55aead2abfb431f5e6b2aa094128efbe.ppt
- Количество слайдов: 92
 Home Computer Security and Privacy: Verification and Prevention a presentation by Patrick Douglas Crispen Faculty Development Center California State University, Fullerton
Home Computer Security and Privacy: Verification and Prevention a presentation by Patrick Douglas Crispen Faculty Development Center California State University, Fullerton
 A quick review: Worms and crackers • Connect to the internet and two things will target and attack your computer: Worms and crackers. • To protect your computer, you need to “hide” it. – If worms and crackers can’t see your computer, they [hopefully] won’t attack you. • How do you hide your computer? Use a firewall.
A quick review: Worms and crackers • Connect to the internet and two things will target and attack your computer: Worms and crackers. • To protect your computer, you need to “hide” it. – If worms and crackers can’t see your computer, they [hopefully] won’t attack you. • How do you hide your computer? Use a firewall.
 A quick review: What is a firewall? • Either hardware or software that stands between your computer and the Internet and provides “access control”—it determines what can and cannot pass. • Broadband users need both a hardware firewall/router and a software firewall. • Dial-up users only need a software firewall.
A quick review: What is a firewall? • Either hardware or software that stands between your computer and the Internet and provides “access control”—it determines what can and cannot pass. • Broadband users need both a hardware firewall/router and a software firewall. • Dial-up users only need a software firewall.
 Uh… WHAT!? If all of this is Greek to you, check out the free “Home Computer Security and Privacy: Firewalls and Exploit Management” presentation at http: //fdc. fullerton. edu/cr ispen/
Uh… WHAT!? If all of this is Greek to you, check out the free “Home Computer Security and Privacy: Firewalls and Exploit Management” presentation at http: //fdc. fullerton. edu/cr ispen/
 Our goals • Double-check your firewall’s effectiveness at preventing attacks. • Verify that your computer really does have all of the critical security patches from Microsoft or Apple. • Learn why up-to-date antivirus software is an absolute necessity. • Protect your computer from spyware and malware. • Do all of this in ENGLISH!
Our goals • Double-check your firewall’s effectiveness at preventing attacks. • Verify that your computer really does have all of the critical security patches from Microsoft or Apple. • Learn why up-to-date antivirus software is an absolute necessity. • Protect your computer from spyware and malware. • Do all of this in ENGLISH!
![Part One: Test your Firewall[s] How can you tell if your firewall is keeping Part One: Test your Firewall[s] How can you tell if your firewall is keeping](https://present5.com/presentation/55aead2abfb431f5e6b2aa094128efbe/image-6.jpg) Part One: Test your Firewall[s] How can you tell if your firewall is keeping the bad stuff out?
Part One: Test your Firewall[s] How can you tell if your firewall is keeping the bad stuff out?
 Testing your firewall • The best way is to have a trusted entity attack it. • There are people called “white hat hackers” or “sneakers” who can do this for you…for a price. – That price is usually the same as the price of a mortgage payment in Beverly Hills. • Or you can do it yourself for free with both “Sygate Online Services” and Steve Gibson’s “Shields Up. ”
Testing your firewall • The best way is to have a trusted entity attack it. • There are people called “white hat hackers” or “sneakers” who can do this for you…for a price. – That price is usually the same as the price of a mortgage payment in Beverly Hills. • Or you can do it yourself for free with both “Sygate Online Services” and Steve Gibson’s “Shields Up. ”
 Sygate Online Services • Sygate is one of the biggest players in the corporate security market, and they also make one of the better software firewalls: Sygate Personal Firewall [http: //smb. sygate. com/] • They also offer a free web tool called “Sygate Online Services” that probes your firewall[s] looking for vulnerabilities. • And since the scan is done online, it works with PCs, Macs, and *nix boxes.
Sygate Online Services • Sygate is one of the biggest players in the corporate security market, and they also make one of the better software firewalls: Sygate Personal Firewall [http: //smb. sygate. com/] • They also offer a free web tool called “Sygate Online Services” that probes your firewall[s] looking for vulnerabilities. • And since the scan is done online, it works with PCs, Macs, and *nix boxes.
 http: //scan. sygate. com/ • scan. sygate. com • Click on the black “Scan Now” button. • This starts something called the “Prescan. ”
http: //scan. sygate. com/ • scan. sygate. com • Click on the black “Scan Now” button. • This starts something called the “Prescan. ”
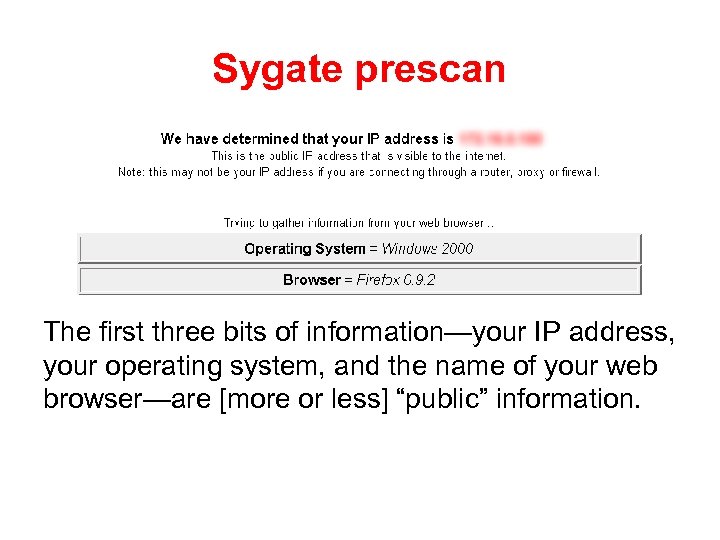 Sygate prescan The first three bits of information—your IP address, your operating system, and the name of your web browser—are [more or less] “public” information.
Sygate prescan The first three bits of information—your IP address, your operating system, and the name of your web browser—are [more or less] “public” information.
 IP and OS and browser, oh my! • If you have a router with NAT, that isn’t your IP address anyway. It’s your router’s. • Your operating system and browser information came from the HTTP GET packet your browser sent when it requested the Sygate web page. – See http: //www. rexswain. com/httpview. html or http: //www. ipchicken. com/ if you don’t believe me. • “There’s nothing to see here. Move along. ”
IP and OS and browser, oh my! • If you have a router with NAT, that isn’t your IP address anyway. It’s your router’s. • Your operating system and browser information came from the HTTP GET packet your browser sent when it requested the Sygate web page. – See http: //www. rexswain. com/httpview. html or http: //www. ipchicken. com/ if you don’t believe me. • “There’s nothing to see here. Move along. ”
 The important stuff • Don’t worry if Sygate can see your computer’s IP address, operating system, or the name of your web browser. • BUT, if Sygate’s can see your computer name or the services running on your computer, your computer could potentially have a serious security problem.
The important stuff • Don’t worry if Sygate can see your computer’s IP address, operating system, or the name of your web browser. • BUT, if Sygate’s can see your computer name or the services running on your computer, your computer could potentially have a serious security problem.
 Windows file and printer sharing Windows comes with a builtin service called “File and Printer Sharing for Microsoft Networks. ” – File sharing lets you make files and folders in a shared folder accessible to others on your home network to view, copy, or modify. – Printer sharing lets you share a printer with all the other computers on your home network. – Check out http: //tinyurl. com/ywh 8 q for more information
Windows file and printer sharing Windows comes with a builtin service called “File and Printer Sharing for Microsoft Networks. ” – File sharing lets you make files and folders in a shared folder accessible to others on your home network to view, copy, or modify. – Printer sharing lets you share a printer with all the other computers on your home network. – Check out http: //tinyurl. com/ywh 8 q for more information
 Your files, now available online • Unless you are really careful, your computer may be sharing your files with everyone on the Internet. • How can you tell? • Scan “port 139” on your computer to see: – If file and printer sharing turned on; and – If those shares are accessible from the Internet.
