42e2c9451821a864e6d2a4dba05e0d9d.ppt
- Количество слайдов: 62

Honeynet By: A. Qahtan 1. A. Qahtan Prepared for: Dr. Khaled Salah 1

Outlines l l l l Introduction Terminology Honeynet Requirements Honeynet Usage Honeynet Risks Honeypot Virtualization Honeynet Tools Defeating Honeynets A. Qahtan 2

Introduction Computer security was primarily defensive l Firewalls, Intrusion Detection Systems, Encryption l Mechanisms to defensively protect computer resources ¡ Attackers have the initiative ¡ l Honeynet attempts to change that A. Qahtan 3

Introduction Honeynet attempt to attract attackers to a system where everything is monitored. l Using Honeynets l Attackers can be identified ¡ New attacking tools can be discovered ¡ Attack patterns can be determined ¡ Attacker motives can be studied ¡ A. Qahtan 4
Honeypot l A honeypot is a security resource whose value lies in being probed, attacked or compromised ¡ ¡ Detect automated probes and attacks Capture tools, new worms, etc. Raise awareness Identify infected/compromised machines A. Qahtan 5
Honeypot Advantages l There is no normal traffic ¡ l Everything is suspicious and potentially malicious Less data to analyze than IDS system ¡ Dramatically reducing if not eliminating false positives Provide valuable information about attackers l Capture new types of malware l Work in IPv 6 and encrypted environments l A. Qahtan 6

Honeypot Disadvantages Potential risks for your network l Time consuming to maintain l Narrow view l ¡ Bad guys have to probe, use or communicate with the honeypot for it to work A. Qahtan 7
Types of Honeypots l Low-interaction ¡ ¡ ¡ ¡ Emulate some parts of services and systems Attacker does not have access to the real OS Attacker can’t compromise the honeypot Easy to install and maintain Low risk Limited information gathering Examples l Listeners, Service emulators, honeyd, tiny honeypot A. Qahtan 8
Types of Honeypots l High-interaction More difficult to install and maintain ¡ High risk ¡ Need containment mechanisms ¡ Extensive information gathering ¡ Examples ¡ l Honeynets, Virtual honeynets A. Qahtan 9

Honey. Token l A honeypot that is not a computer (some type of digital entity) ¡ ¡ e. g. Credit card number, Excel spreadsheet, Power. Point presentation, a database entry, or even a bogus login Bogus credit card numbers can be embedded in a database SSN honeytokens in the students’ database at universities IDS sensors could be configured to watch the local networks for these honeytoken numbers l If detected on the wire, then the databases have most likely been compromised A. Qahtan 10

Honey. Token (example) l Company is concerned about internal employees attempting to find company secrets ¡ Create a bogus email, or honeytoken To: Chief Financial Officer From: Security help desk Subject: Access to financial database Sir, The security team has updated your access to the company's financial records. Your new login and password to the system can be found below. If you need any help or assistance, do not hesitate to contact us. https: //finances. ourcompany. com login: cfo password: Ch 13 ff 1 n Security Help Desk A. Qahtan 11
Honey. Monkey Honeymonkey is a new way of detecting malicious codes from websites that try to exploit certain vulnerabilities of Internet browsers l Automated web/internet patrol system l ¡ ¡ ¡ l To detect harmful materials in the Internet To come up with solutions To catch the people behind these malicious acts. Computer system logs on to websites like a normal computer system to detect harmful codes that a certain website might try to inject or silently install onto computers that access it. A. Qahtan 12
Commercial Honeypots l Mantrap from Recourse Technologies (requires Solaris) Emulates up to 4 hosts (each running Solaris) running various services ¡ Virtually run any application ¡ l Specter (requires Windows NT) ¡ Can emulate 11 operating systems. Limited to emulating 13 different vulnerable services. A. Qahtan 13
Commercial Honeypots l Netfacade (requires Solairs) ¡ l Able to simulate 8 different OSes and 13 different services. Deception Toolkit ¡ Set of PERL scripts that can emulate various vulnerable services. A. Qahtan 14

Commercial Honeypots Easy to install, configure, deploy, manage and maintain l normally very expensive l managed by administrators with less skills and knowledge l ¡ Via administrative GUI ¡ Come with many different functions and utilities A. Qahtan 15

