a6c90b35f7526add32279e5f081d5ba8.ppt
- Количество слайдов: 52

How to Sell SMB Security December 14, 2007 SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential

Topic of Content § Market Opportunity and Trends § Cisco’s Security Story § Security Basics § How to sell Cisco products SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 2

Market Opportunity and Trends SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 3

SMB Definition SMB Small Business 5– 99 Employees SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential Medium-Sized Business 100– 249 Employees 4
SMB Profile § Same technology needs and challenges as enterprise § Little to no internal I. T. § knowledge or competence § Tired of problems and lost productivity from: - Viruses, Worms - Spyware - User error Technology is considered a business foundation, not an office expense! Source: Cisco Focus Groups, 2007 SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 5
Understanding the SMB Decision Maker AND do all that with limited staff and budget? How do I protect my assets? How can I be more adaptive to changing conditions? How can I increase my profitability? SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. How can we be more productive? Cisco Confidential 6
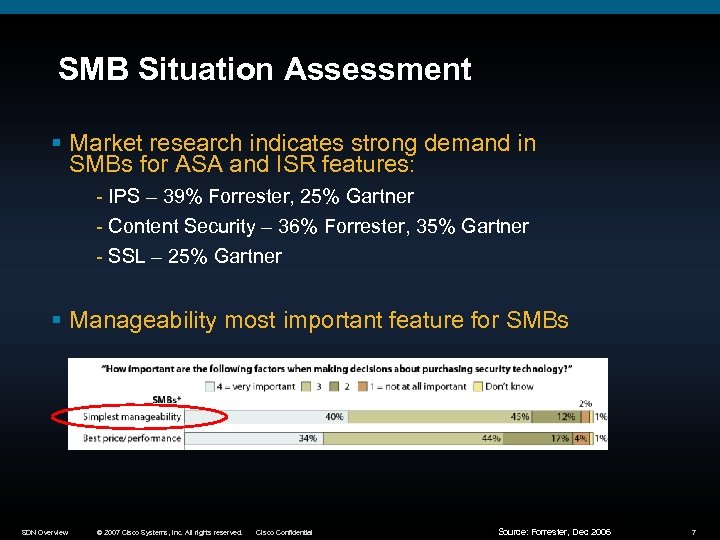
SMB Situation Assessment § Market research indicates strong demand in SMBs for ASA and ISR features: - IPS – 39% Forrester, 25% Gartner - Content Security – 36% Forrester, 35% Gartner - SSL – 25% Gartner § Manageability most important feature for SMBs SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential Source: Forrester, Dec 2006 7
Infrastructure Adoption and Spending* SMBs are looking to buy or upgrade all types of security technologies § Network Firewalls § Intrusion Detection § Content Security § Gateway Anti-Spyware Appliance § Gateway Anti-Virus Appliance *December 2006, Data Overview “The State Of Security In SMBs And Enterprises” SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 8

Cisco’s Security Story SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 9
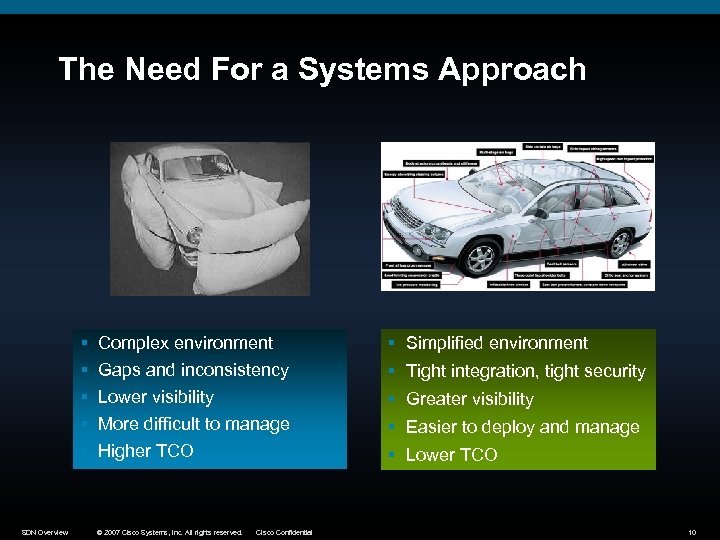
The Need For a Systems Approach § § § SDN Overview Complex environment Gaps and inconsistency § Simplified environment Lower visibility More difficult to manage Higher TCO § Greater visibility © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential § Tight integration, tight security § Easier to deploy and manage § Lower TCO 10
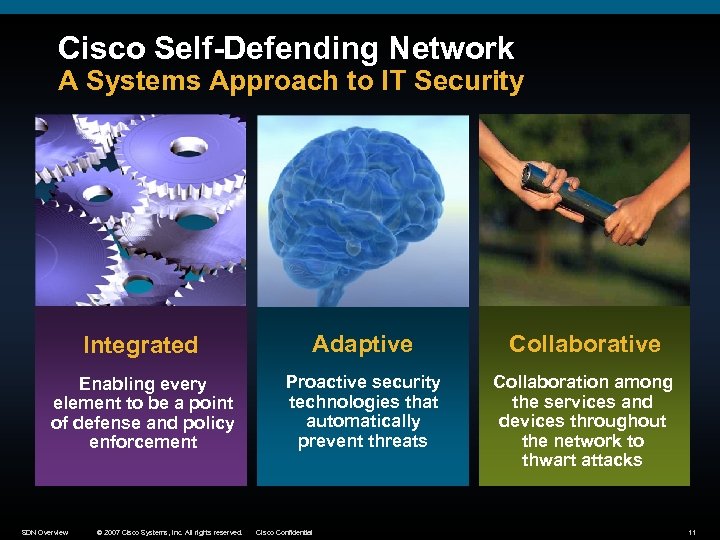
Cisco Self-Defending Network A Systems Approach to IT Security Integrated Adaptive Collaborative Enabling every element to be a point of defense and policy enforcement Proactive security technologies that automatically prevent threats Collaboration among the services and devices throughout the network to thwart attacks SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 11

The Alternative… SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 12

Market Leader with Commitment to Security § Product and Technology Innovation 1500+ security-focused engineers Nine acquisitions added to our solution portfolio in last two years SMB focused security products § Industry Leadership Critical Infrastructure Assurance Group Responsible disclosure “ Because the network is a strategic customer asset, the protection of its business-critical applications and resources is a top priority. ” John Chambers, Chairman & CEO, Cisco SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 13
Why partner with Cisco? Differentiation § Separate yourself from the crowd Leverage the Cisco Brand § Become part of the Cisco Partner Program Cisco SMB Solutions § Cisco ‘purpose built’ products for the SMB security market § Cisco Adaptive Security Appliance and Integrated Service Routers Cisco Support SDN Overview § Access to SMB market opportunity and trends § Support from Distribution partners § Sales and Marketing tools and resources © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 14

