c201036ac660e24cf9e256b3c4b512c5.ppt
- Количество слайдов: 66

Health Insurance Portability & Accountability Act (HIPAA) April 2005 1

Overview of Privacy & the new Security Standards 2

Agenda • • • Review HIPAA Privacy Standards Introduce HIPAA Security Standards What the Security Standards require What it means to the way you work Examples of how things will be different 3

Legislation Federal Law: HIPAA Privacy & Security Standards mandate protection and safeguards for access, use and disclosure of PHI and/or e. PHI with sanctions for violations. 4

Pertinent Law • Security Breach Notification (SB 1386): requirement to notify California residents if their electronically held personal information may have been acquired by an unauthorized person 5
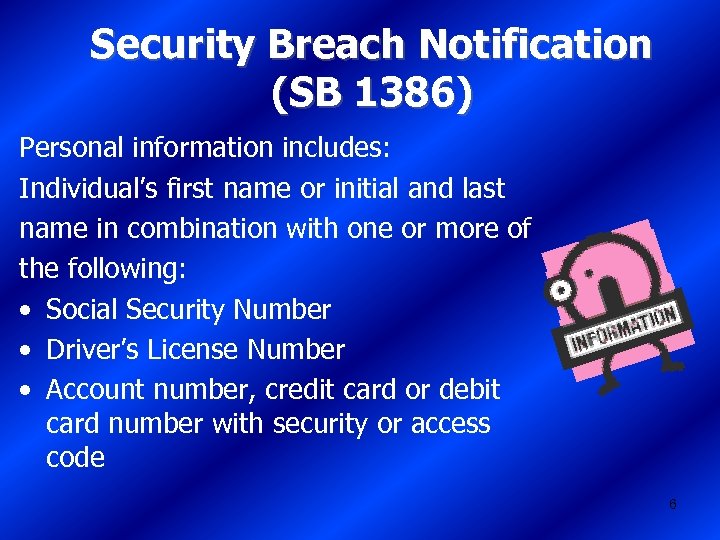
Security Breach Notification (SB 1386) Personal information includes: Individual’s first name or initial and last name in combination with one or more of the following: • Social Security Number • Driver’s License Number • Account number, credit card or debit card number with security or access code 6

What is HIPAA? HIPAA is a federal law enacted to: • Ensure the privacy of an individual’s protected health information (PHI) • Provide security for electronic and physical exchange of PHI • Provide for individual rights regarding PHI. 7

HIPAA is Federal Law that requires HIPAA-Covered Entities to: Protect the privacy and security of an individual’s Protected Health Information (PHI): • health information created, stored or maintained by a health care provider, health plan, health care clearinghouse; and • relates to the past, present or future physical or mental health or condition of the individual, the provision of health care to the individual or the payment for the provisions of health care; and • identifies the individual. 8

Personal Identifiers under HIPAA include: • Name, all types of addresses including email, URL, home • Identifying numbers, including Social Security, medical records, insurance numbers, account numbers • Full facial photos • Dates, including birth date, dates of admission and discharge, or death Personal identifiers coupled with a broad range of health, health care or health care 9 payment information creates PHI

Why it affects your work at UC • UC health plans are Covered Entities; • UC, on behalf of employees, may use or access PHI; • As an employee, you need to understand how HIPAA and other laws allow you to use, access, or disclose a member’s health information. 10

Who or what are HIPAA “Covered Entities”? HIPAA's regulations directly cover three basic groups of individual or corporate entities: health care providers, health plans, and health care clearinghouses. • Health Care Provider means a provider of medical or health services, and entities who furnishes, bills, or is paid for health care in the normal course of business • Health Plan means any individual or group that provides or pays for the cost of medical care, including employee benefit plans • Healthcare Clearinghouse means an entity that either processes or facilitates the processing of health 11 information, e. g. , billing service, print vendors

UC as a “Covered Entity? ” UC’s Group Health Plans Self-Funded plans – UC is the covered entity – Subject to all HIPAA Rules Insured Plans – UC is not the covered entity – When participating in the administration of the plan (e. g. , assisting employees with health claim issues, fielding healthcare complaints, and assisting with claim payment resolution) but, UC has certain obligations under HIPAA To be safe & for consistency, treat individuallyidentifiable health information as PHI 12

UC has various roles • PLAN ADMINSTRATOR/PLAN SPONSOR ROLE Some 'covered' activities under HIPAA are: – handling of a member complaint – resolving a claim payment with a carrier – assisting a member with a health claim issue • EMPLOYER ROLE Some 'non-covered' activities not subject to HIPAA are: - facilitating enrollment into the health plans - verifying eligibility - when a staff member reports an absence - performing Family Medical Leave Act (FMLA) functions 13