Homemade Honeypots Require a considerable amount of effort and time to implement l Require one with good skill and knowledge to manage it l Not limited to customization and configuration l A. Qahtan 16
Honeynet l l l A network of high-interaction honeypots Real system computers left in their default (and insecure) configuration Multiple systems and applications Sits behind a firewall where all inbound and outbound data is contained, captured and controlled Captured information is then analyzed to learn the tools, tactics, and motives of the hacker community A. Qahtan 17
Honeyfarm Honeypots alone have a limited field of view l Solution – honeyfarms l ¡ ¡ Multiple honeypots or even honeynets running vulnerable services are centrally operated Each honeypot virtually belonging to different network domains. Distributed presence Deploying redirectors l ¡ ¡ A redirector acts as a proxy or 'worm hole' that transports an attacker's probes to a honeypot within the honeypot farm Centralized management Convenient attack correlation and data mining. A. Qahtan 18
Honeynet Farm - example Honeynet Research Alliance A. Qahtan 19
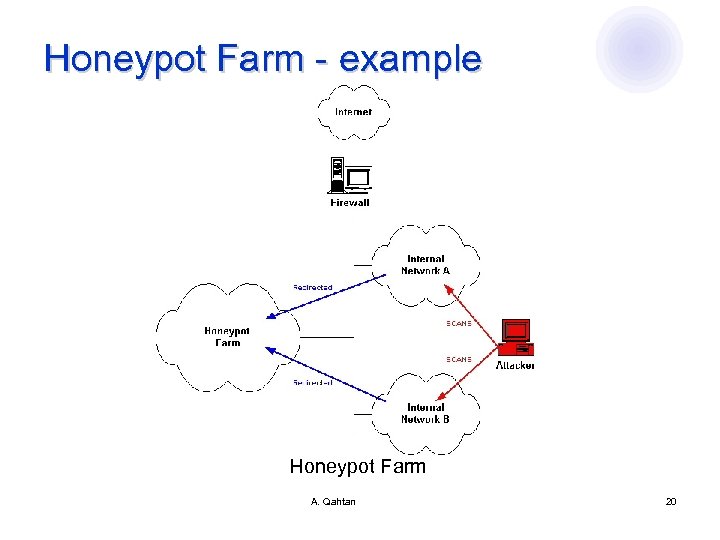
Honeypot Farm - example Honeypot Farm A. Qahtan 20
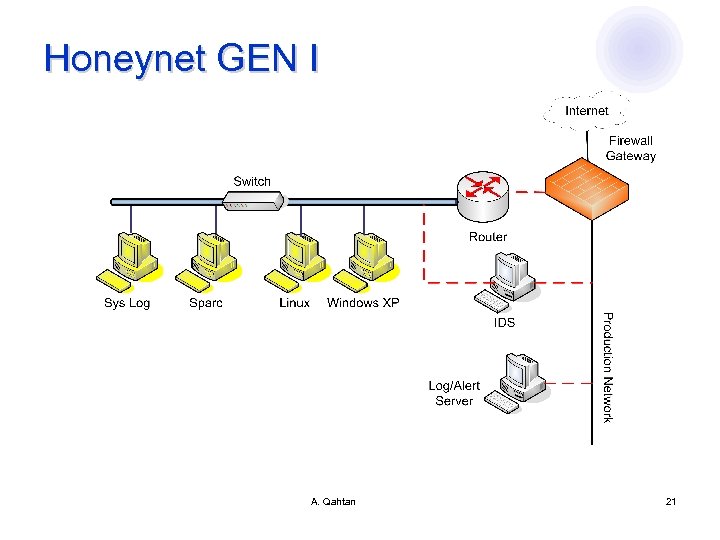
Honeynet GEN I A. Qahtan 21
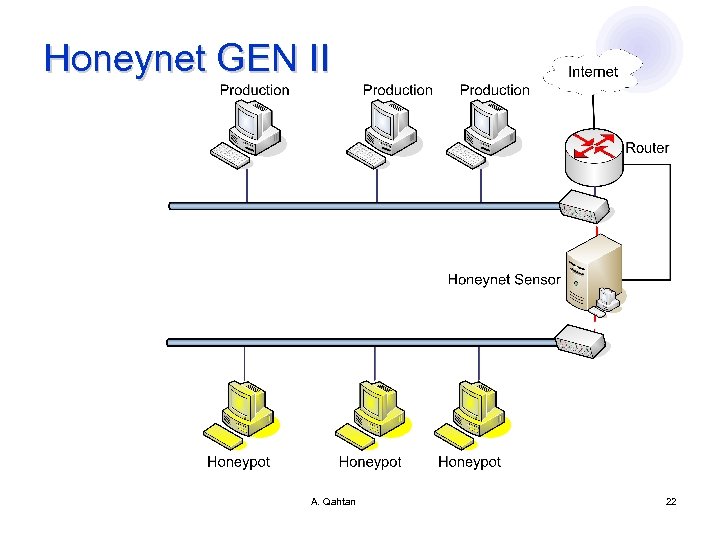
Honeynet GEN II A. Qahtan 22
GEN II l Honeynet sensor (honeywall gateway) ¡ ¡ Layer two bridge (layer three routing gateway can be used also) Bridge is preferred, as it is harder to detect Separates production systems from the honeynet network Three interfaces l eth 0 connected to the production systems' network eth 1 connected to the honeynet systems' network l eth 2 for remote administration of the gateway l A. Qahtan 23
Honeynet Requirements l Data Control l Data Capture l Data Collection l Alerting Mechanism A. Qahtan 24

