8d043b73ca4c6d9895e11ada7e75f09c.ppt
- Количество слайдов: 76

Hardening Linux By Gregg Rosenberg and Lee Leahu Slide # 1 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Contact Information RICIS, Inc. 8018 Mallow Drive Tinley Park IL 60477 -2697 866 -742 -4777 Voice 708 -444 -2690 Voice 866 -997 -4247 Fax 708 -444 -2697 Fax Slide # 2 Gregory D. Rosenberg gregg@ricis. com Lee Leahu lee@ricis. com Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

What You Will Learn • A review of basic security principals • An overview of Common Criteria security certifications • An introduction to hardening servers reasonably close to the CC EAL 4+ security assurance level. Slide # 3 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
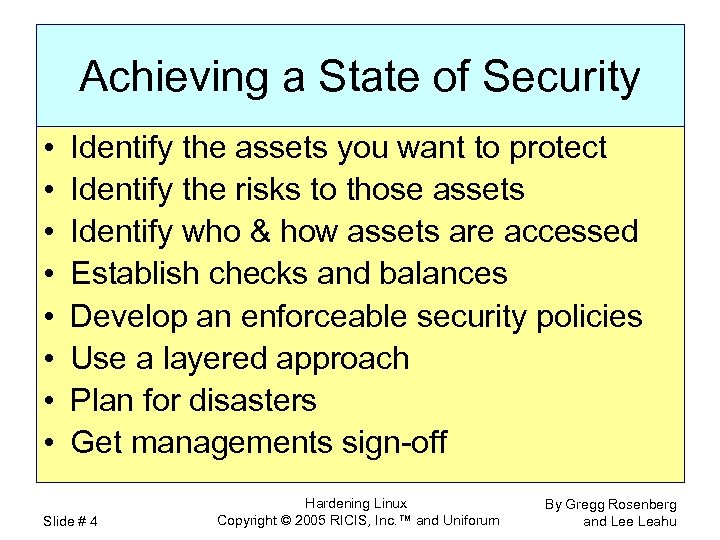
Achieving a State of Security • • Identify the assets you want to protect Identify the risks to those assets Identify who & how assets are accessed Establish checks and balances Develop an enforceable security policies Use a layered approach Plan for disasters Get managements sign-off Slide # 4 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Why Security Policies Fail • • They impair user productivity No or Insufficient user education No policies for handling the unexpected No support from management Security policies are not enforced Laxed monitoring & auditing practices Users having too many privileges Slide # 5 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

The Real Threat • Non malicious damage resulting from: – Human error – Denial of service – Inappropriate disclosure • Policy Breakdown – Key under the doormat – Checks and balances bypassed – Rogues on your network Slide # 6 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
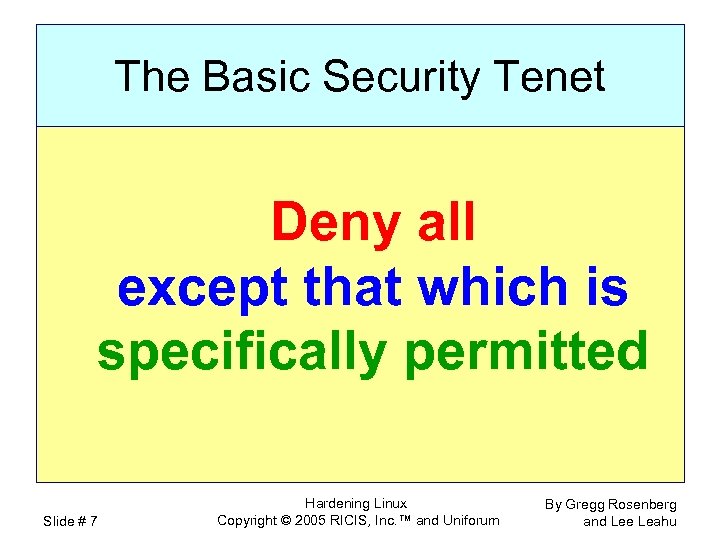
The Basic Security Tenet Deny all except that which is specifically permitted Slide # 7 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
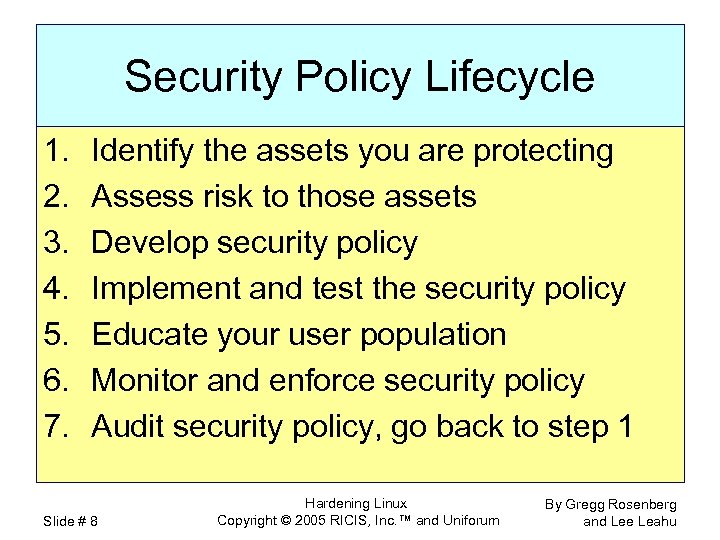
Security Policy Lifecycle 1. 2. 3. 4. 5. 6. 7. Identify the assets you are protecting Assess risk to those assets Develop security policy Implement and test the security policy Educate your user population Monitor and enforce security policy Audit security policy, go back to step 1 Slide # 8 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Evaluation Criteria • • TCSEC (aka Orange Book) FIPS 140 Common Criteria SSE-CMM Slide # 9 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
CC Evaluation Assurance Levels • • EAL 1: Functionally tested EAL 2: Structurally tested EAL 3: Methodically tested and checked EAL 4: Methodically designed, tested, reviewed EAL 5: Semi-formally designed and tested EAL 6: Semi-formally verified design and tested EAL 7: Formally verified design and tested Slide # 10 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Planning for Disasters • • • Securely install your operating system Accurate time source Know every file on your system Validate system integrity Centralize logging Monitor and audit your system regularly Documentation and procedures Emergency response team Backup, backup (Make sure you test your restore procedures periodically) Slide # 11 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Linux Security Certifications • SUSE Linux Enterprise Server archieves – – • • CC EAL 2 in August 2003 (SLES 8) CC EAL 3+ in December 2003 (SLES 8) CC EAL 4+ in December 2004 (SLES 9) CC EAL 5 in March 2005 (SLES 9) Red Hat Linux is nearly a year behind SUSE LINUX, but catching up fast IBM, HP, and others are helping both Slide # 12 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Overview of Security Functions • • • Identification and authentication Audit Object reuse Discretionary Access Control Security management and system protection • Secure communication Slide # 13 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Identification and Authentication • • • Pluggable Authentication Module (PAM) Open. SSH vsftpd su sudo Slide # 14 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Linux Auditing Subsystem (LAUS) • The audit subsystem was implemented by the SUSE Security Team members Olaf Kirch and Thomas Biege • The audit subsystem is intended to be the central interface for collecting and viewing the record of security relevant events • All authentication done through the PAM library, including the identity and location of the user and the success or failure result. Slide # 15 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Linux Auditing Subsystem (2) • Use of su to change identity. All actions done as part of a su session are marked in the audit record with the original user’s login user ID. • Adding, changing, or deleting users or groups • Changes and change attempts to the contents of security critical files • Changes to the access permissions or ownership of any files or IPC objects • Binding network ports and accepting connections Slide # 16 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Discretionary Access Control • Linux is a multi-user operating system. You can control which other users will be able to read or modify your files by setting the Unix permission bits and user/group IDs • You can achieve more precise control using POSIX-style access control lists (ACLs). • The administrators (’root’) are able to override these permissions and access all files on the system. • Use of encryption is RECOMMENDED for additional protection of sensitive data. Slide # 17 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Objects Reuse • the kernel automatically ensures that new objects (disk files, memory, IPC) do not contain any traces of previous contents Slide # 18 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Installation Considerations • Ensure the hardware clock is accurately set to the current date, time, and time zone. • Install the latest system BIOS and firmware • Ensure that all hardware interfaces or devices that are not required are disabled in BIOS • Password protect BIOS and boot menus • Consider using a remote management solution and losing the keyboard, and mouse • Carefully consider disk controllers / spindles Slide # 19 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Installation Considerations (2) • Carefully plan your partition layout before beginning your base operating system installation • Verify your installation source is authentic • Build and harden the system before plugging it into your network • You can also build from a package distribution server if you and it are on a trusted internal network • Do a less than minimum installation • Do not install a GUI Slide # 20 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
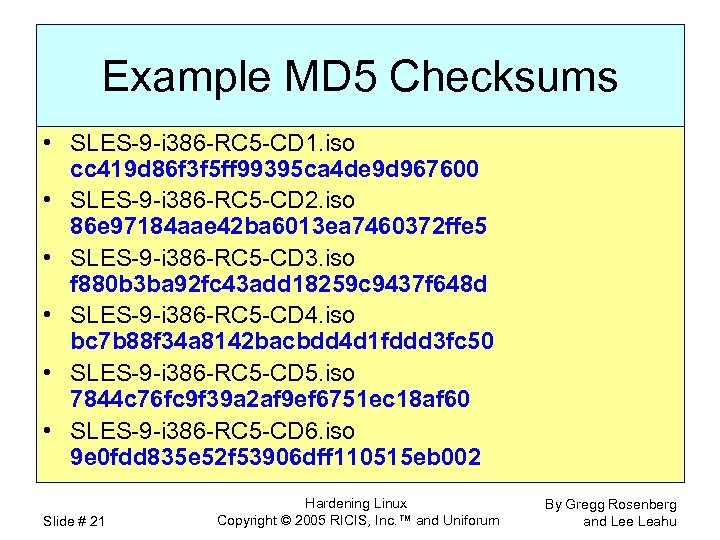
Example MD 5 Checksums • SLES-9 -i 386 -RC 5 -CD 1. iso cc 419 d 86 f 3 f 5 ff 99395 ca 4 de 9 d 967600 • SLES-9 -i 386 -RC 5 -CD 2. iso 86 e 97184 aae 42 ba 6013 ea 7460372 ffe 5 • SLES-9 -i 386 -RC 5 -CD 3. iso f 880 b 3 ba 92 fc 43 add 18259 c 9437 f 648 d • SLES-9 -i 386 -RC 5 -CD 4. iso bc 7 b 88 f 34 a 8142 bacbdd 4 d 1 fddd 3 fc 50 • SLES-9 -i 386 -RC 5 -CD 5. iso 7844 c 76 fc 9 f 39 a 2 af 9 ef 6751 ec 18 af 60 • SLES-9 -i 386 -RC 5 -CD 6. iso 9 e 0 fdd 835 e 52 f 53906 dff 110515 eb 002 Slide # 21 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
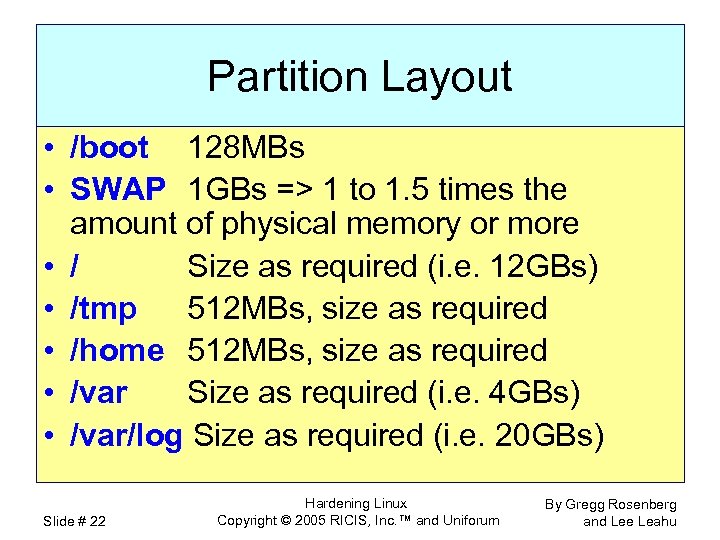
Partition Layout • /boot 128 MBs • SWAP 1 GBs => 1 to 1. 5 times the amount of physical memory or more • / Size as required (i. e. 12 GBs) • /tmp 512 MBs, size as required • /home 512 MBs, size as required • /var Size as required (i. e. 4 GBs) • /var/log Size as required (i. e. 20 GBs) Slide # 22 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
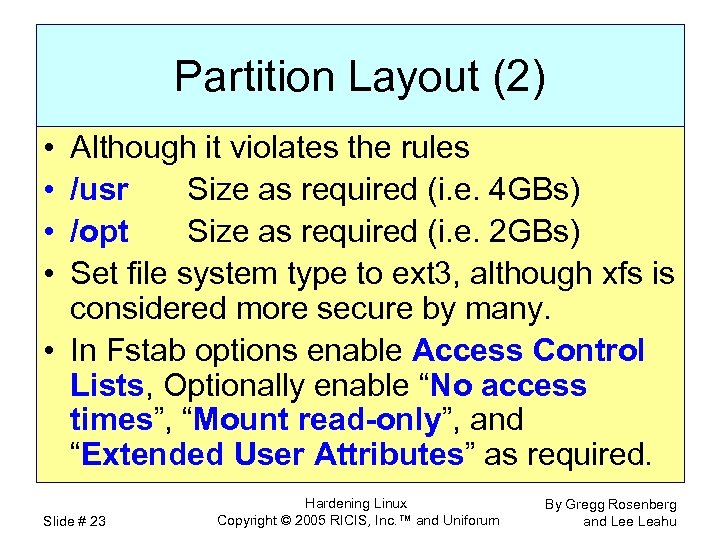
