350ef17a072d907904b02e90236fb097.ppt
- Количество слайдов: 62
 How to Make Windows Secure -with Free Software Howard Fosdick (C) 2006. 5 FCI V 1. 2
How to Make Windows Secure -with Free Software Howard Fosdick (C) 2006. 5 FCI V 1. 2
 Who Am I ? * DBA for Oracle (also DB 2 & SQL Server) * A founder of IDUG, MDUG, CAMP * Management Consultant * Author Rexx Programmers Reference (see www. amazon. com/rexx www. Rexx. Info. org ) Independent Contractor -hfosdick at the domain compuserve. com
Who Am I ? * DBA for Oracle (also DB 2 & SQL Server) * A founder of IDUG, MDUG, CAMP * Management Consultant * Author Rexx Programmers Reference (see www. amazon. com/rexx www. Rexx. Info. org ) Independent Contractor -hfosdick at the domain compuserve. com
 This Presentation is Based On-- * Operating Systems principles (I taught cs 550 at IIT) * Hands-on with the products * My column in Enterprise Open Systems Journal www. eosj. com
This Presentation is Based On-- * Operating Systems principles (I taught cs 550 at IIT) * Hands-on with the products * My column in Enterprise Open Systems Journal www. eosj. com
 Outline Poof ! I. Malware II. Why is Windows Insecure? III. FOSS to Secure Windows IV. Microsoft Alternatives V. Fallout ?
Outline Poof ! I. Malware II. Why is Windows Insecure? III. FOSS to Secure Windows IV. Microsoft Alternatives V. Fallout ?
 I. Malware
I. Malware
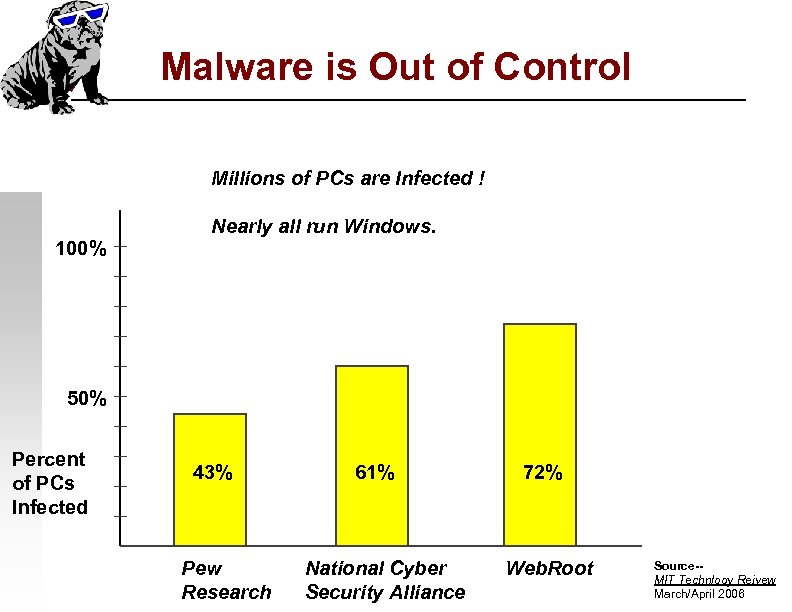 Malware is Out of Control Millions of PCs are Infected ! 100% Nearly all run Windows. 50% Percent of PCs Infected 43% Pew Research 61% National Cyber Security Alliance 72% Web. Root Source-MIT Technlogy Reivew March/April 2006
Malware is Out of Control Millions of PCs are Infected ! 100% Nearly all run Windows. 50% Percent of PCs Infected 43% Pew Research 61% National Cyber Security Alliance 72% Web. Root Source-MIT Technlogy Reivew March/April 2006
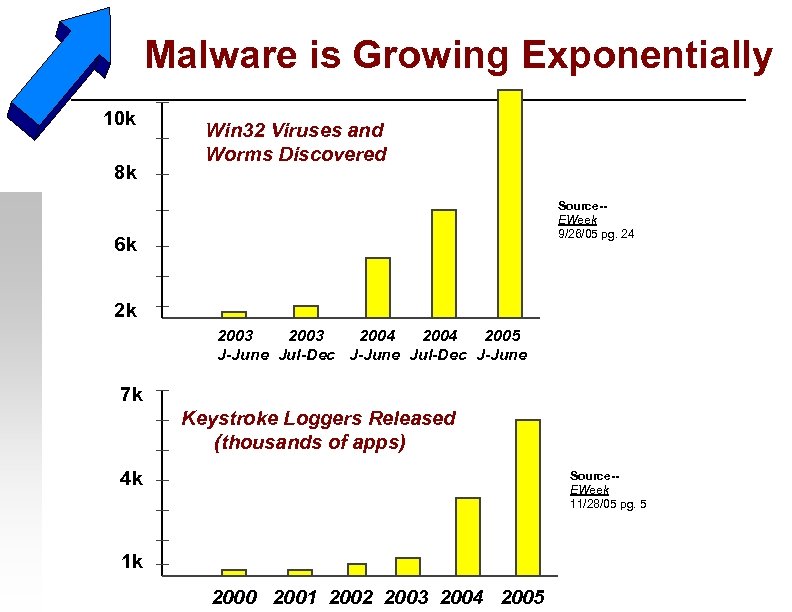 Malware is Growing Exponentially 10 k 8 k Win 32 Viruses and Worms Discovered Source-EWeek 9/26/05 pg. 24 6 k 2 k 2003 2004 2005 J-June Jul-Dec J-June 7 k Keystroke Loggers Released (thousands of apps) 4 k Source-EWeek 11/28/05 pg. 5 1 k 2000 2001 2002 2003 2004 2005
Malware is Growing Exponentially 10 k 8 k Win 32 Viruses and Worms Discovered Source-EWeek 9/26/05 pg. 24 6 k 2 k 2003 2004 2005 J-June Jul-Dec J-June 7 k Keystroke Loggers Released (thousands of apps) 4 k Source-EWeek 11/28/05 pg. 5 1 k 2000 2001 2002 2003 2004 2005
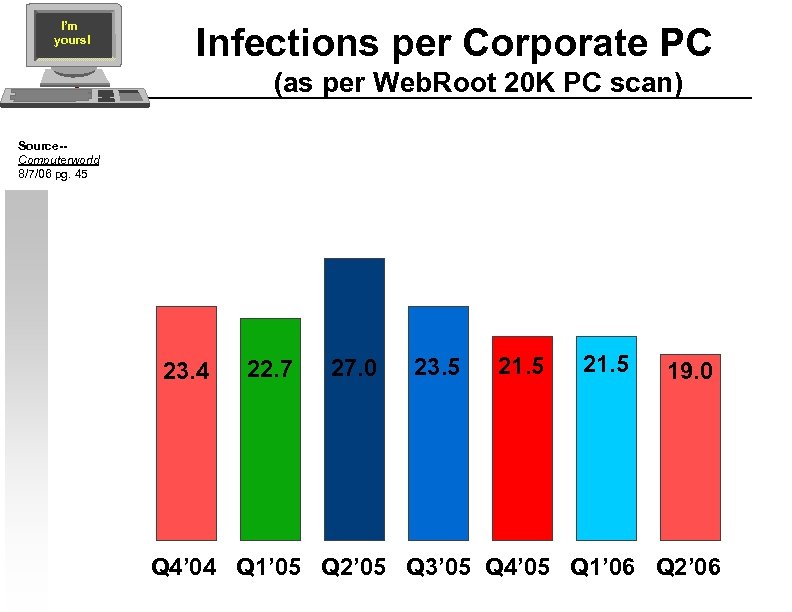 I’m yours! Infections per Corporate PC (as per Web. Root 20 K PC scan) Source-Computerworld 8/7/06 pg. 45 23. 4 22. 7 27. 0 23. 5 21. 5 19. 0 Q 4’ 04 Q 1’ 05 Q 2’ 05 Q 3’ 05 Q 4’ 05 Q 1’ 06 Q 2’ 06
I’m yours! Infections per Corporate PC (as per Web. Root 20 K PC scan) Source-Computerworld 8/7/06 pg. 45 23. 4 22. 7 27. 0 23. 5 21. 5 19. 0 Q 4’ 04 Q 1’ 05 Q 2’ 05 Q 3’ 05 Q 4’ 05 Q 1’ 06 Q 2’ 06
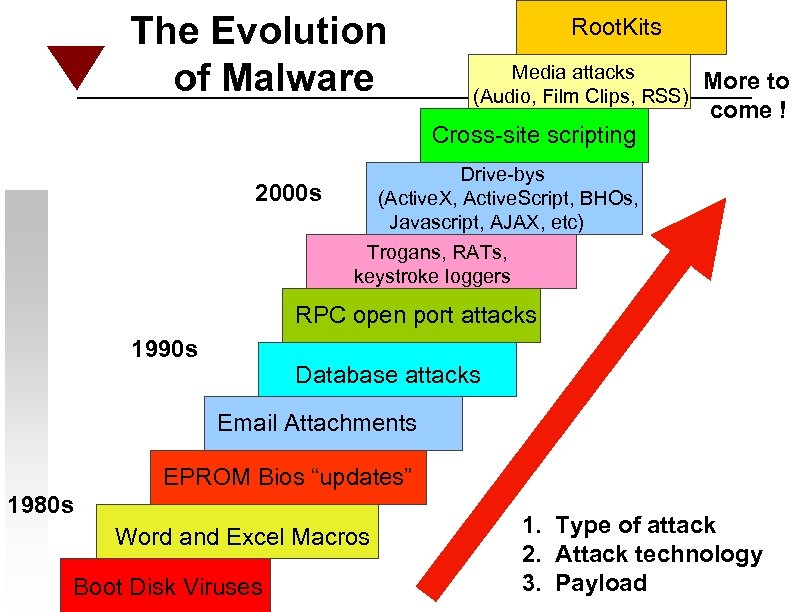 The Evolution of Malware Root. Kits Media attacks (Audio, Film Clips, RSS) Cross-site scripting 2000 s More to come ! Drive-bys (Active. X, Active. Script, BHOs, Javascript, AJAX, etc) Trogans, RATs, keystroke loggers RPC open port attacks 1990 s Database attacks Email Attachments EPROM Bios “updates” 1980 s Word and Excel Macros Boot Disk Viruses 1. Type of attack 2. Attack technology 3. Payload
