170abb51872d9bd6e2572c2d8b4249b1.ppt
- Количество слайдов: 53

Hot Tools for Network Troubleshooting Laura Chappell Sr. Protocol Analyst Protocol Analysis Institute lchappell@packet-level. com

The one Net vision 2 © March 9, 2004 Novell Inc.

The one Net vision 3 © March 9, 2004 Novell Inc.
Introduction White Hat Toolbox Security Tools, Tricks and Traces Password crackers, honeypots (+ markers), forensic tools, vulnerability scanners, wireless detecters, data intercepters/injectors, and more… 4 © March 9, 2004 Novell Inc.
Warning! Make sure you have appropriate authorization to run these tools on your network. 5 © March 9, 2004 Novell Inc.

These Tools Allow You To: 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 13. 6 Sniff network passwords and unencrypted data Open suspect files Map IP to MAC addresses Locate rogue servers on the network Test blocked ports Test for SMTP relaying Perform reconnaissance on an attacker Test UDP flood vulnerabilities Test TCP flood vulnerabilities Find evidence on a hard drive Set up a decoy system Log active connections/endpoints Keylog a suspect system © March 9, 2004 Novell Inc.

Focus of this Course 1. 2. 3. 4. 5. 6. 7. 8. 9. 10. 11. 12. 7 Test password integrity Perform a brute force password crack Audit a suspect system in stealth mode Locate auditing software on the network Intercept traffic and alter data Locate M-i-M devices Locate open shares on network drives Identify unpatched systems Traceback suspicious email View HTTP graphic transfers Locate rogue wireless access points Surf the Internet anonymously © March 9, 2004 Novell Inc.

The White Hat Toolbox Tools • Ethereal • Hex Workshop • Net. Scan. Tools Pro • Nmap Network Scanner • Packet Builder • Hurricane Search • Specter Honeypot • TCPView • Cain and Abel *All are LLK v 5. 0 except Keyghost Keylogger 8 © March 9, 2004 Novell Inc.
Ethereal Price: Free; distributed under the GNU license Link: www. ethereal. com General: 9 © March 9, 2004 Novell Inc. Protocol analyzer; requires winpcap to run over W 32 platform (available atwinpcap. polito. it.
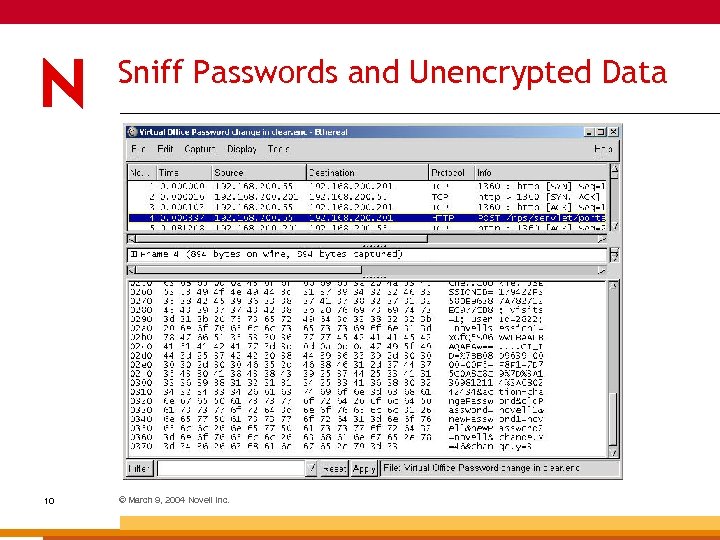
Sniff Passwords and Unencrypted Data 10 © March 9, 2004 Novell Inc.
Hex Workshop Price: US $49. 95 Link: www. bpsoft. com General: 11 © March 9, 2004 Novell Inc. General hex editor; includes Base Converter applet.
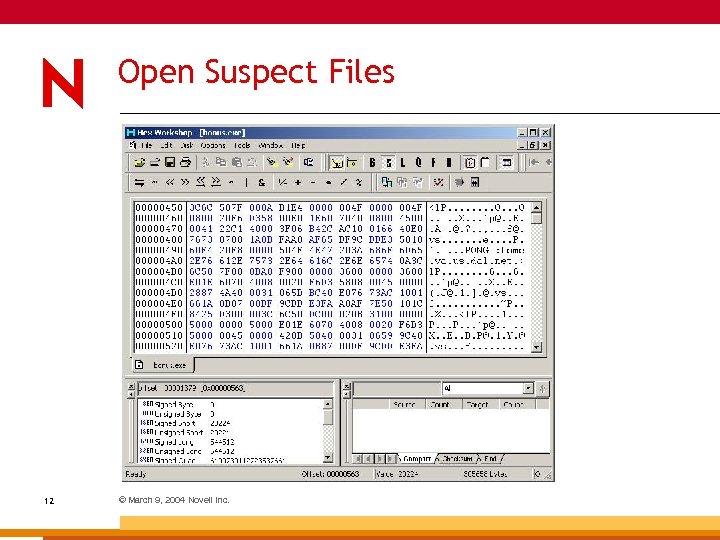
Open Suspect Files 12 © March 9, 2004 Novell Inc.