Security Basics SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 15
Network Security Threats § Network security threats include: - Network service attacks - Data theft and interception - Software-based viruses, worms and Trojan Horses SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 16
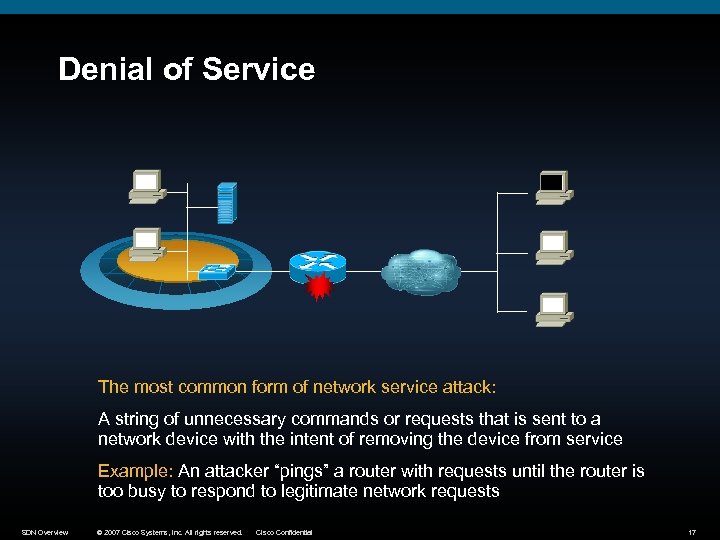
Denial of Service The most common form of network service attack: A string of unnecessary commands or requests that is sent to a network device with the intent of removing the device from service Example: An attacker “pings” a router with requests until the router is too busy to respond to legitimate network requests SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 17
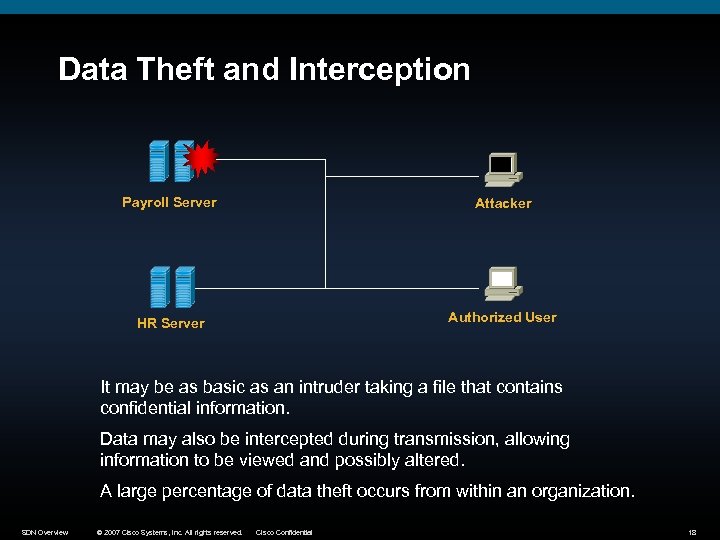
Data Theft and Interception Payroll Server Attacker HR Server Authorized User It may be as basic as an intruder taking a file that contains confidential information. Data may also be intercepted during transmission, allowing information to be viewed and possibly altered. A large percentage of data theft occurs from within an organization. SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 18
Worm, Virus, and Trojan Horse Attacks The primary vulnerabilities for end-user workstations: A worm executes arbitrary code and installs copies of itself in the infected computer’s memory, which infects other hosts. A virus is malicious software that is attached to another program to execute a particular unwanted function on a user's workstation. A Trojan horse is different only in that the entire application was written to look like something else, when in fact it is an attack. SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 19
What is a Firewall? Firewalls provide the first line of perimeter defense by: § Preventing unauthorized access to a network, while allowing in authorized users. § Provides ability to expose internet services in a limited ability to the outside world via a DMZ. SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 20
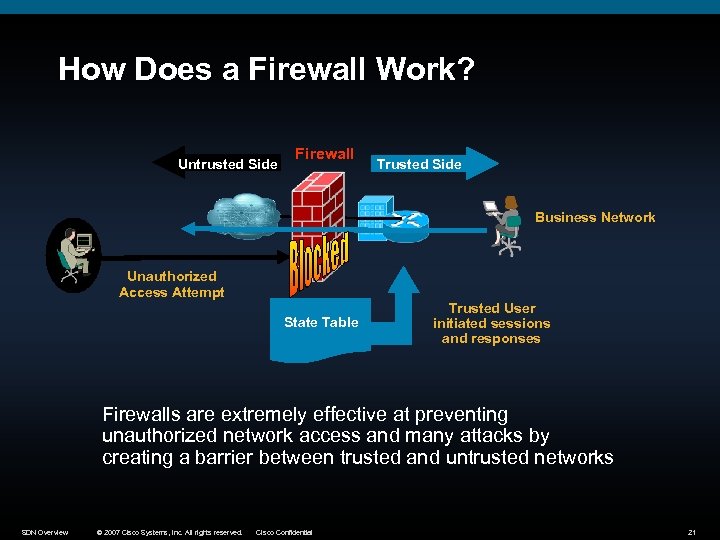
How Does a Firewall Work? Untrusted Side Firewall Trusted Side Business Network Unauthorized Access Attempt State Table Trusted User initiated sessions and responses Firewalls are extremely effective at preventing unauthorized network access and many attacks by creating a barrier between trusted and untrusted networks SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 21
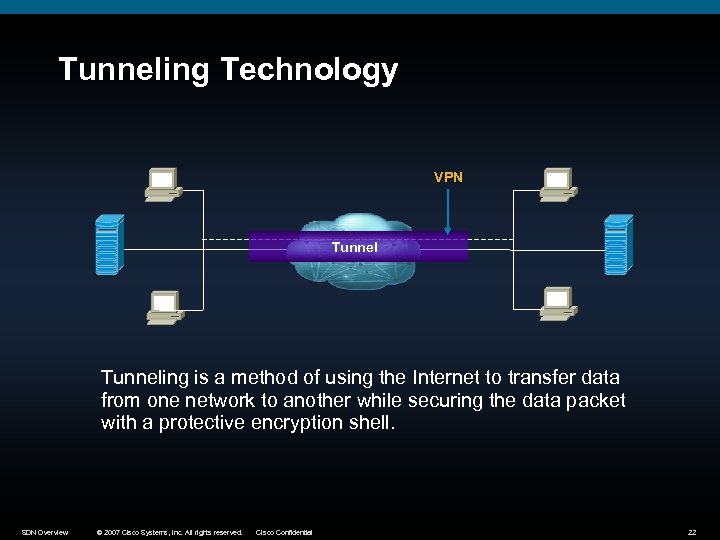
Tunneling Technology VPN Tunneling is a method of using the Internet to transfer data from one network to another while securing the data packet with a protective encryption shell. SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 22

What is a VPN? § VPNs are the solution to ensure that data confidentiality and integrity are protected in dynamic environments. § VPNs provide protection from data interception of unprotected assets using secure connectivity, encryption, and traffic authentication. § Company LANs and remote users can connect to the network using the same Internet access methods: dialup, (DSL), cable, ISDN, and wireless. SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 23
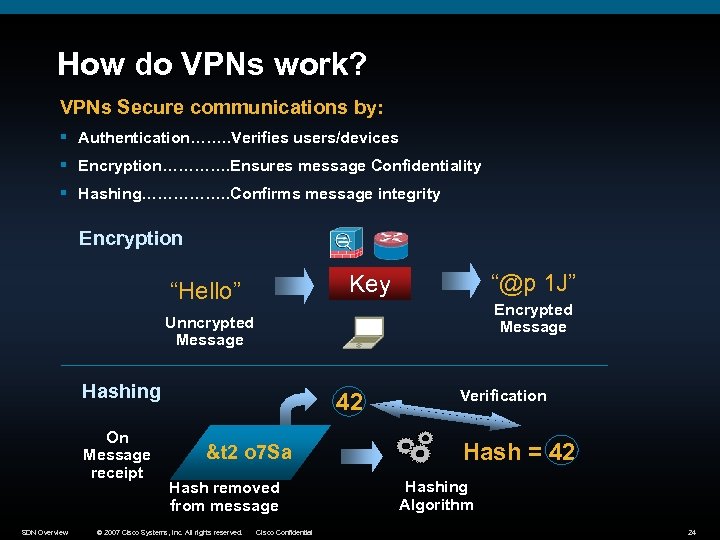
How do VPNs work? VPNs Secure communications by: § Authentication……. . Verifies users/devices § Encryption…………. Ensures message Confidentiality § Hashing……………. . Confirms message integrity Encryption “@p 1 J” Key “Hello” Encrypted Message Unncrypted Message Hashing On Message receipt SDN Overview 42 &t 2 o 7 Sa Hash removed from message © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential Verification Hash = 42 Hashing Algorithm 24

