f33949fa96235a1f42e6051e6fcdf597.ppt
- Количество слайдов: 17

How secure is Darren Adams, Kyle Coble, and Lakshmi Kasoji

Introduction to Bluetooth has become very popular because: • Power efficiency • Low costs • Short range radio frequency wireless device • Bluetooth is a Personal Area Network (PAN) wireless device and can be used for: –Portable laptops –Printers –Keyboards –Headsets –Cell phones –GPS devices –Ipod’s –PDA’s –Automobile equipment 2

Introduction to Bluetooth History: Bluetooth name came from Denmark. Originally created by Jaap Haartsen and Sven Mattisson working for Ericsson in 1994. Further developed by Special Interest Group (SIG) including: • • • Ericsson IBM Nokia Intel Toshiba In 1999, other companies added support including 3 Com Corporation, Lucent Technologies, Microsoft and Motorola 3

Introduction to Bluetooth features… • Frequency ~ 2. 5 GHz. Communication is point to point or one point to several connections. Used globally without a license. • 10 to 100 meter transmit distances at 1 Mbps. • Uses ad-hoc network, also called piconet. In a piconet, one device acts as master and other devices as slaves. Maximum of seven slaves • Low and high level of power depending on room size • Synchronous and asynchronous communication channels wikipedia 4
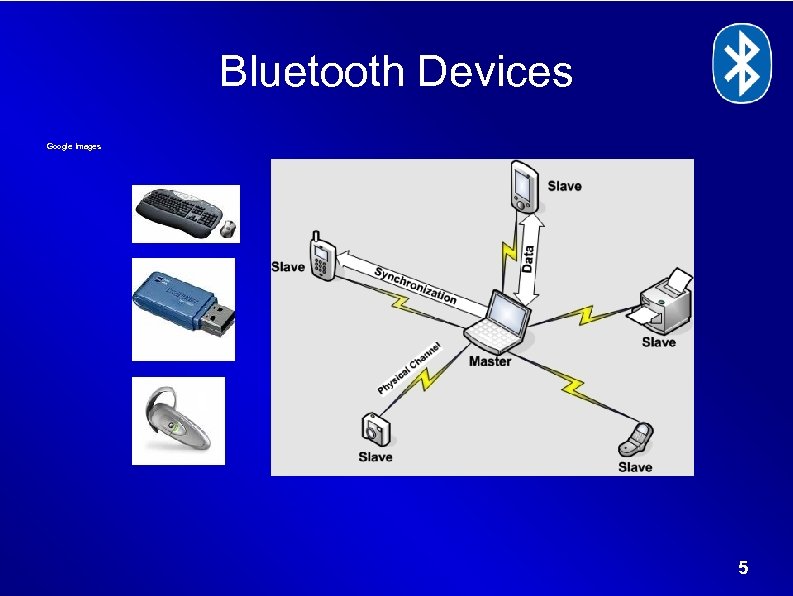
Bluetooth Devices Google Images 5

Bluetooth: Security Risks Significant target due to popularity Newer technology means bugs and vulnerabilities Numerous types of devices means different problems for each 6

PCs and Bluetooth Ad-Hoc network in meeting Problems with fixed passkey Some hubs have no router-like security (simple relay) Class 1 Bluetooth devices can extend 300 feet Short key means easy to guess Separate keys for different types of access is recommended but rarely used (Linux) Initial key exchange is unencrypted Hacker could extrapolate key (similar to cracking WEP encryption) 7

Bluetooth Passwords Using one passkey for all connections Instead of unique keys to each pairing, all devices (Laptop, PDA, Cell Phone, Printer, Headset, etc. ) use same passkey Hacker accesses one trusted device, all devices are now vulnerable MAC address problems Can identify MAC address and monitor traffic on device (class example of 2 companies merging) MAC unencrypted regardless of other encryption Standard Linux commands can be used # hcitool scan Scanning. . . 00: 0 A: D 9: 15: 0 B: 1 C T 610 -phone 8