Net. Scan. Tools Pro Price: US $199. 00 Link: www. netscantools. com General: 13 © March 9, 2004 Novell Inc. Multifunction tool that includes Wizard tool to help trace back and identify a device.

14
Nmap Price: Free Link: www. insecure. org General: 15 © March 9, 2004 Novell Inc. Well-recognized network mapping tool includes timing mechanism, Xmas mapping and idle mapping
The Matrix Reloaded What is Trinity Using? 16 © March 9, 2004 Novell Inc.
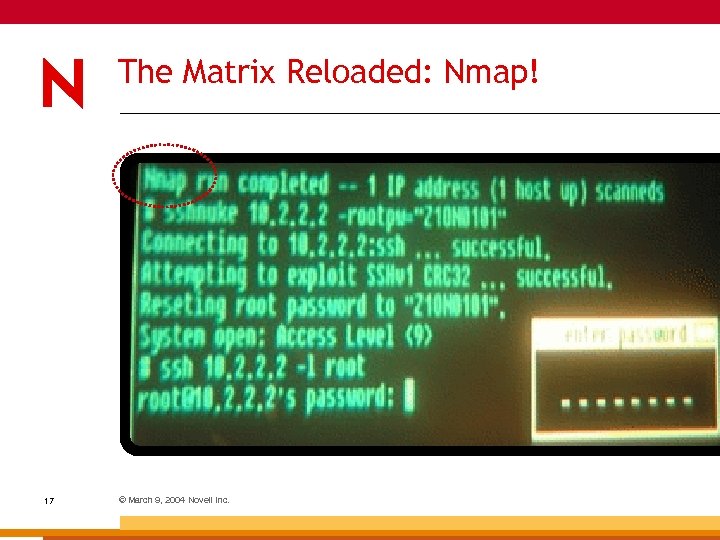
The Matrix Reloaded: Nmap! 17 © March 9, 2004 Novell Inc.
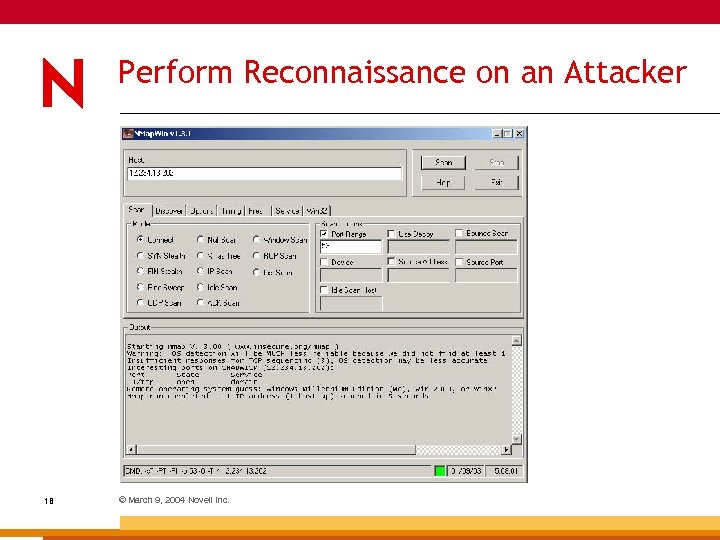
Perform Reconnaissance on an Attacker 18 © March 9, 2004 Novell Inc.
