8865724e91a73ba875e3ff7ae413b50f.ppt
- Количество слайдов: 21

Guardium - kako obezbijediti sigurnost i kontrolu nad podacima Robert Božič, IBM © 2010 IBM Corporation

Agenda § Zašto sigurnost baza podataka § Šta je to Guardium § Guardium arhitektura § Sažetak © 2010 IBM Corporation
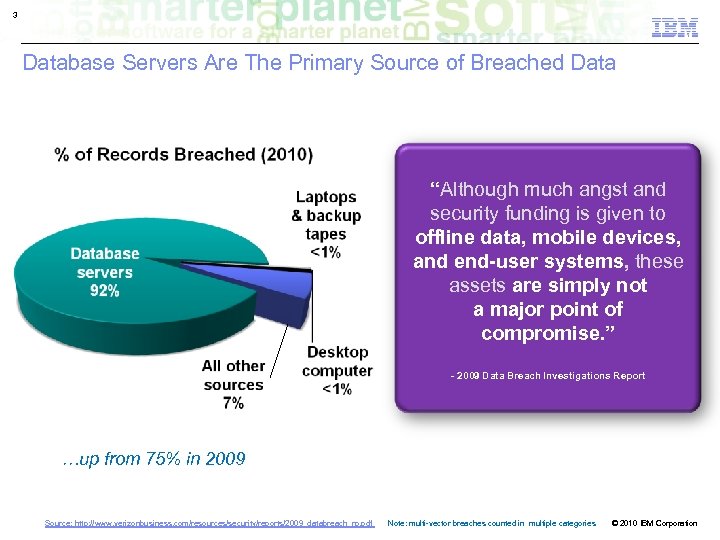
3 Database Servers Are The Primary Source of Breached Data “Although much angst and security funding is given to offline data, mobile devices, and end-user systems, these assets are simply not a major point of compromise. ” - 2009 Data Breach Investigations Report …up from 75% in 2009 Data Breach Report from Verizon Business RISK Team Source: http: //www. verizonbusiness. com/resources/security/reports/2009_databreach_rp. pdf Note: multi-vector breaches counted in multiple categories © 2010 IBM Corporation
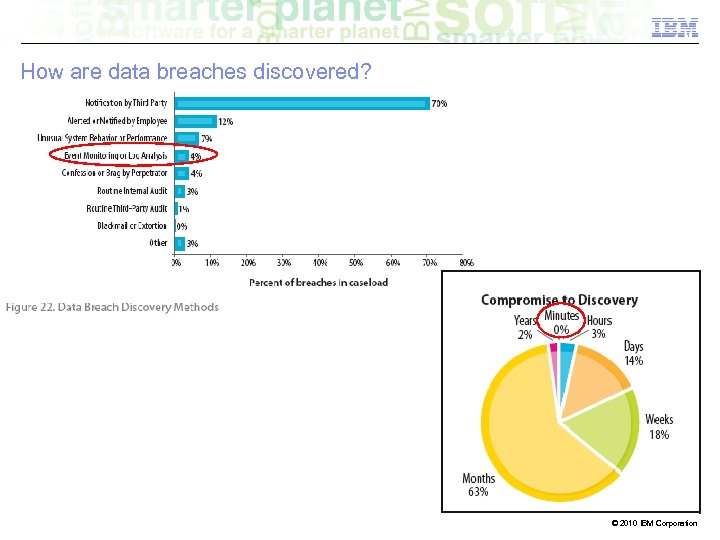
How are data breaches discovered? © 2010 IBM Corporation

Database Activity Monitoring: Three Key Business Drivers 1. Prevent data breaches • Mitigate external and internal threats 2. Ensure data integrity • Prevent unauthorized changes to sensitive data 3. Reduce cost of compliance • Automate and centralize controls Across DBMS platforms and applications Across SOX, PCI, SAS 70, … • Simplify processes © 2010 IBM Corporation