Your files, now available online • Unless you are really careful, your computer may be sharing your files with everyone on the Internet. • How can you tell? • Scan “port 139” on your computer to see: – If file and printer sharing turned on; and – If those shares are accessible from the Internet.
 Grandma, what big pipes you have! • You connect to the Internet through a single wire —a telephone line, a coaxial cable, etc. • That one wire carries everything: Web pages, instant messages, emails, spam, etc. • How does your computer sort through the wire’s incoming data and forward that data to the appropriate software applications? • Well, your computer uses something called “ports. ”
Grandma, what big pipes you have! • You connect to the Internet through a single wire —a telephone line, a coaxial cable, etc. • That one wire carries everything: Web pages, instant messages, emails, spam, etc. • How does your computer sort through the wire’s incoming data and forward that data to the appropriate software applications? • Well, your computer uses something called “ports. ”
 Ports • Ports don’t exist in the physical world. • They’re “pretend” addresses inside of your computer that your computer uses to route incoming data to the appropriate software application. – Port 80 forwards to your web browser. – Port 110 forwards your email program. – Port 5190 forwards to AIM. • How many of these pretend addresses [or ports] are there? Officially, up to 69, 536. Source: http: //www. iana. org/assignments/port-numbers
Ports • Ports don’t exist in the physical world. • They’re “pretend” addresses inside of your computer that your computer uses to route incoming data to the appropriate software application. – Port 80 forwards to your web browser. – Port 110 forwards your email program. – Port 5190 forwards to AIM. • How many of these pretend addresses [or ports] are there? Officially, up to 69, 536. Source: http: //www. iana. org/assignments/port-numbers
 The potential danger of port 139 • Crackers and script kiddies LOVE port 139, the port used by Windows file and printer sharing. • Cracker and script kiddies have software that scans thousands of Internet connections looking for Windows file and printer shares accessible through port 139. • If the cracker or script kiddie maps to that share, he’s in. It’s as if he was sitting in front of your computer [although, in reality, he can only access the stuff that is being shared. ]
The potential danger of port 139 • Crackers and script kiddies LOVE port 139, the port used by Windows file and printer sharing. • Cracker and script kiddies have software that scans thousands of Internet connections looking for Windows file and printer shares accessible through port 139. • If the cracker or script kiddie maps to that share, he’s in. It’s as if he was sitting in front of your computer [although, in reality, he can only access the stuff that is being shared. ]
 Peek-a-boo! We ALL see you! • Your goal is to have Sygate Online Services to tell you that it was both – Unable to determine your computer name; and – Unable to detect any running services. • If Sygate can’t see your computer, neither can the crackers.
Peek-a-boo! We ALL see you! • Your goal is to have Sygate Online Services to tell you that it was both – Unable to determine your computer name; and – Unable to detect any running services. • If Sygate can’t see your computer, neither can the crackers.
 Uh-oh! • But if Sygate can see you, it means that – You don’t have a firewall. – If you do have a firewall, it either isn’t working or isn’t properly configured. – File and Printer Sharing for Microsoft Networks may be sharing your personal files with the entire planet. • To fix your firewall – Check your firewall’s setup instructions. – Visit the support section of your firewall manufacturer’s web site.
Uh-oh! • But if Sygate can see you, it means that – You don’t have a firewall. – If you do have a firewall, it either isn’t working or isn’t properly configured. – File and Printer Sharing for Microsoft Networks may be sharing your personal files with the entire planet. • To fix your firewall – Check your firewall’s setup instructions. – Visit the support section of your firewall manufacturer’s web site.
 Fixing file and printer sharing To fix the File and Printer Sharing for Microsoft Networks problem, – Call both your Internet Service Provider’s and your school’s/employer’s helpdesks and ask them: “Can you think of any reason why I shouldn’t disable Net. BIOS over TCP/IP on my home computer? ” – If the answer is yes, ask for a handout showing you how to secure your Net. BIOS over TCP/IP connection. – If the answer is no, disable Net. BIOS over TCP/IP. You don’t need it.
Fixing file and printer sharing To fix the File and Printer Sharing for Microsoft Networks problem, – Call both your Internet Service Provider’s and your school’s/employer’s helpdesks and ask them: “Can you think of any reason why I shouldn’t disable Net. BIOS over TCP/IP on my home computer? ” – If the answer is yes, ask for a handout showing you how to secure your Net. BIOS over TCP/IP connection. – If the answer is no, disable Net. BIOS over TCP/IP. You don’t need it.
 Disabling Net. BIOS over TCP/IP See http: //comp. bio. uci. edu/s ecurity/netbios. htm for instructions on how to disable Net. BIOS over TCP/IP.
Disabling Net. BIOS over TCP/IP See http: //comp. bio. uci. edu/s ecurity/netbios. htm for instructions on how to disable Net. BIOS over TCP/IP.
 Wait. There’s more. Once Sygate Online Services’ prescan gives you a clean bill of health, there are four more scans you need to run. 1. 2. 3. 4. Stealth Scan Trojan Scan TCP Scan UDP Scan
Wait. There’s more. Once Sygate Online Services’ prescan gives you a clean bill of health, there are four more scans you need to run. 1. 2. 3. 4. Stealth Scan Trojan Scan TCP Scan UDP Scan
 Stealth Scan • This re-runs the prescan using common cracker stealthing techniques to try to sneak past your firewall. • Takes about 30 seconds.
Stealth Scan • This re-runs the prescan using common cracker stealthing techniques to try to sneak past your firewall. • Takes about 30 seconds.
 What you’re looking for • Your goal is to have the Stealth Scan tell you that all of the ports it scanned are "blocked. " • However, if Sygate tells you that a particular port is "Closed" instead of blocked, you could have a problem. – Sygate is telling you that while it couldn't break into that particular port it could still see it. – Remember: If a port can been seen it can be attacked. – You need to IMMEDIATELY check your firewall's setup instructions or the manufacturer's web site to find out how to "stealth" that particular port.
What you’re looking for • Your goal is to have the Stealth Scan tell you that all of the ports it scanned are "blocked. " • However, if Sygate tells you that a particular port is "Closed" instead of blocked, you could have a problem. – Sygate is telling you that while it couldn't break into that particular port it could still see it. – Remember: If a port can been seen it can be attacked. – You need to IMMEDIATELY check your firewall's setup instructions or the manufacturer's web site to find out how to "stealth" that particular port.
![Beware of G[r]eeks bearing gifts • After the Stealth Scan run a Trojan Scan. Beware of G[r]eeks bearing gifts • After the Stealth Scan run a Trojan Scan.](https://present5.com/presentation/55aead2abfb431f5e6b2aa094128efbe/image-25.jpg) Beware of G[r]eeks bearing gifts • After the Stealth Scan run a Trojan Scan. • A Trojan Horse is a type of virus that masquerades as a legitimate program but contains a payload that can damage your computer. • Many Trojan Horses have backdoors—they attach themselves to a particular port to listen for an activate command from the internet. – See http: //scan. sygate. com: 443/cgibin/probe/trojans. cgi for more information
Beware of G[r]eeks bearing gifts • After the Stealth Scan run a Trojan Scan. • A Trojan Horse is a type of virus that masquerades as a legitimate program but contains a payload that can damage your computer. • Many Trojan Horses have backdoors—they attach themselves to a particular port to listen for an activate command from the internet. – See http: //scan. sygate. com: 443/cgibin/probe/trojans. cgi for more information
 Trojan Scan • Sygate's Trojan Scan searches through over 65, 000 ports looking for Trojan Horses hiding on your computer. • Takes about 20 minutes
Trojan Scan • Sygate's Trojan Scan searches through over 65, 000 ports looking for Trojan Horses hiding on your computer. • Takes about 20 minutes
 What you’re looking for • If your firewall is working properly, there won't be anything for Sygate to scan so it will angrily give up. • BUT, if Sygate finds a Trojan Horse on your computer – Write the name of the Trojan Horse on a piece of paper – Go to http: //www. symantec. com/avcenter/vinfodb. html and search for that Trojan's removal instructions.
