bd465a9d0fb9afa978c5abf74c84ff97.ppt
- Количество слайдов: 27

Hardening Web Browsers Against Man-in-the-Middle and Eavesdropping Attacks Dr. José Carlos Brustoloni Dept. Computer Science University of Pittsburgh jcb@cs. pitt. edu Joint work with Haidong Xia May 12, 2005 Jose' Brustoloni

Motivation ♦ Technology for securing Web applications is thought to be well-understood: Ø ♦ HTTPS = HTTP + SSL/TLS What about the usability of this technology? May 12, 2005 Jose' Brustoloni 2

Contributions We performed user studies to answer three related questions: 1. With current browsers and users, how likely is an attack to succeed? Ø 2. Is it possible to make browsers more foolproof? Ø 3. A: Very likely. HTTPS provides alarmingly little actual security. A: Yes. We propose and demonstrate new user interface techniques, CSCV and SPW, that greatly increase usable security. Can user education improve Web browsing security? Ø A: Yes, but better browser/CSCV had greater impact than did Jose' Brustoloni 3 education. May 12, 2005

Eavesdropping attacks ♦ Easy to perform on local area networks with shared medium, e. g. : Ø Ethernet (with hubs) Ø Wi-Fi ♦ Many free applications can be used for eavesdropping, e. g. : Ø tcpdump Ø ethereal May 12, 2005 Jose' Brustoloni 4
Man-in-the-middle (MITM) attacks Actually only slightly more complicated than eavesdropping ♦ Easily available, free tools: ♦ arpspoof Ø dnsspoof Ø webmitm Ø ♦ Necessary if no shared medium (e. g. switched Ethernet) or packets encrypted (e. g. WPA, SSL/TLS) May 12, 2005 Jose' Brustoloni 5
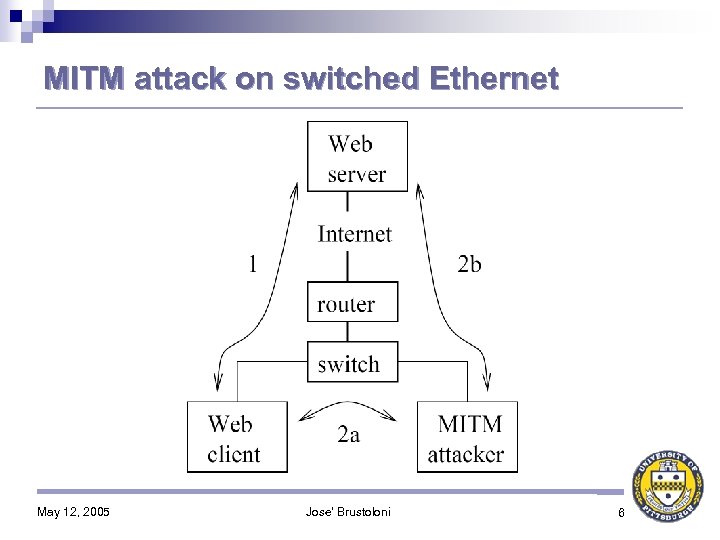
MITM attack on switched Ethernet May 12, 2005 Jose' Brustoloni 6
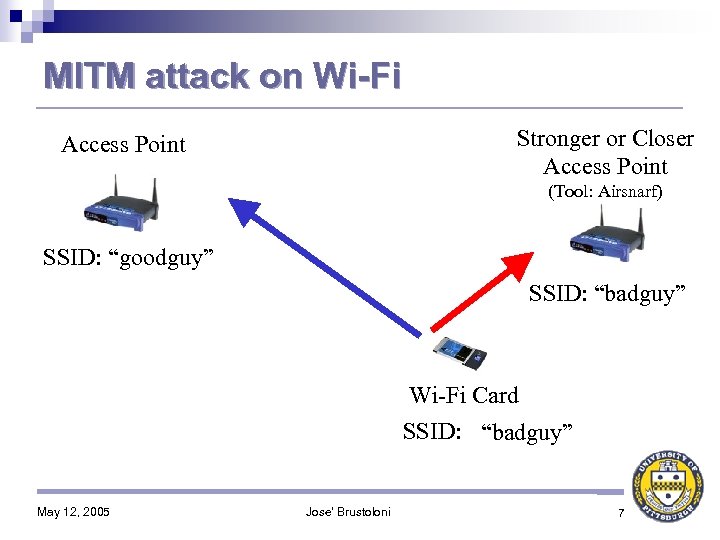
MITM attack on Wi-Fi Stronger or Closer Access Point (Tool: Airsnarf) SSID: “goodguy” SSID: “badguy” Wi-Fi Card SSID: “ANY” “goodguy” “badguy” May 12, 2005 Jose' Brustoloni 7