HIPAA is on you! 14

Understand your individual responsibility • Always maintain a separation between your covered and non-covered activities and know what additional state or federal laws apply to the privacy of an individual’s health information • Never disclose PHI to other non-covered entities (UC or third parties) without Authorization or unless required or permitted by law • Always apply the Minimum Necessary Standard to uses and disclosures of PHI • 90/10 Rule 15

Minimum Necessary Standard • Use or disclose only the minimum PHI that you need to know to do your job • A Covered Entity should have in place procedures that limit access according to job class • Limit access, use or disclosure of PHI by others to the minimum amount necessary to accomplish the intended purpose • “Think Twice” Rule: – Is it reasonable? – Is it necessary? 16

HIPAA Security Standards • The Security Standards require information security, confidentiality, integrity, and availability of electronic Protected Health Information (e. PHI) 17

What are the Security Rule General Requirements? Compliance required by April 20, 2005 • Ensure the confidentiality, integrity and availability of all electronic protected health information (e. PHI) that the covered entity creates, receives, maintains, or transmits. • Protect against reasonably anticipated threats or hazards to the security or integrity of e. PHI, e. g. , hackers, viruses, data back-ups • Protect against unauthorized disclosures • Train workforce members (“awareness of good 18 computing practices”)

What this means • “Information Security” means to ensure the confidentiality, integrity, and availability of information through safeguards. • “Confidentiality” – that information will not be disclosed to unauthorized individuals or processes • “Integrity” – the condition of data or information that has not been altered or destroyed in an unauthorized manner. Data from one system is consistently and accurately transferred to other systems. 19 • “Availability” – the property that data or information
Definition of “e. PHI” • e. PHI or electronic Protected Health Information is patient/member health information which is computer based, e. g. , created, received, stored or maintained, processed and/or transmitted in electronic media. • Electronic media includes computers, laptops, disks, memory stick, PDAs, servers, networks, dial-up modems, Email, web-sites, efax. 20

Why do I need to learn about Security – “Isn’t this just a Systems Problem? ” Good Security Standards follow the “ 90 / 10” Rule: • • 10% of security safeguards are technical 90% of security safeguards rely on the computer user (“YOU”) to adhere to good computing practices – Example: The lock on the door is the 10%. You remembering to lock, check to see if it is closed, 21 ensuring others do not prop the door open, keeping

Culture Change is Coming • The way we at Human Resources & Benefits do business will change • Your work will be impacted as new paths are found 22

Easiest Solution Don’t do it! 23

So what do we do and why are we doing it? 24

Workstation Security “Workstations” include any electronic computing device, for example, a laptop or desktop computer, plus electronic media stored in its immediate environment (e. g. , diskettes, CDs, e-fax). 25

Workstation Controls • Lock-up when you leave your desk! – Offices, files, workstations, sensitive papers and PDAs, laptops, mobile devices / media. – Lock your workstation (Cntrl+Alt+Del and Lock Computer) – Windows XP, Windows 2000 – Do not leave sensitive 26 information on printers, fax

Workstation Controls • Automatic Screen Savers: Set to 15 minutes with password protection. • Shut down before leaving your workstation unattended or leaving work. – This will prevent other individuals from accessing information under your User-ID and limit access by 27

Unique User Log-In / User Access Controls/ Passwords Access Controls: • Users are assigned a unique “User ID” for login purposes • Each individual user’s access to e. PHI system(s) is appropriate and authorized • Unauthorized access to e. PHI by former employees is prevented by terminating access • Follow procedures to terminate accounts in a timely manner 28

Your Account Is Only As Secure As Its Password • Change your password often (at least once every 180 days) • Don't let others watch you log in • Don’t write your password on a post-it note • Don’t attach it to your video monitor or under the keyboard 29

Password Construction • It can’t be obvious or exist in a dictionary. • Every word in a dictionary can be tried within minutes. • Don’t use a password that has any obvious significance to you. 30

Pick a sentence that reminds you of the password. For example: • If my car makes it through 2 semesters, I'll be lucky (imcmit 2 s, Ibl) • Only Bill Gates could afford this $70. 00 textbook (o. BGcat$7 t) • Just what I need, another dumb thing to remember! (Jw 1 n, adttr!) 31

Password Management We share offices, equipment and ideas, but. . . Do not share your password with anyone, anytime! Do not use the same password for critical services at work as you do for personal use. 32