Data Control Prevent attackers from using the honeynet to attack or harm other non-honeynet systems l Mitigates risk, it does not eliminate it l stealthiness vs safety l More you allow = more you can learn ¡ More you allow = more harm they can potentially cause ¡ A. Qahtan 25
Data Control: Firewall is the primary tool for controlling inbound and outbound connections. l Firewall is designed to allow any inbound connection and limit the number of outbound connections l A. Qahtan 26

Data Control: Router Supplements the firewall l Protect against spoofed or ICMP based attacks l Allows only packets with the source IP address of the Honeynet to leave the router (ingress filtering) l A. Qahtan 27

Data Control: NIPS Inspecting each packet as it travels through our gateway l On matching any of the IDS rules, alert is generated and packet can be dropped (blocking the attack) or modified (disabling the attack) l A. Qahtan 28
Data Capture: NIDS Log all attacker activities l Firewall logs all connections initiated to and from the Honeynet l IDS logs ALL data in tcpdump format l IDS configured to send an alert when certain attack signatures are seen l A. Qahtan 29
Data Capture: Sys. Log The central syslog server is a hardened host within the honeynet l Attract more sophisticated attacks once a blackhat has compromised one of the default configuration honeynet systems l A. Qahtan 30

Data Collection Applies to organizations that have multiple honeynets in distributed environments l Single honeynet requires only data control and data capture l Multiple honeynets have to collect all of the captured data and store it in a central location l Captured data can be combined, exponentially increasing its value l l Honeyfarm A. Qahtan 31
Alerting Some organizations that cannot support 24/7 staff l Alternative is automated alerting l Automated monitoring using Swatch, the Simple Watcher l A. Qahtan 32

Honeynet Usage l l l Learn about hackers Tune the IT security process Intrusion prevention Honeypot-based forensics Eliminating false positive of the IDSs A. Qahtan 33

Honeynet Risks Attracting attention to their seemingly insecure configuration l Require constant maintenance and administration l Data Analysis is very time consuming l ¡ l Single compromise on average requires 30 -40 hours of analysis Risk of detection A. Qahtan 34