What you’re looking for • If your firewall is working properly, there won't be anything for Sygate to scan so it will angrily give up. • BUT, if Sygate finds a Trojan Horse on your computer – Write the name of the Trojan Horse on a piece of paper – Go to http: //www. symantec. com/avcenter/vinfodb. html and search for that Trojan's removal instructions.
 TCP Scan • Sygate’s TCP Scan checks if any of the first 1, 024 ports on your computer are both open for attack and visible to crackers. • Can take up to 45 minutes.
TCP Scan • Sygate’s TCP Scan checks if any of the first 1, 024 ports on your computer are both open for attack and visible to crackers. • Can take up to 45 minutes.
![What you’re looking for • If your firewall is working properly, Sygate will [eventually] What you’re looking for • If your firewall is working properly, Sygate will [eventually]](https://present5.com/presentation/55aead2abfb431f5e6b2aa094128efbe/image-29.jpg) What you’re looking for • If your firewall is working properly, Sygate will [eventually] tell you that all of your first 1, 024 TCP ports are closed to outside attack. • BUT, If Sygate tells you that a particular port is "Open, " immediately check your firewall's setup instructions or the manufacturer's web site to find out how to both close and stealth that particular port.
What you’re looking for • If your firewall is working properly, Sygate will [eventually] tell you that all of your first 1, 024 TCP ports are closed to outside attack. • BUT, If Sygate tells you that a particular port is "Open, " immediately check your firewall's setup instructions or the manufacturer's web site to find out how to both close and stealth that particular port.
 UDP Scan • Besides TCP ports your computer also has UDP ports. • Sygate’s UDP Scan tells you if any UDP ports on your computer are both open for attack and visible to crackers. • Can take up to 20 minutes.
UDP Scan • Besides TCP ports your computer also has UDP ports. • Sygate’s UDP Scan tells you if any UDP ports on your computer are both open for attack and visible to crackers. • Can take up to 20 minutes.
 What you’re looking for • Like with the previous scans, you’re hoping that Sygate tells your firewall blocked all of its probes. • BUT, if Sygate tells your firewall isn't blocking UDP ports, check your firewall's setup instructions or the manufacturer's web site.
What you’re looking for • Like with the previous scans, you’re hoping that Sygate tells your firewall blocked all of its probes. • BUT, if Sygate tells your firewall isn't blocking UDP ports, check your firewall's setup instructions or the manufacturer's web site.
 Done? • Once you've run all the firewall tests at Sygate Online Services you're done, right? • Not exactly. • To be COMPLETELY sure your firewall is protecting your computer, you really need to test your firewall one more time using a different tool: Steve Gibson's “Shields Up. ”
Done? • Once you've run all the firewall tests at Sygate Online Services you're done, right? • Not exactly. • To be COMPLETELY sure your firewall is protecting your computer, you really need to test your firewall one more time using a different tool: Steve Gibson's “Shields Up. ”
 Shields Up! • grc. com or search for “Shields Up” • Click on the file sharing, common ports, all service ports, and messenger spam buttons to test those particular vulnerabilities.
Shields Up! • grc. com or search for “Shields Up” • Click on the file sharing, common ports, all service ports, and messenger spam buttons to test those particular vulnerabilities.
![DONE! • Once you've tested your firewall[s] with both Sygate Online services and Shields DONE! • Once you've tested your firewall[s] with both Sygate Online services and Shields](https://present5.com/presentation/55aead2abfb431f5e6b2aa094128efbe/image-34.jpg) DONE! • Once you've tested your firewall[s] with both Sygate Online services and Shields Up—and once you've received a clean bill of health from both—you can pretty much forget about your firewall[s]. • It's as squared away as it's going to get. • The next step is to double-check Windows Update / Apple Software Update.
DONE! • Once you've tested your firewall[s] with both Sygate Online services and Shields Up—and once you've received a clean bill of health from both—you can pretty much forget about your firewall[s]. • It's as squared away as it's going to get. • The next step is to double-check Windows Update / Apple Software Update.
 Part Two: Run Windows Update, Apple Software Update, and MBSA Close the known operating system vulnerabilities
Part Two: Run Windows Update, Apple Software Update, and MBSA Close the known operating system vulnerabilities
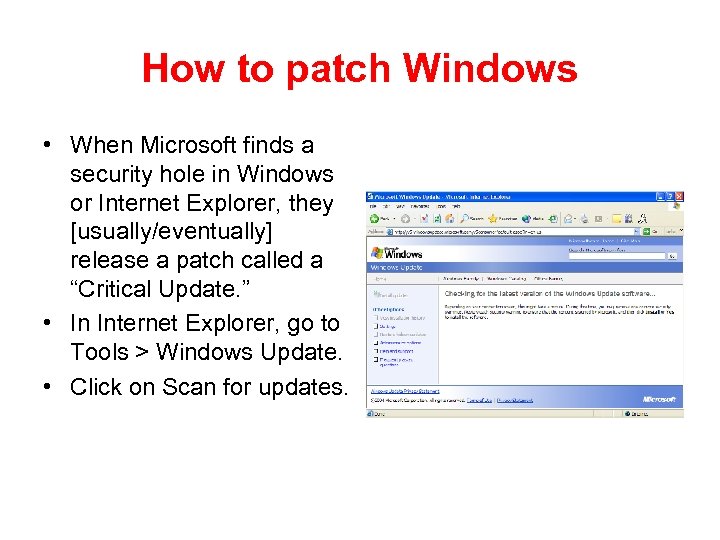 How to patch Windows • When Microsoft finds a security hole in Windows or Internet Explorer, they [usually/eventually] release a patch called a “Critical Update. ” • In Internet Explorer, go to Tools > Windows Update. • Click on Scan for updates.
How to patch Windows • When Microsoft finds a security hole in Windows or Internet Explorer, they [usually/eventually] release a patch called a “Critical Update. ” • In Internet Explorer, go to Tools > Windows Update. • Click on Scan for updates.
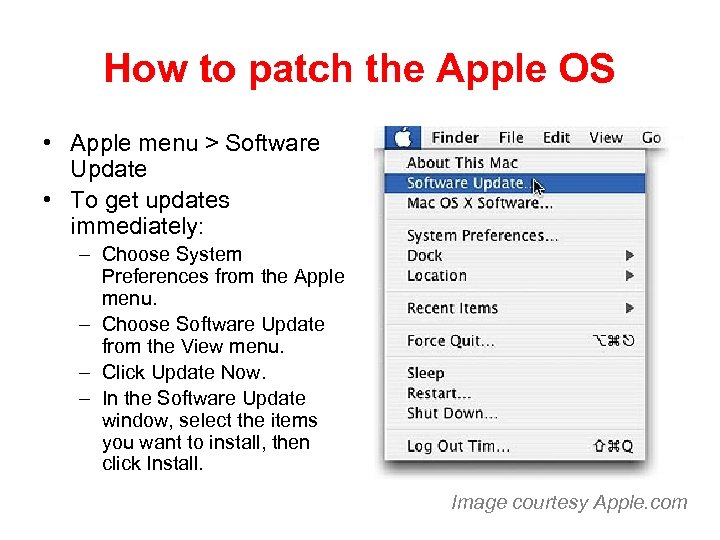 How to patch the Apple OS • Apple menu > Software Update • To get updates immediately: – Choose System Preferences from the Apple menu. – Choose Software Update from the View menu. – Click Update Now. – In the Software Update window, select the items you want to install, then click Install. Image courtesy Apple. com
How to patch the Apple OS • Apple menu > Software Update • To get updates immediately: – Choose System Preferences from the Apple menu. – Choose Software Update from the View menu. – Click Update Now. – In the Software Update window, select the items you want to install, then click Install. Image courtesy Apple. com
 Manually run Windows Update or Apple Software Update at least once a week. Your computer should, by default, automatically check for updates. That’s cool, but also run the update manually just to be safe.
