9bc2330601d0b256a5a237910c9d7a83.ppt
- Количество слайдов: 14

HASP SRM ® Enabling Business Growth through Software Rights Management Yariv Drory International Technical Support Manager June 2007 All Rights Reserved © 2007 Aladdin Knowledge Systems.

HASP Software Rights Management • Hardware-based and software-based protection & licensing system • The industry’s first all-in-one solution • Advantages of both worlds gives numerous options for: – Strong protection against software piracy – Unmatched protection for your intellectual property – Flexible and secure licensing & distribution
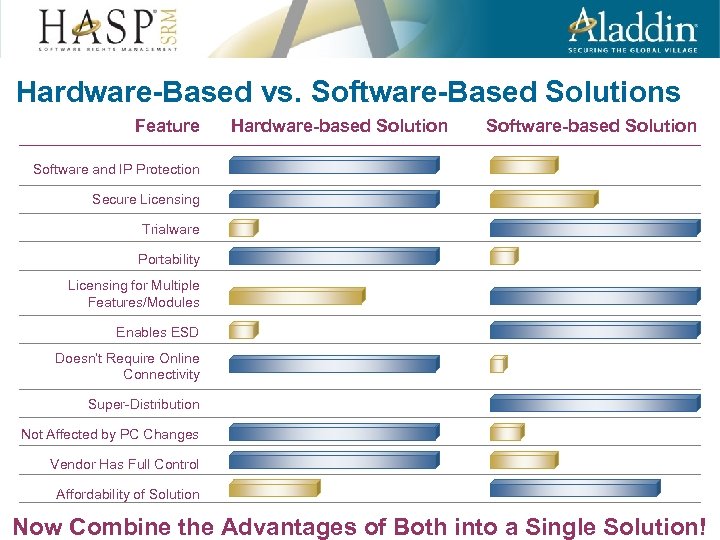
Hardware-Based vs. Software-Based Solutions Feature Hardware-based Solution Software and IP Protection Secure Licensing Trialware Portability Licensing for Multiple Features/Modules Enables ESD Doesn’t Require Online Connectivity Super-Distribution Not Affected by PC Changes Vendor Has Full Control Affordability of Solution Now Combine the Advantages of Both into a Single Solution!
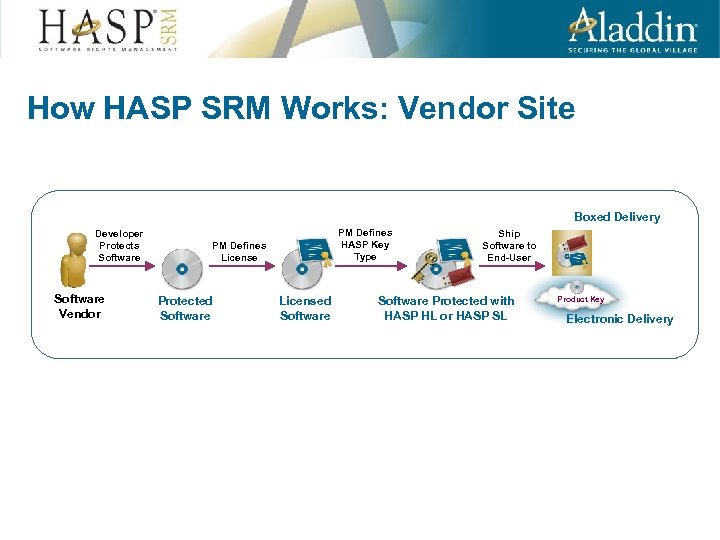
How HASP SRM Works: Vendor Site Boxed Delivery Developer Protects Software Vendor PM Defines HASP Key Type PM Defines License Protected Software Licensed Software Ship Software to End-User Software Protected with HASP HL or HASP SL Product Key Electronic Delivery
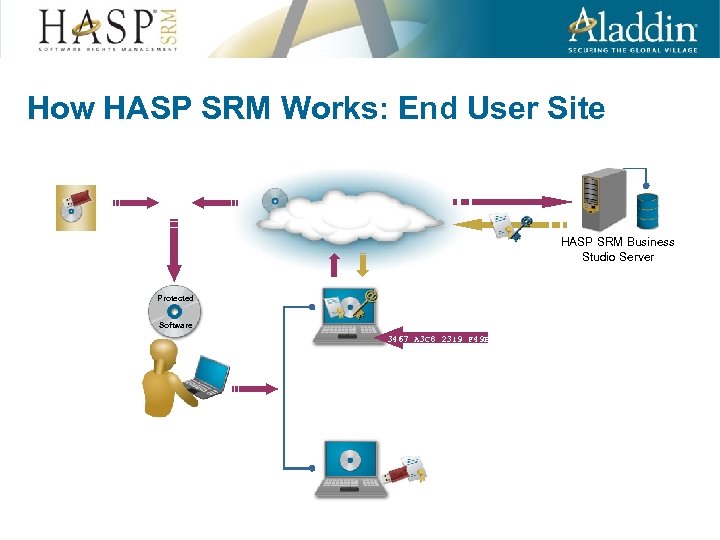
How HASP SRM Works: End User Site HASP SRM Business Studio Server Protected Software 3467 A 3 C 8 2319 F 49 B
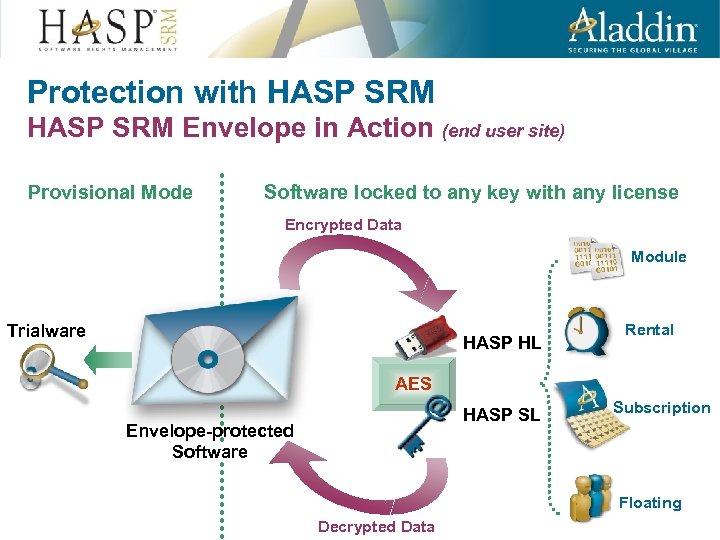
