79809a7e7379ff9361e7a77f0bd6306f.ppt
- Количество слайдов: 37
 How To Implement Windows Vista Content Output Protection Dave Marsh Program Manager Windows Audio Video Microsoft Corporation
How To Implement Windows Vista Content Output Protection Dave Marsh Program Manager Windows Audio Video Microsoft Corporation
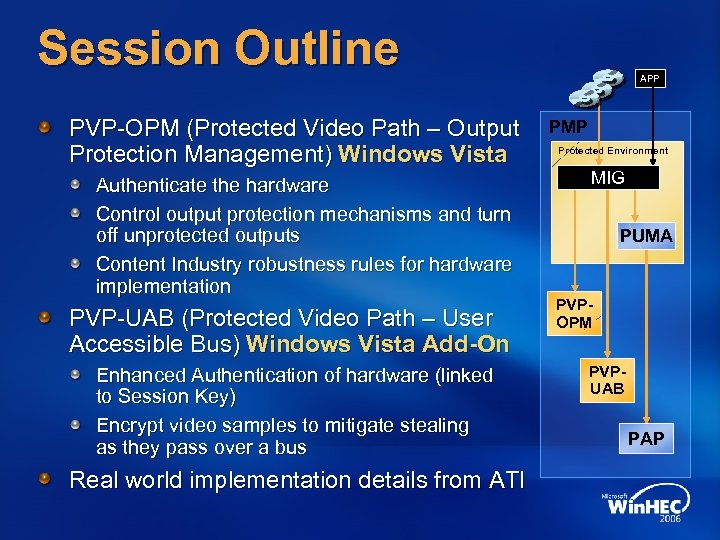 Session Outline PVP-OPM (Protected Video Path – Output Protection Management) Windows Vista Authenticate the hardware Control output protection mechanisms and turn off unprotected outputs Content Industry robustness rules for hardware implementation PVP-UAB (Protected Video Path – User Accessible Bus) Windows Vista Add-On Enhanced Authentication of hardware (linked to Session Key) Encrypt video samples to mitigate stealing as they pass over a bus Real world implementation details from ATI APP PMP Protected Environment MIG PUMA PVPOPM PVPUAB PAP
Session Outline PVP-OPM (Protected Video Path – Output Protection Management) Windows Vista Authenticate the hardware Control output protection mechanisms and turn off unprotected outputs Content Industry robustness rules for hardware implementation PVP-UAB (Protected Video Path – User Accessible Bus) Windows Vista Add-On Enhanced Authentication of hardware (linked to Session Key) Encrypt video samples to mitigate stealing as they pass over a bus Real world implementation details from ATI APP PMP Protected Environment MIG PUMA PVPOPM PVPUAB PAP
 Objective Enable the PC to play premium content in 2007 and beyond We just provide the content protection tools l Content owners specify their requirements for the content to play
Objective Enable the PC to play premium content in 2007 and beyond We just provide the content protection tools l Content owners specify their requirements for the content to play
 The Requirement Enable Premium Content on PC Platform Meet requirements of HD-DVD / Blu-Ray and DTCP (5 C), etc. Protect against stealing content from system or video memory (Software attack) Protect and control PC AV outputs (Hardware attack) Protect content on user accessible buses (Hardware attack) Appliance-like user experience Safeguard user privacy
The Requirement Enable Premium Content on PC Platform Meet requirements of HD-DVD / Blu-Ray and DTCP (5 C), etc. Protect against stealing content from system or video memory (Software attack) Protect and control PC AV outputs (Hardware attack) Protect content on user accessible buses (Hardware attack) Appliance-like user experience Safeguard user privacy
 PVP-OPM (Protected Video Path – Output Protection Management) Windows Vista feature that provides hardware authentication and robust control of the outputs
PVP-OPM (Protected Video Path – Output Protection Management) Windows Vista feature that provides hardware authentication and robust control of the outputs
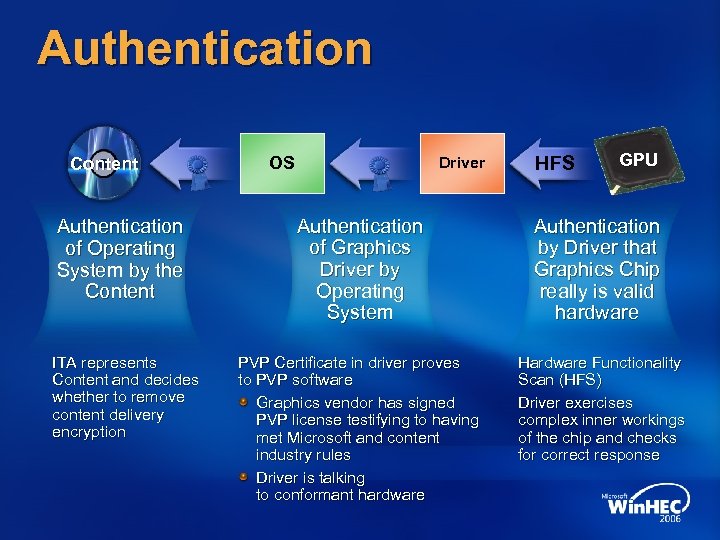 Authentication Content Authentication of Operating System by the Content ITA represents Content and decides whether to remove content delivery encryption OS Driver HFS GPU Authentication of Graphics Driver by Operating System Authentication by Driver that Graphics Chip really is valid hardware PVP Certificate in driver proves to PVP software Graphics vendor has signed PVP license testifying to having met Microsoft and content industry rules Driver is talking to conformant hardware Hardware Functionality Scan (HFS) Driver exercises complex inner workings of the chip and checks for correct response