Partition Layout (2) • • Although it violates the rules /usr Size as required (i. e. 4 GBs) /opt Size as required (i. e. 2 GBs) Set file system type to ext 3, although xfs is considered more secure by many. • In Fstab options enable Access Control Lists, Optionally enable “No access times”, “Mount read-only”, and “Extended User Attributes” as required. Slide # 23 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Trusted, Tolerated, and Unknown Software • Trusted software has been evaluated and can be well trusted. • Tolerated software has been evaluated, but should be carefully considered before use. • Unknown software is any other software you intend to install on the system that has not been formally evaluated Slide # 24 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Additional Required Packages • laus - The Linux Audit System • laus-64 bit - ONLY for ppc 64 (p. Series, i. Series) systems • pam-laus - Audit-enabled version of the PAM libraries • The above packages should be installed after you finish the base minimum install. • Star - Data archival tool with ACL support Slide # 25 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Recommended Packages • texinfo - Info documentation viewer • man-pages - Manual pages • howtoenh - how-to documentation (HTML format) • sles-admin_en - Administrator Manual Slide # 26 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Optional Packages • lprng - Print spooler • cups – May be a better choice, but it is not on the trusted or tollerated list. • xinetd - XInetd (only used for vsftpd) • vsftpd - FTP daemon (needs xinetd) • stunnel - set up encrypted SSL tunnels There additional packages on the trusted or tolerated list that can be installed Slide # 27 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
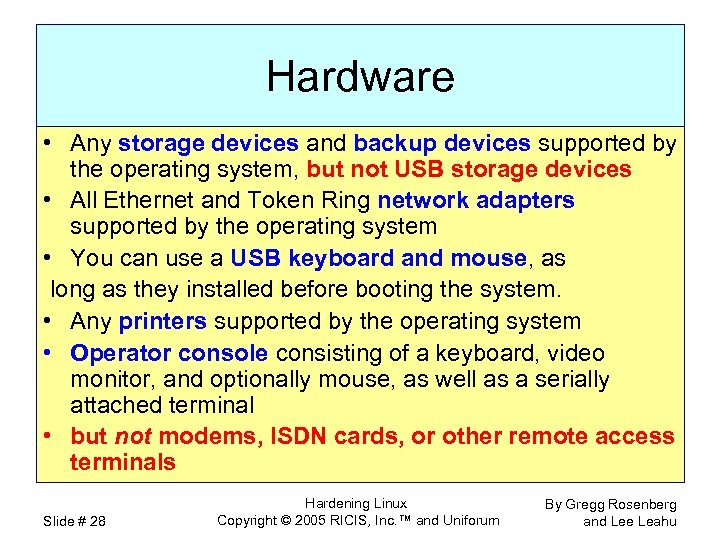
Hardware • Any storage devices and backup devices supported by the operating system, but not USB storage devices • All Ethernet and Token Ring network adapters supported by the operating system • You can use a USB keyboard and mouse, as long as they installed before booting the system. • Any printers supported by the operating system • Operator console consisting of a keyboard, video monitor, and optionally mouse, as well as a serially attached terminal • but not modems, ISDN cards, or other remote access terminals Slide # 28 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Installation • • Disconnect network cables Verify authenticity of installation source Boot from Service Pack 2 CD # 1 Launch installer You may use text mode or a serial console Accept EULA Select English language Slide # 29 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Installation (2) • • • On the “Installation Settings” screen: Select “New Installation” for mode Select appropriate keyboard Customize partitioning Select minimum software installation and add / remove additional packages discussed in the prior slides • Keep default boot options (no other OS allowed) Slide # 30 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Installation (3) • Keep hardware clock on UTC and select your local time zone • Choose “Accept” to start installation • The installer will reboot • Secure boot settings in BIOS to HDD only • Configure network interface with static IP, host name, default gateway, no DHCP • Do not enable LDAP, use local only Slide # 31 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Secure Initial System Config • Enable the SUSE Firewall 2 and only permit ssh. Later you can open other ports that are required. • Setup /etc/hosts. allow to restrict access further. • Lockdown removable media (CD/DVD) devices, -t ISO 9660 -o ro, nodev, nosuid, noauto • Disable usbfs • Disable all unneeded services • Remove or rename links to their startup and shutdown scripts in /etc/init. d Slide # 32 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Secure Initial System Config (2) • If not using NIS, removed NIS on