Manually run Windows Update or Apple Software Update at least once a week. Your computer should, by default, automatically check for updates. That’s cool, but also run the update manually just to be safe.
 A dirty Microsoft secret • Windows Update lies. • It frequently thinks you’ve installed a critical update you haven’t, leaving your computer vulnerable. • That’s where Microsoft’s Baseline Security Analyzer [MBSA] comes in.
A dirty Microsoft secret • Windows Update lies. • It frequently thinks you’ve installed a critical update you haven’t, leaving your computer vulnerable. • That’s where Microsoft’s Baseline Security Analyzer [MBSA] comes in.
 MBSA 1. 2. 1 MBSA is a free program from Microsoft that scans for over 60 common system misconfigurations and almost any Microsoft security update your computer may be missing.
MBSA 1. 2. 1 MBSA is a free program from Microsoft that scans for over 60 common system misconfigurations and almost any Microsoft security update your computer may be missing.
 What MBSA does • MBSA double-checks the security of – – – Windows (*) Microsoft Office 2000 and later Internet Explorer 5. 01 and later Windows Media Player 6. 4 and later A bunch of other Microsoft applications and services • MBSA analyzes, you fix. – MBSA tells you what’s wrong and points you to the solution. – You have to apply the solution.
What MBSA does • MBSA double-checks the security of – – – Windows (*) Microsoft Office 2000 and later Internet Explorer 5. 01 and later Windows Media Player 6. 4 and later A bunch of other Microsoft applications and services • MBSA analyzes, you fix. – MBSA tells you what’s wrong and points you to the solution. – You have to apply the solution.
 Bad news/good news • (*) MBSA only works on Windows XP, 2000, and Server 2003. • It was designed for corporate tech support, but there is no reason why you can’t use it at home. • Oh, and it’s free. • To get the latest version of Microsoft’s MBSA, – Search for “microsoft mbsa” at Google. – The first hit—Microsoft Baseline Security Analyzer V 1. 2. 1—takes you to the download page.
Bad news/good news • (*) MBSA only works on Windows XP, 2000, and Server 2003. • It was designed for corporate tech support, but there is no reason why you can’t use it at home. • Oh, and it’s free. • To get the latest version of Microsoft’s MBSA, – Search for “microsoft mbsa” at Google. – The first hit—Microsoft Baseline Security Analyzer V 1. 2. 1—takes you to the download page.
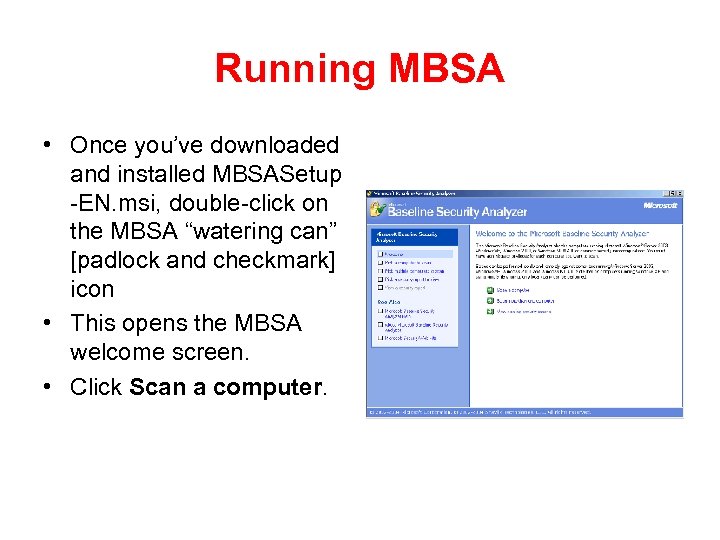 Running MBSA • Once you’ve downloaded and installed MBSASetup -EN. msi, double-click on the MBSA “watering can” [padlock and checkmark] icon • This opens the MBSA welcome screen. • Click Scan a computer.
Running MBSA • Once you’ve downloaded and installed MBSASetup -EN. msi, double-click on the MBSA “watering can” [padlock and checkmark] icon • This opens the MBSA welcome screen. • Click Scan a computer.
 Running MBSA • On the next screen, don’t change anything. • Make sure you are connected to the Internet and then click Start scan. • MBSA calls home to Microsoft and downloads something called “MSSecure. cab” – This file contains information about practically every patch Microsoft has released.
Running MBSA • On the next screen, don’t change anything. • Make sure you are connected to the Internet and then click Start scan. • MBSA calls home to Microsoft and downloads something called “MSSecure. cab” – This file contains information about practically every patch Microsoft has released.
 How MBSA really works • MBSA scans your computer’s operating system, operating system components, and Microsoft applications. • MBSA then compares the version numbers of the stuff on your computer with the latest version numbers in the MSSecure. cab file. • Finally, MBSA shows you which updates your computer is missing.
How MBSA really works • MBSA scans your computer’s operating system, operating system components, and Microsoft applications. • MBSA then compares the version numbers of the stuff on your computer with the latest version numbers in the MSSecure. cab file. • Finally, MBSA shows you which updates your computer is missing.
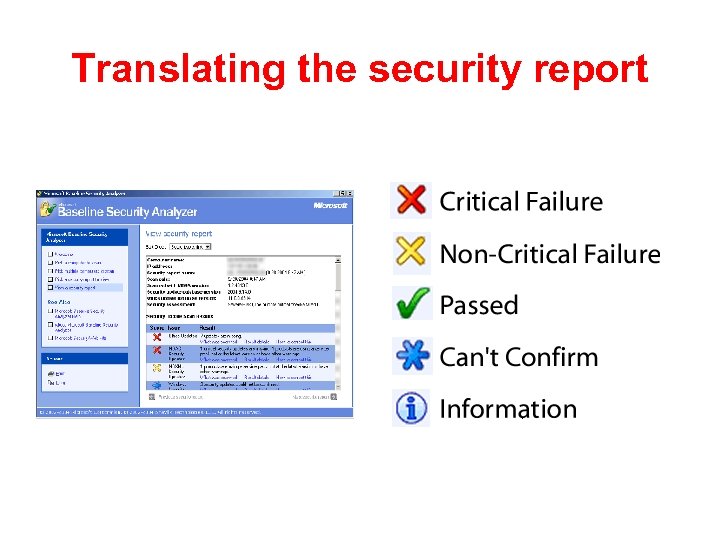 Translating the security report
Translating the security report
![Failures • Critical failures [red Xs] require you to immediately install a patch or Failures • Critical failures [red Xs] require you to immediately install a patch or](https://present5.com/presentation/55aead2abfb431f5e6b2aa094128efbe/image-47.jpg) Failures • Critical failures [red Xs] require you to immediately install a patch or update to ensure the strongest security of your computer. • Non-critical failures [yellow Xs] happen when there is a newer version of something available, but you don’t really have to upgrade…yet. • Best practices [blue asterisks] could signify a problem—MBSA can’t confirm that those particular security updates have been installed.
Failures • Critical failures [red Xs] require you to immediately install a patch or update to ensure the strongest security of your computer. • Non-critical failures [yellow Xs] happen when there is a newer version of something available, but you don’t really have to upgrade…yet. • Best practices [blue asterisks] could signify a problem—MBSA can’t confirm that those particular security updates have been installed.
 What’s important and what isn’t • MBSA’s security report has seven sections, and you only have to worry about two: – Security Update Scan Results [at the top of the report] – Desktop Application Scan Results [at the very bottom] • The five sections in the middle don’t really apply to home users. – Problems here are important but rarely critical. – You can fix the problems in the middle five sections if you want, but you don’t have to.
