68bee3651d813ec6c206a708fc9f54dd.ppt
- Количество слайдов: 25
 Here Come the Internet Cops TJ Mc. Intyre University College Dublin Digital Rights Ireland Merrion Legal Solicitors tjmcintyre@ucd. ie
Here Come the Internet Cops TJ Mc. Intyre University College Dublin Digital Rights Ireland Merrion Legal Solicitors tjmcintyre@ucd. ie
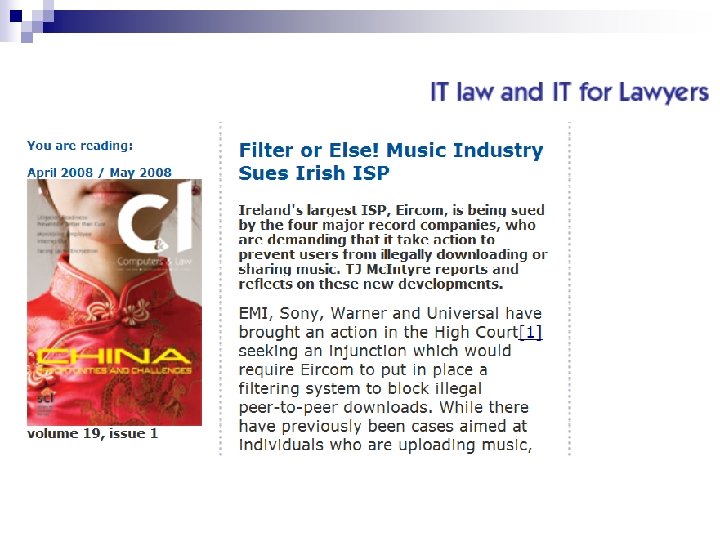
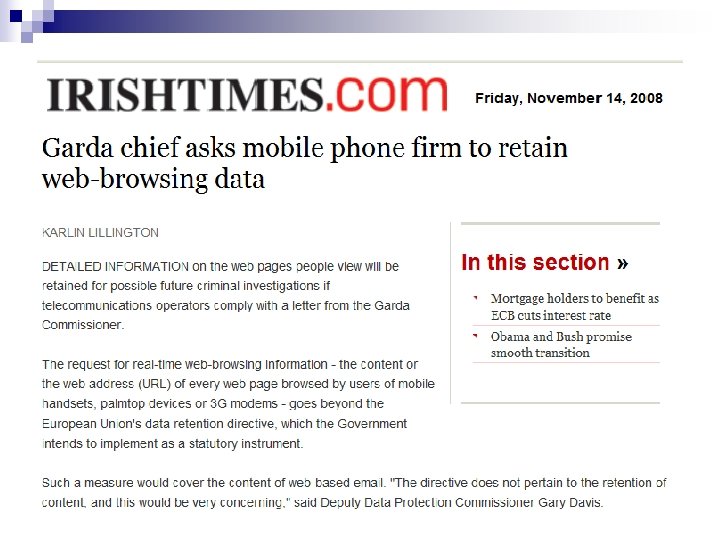
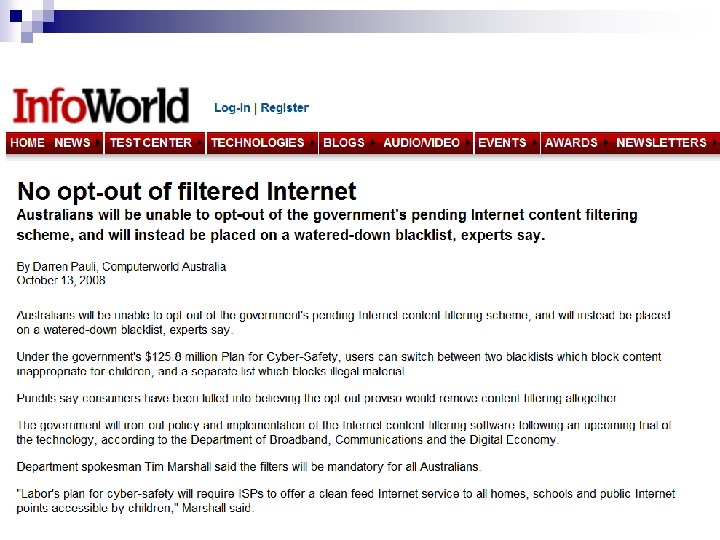
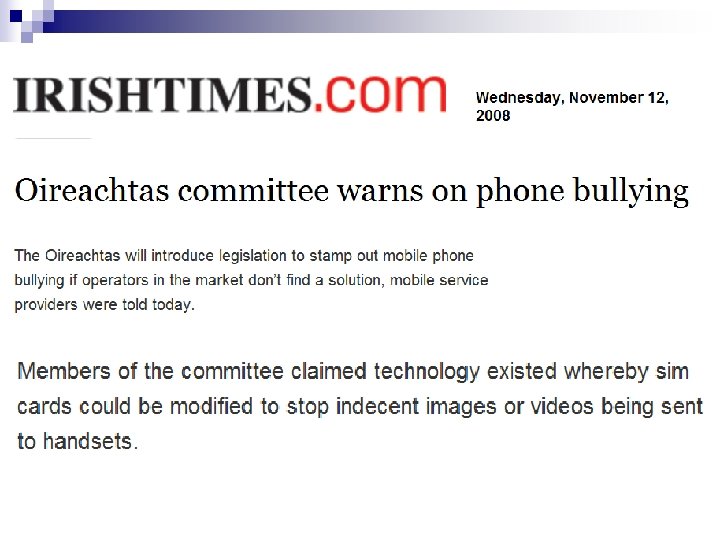
 “Three strikes…”
“Three strikes…”
 The cyber-libertarian utopia n Disintermediation ¨ Everyone a publisher ¨ Editors, producers, financial removed n barriers to entry… all Structural resistance to control ¨ Internet does not respect borders ¨ Encourages regulatory arbitrage ¨ No central points of control ¨ “The internet interprets censorship filters around it” as damage and
The cyber-libertarian utopia n Disintermediation ¨ Everyone a publisher ¨ Editors, producers, financial removed n barriers to entry… all Structural resistance to control ¨ Internet does not respect borders ¨ Encourages regulatory arbitrage ¨ No central points of control ¨ “The internet interprets censorship filters around it” as damage and
 …and the response of cyberpaternalism n Re-intermediation ¨ Internet use results in new intermediaries ¨ Often exempt from existing laws ¨ Giving the possibility of finer grained controls ¨ Regulators will shift their focus to “elephants” rather than “mice” ¨ Why target the user when you can target the host, ISP or software author?
…and the response of cyberpaternalism n Re-intermediation ¨ Internet use results in new intermediaries ¨ Often exempt from existing laws ¨ Giving the possibility of finer grained controls ¨ Regulators will shift their focus to “elephants” rather than “mice” ¨ Why target the user when you can target the host, ISP or software author?
