b436516ba45646b5376e49c0bebaf7d4.ppt
- Количество слайдов: 15
 How to Make E-cash with Non-Repudiation and Anonymity Authors: Ronggong Song and Larry Korba Source: Information Technology: Coding and Computing, 2004. Proceedings of International Conference on ITCC 2004, Vol. 2, 2004, pp. 167 -172 Presenter: Jung-wen Lo (駱榮問) Date: 2004/09/23
How to Make E-cash with Non-Repudiation and Anonymity Authors: Ronggong Song and Larry Korba Source: Information Technology: Coding and Computing, 2004. Proceedings of International Conference on ITCC 2004, Vol. 2, 2004, pp. 167 -172 Presenter: Jung-wen Lo (駱榮問) Date: 2004/09/23
 Outline l Introduction l l l The proposed scheme l l l Motivation Abe-Fujisaki’s protocol Architecture Protocol l E-cash Issue l On-line shopping l E-cash renew Protocol Characteristics Analysis Conclusions Comment 2
Outline l Introduction l l l The proposed scheme l l l Motivation Abe-Fujisaki’s protocol Architecture Protocol l E-cash Issue l On-line shopping l E-cash renew Protocol Characteristics Analysis Conclusions Comment 2
 Introduction l Chaum: Blind signature (1982) l l l Authenticity Integrity Nonrepuditation Blind to signer May not be traced by the signer after the signature is revealed E_cash l l Easily duplicate => Double-spending Bank implement double-spending checking => Lack of nonrepudiaion 3
Introduction l Chaum: Blind signature (1982) l l l Authenticity Integrity Nonrepuditation Blind to signer May not be traced by the signer after the signature is revealed E_cash l l Easily duplicate => Double-spending Bank implement double-spending checking => Lack of nonrepudiaion 3
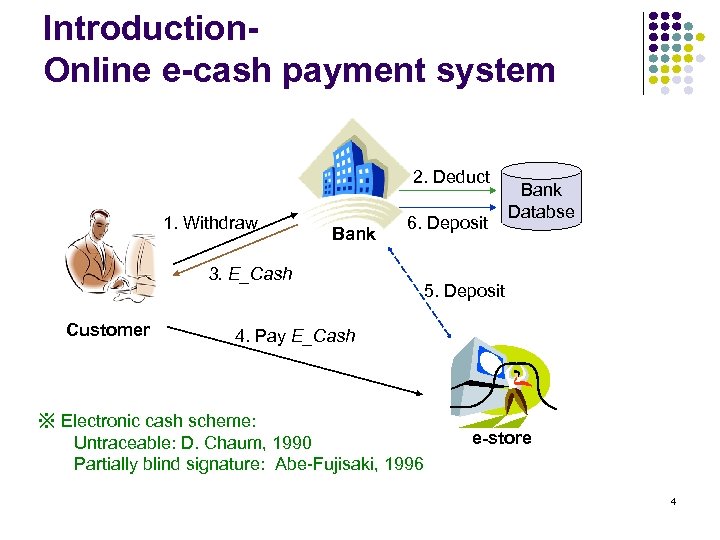 Introduction. Online e-cash payment system 2. Deduct 1. Withdraw Bank 3. E_Cash Customer 6. Deposit Bank Databse 5. Deposit 4. Pay E_Cash ※ Electronic cash scheme: Untraceable: D. Chaum, 1990 Partially blind signature: Abe-Fujisaki, 1996 e-store 4