The Evolution of Malware Root. Kits Media attacks (Audio, Film Clips, RSS) Cross-site scripting 2000 s More to come ! Drive-bys (Active. X, Active. Script, BHOs, Javascript, AJAX, etc) Trogans, RATs, keystroke loggers RPC open port attacks 1990 s Database attacks Email Attachments EPROM Bios “updates” 1980 s Word and Excel Macros Boot Disk Viruses 1. Type of attack 2. Attack technology 3. Payload
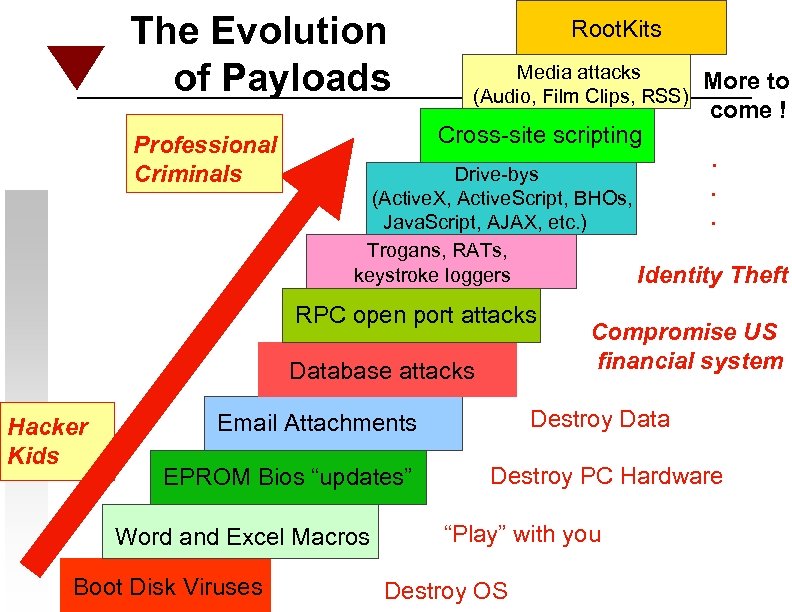 The Evolution of Payloads Professional Criminals Root. Kits Media attacks (Audio, Film Clips, RSS) Cross-site scripting Database attacks EPROM Bios “updates” Word and Excel Macros Destroy PC Hardware “Play” with you Destroy OS Theft Compromise US financial system Destroy Data Email Attachments Boot Disk Viruses . . . Drive-bys (Active. X, Active. Script, BHOs, Java. Script, AJAX, etc. ) Trogans, RATs, keystroke loggers Identity RPC open port attacks Hacker Kids More to come !
The Evolution of Payloads Professional Criminals Root. Kits Media attacks (Audio, Film Clips, RSS) Cross-site scripting Database attacks EPROM Bios “updates” Word and Excel Macros Destroy PC Hardware “Play” with you Destroy OS Theft Compromise US financial system Destroy Data Email Attachments Boot Disk Viruses . . . Drive-bys (Active. X, Active. Script, BHOs, Java. Script, AJAX, etc. ) Trogans, RATs, keystroke loggers Identity RPC open port attacks Hacker Kids More to come !
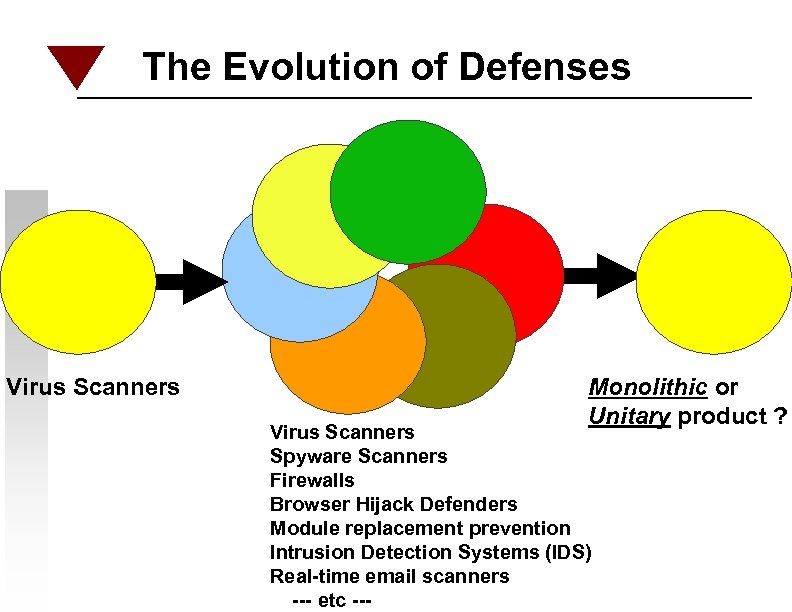 The Evolution of Defenses Virus Scanners Monolithic or Unitary product ? Virus Scanners Spyware Scanners Firewalls Browser Hijack Defenders Module replacement prevention Intrusion Detection Systems (IDS) Real-time email scanners --- etc ---
The Evolution of Defenses Virus Scanners Monolithic or Unitary product ? Virus Scanners Spyware Scanners Firewalls Browser Hijack Defenders Module replacement prevention Intrusion Detection Systems (IDS) Real-time email scanners --- etc ---
 II. Why is Windows Insecure ?
II. Why is Windows Insecure ?
 Why is Windows Insecure ? * “Windows is a target because it predominates” -- This explains why Windows is subject to attacks, not why it succumbs to them * “Any other OS would have the same problems subject to the same attacks” -- Not true! OS’s are as different as programming languages. They have different design goals, philosophies, etc Some are more secure than Windows, others are less secure.
Why is Windows Insecure ? * “Windows is a target because it predominates” -- This explains why Windows is subject to attacks, not why it succumbs to them * “Any other OS would have the same problems subject to the same attacks” -- Not true! OS’s are as different as programming languages. They have different design goals, philosophies, etc Some are more secure than Windows, others are less secure.
 Why is Windows Insecure ? To simply say that “Windows is insecure” is wrong. The problem is that Windows security is inadequate for its role as the untrained public’s primary--- PC operating system -- for Internet access Windows’ security is just fine for many other purposes.
Why is Windows Insecure ? To simply say that “Windows is insecure” is wrong. The problem is that Windows security is inadequate for its role as the untrained public’s primary--- PC operating system -- for Internet access Windows’ security is just fine for many other purposes.