Authentication Content Authentication of Operating System by the Content ITA represents Content and decides whether to remove content delivery encryption OS Driver HFS GPU Authentication of Graphics Driver by Operating System Authentication by Driver that Graphics Chip really is valid hardware PVP Certificate in driver proves to PVP software Graphics vendor has signed PVP license testifying to having met Microsoft and content industry rules Driver is talking to conformant hardware Hardware Functionality Scan (HFS) Driver exercises complex inner workings of the chip and checks for correct response
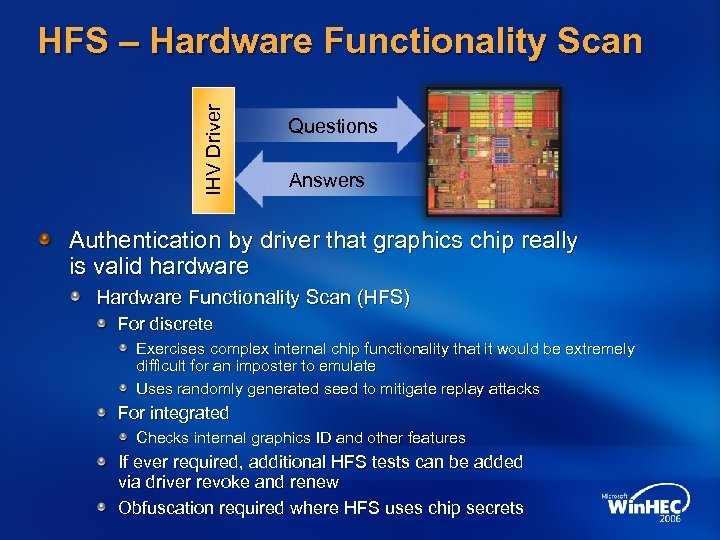 IHV Driver HFS – Hardware Functionality Scan Questions Answers Authentication by driver that graphics chip really is valid hardware Hardware Functionality Scan (HFS) For discrete Exercises complex internal chip functionality that it would be extremely difficult for an imposter to emulate Uses randomly generated seed to mitigate replay attacks For integrated Checks internal graphics ID and other features If ever required, additional HFS tests can be added via driver revoke and renew Obfuscation required where HFS uses chip secrets
IHV Driver HFS – Hardware Functionality Scan Questions Answers Authentication by driver that graphics chip really is valid hardware Hardware Functionality Scan (HFS) For discrete Exercises complex internal chip functionality that it would be extremely difficult for an imposter to emulate Uses randomly generated seed to mitigate replay attacks For integrated Checks internal graphics ID and other features If ever required, additional HFS tests can be added via driver revoke and renew Obfuscation required where HFS uses chip secrets
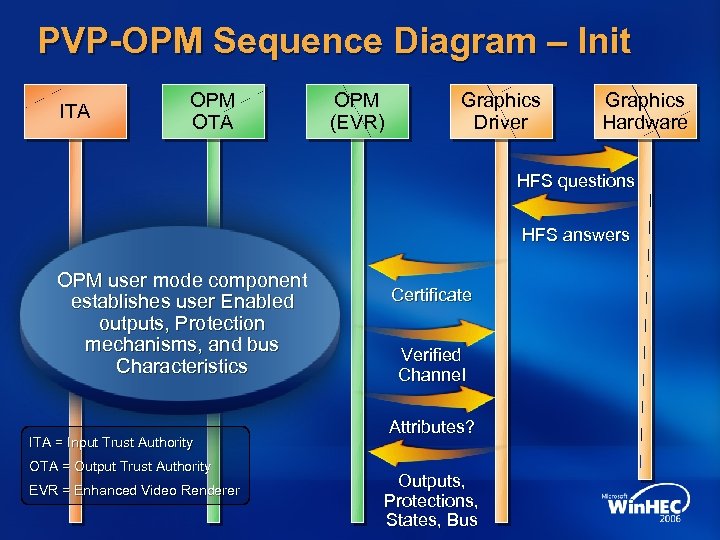 PVP-OPM Sequence Diagram – Init ITA OPM OTA OPM (EVR) Graphics Driver Graphics Hardware HFS questions HFS answers OPM user mode component establishes user Enabled outputs, Protection mechanisms, and bus Characteristics ITA = Input Trust Authority OTA = Output Trust Authority EVR = Enhanced Video Renderer Certificate Verified Channel Attributes? Outputs, Protections, States, Bus
PVP-OPM Sequence Diagram – Init ITA OPM OTA OPM (EVR) Graphics Driver Graphics Hardware HFS questions HFS answers OPM user mode component establishes user Enabled outputs, Protection mechanisms, and bus Characteristics ITA = Input Trust Authority OTA = Output Trust Authority EVR = Enhanced Video Renderer Certificate Verified Channel Attributes? Outputs, Protections, States, Bus
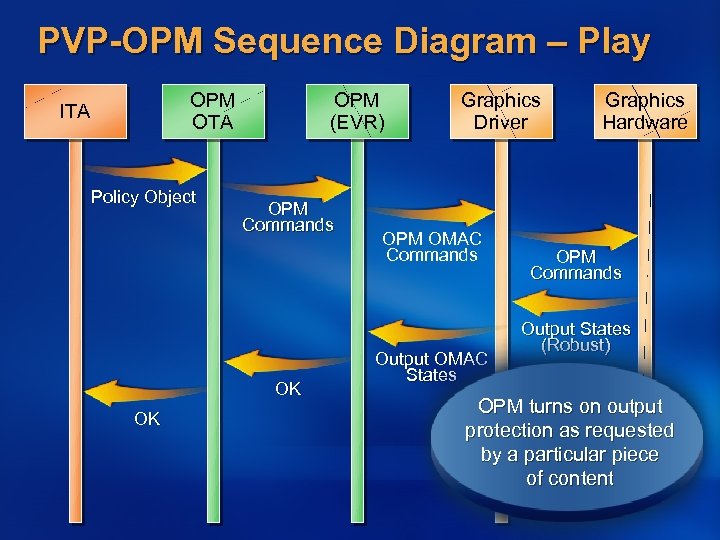 PVP-OPM Sequence Diagram – Play OPM OTA ITA Policy Object OPM (EVR) OPM Commands OK OK Graphics Driver OPM OMAC Commands Output OMAC States Graphics Hardware OPM Commands Output States (Robust) OPM turns on output protection as requested by a particular piece of content