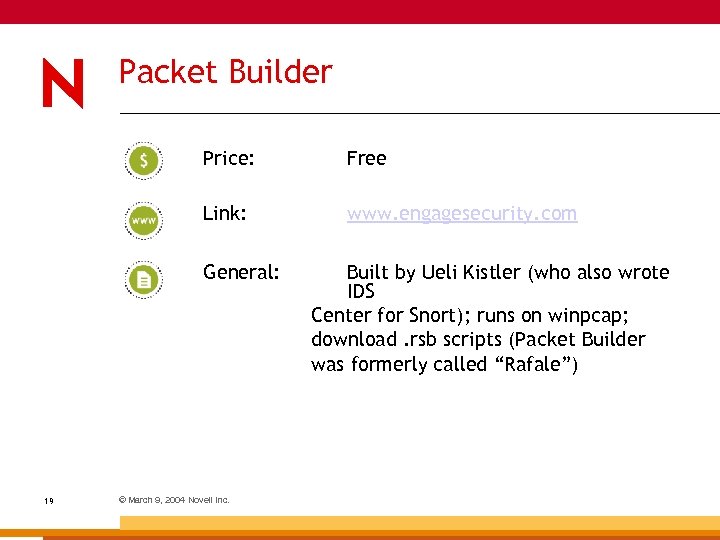
Packet Builder Price: Free Link: www. engagesecurity. com General: 19 © March 9, 2004 Novell Inc. Built by Ueli Kistler (who also wrote IDS Center for Snort); runs on winpcap; download. rsb scripts (Packet Builder was formerly called “Rafale”)
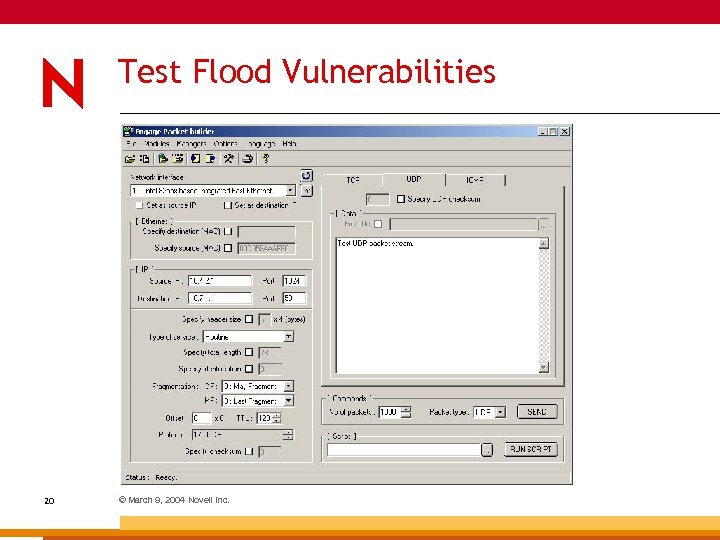
Test Flood Vulnerabilities 20 © March 9, 2004 Novell Inc.
Hurricane Search Price: US $149 Link: www. hurricanesoft. com General: 21 © March 9, 2004 Novell Inc. Grep-like tool; can search through zipped files; use “|” to search for multiple terms.
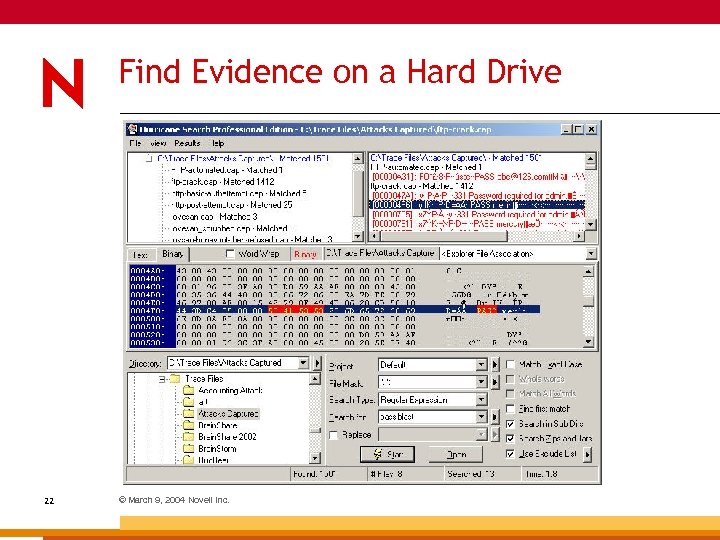
Find Evidence on a Hard Drive 22 © March 9, 2004 Novell Inc.

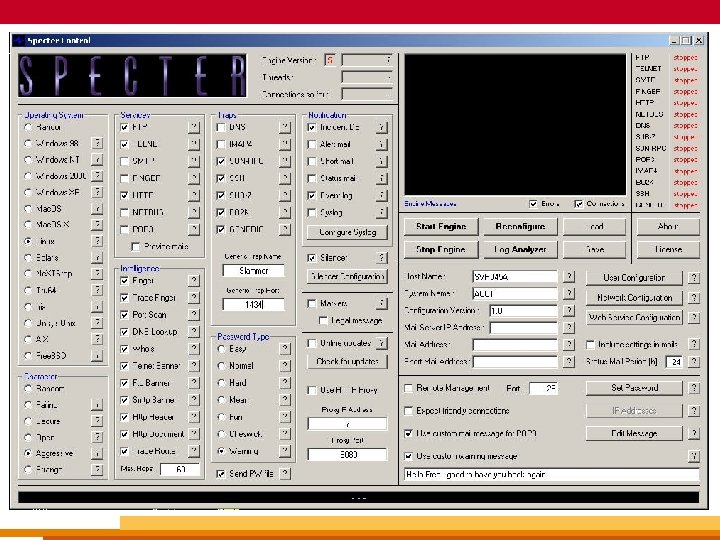
Specter Honeypot Price: Link: General: 23 © March 9, 2004 Novell Inc. $400 -$899 depending on OS spoofing abilities www. specter. com Slick interface; spoofs numerous OS types; silencer option addresses Do. S possibility; use markers to correlate hard drive with an attack.
