a9550b61b4bff193c52868349352dd74.ppt
- Количество слайдов: 17

Hacking outside the box Mike Aiello

Objectives • Describe jobs in “Infosec" • Discuss why communication is critically important to Infosec professionals – How to communicate well • What to know about working in large organizations • Interactive discussion: solving a complicated security problem • Advice for succeeding as an Infosec professional

Background • Poly Grad 2006 BS/MS • Worked with ISIS Lab students on various projects (CTF, research projects) • Own a business that sells RFID blocking wallets • Work at an investment Bank as an “Application Risk Analyst”

Assumptions & Context • Once you are done with the penetration testing course, you should be able to break into any computer system given enough time, money and energy • You can poke holes in encryption algorithms, design secure architectures and publish vulnerabilities in products built by multimillion dollar companies. • Published research reports in major books and journals. • Now what? ?
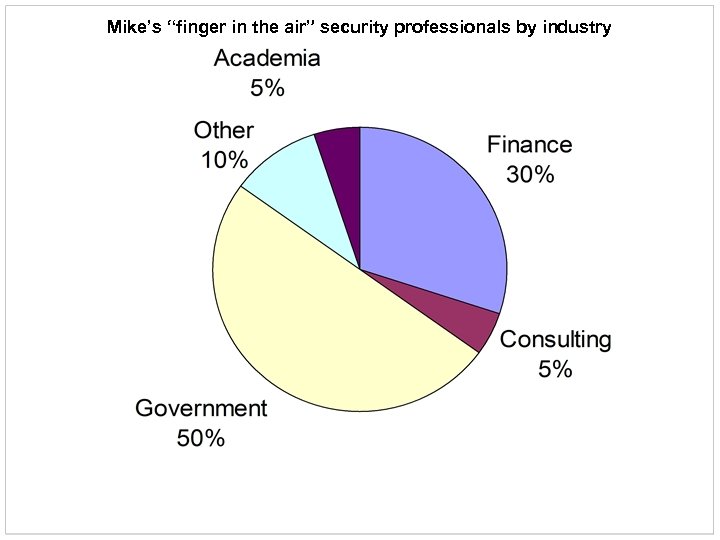
Mike’s “finger in the air” security professionals by industry
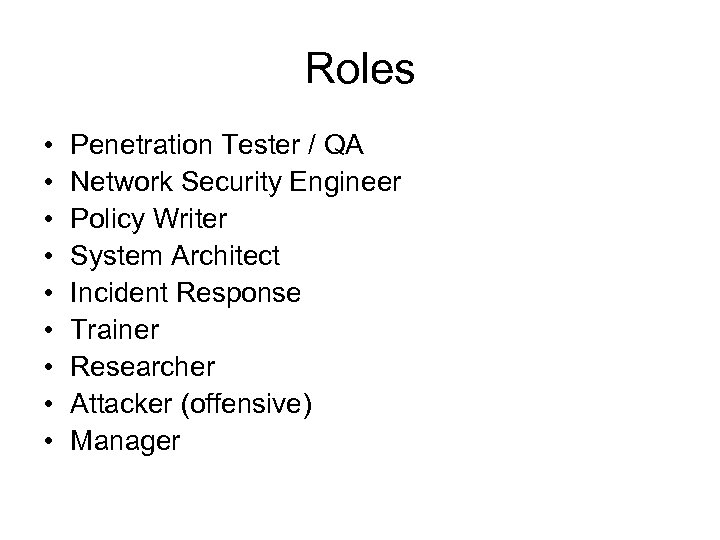
Roles • • • Penetration Tester / QA Network Security Engineer Policy Writer System Architect Incident Response Trainer Researcher Attacker (offensive) Manager
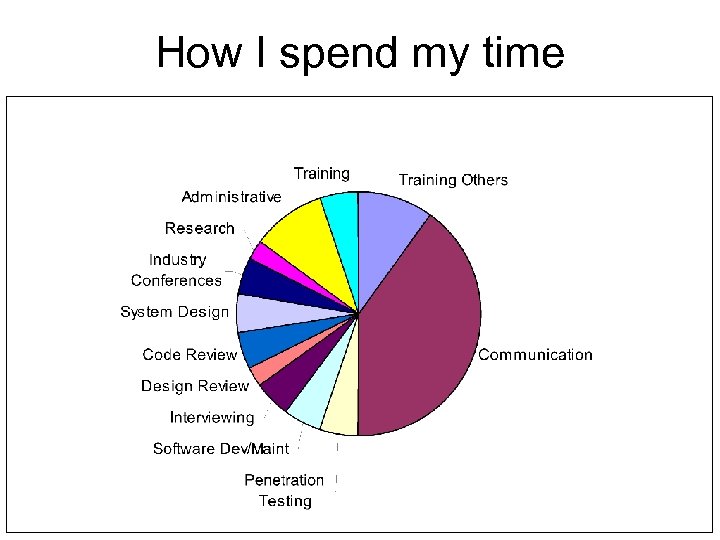
How I spend my time
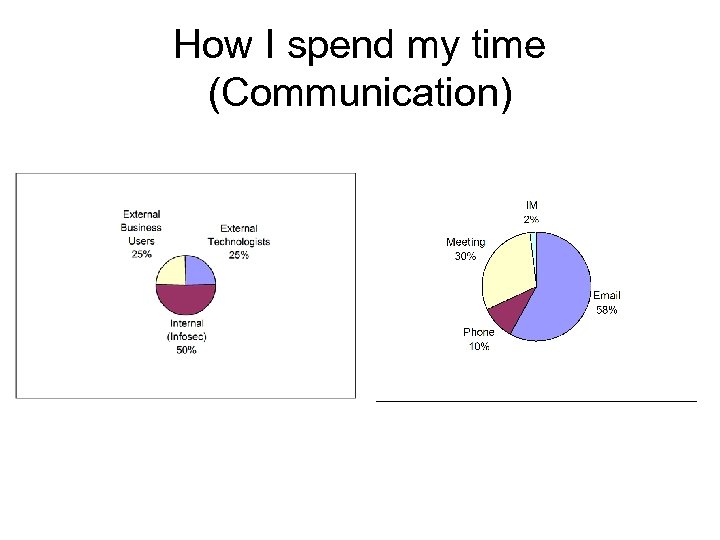
How I spend my time (Communication)