PVP-OPM Sequence Diagram – Play OPM OTA ITA Policy Object OPM (EVR) OPM Commands OK OK Graphics Driver OPM OMAC Commands Output OMAC States Graphics Hardware OPM Commands Output States (Robust) OPM turns on output protection as requested by a particular piece of content
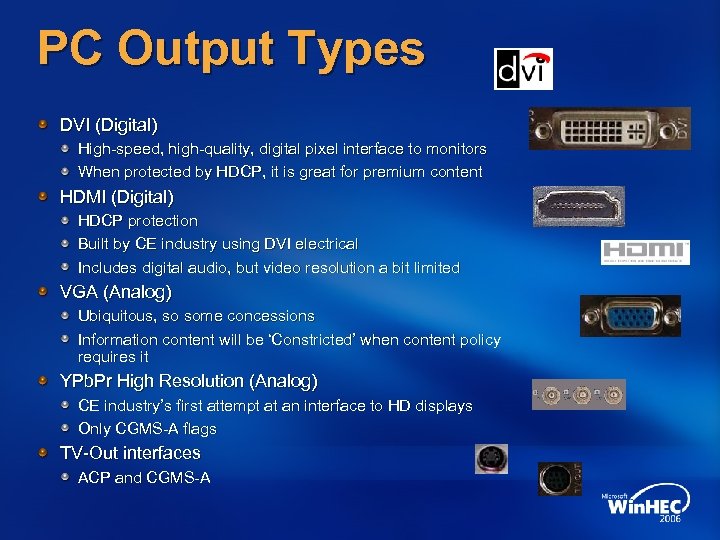 PC Output Types DVI (Digital) High-speed, high-quality, digital pixel interface to monitors When protected by HDCP, it is great for premium content HDMI (Digital) HDCP protection Built by CE industry using DVI electrical Includes digital audio, but video resolution a bit limited VGA (Analog) Ubiquitous, so some concessions Information content will be ‘Constricted’ when content policy requires it YPb. Pr High Resolution (Analog) CE industry’s first attempt at an interface to HD displays Only CGMS-A flags TV-Out interfaces ACP and CGMS-A
PC Output Types DVI (Digital) High-speed, high-quality, digital pixel interface to monitors When protected by HDCP, it is great for premium content HDMI (Digital) HDCP protection Built by CE industry using DVI electrical Includes digital audio, but video resolution a bit limited VGA (Analog) Ubiquitous, so some concessions Information content will be ‘Constricted’ when content policy requires it YPb. Pr High Resolution (Analog) CE industry’s first attempt at an interface to HD displays Only CGMS-A flags TV-Out interfaces ACP and CGMS-A
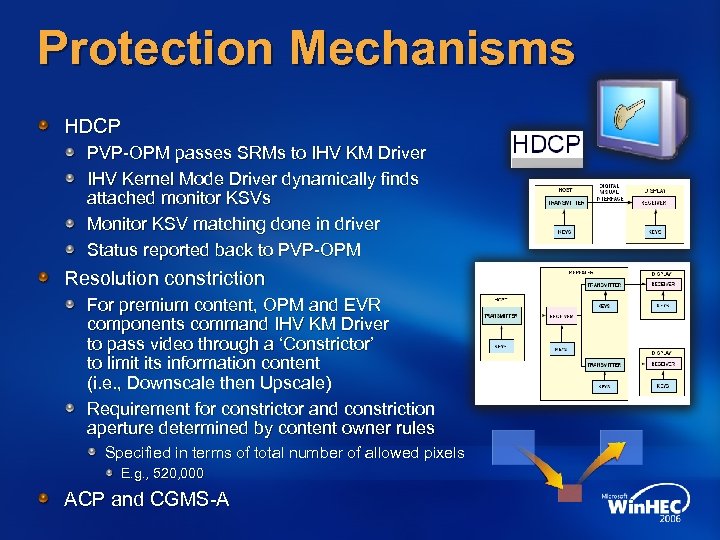 Protection Mechanisms HDCP PVP-OPM passes SRMs to IHV KM Driver IHV Kernel Mode Driver dynamically finds attached monitor KSVs Monitor KSV matching done in driver Status reported back to PVP-OPM Resolution constriction For premium content, OPM and EVR components command IHV KM Driver to pass video through a ‘Constrictor’ to limit its information content (i. e. , Downscale then Upscale) Requirement for constrictor and constriction aperture determined by content owner rules Specified in terms of total number of allowed pixels E. g. , 520, 000 ACP and CGMS-A
Protection Mechanisms HDCP PVP-OPM passes SRMs to IHV KM Driver IHV Kernel Mode Driver dynamically finds attached monitor KSVs Monitor KSV matching done in driver Status reported back to PVP-OPM Resolution constriction For premium content, OPM and EVR components command IHV KM Driver to pass video through a ‘Constrictor’ to limit its information content (i. e. , Downscale then Upscale) Requirement for constrictor and constriction aperture determined by content owner rules Specified in terms of total number of allowed pixels E. g. , 520, 000 ACP and CGMS-A
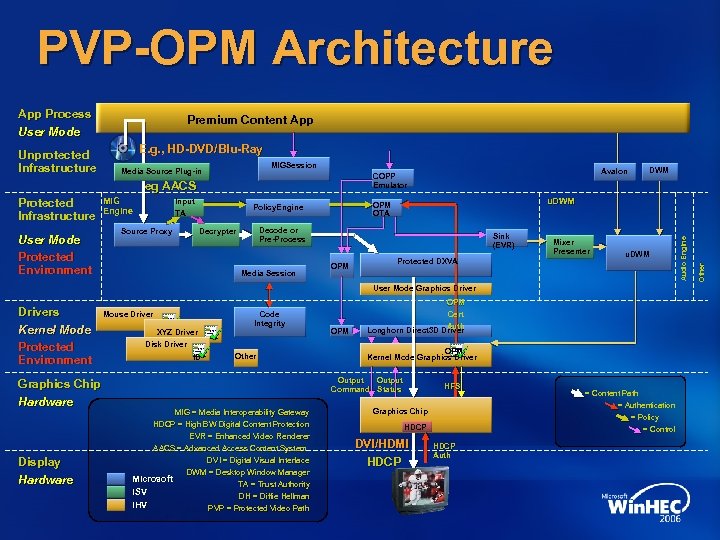 PVP-OPM Architecture App Process User Mode E. g. , HD-DVD/Blu-Ray MIGSession eg AACS Protected Infrastructure User Mode Protected Environment MIG Engine Input TA Source Proxy Avalon COPP Emulator u. DWM OPM OTA Policy. Engine Decode or Pre-Process Decrypter Media Session Sink (EVR) OPM DWM Protected DXVA Mixer Presenter u. DWM User Mode Graphics Drivers Kernel Mode Protected Environment Graphics Chip Hardware Display Hardware Mouse Driver ID XYZ Driver Disk Driver ID Code Integrity Other OPM Cert Auth Longhorn Direct 3 D Driver OPM Kernel Mode Graphics Driver Output Command Status MIG = Media Interoperability Gateway HDCP = High BW Digital Content Protection EVR = Enhanced Video Renderer AACS = Advanced Access Content System DVI = Digital Visual Interface DWM = Desktop Window Manager Microsoft TA = Trust Authority ISV DH = Diffie Hellman IHV PVP = Protected Video Path HFS Graphics Chip HDCP DVI/HDMI HDCP Auth = Content Path = Authentication = Policy = Control Other Media Source Plug-in Audio Engine Unprotected Infrastructure Premium Content App