This is what the Systems staff does for you: • • Uses an Internet firewall Uses up-to-date anti-virus software Installs computer software updates & patches Does automated back-ups & storage for TSM users only In addition you should routinely backup all important data and documents • Cleans devices/media before recycling or destroying ―If you want to reuse or recycle zip disks or diskettes send them to BENHUR. ―If you need to destroy CDs send them to BENHUR ―BENHUR will overwrite or clean a workstation 33
Automated Data Backup & Storage Tool = TSM • Systems staff controls backup for critical data for those with TSM (Tivoli Storage Management)** • If you don’t have TSM, you will need to backup your computer manually • Contact your supervisor to determine if you have sensitive & critical data, and need TSM • Supervisors may download forms from http: //hriss. ucop. edu/op/access/ **You should manually backup your computer periodically even if you have TSM 34

Device and Media 35

Security for USB Flash Drives & Other Storage Devices • Flash Drives are devices which pack big data in tiny packages, e. g. , 256 MB, 512 MB, 1 GB. • HR/Benefits strongly recommends that these devices not be used to house sensitive & critical data • If these devices must be used, all files must be password protected. Delete temporar y e. PHI files from local drives & portable media too! 36

Security for PDAs (Personal Digital Assistants) • • ; PDA or Personal Digital t; Assistants are HP o Pil personal organizer alm Q e. g. , calendar, tools, s: P le PA mp q inumbers, a address book, phone Exa mp ; Co o productivity tools, and can contain Tre databases of information and data files with e. PHI. PDAs are at risk for loss or theft. HR/Benefits strongly recommends that these devices not be used to house 37

Remote Access The following minimum standards are required for remote access by personal home computer. More stringent standards may apply in individual units. Apply these same standards to all portable devices. Minimum security standards that you are have: 1. 2. 3. 4. required to Software security patches up-to-date Anti-virus software running and up-to-date Turn-off unnecessary services & programs Physical security safeguards to prevent unauthorized access HR/Benefits strongly recommends that your personal 38 home computer not be used to house sensitive & critical

Email Security Email is like a “postcard”. Email may potentially be viewed in transit by many individuals, since it may pass through several switches enroute to its final destination (e. g. , forwarded, misdirected or never received). Although the risks to a single piece of email are small given the volume of email traffic, emails containing e. PHI need a higher level of security. 39

New Email Policy • Use the Minimum Necessary Standard • Do not send e. PHI outside the department (scrub an email before replying to members and others) • Destroy the original email containing PHI as soon as it is not needed 40

New Email Policy Response to a member sending an email with unnecessary medical information: We have received your email requesting ______. We are working (have worked) on a resolution of your issue (and the status is_______). For your protection, due to HIPAA and other privacy requirements, we may delete your initial email or the unnecessary personal medical information contained in your email, because we did not require it to address your problem. It is the policy of the University to use only the minimum necessary information to resolve our plan members’ issues. 41

New Email Policy TO: Customer. service@ucop. edu From: Anxious. Annie@sbc. net Subject: I need an Operation Dear Vice President Judy Boyette: I retired from the University in 1998 after thirty-five years at UC Berkeley. I have always been with Health Net for my medical plan, and have had no problems with them until recently. They even took care of my treatment with Dr. Freud for severe anxiety disorder after my husband died in 1995. But now they have cancelled my coverage. I have been seeing my doctor recently for back pain and back aches, which he has diagnosed as degenerative disc disease of the lower lumbar. He thinks I will need an operation in the next few months. The Percodan prescription he gave me for pain over the last few months is no longer working. I need surgery soon and can’t get it without my medical coverage. Please help me. Anxious Annie 42

New Email Policy To: Anxious. Annie@sbc. net From: Customer. service@ucop. edu Subject: Your Health Net coverage Dear Annie: We have received your email requesting reinstatement of your Health Net medical coverage. We are working on a resolution of your issue. You should hear from us in the next few days. UC Employee For your protection, due to HIPAA and other privacy requirements, we may delete your initial email or the unnecessary personal medical information contained in your email, because we did not require it to address your problem. It is the policy of the University to use only the minimum necessary information to resolve our plan members’ issues. 43

New Email Policy If you must send PHI to someone, this is what you should do: Use the alternate delivery method of: • phone, • dedicated fax machine, • dedicated carrier line, or • hardcopy. 44

New Email Policy This is also acceptable for sending PHI 1. Send an email with the PHI in an attached password protected Word document. 2. Call the recipients and give them the password over the phone, or send a separate email with the password. 45