Cracking Bluetooth Red. Fang Scans MACs one at a time Odds of finding are low Average 3 -10 sec / address Sony Ericsson alone has 16, 777, 216 possible = 1, 000+ days Devices available to analyze Bluetooth data Cost prohibitive ($9500. 00) 9
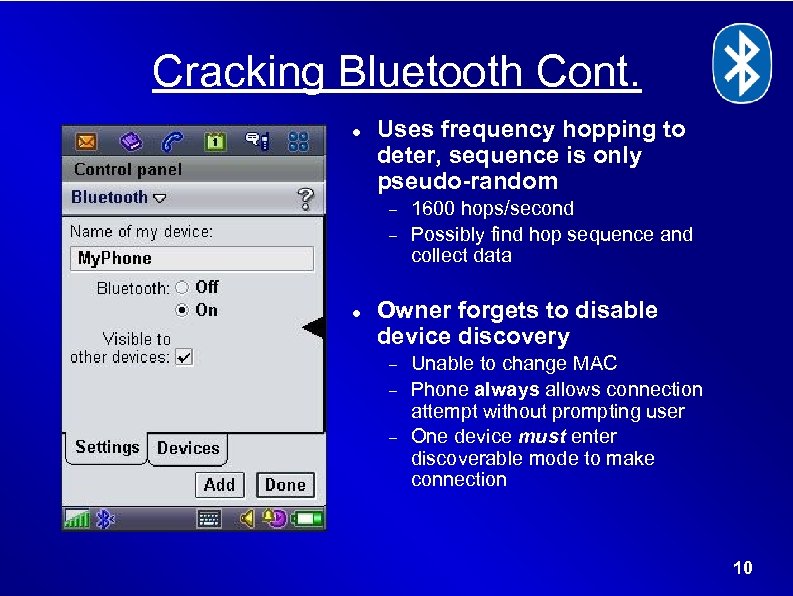
Cracking Bluetooth Cont. Uses frequency hopping to deter, sequence is only pseudo-random 1600 hops/second Possibly find hop sequence and collect data Owner forgets to disable device discovery Unable to change MAC Phone always allows connection attempt without prompting user One device must enter discoverable mode to make connection 10
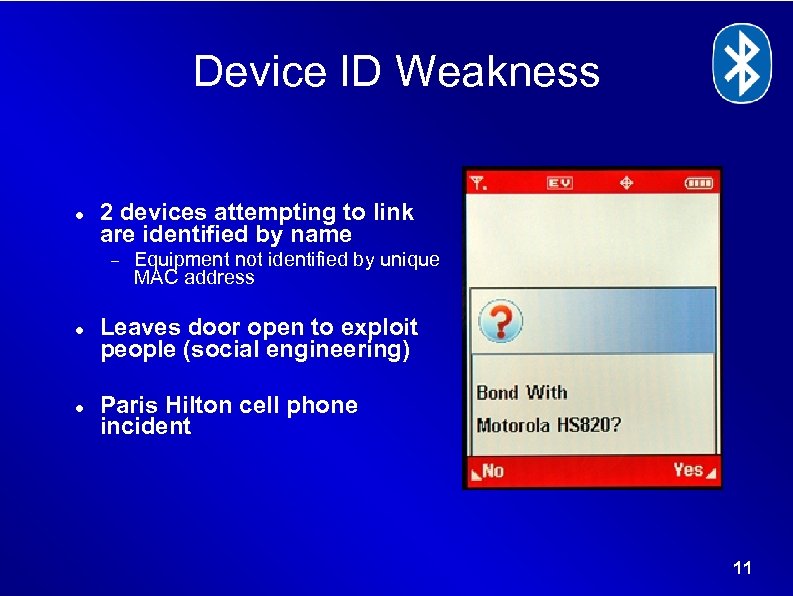
Device ID Weakness 2 devices attempting to link are identified by name Equipment not identified by unique MAC address Leaves door open to exploit people (social engineering) Paris Hilton cell phone incident 11
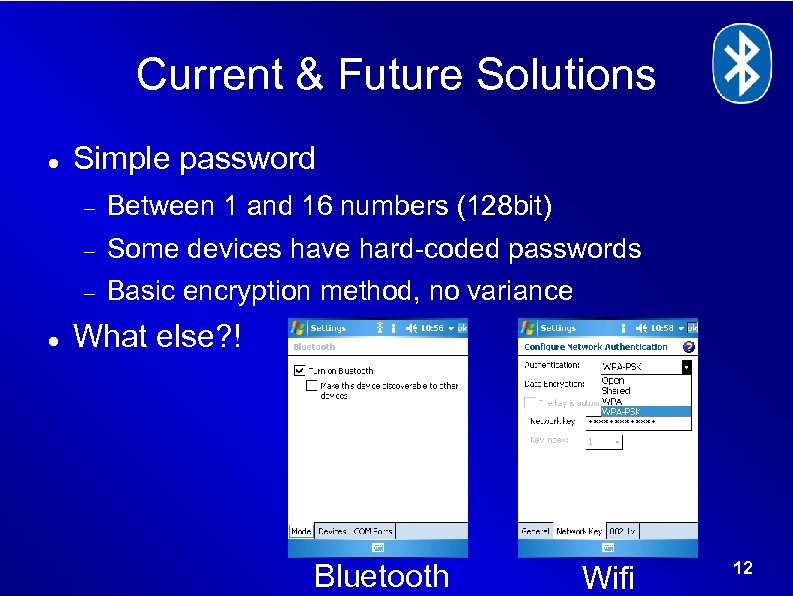
Current & Future Solutions Simple password Some devices have hard-coded passwords Between 1 and 16 numbers (128 bit) Basic encryption method, no variance What else? ! Bluetooth Wifi 12
Current & Future Solutions Security Mode 1 Security Mode 2 Device does not initiate special security mechanism but responds to authentication requests No Encryption Use of security mechanisms determined by trust status. Security is performed after authentication requests from other devices Broadcast traffic is unencrypted Security Mode 3 Authentication is necessary for connection establishment All traffic is encrypted. 13

Current & Future Solutions Simple current solutions Lower the transmission power Set to un-discoverable Pairing in an inception-proof environment Use complex keys 14

Current & Future Solutions Example : Acter. Blue Designed to make mobile e-commerce secure via Bluetooth Done through onboard biometric ID system Passwords are removed – instead, fingerprint images are processed/stored on the card 15

Current & Future Solutions Hardware access point? Allows owner to create up to 8 users with unique passwords. Connects by standard ethernet More secure than standard Bluetooth? Belkin F 8 T 030 16
References: http: //books. google. com/books? id=f. UR 0 OGZ 7 b. QC&pg=PA 58&lpg=PA 58&dq=bluetooth+combination+key&source=we b&ots=Rwk. D 5 ANJc. H&sig=FAhe. S 6 Y 29 u. E 3 EUq. LZRMg. S 3 i 5 v 5 I http: //www. securityfocus. com/infocus/1830 http: //www. bluetooth-headset. co. uk/images/jabra%20 jx 10%20 hub. bmp http: //windowsecurity. com/articles/Bluetooth-Security-Threat. html http: //www. cyberindian. net/wp-content/uploads/sony-ericsson-k 790 i-mobilephones. jpg http: //www. askdavetaylor. com/sync_motorola_razr_v 3 c_with_windows_xp_via_blu etooth. html 17
f33949fa96235a1f42e6051e6fcdf597.ppt