Certificate verification (in theory) Browser has public keys of major certifying authorities (CAs, e. g. , Verisign) ♦ Secure site supposed to get certificate from one of these CAs, with: ♦ CA’s signature Ø certificate expiration Ø site’s name Ø site’s public key Ø ♦ Browser supposed to: check CA’s signature, expiration, site’s name, CA’s revocation list Ø get site’s public key and use it to authenticate site Ø May 12, 2005 Jose' Brustoloni 8
Certificate verification (in practice) Public-key infrastructure (PKI) not universally deployed ♦ Certificate verification errors are common ♦ Browsers warn users of errors, but allow users to continue despite errors ♦ → Vulnerability to MITM attacks despite HTTPS May 12, 2005 Jose' Brustoloni 9

Why certificate verification fails 1. Browser does not have public key of certificate’s issuer very common for internal sites → often not attack Ø uncommon for public sites → high risk of attack Ø 2. Certificate expired may result from simple inattention Ø unlikely to be attack Ø 3. Certificate’s subject not desired site if subject in same domain as desired site → unlikely to be attack Ø otherwise → high risk of attack Ø Current browsers allow user to proceed despite error in all of these cases May 12, 2005 Jose' Brustoloni 10
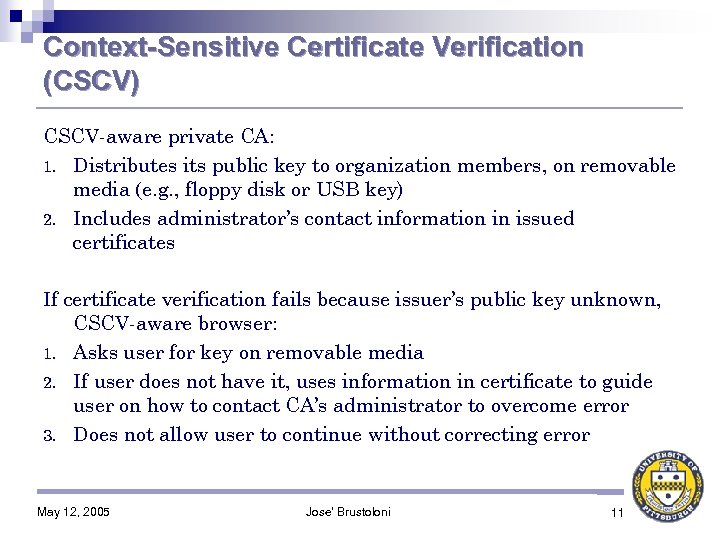
Context-Sensitive Certificate Verification (CSCV) CSCV-aware private CA: 1. Distributes its public key to organization members, on removable media (e. g. , floppy disk or USB key) 2. Includes administrator’s contact information in issued certificates If certificate verification fails because issuer’s public key unknown, CSCV-aware browser: 1. Asks user for key on removable media 2. If user does not have it, uses information in certificate to guide user on how to contact CA’s administrator to overcome error 3. Does not allow user to continue without correcting error May 12, 2005 Jose' Brustoloni 11
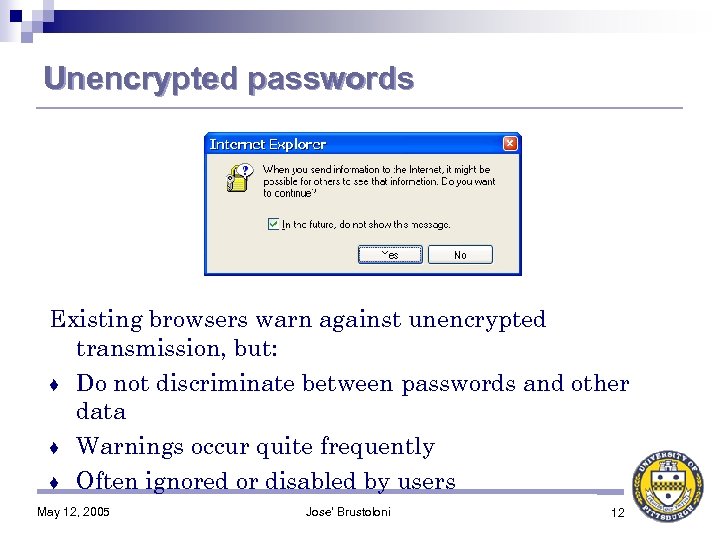
Unencrypted passwords Existing browsers warn against unencrypted transmission, but: ♦ Do not discriminate between passwords and other data ♦ Warnings occur quite frequently ♦ Often ignored or disabled by users May 12, 2005 Jose' Brustoloni 12