Introduction. Online e-cash payment system 2. Deduct 1. Withdraw Bank 3. E_Cash Customer 6. Deposit Bank Databse 5. Deposit 4. Pay E_Cash ※ Electronic cash scheme: Untraceable: D. Chaum, 1990 Partially blind signature: Abe-Fujisaki, 1996 e-store 4
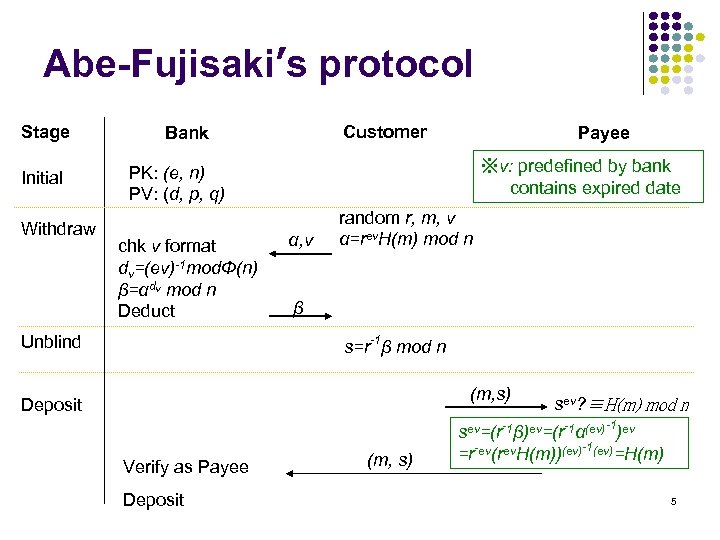 Abe-Fujisaki’s protocol Stage Initial Withdraw Customer Bank Payee ※v: predefined by bank contains expired date PK: (e, n) PV: (d, p, q) chk v format dv=(ev)-1 modΦ(n) β=αdv mod n Deduct Unblind α, v random r, m, v α=rev. H(m) mod n β s=r-1β mod n (m, s) Deposit Verify as Payee Deposit (m, s) sev? ≡H(m) mod n sev=(r-1β)ev=(r-1α(ev)-1)ev =r-ev(rev. H(m))(ev)-1(ev)=H(m) 5
Abe-Fujisaki’s protocol Stage Initial Withdraw Customer Bank Payee ※v: predefined by bank contains expired date PK: (e, n) PV: (d, p, q) chk v format dv=(ev)-1 modΦ(n) β=αdv mod n Deduct Unblind α, v random r, m, v α=rev. H(m) mod n β s=r-1β mod n (m, s) Deposit Verify as Payee Deposit (m, s) sev? ≡H(m) mod n sev=(r-1β)ev=(r-1α(ev)-1)ev =r-ev(rev. H(m))(ev)-1(ev)=H(m) 5
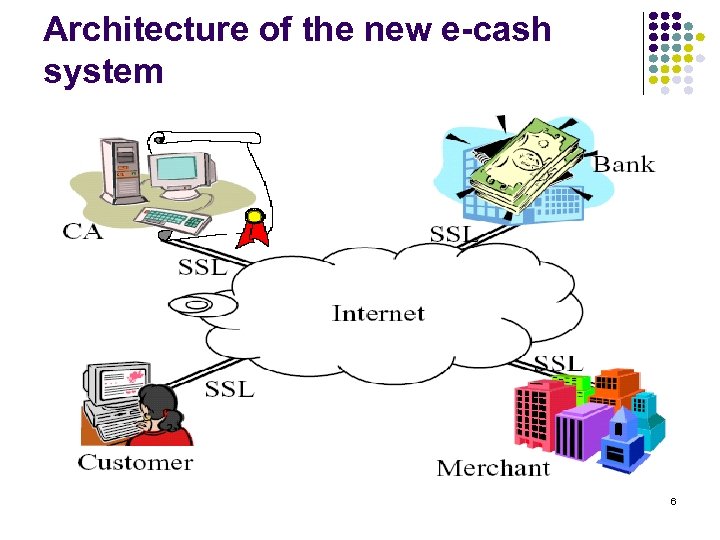 Architecture of the new e-cash system 6
Architecture of the new e-cash system 6
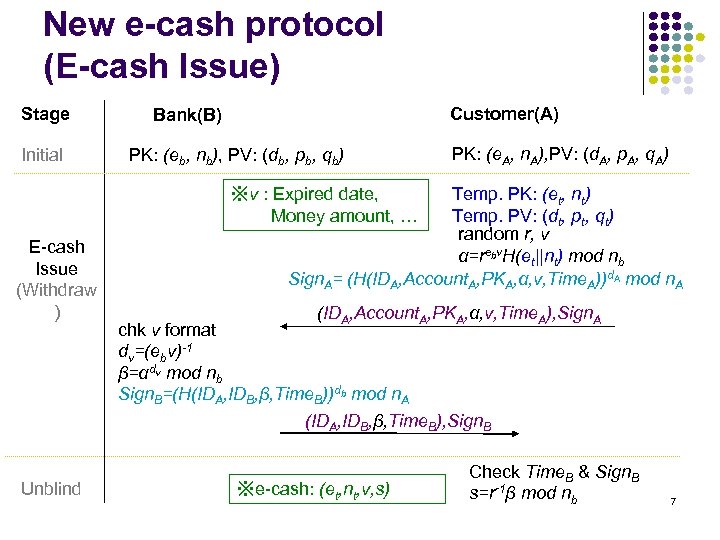 New e-cash protocol (E-cash Issue) Stage Initial Customer(A) Bank(B) PK: (eb, nb), PV: (db, pb, qb) PK: (e. A, n. A), PV: (d. A, p. A, q. A) Temp. PK: (et, nt) Temp. PV: (dt, pt, qt) random r, v α=rebv. H(et||nt) mod nb Sign. A= (H(IDA, Account. A, PKA, α, v, Time. A))d. A mod n. A ※v : Expired date, Money amount, … E-cash Issue (Withdraw ) Unblind (IDA, Account. A, PKA, α, v, Time. A), Sign. A chk v format dv=(ebv)-1 β=αdv mod nb Sign. B=(H(IDA, IDB, β, Time. B))db mod n. A (IDA, IDB, β, Time. B), Sign. B ※e-cash: (et, nt, v, s) Check Time. B & Sign. B s=r-1β mod nb 7