Protection with HASP SRM Envelope in Action (end user site) Provisional Mode Software locked to any key with any license Encrypted Data Module Trialware HASP HL Rental AES HASP SL Envelope-protected Software Subscription Floating Decrypted Data
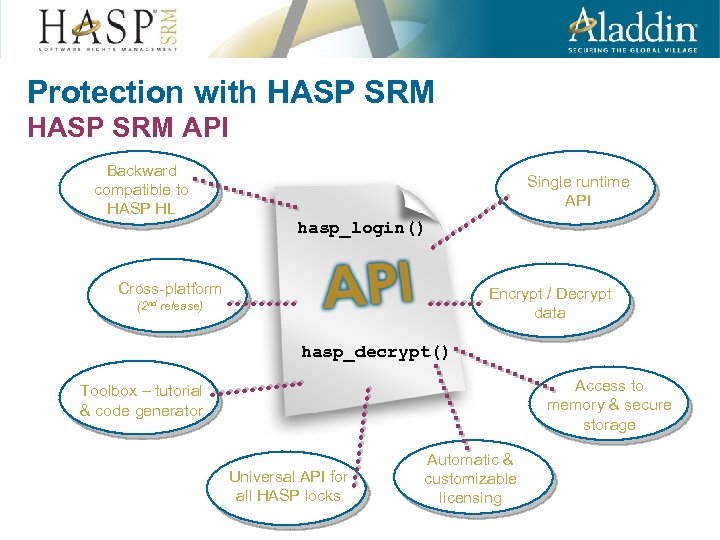
Protection with HASP SRM API Backward compatible to HASP HL Single runtime API hasp_login() Cross-platform Encrypt / Decrypt data (2 nd release) hasp_decrypt() Access to memory & secure storage Toolbox – tutorial & code generator Universal API for all HASP locks Automatic & customizable licensing
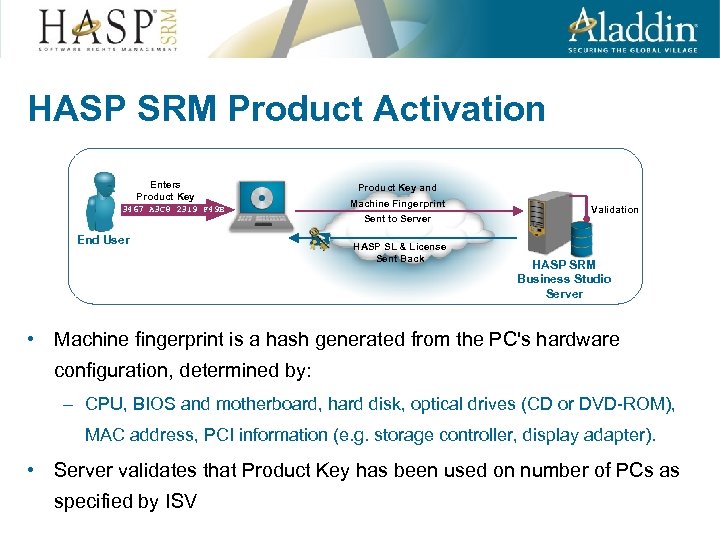
HASP SRM Product Activation Enters Product Key 3467 A 3 C 8 2319 F 49 B End User Product Key and Machine Fingerprint Sent to Server HASP SL & License Sent Back Validation HASP SRM Business Studio Server • Machine fingerprint is a hash generated from the PC's hardware configuration, determined by: – CPU, BIOS and motherboard, hard disk, optical drives (CD or DVD-ROM), MAC address, PCI information (e. g. storage controller, display adapter). • Server validates that Product Key has been used on number of PCs as specified by ISV
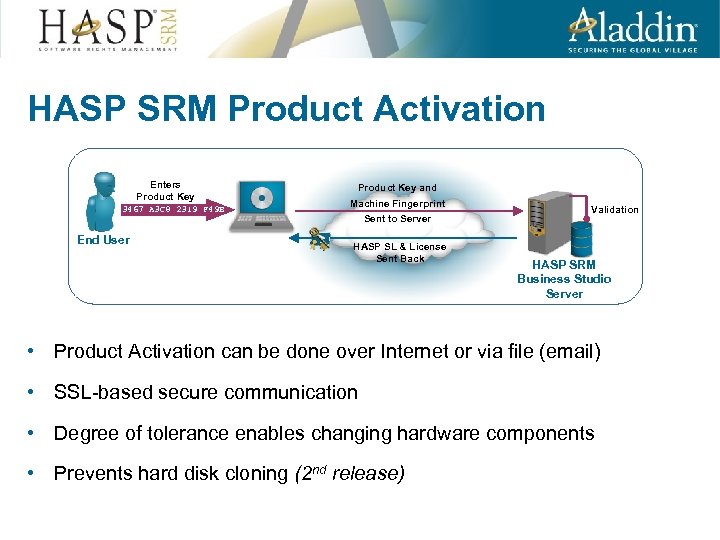
HASP SRM Product Activation Enters Product Key 3467 A 3 C 8 2319 F 49 B End User Product Key and Machine Fingerprint Sent to Server HASP SL & License Sent Back Validation HASP SRM Business Studio Server • Product Activation can be done over Internet or via file (email) • SSL-based secure communication • Degree of tolerance enables changing hardware components • Prevents hard disk cloning (2 nd release)