the automount line in /etc/nsswitch. conf. • It is a good idea to setup an ntp client to draw time from a reliable and accurate local time source. • You can use the “ntpq –c peer” command to verify that time synchronization is working correctly. Slide # 33 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Secure Initial System Config (3) • Install the optional CC EAL 4+ Security Update. rpm -Uvh /root/rpm/certification-slesibm-eal 4*. noarch. rpm • Please check the file /usr/share/doc/packages/certificationsles-ibm-eal 4/README-eal 4. txt from the certification-sles-ibm-eal 4. rpm for the latest errata information. Slide # 34 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Disable Services • Disable the following services using the run level editor: – Nfsboot – Powersaved – ACPI modules – Slpd – xdm - although it is not installed – fbset Slide # 35 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Disable Services (2) • The system runlevel as specified in the ’initdefault’ entry in /etc/inittab MUST BE ’ 3’ • The following services are REQUIRED for runlevel 3: atd audit coldplug cron hwscan network random syslog rpmconfigcheck Slide # 36 • The following services are OPTIONAL for runlevel 3: hotplug lpd sshd kbd postfix xinetd – Disable usbfs Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Restricted Execution Environment • Setup a chroot directory structure • Enable chroot support for those services that can be chroot’d • Some services can be installed into your chroot’d environment Slide # 37 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Remove SUID/SGID • Remove SUID / SGID root settings from binaries find / ( ! -fstype ext 3 -prune -false ) -o -type f ( -perm -4000 -o -perm -2000 ) -exec chmod u-s, g-s {} ; -print • Make sure that /etc/sysconfig/security has the following two variables set: – CHECK_PERMISSIONS=set – PERMISSION_SECURITY="eal 4" • Then run “chkstat -set /etc/permissions. eal 4” to set the needed SUID and SGID bits. Slide # 38 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
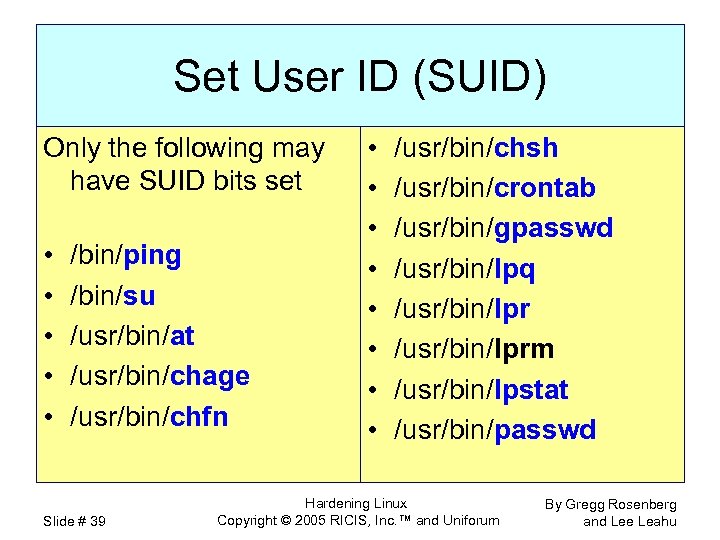
Set User ID (SUID) Only the following may have SUID bits set • • • /bin/ping /bin/su /usr/bin/at /usr/bin/chage /usr/bin/chfn Slide # 39 • • /usr/bin/chsh /usr/bin/crontab /usr/bin/gpasswd /usr/bin/lpq /usr/bin/lprm /usr/bin/lpstat /usr/bin/passwd Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Set Group ID (SGID) The SGID bit MUST NOT be used to give group ”root” privileges to any binary. • /usr/sbin/postdrop - group "maildrop" • /usr/sbin/postqueue - group "maildrop" • /usr/sbin/utempter - group "tty" Slide # 40 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
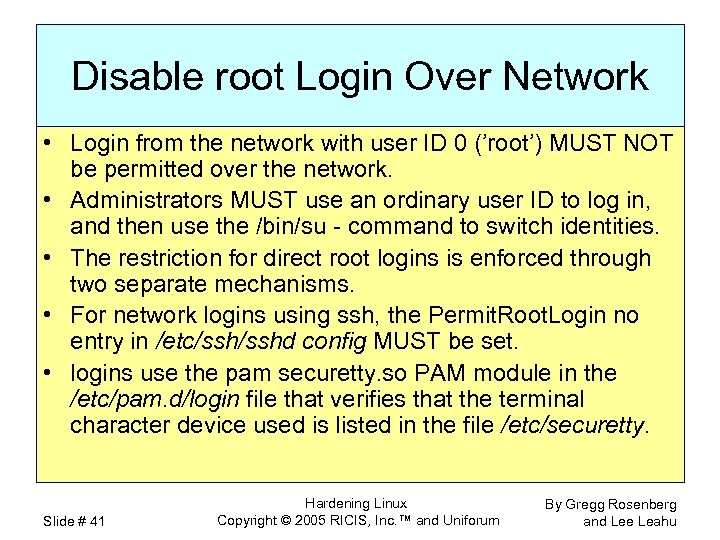
Disable root Login Over Network • Login from the network with user ID 0 (’root’) MUST NOT be permitted over the network. • Administrators MUST use an ordinary user ID to log in, and then use the /bin/su - command to switch identities. • The restriction for direct root logins is enforced through two separate mechanisms. • For network logins using ssh, the Permit. Root. Login no entry in /etc/sshd config MUST be set. • logins use the pam securetty. so PAM module in the /etc/pam. d/login file that verifies that the terminal character device used is listed in the file /etc/securetty. Slide # 41 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Reminder Alias for su • It is RECOMMENDED that you remind administrators of this by adding the following alias to the bash configuration file /etc/bashrc. local that disables the pathless ’su’ command: alias su="echo "Always use ’/bin/su -’ (see Configuration Guide)"" • This alias can be disabled for the root user in /root/. bashrc: unalias su Slide # 42 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
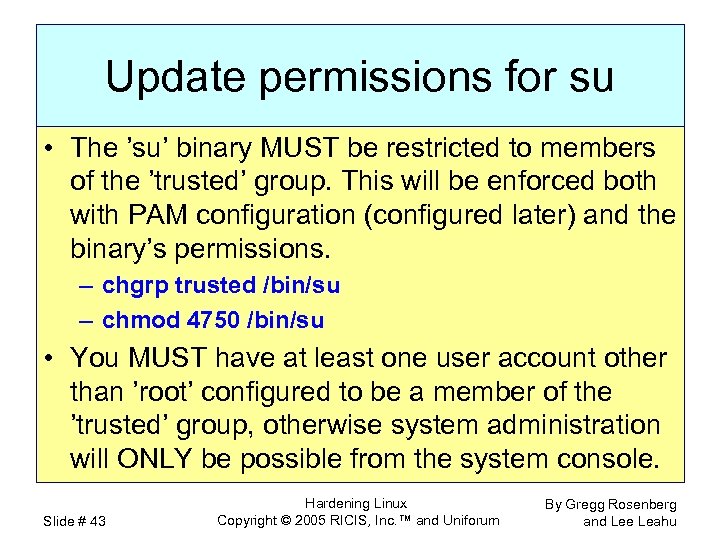