24
TCPView Price: Free Link: www. sysinternals. com General: 25 © March 9, 2004 Novell Inc. TCP connection and UDP endpoint tracking; tear down connections.
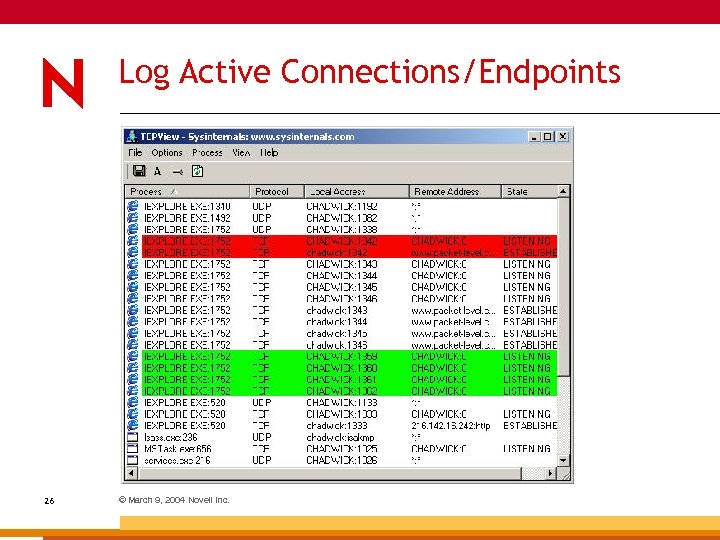
Log Active Connections/Endpoints 26 © March 9, 2004 Novell Inc.

Keyghost Keylogger Price: US $89 (home edition) Link: www. keyghost. com General: 27 © March 9, 2004 Novell Inc. Hardware keylogging device; formats include plug style and full keyboard style.
Keylog a Suspect System 28 © March 9, 2004 Novell Inc.
Brutus Price: Free Link: www. hoobie. net General: 29 © March 9, 2004 Novell Inc. Specialized and brute force password cracking tool; contains 800 word password list; username and password process can be customized.
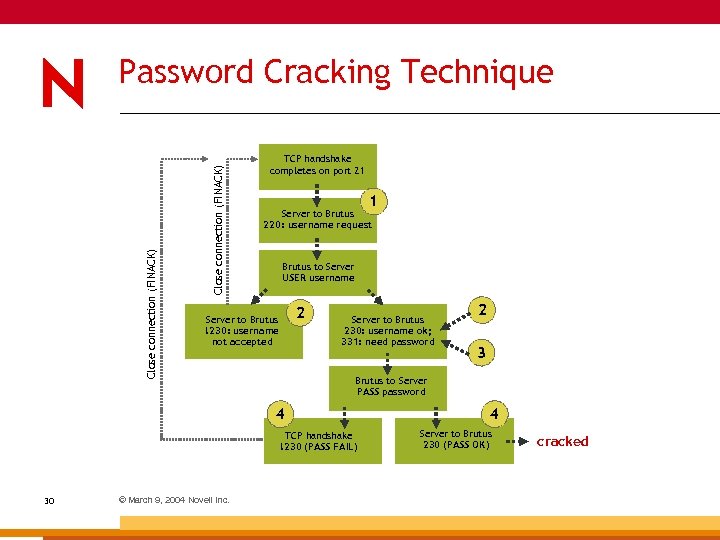
Close connection (FINACK) Password Cracking Technique TCP handshake completes on port 21 1 Server to Brutus 220: username request Brutus to Server USER username 2 Server to Brutus !230: username not accepted Server to Brutus 230: username ok; 331: need password TCP handshake !230 (PASS FAIL) © March 9, 2004 Novell Inc. 3 Brutus to Server PASS password 4 30 2 4 Server to Brutus 230 (PASS OK) cracked
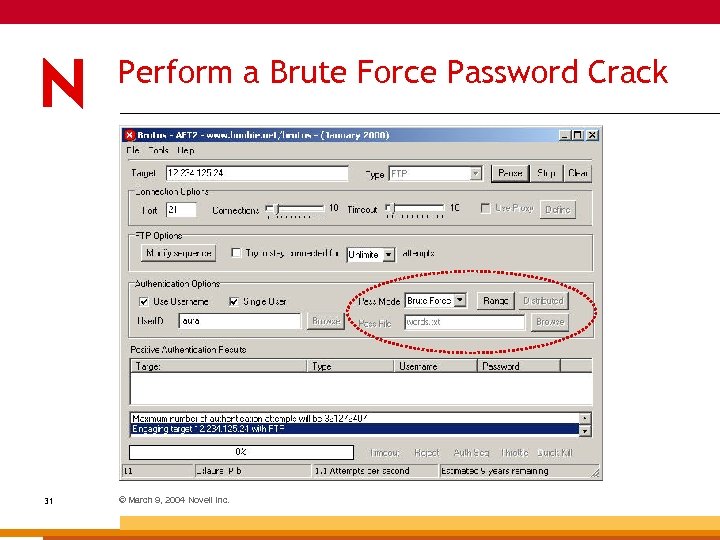
Perform a Brute Force Password Crack 31 © March 9, 2004 Novell Inc.