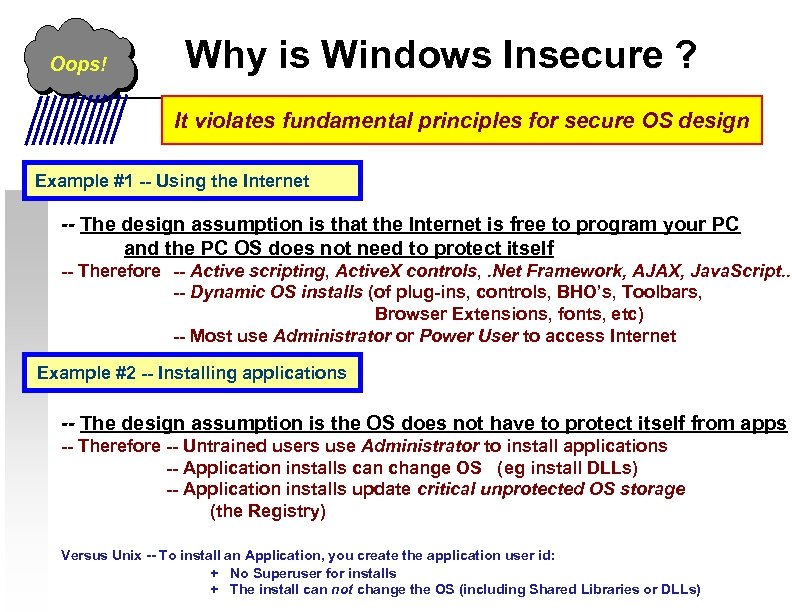 Oops! Why is Windows Insecure ? It violates fundamental principles for secure OS design Example #1 ---- Using the Internet Example #1 Using the Internet -- The design assumption is that the Internet is free to program your PC and the PC OS does not need to protect itself -- Therefore -- Active scripting, Active. X controls, . Net Framework, AJAX, Java. Script. . -- Dynamic OS installs (of plug-ins, controls, BHO’s, Toolbars, Browser Extensions, fonts, etc) -- Most use Administrator or Power User to access Internet Example #2 Installing applications Example #2 -- -- Installing applications -- The design assumption is the OS does not have to protect itself from apps -- Therefore -- Untrained users use Administrator to install applications -- Application installs can change OS (eg install DLLs) -- Application installs update critical unprotected OS storage (the Registry) Versus Unix -- To install an Application, you create the application user id: + No Superuser for installs + The install can not change the OS (including Shared Libraries or DLLs)
Oops! Why is Windows Insecure ? It violates fundamental principles for secure OS design Example #1 ---- Using the Internet Example #1 Using the Internet -- The design assumption is that the Internet is free to program your PC and the PC OS does not need to protect itself -- Therefore -- Active scripting, Active. X controls, . Net Framework, AJAX, Java. Script. . -- Dynamic OS installs (of plug-ins, controls, BHO’s, Toolbars, Browser Extensions, fonts, etc) -- Most use Administrator or Power User to access Internet Example #2 Installing applications Example #2 -- -- Installing applications -- The design assumption is the OS does not have to protect itself from apps -- Therefore -- Untrained users use Administrator to install applications -- Application installs can change OS (eg install DLLs) -- Application installs update critical unprotected OS storage (the Registry) Versus Unix -- To install an Application, you create the application user id: + No Superuser for installs + The install can not change the OS (including Shared Libraries or DLLs)
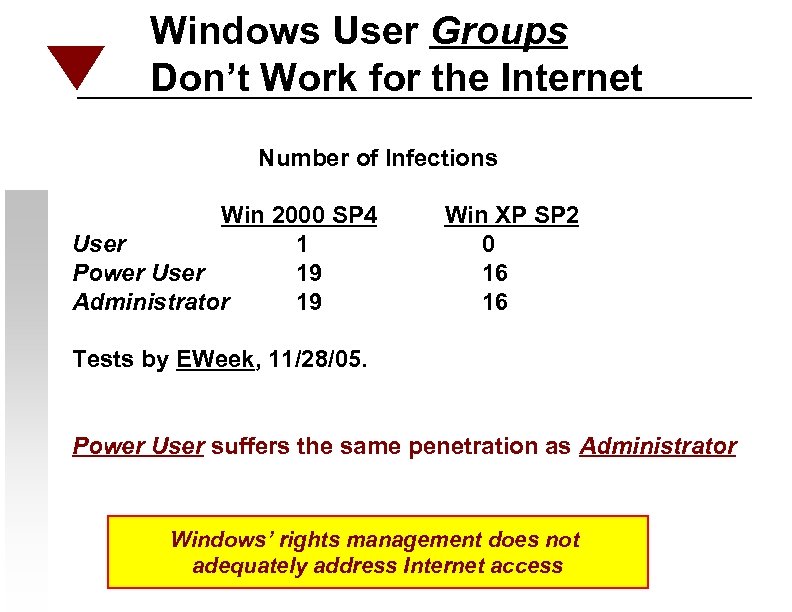 Windows User Groups Don’t Work for the Internet Number of Infections Win 2000 SP 4 User 1 Power User 19 Administrator 19 Win XP SP 2 0 16 16 Tests by EWeek, 11/28/05. Power User suffers the same penetration as Administrator Windows’ rights management does not adequately address Internet access
Windows User Groups Don’t Work for the Internet Number of Infections Win 2000 SP 4 User 1 Power User 19 Administrator 19 Win XP SP 2 0 16 16 Tests by EWeek, 11/28/05. Power User suffers the same penetration as Administrator Windows’ rights management does not adequately address Internet access
 Oops! Technologies for OS Security ? Where’s the sandbox ? Where’s VM (virtualization technologies) ? What about user rights management ? Ring privileges that work for the requirements ? A system of id groups that make sense! ? Special “Browser State” run level ? Locks and keys ? Other security techniques
Oops! Technologies for OS Security ? Where’s the sandbox ? Where’s VM (virtualization technologies) ? What about user rights management ? Ring privileges that work for the requirements ? A system of id groups that make sense! ? Special “Browser State” run level ? Locks and keys ? Other security techniques
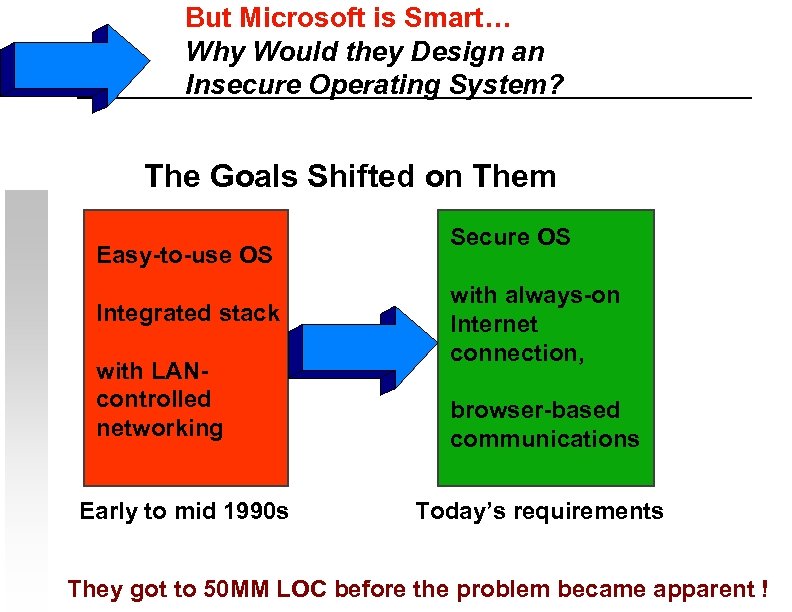 But Microsoft is Smart… Why Would they Design an Insecure Operating System? The Goals Shifted on Them Easy-to-use OS Integrated stack with LANcontrolled networking Early to mid 1990 s Secure OS with always-on Internet connection, browser-based communications Today’s requirements They got to 50 MM LOC before the problem became apparent !
But Microsoft is Smart… Why Would they Design an Insecure Operating System? The Goals Shifted on Them Easy-to-use OS Integrated stack with LANcontrolled networking Early to mid 1990 s Secure OS with always-on Internet connection, browser-based communications Today’s requirements They got to 50 MM LOC before the problem became apparent !
 But Microsoft is Smart… Why Would they Design an Insecure Operating System? -- Microsoft chose ease of use and integration over security * This is how they won the “suite wars” (vs. Wordperfect, Lotus) -- The “integrated stack” yielded their desktop monopoly -- by locking out competing products -- Gates did not understand the importance of the Internet until it was too late and they had 50 MM lines of legacy code -- Bill Gates’ The Road Ahead (1995) had 2 pages on Internet! (It was quickly yanked from shelves and quietly replaced with a re-written version with longer Internet coverage) -- “When the Internet really took off, we were surprised…” --Bill Gates, Preface to the 2 nd Edition 1996
But Microsoft is Smart… Why Would they Design an Insecure Operating System? -- Microsoft chose ease of use and integration over security * This is how they won the “suite wars” (vs. Wordperfect, Lotus) -- The “integrated stack” yielded their desktop monopoly -- by locking out competing products -- Gates did not understand the importance of the Internet until it was too late and they had 50 MM lines of legacy code -- Bill Gates’ The Road Ahead (1995) had 2 pages on Internet! (It was quickly yanked from shelves and quietly replaced with a re-written version with longer Internet coverage) -- “When the Internet really took off, we were surprised…” --Bill Gates, Preface to the 2 nd Edition 1996
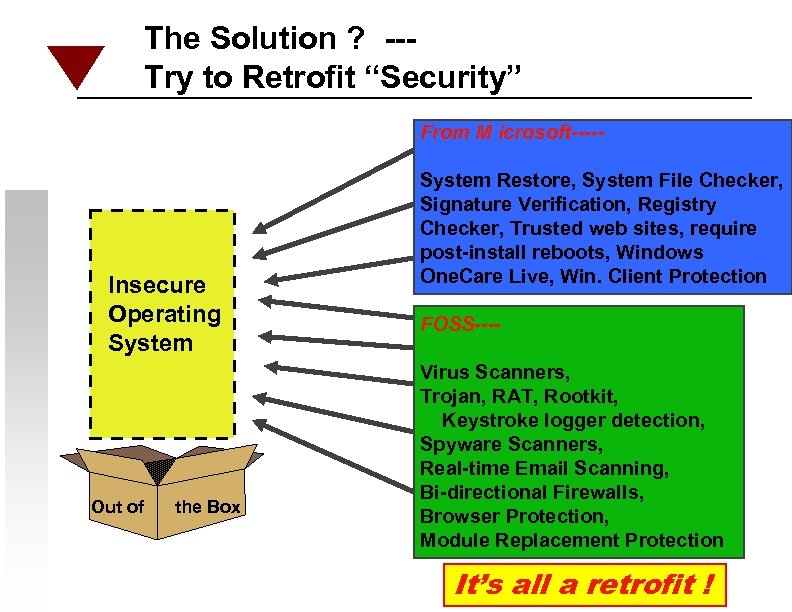 The Solution ? --Try to Retrofit “Security” From M icrosoft----- Insecure Operating System Out of the Box System Restore, System File Checker, Signature Verification, Registry Checker, Trusted web sites, require post-install reboots, Windows One. Care Live, Win. Client Protection FOSS---Virus Scanners, Trojan, RAT, Rootkit, Keystroke logger detection, Spyware Scanners, Real-time Email Scanning, Bi-directional Firewalls, Browser Protection, Module Replacement Protection It’s all a retrofit !