Honeypot Virtualization Tar pits l VMWare l Honeyd l UML l A. Qahtan 35

Tar Pits Computer entity that intentionally responds slowly to incoming requests l Delude clients l ¡ l Layer 7 tarpits (defeating spammers) ¡ l Unauthorized or illicit use of a fake service might be logged and slowed down Looks like open mail relays, but instead answer very slowly to SMTP commands Layer 4 Labrea tarpit ¡ ¡ ¡ Slow down the spread of worms over the Internet TCP window size reduced to zero Tar pit continues to acknowledge incoming packets A. Qahtan 36
VMWare Commercial software for virtual machines l Allows you to launch multiple instances of different operating systems on a single piece of hardware l ¡ ¡ Isolates OSes in secure virtual machines Maps the physical hardware resources to the virtual machine's resources Emulates x 86 hardware l Widely used by honeypot operators l Allows easy deployment of honeypots l A. Qahtan 37
Honeyd l l l Open source honeypot daemon Was used with another tool arpd Arpd answeres ARP requests in order to redirect needed traffic to Honeyd Simulates several virtual hosts at the same time Permits configuration of arbitrary services Supports only IPv 4, TCP, UDP and ICMP protocols A. Qahtan 38
User-Mode Linux (UML) Free software under the GPL l Create virtual machines l Virtualizes Linux itself l ¡ ¡ l Runs an entire Linux environment in user-space Runs multiple instances of Linux on the same hardware Dedicated to Linux A. Qahtan 39
Building Blocks Honeywall l Sebek l Bait and switch technique l A. Qahtan 40
Honeywall Data capture and data control l IDS snort / IPS snort_inline l Netfilter/iptables for traffic limiting l Further monitoring - swatch l A. Qahtan 41

Snort_inline Inline packet modification engine l Modified version Snort (in recent snort version it becomes part of snort) l Adds several new rule types (drop, sdrop and reject) l Provides packet rewriting from something dangerous into something harmless l ¡ e. g replacing the string /bin/sh by /ben/sh using the rule alert ip $HONEYNET any -> $EXTERNAL_NET any (msg: "SHELLCODE x 86 stealth NOOP"; sid: 651; content: "|EB 02|"; replace: "|24 00 99 DE 6 C 3 E|"; ) A. Qahtan 42

Netfilter/iptables for traffic limiting Netfilter/iptables-functionality of the Linux kernel for connection limitation l Prevents the abuse of a compromised honeypot for: l ¡ l Denial-of-service attacks, mass scanning, download toolkits and setup automated bots Honeynet Project allows 15 outgoing TCP-connections and 50 outgoing ICMP packets per day [. . . ] ### Set the connection outbound limits for different protocols. SCALE="day" TCPRATE="15" UDPRATE="20" ICMPRATE="50" OTHERRATE="15" A. Qahtan [. . . ] 43
Sebek Client/server based application l The primary data capture tool used by honeynet researchers l Kernel-module on Linux & Solaris, patch on Open. BSD / Net. BSD, device driver for Windows l Kernel-based rootkit that hijacks the read() system call l ¡ Remember API Hooking ? ? Record all data accessed via read() l Send data passing through sys_read() in covert manner over the network to the sebek server l Overwrites part of the network stack (packet_recvmsg) to hide Sebek data passing on to the network l Network counters and data structures have to be adapted l A. Qahtan 44

Bait and switch technique l l l l Follows the security paradigm of "Protect, Detect and React“ Protect the network as best as possible (Firewalls) Detect any failures in the defense (IDS) React to failures (alerting) Bait and Switch redirects all malicious network traffic to a honeypot Attacker is attacking a trap instead of real data based on Snort, iproute 2, netfilter/iptables and some custom code A. Qahtan 45