PVP-OPM Architecture App Process User Mode E. g. , HD-DVD/Blu-Ray MIGSession eg AACS Protected Infrastructure User Mode Protected Environment MIG Engine Input TA Source Proxy Avalon COPP Emulator u. DWM OPM OTA Policy. Engine Decode or Pre-Process Decrypter Media Session Sink (EVR) OPM DWM Protected DXVA Mixer Presenter u. DWM User Mode Graphics Drivers Kernel Mode Protected Environment Graphics Chip Hardware Display Hardware Mouse Driver ID XYZ Driver Disk Driver ID Code Integrity Other OPM Cert Auth Longhorn Direct 3 D Driver OPM Kernel Mode Graphics Driver Output Command Status MIG = Media Interoperability Gateway HDCP = High BW Digital Content Protection EVR = Enhanced Video Renderer AACS = Advanced Access Content System DVI = Digital Visual Interface DWM = Desktop Window Manager Microsoft TA = Trust Authority ISV DH = Diffie Hellman IHV PVP = Protected Video Path HFS Graphics Chip HDCP DVI/HDMI HDCP Auth = Content Path = Authentication = Policy = Control Other Media Source Plug-in Audio Engine Unprotected Infrastructure Premium Content App
 PVP-OPM Implementation Pete Levinthal Software Director ATI
PVP-OPM Implementation Pete Levinthal Software Director ATI
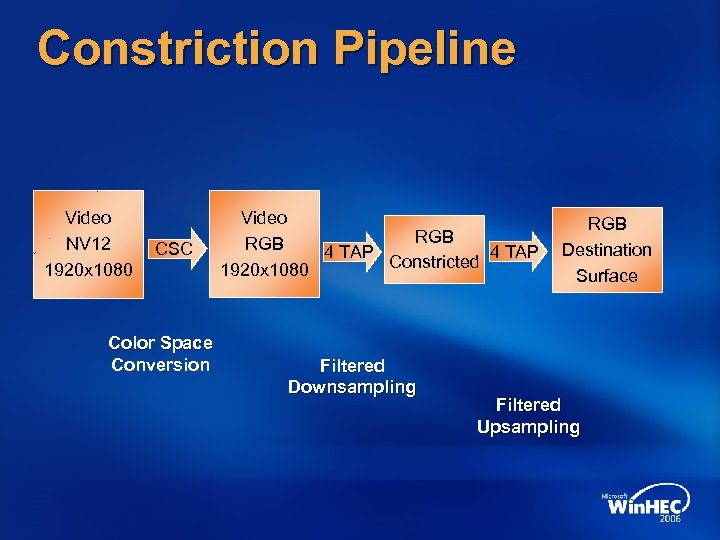 Constriction Pipeline Video NV 12 1920 x 1080 CSC Color Space Conversion Video RGB 4 TAP Constricted 1920 x 1080 Filtered Downsampling RGB Destination Surface Filtered Upsampling
Constriction Pipeline Video NV 12 1920 x 1080 CSC Color Space Conversion Video RGB 4 TAP Constricted 1920 x 1080 Filtered Downsampling RGB Destination Surface Filtered Upsampling
 Constriction Quality ATI
Constriction Quality ATI
 HFS Implementation Purpose: Driver tests GPU to ensure it is not an imposter Uses unique, undocumented features of hardware Enables certainty that driver is communicating with ATI hardware Unique for each driver and hardware generation
HFS Implementation Purpose: Driver tests GPU to ensure it is not an imposter Uses unique, undocumented features of hardware Enables certainty that driver is communicating with ATI hardware Unique for each driver and hardware generation
 PVP-OPM Implementation Straightforward technically to implement A lot of work, though Implemented in Kernel Mode Driver Implemented in separate Content Protection Library Robustness Obfuscation Source code strictly controlled
PVP-OPM Implementation Straightforward technically to implement A lot of work, though Implemented in Kernel Mode Driver Implemented in separate Content Protection Library Robustness Obfuscation Source code strictly controlled
 Protecting Analog Outputs Important part of PVP-OPM implementation since almost all boards have analog output Macrovision and CGMS-A implemented on -chip S-Video Composite YPb. Pr Secure support from driver to outputs