Specific Password Warnings (SPW) Browser detects user about to send password unencrypted ♦ Asks if password protects important account ♦ If so, strongly discourages user from continuing: ♦ Tells user signs of secure site (https: , closed padlock) Ø Asks user to consider possibility of MITM replica of usually secure site Ø Asks user to consider consequences of financial or privacy loss Ø May 12, 2005 Jose' Brustoloni 13
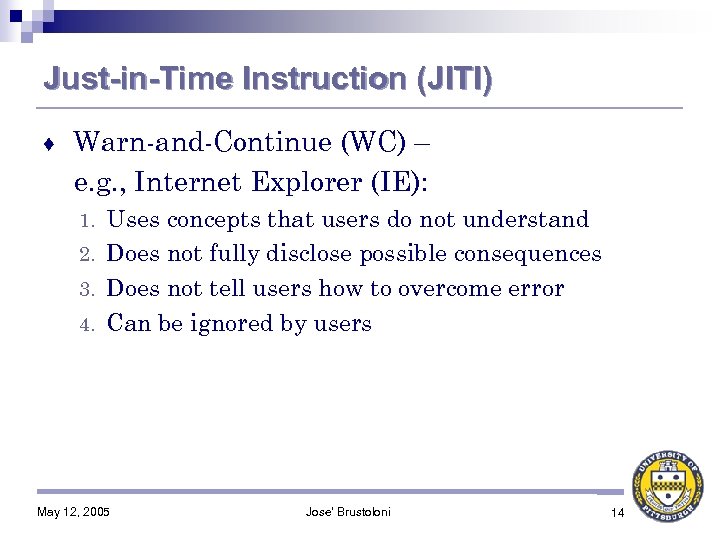
Just-in-Time Instruction (JITI) ♦ Warn-and-Continue (WC) – e. g. , Internet Explorer (IE): Uses concepts that users do not understand 2. Does not fully disclose possible consequences 3. Does not tell users how to overcome error 4. Can be ignored by users 1. May 12, 2005 Jose' Brustoloni 14