What’s important and what isn’t • MBSA’s security report has seven sections, and you only have to worry about two: – Security Update Scan Results [at the top of the report] – Desktop Application Scan Results [at the very bottom] • The five sections in the middle don’t really apply to home users. – Problems here are important but rarely critical. – You can fix the problems in the middle five sections if you want, but you don’t have to.
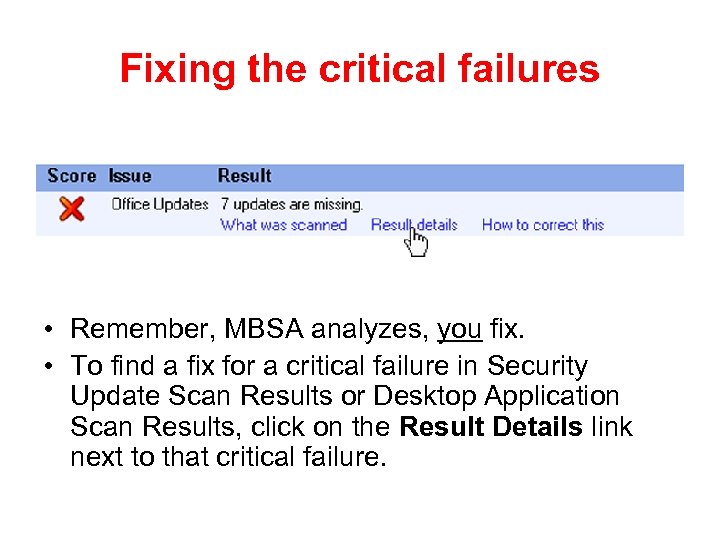 Fixing the critical failures • Remember, MBSA analyzes, you fix. • To find a fix for a critical failure in Security Update Scan Results or Desktop Application Scan Results, click on the Result Details link next to that critical failure.
Fixing the critical failures • Remember, MBSA analyzes, you fix. • To find a fix for a critical failure in Security Update Scan Results or Desktop Application Scan Results, click on the Result Details link next to that critical failure.
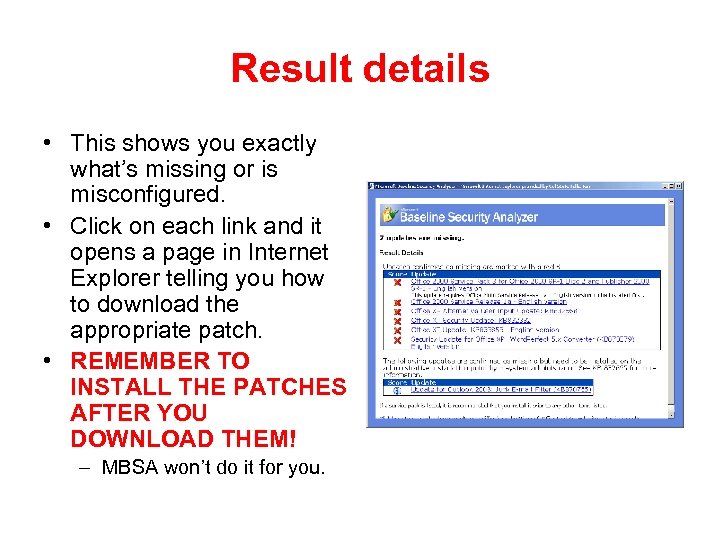 Result details • This shows you exactly what’s missing or is misconfigured. • Click on each link and it opens a page in Internet Explorer telling you how to download the appropriate patch. • REMEMBER TO INSTALL THE PATCHES AFTER YOU DOWNLOAD THEM! – MBSA won’t do it for you.
Result details • This shows you exactly what’s missing or is misconfigured. • Click on each link and it opens a page in Internet Explorer telling you how to download the appropriate patch. • REMEMBER TO INSTALL THE PATCHES AFTER YOU DOWNLOAD THEM! – MBSA won’t do it for you.
 “Attention K-Mart shoppers!” • Sometimes MBSA gets confused and can’t confirm if your computer has a particular patch. • That’s what the blue asterisks signify. • Fixing those blue asterisks is a little more complicated.
“Attention K-Mart shoppers!” • Sometimes MBSA gets confused and can’t confirm if your computer has a particular patch. • That’s what the blue asterisks signify. • Fixing those blue asterisks is a little more complicated.
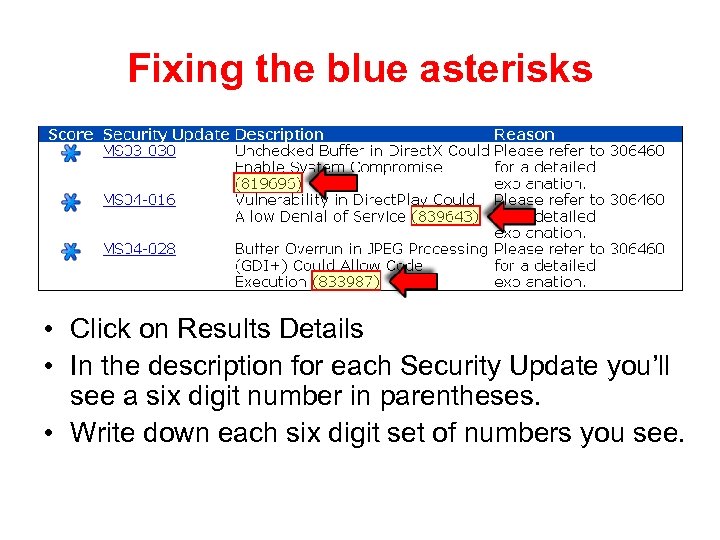 Fixing the blue asterisks • Click on Results Details • In the description for each Security Update you’ll see a six digit number in parentheses. • Write down each six digit set of numbers you see.
Fixing the blue asterisks • Click on Results Details • In the description for each Security Update you’ll see a six digit number in parentheses. • Write down each six digit set of numbers you see.
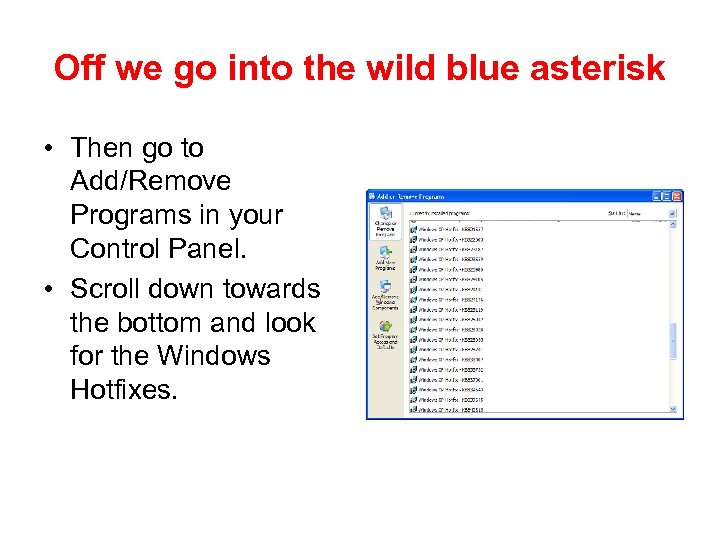 Off we go into the wild blue asterisk • Then go to Add/Remove Programs in your Control Panel. • Scroll down towards the bottom and look for the Windows Hotfixes.
Off we go into the wild blue asterisk • Then go to Add/Remove Programs in your Control Panel. • Scroll down towards the bottom and look for the Windows Hotfixes.
 Windows hotfixes • Compare those six digits you wrote down in MBSA with the last six digits of the various hotfixes in Add/Remove Programs. • If you find a match, you have the patch. MBSA just got confused. • If you don’t find a match, go back to the MBSA Results Details page and manually download and install the missing patches.
