 How Secure are YOU? Information System Audit and Control Association May 2008 Meeting Presented by Brian Findley Counterintelligence Cyber TE Honeywell FM&T
How Secure are YOU? Information System Audit and Control Association May 2008 Meeting Presented by Brian Findley Counterintelligence Cyber TE Honeywell FM&T
 How Secure are YOU? • How many of you? – Have a Computer at Home – Travel with a Laptop – High Speed Internet at Home – Have wireless networks at Home – Connect to wireless networks on Travel – Connect to the Internet in Hotels – Children with game consoles connected to the Internet or use any of the above May 2008 BEF
How Secure are YOU? • How many of you? – Have a Computer at Home – Travel with a Laptop – High Speed Internet at Home – Have wireless networks at Home – Connect to wireless networks on Travel – Connect to the Internet in Hotels – Children with game consoles connected to the Internet or use any of the above May 2008 BEF
 Then you may not be as secure as you think! • New Headlines – – – TJX losing 2. 4 million records Two charged for allegedly stealing trade secrets Pfizer investigates data lost Stolen Johns Hopkins Hospital computer holds patient data Gap stolen laptop loses information on 800, 000 present and past employees – Monster. com users target of phishing and ransom schemes – 3 com agrees to a buy-in by Huawei worth 2. 2 billion – Mass web attacks confounds Law Enforcement and Researchers May 2008 BEF
Then you may not be as secure as you think! • New Headlines – – – TJX losing 2. 4 million records Two charged for allegedly stealing trade secrets Pfizer investigates data lost Stolen Johns Hopkins Hospital computer holds patient data Gap stolen laptop loses information on 800, 000 present and past employees – Monster. com users target of phishing and ransom schemes – 3 com agrees to a buy-in by Huawei worth 2. 2 billion – Mass web attacks confounds Law Enforcement and Researchers May 2008 BEF