Aida 32 Price: Free Link: www. aida 32. hu General: 32 © March 9, 2004 Novell Inc. System auditing tool; excellent reporting abilities; can be set in stealth mode for remote auditing (not completely undetectable).
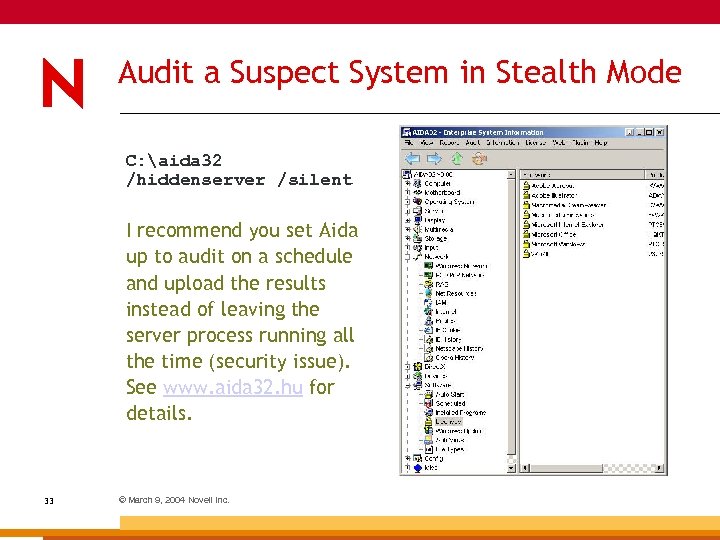
Audit a Suspect System in Stealth Mode C: aida 32 /hiddenserver /silent I recommend you set Aida up to audit on a schedule and upload the results instead of leaving the server process running all the time (security issue). See www. aida 32. hu for details. 33 © March 9, 2004 Novell Inc.
Ettercap Price: Free Link: www. sourceforge. net General: 34 © March 9, 2004 Novell Inc. Traffic intercepter using Man-in-the Middle attack method; catches passwords; can inject data into traffic; can alter date in traffic path.
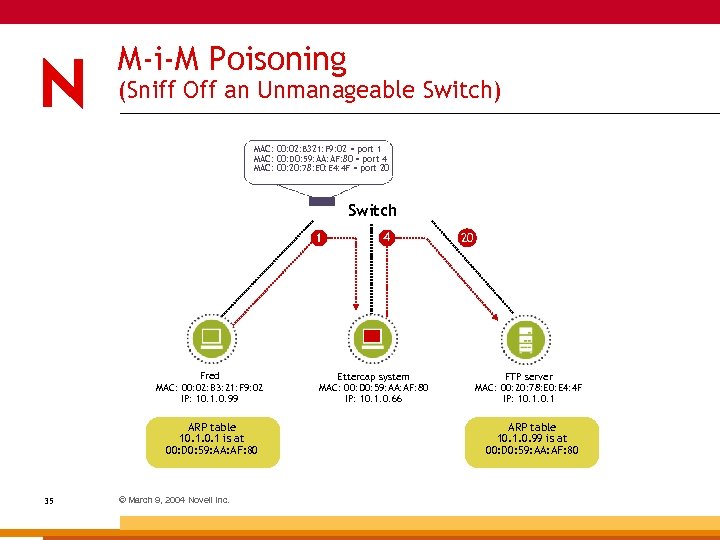
M-i-M Poisoning (Sniff Off an Unmanageable Switch) MAC: 00: 02: B 321: F 9: 02 = port 1 MAC: 00: D 0: 59: AA: AF: 80 = port 4 MAC: 00: 20: 78: E 0: E 4: 4 F = port 20 Switch 1 Fred MAC: 00: 02: B 3: 21: F 9: 02 IP: 10. 1. 0. 99 ARP table 10. 1 is at 00: D 0: 59: AA: AF: 80 35 © March 9, 2004 Novell Inc. 4 Ettercap system MAC: 00: D 0: 59: AA: AF: 80 IP: 10. 1. 0. 66 20 FTP server MAC: 00: 20: 78: E 0: E 4: 4 F IP: 10. 1 ARP table 10. 1. 0. 99 is at 00: D 0: 59: AA: AF: 80
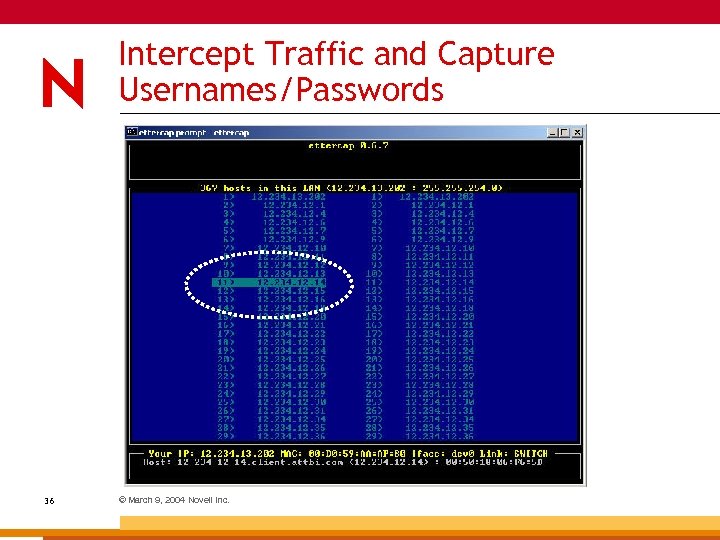
Intercept Traffic and Capture Usernames/Passwords 36 © March 9, 2004 Novell Inc.