Protecting Analog Outputs Important part of PVP-OPM implementation since almost all boards have analog output Macrovision and CGMS-A implemented on -chip S-Video Composite YPb. Pr Secure support from driver to outputs
 Protecting Digital Outputs With HDCP External DVI/HDMI Transmitter Pro: Easy to deploy on boards Pro: Easy to manufacture Con: BOM cost External ROM Based Pro: Cost reduction Con: Board manufacturing overhead Con: BOM cost Internal to GPU Pro: Cost reduction Con: ASIC design and manufacturing overhead
Protecting Digital Outputs With HDCP External DVI/HDMI Transmitter Pro: Easy to deploy on boards Pro: Easy to manufacture Con: BOM cost External ROM Based Pro: Cost reduction Con: Board manufacturing overhead Con: BOM cost Internal to GPU Pro: Cost reduction Con: ASIC design and manufacturing overhead
 Which HDCP Solution? Key variable is attach rate for HDCP display devices When attach rate is low – external TMDS makes sense As attach rate rises – investments in cost reductions become justified
Which HDCP Solution? Key variable is attach rate for HDCP display devices When attach rate is low – external TMDS makes sense As attach rate rises – investments in cost reductions become justified
 PVP-UAB (Protected Video Path – User Accessible Bus) A Windows Vista Add-On that provides bus encryption for graphics cards
PVP-UAB (Protected Video Path – User Accessible Bus) A Windows Vista Add-On that provides bus encryption for graphics cards
 Encryption AES 128 -bit Counter Mode encryption of compressed premium content on the bus Uses 50 MB/sec (or better) hardware AES engine in graphics chip Also applies to partial compression cases AES 128 -bit Counter Mode is a base level requirement
Encryption AES 128 -bit Counter Mode encryption of compressed premium content on the bus Uses 50 MB/sec (or better) hardware AES engine in graphics chip Also applies to partial compression cases AES 128 -bit Counter Mode is a base level requirement
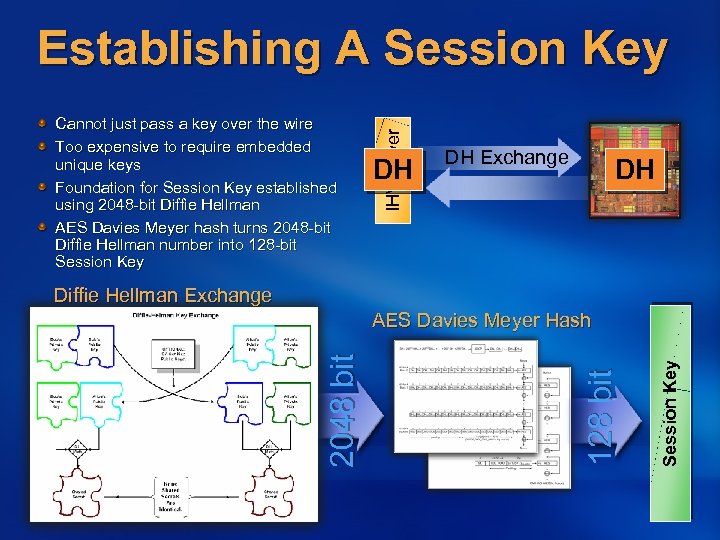 Cannot just pass a key over the wire Too expensive to require embedded unique keys Foundation for Session Key established using 2048 -bit Diffie Hellman AES Davies Meyer hash turns 2048 -bit Diffie Hellman number into 128 -bit Session Key IHV Driver Establishing A Session Key DH DH Exchange DH Diffie Hellman Exchange Session Key 128 bit 2048 bit AES Davies Meyer Hash
Cannot just pass a key over the wire Too expensive to require embedded unique keys Foundation for Session Key established using 2048 -bit Diffie Hellman AES Davies Meyer hash turns 2048 -bit Diffie Hellman number into 128 -bit Session Key IHV Driver Establishing A Session Key DH DH Exchange DH Diffie Hellman Exchange Session Key 128 bit 2048 bit AES Davies Meyer Hash
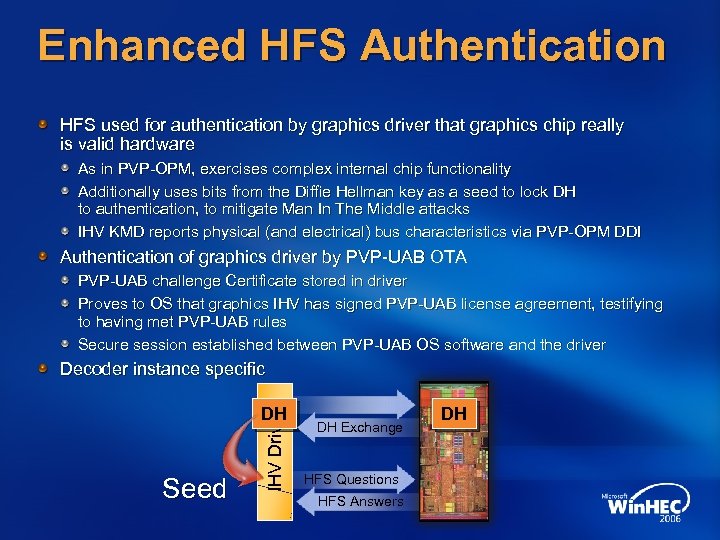 Enhanced HFS Authentication HFS used for authentication by graphics driver that graphics chip really is valid hardware As in PVP-OPM, exercises complex internal chip functionality Additionally uses bits from the Diffie Hellman key as a seed to lock DH to authentication, to mitigate Man In The Middle attacks IHV KMD reports physical (and electrical) bus characteristics via PVP-OPM DDI Authentication of graphics driver by PVP-UAB OTA PVP-UAB challenge Certificate stored in driver Proves to OS that graphics IHV has signed PVP-UAB license agreement, testifying to having met PVP-UAB rules Secure session established between PVP-UAB OS software and the driver Decoder instance specific Seed IHV Driver DH DH Exchange HFS Questions HFS Answers DH