Communicating Well • Practice – Professional Email – Clear & concise writing in English – Policies, Standards, Guidelines • Organization – Don’t drop the ball. Get things done. • “Know your business” • Know how the organization works
Architecting Exercise – The New Green • The New Green (Forbes 01/07/2008) • The U. S. Treasury makes money the old-fashioned way, by printing it. • The Treasury should let others get into the business of issuing money • Why not print money at home on your laser printer rather than go to the ATM? Today, we can do this with stamps; the illustration shows postage produced by stamps. com.

Architecting Exercise – The New Green • Context. You work for the treasury, you’ve been tasked with making this happen. • Who needs to be involved making the decisions? • How much will it cost? (What needs to be done? ) • Timeline? • Prove it will succeed, demonstrate situations where it could fail?

Advice • Please take with grain of salt

Be in motion: commoditization is the goal • People are expensive, replace them with cheap computers • Web Authoring – HTML “coders” replaced with Front. Page • Infosec – Testing/QA • Automated Web Application Testing • Automated Static Code Analysis • Automated Network Assessment – Policy (maybe) • Templates for policy, standards, guidelines, audit reports – Operations • Firewalls, VPNs, Routers & other security products becoming trivial to manage

Don’t be ignorable • Know your industry & tell people what is going on in it – Read: Blogs, proceedings, news • Security Focus, Bruce Schneier, ha. ckers. org – Go to: Conferences, trade group meetings • OWASP, Black. Hat • • Elevator pitch for “what you do” Know the business as well as anyone else who works there Network like a crazy person “Be the Don” Know who matters Be the best at something SHY & QUIET KILLS YOUR CAREER. Make sure people know “what you do” • Be especially nice to administrators, they know everything

Do something scary every day • Know the risk reward curve • Tell people they are wrong! Your boss doesn't know everything, you were hired you as an expert • Ask for critical feedback • Give critical feedback • Ask for help • Talk to someone you don’t know
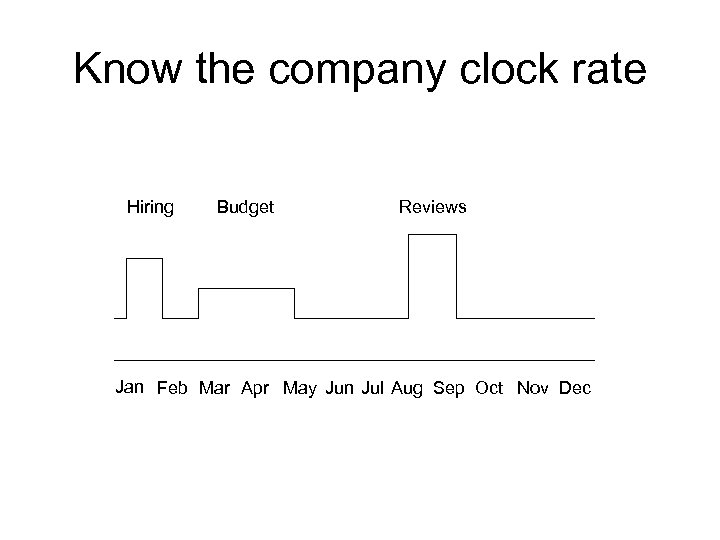
Know the company clock rate Hiring Budget Reviews Jan Feb Mar Apr May Jun Jul Aug Sep Oct Nov Dec
a9550b61b4bff193c52868349352dd74.ppt