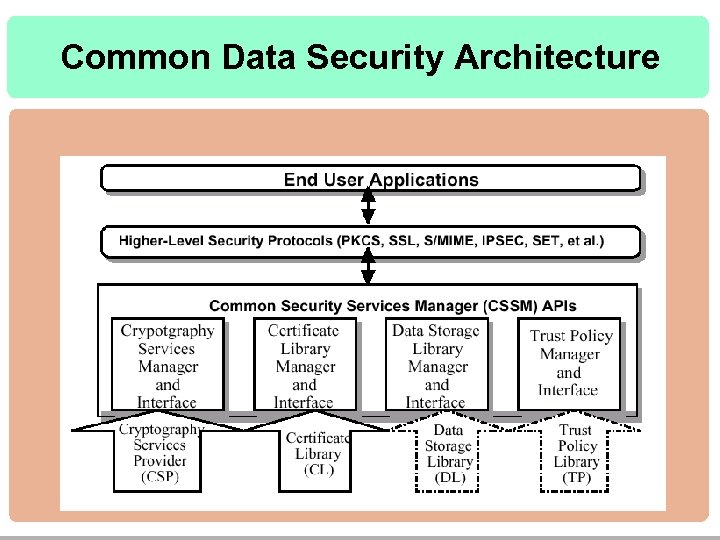
Common Data Security Architecture

Thank You
ba78cfee517a3cd7c9c4e2d5cf22dbea.ppt