New e-cash protocol (E-cash Issue) Stage Initial Customer(A) Bank(B) PK: (eb, nb), PV: (db, pb, qb) PK: (e. A, n. A), PV: (d. A, p. A, q. A) Temp. PK: (et, nt) Temp. PV: (dt, pt, qt) random r, v α=rebv. H(et||nt) mod nb Sign. A= (H(IDA, Account. A, PKA, α, v, Time. A))d. A mod n. A ※v : Expired date, Money amount, … E-cash Issue (Withdraw ) Unblind (IDA, Account. A, PKA, α, v, Time. A), Sign. A chk v format dv=(ebv)-1 β=αdv mod nb Sign. B=(H(IDA, IDB, β, Time. B))db mod n. A (IDA, IDB, β, Time. B), Sign. B ※e-cash: (et, nt, v, s) Check Time. B & Sign. B s=r-1β mod nb 7
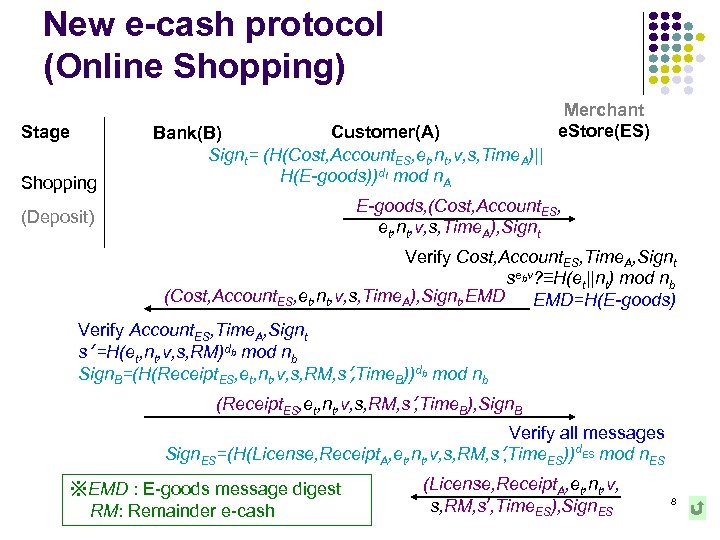 New e-cash protocol (Online Shopping) Stage Shopping Customer(A) Bank(B) Signt= (H(Cost, Account. ES, et, nt, v, s, Time. A)|| H(E-goods))dt mod n. A Merchant e. Store(ES) E-goods, (Cost, Account. ES, et, nt, v, s, Time. A), Signt (Deposit) Verify Cost, Account. ES, Time. A, Signt sebv? ≡H(et||nt) mod nb (Cost, Account. ES, et, nt, v, s, Time. A), Signt, EMD=H(E-goods) Verify Account. ES, Time. A, Signt s’ =H(et, nt, v, s, RM)db mod nb Sign. B=(H(Receipt. ES, et, nt, v, s, RM, s’, Time. B))db mod nb (Receipt. ES, et, nt, v, s, RM, s’, Time. B), Sign. B Verify all messages Sign. ES=(H(License, Receipt. A, et, nt, v, s, RM, s’, Time. ES))d. ES mod n. ES ※EMD : E-goods message digest RM: Remainder e-cash (License, Receipt. A, et, nt, v, s, RM, s’, Time. ES), Sign. ES 8
New e-cash protocol (Online Shopping) Stage Shopping Customer(A) Bank(B) Signt= (H(Cost, Account. ES, et, nt, v, s, Time. A)|| H(E-goods))dt mod n. A Merchant e. Store(ES) E-goods, (Cost, Account. ES, et, nt, v, s, Time. A), Signt (Deposit) Verify Cost, Account. ES, Time. A, Signt sebv? ≡H(et||nt) mod nb (Cost, Account. ES, et, nt, v, s, Time. A), Signt, EMD=H(E-goods) Verify Account. ES, Time. A, Signt s’ =H(et, nt, v, s, RM)db mod nb Sign. B=(H(Receipt. ES, et, nt, v, s, RM, s’, Time. B))db mod nb (Receipt. ES, et, nt, v, s, RM, s’, Time. B), Sign. B Verify all messages Sign. ES=(H(License, Receipt. A, et, nt, v, s, RM, s’, Time. ES))d. ES mod n. ES ※EMD : E-goods message digest RM: Remainder e-cash (License, Receipt. A, et, nt, v, s, RM, s’, Time. ES), Sign. ES 8
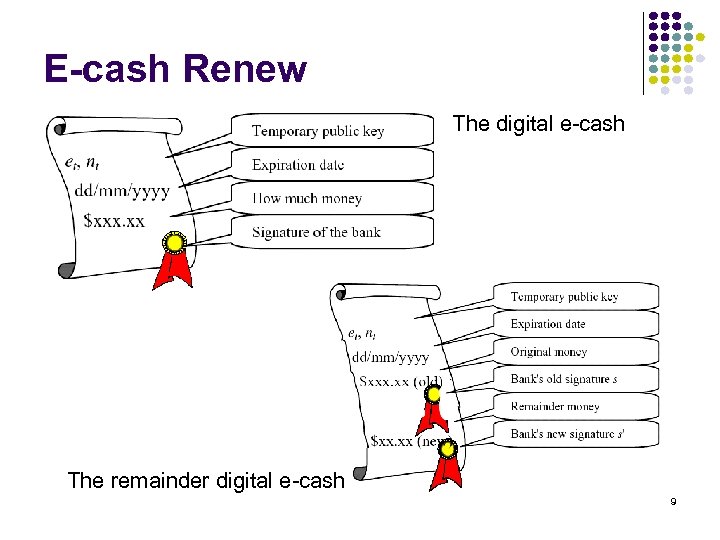 E-cash Renew The digital e-cash The remainder digital e-cash 9
E-cash Renew The digital e-cash The remainder digital e-cash 9
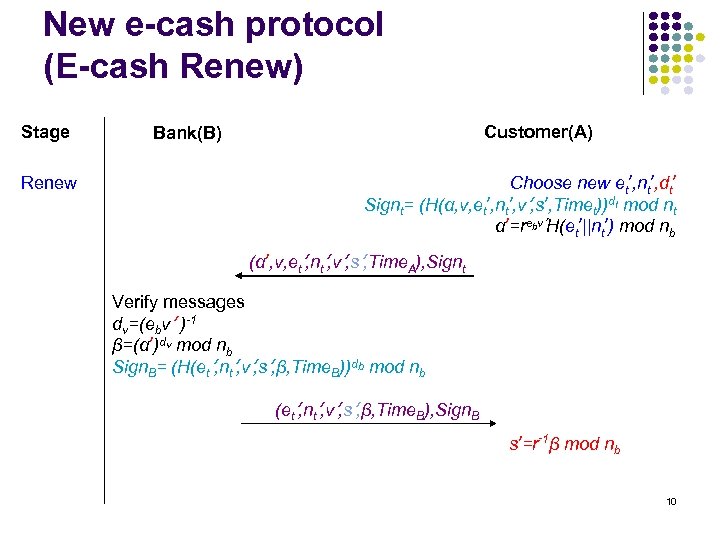 New e-cash protocol (E-cash Renew) Stage Renew Customer(A) Bank(B) Choose new et’, nt’, dt’ Signt= (H(α, v, et’, nt’, v’, s’, Timet))dt mod nt α’=rebv’H(et’||nt’) mod nb (α’, v, et’, nt’, v’, s’, Time. A), Signt Verify messages dv=(ebv’ )-1 β=(α’)dv mod nb Sign. B= (H(et’, nt’, v’, s’, β, Time. B))db mod nb (et’, nt’, v’, s’, β, Time. B), Sign. B s’=r-1β mod nb 10
New e-cash protocol (E-cash Renew) Stage Renew Customer(A) Bank(B) Choose new et’, nt’, dt’ Signt= (H(α, v, et’, nt’, v’, s’, Timet))dt mod nt α’=rebv’H(et’||nt’) mod nb (α’, v, et’, nt’, v’, s’, Time. A), Signt Verify messages dv=(ebv’ )-1 β=(α’)dv mod nb Sign. B= (H(et’, nt’, v’, s’, β, Time. B))db mod nb (et’, nt’, v’, s’, β, Time. B), Sign. B s’=r-1β mod nb 10
 Protocol Characteristics l Strong privacy protection l l Non-repudiation l l Bank and merchant cannot determine buyer All message are signed Strong safety protection l Only authorize e-cash owner can use the e-cash 11
Protocol Characteristics l Strong privacy protection l l Non-repudiation l l Bank and merchant cannot determine buyer All message are signed Strong safety protection l Only authorize e-cash owner can use the e-cash 11