Update permissions for su • The ’su’ binary MUST be restricted to members of the ’trusted’ group. This will be enforced both with PAM configuration (configured later) and the binary’s permissions. – chgrp trusted /bin/su – chmod 4750 /bin/su • You MUST have at least one user account other than ’root’ configured to be a member of the ’trusted’ group, otherwise system administration will ONLY be possible from the system console. Slide # 43 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
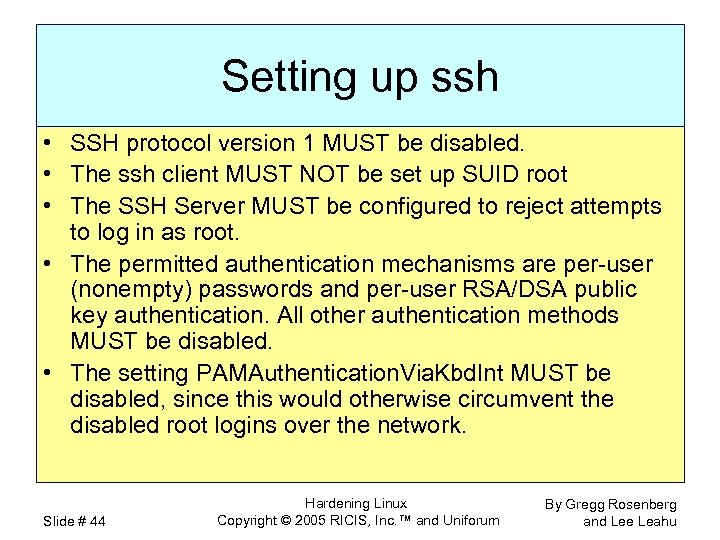
Setting up ssh • SSH protocol version 1 MUST be disabled. • The ssh client MUST NOT be set up SUID root • The SSH Server MUST be configured to reject attempts to log in as root. • The permitted authentication mechanisms are per-user (nonempty) passwords and per-user RSA/DSA public key authentication. All other authentication methods MUST be disabled. • The setting PAMAuthentication. Via. Kbd. Int MUST be disabled, since this would otherwise circumvent the disabled root logins over the network. Slide # 44 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
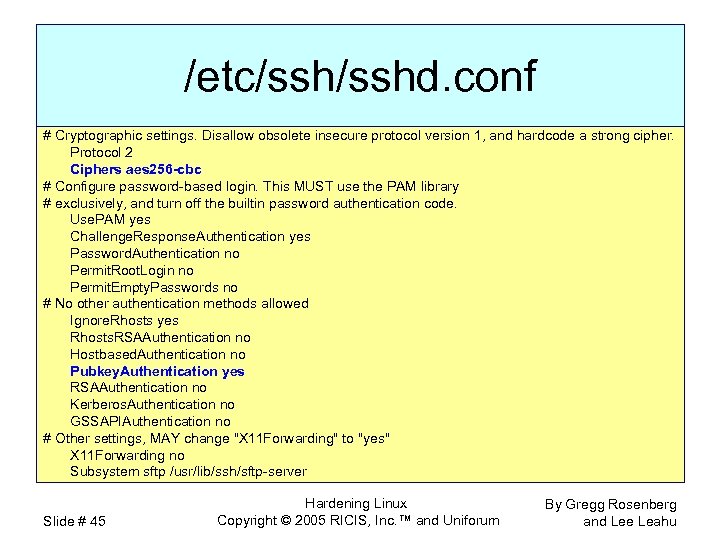
/etc/sshd. conf # Cryptographic settings. Disallow obsolete insecure protocol version 1, and hardcode a strong cipher. Protocol 2 Ciphers aes 256 -cbc # Configure password-based login. This MUST use the PAM library # exclusively, and turn off the builtin password authentication code. Use. PAM yes Challenge. Response. Authentication yes Password. Authentication no Permit. Root. Login no Permit. Empty. Passwords no # No other authentication methods allowed Ignore. Rhosts yes Rhosts. RSAAuthentication no Hostbased. Authentication no Pubkey. Authentication yes RSAAuthentication no Kerberos. Authentication no GSSAPIAuthentication no # Other settings, MAY change "X 11 Forwarding" to "yes" X 11 Forwarding no Subsystem sftp /usr/lib/ssh/sftp-server Slide # 45 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Setting up the Audit Subsystem • Setting up the audit configuration files • For all platforms, it is RECOMMENDED to use the following settings in the /etc/sysconfig/audit file: AUDIT_ALLOW_SUSPEND=1 AUDIT_ATTACH_ALL=0 AUDIT_MAX_MESSAGES=1024 AUDIT_PARANOIA=0 • The laus package by default installs these files with the RECOMMENDED contents: /etc/audit. conf /etc/audit/filter. conf /etc/audit/filesets. conf • Make auditd start at boot, insserv audit Slide # 46 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
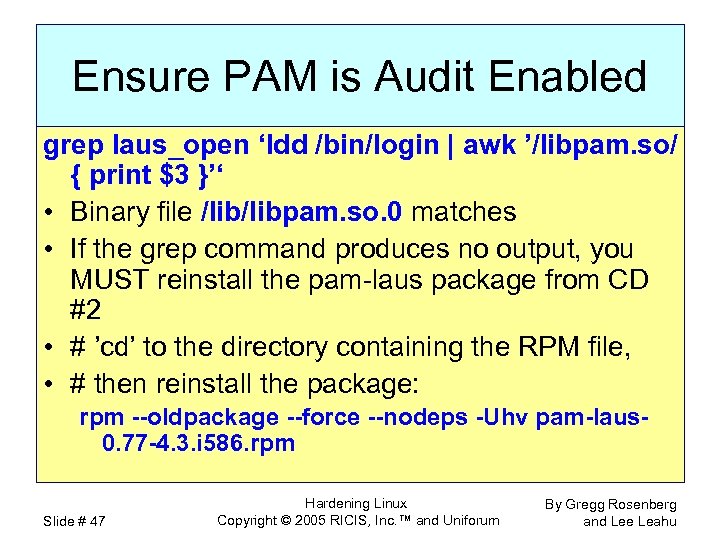
Ensure PAM is Audit Enabled grep laus_open ‘ldd /bin/login | awk ’/libpam. so/ { print $3 }’‘ • Binary file /libpam. so. 0 matches • If the grep command produces no output, you MUST reinstall the pam-laus package from CD #2 • # ’cd’ to the directory containing the RPM file, • # then reinstall the package: rpm --oldpackage --force --nodeps -Uhv pam-laus 0. 77 -4. 3. i 586. rpm Slide # 47 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
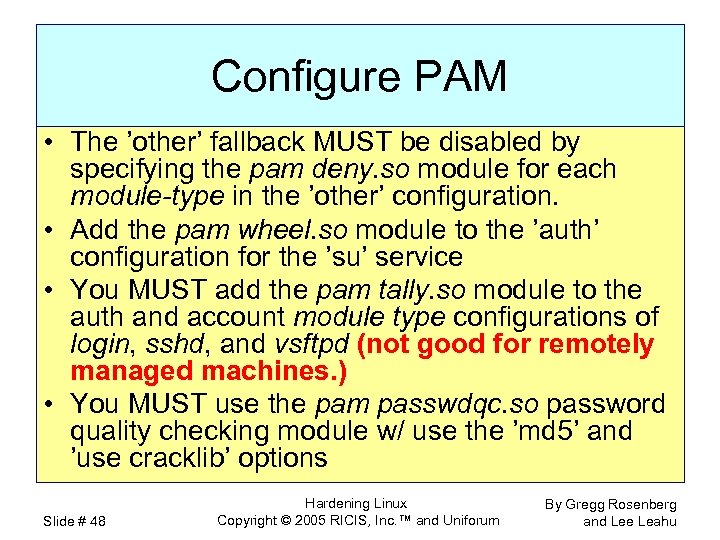
Configure PAM • The ’other’ fallback MUST be disabled by specifying the pam deny. so module for each module-type in the ’other’ configuration. • Add the pam wheel. so module to the ’auth’ configuration for the ’su’ service • You MUST add the pam tally. so module to the auth and account module type configurations of login, sshd, and vsftpd (not good for remotely managed machines. ) • You MUST use the pam passwdqc. so password quality checking module w/ use the ’md 5’ and ’use cracklib’ options Slide # 48 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Configuring PAM (2) • The ’remember=XX’ option must be added to the /etc/security/pam pwcheck. conf file to force users to create new passwords and not re-use • In general, you MAY add PAM modules that additional restrictions. You MUST NOT weaken the restrictions Slide # 49 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
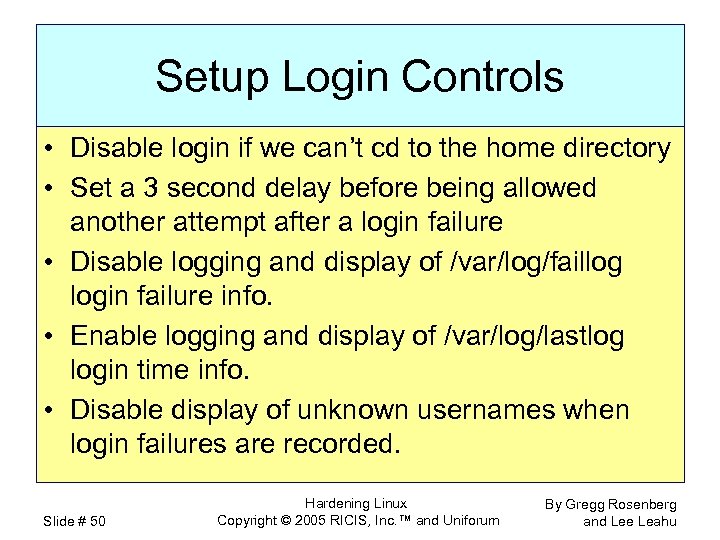