The Solution ? --Try to Retrofit “Security” From M icrosoft----- Insecure Operating System Out of the Box System Restore, System File Checker, Signature Verification, Registry Checker, Trusted web sites, require post-install reboots, Windows One. Care Live, Win. Client Protection FOSS---Virus Scanners, Trojan, RAT, Rootkit, Keystroke logger detection, Spyware Scanners, Real-time Email Scanning, Bi-directional Firewalls, Browser Protection, Module Replacement Protection It’s all a retrofit !
 What About Vista ? -- Trustworthy Computing announced Jan. 2002 -- Microsoft’s promise to fix security in every prior release ========================= + Vista brings incremental improvements. . . again ? ? Sandbox for IE Better user rights management Drive encryption More secure Registry Speculative -- I’m not a Vista tester, Vista not yet finalized
What About Vista ? -- Trustworthy Computing announced Jan. 2002 -- Microsoft’s promise to fix security in every prior release ========================= + Vista brings incremental improvements. . . again ? ? Sandbox for IE Better user rights management Drive encryption More secure Registry Speculative -- I’m not a Vista tester, Vista not yet finalized
 III. FOSS to Secure Windows
III. FOSS to Secure Windows
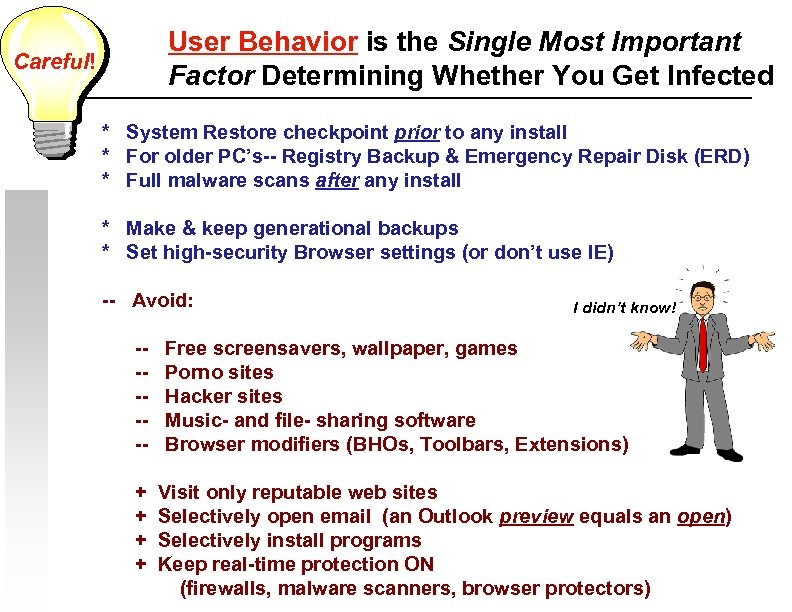 User Behavior is the Single Most Important Factor Determining Whether You Get Infected Careful! * System Restore checkpoint prior to any install * For older PC’s-- Registry Backup & Emergency Repair Disk (ERD) * Full malware scans after any install * Make & keep generational backups * Set high-security Browser settings (or don’t use IE) -- Avoid: -----+ + I didn’t know! Free screensavers, wallpaper, games Porno sites Hacker sites Music- and file- sharing software Browser modifiers (BHOs, Toolbars, Extensions) Visit only reputable web sites Selectively open email (an Outlook preview equals an open) Selectively install programs Keep real-time protection ON (firewalls, malware scanners, browser protectors)
User Behavior is the Single Most Important Factor Determining Whether You Get Infected Careful! * System Restore checkpoint prior to any install * For older PC’s-- Registry Backup & Emergency Repair Disk (ERD) * Full malware scans after any install * Make & keep generational backups * Set high-security Browser settings (or don’t use IE) -- Avoid: -----+ + I didn’t know! Free screensavers, wallpaper, games Porno sites Hacker sites Music- and file- sharing software Browser modifiers (BHOs, Toolbars, Extensions) Visit only reputable web sites Selectively open email (an Outlook preview equals an open) Selectively install programs Keep real-time protection ON (firewalls, malware scanners, browser protectors)
 Free! Where to Download Products * www. The. Free. Country. com * www. Download. com * www. Major. Geeks. com . . . Sites offer-+ Central repository for Downloads + Reviews, ratings + Product descriptions Good also for learning about Windows security ! Keep a copy of what you download, free status sometimes changes ! --> or google “Last Freeware Version” (LFV)
Free! Where to Download Products * www. The. Free. Country. com * www. Download. com * www. Major. Geeks. com . . . Sites offer-+ Central repository for Downloads + Reviews, ratings + Product descriptions Good also for learning about Windows security ! Keep a copy of what you download, free status sometimes changes ! --> or google “Last Freeware Version” (LFV)
 Firewalls -- Microsoft’s firewall is uni-directional & inadequate. -- Because Microsoft is a spyware vendor. ----- WGA scandal WMP scandal WPA controversy Windows Search phones home Alexa controversy Win-98 registration scandal Embedded GUIDs Index. dat files many others Why? Examples-- in you out * Bidirectional firewall is a must -+ + Zone. Alarm Tiny Kerio Agnitum => Very widely used, easy user interface => Small, fast, light, pre-XP (see LFV) => Evolved from Tiny Products I can vouch for personally are in italics
Firewalls -- Microsoft’s firewall is uni-directional & inadequate. -- Because Microsoft is a spyware vendor. ----- WGA scandal WMP scandal WPA controversy Windows Search phones home Alexa controversy Win-98 registration scandal Embedded GUIDs Index. dat files many others Why? Examples-- in you out * Bidirectional firewall is a must -+ + Zone. Alarm Tiny Kerio Agnitum => Very widely used, easy user interface => Small, fast, light, pre-XP (see LFV) => Evolved from Tiny Products I can vouch for personally are in italics
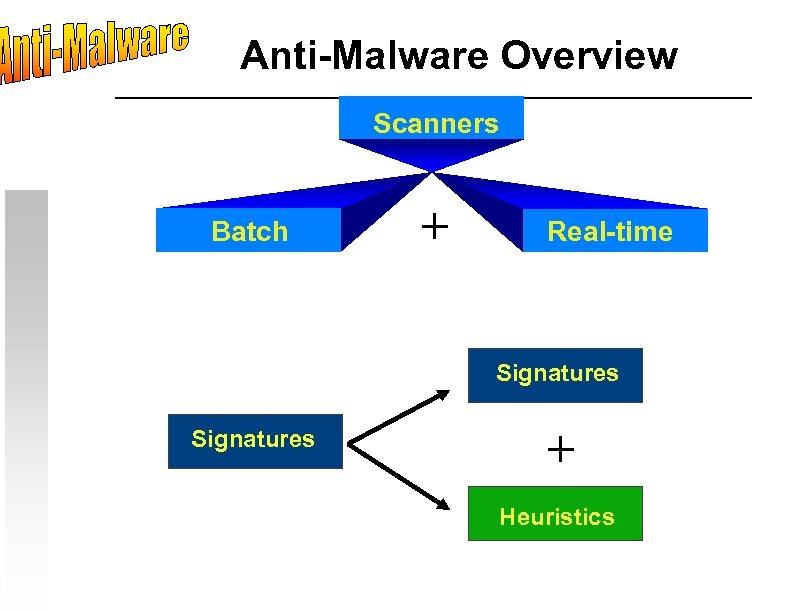 Anti-Malware Overview Scanners Batch + Real-time Signatures + Heuristics
Anti-Malware Overview Scanners Batch + Real-time Signatures + Heuristics
 Anti-Malware Overview Categories: * * Anti-virus Anti-spyware Real-time install prevention Real-time module replacement protection (aka intrusion protection) * Browser hijack prevention * Rootkit detection. . . etc. . . Categories of malware they detect vary. No one product does it all, you need several. Keep definition files updated !
Anti-Malware Overview Categories: * * Anti-virus Anti-spyware Real-time install prevention Real-time module replacement protection (aka intrusion protection) * Browser hijack prevention * Rootkit detection. . . etc. . . Categories of malware they detect vary. No one product does it all, you need several. Keep definition files updated !
 What About Microsoft’s One. Care Live ? + Single-vendor, integrated solution -- Microsoft has a long track record -- As a spyware vendor -- For inadequate security -- Of privacy violations They sold you a leaky boat. . . Now you’re gonna buy your lifeboat from them ?
What About Microsoft’s One. Care Live ? + Single-vendor, integrated solution -- Microsoft has a long track record -- As a spyware vendor -- For inadequate security -- Of privacy violations They sold you a leaky boat. . . Now you’re gonna buy your lifeboat from them ?