Windows hotfixes • Compare those six digits you wrote down in MBSA with the last six digits of the various hotfixes in Add/Remove Programs. • If you find a match, you have the patch. MBSA just got confused. • If you don’t find a match, go back to the MBSA Results Details page and manually download and install the missing patches.
 MBSA tips • Run MBSA from time to time just to doublecheck your computer’s security. • Don’t be surprised if MBSA still gives you blue asterisks even after you’ve installed all the patches. – Sometimes MBSA gets confused. – There’s no real way to unconfuse it. • There’s no such thing as a “clean” MBSA scan, especially in the middle five sections.
MBSA tips • Run MBSA from time to time just to doublecheck your computer’s security. • Don’t be surprised if MBSA still gives you blue asterisks even after you’ve installed all the patches. – Sometimes MBSA gets confused. – There’s no real way to unconfuse it. • There’s no such thing as a “clean” MBSA scan, especially in the middle five sections.
 To summarize • MBSA is a free program from Microsoft that scans for over 60 common system misconfigurations and almost any Microsoft security update your computer may be missing. • Fix the critical failures [red Xs] and the best practices [blue asterisks] as soon as possible. • Think about fixing the non-critical failures [yellow Xs] when you get the time. • MBSA’s security report has seven sections, and you only have to worry about two: – Security Update Scan Results [at the top of the report] – Desktop Application Scan Results [at the very bottom]
To summarize • MBSA is a free program from Microsoft that scans for over 60 common system misconfigurations and almost any Microsoft security update your computer may be missing. • Fix the critical failures [red Xs] and the best practices [blue asterisks] as soon as possible. • Think about fixing the non-critical failures [yellow Xs] when you get the time. • MBSA’s security report has seven sections, and you only have to worry about two: – Security Update Scan Results [at the top of the report] – Desktop Application Scan Results [at the very bottom]
 Part Three: Update your Antivirus You’d be shocked at how many people never do this.
Part Three: Update your Antivirus You’d be shocked at how many people never do this.
 True or False? If you have a hardware and software firewall that you’ve tested and you also have all of the necessary patches for your operating system, you don’t really need an antivirus program.
True or False? If you have a hardware and software firewall that you’ve tested and you also have all of the necessary patches for your operating system, you don’t really need an antivirus program.
 FALSE!
FALSE!
 The reality of the situation • According to Symantec, as of late September 2004 there were nearly 68, 152 PC viruses out there. • 10 to 15 new viruses are discovered each day. • Between 3, 650 and 5, 475 brand new viruses were discovered in just the past year alone. • The moment you connect your computer to the Internet your computer is immediately vulnerable to ALL of these viruses.
The reality of the situation • According to Symantec, as of late September 2004 there were nearly 68, 152 PC viruses out there. • 10 to 15 new viruses are discovered each day. • Between 3, 650 and 5, 475 brand new viruses were discovered in just the past year alone. • The moment you connect your computer to the Internet your computer is immediately vulnerable to ALL of these viruses.
 True or False? As long as you keep updating your antivirus definitions, the antivirus software that came with your computer should protect you.
True or False? As long as you keep updating your antivirus definitions, the antivirus software that came with your computer should protect you.
 FALSE!
FALSE!
 Now for the Bad News • Unless your computer is only a few months old, your antivirus software is outdated and may not be able to detect the newest, polymorphic viruses. • Your antivirus software has two distinct parts: – A computer program that scans your computer for viruses. – Antivirus definitions that tell that program exactly what to look for. • Updating your antivirus definitions—which you should do frequently—is not the same thing as updating your antivirus software.
Now for the Bad News • Unless your computer is only a few months old, your antivirus software is outdated and may not be able to detect the newest, polymorphic viruses. • Your antivirus software has two distinct parts: – A computer program that scans your computer for viruses. – Antivirus definitions that tell that program exactly what to look for. • Updating your antivirus definitions—which you should do frequently—is not the same thing as updating your antivirus software.
 Out with the old, in with the new. Just like you need to change the oil in your car every few months, you need to change your antivirus software every 12 to 18 months. – Completely uninstall the old version [like Norton Antivirus 2002. ] – Purchase and install the latest version [like Norton Antivirus 2005. ]
Out with the old, in with the new. Just like you need to change the oil in your car every few months, you need to change your antivirus software every 12 to 18 months. – Completely uninstall the old version [like Norton Antivirus 2002. ] – Purchase and install the latest version [like Norton Antivirus 2005. ]
 62% of broadband computer users do not have current antivirus software. Source AOL [as quoted by http: //tinyurl. com/5 kdh 9 ]
62% of broadband computer users do not have current antivirus software. Source AOL [as quoted by http: //tinyurl. com/5 kdh 9 ]
 The latest antivirus software • The top two consumer antivirus software programs are – Norton Antivirus 2005 [~US$50] – Mc. Afee Virus. Scan 2005 Version 9 [~US$50] • The best free antivirus program is AVG Anti-Virus Free Edition version 7 at http: //www. grisoft. com/
The latest antivirus software • The top two consumer antivirus software programs are – Norton Antivirus 2005 [~US$50] – Mc. Afee Virus. Scan 2005 Version 9 [~US$50] • The best free antivirus program is AVG Anti-Virus Free Edition version 7 at http: //www. grisoft. com/
 Update schedule • Completely replace your antivirus software every 12 to 18 months. • Update your antivirus definitions daily. – Most antivirus programs do this automatically. • Manually update your antivirus definitions weekly. – Automatic updates are cool, but run an update by hand each week just to be safe.
Update schedule • Completely replace your antivirus software every 12 to 18 months. • Update your antivirus definitions daily. – Most antivirus programs do this automatically. • Manually update your antivirus definitions weekly. – Automatic updates are cool, but run an update by hand each week just to be safe.
 If your antivirus program doesn’t have the latest virus definitions, your computer isn’t protected against ANY of the new viruses!
If your antivirus program doesn’t have the latest virus definitions, your computer isn’t protected against ANY of the new viruses!
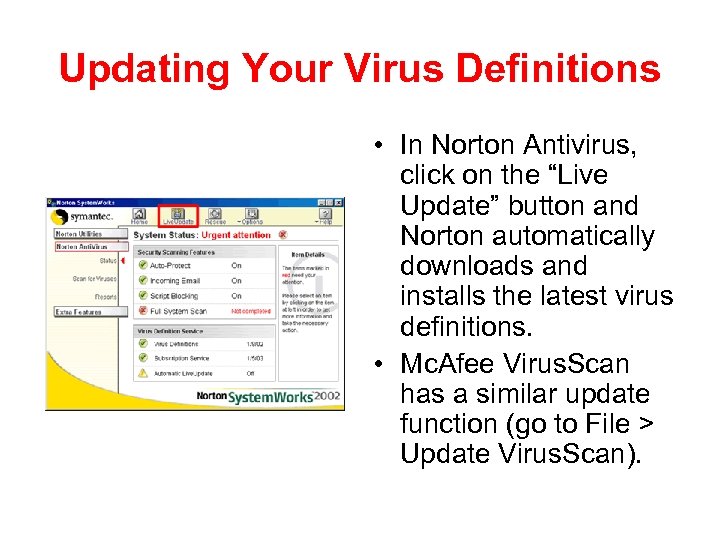 Updating Your Virus Definitions • In Norton Antivirus, click on the “Live Update” button and Norton automatically downloads and installs the latest virus definitions. • Mc. Afee Virus. Scan has a similar update function (go to File > Update Virus. Scan).
Updating Your Virus Definitions • In Norton Antivirus, click on the “Live Update” button and Norton automatically downloads and installs the latest virus definitions. • Mc. Afee Virus. Scan has a similar update function (go to File > Update Virus. Scan).
 Updating Other AV Programs • If you are unsure how to update your virus definitions, visit the Web site of your antivirus software manufacturer and look for their “download, ” “update, ” or “technical support” section. • If you are on AOL, you can find the latest virus definitions for most antivirus programs at keyword: virus.