What is Intrusion Prevention (IPS) § IPS adds a layer of protection that firewalls alone cannot address. Follows are some key threats where IPS provides added protection: - Worms - Trojan Horses - Bots - Application Attacks - Port Scans and Hacking attempts - Covert Channel Communications SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 25
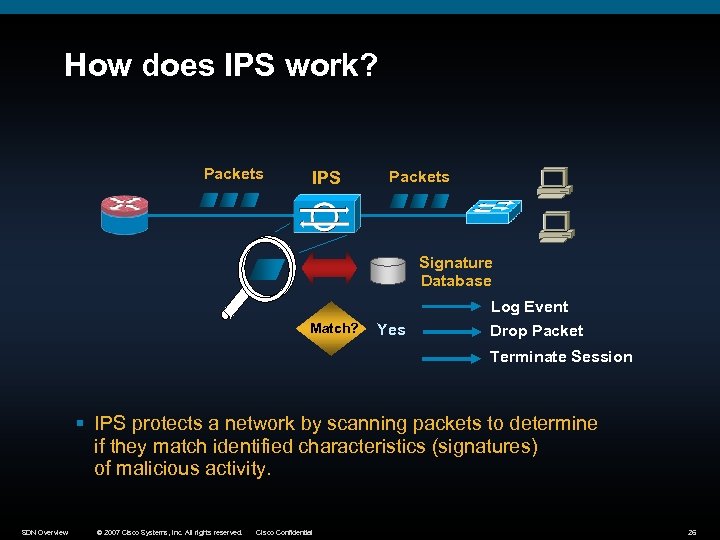
How does IPS work? Packets IPS Packets Signature Database Log Event Match? Yes Drop Packet Terminate Session § IPS protects a network by scanning packets to determine if they match identified characteristics (signatures) of malicious activity. SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 26
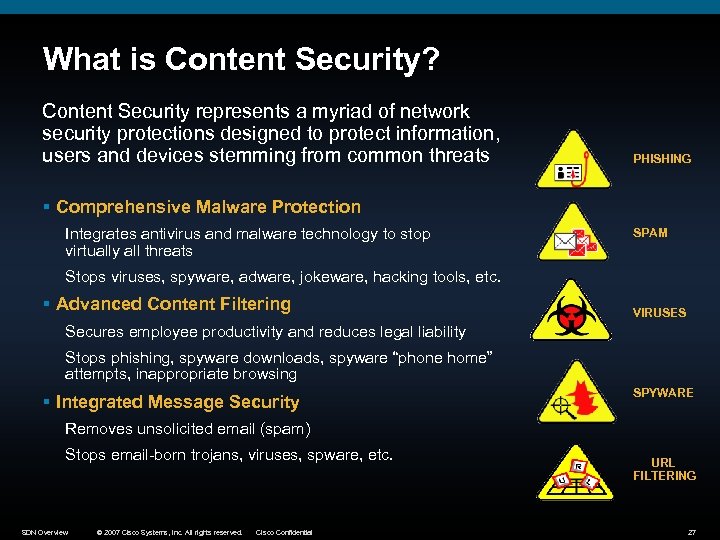
What is Content Security? Content Security represents a myriad of network security protections designed to protect information, users and devices stemming from common threats PHISHING § Comprehensive Malware Protection Integrates antivirus and malware technology to stop virtually all threats SPAM Stops viruses, spyware, adware, jokeware, hacking tools, etc. § Advanced Content Filtering VIRUSES Secures employee productivity and reduces legal liability Stops phishing, spyware downloads, spyware “phone home” attempts, inappropriate browsing § Integrated Message Security SPYWARE Removes unsolicited email (spam) Stops email-born trojans, viruses, spware, etc. SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential URL FILTERING 27

Security Is Now a Baseline Architecture for IT Infrastructure Switching IP Telephony Wireless LAN SDN Overview Routing Storage Networking Networked Home © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 28