 Anti-Virus * These features distinguish the best products: + On-access file scans + Incoming email scanner + Real-time activity scanning Recommendations-+ AVG anti-virus + avast! => As good as any purchased pdt * Lesser products are simple batch scanners (but they may excel at that!) Recommendations-+ Clam. Win (aka Clam. AV) + Bit. Defender Console => Slow scan but finds rootkits, runs on smaller / older PCs => Finds Sony/XCP rootkit
Anti-Virus * These features distinguish the best products: + On-access file scans + Incoming email scanner + Real-time activity scanning Recommendations-+ AVG anti-virus + avast! => As good as any purchased pdt * Lesser products are simple batch scanners (but they may excel at that!) Recommendations-+ Clam. Win (aka Clam. AV) + Bit. Defender Console => Slow scan but finds rootkits, runs on smaller / older PCs => Finds Sony/XCP rootkit
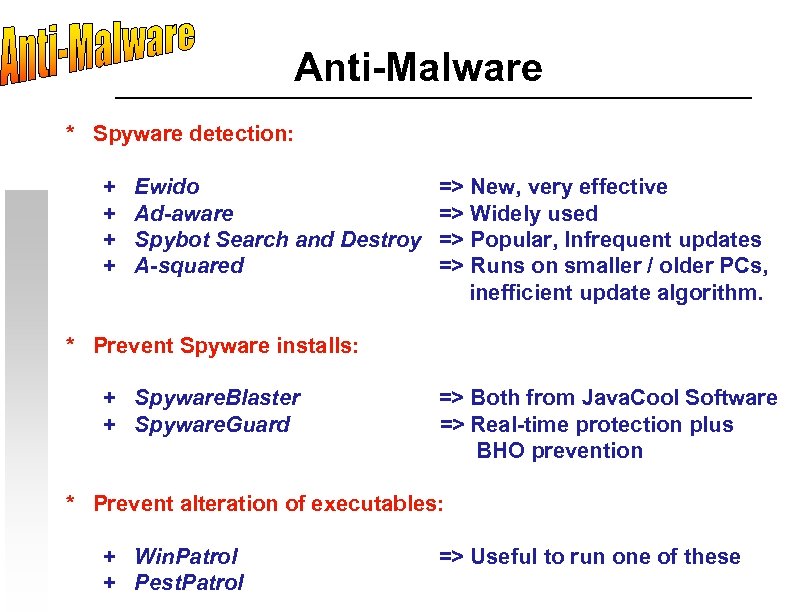 Anti-Malware * Spyware detection: + + Ewido Ad-aware Spybot Search and Destroy A-squared => New, very effective => Widely used => Popular, Infrequent updates => Runs on smaller / older PCs, inefficient update algorithm. * Prevent Spyware installs: + Spyware. Blaster + Spyware. Guard => Both from Java. Cool Software => Real-time protection plus BHO prevention * Prevent alteration of executables: + Win. Patrol + Pest. Patrol => Useful to run one of these
Anti-Malware * Spyware detection: + + Ewido Ad-aware Spybot Search and Destroy A-squared => New, very effective => Widely used => Popular, Infrequent updates => Runs on smaller / older PCs, inefficient update algorithm. * Prevent Spyware installs: + Spyware. Blaster + Spyware. Guard => Both from Java. Cool Software => Real-time protection plus BHO prevention * Prevent alteration of executables: + Win. Patrol + Pest. Patrol => Useful to run one of these
 Anti-Malware * Startup protection: + Startup Cop + MSConfig => Easy, works great => Built into Windows * Browser hijacker protection: => Protects you from browser hijacking through secret installs of Browser Help Objects, Browser Extensions, Toolbars, etc. + Don’t use IE => Use Firefox, Mozilla or Opera + Or set IE Options (Security, Privacy, Advanced) very carefully! + Hijack This! => Thorough, requires expertise + Spyware. Guard => Prevents malware installs
Anti-Malware * Startup protection: + Startup Cop + MSConfig => Easy, works great => Built into Windows * Browser hijacker protection: => Protects you from browser hijacking through secret installs of Browser Help Objects, Browser Extensions, Toolbars, etc. + Don’t use IE => Use Firefox, Mozilla or Opera + Or set IE Options (Security, Privacy, Advanced) very carefully! + Hijack This! => Thorough, requires expertise + Spyware. Guard => Prevents malware installs
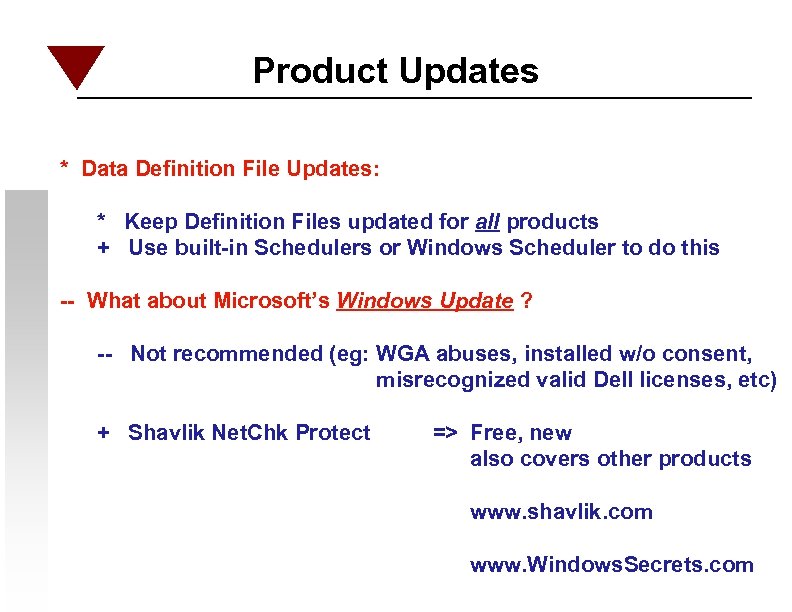 Product Updates * Data Definition File Updates: * Keep Definition Files updated for all products + Use built-in Schedulers or Windows Scheduler to do this -- What about Microsoft’s Windows Update ? -- Not recommended (eg: WGA abuses, installed w/o consent, misrecognized valid Dell licenses, etc) + Shavlik Net. Chk Protect => Free, new also covers other products www. shavlik. com www. Windows. Secrets. com
Product Updates * Data Definition File Updates: * Keep Definition Files updated for all products + Use built-in Schedulers or Windows Scheduler to do this -- What about Microsoft’s Windows Update ? -- Not recommended (eg: WGA abuses, installed w/o consent, misrecognized valid Dell licenses, etc) + Shavlik Net. Chk Protect => Free, new also covers other products www. shavlik. com www. Windows. Secrets. com
 Rootkits Rootkit -- software that gets Superuser rights and compromises the operating system. New, growing threat. Full Detection Versus Ease of Use Removal ! * Rootkit detection: + + + Rootkit Revealer Anti-Hook Rootkit Detector (RD-CD) Ice. Sword Clam. Win Bit. Defender Console => Thorough, requires expertise => From IIT students => => Finds some Rootkits If a successful Rootkit causes mass re-installs, it could kill Windows in the market place !
Rootkits Rootkit -- software that gets Superuser rights and compromises the operating system. New, growing threat. Full Detection Versus Ease of Use Removal ! * Rootkit detection: + + + Rootkit Revealer Anti-Hook Rootkit Detector (RD-CD) Ice. Sword Clam. Win Bit. Defender Console => Thorough, requires expertise => From IIT students => => Finds some Rootkits If a successful Rootkit causes mass re-installs, it could kill Windows in the market place !