Database Danger from Within § “Organizations overlook the most imminent threat to their databases: authorized users. ” (Dark Reading) § “No one group seems to own database security … This is not a recipe for strong database security” … 63% depend primarily on manual processes. ” (ESG) § Most organizations (62%) cannot prevent super users from reading or tampering with sensitive information … most are unable to even detect such incidents … only 1 out of 4 believe their data assets are securely configured (Independent Oracle User Group). http: //www. darkreading. com/database_security/app-security/show. Article. jhtml? article. ID=220300753 http: //www. guardium. com/index. php/landing/866/ © 2010 IBM Corporation
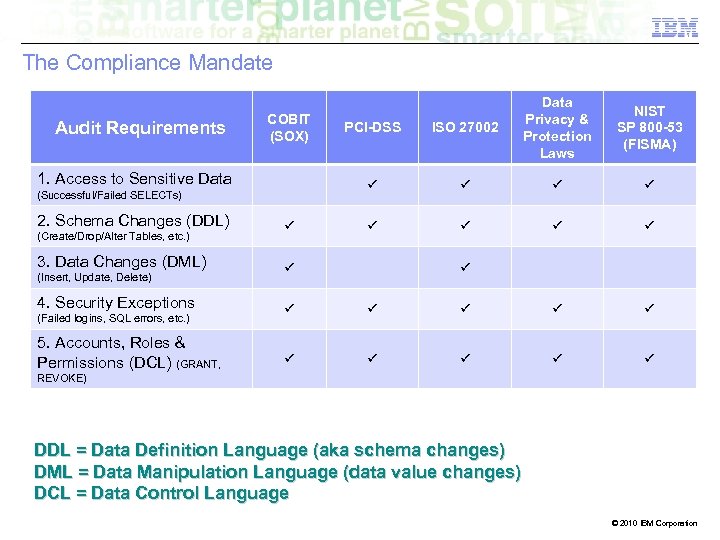
The Compliance Mandate Audit Requirements 1. Access to Sensitive Data (Successful/Failed SELECTs) 2. Schema Changes (DDL) (Create/Drop/Alter Tables, etc. ) 3. Data Changes (DML) (Insert, Update, Delete) 4. Security Exceptions (Failed logins, SQL errors, etc. ) 5. Accounts, Roles & Permissions (DCL) (GRANT, PCI-DSS ISO 27002 COBIT (SOX) Data Privacy & Protection Laws NIST SP 800 -53 (FISMA) REVOKE) DDL = Data Definition Language (aka schema changes) DML = Data Manipulation Language (data value changes) DCL = Data Control Language © 2010 IBM Corporation

Why is database auditing so challenging? 8 © 2010 IBM Corporation