How To Sell Cisco Security Products SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 29
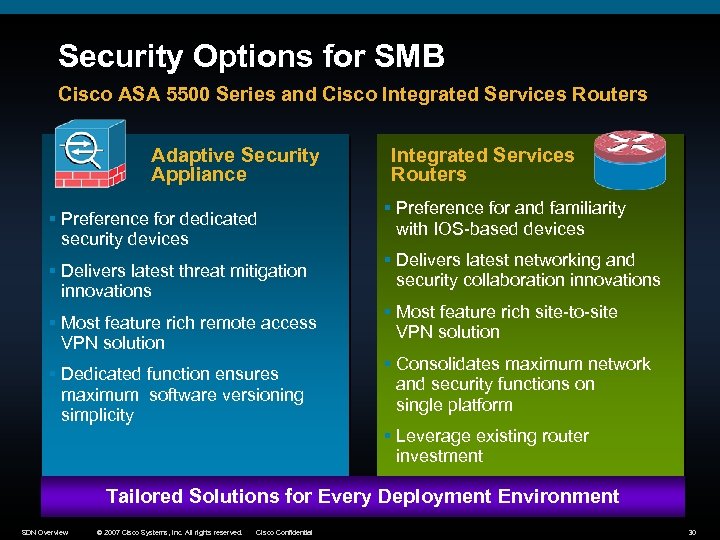
Security Options for SMB Cisco ASA 5500 Series and Cisco Integrated Services Routers Adaptive Security Appliance § Preference for dedicated security devices § Delivers latest threat mitigation innovations § Most feature rich remote access VPN solution § Dedicated function ensures maximum software versioning simplicity Integrated Services Routers § Preference for and familiarity with IOS-based devices § Delivers latest networking and security collaboration innovations § Most feature rich site-to-site VPN solution § Consolidates maximum network and security functions on single platform § Leverage existing router investment Tailored Solutions for Every Deployment Environment SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 30
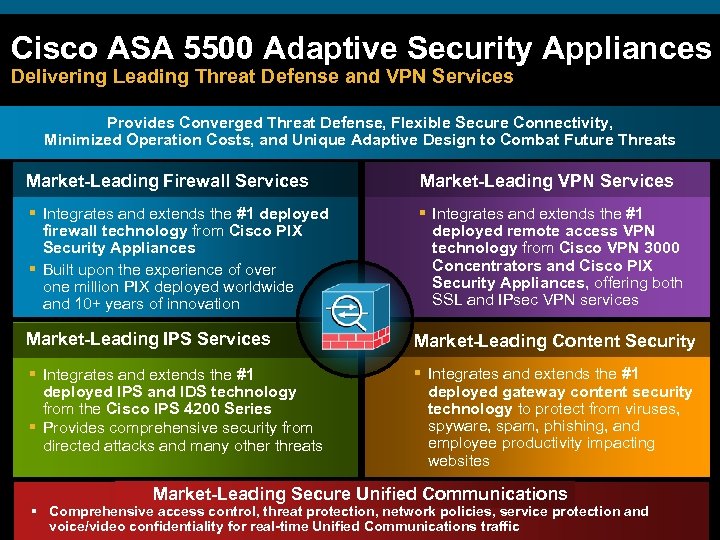
Cisco ASA 5500 Adaptive Security Appliances Delivering Leading Threat Defense and VPN Services Provides Converged Threat Defense, Flexible Secure Connectivity, Minimized Operation Costs, and Unique Adaptive Design to Combat Future Threats Market-Leading Firewall Services Market-Leading VPN Services § Integrates and extends the #1 deployed firewall technology from Cisco PIX Security Appliances § Built upon the experience of over one million PIX deployed worldwide and 10+ years of innovation § Integrates and extends the #1 deployed remote access VPN technology from Cisco VPN 3000 Concentrators and Cisco PIX Security Appliances, offering both SSL and IPsec VPN services Market-Leading IPS Services Market-Leading Content Security § Integrates and extends the #1 deployed IPS and IDS technology from the Cisco IPS 4200 Series § Provides comprehensive security from directed attacks and many other threats § Integrates and extends the #1 deployed gateway content security technology to protect from viruses, spyware, spam, phishing, and employee productivity impacting websites Market-Leading Secure Unified Communications § Comprehensive access control, threat protection, network policies, service protection and voice/video confidentiality for real-time Unified Communications traffic SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 31
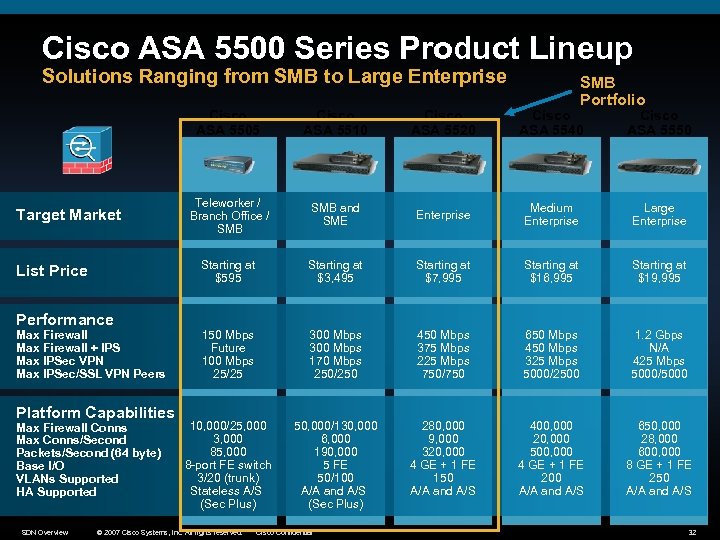
Cisco ASA 5500 Series Product Lineup Solutions Ranging from SMB to Large Enterprise SMB Portfolio Cisco ASA 5505 List Price Performance Max Firewall + IPS Max IPSec VPN Max IPSec/SSL VPN Peers Platform Capabilities Max Firewall Conns Max Conns/Second Packets/Second (64 byte) Base I/O VLANs Supported HA Supported SDN Overview Cisco ASA 5520 Cisco ASA 5540 Cisco ASA 5550 Teleworker / Branch Office / SMB and SME Enterprise Medium Enterprise Large Enterprise Starting at $595 Target Market Cisco ASA 5510 Starting at $3, 495 Starting at $7, 995 Starting at $16, 995 Starting at $19, 995 150 Mbps Future 100 Mbps 25/25 300 Mbps 170 Mbps 250/250 450 Mbps 375 Mbps 225 Mbps 750/750 650 Mbps 450 Mbps 325 Mbps 5000/2500 1. 2 Gbps N/A 425 Mbps 5000/5000 10, 000/25, 000 3, 000 85, 000 8 -port FE switch 3/20 (trunk) Stateless A/S (Sec Plus) 50, 000/130, 000 6, 000 190, 000 5 FE 50/100 A/A and A/S (Sec Plus) 280, 000 9, 000 320, 000 4 GE + 1 FE 150 A/A and A/S 400, 000 20, 000 500, 000 4 GE + 1 FE 200 A/A and A/S 650, 000 28, 000 600, 000 8 GE + 1 FE 250 A/A and A/S © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 32
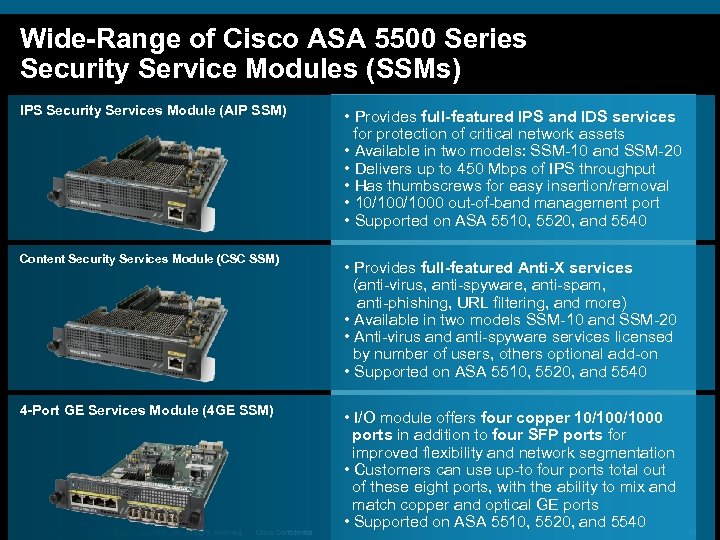
Wide-Range of Cisco ASA 5500 Series Security Service Modules (SSMs) IPS Security Services Module (AIP SSM) • Provides full-featured IPS and IDS services for protection of critical network assets • Available in two models: SSM-10 and SSM-20 • Delivers up to 450 Mbps of IPS throughput • Has thumbscrews for easy insertion/removal • 10/1000 out-of-band management port • Supported on ASA 5510, 5520, and 5540 Content Security Services Module (CSC SSM) • Provides full-featured Anti-X services (anti-virus, anti-spyware, anti-spam, anti-phishing, URL filtering, and more) • Available in two models SSM-10 and SSM-20 • Anti-virus and anti-spyware services licensed by number of users, others optional add-on • Supported on ASA 5510, 5520, and 5540 4 -Port GE Services Module (4 GE SSM) • I/O module offers four copper 10/1000 ports in addition to four SFP ports for improved flexibility and network segmentation • Customers can use up-to four ports total out of these eight ports, with the ability to mix and match copper and optical GE ports • Supported on ASA 5510, 5520, and 5540 SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 33
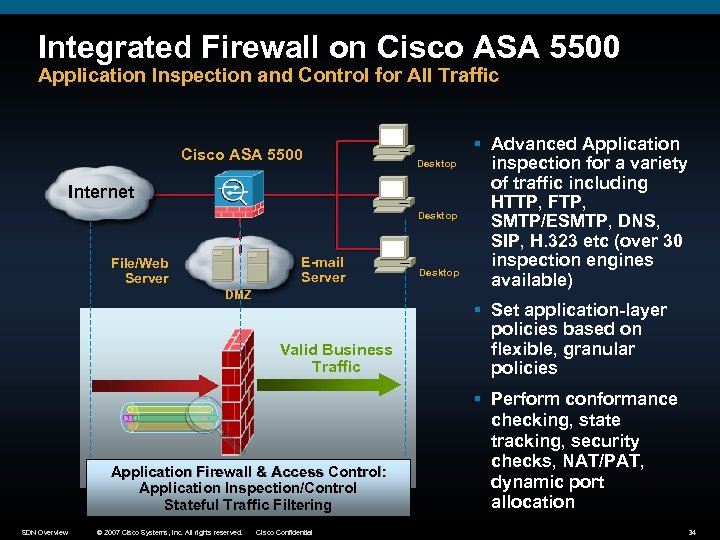
Integrated Firewall on Cisco ASA 5500 Application Inspection and Control for All Traffic Cisco ASA 5500 Desktop Internet Desktop E-mail Server File/Web Server DMZ Valid Business Traffic Application Firewall & Access Control: Application Inspection/Control Stateful Traffic Filtering SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential Desktop § Advanced Application inspection for a variety of traffic including HTTP, FTP, SMTP/ESMTP, DNS, SIP, H. 323 etc (over 30 inspection engines available) § Set application-layer policies based on flexible, granular policies § Perform conformance checking, state tracking, security checks, NAT/PAT, dynamic port allocation 34
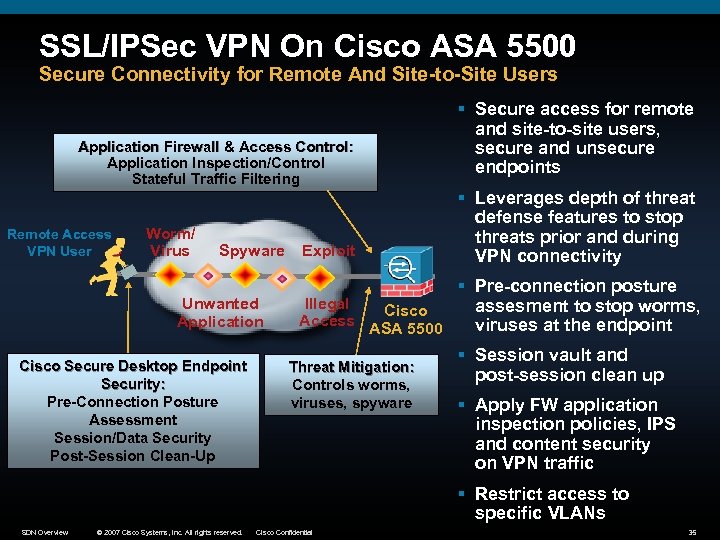
SSL/IPSec VPN On Cisco ASA 5500 Secure Connectivity for Remote And Site-to-Site Users Application Firewall & Access Control: Application Inspection/Control Stateful Traffic Filtering Remote Access VPN User Worm/ Virus Spyware Unwanted Application Cisco Secure Desktop Endpoint Security: Pre-Connection Posture Assessment Session/Data Security Post-Session Clean-Up Exploit § Secure access for remote and site-to-site users, secure and unsecure endpoints § Leverages depth of threat defense features to stop threats prior and during VPN connectivity § Pre-connection posture Illegal assesment to stop worms, Cisco Access ASA 5500 viruses at the endpoint § Session vault and Threat Mitigation: post-session clean up Controls worms, viruses, spyware § Apply FW application inspection policies, IPS and content security on VPN traffic § Restrict access to specific VLANs SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 35
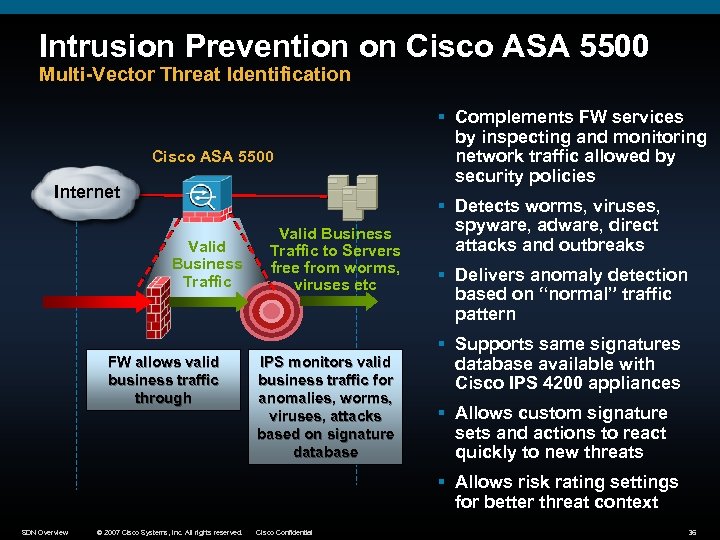
Intrusion Prevention on Cisco ASA 5500 Multi-Vector Threat Identification Cisco ASA 5500 Internet Valid Business Traffic FW allows valid business traffic through Valid Business Traffic to Servers free from worms, viruses etc IPS monitors valid business traffic for anomalies, worms, viruses, attacks based on signature database § Complements FW services by inspecting and monitoring network traffic allowed by security policies § Detects worms, viruses, spyware, adware, direct attacks and outbreaks § Delivers anomaly detection based on “normal” traffic pattern § Supports same signatures database available with Cisco IPS 4200 appliances § Allows custom signature sets and actions to react quickly to new threats § Allows risk rating settings for better threat context SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 36
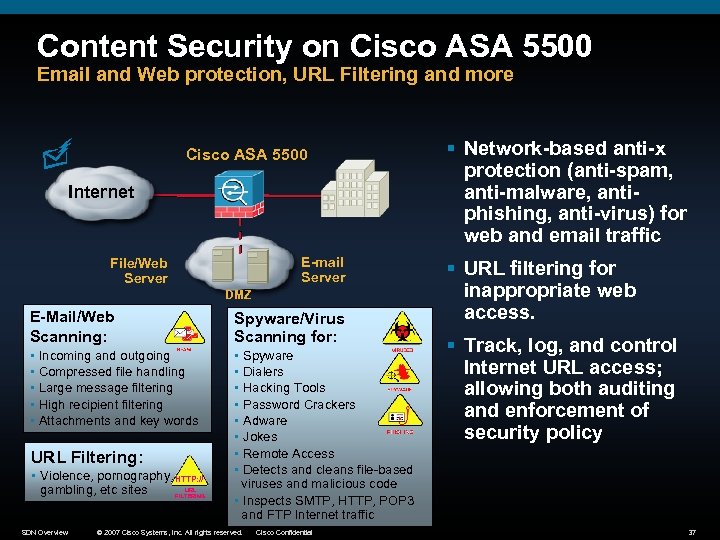
Content Security on Cisco ASA 5500 Email and Web protection, URL Filtering and more Cisco ASA 5500 Internet E-mail Server File/Web Server DMZ E-Mail/Web Scanning: § § § Spyware/Virus Scanning for: Incoming and outgoing Compressed file handling Large message filtering High recipient filtering Attachments and key words URL Filtering: § Violence, pornography, HTTP: // gambling, etc sites SDN Overview URL FILTERING Spyware Dialers Hacking Tools Password Crackers Adware Jokes Remote Access Detects and cleans file-based viruses and malicious code § Inspects SMTP, HTTP, POP 3 and FTP Internet traffic § § § § © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential § Network-based anti-x protection (anti-spam, anti-malware, antiphishing, anti-virus) for web and email traffic § URL filtering for inappropriate web access. § Track, log, and control Internet URL access; allowing both auditing and enforcement of security policy 37
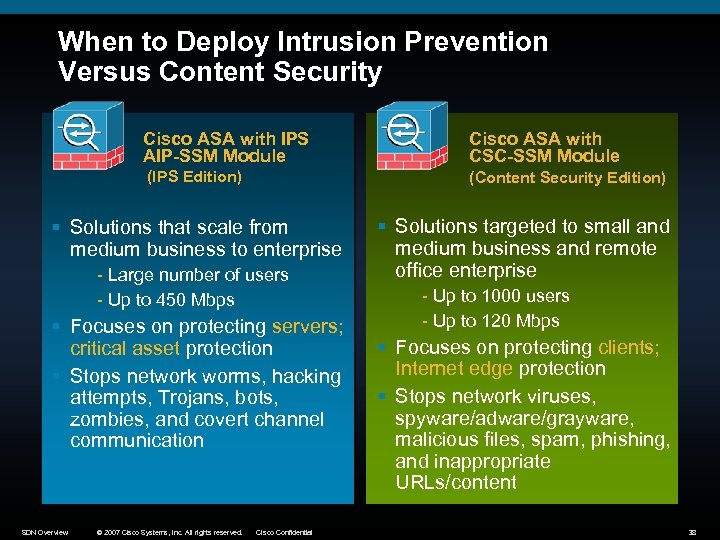
When to Deploy Intrusion Prevention Versus Content Security Cisco ASA with IPS AIP-SSM Module Cisco ASA with CSC-SSM Module (IPS Edition) (Content Security Edition) § Solutions that scale from medium business to enterprise - Large number of users - Up to 450 Mbps § Focuses on protecting servers; critical asset protection § Stops network worms, hacking attempts, Trojans, bots, zombies, and covert channel communication SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential § Solutions targeted to small and medium business and remote office enterprise - Up to 1000 users - Up to 120 Mbps § Focuses on protecting clients; Internet edge protection § Stops network viruses, spyware/adware/grayware, malicious files, spam, phishing, and inappropriate URLs/content 38