 Your Computer Spies on You ! Windows tracks everything you do Windows Tracks---- All the web sites you visit The email addresses you send to Who creates/edits all Office files Office file editing statistics Puts permanent ID in all Office documents you create Tracks everything you have done recently Why do we care ? -- Identity theft -- Loss of your personal power to businesses & governments Privacy is power, and you have none ! (This is “Trustworthy Computing” ? )
Your Computer Spies on You ! Windows tracks everything you do Windows Tracks---- All the web sites you visit The email addresses you send to Who creates/edits all Office files Office file editing statistics Puts permanent ID in all Office documents you create Tracks everything you have done recently Why do we care ? -- Identity theft -- Loss of your personal power to businesses & governments Privacy is power, and you have none ! (This is “Trustworthy Computing” ? )
 Your Computer Spies on You ! -- When you delete a file, Windows only removes an index pointer to it, the file is still on disk. How long the file remains on disk depends on the disk allocation operations that follow the delete. * Secure deletion (overwriting): + Eraser + BCWipe + Derek’s Boot and Nuke => Shell program => Can also erase disk (see LFV) => Good for volume wiping * Erase temporary file areas: + + Browser option built-in, also cache reset Built-in Disk Cleanup Emp. Runner Empty Temp Folders
Your Computer Spies on You ! -- When you delete a file, Windows only removes an index pointer to it, the file is still on disk. How long the file remains on disk depends on the disk allocation operations that follow the delete. * Secure deletion (overwriting): + Eraser + BCWipe + Derek’s Boot and Nuke => Shell program => Can also erase disk (see LFV) => Good for volume wiping * Erase temporary file areas: + + Browser option built-in, also cache reset Built-in Disk Cleanup Emp. Runner Empty Temp Folders
 Your Computer Spies on You ! -- Windows tracks your recent activities: Delete traces of your recent activities: + Ad-aware + MRU Blaster + Windows Washer => This feature is included -- Windows tracks all web sites you visit: + Index Dat Spy => Lists sites you visited * Erase Internet sites visited logs: + Windows Washer + Purge. IE, Purge. Fox -- Not free after 15 days use
Your Computer Spies on You ! -- Windows tracks your recent activities: Delete traces of your recent activities: + Ad-aware + MRU Blaster + Windows Washer => This feature is included -- Windows tracks all web sites you visit: + Index Dat Spy => Lists sites you visited * Erase Internet sites visited logs: + Windows Washer + Purge. IE, Purge. Fox -- Not free after 15 days use
 Your Computer Spies on You ! -- MS Office -- Keeps Edit Info and GUIDs: Erase document creator, edit statistics: + File Properties Remove GUIDs & other hidden data from Office files: + MS offers manual procedures -- Impractical ! + Doc Scrubber + ID Blaster => Use w/ care My best recommendation-- Replace Microsoft Office with Open. Office
Your Computer Spies on You ! -- MS Office -- Keeps Edit Info and GUIDs: Erase document creator, edit statistics: + File Properties Remove GUIDs & other hidden data from Office files: + MS offers manual procedures -- Impractical ! + Doc Scrubber + ID Blaster => Use w/ care My best recommendation-- Replace Microsoft Office with Open. Office
 Your Computer Spies on You ! -- Data Security Circumvention -* Boot a Live Linux CD (eg Ophcrack or Knoppix) * Use Win 2 K Recovery Disk * Break the password with ntpasswd Therefore you must encrypt data: + Built into Win XP on + Quick. Crypt + Many others -- Transparent & convenient, but used to leave around unencrypted files in Temp area => Work on Files, Folders, Volumes, entire System + Email encryption with: + PGP + GNU Privacy Guard + Hushmail
Your Computer Spies on You ! -- Data Security Circumvention -* Boot a Live Linux CD (eg Ophcrack or Knoppix) * Use Win 2 K Recovery Disk * Break the password with ntpasswd Therefore you must encrypt data: + Built into Win XP on + Quick. Crypt + Many others -- Transparent & convenient, but used to leave around unencrypted files in Temp area => Work on Files, Folders, Volumes, entire System + Email encryption with: + PGP + GNU Privacy Guard + Hushmail
 The Web Spies on You ! You! * Anonymous Surfing Web sites you visit get your: ------- IP address (which may uniquely identify you) OS type and version Browser type and version Where you came in from What you see on their site Your behavior on their site. . . etc. . . To be anonymous to web sites you visit-+ TOR => Firefox with add-ins for anonymity + JAP + I 2 P + Freenet Note-- this is not a Windows issue, it is an Internet issue
The Web Spies on You ! You! * Anonymous Surfing Web sites you visit get your: ------- IP address (which may uniquely identify you) OS type and version Browser type and version Where you came in from What you see on their site Your behavior on their site. . . etc. . . To be anonymous to web sites you visit-+ TOR => Firefox with add-ins for anonymity + JAP + I 2 P + Freenet Note-- this is not a Windows issue, it is an Internet issue
 You! The Web Spies on You ! * Anonymous Surfing It’s much more difficult to avoid your ISP tracking your every move + See SSL procedures for major subscription services like + Anonymizer -- Not free for ISP anonymity + Guardster -- Not free for ISP anonymity Why do we care ? -- ISP can sell your data to anyone -- ISP gives your data to the government -- AT&T’s new so-called “Privacy Policy” -“While your account may be personal to you, these records constitute business records that are owned by AT&T” -- Evidence indicates government is spying on your emails, surfing habits, searches, and phone calls Note-- this is not a Windows issue, it is an Internet issue
You! The Web Spies on You ! * Anonymous Surfing It’s much more difficult to avoid your ISP tracking your every move + See SSL procedures for major subscription services like + Anonymizer -- Not free for ISP anonymity + Guardster -- Not free for ISP anonymity Why do we care ? -- ISP can sell your data to anyone -- ISP gives your data to the government -- AT&T’s new so-called “Privacy Policy” -“While your account may be personal to you, these records constitute business records that are owned by AT&T” -- Evidence indicates government is spying on your emails, surfing habits, searches, and phone calls Note-- this is not a Windows issue, it is an Internet issue