 Cyber-paternalism ctd. n Remaking internet architecture ¨ Code as a means of regulation and surveillance ¨ Anonymous speech, decentralised distribution, encryption, virtual geography are contingent features only ¨ “Spam, security and spondoolicks” threaten the end to end architecture of the internet n n n Sender authentication Application signing Content geolocation
Cyber-paternalism ctd. n Remaking internet architecture ¨ Code as a means of regulation and surveillance ¨ Anonymous speech, decentralised distribution, encryption, virtual geography are contingent features only ¨ “Spam, security and spondoolicks” threaten the end to end architecture of the internet n n n Sender authentication Application signing Content geolocation
 Implications? n Advantages? ¨ Effectiveness ¨ Cost-effectiveness (for governments, at least) ¨ “Light touch” self regulation n Possible disadvantages? ¨ What effect does regulation by architecture and intermediary have on constitutional norms?
Implications? n Advantages? ¨ Effectiveness ¨ Cost-effectiveness (for governments, at least) ¨ “Light touch” self regulation n Possible disadvantages? ¨ What effect does regulation by architecture and intermediary have on constitutional norms?
 Transparency
Transparency
 Transparency n How are controls introduced? Primary legislation? ¨ Litigation? (e. g. Sony v. Eircom) ¨ Agreement between state and intermediaries? (“Three strikes”) ¨ n n Who is a party to the negotiations? Is the agreement public? Secret government action (data retention) ¨ Are restrictions “prescribed by law” as required by ECHR? ¨ n n Do e. g. users know that ISPs filter URLs, or search engines filter results? Does e. g. a filtering system deceive users as to why a page is inaccessible?