How are most databases audited today? Reliance on native audit logs within DBMS • • • Lacks visibility and granularity • Privileged users difficult to monitor • Tracing the “real user” of application is difficult • Level of audit detail is insufficient Inefficient and costly • Impacts database performance • Large log files provide little value • Different methods for each DB type No segregation of duties • DBAs manage monitoring system • Privileged users can bypass the system • Audit trail is unsecured © 2010 IBM Corporation

Osnovne funkcionalnosti Guardium rješenja § Pračenje aktivnosti u realnom vrjemenu (auditing) § Zabrana internih/internetnih napada i gubljenje podataka § Pračenje promjena na podatkovnoj bazi § Zabrana/pračenje pristupa administratora podatkovnih baza § Identifikacija prevara na aplikacijskom nivou § Provjeravanje novih “patch”-ova na podatkovnim bazama § “Data privacy accelerator” – unaprjed definirane politike, izvještaji, automtsko obavještavanje u realnom vrjemenu © 2010 IBM Corporation
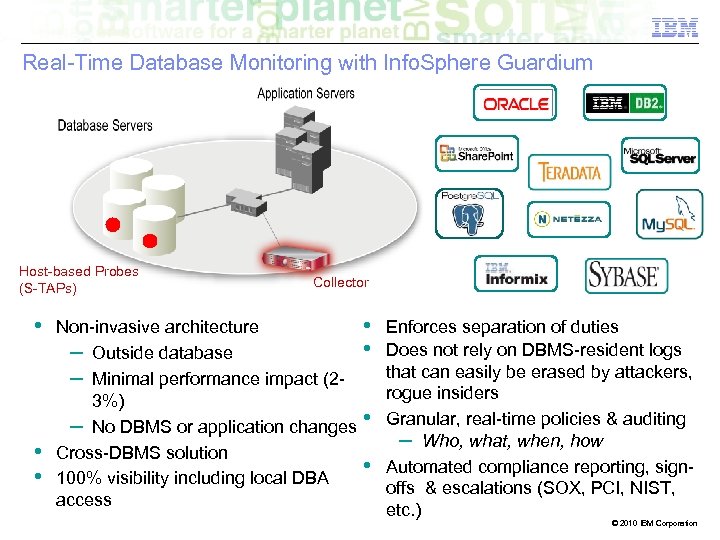
Real-Time Database Monitoring with Info. Sphere Guardium Host-based Probes (S-TAPs) • • • Collector Non-invasive architecture – Outside database – Minimal performance impact (23%) – No DBMS or application changes Cross-DBMS solution 100% visibility including local DBA access • • Enforces separation of duties Does not rely on DBMS-resident logs that can easily be erased by attackers, rogue insiders Granular, real-time policies & auditing – Who, what, when, how Automated compliance reporting, signoffs & escalations (SOX, PCI, NIST, etc. ) © 2010 IBM Corporation