 You! The Web Spies on You ! * Cookies: + They don’t store them where they used to + Cookie Managers built into Fire. Fox, Mozilla + FOSS available * Web Bugs: + Bugnosis -- IE only Final Exam-- test your system by Shields. UP! at www. grc. com Note-- this is not a Windows issue, it is an Internet issue
You! The Web Spies on You ! * Cookies: + They don’t store them where they used to + Cookie Managers built into Fire. Fox, Mozilla + FOSS available * Web Bugs: + Bugnosis -- IE only Final Exam-- test your system by Shields. UP! at www. grc. com Note-- this is not a Windows issue, it is an Internet issue
 Even Your Printer Spies on You ! -- Your Printer Spies on You -- See www. eff. org (www. eff. org/Privacy/printers) for a list of printers that spy on you John wrote this ! This is a Government issue, much like the tracking device in your cell phone
Even Your Printer Spies on You ! -- Your Printer Spies on You -- See www. eff. org (www. eff. org/Privacy/printers) for a list of printers that spy on you John wrote this ! This is a Government issue, much like the tracking device in your cell phone
 IV. Microsoft Alternatives
IV. Microsoft Alternatives
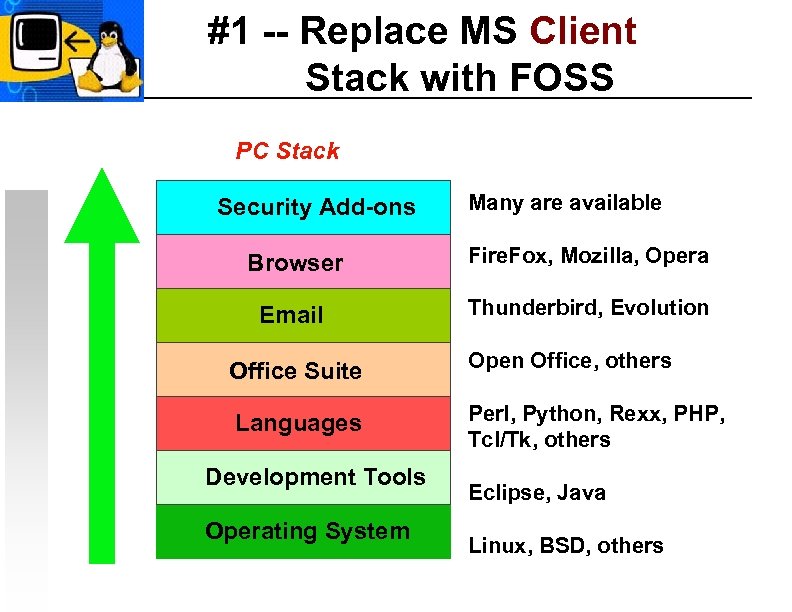 #1 -- Replace MS Client Stack with FOSS PC Stack Security Add-ons Many are available Browser Fire. Fox, Mozilla, Opera Email Thunderbird, Evolution Office Suite Open Office, others Languages Perl, Python, Rexx, PHP, Tcl/Tk, others Development Tools Operating System Eclipse, Java Linux, BSD, others
#1 -- Replace MS Client Stack with FOSS PC Stack Security Add-ons Many are available Browser Fire. Fox, Mozilla, Opera Email Thunderbird, Evolution Office Suite Open Office, others Languages Perl, Python, Rexx, PHP, Tcl/Tk, others Development Tools Operating System Eclipse, Java Linux, BSD, others
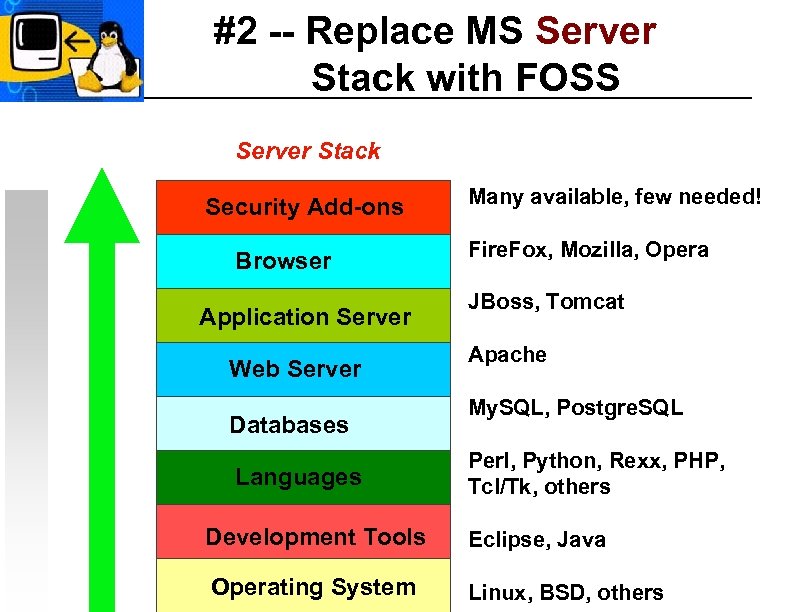 #2 -- Replace MS Server Stack with FOSS Server Stack Security Add-ons Browser Application Server Web Server Databases Languages Many available, few needed! Fire. Fox, Mozilla, Opera JBoss, Tomcat Apache My. SQL, Postgre. SQL Perl, Python, Rexx, PHP, Tcl/Tk, others Development Tools Eclipse, Java Operating System Linux, BSD, others
#2 -- Replace MS Server Stack with FOSS Server Stack Security Add-ons Browser Application Server Web Server Databases Languages Many available, few needed! Fire. Fox, Mozilla, Opera JBoss, Tomcat Apache My. SQL, Postgre. SQL Perl, Python, Rexx, PHP, Tcl/Tk, others Development Tools Eclipse, Java Operating System Linux, BSD, others
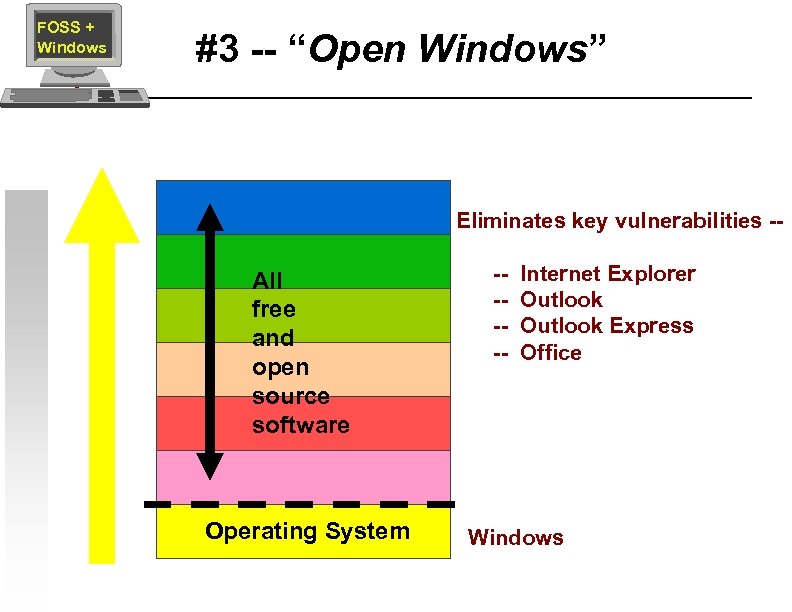 FOSS + Windows #3 -- “Open Windows” Eliminates key vulnerabilities -- All free and open source software Operating System ----- Internet Explorer Outlook Express Office Windows
FOSS + Windows #3 -- “Open Windows” Eliminates key vulnerabilities -- All free and open source software Operating System ----- Internet Explorer Outlook Express Office Windows
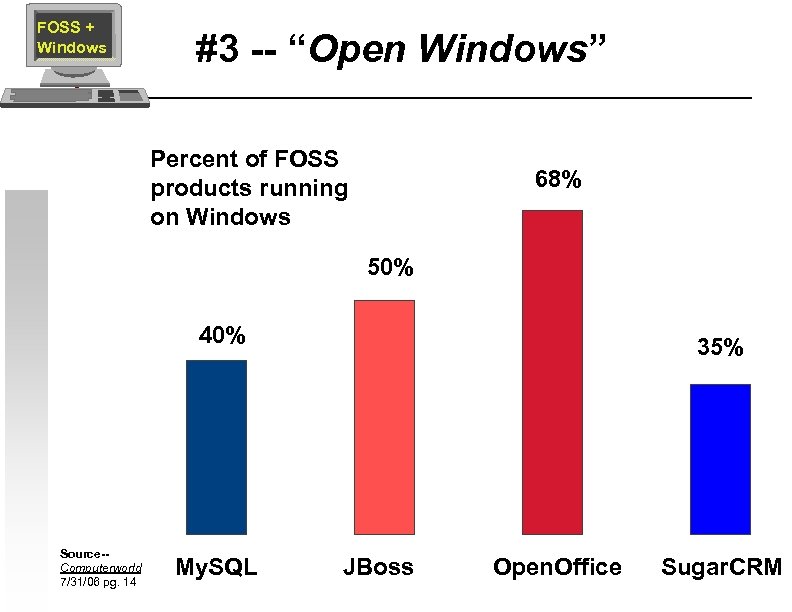 FOSS + Windows #3 -- “Open Windows” Percent of FOSS products running on Windows 68% 50% 40% Source-Computerworld 7/31/06 pg. 14 My. SQL 35% JBoss Open. Office Sugar. CRM
FOSS + Windows #3 -- “Open Windows” Percent of FOSS products running on Windows 68% 50% 40% Source-Computerworld 7/31/06 pg. 14 My. SQL 35% JBoss Open. Office Sugar. CRM
 ? Why Keep Windows ? “I’m only happy when it rains…” -- You don’t know any better -- Most consumers -- It ships with the machine -- You buy it whether you want it or not -- Because everybody else does (and compatibility) -- Example #1 -- As a contractor, I use what client uses #2 -- My backup for this presentation is in Powerpoint #3 -- Microsoft controls file formats & file systems #4 -- WINE emulator for Linux doesn’t run all applications -- You need an app -- Example -- ATT/Yahoo DSL only supports Windows
? Why Keep Windows ? “I’m only happy when it rains…” -- You don’t know any better -- Most consumers -- It ships with the machine -- You buy it whether you want it or not -- Because everybody else does (and compatibility) -- Example #1 -- As a contractor, I use what client uses #2 -- My backup for this presentation is in Powerpoint #3 -- Microsoft controls file formats & file systems #4 -- WINE emulator for Linux doesn’t run all applications -- You need an app -- Example -- ATT/Yahoo DSL only supports Windows
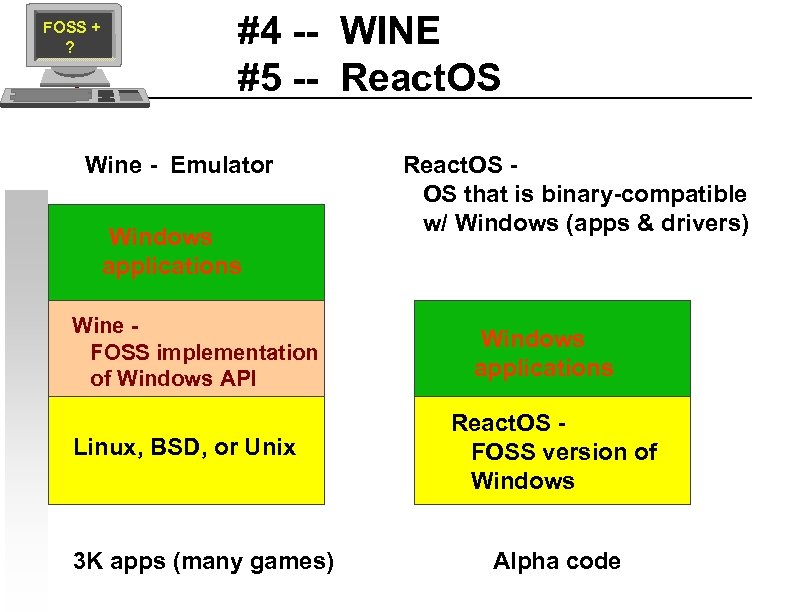 FOSS + ? #4 -- WINE #5 -- React. OS Wine - Emulator Windows applications Wine FOSS implementation of Windows API Linux, BSD, or Unix 3 K apps (many games) React. OS OS that is binary-compatible w/ Windows (apps & drivers) Windows applications React. OS FOSS version of Windows Alpha code
FOSS + ? #4 -- WINE #5 -- React. OS Wine - Emulator Windows applications Wine FOSS implementation of Windows API Linux, BSD, or Unix 3 K apps (many games) React. OS OS that is binary-compatible w/ Windows (apps & drivers) Windows applications React. OS FOSS version of Windows Alpha code
 IV. Concluding Thoughts
IV. Concluding Thoughts
 We have an Internet Security Crisis -- Malware is geometrically increasing -- Infestation is huge -- “Script kiddies” ==> professional criminals -- Identity theft is huge -- Fastest growing crime for past 5 years -- Pew & Gartner studies show public is scared Let’s dance while Rome burns ! Our online financial system is at risk !
We have an Internet Security Crisis -- Malware is geometrically increasing -- Infestation is huge -- “Script kiddies” ==> professional criminals -- Identity theft is huge -- Fastest growing crime for past 5 years -- Pew & Gartner studies show public is scared Let’s dance while Rome burns ! Our online financial system is at risk !
 Is the Internet Broken ? “The Internet is Broken” MIT Technology Review by Talbot & Clark Dec 2005/Jan 2006 issue at www. techreview. com -- They recommend “locking down the Internet” -- A comprehensive system of controls => End points handle security, not transport => The problem is Windows security, not Internet security ! => “Controlling the Internet” means disastrous side effects !
Is the Internet Broken ? “The Internet is Broken” MIT Technology Review by Talbot & Clark Dec 2005/Jan 2006 issue at www. techreview. com -- They recommend “locking down the Internet” -- A comprehensive system of controls => End points handle security, not transport => The problem is Windows security, not Internet security ! => “Controlling the Internet” means disastrous side effects !