 Analysis l Anonymity analysis l l l Partial blind signature Anonymous temporary public key Non-repudiation analysis l E-cash issue l l The message is signed with the customer’s certificate Online shopping l The messages are signed with the private key of the e -cash 12
Analysis l Anonymity analysis l l l Partial blind signature Anonymous temporary public key Non-repudiation analysis l E-cash issue l l The message is signed with the customer’s certificate Online shopping l The messages are signed with the private key of the e -cash 12
 Analysis l Security analysis l Passive attacks l l l Transmiting messages are protected with SSL security channel Bank cannot determine who holds the temporary public key Active attacks l l Replay attack: Time stamp “Time” Modification attack: Verify signature “Sign” 13
Analysis l Security analysis l Passive attacks l l l Transmiting messages are protected with SSL security channel Bank cannot determine who holds the temporary public key Active attacks l l Replay attack: Time stamp “Time” Modification attack: Verify signature “Sign” 13
 Conclusions l l Strong privacy protection Non-repudiation services Against denying, double-spending, losting, misusing and stealing of the e-cash Could be implmented with XML and SSL security channel 14
Conclusions l l Strong privacy protection Non-repudiation services Against denying, double-spending, losting, misusing and stealing of the e-cash Could be implmented with XML and SSL security channel 14
 Comments l l Bank should verify s and v in on-line shoping stage How to use remainder money? l l Bank records e-cahs (et, nt, v, s) and remainder ecash RM Future work l l Implemented in public network? Without CA? 15
Comments l l Bank should verify s and v in on-line shoping stage How to use remainder money? l l Bank records e-cahs (et, nt, v, s) and remainder ecash RM Future work l l Implemented in public network? Without CA? 15