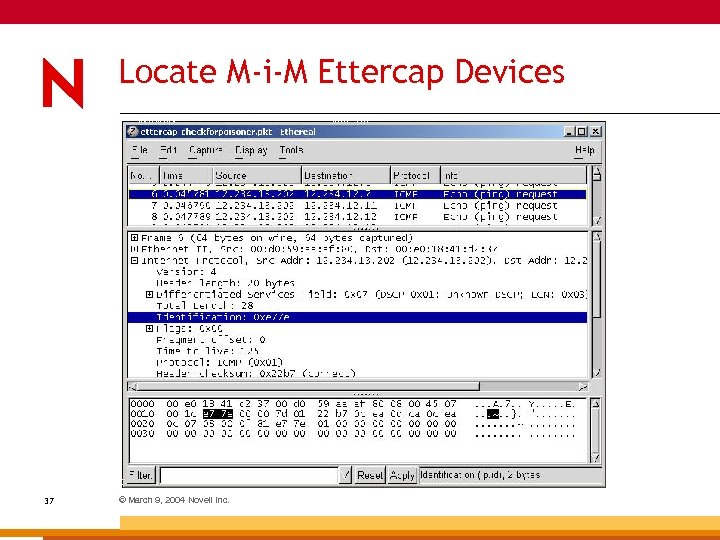
Locate M-i-M Ettercap Devices 37 © March 9, 2004 Novell Inc.
LANguard Network Scanner Price: US $295 and up Link: www. gfi. com General: 38 © March 9, 2004 Novell Inc. Vulnerability scanner; OS fingerprinting; port scanning; locate open shares; locate cgi script vulnerabilities; patch/hotfix detection.
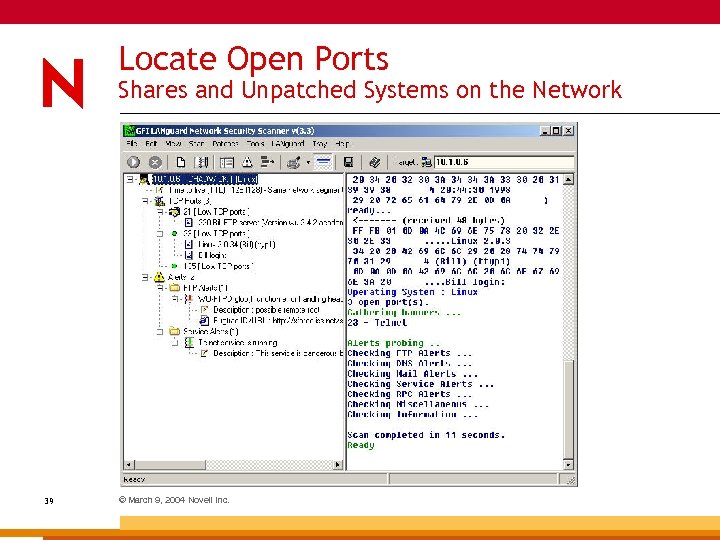
Locate Open Ports Shares and Unpatched Systems on the Network 39 © March 9, 2004 Novell Inc.
Visual. Route Price: US $49. 95 and up Link: www. visualware. com General: 40 © March 9, 2004 Novell Inc. Visual representation of traceroute operation; includes whois functionality.
Trace Back Suspicious Email 41 © March 9, 2004 Novell Inc.