Enhanced HFS Authentication HFS used for authentication by graphics driver that graphics chip really is valid hardware As in PVP-OPM, exercises complex internal chip functionality Additionally uses bits from the Diffie Hellman key as a seed to lock DH to authentication, to mitigate Man In The Middle attacks IHV KMD reports physical (and electrical) bus characteristics via PVP-OPM DDI Authentication of graphics driver by PVP-UAB OTA PVP-UAB challenge Certificate stored in driver Proves to OS that graphics IHV has signed PVP-UAB license agreement, testifying to having met PVP-UAB rules Secure session established between PVP-UAB OS software and the driver Decoder instance specific Seed IHV Driver DH DH Exchange HFS Questions HFS Answers DH
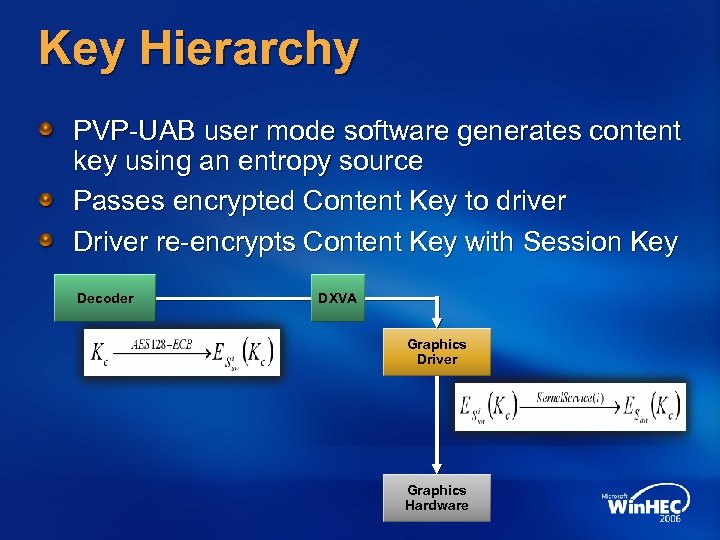 Key Hierarchy PVP-UAB user mode software generates content key using an entropy source Passes encrypted Content Key to driver Driver re-encrypts Content Key with Session Key Decoder DXVA Graphics Driver Graphics Hardware
Key Hierarchy PVP-UAB user mode software generates content key using an entropy source Passes encrypted Content Key to driver Driver re-encrypts Content Key with Session Key Decoder DXVA Graphics Driver Graphics Hardware
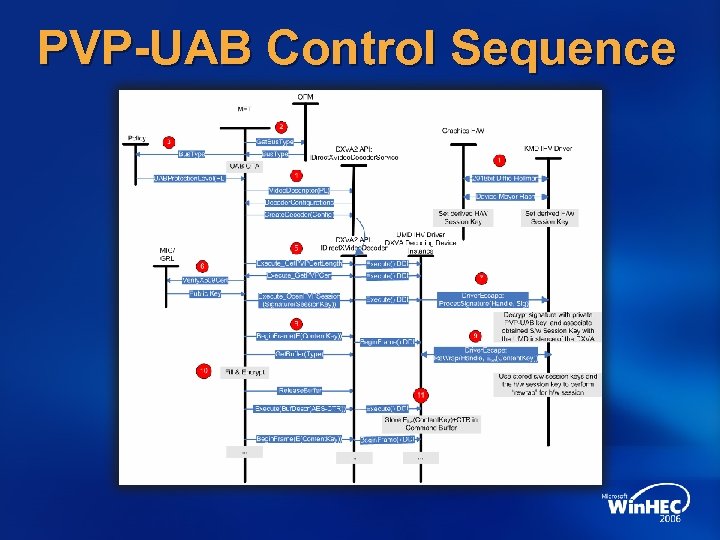 PVP-UAB Control Sequence
PVP-UAB Control Sequence
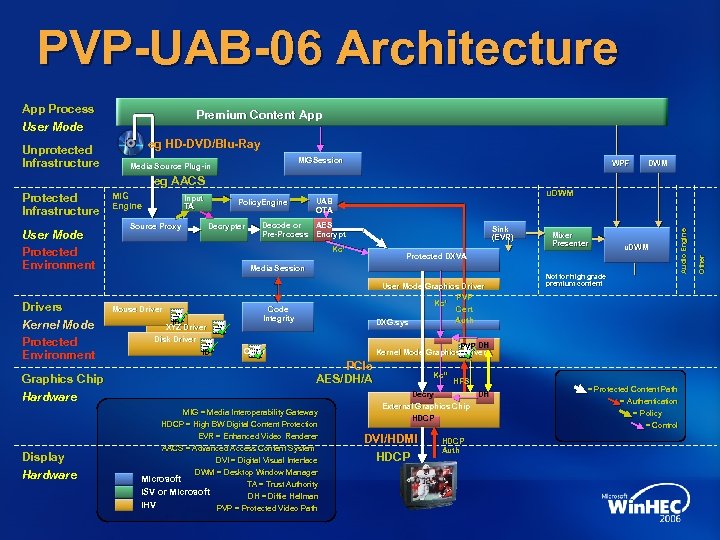 PVP-UAB-06 Architecture App Process User Mode Unprotected Infrastructure Premium Content App eg HD-DVD/Blu-Ray MIGSession Media Source Plug-in WPF DWM eg AACS Drivers Kernel Mode Protected Environment Graphics Chip Hardware Display Hardware Source Proxy Policy. Engine Decrypter u. DWM UAB OTA Decode or AES Pre-Process Encrypt Sink (EVR) Kc’ Protected DXVA Media Session Mouse Driver ID XYZ Driver Disk Driver ID Mixer Presenter User Mode Graphics Driver PVP Kc’ Cert Auth DXG. sys Code Integrity u. DWM Not for high grade premium content PVP DH Kernel Mode Graphics Driver Other PCIe AES/DH/A MIG = Media Interoperability Gateway HDCP = High BW Digital Content Protection EVR = Enhanced Video Renderer AACS = Advanced Access Content System DVI = Digital Visual Interface DWM = Desktop Window Manager Microsoft TA = Trust Authority ISV or Microsoft DH = Diffie Hellman IHV PVP = Protected Video Path Kc’’ HFS Decry DH External Graphics Chip HDCP DVI/HDMI HDCP Auth = Protected Content Path = Authentication = Policy = Control Other User Mode Protected Environment Input TA Audio Engine Protected Infrastructure MIG Engine
PVP-UAB-06 Architecture App Process User Mode Unprotected Infrastructure Premium Content App eg HD-DVD/Blu-Ray MIGSession Media Source Plug-in WPF DWM eg AACS Drivers Kernel Mode Protected Environment Graphics Chip Hardware Display Hardware Source Proxy Policy. Engine Decrypter u. DWM UAB OTA Decode or AES Pre-Process Encrypt Sink (EVR) Kc’ Protected DXVA Media Session Mouse Driver ID XYZ Driver Disk Driver ID Mixer Presenter User Mode Graphics Driver PVP Kc’ Cert Auth DXG. sys