Improving JITI ♦ Guidance Without Override (GWO) – e. g. , CSCV: Addresses all four shortcomings in WC Ø Not always possible Ø ♦ Guidance With Override (G+O) – e. g. , SPW: Unlike GWO, can be ignored by user Ø More generally applicable, but less secure Ø May 12, 2005 Jose' Brustoloni 15
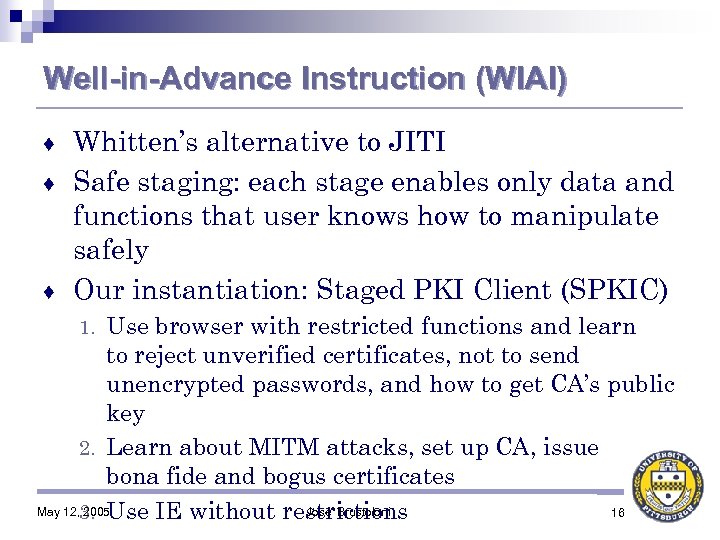
Well-in-Advance Instruction (WIAI) Whitten’s alternative to JITI ♦ Safe staging: each stage enables only data and functions that user knows how to manipulate safely ♦ Our instantiation: Staged PKI Client (SPKIC) ♦ Use browser with restricted functions and learn to reject unverified certificates, not to send unencrypted passwords, and how to get CA’s public key 2. Learn about MITM attacks, set up CA, issue bona fide and bogus certificates May 12, 3. Use IE without restrictions 2005 Jose' Brustoloni 16 1.
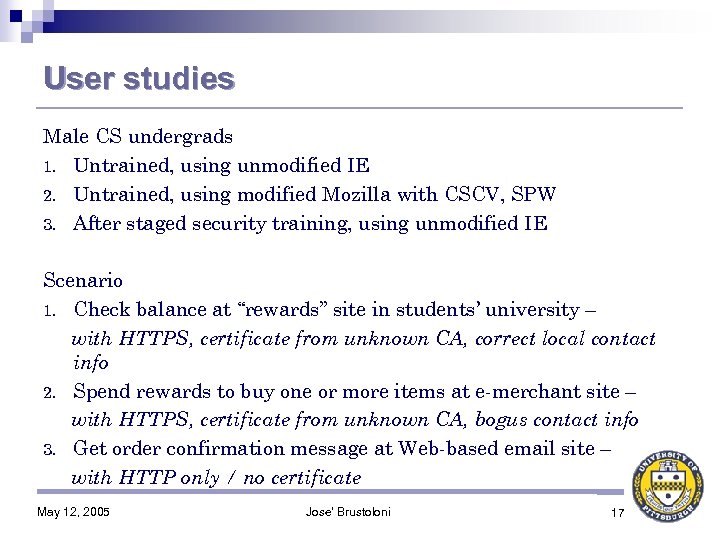
User studies Male CS undergrads 1. Untrained, using unmodified IE 2. Untrained, using modified Mozilla with CSCV, SPW 3. After staged security training, using unmodified IE Scenario 1. Check balance at “rewards” site in students’ university – with HTTPS, certificate from unknown CA, correct local contact info 2. Spend rewards to buy one or more items at e-merchant site – with HTTPS, certificate from unknown CA, bogus contact info 3. Get order confirmation message at Web-based email site – with HTTP only / no certificate May 12, 2005 Jose' Brustoloni 17
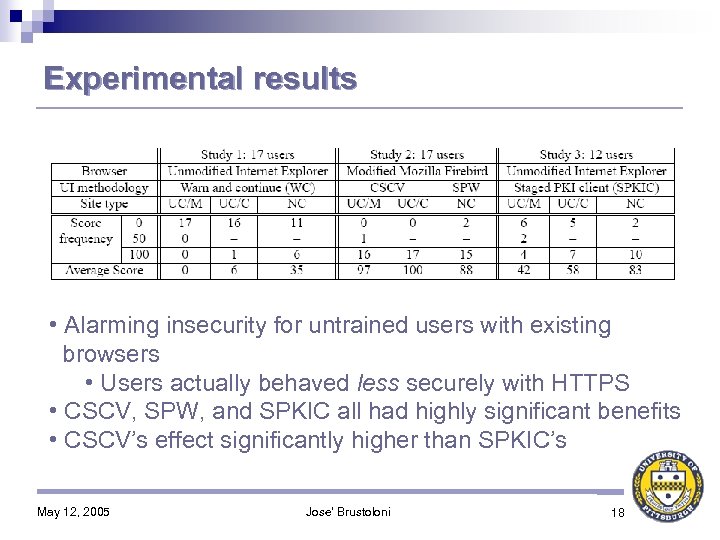
Experimental results • Alarming insecurity for untrained users with existing browsers • Users actually behaved less securely with HTTPS • CSCV, SPW, and SPKIC all had highly significant benefits • CSCV’s effect significantly higher than SPKIC’s May 12, 2005 Jose' Brustoloni 18

Caveats Task completion bias ♦ Difficulty effect ♦ Age, gender, education level, ability not controlled ♦ May 12, 2005 Jose' Brustoloni 19

Related work ♦ ♦ ♦ ♦ Usable security (Adams & Sasse, Anderson, Zurko & Simon, Sandhu, Xia & Brustoloni) Whitten & Tygar – PGP Out-of-band certificate fingerprint verification Identity-based cryptography Ackerman & Cranor – critics Ye & Smith – browser trusted paths Yan & al. – education on password selection May 12, 2005 Jose' Brustoloni 20