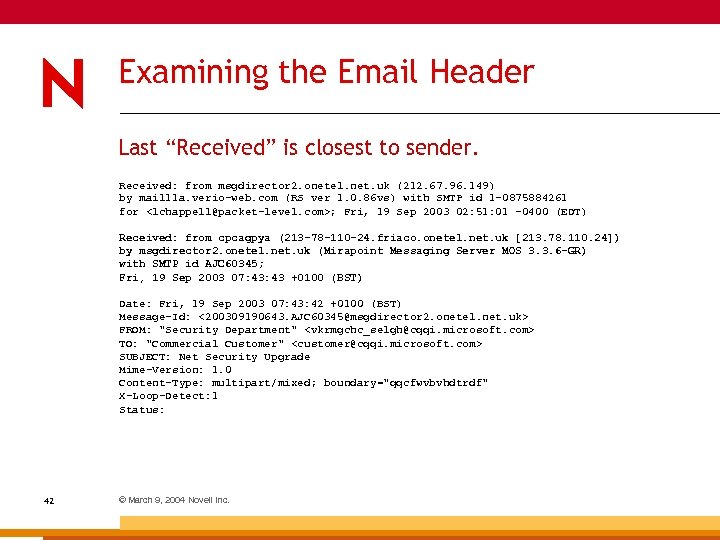
Examining the Email Header Last “Received” is closest to sender. Received: from msgdirector 2. onetel. net. uk (212. 67. 96. 149) by mail 11 a. verio-web. com (RS ver 1. 0. 86 vs) with SMTP id 1 -0875884261 for <lchappell@packet-level. com>; Fri, 19 Sep 2003 02: 51: 01 -0400 (EDT) Received: from cpcagpya (213 -78 -110 -24. friaco. onetel. net. uk [213. 78. 110. 24]) by msgdirector 2. onetel. net. uk (Mirapoint Messaging Server MOS 3. 3. 6 -GR) with SMTP id AJC 60345; Fri, 19 Sep 2003 07: 43 +0100 (BST) Date: Fri, 19 Sep 2003 07: 43: 42 +0100 (BST) Message-Id: <200309190643. AJC 60345@msgdirector 2. onetel. net. uk> FROM: "Security Department" <vkrmgchc_selgh@cqqi. microsoft. com> TO: "Commercial Customer" <customer@cqqi. microsoft. com> SUBJECT: Net Security Upgrade Mime-Version: 1. 0 Content-Type: multipart/mixed; boundary="qqcfwvbvhdtrdf" X-Loop-Detect: 1 Status: 42 © March 9, 2004 Novell Inc.
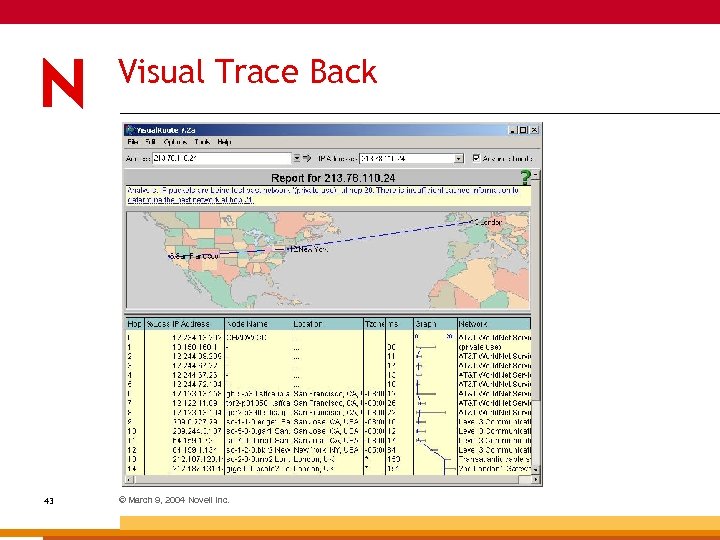
Visual Trace Back 43 © March 9, 2004 Novell Inc.
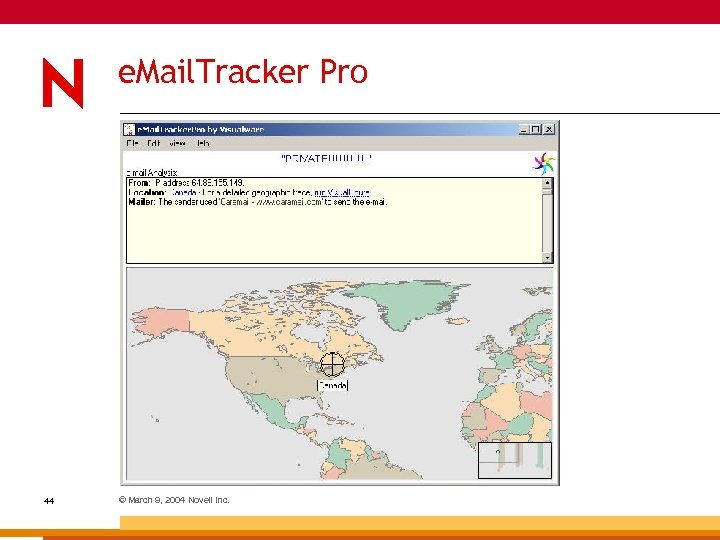
e. Mail. Tracker Pro 44 © March 9, 2004 Novell Inc.