How to Sell Cisco ASA in SMB Security § Identify SMBs whose security needs have evolved Increased collaboration with partners and customers across the Internet Need protection from proliferation of more sophisticated attacks Increased expectation of the level of access by remote users or mobile devices Security for compliance such as Payment Card Industry (PCI) requiring all businesses handling credit card data to have a secure network (including a Vo. IP network) § Identify existing Cisco PIX customers to migrate Customers with expanding locations (stores, offices, warehouses) Protection of new applications such as Unified Communications Greater performance needed More protection and security services needed such as intrusion prevention services, content security and more SSL VPN for secure connectivity services to connect remote workers and partners SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 39
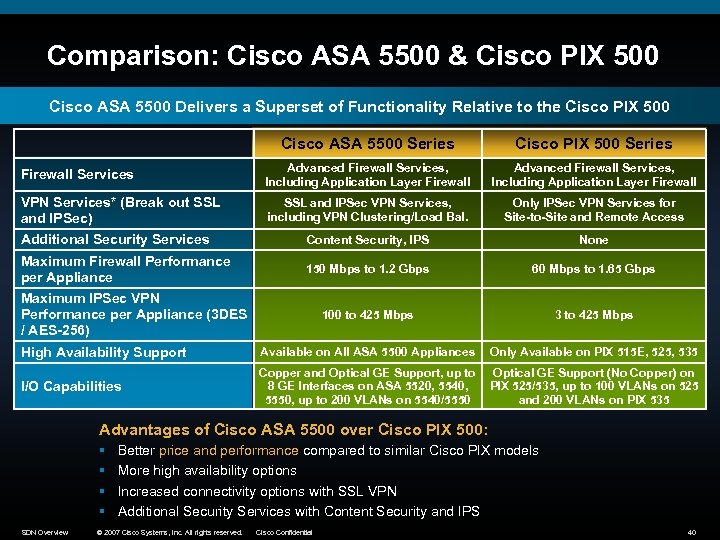
Comparison: Cisco ASA 5500 & Cisco PIX 500 Cisco ASA 5500 Delivers a Superset of Functionality Relative to the Cisco PIX 500 Cisco ASA 5500 Series Cisco PIX 500 Series Firewall Services Advanced Firewall Services, Including Application Layer Firewall VPN Services* (Break out SSL and IPSec) SSL and IPSec VPN Services, including VPN Clustering/Load Bal. Only IPSec VPN Services for Site-to-Site and Remote Access Additional Security Services Content Security, IPS None Maximum Firewall Performance per Appliance 150 Mbps to 1. 2 Gbps 60 Mbps to 1. 65 Gbps 100 to 425 Mbps 3 to 425 Mbps High Availability Support Available on All ASA 5500 Appliances Only Available on PIX 515 E, 525, 535 I/O Capabilities Copper and Optical GE Support, up to 8 GE Interfaces on ASA 5520, 5540, 5550, up to 200 VLANs on 5540/5550 Optical GE Support (No Copper) on PIX 525/535, up to 100 VLANs on 525 and 200 VLANs on PIX 535 Maximum IPSec VPN Performance per Appliance (3 DES / AES-256) Advantages of Cisco ASA 5500 over Cisco PIX 500: § § SDN Overview Better price and performance compared to similar Cisco PIX models More high availability options Increased connectivity options with SSL VPN Additional Security Services with Content Security and IPS © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 40