Setup Login Controls • Disable login if we can’t cd to the home directory • Set a 3 second delay before being allowed another attempt after a login failure • Disable logging and display of /var/log/faillog login failure info. • Enable logging and display of /var/log/lastlog login time info. • Disable display of unknown usernames when login failures are recorded. Slide # 50 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Setup Login Controls (2) • Set max number of login retries to <= 3 if password is bad • Set max time to <= 60 seconds for login • Require password before chfn/chsh can make any changes. • Restrict fields to “rwh” that may be changed by regular users using chfn Slide # 51 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Setup Login Controls (3) • The default umask for logged-in users is set in the /etc/profile, not here. • Umask to 077 which is used by useradd and newusers for creating new home directories. • Password aging controls (used by useradd): – – PASS_MAX_DAYS 60 PASS_MIN_DAYS 1 PASS_WARN_AGE 7 PASS_MIN_LEN 8 Slide # 52 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Configure the Boot Loader • Ensure the system boots exclusively from the disk partition containing Linux • Make sure you use BIOS password to protect access to this configuration. • Use the password command in /boot/grub/menu. lst to prevent unauthorized use of the boot loader interface. • Use md 5 encoded passwords, run the command grub-md 5 -crypt to generate the encoded version of a password. Slide # 53 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Configure the Boot Loader • Protect all menu entries other than the default SLES boot with the lock option • Add a line containing just the keyword lock after the title entry in the /boot/grub/menu. lst file • Remove group and world read permissions from the grub configuration file if it contains a password chmod 600 /boot/grub/menu. lst • All changes to the configuration take effect automatically on the next boot Slide # 54 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Adding Additional Software • Kernel modules other than those provided as part of the evaluated configuration MUST NOT be installed or loaded. • You MUST NOT load the tux kernel module (the in-kernel web server is not supported). • You MUST NOT add support for non-ELF binary formats or foreign binary format emulation that circumvents system call auditing. • You MUST NOT activate knfsd or export NFS file systems. Slide # 55 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Adding Additional Software (2) • Device special nodes MUST NOT be added to the system • SUID root or SGID root programs MUST NOT be added to the system. • Programs which use the SUID or SGID bits to run with identities other than ’root’ MAY be added. • The content, permissions, and ownership of all existing file-system objects (including directories and device-nodes) that are part of the evaluated configuration MUST NOT be modified. Slide # 56 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Adding additional Software (4) • Programs automatically launched with ’root’ privileges MUST NOT be added to the system. • Processes that immediately and permanently switch to a non privileged identity on launch are permitted, • Automatic launch mechanisms are: • – Entries in /etc/inittab • – Executable files or links in /etc/init. d/ and its subdirectories Slide # 57 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Document your system • Rebooted server to implement new SMP kernel. # uname –a Linux avflyer-asp 2. 6. 5 -7. 