HTTP Sniffer Price: US $29. 95 Link: www. effetech. com General: 45 © March 9, 2004 Novell Inc. HTTP traffic sniffer; graphic reassembler.
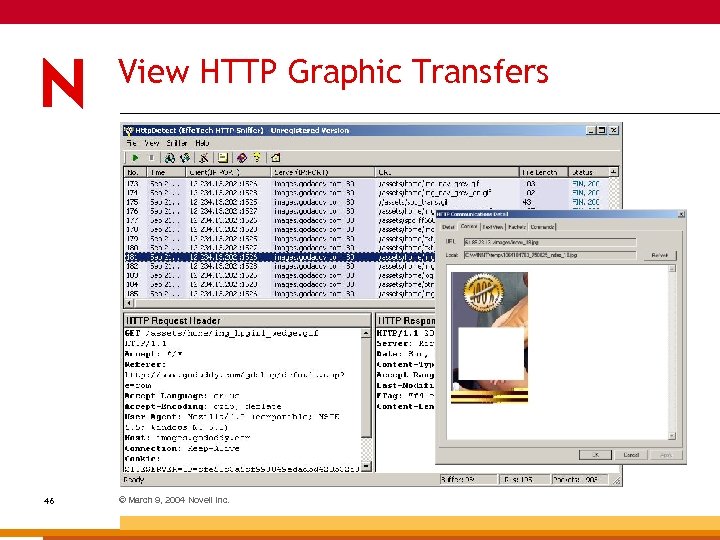
View HTTP Graphic Transfers 46 © March 9, 2004 Novell Inc.
Net. Stumbler/Mini. Stumbler Price: Link: www. netstumbler. com General: 47 Free Wireless access point locater; denotes whether WEP is enabled; displays signal-to-noise ratio © March 9, 2004 Novell Inc.
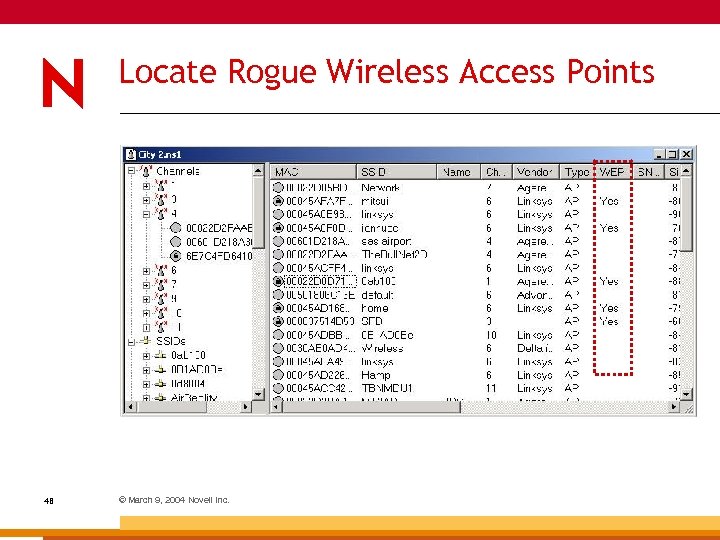
Locate Rogue Wireless Access Points 48 © March 9, 2004 Novell Inc.
Anonymizer Price: US $29. 95 Link: www. anonymizer. com General: 49 © March 9, 2004 Novell Inc. Anonymous surfing tool; also includes some added features such as cookie erasing and pop-up blocking.

Conclusion • • Work with the tools listed (with appropriate authorization, of course). • Get the trace files of the tools as they are run. • 50 Join the Protocol Analysis Institute mailing list online at www. packet-level. com. Send me your tools list! © March 9, 2004 Novell Inc.

51 © March 9, 2004 Novell Inc.


General Disclaimer This document is not to be construed as a promise by any participating company to develop, deliver, or market a product. Novell, Inc. , makes no representations or warranties with respect to the contents of this document, and specifically disclaims any express or implied warranties of merchantability or fitness for any particular purpose. Further, Novell, Inc. , reserves the right to revise this document and to make changes to its content, at any time, without obligation to notify any person or entity of such revisions or changes. All Novell marks referenced in this presentation are trademarks or registered trademarks of Novell, Inc. in the United States and other countries. All third-party trademarks are the property of their respective owners. No part of this work may be practiced, performed, copied, distributed, revised, modified, translated, abridged, condensed, expanded, collected, or adapted without the prior written consent of Novell, Inc. Any use or exploitation of this work without authorization could subject the perpetrator to criminal and civil liability. 53 © March 9, 2004 Novell Inc.
170abb51872d9bd6e2572c2d8b4249b1.ppt