Recommended Migration Path for Cisco PIX Security Appliance Customers Cisco ASA 5505 Series Key Migration Benefits • 1. 5 - 2. 5 X firewall throughput • 3 - 33 X VPN throughput • 8 port switch with 2 Po. E ports • VLAN support (20 with Sec+) • Supports SSL VPN • Modular for future upgrades Cisco PIX 501 Series SDN Overview Cisco PIX 506 E Series Cisco ASA 5510 / 5520 Series Cisco ASA 5520 / 5540 Series Cisco ASA 5550 / 5580 Series Key Migration Benefits • 1. 6 - 2. 4 x firewall throughput • 2. 3 - 3 x scalability (conns/sec) • Gigabit Ethernet support • A/A solution costs 30% less • VPN clustering/load balancing • Supports IPS, CSC, SSL VPN Key Migration Benefits • 1. 5 - 2 x firewall throughput • 1. 3 - 2. 7 x scalability • Supports 3 X Gig. E density • A/A solution costs 30% less • VPN clustering/load balancing • Supports IPS, CSC, SSL VPN Key Migration Benefits • 2 - 20 x real-world FW throughput • 2 - 8 x scalability (conns/sec) • Supports SSL VPN, inc. clus/LB • 10 GE I/O support (5580) • Supports 2. 5 x GE density (5580) • A/A solution costs 35% less Cisco PIX 515 E Series Cisco PIX 525 Series Cisco PIX 535 Series © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 41
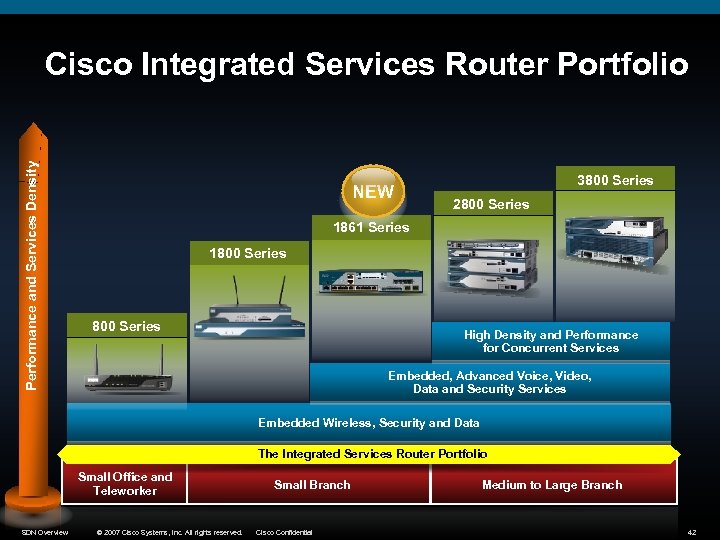
Performance and Services Density Cisco Integrated Services Router Portfolio NEW 3800 Series 2800 Series 1861 Series 1800 Series High Density and Performance for Concurrent Services Embedded, Advanced Voice, Video, Data and Security Services Embedded Wireless, Security and Data The Integrated Services Router Portfolio Small Office and Teleworker SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Small Branch Cisco Confidential Medium to Large Branch 42
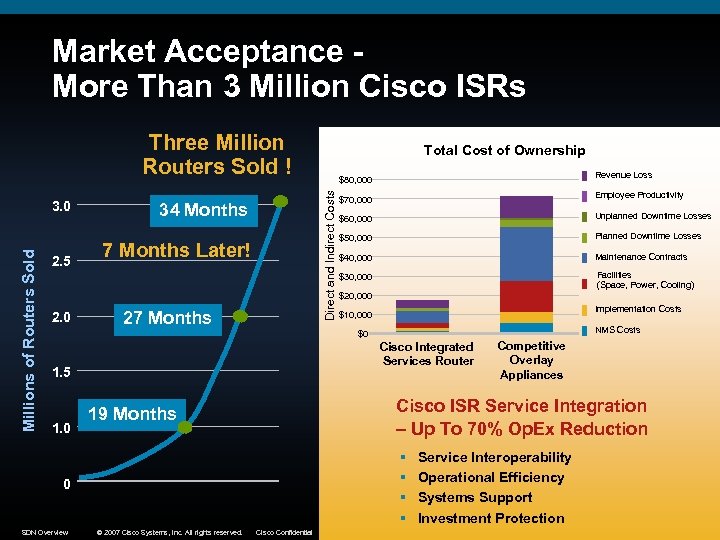
Market Acceptance More Than 3 Million Cisco ISRs Three Million Routers Sold ! 2. 5 2. 0 34 Months 7 Months Later! 27 Months Revenue Loss $80, 000 Direct and Indirect Costs Millions of Routers Sold 3. 0 Total Cost of Ownership $70, 000 Employee Productivity $60, 000 Unplanned Downtime Losses $50, 000 Planned Downtime Losses $40, 000 Maintenance Contracts $30, 000 Facilities (Space, Power, Cooling) $20, 000 Implementation Costs $10, 000 NMS Costs $0 Cisco Integrated Services Router 1. 5 1. 0 Cisco ISR Service Integration – Up To 70% Op. Ex Reduction 19 Months § § 0 SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Competitive Overlay Appliances Cisco Confidential Service Interoperability Operational Efficiency Systems Support Investment Protection 43