World Wide Web 46

On the Wire Universal Access… • Estimated 500 million people with Internet access • All of them can communicate with your connected computer • Any of them can “rattle” the door to your computer to see if it’s locked 47

Opportunities for Abuse • To break into a safe, the safe cracker needs to know something about safes • To break into your computer, the computer cracker only needs to know where to download a program 48

Use of UC’s Internet • UC's Electronic Communications Policy governs use of its computing resources, web-sites, and networks. – Appropriate use of UC's electronic resources must be in accordance with the University principles of academic freedom and privacy. • Protection of UC's electronic resources Remember: The Internet is not private! Access to any requires that everyone use responsible site on the Internet could be traced to your name and location. practices when accessing online resources. – Be suspicious of accessing sites offering questionable content. These often result in spam or the release of viruses. • Be careful about providing personal, sensitive or confidential information to an Internet site or to web-based surveys that are not from trusted 49 sources.

90/10 Rule • System ownership rests with systems staff, systems managers and executive staff • Information ownership rests with you. 50

Your Responsibility to Adhere to UC-Information Security Policies • Users of electronic information resources are responsible for familiarizing themselves with and complying with all University policies, procedures and standards relating to information security. • Users are responsible for appropriate handling of electronic information 51

Safeguards: Your Responsibility • Protect your computer systems from unauthorized use and damage by using: – Common sense – Simple rules – Technology • Remember – By protecting yourself, you're also doing your part to protect 52 UC and our members’ data and

Security Incidents and e. PHI (HIPAA Security Rule) Security Incident defined: “The attempted or successful or improper instance of unauthorized access to, or use of information, or mis-use of information, disclosure, modification, or destruction of information or interference with system operations in an information system. ” 53

Another Security Breach Law SB 1386 • “Security breach” per UC Information Security policy (IS-3) is when a California resident’s unencrypted personal information is reasonably believed to have been acquired by an unauthorized person. Personal Identifiable information means: – Name + SSN + Drivers License + – Financial Account /Credit Card Information • Good faith acquisition of personal information by a University employee or agent for University purposes does not constitute a security breach, provided the personal information is not used or subject to further unauthorized disclosure. 54

Examples of Security Breach • UC Berkeley library data base hacked • UC Berkeley laptop stolen • UCSF accounting department test server compromised • UCLA laptop with blood bank information stolen • UCSD student database hacked 55

Report Security Incidents You are responsible for: • Reporting and responding to security incidents and security breaches. • Reporting security incidents & breaches to: HIPAA Privacy Liaison & HR/B IT Security Officer: Eva Devincenzi Or, HR/B Security Coordinator: Stephanie Rosh 56

What are the Consequences for Security Violations? • Risk to integrity of sensitive & critical information, e. g. , data corruption or destruction • Risk to security of personal information, e. g. , identity theft • Loss of valuable business information • Loss of confidentiality, integrity & availability of data (and time) due to poor or untested disaster data recovery plan 57

What are the Consequences for Security Violations? • Embarrassment, bad publicity, media coverage, news reports • Loss of members’, employees’, and public trust • Costly reporting requirements for SB 1386 issues • Internal disciplinary action(s), termination of employment • Penalties, prosecution and potential for sanctions/lawsuits 58

Sanctions for Violators Employees who violate UC policies and procedures regarding privacy/security of confidential, restricted, and/or protected health information or e. PHI are subject to corrective and disciplinary actions according to existing policies. 59

Want to Learn More? References & Resources • UC Systemwide HIPAA Website (http: //www. universityofcalifornia. edu/hipaa/) • ISS Website (http: //hr-iss. ucop. edu) • Exchange (under Benefits Information/HIPAA folder) • UC Information Security Policy (http: //www. ucop. edu/ucophome/policies/bsfb/bfbis. html) • Guidelines for HIPAA Security Rule Compliance, University of California (On Exchange under Benefits Information/HIPAAfolder/HIPAA policies. doc) 60

Summary • • • Review of HIPAA Privacy Standards Introduce HIPAA Security Standards What the Security Standards require What it means to the way you work Examples of how things will be different Effective April 20, 2005 61

Security Awareness Training HR/B CERTIFICATE Security Awareness Training Module completed by: • Print Name: First: ______Last: _____ • Date of Training: _____ • Unit: ______ Phone # _____________________ 62

Questions? 63
64
Answer the following questions HIPAA requires us to manage our email differently if it contains A. B. C. D. any confidential information personal identifiers & health information personal data and social security number None of the above 65

No Try again. 66
c201036ac660e24cf9e256b3c4b512c5.ppt