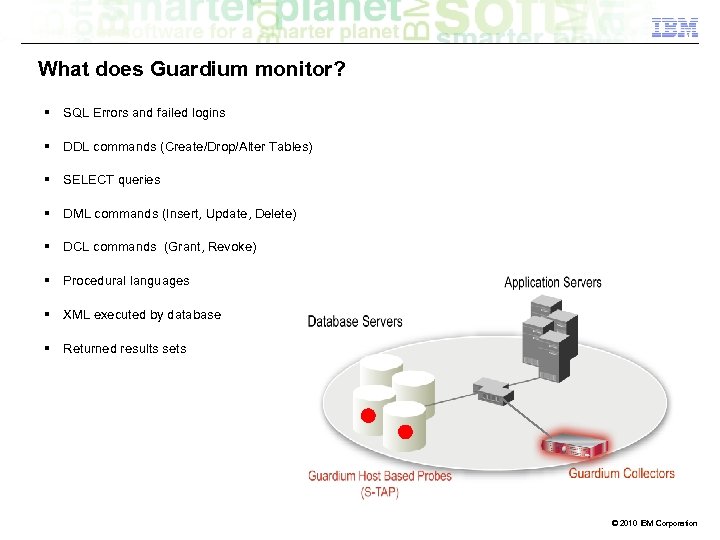
What does Guardium monitor? § SQL Errors and failed logins § DDL commands (Create/Drop/Alter Tables) § SELECT queries § DML commands (Insert, Update, Delete) § DCL commands (Grant, Revoke) § Procedural languages § XML executed by database § Returned results sets 12 © 2010 IBM Corporation
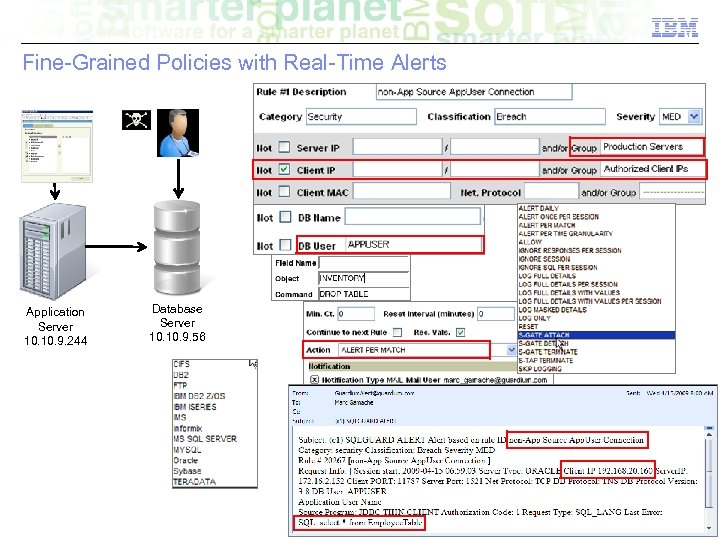
Fine-Grained Policies with Real-Time Alerts Application Server 10. 9. 244 Database Server 10. 9. 56 © 2010 IBM Corporation
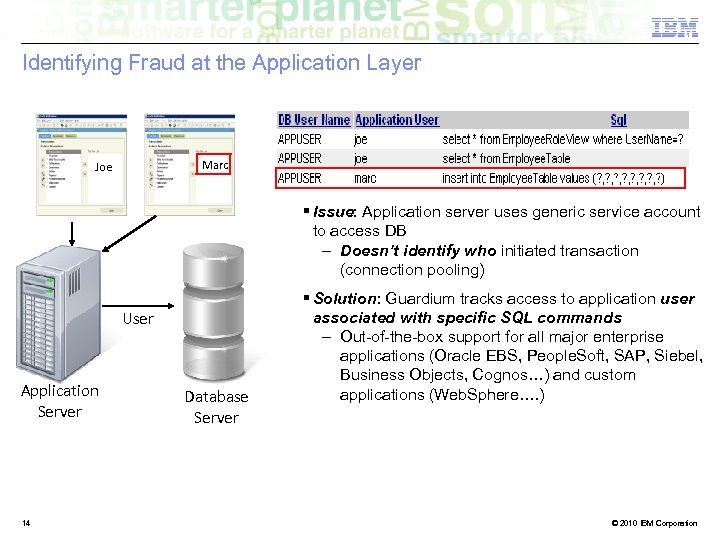
Identifying Fraud at the Application Layer Marc Joe § Issue: Application server uses generic service account to access DB – Doesn’t identify who initiated transaction (connection pooling) User Application Server 14 Database Server § Solution: Guardium tracks access to application user associated with specific SQL commands – Out-of-the-box support for all major enterprise applications (Oracle EBS, People. Soft, SAP, Siebel, Business Objects, Cognos…) and custom applications (Web. Sphere…. ) © 2010 IBM Corporation
Guardium u SAP okolini § § Upotreba za sve SAP module – SAP ERP, SAP CRM, SAP BI, . . . Guardium ima poseban “plug-in” za SAP © 2010 IBM Corporation