Code Integrity u. DWM Not for high grade premium content PVP DH Kernel Mode Graphics Driver Other PCIe AES/DH/A MIG = Media Interoperability Gateway HDCP = High BW Digital Content Protection EVR = Enhanced Video Renderer AACS = Advanced Access Content System DVI = Digital Visual Interface DWM = Desktop Window Manager Microsoft TA = Trust Authority ISV or Microsoft DH = Diffie Hellman IHV PVP = Protected Video Path Kc’’ HFS Decry DH External Graphics Chip HDCP DVI/HDMI HDCP Auth = Protected Content Path = Authentication = Policy = Control Other User Mode Protected Environment Input TA Audio Engine Protected Infrastructure MIG Engine
 PVP-UAB Implementation Pete Levinthal Software Director ATI
PVP-UAB Implementation Pete Levinthal Software Director ATI
 Hardware Implementation Cryptography team developed comprehensive approach HFS Additional handshaking and validation AES Straightforward and efficient to implement Logic can be re-purposed Secure Paging Support Synchronized with WDDM v 2. 1
Hardware Implementation Cryptography team developed comprehensive approach HFS Additional handshaking and validation AES Straightforward and efficient to implement Logic can be re-purposed Secure Paging Support Synchronized with WDDM v 2. 1
 Session Keys Essential to have a two-party secret key to use for encryption/decryption of data PVP solution is Diffie-Hellman Relies on the (current) intractability of computing discrete logarithms over large prime integer fields Initiated on cold boot and resume from deep sleep modes
Session Keys Essential to have a two-party secret key to use for encryption/decryption of data PVP solution is Diffie-Hellman Relies on the (current) intractability of computing discrete logarithms over large prime integer fields Initiated on cold boot and resume from deep sleep modes
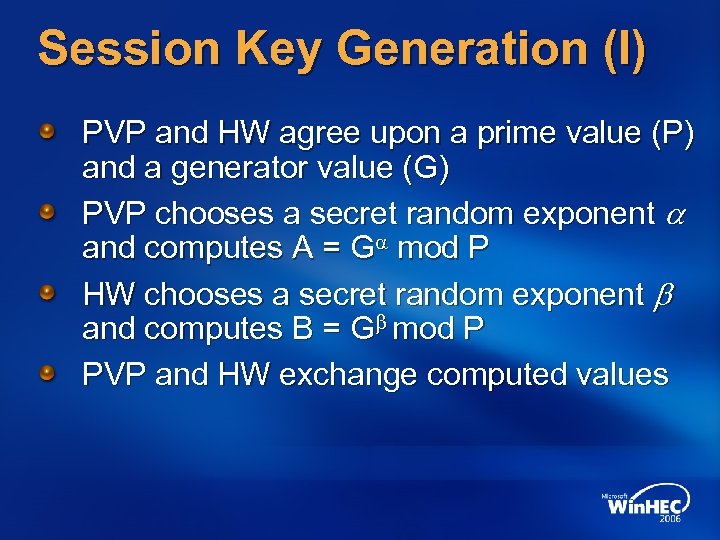 Session Key Generation (I) PVP and HW agree upon a prime value (P) and a generator value (G) PVP chooses a secret random exponent a and computes A = Ga mod P HW chooses a secret random exponent b and computes B = Gb mod P PVP and HW exchange computed values
Session Key Generation (I) PVP and HW agree upon a prime value (P) and a generator value (G) PVP chooses a secret random exponent a and computes A = Ga mod P HW chooses a secret random exponent b and computes B = Gb mod P PVP and HW exchange computed values
 Session Key Generation (II) PVP uses HW’s computed B and computes shared secret Y: Y = Ba mod P HW uses PVP’s computed A and computes shared secret Y: Y = Ab mod P An attacker listening to the public values cannot compute Y “Man in the middle” attacks are prevented by authenticating the HW through HFS and tying this value to Y
Session Key Generation (II) PVP uses HW’s computed B and computes shared secret Y: Y = Ba mod P HW uses PVP’s computed A and computes shared secret Y: Y = Ab mod P An attacker listening to the public values cannot compute Y “Man in the middle” attacks are prevented by authenticating the HW through HFS and tying this value to Y
 Certification PVP OPM Sign the license, get the certificate Legal promise that you’ve done everything spec requires Compliance Rules These are just a summary of the requirements stated in the spec If it turns out the requirements have not been properly met then Revocation Other remedies