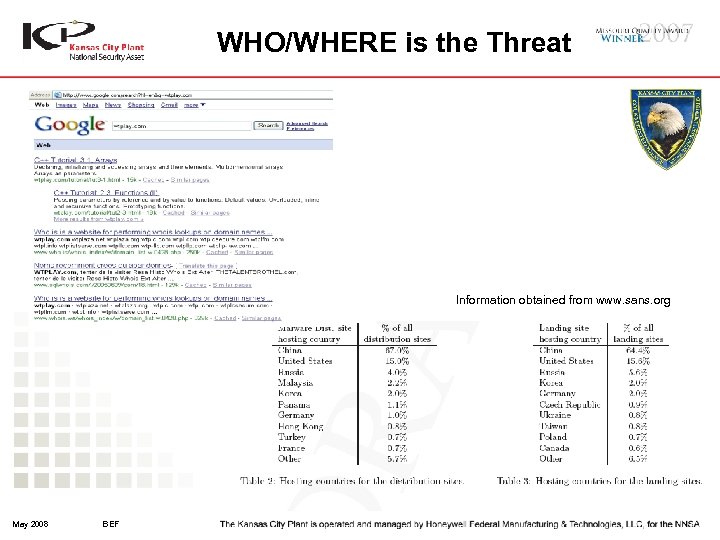 WHO/WHERE is the Threat Information obtained from www. sans. org May 2008 BEF
WHO/WHERE is the Threat Information obtained from www. sans. org May 2008 BEF
 What is the Threat. • Request for Information – Unsolicited inquiries – Direct or Indirect • Acquisition of Technology – Attempts to gain access to sensitive technologies • Solicitation of Marketing Services – Foreign individuals with technical backgrounds offering services • Targeting of US personal abroad – Requesting access sensitive facilities or personal information • Targeting at Conventions – Provides access to all of the above May 2008 BEF
What is the Threat. • Request for Information – Unsolicited inquiries – Direct or Indirect • Acquisition of Technology – Attempts to gain access to sensitive technologies • Solicitation of Marketing Services – Foreign individuals with technical backgrounds offering services • Targeting of US personal abroad – Requesting access sensitive facilities or personal information • Targeting at Conventions – Provides access to all of the above May 2008 BEF
 What is the Threat. • Exploitation of Relationships – Partnership through joint ventures and research • Suspicious Internet Activity – Exploitation of computing resources • Other – Luggage searches – Unauthorized access to portable computing devices – Extensive questioning May 2008 BEF
What is the Threat. • Exploitation of Relationships – Partnership through joint ventures and research • Suspicious Internet Activity – Exploitation of computing resources • Other – Luggage searches – Unauthorized access to portable computing devices – Extensive questioning May 2008 BEF
 How Secure Are You? • Let’s see what could potential happen to anyone of us. • Killing_with_Keyboards KCP. pps May 2008 BEF
How Secure Are You? • Let’s see what could potential happen to anyone of us. • Killing_with_Keyboards KCP. pps May 2008 BEF