Defeating Honeynets l l l Tarpits VMWare Snort_inline Netfilter/iptables Sebek Bait and switch A. Qahtan 46
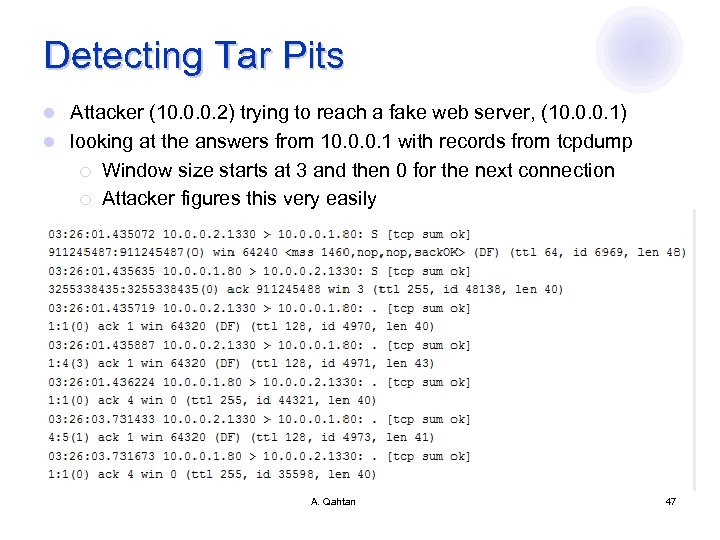
Detecting Tar Pits Attacker (10. 0. 0. 2) trying to reach a fake web server, (10. 0. 0. 1) l looking at the answers from 10. 0. 0. 1 with records from tcpdump ¡ Window size starts at 3 and then 0 for the next connection ¡ Attacker figures this very easily l A. Qahtan 47
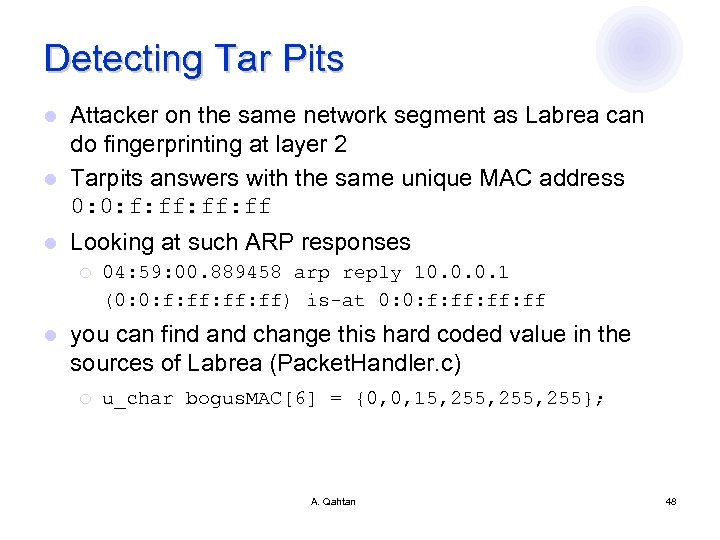
Detecting Tar Pits Attacker on the same network segment as Labrea can do fingerprinting at layer 2 l Tarpits answers with the same unique MAC address 0: 0: f: ff: ff l l Looking at such ARP responses ¡ l 04: 59: 00. 889458 arp reply 10. 0. 0. 1 (0: 0: f: ff: ff) is-at 0: 0: f: ff: ff you can find and change this hard coded value in the sources of Labrea (Packet. Handler. c) ¡ u_char bogus. MAC[6] = {0, 0, 15, 255, 255}; A. Qahtan 48

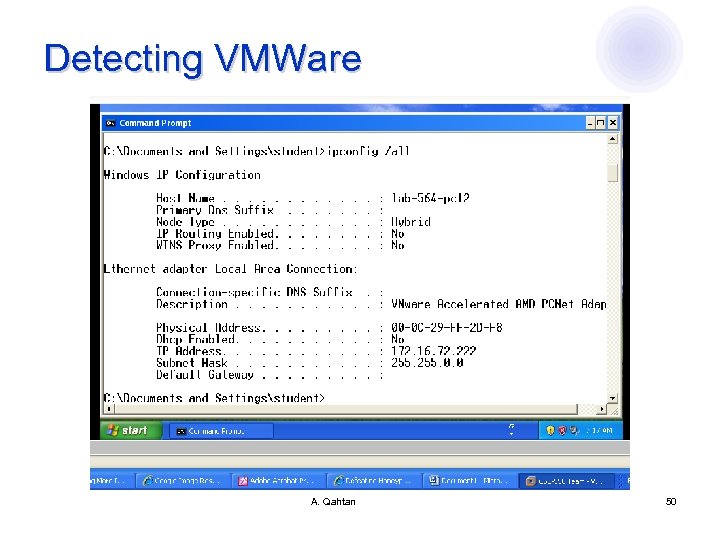
Detecting VMWare l IEEE standards assigned MAC addresses to VMWare in the ranges ¡ 00 -05 -69 -xx-xx-xx 00 -0 C-29 -xx-xx-xx ¡ 00 -50 -56 -xx-xx-xx ¡ l MAC addresses can be obtained via ¡ ¡ l arp –a Unix: ifconfig or Windows: ipconfig /all Honeypots operators usually the Net. BIOS port ¡ ¡ Attacker interacts with Net. BIOS services can obtain the MAC address using commands Unix: nmblookup or Windows: nbtstat -A @IP A. Qahtan 49
Detecting VMWare A. Qahtan 50
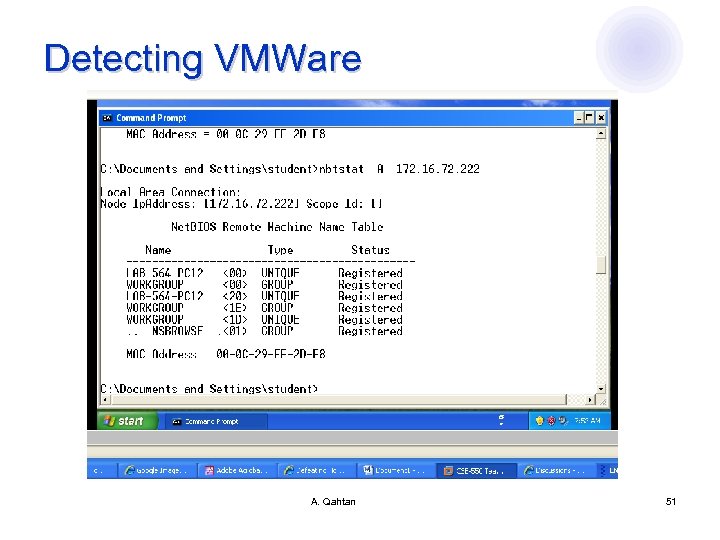
Detecting VMWare A. Qahtan 51