Certification PVP OPM Sign the license, get the certificate Legal promise that you’ve done everything spec requires Compliance Rules These are just a summary of the requirements stated in the spec If it turns out the requirements have not been properly met then Revocation Other remedies
 Call To Action Implement industry-standard protection mechanisms on graphics card outputs, and get a PVP-OPM license for your graphics driver For discrete graphics cards, implement PVP-UAB decryption and key mechanism in your chip, and get a PVP-UAB license for your driver
Call To Action Implement industry-standard protection mechanisms on graphics card outputs, and get a PVP-OPM license for your graphics driver For discrete graphics cards, implement PVP-UAB decryption and key mechanism in your chip, and get a PVP-UAB license for your driver
 Additional Resources PVP-OPM and PVP-UAB feedback to PVP @ microsoft. com Last year’s Win. HEC whitepaper http: //download. microsoft. com/download/5/D/6/5 D 6 EAF 2 B-7 DDF-476 B-93 DC 7 CF 0072878 E 6/output_protect. doc Bit out of date, but still useful COPP info (Legacy) http: //msdn. microsoft. com/library/default. asp? url=/library/enus/dnwmt/html/t_d_testing_whether_a_graphics_driver_supports_certified_output_prot ection_protocol_copp__xfsi. asp Other Win. HEC sessions PRI 034 – Future Directions in Graphics – David Blythe MED 134 – Windows Vista Video Pipeline Architecture and Implementation Glenn Evans MED 025 – DXVA 2. 0: A New Hardware Video Acceleration Pipeline for Windows Vista – Rodolfo Vargas Guerrero CPA 127 – Windows Vista And Windows Server Longhorn Security Platform Enhancements – Chris Corio
Additional Resources PVP-OPM and PVP-UAB feedback to PVP @ microsoft. com Last year’s Win. HEC whitepaper http: //download. microsoft. com/download/5/D/6/5 D 6 EAF 2 B-7 DDF-476 B-93 DC 7 CF 0072878 E 6/output_protect. doc Bit out of date, but still useful COPP info (Legacy) http: //msdn. microsoft. com/library/default. asp? url=/library/enus/dnwmt/html/t_d_testing_whether_a_graphics_driver_supports_certified_output_prot ection_protocol_copp__xfsi. asp Other Win. HEC sessions PRI 034 – Future Directions in Graphics – David Blythe MED 134 – Windows Vista Video Pipeline Architecture and Implementation Glenn Evans MED 025 – DXVA 2. 0: A New Hardware Video Acceleration Pipeline for Windows Vista – Rodolfo Vargas Guerrero CPA 127 – Windows Vista And Windows Server Longhorn Security Platform Enhancements – Chris Corio
 © 2006 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.
© 2006 Microsoft Corporation. All rights reserved. Microsoft, Windows Vista and other product names are or may be registered trademarks and/or trademarks in the U. S. and/or other countries. The information herein is for informational purposes only and represents the current view of Microsoft Corporation as of the date of this presentation. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information provided after the date of this presentation. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, AS TO THE INFORMATION IN THIS PRESENTATION.