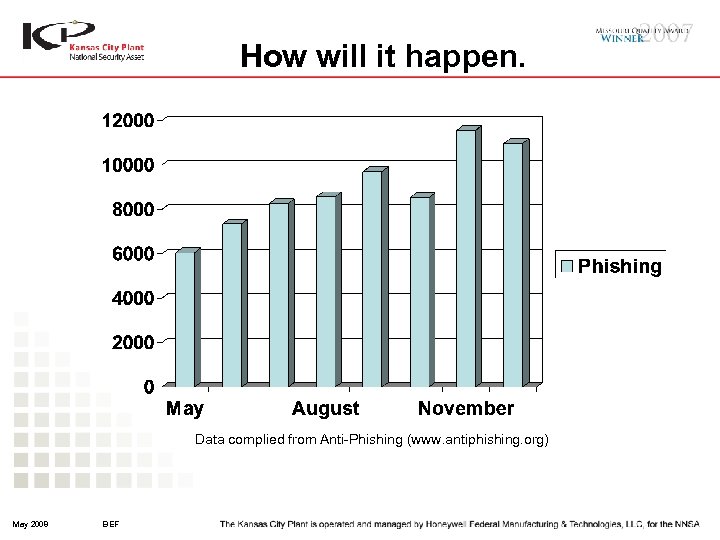 How will it happen. Data complied from Anti-Phishing (www. antiphishing. org) May 2008 BEF
How will it happen. Data complied from Anti-Phishing (www. antiphishing. org) May 2008 BEF
 How will it happen. May 2008 BEF
How will it happen. May 2008 BEF
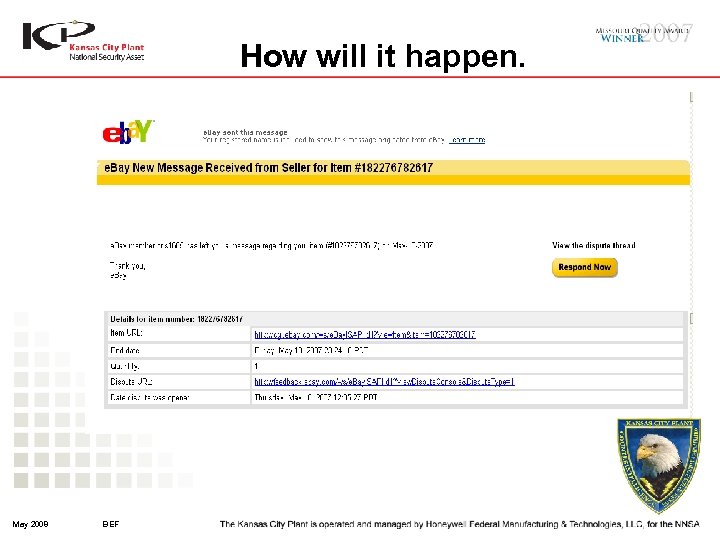 How will it happen. May 2008 BEF
How will it happen. May 2008 BEF
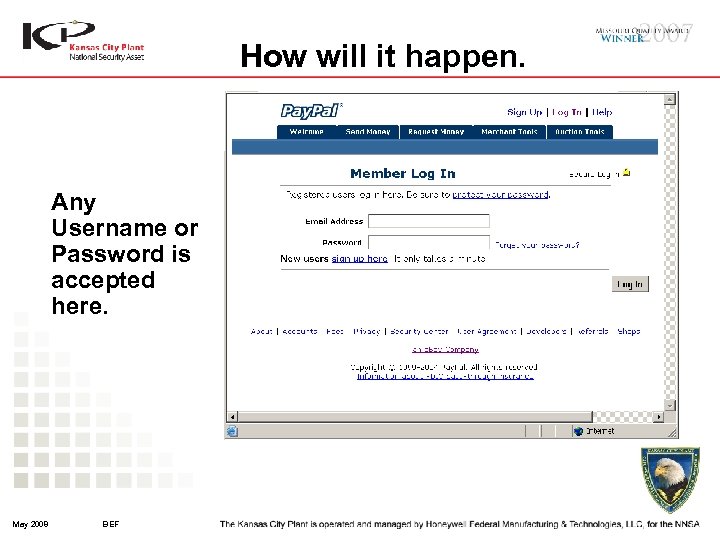 How will it happen. Any Username or Password is accepted here. May 2008 BEF
How will it happen. Any Username or Password is accepted here. May 2008 BEF
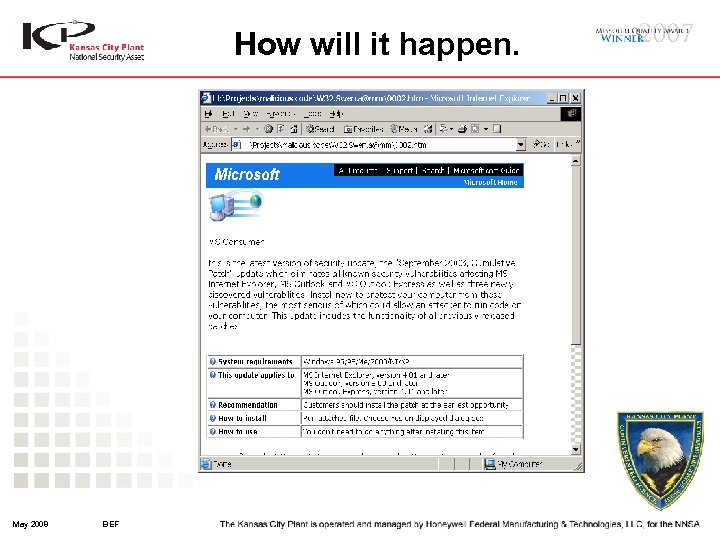 How will it happen. May 2008 BEF
How will it happen. May 2008 BEF
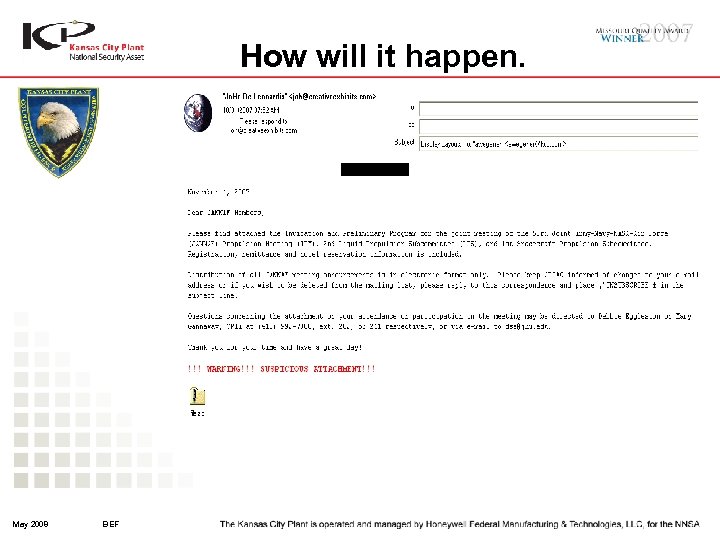 How will it happen. May 2008 BEF
How will it happen. May 2008 BEF
 How Secure Are YOU? • Let’s see what could potentially happen to anyone of us. • Without a trace. doc • TTN_October_'06 10 -17 -06. doc May 2008 BEF
How Secure Are YOU? • Let’s see what could potentially happen to anyone of us. • Without a trace. doc • TTN_October_'06 10 -17 -06. doc May 2008 BEF
 When will it happen • You tell me. • Here are my thoughts: – Globalization of business – Use of front companies – Enhancing the efficiency of command, control, communication, and intelligence will be a priority – The shift to government sponsorship – Increase in the number of incidents – Increase in suspicious internet activity – just one • Your guess is as good as mine, however, I will say sooner that later. May 2008 BEF
When will it happen • You tell me. • Here are my thoughts: – Globalization of business – Use of front companies – Enhancing the efficiency of command, control, communication, and intelligence will be a priority – The shift to government sponsorship – Increase in the number of incidents – Increase in suspicious internet activity – just one • Your guess is as good as mine, however, I will say sooner that later. May 2008 BEF
 May 2008 BEF
May 2008 BEF