How to Sell Secure WAN? Identify Opportunities Qualify Customers § Any router sale, e. g. network expansion § Identify business needs – use secure WAN qualification questions § Greenfield taking advantage of new applications § Migrate $10 B installed base SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential Show The Value § Use ROI tools, case studies § Use TDM presentation, Flash demos, not-for-resale kits, demo vans and Vo. Ds Close The Sale § Now vs later – Security Bundles reduce cost of ownership, minimize exposure 44
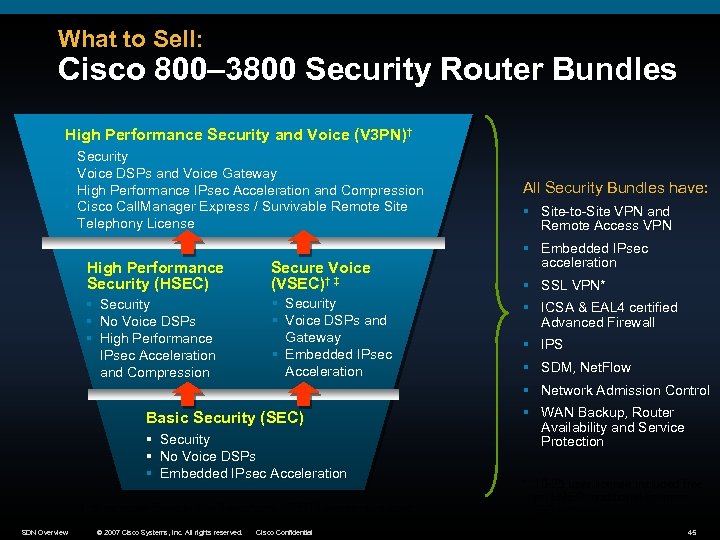
What to Sell: Cisco 800– 3800 Security Router Bundles High Performance Security and Voice (V 3 PN)† § § Security Voice DSPs and Voice Gateway High Performance IPsec Acceleration and Compression Cisco Call. Manager Express / Survivable Remote Site Telephony License High Performance Security (HSEC) Secure Voice (VSEC)† ‡ § Security § No Voice DSPs § High Performance IPsec Acceleration and Compression § Security § Voice DSPs and Gateway § Embedded IPsec Acceleration All Security Bundles have: § Site-to-Site VPN and Remote Access VPN § Embedded IPsec acceleration § SSL VPN* § ICSA & EAL 4 certified Advanced Firewall § IPS § SDM, Net. Flow § Network Admission Control Basic Security (SEC) § Security § No Voice DSPs § Embedded IPsec Acceleration † Survivable Remote Site Telephony (SRST) version available ‡ Cisco Call. Manager Express (CCME) version available SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential § WAN Backup, Router Availability and Service Protection * 10 -25 user license included free on HSEC; additional licenses $30 per user 45
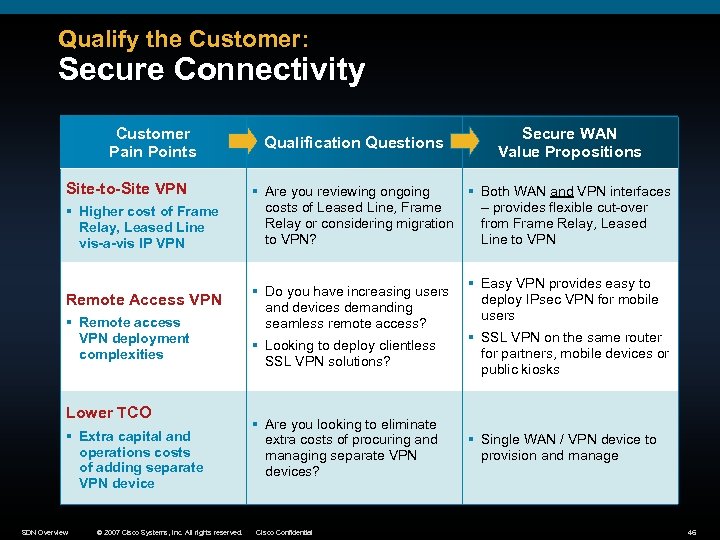
Qualify the Customer: Secure Connectivity Customer Pain Points Site-to-Site VPN § Higher cost of Frame Relay, Leased Line vis-a-vis IP VPN Remote Access VPN § Remote access VPN deployment complexities Lower TCO § Extra capital and operations costs of adding separate VPN device SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Qualification Questions Secure WAN Value Propositions § Are you reviewing ongoing § Both WAN and VPN interfaces costs of Leased Line, Frame – provides flexible cut-over Relay or considering migration from Frame Relay, Leased to VPN? Line to VPN § Do you have increasing users and devices demanding seamless remote access? § Easy VPN provides easy to deploy IPsec VPN for mobile users § Looking to deploy clientless SSL VPN solutions? § SSL VPN on the same router for partners, mobile devices or public kiosks § Are you looking to eliminate extra costs of procuring and managing separate VPN devices? § Single WAN / VPN device to provision and manage Cisco Confidential 46
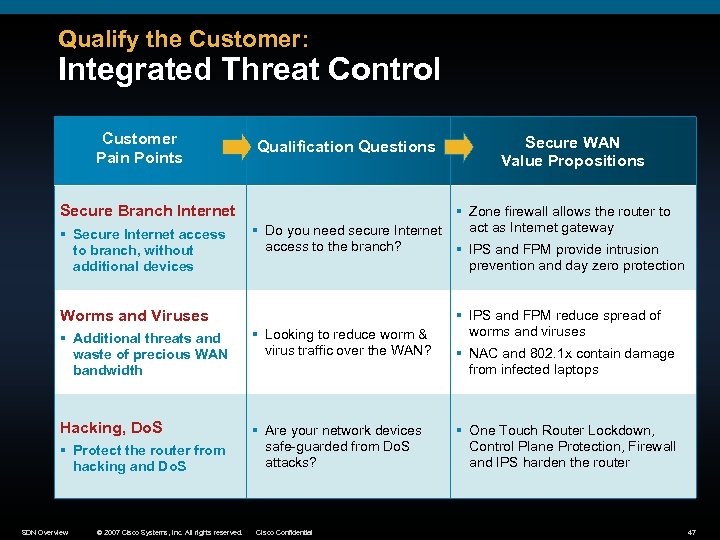
Qualify the Customer: Integrated Threat Control Customer Pain Points Secure Branch Internet § Secure Internet access to branch, without additional devices Qualification Questions § Zone firewall allows the router to act as Internet gateway § Do you need secure Internet access to the branch? § IPS and FPM provide intrusion prevention and day zero protection Worms and Viruses § Additional threats and waste of precious WAN bandwidth § Looking to reduce worm & virus traffic over the WAN? Hacking, Do. S § Are your network devices safe-guarded from Do. S attacks? § Protect the router from hacking and Do. S SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Secure WAN Value Propositions Cisco Confidential § IPS and FPM reduce spread of worms and viruses § NAC and 802. 1 x contain damage from infected laptops § One Touch Router Lockdown, Control Plane Protection, Firewall and IPS harden the router 47
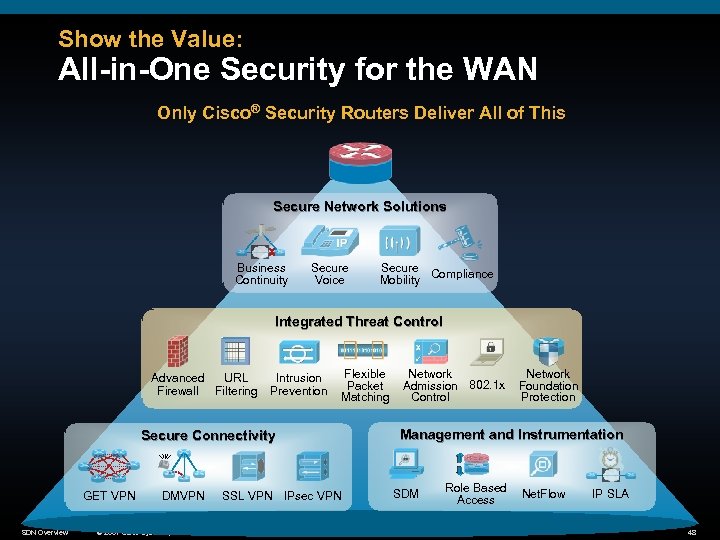
Show the Value: All-in-One Security for the WAN Only Cisco® Security Routers Deliver All of This Secure Network Solutions Business Continuity Secure Voice Secure Compliance Mobility Integrated Threat Control Advanced URL Firewall Filtering Intrusion Prevention Flexible Packet Matching Secure Connectivity GET VPN SDN Overview DMVPN SSL VPN IPsec VPN © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential Network Admission 802. 1 x Control Network Foundation Protection Management and Instrumentation SDM Role Based Access Net. Flow IP SLA 48
Show the Value: Top Reasons to Buy Security Routers 1. PROTECT THE ROUTER ITSELF – your first line of defense 2. A SINGLE BREACH could gravely impact the business 3. Advanced backup and teleworking for BUSINESS CONTINUITY 4. COMPLY with Government data and network privacy laws 5. Consolidate voice/video/data and wired/wireless SECURELY 6. Advanced ENCRYPTION for voice conversations and signaling 7. New ISRs deliver wire-rate PERFORMANCE WITH SERVICES 8. Easy to MANAGE a single-box Router/VPN/Firewall/IPS solution 9. 10. SDN Overview REDUCE COST of service and subscription: single contract 30 -40% SAVINGS built into Security Router bundles © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 49