Conclusions Most users do not check or understand certificates and ignore warnings ♦ Delegating security decisions to users defeats Web security ♦ CSCV: Discriminate context in which certificate verification fails & guide user in correction ♦ SPW: Warn possible consequences of sending passwords unencrypted ♦ CSCV and SPW greatly increase usable security of browsers Brustoloni May 12, 2005 Jose' 21 ♦
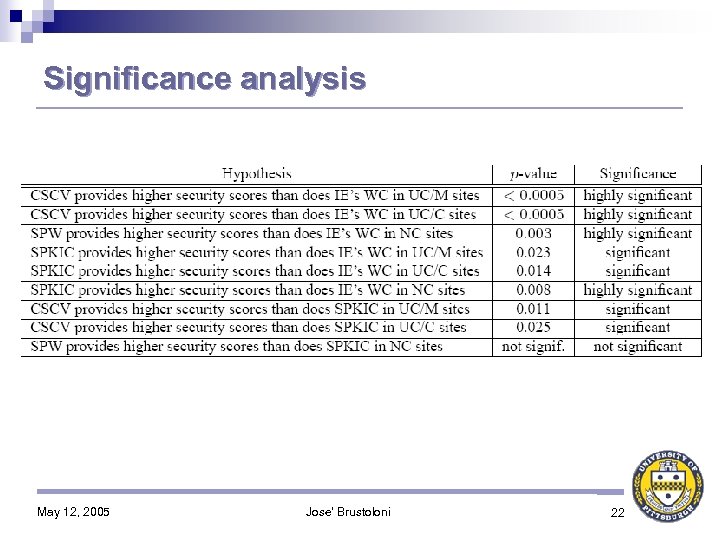
Significance analysis May 12, 2005 Jose' Brustoloni 22
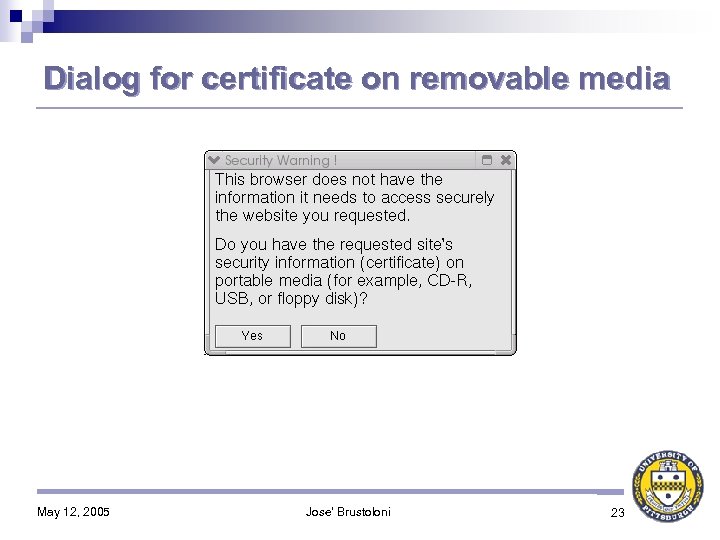
Dialog for certificate on removable media May 12, 2005 Jose' Brustoloni 23