Transparency n How are controls introduced? Primary legislation? ¨ Litigation? (e. g. Sony v. Eircom) ¨ Agreement between state and intermediaries? (“Three strikes”) ¨ n n Who is a party to the negotiations? Is the agreement public? Secret government action (data retention) ¨ Are restrictions “prescribed by law” as required by ECHR? ¨ n n Do e. g. users know that ISPs filter URLs, or search engines filter results? Does e. g. a filtering system deceive users as to why a page is inaccessible?
 Are public law norms evaded? n James Boyle’s prediction: ¨ “Intrusions into privacy, automatic scrutiny of email, curtailing of fair use rights … all of these would occur in the private realm, far from the scrutiny of public law”.
Are public law norms evaded? n James Boyle’s prediction: ¨ “Intrusions into privacy, automatic scrutiny of email, curtailing of fair use rights … all of these would occur in the private realm, far from the scrutiny of public law”.
 Fair procedures Is there a right to be notified / to make submissions before e. g. a site is blacklisted? n Do these systems provide for a “separation of powers”? n Is there an (independent) appeal mechanism? n
Fair procedures Is there a right to be notified / to make submissions before e. g. a site is blacklisted? n Do these systems provide for a “separation of powers”? n Is there an (independent) appeal mechanism? n
 Incentives and Intermediaries Commercial realities - Block / takedown first, ask questions later or not at all? n US v. EU (E-Commerce Directive) protections – how have intermediary incentives affected speech? n Effect on proportionality? n
Incentives and Intermediaries Commercial realities - Block / takedown first, ask questions later or not at all? n US v. EU (E-Commerce Directive) protections – how have intermediary incentives affected speech? n Effect on proportionality? n
 Proportionality n Filtering and collateral damage ¨ DNS blacklisting – e. g. Finland Pennsylvania ¨ Blocks all sites hosted on a particular server – not merely Pirates’r’us. com but also Innocent. Bystanders. com n n More granular filtering will struggle with borderline cases – e. g. fair use By outsourcing costs, will states be tempted to engage in over-blocking?
Proportionality n Filtering and collateral damage ¨ DNS blacklisting – e. g. Finland Pennsylvania ¨ Blocks all sites hosted on a particular server – not merely Pirates’r’us. com but also Innocent. Bystanders. com n n More granular filtering will struggle with borderline cases – e. g. fair use By outsourcing costs, will states be tempted to engage in over-blocking?
 The UK Experience: “Cleanfeed” n The Internet Watch Foundation ¨ Established 1996 Agreement between Government, Police and ISPs n ISP liability for illegal material then unclear n Met. Police threatened to prosecute ISPs unless they blocked certain newsgroups and established take down procedures n
The UK Experience: “Cleanfeed” n The Internet Watch Foundation ¨ Established 1996 Agreement between Government, Police and ISPs n ISP liability for illegal material then unclear n Met. Police threatened to prosecute ISPs unless they blocked certain newsgroups and established take down procedures n
 Status of IWF Private, charitable body n No state representation on board n Works closely with Police, Government n Funded by EU and Internet Industry n Designated as a “relevant authority” under UK legislation for immunity purposes n
Status of IWF Private, charitable body n No state representation on board n Works closely with Police, Government n Funded by EU and Internet Industry n Designated as a “relevant authority” under UK legislation for immunity purposes n
 The IWF Blacklist n Child sexual images and content URL list ¨ Initially maintained and used internally only ¨ Based on public complaints ¨ Classified in-house ¨ No prior notification to blocked sites ¨ Internal complaints mechanism for wrongful inclusion ¨ Appeal lies to Met. Police