Responses to Potential Objections Objection: There’s already a firewall behind the router Response: ü The firewall does not protect the mission-critical router – the router faces the Internet while the firewall is behind the router ü No IPS, IPsec VPN, SSL VPN, URL Filtering, etc. on most legacy firewalls – require multiple devices ü Ongoing support and maintenance cost of existing firewalls may pay for the life-time costs of a Cisco router security bundle Objection: Can the router handle security and routing with adequate performance Response: ü YES – ISRs are designed from ground up to run WAN, LAN, WLAN, Security, and IPC services concurrently ü About 2 million Cisco ISRs now deployed worldwide Objection: I can always upgrade the router later to add security Response: ü You save 30 -40% typically by buying security router bundles now as compared to upgrading the router later ü Exposure to risk – A single security breach can be several times the incremental cost of a security router bundle SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 50

Summary § Cisco is the Network Security Market Leader – 41%* § Adaptive Security Appliances provide best of breed security services § Secure Integrated Services Routers have excellent value for your customers combining routing and security in one single platform § For more details http: //www. cisco. com/web/partners/sell/technology/security/smb. html *Infonetics Q 3 2007 Report SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. *Infonectics 3 Q, 2007 Report Cisco Confidential 51

SDN Overview © 2007 Cisco Systems, Inc. All rights reserved. Cisco Confidential 52
a6c90b35f7526add32279e5f081d5ba8.ppt