 Trustworthy Computing ? From Microsoft’s Trustworthy Computing Web Site--“REDMOND, Wash. , Feb. 6, 2006 -- As Trustworthy Computing at Microsoft reaches the fouryear mark, a look back at 2005 provides a solid picture of sure and steady progress toward long-term success. . . Launched in January 2002. . . Trustworthy Computing is a long-term, collaborative effort to create and deliver safe, private and reliable computing experiences. Trustworthy Computing encompasses four key areas of focus that Microsoft considers vital to building a foundation of trust in computing: Security means helping to ensure the confidentiality, integrity and availability of customer systems and data. Privacy entails protecting a customer’s right to be left alone (e. g. , from any kind of unwanted communication, including spam and pop ups), as well as ensuring adherence to fair information principles that put people in control of how their data is accessed and used. Reliability refers to ensuring that software and systems are dependable and behave the way customers expect them to. Business practices addresses Microsoft’s goal of being transparent and responsive in all customer interaction, with a focus on excellence in the company’s internal decision-making and implementation processes. ” --http: //www. microsoft. com/presspass/features/2006/feb 06/02 -08 Trustworthy. mspx
Trustworthy Computing ? From Microsoft’s Trustworthy Computing Web Site--“REDMOND, Wash. , Feb. 6, 2006 -- As Trustworthy Computing at Microsoft reaches the fouryear mark, a look back at 2005 provides a solid picture of sure and steady progress toward long-term success. . . Launched in January 2002. . . Trustworthy Computing is a long-term, collaborative effort to create and deliver safe, private and reliable computing experiences. Trustworthy Computing encompasses four key areas of focus that Microsoft considers vital to building a foundation of trust in computing: Security means helping to ensure the confidentiality, integrity and availability of customer systems and data. Privacy entails protecting a customer’s right to be left alone (e. g. , from any kind of unwanted communication, including spam and pop ups), as well as ensuring adherence to fair information principles that put people in control of how their data is accessed and used. Reliability refers to ensuring that software and systems are dependable and behave the way customers expect them to. Business practices addresses Microsoft’s goal of being transparent and responsive in all customer interaction, with a focus on excellence in the company’s internal decision-making and implementation processes. ” --http: //www. microsoft. com/presspass/features/2006/feb 06/02 -08 Trustworthy. mspx
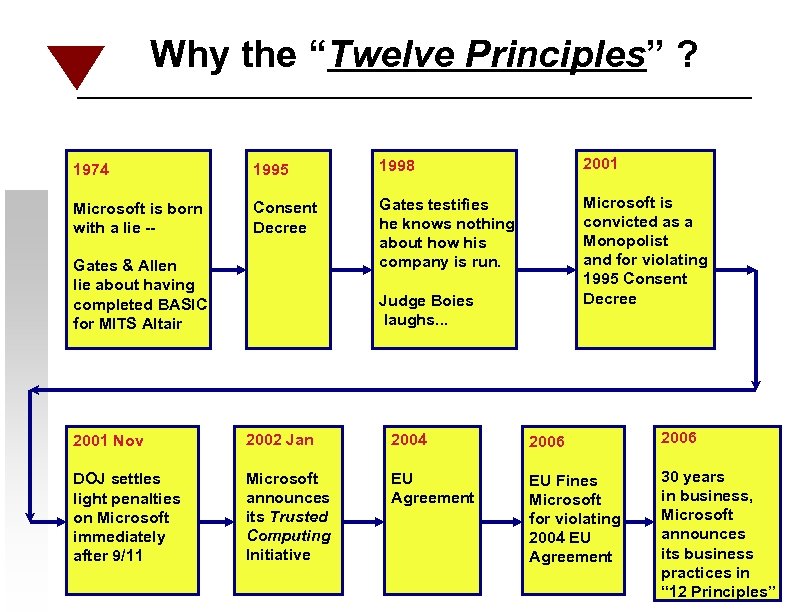 Why the “Twelve Principles” ? 1974 1995 1998 2001 Microsoft is born with a lie -- Consent Decree Gates testifies he knows nothing about how his company is run. Microsoft is convicted as a Monopolist and for violating 1995 Consent Decree Gates & Allen lie about having completed BASIC for MITS Altair Judge Boies laughs. . . 2001 Nov 2002 Jan 2004 2006 DOJ settles light penalties on Microsoft immediately after 9/11 Microsoft announces its Trusted Computing Initiative EU Agreement EU Fines Microsoft for violating 2004 EU Agreement 30 years in business, Microsoft announces its business practices in “ 12 Principles”
Why the “Twelve Principles” ? 1974 1995 1998 2001 Microsoft is born with a lie -- Consent Decree Gates testifies he knows nothing about how his company is run. Microsoft is convicted as a Monopolist and for violating 1995 Consent Decree Gates & Allen lie about having completed BASIC for MITS Altair Judge Boies laughs. . . 2001 Nov 2002 Jan 2004 2006 DOJ settles light penalties on Microsoft immediately after 9/11 Microsoft announces its Trusted Computing Initiative EU Agreement EU Fines Microsoft for violating 2004 EU Agreement 30 years in business, Microsoft announces its business practices in “ 12 Principles”
 Microsoft Versus the Internet -- Microsoft’s interests diverge from having an healthy Internet -- Policies to Eliminate piracy and force Planned obsolescence mean millions of ------ Unpatched & unsupported Windows systems Bots Spam servers etc -- Mono-culture with an insecure Internet OS
Microsoft Versus the Internet -- Microsoft’s interests diverge from having an healthy Internet -- Policies to Eliminate piracy and force Planned obsolescence mean millions of ------ Unpatched & unsupported Windows systems Bots Spam servers etc -- Mono-culture with an insecure Internet OS
 Possible Outcomes #1 Vista’s incremental improvements will be enough for the world to stay with Windows … 4+ years into “Trustworthy Computing, ” Microsoft has not solved the problem But everyone bought into previous Microsoft “solutions” in earlier Windows releases #2 FOSS replaces Windows in response to Microsoft’s failure Like Apache took off in response to IIS’s virus crisis 3 years ago Protecting Microsoft’s OS monopoly could result in a web meltdown
Possible Outcomes #1 Vista’s incremental improvements will be enough for the world to stay with Windows … 4+ years into “Trustworthy Computing, ” Microsoft has not solved the problem But everyone bought into previous Microsoft “solutions” in earlier Windows releases #2 FOSS replaces Windows in response to Microsoft’s failure Like Apache took off in response to IIS’s virus crisis 3 years ago Protecting Microsoft’s OS monopoly could result in a web meltdown
 Predictions for Next Few Years * “Controlled Internet” can only happen if it has political support * Upcoming Elections determine this * “Bush Continuation” candidate means maybe yes * Any other candidate means definite no In USA Unless the outside chance of a severe security incident occurs (example-- Rootkit requires many re-installs) -- Most will buy into Vista, so Microsoft maintains its monopoly * FOSS continues gains but can not dislodge Windows Long Term + Microsoft monopoly erodes: (1) Microsoft’s Annual Report cites FOSS threat (2) Microsoft investing elsewhere (3) Need only to achieve the tipping point Baby “Future”
Predictions for Next Few Years * “Controlled Internet” can only happen if it has political support * Upcoming Elections determine this * “Bush Continuation” candidate means maybe yes * Any other candidate means definite no In USA Unless the outside chance of a severe security incident occurs (example-- Rootkit requires many re-installs) -- Most will buy into Vista, so Microsoft maintains its monopoly * FOSS continues gains but can not dislodge Windows Long Term + Microsoft monopoly erodes: (1) Microsoft’s Annual Report cites FOSS threat (2) Microsoft investing elsewhere (3) Need only to achieve the tipping point Baby “Future”
 Predictions for Next Few Years Outside USA + Microsoft monopoly is presently eroding: (1) (2) (3) (4) Less of a Microsoft monopoly to start with Courts reject the monopoly Governmental leadership Cost pressures Baby “Future” Most products in this presentation are from the EU.
Predictions for Next Few Years Outside USA + Microsoft monopoly is presently eroding: (1) (2) (3) (4) Less of a Microsoft monopoly to start with Courts reject the monopoly Governmental leadership Cost pressures Baby “Future” Most products in this presentation are from the EU.
 Benefits to FOSS + No cost + No license tracking or inventory issues + No forced upgrade or planned obsolescence + No WPA, WGA, Registry, MS spyware, other control mechanisms + No BSA / Microsoft “compliance campaigns” + Stop divergence of OS provider’s interest, and the internet’s interests + Fix the mis-named “Internet security” problem! Cost is the least of these benefits !
Benefits to FOSS + No cost + No license tracking or inventory issues + No forced upgrade or planned obsolescence + No WPA, WGA, Registry, MS spyware, other control mechanisms + No BSA / Microsoft “compliance campaigns” + Stop divergence of OS provider’s interest, and the internet’s interests + Fix the mis-named “Internet security” problem! Cost is the least of these benefits !
 ? ? ? questions. . . ? ?
? ? ? questions. . . ? ?
 V. Extras
V. Extras
 The Registry is all about Control OS’s do not require a “Registry”-+ Some that do not have a Registry include Unix, Linux, BSD, VAX/VMS, z/OS, z/VM, z/VSE, i 5/OS, AS/400, Sky. OS, THEOS. . . Registry -- an artificial mechanism to enforce proprietary control of--- Users -- Microsoft’s Property rights -- Limit and control software use Registry prevents you from operations that are easy on other OS’s--- Cloning of OSs across machines -- Cloning of software products across machines -- Cloning a disk to a backup disk The Registry increases Windows’ insecurity
The Registry is all about Control OS’s do not require a “Registry”-+ Some that do not have a Registry include Unix, Linux, BSD, VAX/VMS, z/OS, z/VM, z/VSE, i 5/OS, AS/400, Sky. OS, THEOS. . . Registry -- an artificial mechanism to enforce proprietary control of--- Users -- Microsoft’s Property rights -- Limit and control software use Registry prevents you from operations that are easy on other OS’s--- Cloning of OSs across machines -- Cloning of software products across machines -- Cloning a disk to a backup disk The Registry increases Windows’ insecurity