201 -smp #1 SMP Thu Aug 25 06: 20: 45 UTC 2005 i 686 i 386 GNU/Linux • List services now running on the system. # chkconfig | grep -v "off" | more • List directories with the sticky bit set # find / -type d -perm -1000 -ls Slide # 58 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Document Your System (2) • List files with Set User ID (SUID) bit set. find / -type f -perm -4000 -ls • List files with Set Group ID (SGID) bit set. find / -type f -perm -2000 –ls • List files that are world writeable. find / -type f -perm -0002 -ls • List all installed packages. rpm -qa --qf '%-25{NAME}t%-20{VERSION}t%8{RELEASE}t%{Summary}n' | sort > /root/rpmpackagelist Slide # 59 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Security monitoring & management • Setup tripwire to monitor system file integrity and to audit changes. • Setup and implement log file rotation policies. • Setup a central syslog server (syslog-ng) • Use a log analyzer, such as logcheck. • Setup a monitoring system like Nagios or Argus on your network. Slide # 60 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Sec Monitoring & Management (2) • Created /var/log/btmp to log bad login attempts. # touch /var/log/btmp # lastb btmp begins Sun Sep 11 13: 58: 05 2005 Slide # 61 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
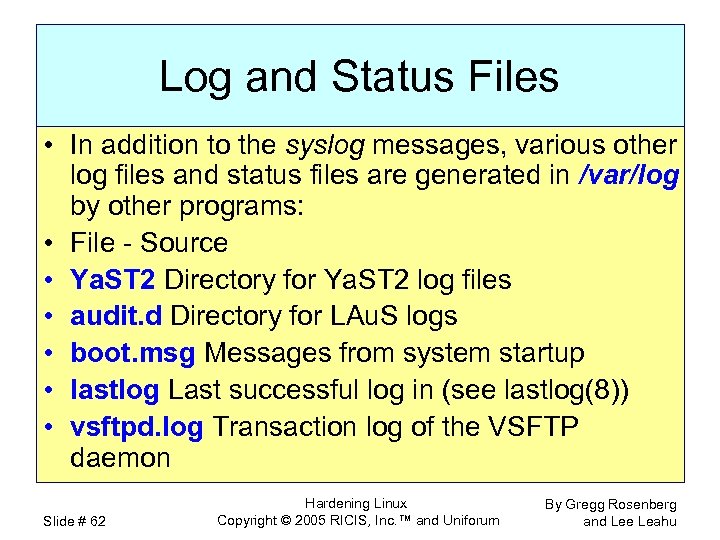
Log and Status Files • In addition to the syslog messages, various other log files and status files are generated in /var/log by other programs: • File - Source • Ya. ST 2 Directory for Ya. ST 2 log files • audit. d Directory for LAu. S logs • boot. msg Messages from system startup • lastlog Last successful log in (see lastlog(8)) • vsftpd. log Transaction log of the VSFTP daemon Slide # 62 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
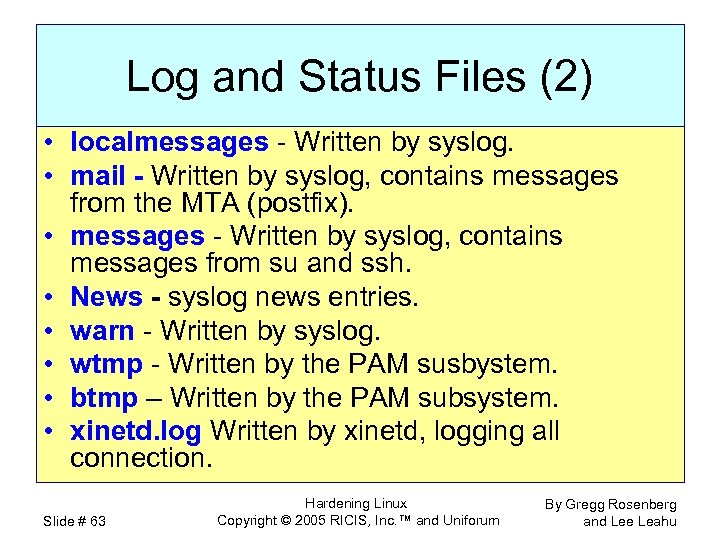
Log and Status Files (2) • localmessages - Written by syslog. • mail - Written by syslog, contains messages from the MTA (postfix). • messages - Written by syslog, contains messages from su and ssh. • News - syslog news entries. • warn - Written by syslog. • wtmp - Written by the PAM susbystem. • btmp – Written by the PAM subsystem. • xinetd. log Written by xinetd, logging all connection. Slide # 63 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Auditing Your System • It is RECOMMENDED that you review the system’s configuration at regular intervals to verify if it still agrees with the evaluated configuration. • This primarily concerns those processes that may run with ’root’ privileges. • The permissions of the device files /dev/* MUST NOT be modified. • In particular, review settings in the following files and directories to ensure that the contents and permissions have not been modified: Slide # 64 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
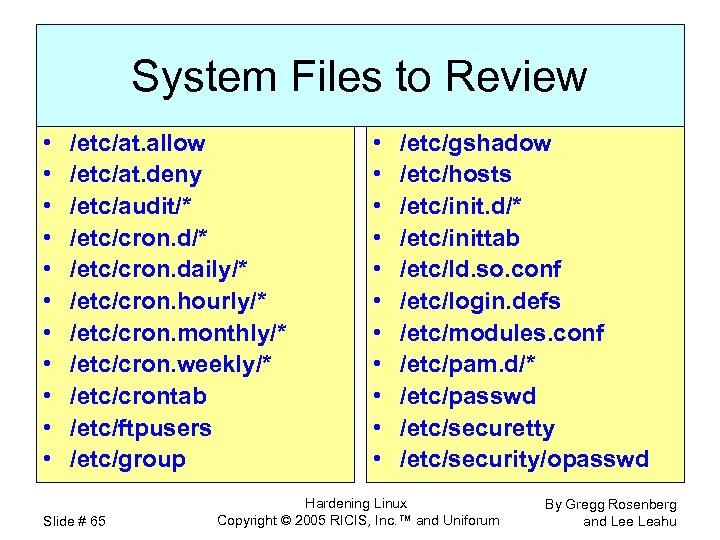
System Files to Review • • • /etc/at. allow /etc/at. deny /etc/audit/* /etc/cron. daily/* /etc/cron. hourly/* /etc/cron. monthly/* /etc/cron. weekly/* /etc/crontab /etc/ftpusers /etc/group Slide # 65 • • • /etc/gshadow /etc/hosts /etc/init. d/* /etc/inittab /etc/ld. so. conf /etc/login. defs /etc/modules. conf /etc/pam. d/* /etc/passwd /etc/securetty /etc/security/opasswd Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
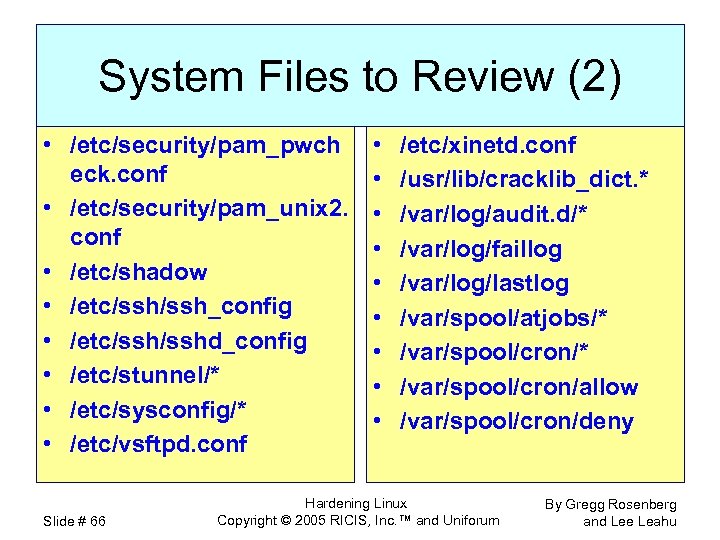
System Files to Review (2) • /etc/security/pam_pwch eck. conf • /etc/security/pam_unix 2. conf • /etc/shadow • /etc/ssh_config • /etc/sshd_config • /etc/stunnel/* • /etc/sysconfig/* • /etc/vsftpd. conf Slide # 66 • • • /etc/xinetd. conf /usr/lib/cracklib_dict. * /var/log/audit. d/* /var/log/faillog /var/log/lastlog /var/spool/atjobs/* /var/spool/cron/allow /var/spool/cron/deny Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Auditing Your System (2) • Use the command lastlogb to detect unusual patterns of logins. • Also verify the output of the following commands (run as ’root’): # atq # crontab -l # find / ( -perm -4000 -o -perm -2000 ) -ls # find / ( -type f -o -type d -o -type b ) -perm -0002 -ls # find /bin /boot /etc /lib /sbin /usr ! -type l ( ! -uid 0 -o -perm +022 ) Slide # 67 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Auditing Your System (3) • Use the aucat(8) and augrep(8) tools to retrieve information from the audit logs. The information available for retrieval depends on the active filter configuration. 