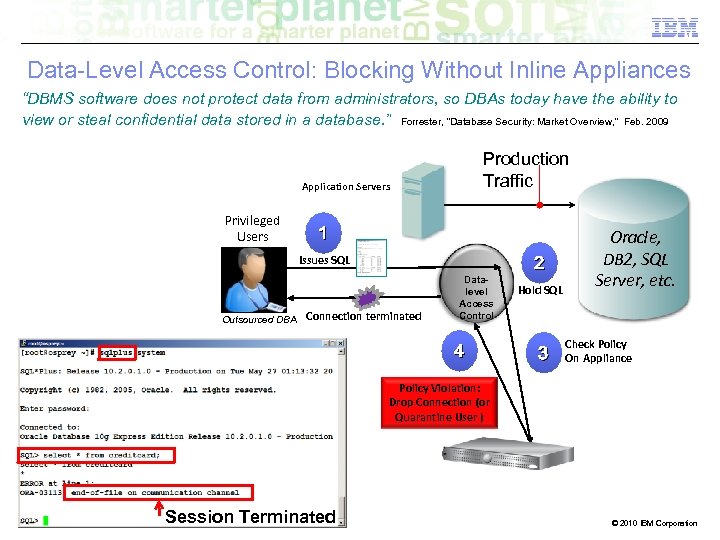
Data-Level Access Control: Blocking Without Inline Appliances “DBMS software does not protect data from administrators, so DBAs today have the ability to view or steal confidential data stored in a database. ” Forrester, “Database Security: Market Overview, ” Feb. 2009 Production Traffic Application Servers Privileged Users 1 Issues SQL Outsourced DBA Connection terminated Datalevel Access Control 4 2 Hold SQL 3 Oracle, DB 2, SQL Server, etc. Check Policy On Appliance Policy Violation: Drop Connection (or Quarantine User ) Session Terminated © 2010 IBM Corporation
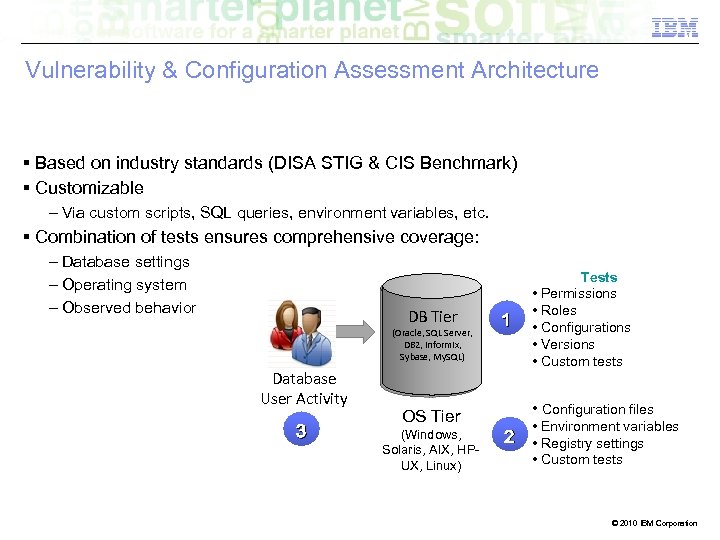
Vulnerability & Configuration Assessment Architecture § Based on industry standards (DISA STIG & CIS Benchmark) § Customizable – Via custom scripts, SQL queries, environment variables, etc. § Combination of tests ensures comprehensive coverage: – Database settings – Operating system – Observed behavior DB Tier (Oracle, SQL Server, DB 2, Informix, Sybase, My. SQL) Database User Activity 3 OS Tier (Windows, Solaris, AIX, HPUX, Linux) 1 Tests • Permissions • Roles • Configurations • Versions • Custom tests • Configuration files • Environment variables 2 • Registry settings • Custom tests © 2010 IBM Corporation
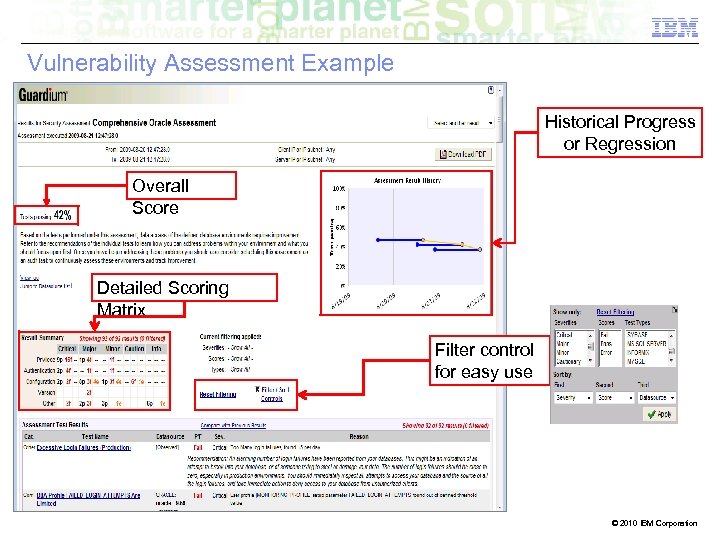
Vulnerability Assessment Example Historical Progress or Regression Overall Score Detailed Scoring Matrix Filter control for easy use © 2010 IBM Corporation