Updating Other AV Programs • If you are unsure how to update your virus definitions, visit the Web site of your antivirus software manufacturer and look for their “download, ” “update, ” or “technical support” section. • If you are on AOL, you can find the latest virus definitions for most antivirus programs at keyword: virus.
 What About Macs? • The possibility of new Mac viruses, while slight, is still greater than zero. • The possibility of future, cross-platform viruses (viruses that infect both PCs and Macs) is also quite real. • So, yes, Mac users also need antivirus software. • And keep it updated. Image courtesy http: //www. apple. com/
What About Macs? • The possibility of new Mac viruses, while slight, is still greater than zero. • The possibility of future, cross-platform viruses (viruses that infect both PCs and Macs) is also quite real. • So, yes, Mac users also need antivirus software. • And keep it updated. Image courtesy http: //www. apple. com/
 Part Four: Detect, Delete, and Block Spyware and Malware Give spyware and malware the boot.
Part Four: Detect, Delete, and Block Spyware and Malware Give spyware and malware the boot.
 Adware • Adware is software that displays advertisements when a particular program is running. • A good example is the Eudora email client. – You can buy it for ~US$50. – You can also get the exact same program for free, but the free version displays an ad window and up to 3 sponsored toolbar links.
Adware • Adware is software that displays advertisements when a particular program is running. • A good example is the Eudora email client. – You can buy it for ~US$50. – You can also get the exact same program for free, but the free version displays an ad window and up to 3 sponsored toolbar links.
 Adware: Good. • Pure adware is a good thing. – You get software that you otherwise wouldn’t be able to afford. – In return, the software displays some ads. • Unfortunately, pure adware is also rare.
Adware: Good. • Pure adware is a good thing. – You get software that you otherwise wouldn’t be able to afford. – In return, the software displays some ads. • Unfortunately, pure adware is also rare.
 Spyware: Bad. • Spyware is software that tracks what you do and where you go online. • Pure spyware like the Google toolbar respects your privacy and doesn’t share this tracking information with anyone else. • Unfortunately, – Pure spyware is the exception, not the rule. – An overwhelming majority of spyware [like 99. 99%] sells your personal information to marketing companies.
Spyware: Bad. • Spyware is software that tracks what you do and where you go online. • Pure spyware like the Google toolbar respects your privacy and doesn’t share this tracking information with anyone else. • Unfortunately, – Pure spyware is the exception, not the rule. – An overwhelming majority of spyware [like 99. 99%] sells your personal information to marketing companies.
 Why is spyware so bad? • Besides the privacy implications, spyware can often break your computer. – Spyware code is often poorly-written. – You may have so many spyware programs running at once that your computer slows to a crawl or crashes. • Spyware has been linked to an increase in both spam and pop-ups. • Pornographers use spyware to push explicit advertisements to your computer. – “Will some please think about the children? ”
Why is spyware so bad? • Besides the privacy implications, spyware can often break your computer. – Spyware code is often poorly-written. – You may have so many spyware programs running at once that your computer slows to a crawl or crashes. • Spyware has been linked to an increase in both spam and pop-ups. • Pornographers use spyware to push explicit advertisements to your computer. – “Will some please think about the children? ”
 How pervasive is spyware? • Over 90% of broadband users have spyware installed on their systems. Source AOL [as quoted by http: //tinyurl. com/5 kdh 9 ] • Pest. Patrol has identified 124, 474 different spyware programs or objects on the loose as of late September 2004.
How pervasive is spyware? • Over 90% of broadband users have spyware installed on their systems. Source AOL [as quoted by http: //tinyurl. com/5 kdh 9 ] • Pest. Patrol has identified 124, 474 different spyware programs or objects on the loose as of late September 2004.
 Where does spyware come from? • Some spyware piggybacks on top of free software you download and install from the Internet. • Software that comes bundled with spyware include: – File-sharing programs like Grokster and Kazaa – Di. Vx – Weatherbug
Where does spyware come from? • Some spyware piggybacks on top of free software you download and install from the Internet. • Software that comes bundled with spyware include: – File-sharing programs like Grokster and Kazaa – Di. Vx – Weatherbug
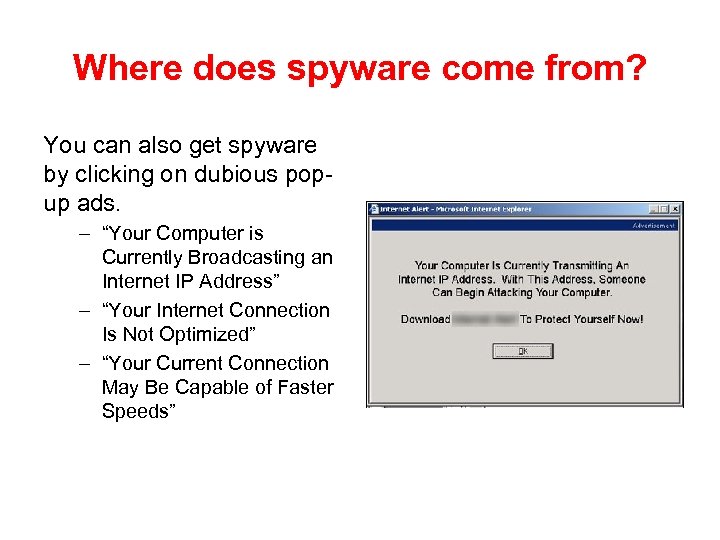 Where does spyware come from? You can also get spyware by clicking on dubious popup ads. – “Your Computer is Currently Broadcasting an Internet IP Address” – “Your Internet Connection Is Not Optimized” – “Your Current Connection May Be Capable of Faster Speeds”
Where does spyware come from? You can also get spyware by clicking on dubious popup ads. – “Your Computer is Currently Broadcasting an Internet IP Address” – “Your Internet Connection Is Not Optimized” – “Your Current Connection May Be Capable of Faster Speeds”
 Where does spyware come from? • Another way to get spyware is from a virus or Trojan Horse, but that’s rare. • And if you use Internet Explorer, you can even get spyware just by visiting a particular website. – You don’t have to click or download anything. – Internet Explorer automatically installs the spyware for you. [“Thank you, Microsoft!”] – You can download the fix at mozilla. org. • MANY of these drive-by installations involve not only spyware but malware.
Where does spyware come from? • Another way to get spyware is from a virus or Trojan Horse, but that’s rare. • And if you use Internet Explorer, you can even get spyware just by visiting a particular website. – You don’t have to click or download anything. – Internet Explorer automatically installs the spyware for you. [“Thank you, Microsoft!”] – You can download the fix at mozilla. org. • MANY of these drive-by installations involve not only spyware but malware.