1. # view the last 100 audit records aucat | tail -100 2. # view all successful PAM authentications augrep -e TEXT -U AUTH_success 3. # all actions recorded for a specified login UID (this includes 4. # actions done by this user with a different effective UID, 5. # for example, via SUID programs or as part of a "su" session) augrep -l kw 6. # file removals augrep -e SYSCALL -S unlink Slide # 68 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Secure Communication • • • SSH V 2 Stunnel with Open. SSL X 11 Forwarding through an SSH tunnel Secure FTP Externally signed SSL certificate Slide # 69 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

System maintenance • Download, verify, and carefully review each patch before you install it. • If possible test patches in a non-production environment. • Keep a manual logbook, as well as a README file in the /root home directory with any updates or changes you make to the system. Slide # 70 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Considerations for Servers • Customize firewall (iptables) • Port restrictions • Ensure current directory is not in any ones (root or a regular user) path • Configures standard system cron jobs, like deletion of old files in /tmp or update of the man databases. The settings are read by the shell scripts /etc/cron. daily/*. • Configures some system variables for the boot process. IP_DYNIP=no # The system only has a static address IP_TCP_SYNCOOKIES=yes # Syn Flood protection IP_FORWARD=no # Set to yes if the system acts as a router. ENABLE_SYSRQ=no # System request key MUST be disabled. Slide # 71 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Considerations for DNS Servers • • Enable bind chroot support. Apply port restrictions in firewall. Customize logging as desired. Authoritative DNS servers should not be used as resolving or caching DNS servers. • Disable recursive queries on authoritative servers. • Enable numerous security settings in /etc/named. conf to suit your environment. Slide # 72 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Considerations for Email Servers • Chroot postfix (manual process) • Ensure unauthorized parties can’t relay • Establish port restrictions and access control with iptables. • Configure smtp restrictions in postfix. • Use ldap or access file to restrict inbound mail to valid users • Anti-virus / Anti-Spam Slide # 73 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Useful Resources • Practical Unix & Internet Security, 3 rd Edition by Simson Garfinkel, Gene Spafford, Alan Schwartz Publisher: O'Reilly; 3 edition (February 21, 2003) ISBN: 0596003234 • Hardening Linux by John H. Terpstra, Paul Love, Ronald P. Reck Publisher Mc. Graw Hill Osborne ISBN: 0 -07 -225497 -1 • There are way too many books to list even a fraction of the good ones I keep handy on my shelf here. Slide # 74 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu

Useful resources (2) • If there are conflicting recommendations in this guide and in one of the sources listed here, the Configuration Guide has precedence concerning the evaluated configuration. • Su. SE Linux Enterprise Server Installation Guide, – /usr/share/doc/packages/sles-inst-x 86+x 86 -64 en/ – /usr/share/doc/packages/sles-inst-ipseries en/ – /usr/share/doc/packages/sles-inst-zseries en/ • Su. SE Linux Enterprise Server Administrator Guide, – /usr/share/doc/packages/sles-admin-x 86+x 86 -64 en/ – /usr/share/doc/packages/sles-admin-ipseries en/ – /usr/share/doc/packages/sles-admin-zseries en/ Slide # 75 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
Questions Slide # 76 Hardening Linux Copyright © 2005 RICIS, Inc. ™ and Uniforum By Gregg Rosenberg and Lee Leahu
8d043b73ca4c6d9895e11ada7e75f09c.ppt