Detecting Snort_inline Dropping of outgoing packets = blackhole l Modification = can be detected by sophisticated attacker l Stealthiness of Snort_inline can be increased with fewer rules, but this leads to more attacks that will not be noticed l A. Qahtan 52

Detecting Netfilters/iptables l Aggressor can simply try to Open many outgoing connections to different hosts ¡ Send a lot of ICMP echo request packets to varying hosts ¡ l If after some time no more outgoing packets can reach the target then it is a honeypot A. Qahtan 53

Detecting Sebek l Latency ¡ ¡ ¡ Read a single byte via a read(1) call = Sebek will transfer nearly 100 bytes of data Do it tens of thousands of times = network congestion e. g. ping a local IP (the gateway) dd if=/dev/zero of=/dev/null bs=1 Ping again Average round-trip time grew from 0. 7 milliseconds to over 4800 milliseconds A. Qahtan 54

Detecting Sebek l Displaying hidden modules ¡ ¡ ¡ Sebek uses cleaner. c, a simple loadable kernel module that unlinks the last module in the kernel's module list module_hunter. c is able to locate hidden modules module_hunter. c searches for patterns of module structures in the kernel's address space and is able to detect modules hidden via unlinking Using the same technique one can get the address of Sebek’s cleanup_module() and disable Sebek Toolkit written in Python 2. 3 can detect and remove Sebek from honeypot l Get the source code at md. hudora. de A. Qahtan 55
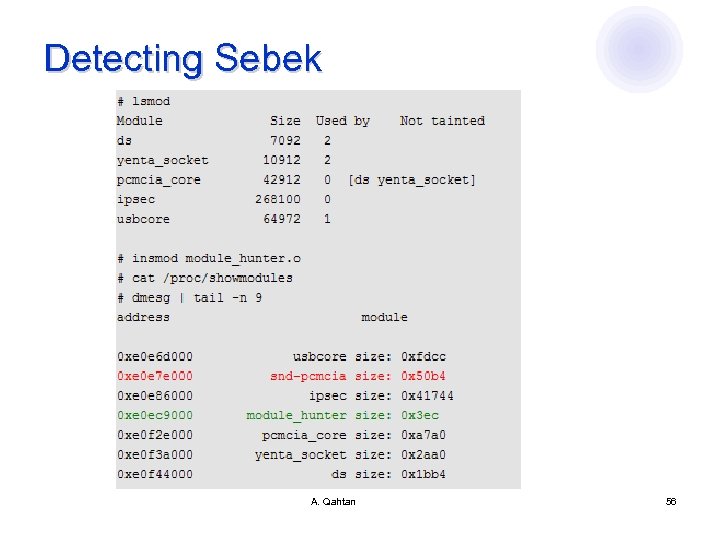
Detecting Sebek A. Qahtan 56
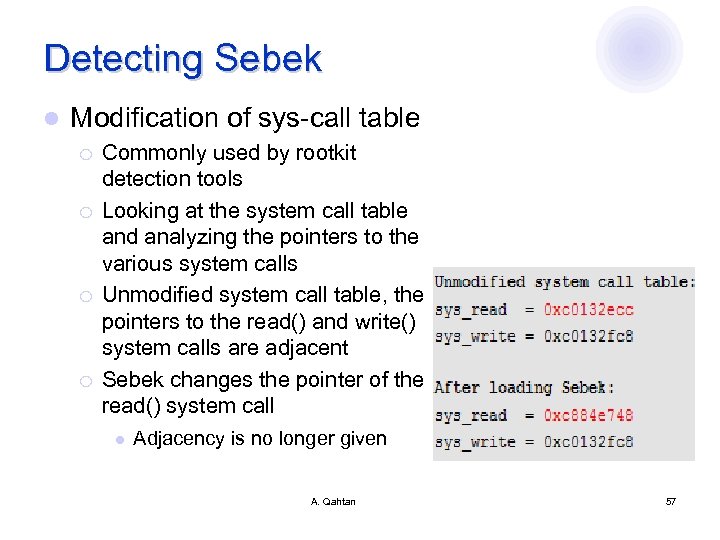
Detecting Sebek l Modification of sys-call table ¡ ¡ Commonly used by rootkit detection tools Looking at the system call table and analyzing the pointers to the various system calls Unmodified system call table, the pointers to the read() and write() system calls are adjacent Sebek changes the pointer of the read() system call l Adjacency is no longer given A. Qahtan 57