Licensing with HASP SRM • All licenses can be locked to HASP HL or HASP SL • Out-of-the-box or customized • Supported licenses: Try-Before-You-Buy Floating Rental/Subscription Floating & Time-Based Module/Feature-Based Volume
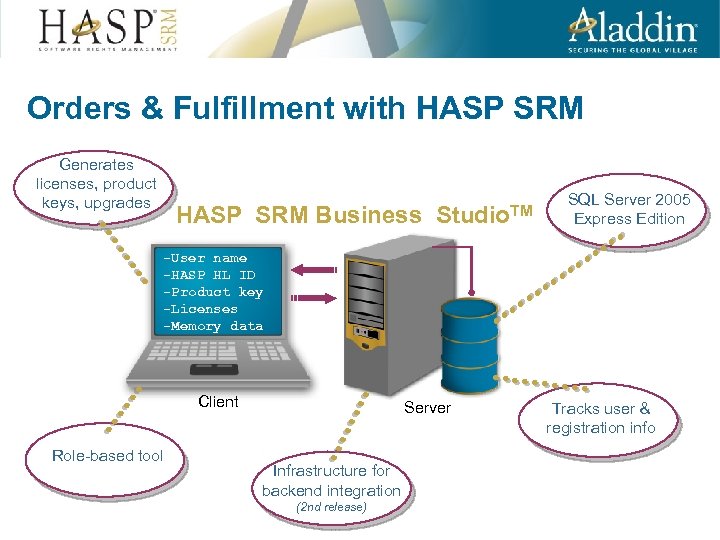
Orders & Fulfillment with HASP SRM Generates licenses, product keys, upgrades HASP SRM Business Studio. TM SQL Server 2005 Express Edition -User name -HASP HL ID -Product key -Licenses -Memory data Client Role-based tool Server Infrastructure for backend integration (2 nd release) Tracks user & registration info

Questions?

Summary: Choices & Flexibility with SRM • Protect Once: Get paid for every software copy: Envelope or API • Deliver Many: Create attractive packages and pricing models with secure flexible licensing & secure remote update: automatic or customized • Cross-Locking : TM New business opportunities: HASP HL or HASP SL • Distribution: Reach the market quickly with Web download or sell traditionally (shrink-wrapped) • Activation: Security in the field: Server-based or HASP HL-based
Protection Licensing Distribution Mix and Match to create the optimum DRM solution that meets your business needs
9bc2330601d0b256a5a237910c9d7a83.ppt