 Malware: Very bad! Malware can – Replace legitimate ads on commercial web sites with ads from vendors who financially support the malware’s author [a. k. a. , “scumware. ”] – Permanently and irreparably change your browser’s home page and search settings so that they point to the malware author’s site [a. k. a. , “homepage hijackers. ”] • The site is usually overflowing with advertising and pop-ups. • Fixing homepage hijackers is often quite difficult. Source: http: //www. doxdesk. com/parasite/
Malware: Very bad! Malware can – Replace legitimate ads on commercial web sites with ads from vendors who financially support the malware’s author [a. k. a. , “scumware. ”] – Permanently and irreparably change your browser’s home page and search settings so that they point to the malware author’s site [a. k. a. , “homepage hijackers. ”] • The site is usually overflowing with advertising and pop-ups. • Fixing homepage hijackers is often quite difficult. Source: http: //www. doxdesk. com/parasite/
 Malware: Very bad! Malware can – Cause your modem to automatically dial 900, long-distance, or international telephone numbers whose revenues support the malware’s author [a. k. a. , “autodialers. ”] – Open security holes on your computer that can be used later to remotely take control of your computer [a. k. a. , “Trojan horses. ”] Source: http: //www. doxdesk. com/parasite/
Malware: Very bad! Malware can – Cause your modem to automatically dial 900, long-distance, or international telephone numbers whose revenues support the malware’s author [a. k. a. , “autodialers. ”] – Open security holes on your computer that can be used later to remotely take control of your computer [a. k. a. , “Trojan horses. ”] Source: http: //www. doxdesk. com/parasite/
 Malware: Very bad! Malware can – Degrade your computer’s performance and cause errors thanks to it being badly-written [a. k. a. , “Microsoft Windows”] – Provide no uninstall feature and put its code in unexpected and hidden places to make it difficult to remove [ibid] Source: http: //www. doxdesk. com/parasite/
Malware: Very bad! Malware can – Degrade your computer’s performance and cause errors thanks to it being badly-written [a. k. a. , “Microsoft Windows”] – Provide no uninstall feature and put its code in unexpected and hidden places to make it difficult to remove [ibid] Source: http: //www. doxdesk. com/parasite/
 Bye-bye, IE! • All kidding aside, it’s time to stop using IE. – IE has way too many security holes. – There hasn’t been a major IE upgrade in over three years. – Microsoft only supports IE on XP. There will be no more free IE security updates for non-XP users. • Keep IE around so that you can access the sites that require it—Windows Update, Expedia, MSN, Shutterfly, etc. • Use an alternative browser [like Mozilla Firefox, Opera, or Safari] to access everything else!
Bye-bye, IE! • All kidding aside, it’s time to stop using IE. – IE has way too many security holes. – There hasn’t been a major IE upgrade in over three years. – Microsoft only supports IE on XP. There will be no more free IE security updates for non-XP users. • Keep IE around so that you can access the sites that require it—Windows Update, Expedia, MSN, Shutterfly, etc. • Use an alternative browser [like Mozilla Firefox, Opera, or Safari] to access everything else!
 Detect and delete • To detect and delete both spyware and malware, download and install both – Ad-Aware Personal SE at http: //www. lavasoftusa. com/ – Spybot Search & Destroy 1. 3 at http: //www. safer-networking. org/ • Why both? – Ad-Aware catches stuff that Spybot misses, and viceversa. – They’re both free.
Detect and delete • To detect and delete both spyware and malware, download and install both – Ad-Aware Personal SE at http: //www. lavasoftusa. com/ – Spybot Search & Destroy 1. 3 at http: //www. safer-networking. org/ • Why both? – Ad-Aware catches stuff that Spybot misses, and viceversa. – They’re both free.
 Other spyware removal tools • But what about [insert your favorite spyware removal tool’s name here]? • There are some great spyware removal tools out there—some free, some not—but Ad-Aware and Spybot are the market leaders. – Ad-Aware has been downloaded 73 million times and Spybot 34 million times. – AND BOTH ARE FREE!
Other spyware removal tools • But what about [insert your favorite spyware removal tool’s name here]? • There are some great spyware removal tools out there—some free, some not—but Ad-Aware and Spybot are the market leaders. – Ad-Aware has been downloaded 73 million times and Spybot 34 million times. – AND BOTH ARE FREE!
 Definitions • Both Ad-Aware and Spybot are similar to your antivirus program in that they both use definition files to know what to look for. • Always update the definitions before you scan your computer. – In Ad-Aware, click on Check for updates now. – In Spybot, click on Search for Updates.
Definitions • Both Ad-Aware and Spybot are similar to your antivirus program in that they both use definition files to know what to look for. • Always update the definitions before you scan your computer. – In Ad-Aware, click on Check for updates now. – In Spybot, click on Search for Updates.
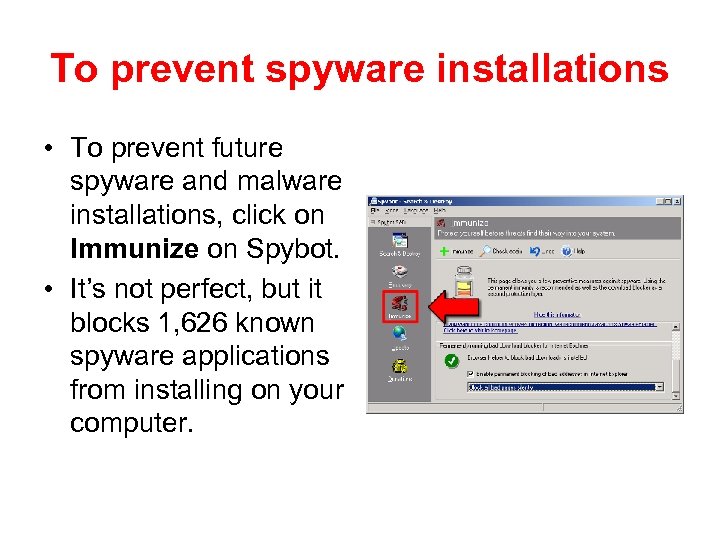 To prevent spyware installations • To prevent future spyware and malware installations, click on Immunize on Spybot. • It’s not perfect, but it blocks 1, 626 known spyware applications from installing on your computer.
To prevent spyware installations • To prevent future spyware and malware installations, click on Immunize on Spybot. • It’s not perfect, but it blocks 1, 626 known spyware applications from installing on your computer.
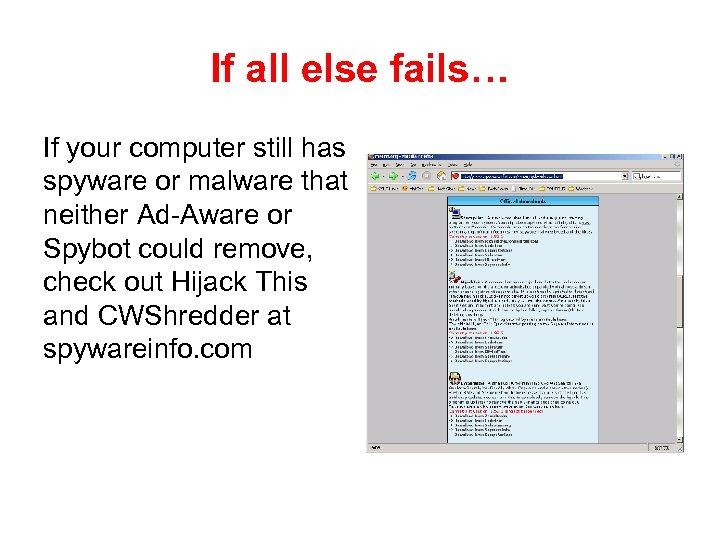 If all else fails… If your computer still has spyware or malware that neither Ad-Aware or Spybot could remove, check out Hijack This and CWShredder at spywareinfo. com
If all else fails… If your computer still has spyware or malware that neither Ad-Aware or Spybot could remove, check out Hijack This and CWShredder at spywareinfo. com
 Dealing with spyware/malware • To get rid of spyware and malware, run Ad -Aware and Spybot weekly. • To prevent future spyware and malware installations, – Don’t download and install any free software without first verifying that it is free of spyware. [Search Google for the name of the software +spyware] – Enable the Immunize feature in Spybot.
Dealing with spyware/malware • To get rid of spyware and malware, run Ad -Aware and Spybot weekly. • To prevent future spyware and malware installations, – Don’t download and install any free software without first verifying that it is free of spyware. [Search Google for the name of the software +spyware] – Enable the Immunize feature in Spybot.
 That’s it for today!
That’s it for today!
 Home Computer Security and Privacy: Verification and Prevention a presentation by Patrick Douglas Crispen Faculty Development Center California State University, Fullerton
Home Computer Security and Privacy: Verification and Prevention a presentation by Patrick Douglas Crispen Faculty Development Center California State University, Fullerton