Detecting Sebek l Network traffic counters ¡ Sebek adjusts some counters to conceal the transmission of the logging data ¡ Sophisticated attacker compares the kernel's internal network counters and the output of ifconfig or other tools A. Qahtan 58
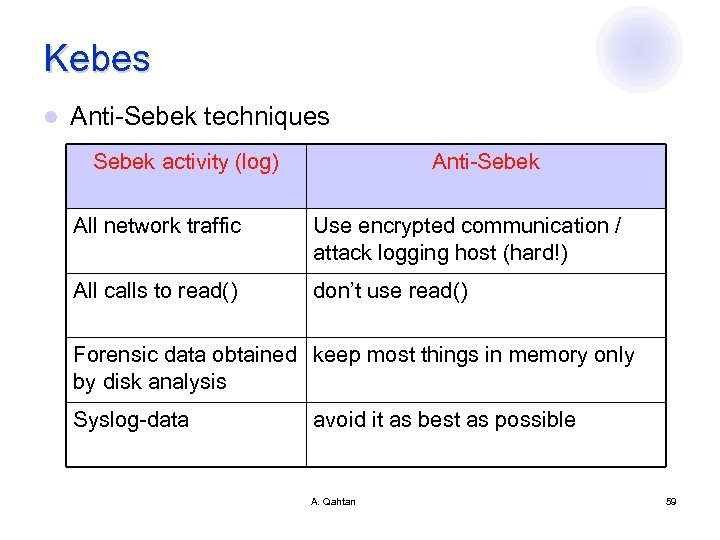
Kebes l Anti-Sebek techniques Sebek activity (log) Anti-Sebek All network traffic Use encrypted communication / attack logging host (hard!) All calls to read() don’t use read() Forensic data obtained keep most things in memory only by disk analysis Syslog-data avoid it as best as possible A. Qahtan 59

Kebes Under the project name No. SEBr. Ea. K l Entirely written in Python 2. 3 for portability with no external dependency l Uses mmap() to avoid read() system calls l Implements all basic functionality of a shell l ¡ Reading and writing of files Secure deleting ¡ Direct executing of programs ¡ l Implements an encrypted channel between the attacker and the honeypot ¡ logging of network activity is useless A. Qahtan 60

Summary l Never end fight between hackers and security community l Honeynets should be carefully deployed and should act as real system (stealthness vs safety) l Be aware of hackers techniques in detecting honeypots A. Qahtan 61

Q&A l Thank A. Qahtan you 62
42e2c9451821a864e6d2a4dba05e0d9d.ppt