55a014341323a33839db7c261376a238.ppt
- Количество слайдов: 28

Hardware Attack Vectors Yashin Mehaboobe Security Researcher

#whoami • Security Researcher, Open Security • Interested in : • • Embedded system security Radio/ RTL-SDR research Malware Analysis My little projects (Arcanum, Py. Triage) • Organizer, Defcon Kerala ( Mar 4. Be there! ) • Python aficionado • Open source contributor.

Why Hardware? • • • More interesting Less well known = easier to exploit More rewarding Usually open entry point into an otherwise secure network It’s awesome!

Keys to the kingdom?
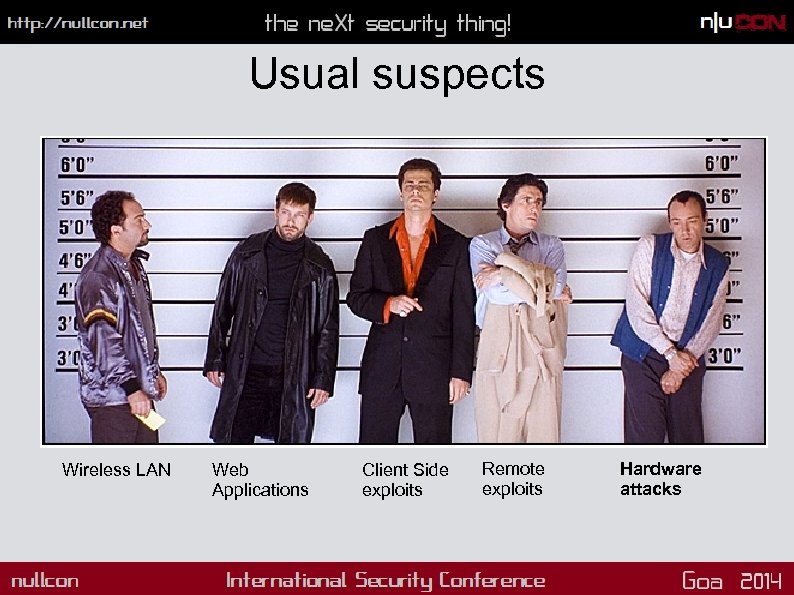
Usual suspects Wireless LAN Web Applications Client Side exploits Remote exploits Hardware attacks

What is covered: • The attack of the HID • Simulating physical access for fun and profit. • IR vector • Let TVs be bygones. • Radio!= FM or Radio!= Wi. Fi • Bus attacks: • Unprotected = Easy to pwn (mostly)

HIDe it • A little bit of physical access is a dangerous thing. • Usually physical access = pwning • Software can’t protect hardware • HID attacks simulate an automated keyboard and mouse • = Attacker gets to run code as if he is physically there.

The Rise of the Rubber Ducky • USB Rubber Ducky by the Hak 5 team. • Comes with an automated script creator. • Looks like a normal USB drive. • Runs the payload burned into the memory when connected.

Teensy • Arduino clone by PJRC • Can emulate an HID device • Existing tools like kautilya and SET to generate payloads. • Again, multiplatform mayhem

DEMO
IR • TV, Pedestrian lights, Old smartphones • Uses one of four: • Philips • Sony • NEC • RAW • IR Library already available for Arduino

Tools of the Trade: • Arduino or a similar microcontroller • TSOP 382 IR receiver • IR LED • Little bit of mischief

IR Attack 1 : Replay • Receive the code using TSOP 382 • Check the code type • Transmit accordingly whenever the button is pressed

TV-B-Gone • Most TVs have predefined poweroff sequence • Widely available • Create a script that goes through the popular off codes one by one • No more pesky TVs
DEMO

Tangoing with Radio • SDR=Software Defined Radio • Usually pretty expensive. • Until the rise of RTLSDR • Scope=AIS, GSM, ADS-B, GPS you name it.

RTL-SDR or cheap radio sniffer • Mainly two types: • • • E 4000: 52 -2200 Mhz R 820 T: 24 -1766 Mhz Software used: • • rtl_sdr • • GQRX SDRSharp Log most data broadcast within the frequency ranges

Sniffing Radio Traffic • AIS (ship transmissions) are easily picked up • So is Aircraft broadcasts • You can sniff most protocols off the air • Decode using baudline • Possible attacks against : Home automation systems and car keyfobs • Keyfobs are supposed to use rolling key codes • “Supposed to”

Antennas ● ● Dependent on the frequency that you want to capture. Different types for different purposes: ● Monopole: ACARS, ADS-B, AIS (Airplanes/Ships) ● Rubber Ducky Antennaes for short range ● Discone for wide coverage (More noise)

Discone Monopole Rubber Ducky
DEMO TIME!

Bus Attacks
The Magic Electronic Buses ● ● ● Buses are used by components in an embedded system to communicate with each other Not secured Most commonly used protocols are SPI, I 2 C and UART ● No authentication ● I 2 C utilizes addressing
Attacking bus protocols ● Sniffing: ● ● ● Logic analyzers pick up most of the protocols Bus pirate is your friend Replay: ● ● ● Sniffed sequences can be played back at later times Bus pirate is your best friend Debug ports: ● ● UART/JTAG ports are left open for debugging purposes Can be used to dump firmware and mess with the memory
Here there be Pirates ● ● Hardware hacker's multitool Read/write I 2 C, SPI, UART ● Midlevel JTAG support ● AVR programmer too! ● Can be accessed via USB.
DEMO
Thank you! Questions?
Contact Details Twitter: twitter. com/yashin. mehaboobe Email: yashinm 92<at>gmail. com
55a014341323a33839db7c261376a238.ppt