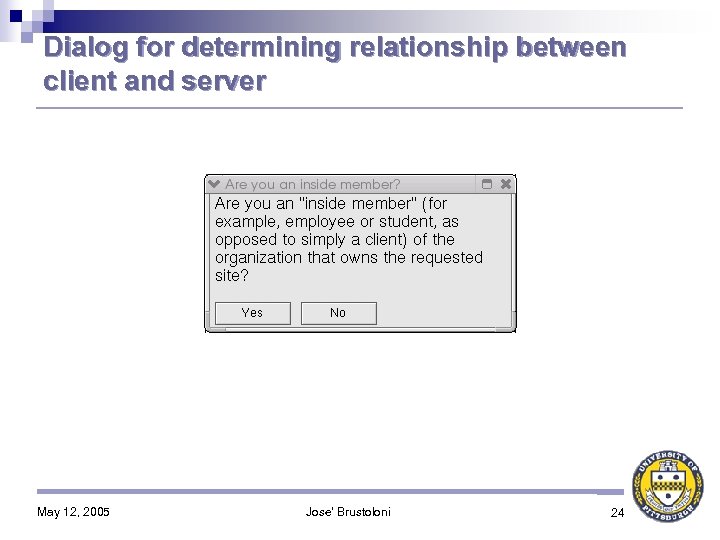
Dialog for determining relationship between client and server May 12, 2005 Jose' Brustoloni 24
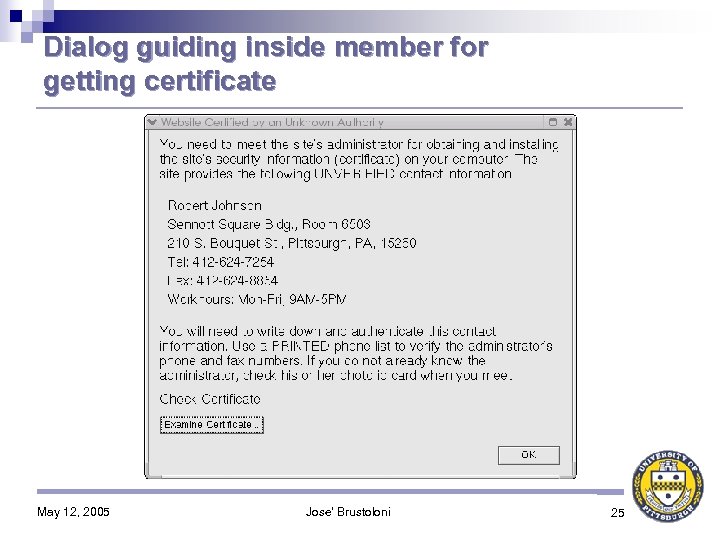
Dialog guiding inside member for getting certificate May 12, 2005 Jose' Brustoloni 25
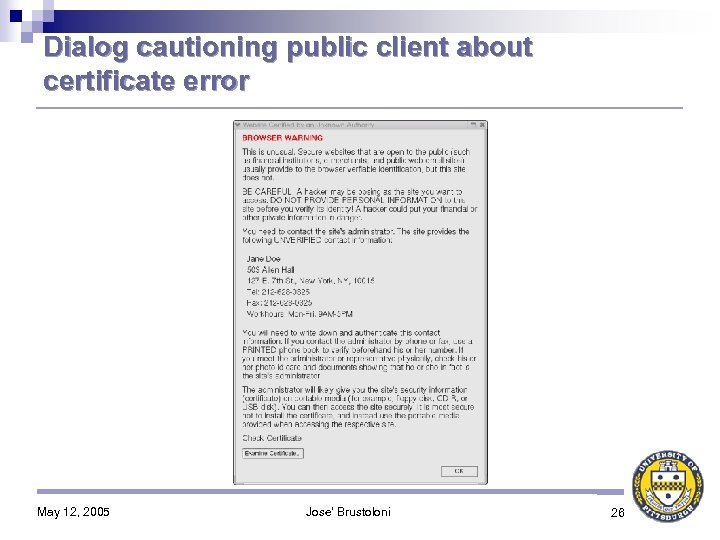
Dialog cautioning public client about certificate error May 12, 2005 Jose' Brustoloni 26
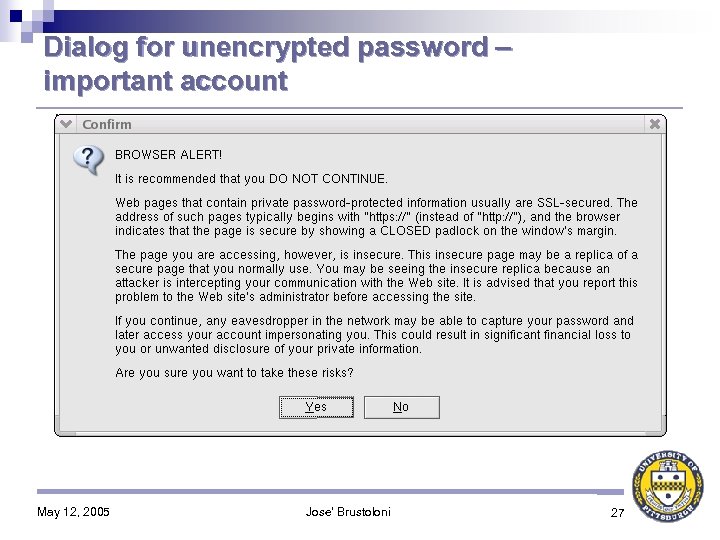
Dialog for unencrypted password – important account May 12, 2005 Jose' Brustoloni 27
bd465a9d0fb9afa978c5abf74c84ff97.ppt