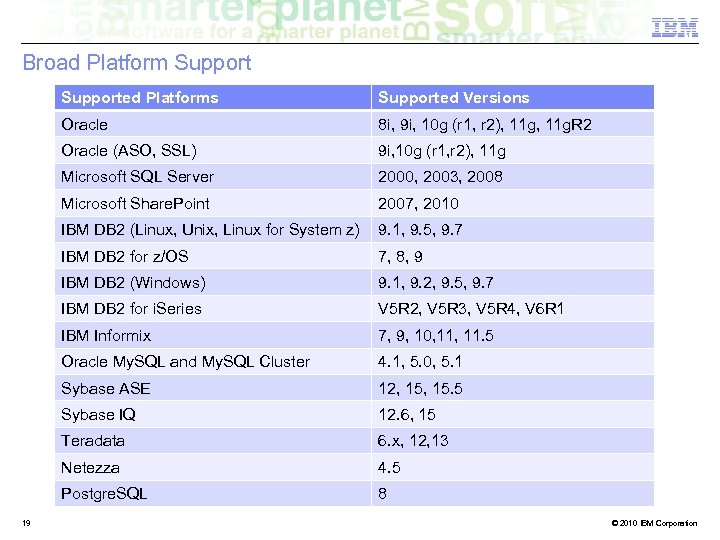
Broad Platform Supported Platforms Oracle 8 i, 9 i, 10 g (r 1, r 2), 11 g. R 2 Oracle (ASO, SSL) 9 i, 10 g (r 1, r 2), 11 g Microsoft SQL Server 2000, 2003, 2008 Microsoft Share. Point 2007, 2010 IBM DB 2 (Linux, Unix, Linux for System z) 9. 1, 9. 5, 9. 7 IBM DB 2 for z/OS 7, 8, 9 IBM DB 2 (Windows) 9. 1, 9. 2, 9. 5, 9. 7 IBM DB 2 for i. Series V 5 R 2, V 5 R 3, V 5 R 4, V 6 R 1 IBM Informix 7, 9, 10, 11. 5 Oracle My. SQL and My. SQL Cluster 4. 1, 5. 0, 5. 1 Sybase ASE 12, 15. 5 Sybase IQ 12. 6, 15 Teradata 6. x, 12, 13 Netezza 4. 5 Postgre. SQL 19 Supported Versions 8 © 2010 IBM Corporation
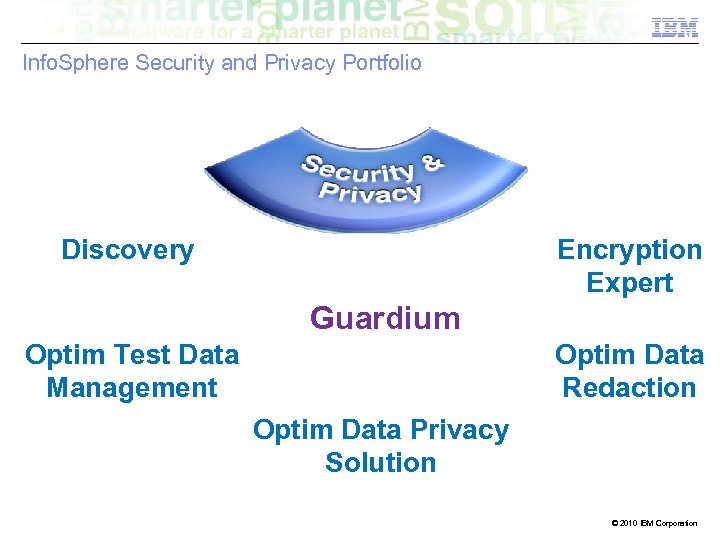
Info. Sphere Security and Privacy Portfolio Discovery Encryption Expert Guardium Optim Test Data Management Optim Data Redaction Optim Data Privacy Solution © 2010 IBM Corporation

Summary • Risks related to data privacy breaches have never been greater • Fine-grained monitoring of database access is the best way to protect from data being compromised • A unified and consistent approach across the database infrastructure will save time, money, and increase security • Guardium continues to be the market leader because of comprehensive functionality and ease of implementation © 2010 IBM Corporation
8865724e91a73ba875e3ff7ae413b50f.ppt