The IWF Blacklist n Child sexual images and content URL list ¨ Initially maintained and used internally only ¨ Based on public complaints ¨ Classified in-house ¨ No prior notification to blocked sites ¨ Internal complaints mechanism for wrongful inclusion ¨ Appeal lies to Met. Police
 Takeup by ISPs n 2004 – list made available to IWF members ¨ n n Following Home Office pressure BT take lead in developing blocking system (internally – “Cleanfeed”); agree to make it available to others Voluntary takeup by other ISPs during 2006 / 2007 Government indicated plans to legislate unless 100% of ISPs implemented a content blocking system by end 2007 95% of broadband providers now appear to “voluntarily” filter against the IWF list
Takeup by ISPs n 2004 – list made available to IWF members ¨ n n Following Home Office pressure BT take lead in developing blocking system (internally – “Cleanfeed”); agree to make it available to others Voluntary takeup by other ISPs during 2006 / 2007 Government indicated plans to legislate unless 100% of ISPs implemented a content blocking system by end 2007 95% of broadband providers now appear to “voluntarily” filter against the IWF list
 Lessons from “Cleanfeed”? n Transparency and legitimacy ¨ No formal legal basis ¨ May clash with E-Commerce Directive guarantees n Is this a general duty to monitor? ¨ Difficult to assess the effectiveness of a system divided between various private actors n ¨ No E. g. BT – 230, 000 attempts to access child pornography over three weeks? indication to owners or users that a site has been blocked:
Lessons from “Cleanfeed”? n Transparency and legitimacy ¨ No formal legal basis ¨ May clash with E-Commerce Directive guarantees n Is this a general duty to monitor? ¨ Difficult to assess the effectiveness of a system divided between various private actors n ¨ No E. g. BT – 230, 000 attempts to access child pornography over three weeks? indication to owners or users that a site has been blocked:
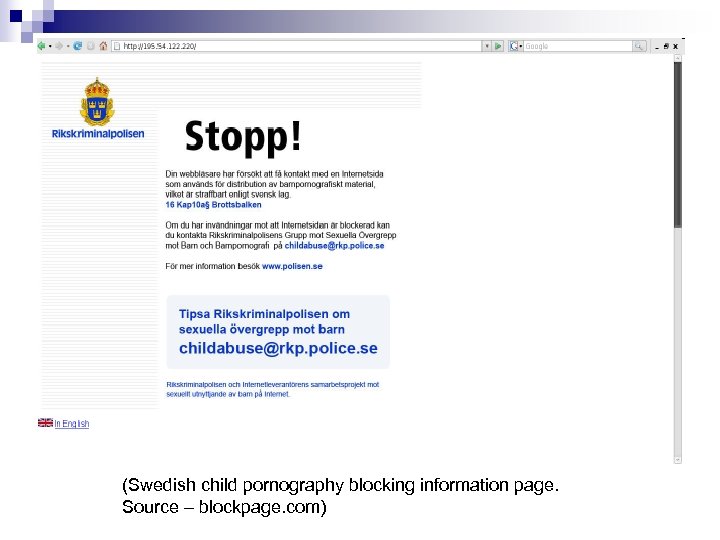 (Swedish child pornography blocking information page. Source – blockpage. com)
(Swedish child pornography blocking information page. Source – blockpage. com)
 Other public law norms? n Proportionality? Be Unlimited – IP blocking & collateral damage ¨ System blocks only a very limited subset of internet traffic – IRC, filesharing, Usenet, etc. are left untouched. ¨ TOR / other proxies defeat it entirely ¨ n Accountability ¨ ¨ ¨ No prior notification Limited ability to challenge decisions No independent appeal mechanism as required by Art. 6 ECHR Amenable to judicial review? Outside the scope of e. g. Freedom of Information Act 2000
Other public law norms? n Proportionality? Be Unlimited – IP blocking & collateral damage ¨ System blocks only a very limited subset of internet traffic – IRC, filesharing, Usenet, etc. are left untouched. ¨ TOR / other proxies defeat it entirely ¨ n Accountability ¨ ¨ ¨ No prior notification Limited ability to challenge decisions No independent appeal mechanism as required by Art. 6 ECHR Amenable to judicial review? Outside the scope of e. g. Freedom of Information Act 2000
 Function creep? n n n Reuters 10/11/2007 – “Web search for bomb recipes should be blocked: EU” The Guardian 17/1/2008 – “Government targets extremist websites” Byron Review 3/2008 ¨ Extreme pornography and racial hatred; Blocking of non-illegal material to be kept under review n n The Telegraph 1/8/2008 – “Ministers seek curbs on internet suicide sites” Pro-anorexia sites, etc. ?
Function creep? n n n Reuters 10/11/2007 – “Web search for bomb recipes should be blocked: EU” The Guardian 17/1/2008 – “Government targets extremist websites” Byron Review 3/2008 ¨ Extreme pornography and racial hatred; Blocking of non-illegal material to be kept under review n n The Telegraph 1/8/2008 – “Ministers seek curbs on internet suicide sites” Pro-anorexia sites, etc. ?
 Thank you tjmcintyre@ucd. ie
Thank you tjmcintyre@ucd. ie


