4c18c63a01763217a51fa3be68e6f2ca.ppt
- Количество слайдов: 34
 GT 3 Security Features Sam Meder
GT 3 Security Features Sam Meder
 Assumptions l Familiarity with PKI concepts Certificates (CA, EEC, Proxy) u Delegation u l Some knowledge of Web Services Security Standards: WS-Security u XML-Signature u XML-Encryption u l Some knowledge of GSSAPI
Assumptions l Familiarity with PKI concepts Certificates (CA, EEC, Proxy) u Delegation u l Some knowledge of Web Services Security Standards: WS-Security u XML-Signature u XML-Encryption u l Some knowledge of GSSAPI
 GT Security Overview l GT 3. 0 Authentication Mechanisms X 509/SSL/GSSAPI based (GSI Secure Conversation) u X 509/public key based (GSI Secure Message) u l GT 3. 0 Authorization Mechanisms Gridmap u Host u Self u None u
GT Security Overview l GT 3. 0 Authentication Mechanisms X 509/SSL/GSSAPI based (GSI Secure Conversation) u X 509/public key based (GSI Secure Message) u l GT 3. 0 Authorization Mechanisms Gridmap u Host u Self u None u
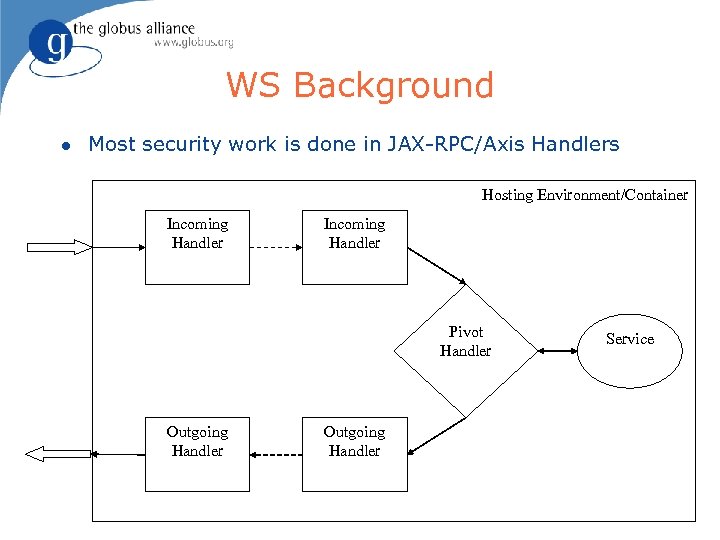 WS Background l Most security work is done in JAX-RPC/Axis Handlers Hosting Environment/Container Incoming Handler Pivot Handler Outgoing Handler Service
WS Background l Most security work is done in JAX-RPC/Axis Handlers Hosting Environment/Container Incoming Handler Pivot Handler Outgoing Handler Service
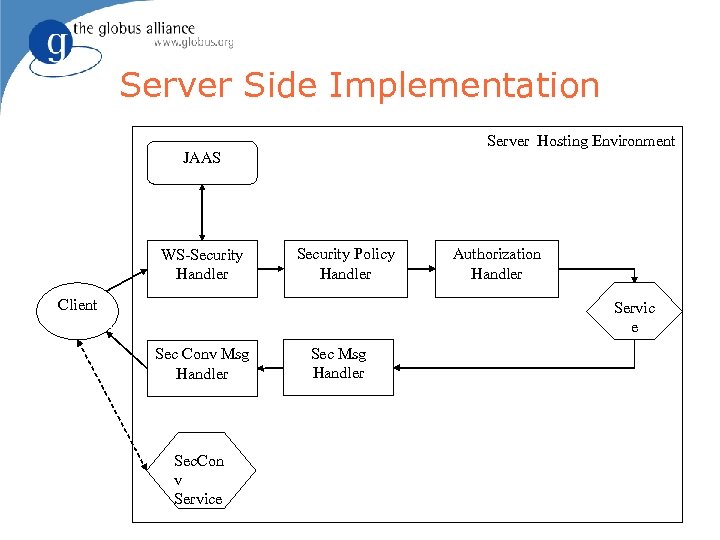 Server Side Implementation Server Hosting Environment JAAS WS-Security Handler Security Policy Handler Client Authorization Handler Servic e Sec Conv Msg Handler Sec. Con v Service Sec Msg Handler
Server Side Implementation Server Hosting Environment JAAS WS-Security Handler Security Policy Handler Client Authorization Handler Servic e Sec Conv Msg Handler Sec. Con v Service Sec Msg Handler
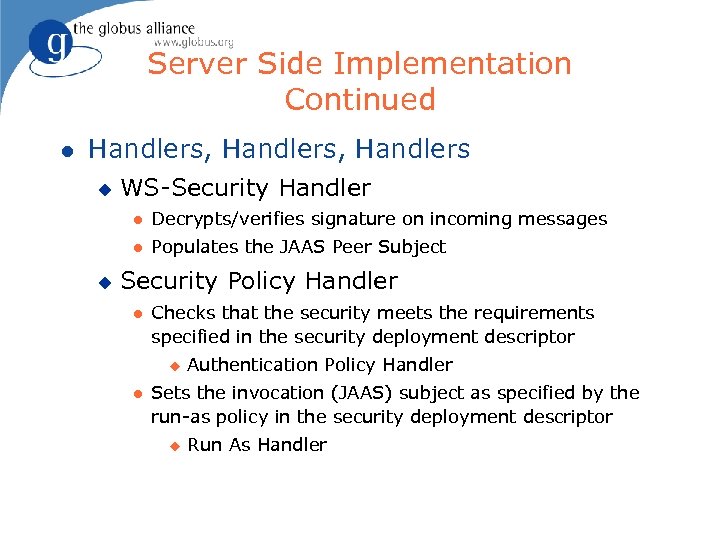 Server Side Implementation Continued l Handlers, Handlers u WS-Security Handler l l u Decrypts/verifies signature on incoming messages Populates the JAAS Peer Subject Security Policy Handler l Checks that the security meets the requirements specified in the security deployment descriptor u l Authentication Policy Handler Sets the invocation (JAAS) subject as specified by the run-as policy in the security deployment descriptor u Run As Handler
Server Side Implementation Continued l Handlers, Handlers u WS-Security Handler l l u Decrypts/verifies signature on incoming messages Populates the JAAS Peer Subject Security Policy Handler l Checks that the security meets the requirements specified in the security deployment descriptor u l Authentication Policy Handler Sets the invocation (JAAS) subject as specified by the run-as policy in the security deployment descriptor u Run As Handler
 Server Side Implementation Continued l Even more handlers u Authorization Handler l u Credential Refresh Handler l u Refreshes credential in invocation subject based on delegated credential Authentication Service Handler l u Authorizes incoming messages – more later Redirects messages to Secure Conversation Service Secure Message Handler (aka X 509 Sign Handler) l Signs GSI Secure Message secured communications
Server Side Implementation Continued l Even more handlers u Authorization Handler l u Credential Refresh Handler l u Refreshes credential in invocation subject based on delegated credential Authentication Service Handler l u Authorizes incoming messages – more later Redirects messages to Secure Conversation Service Secure Message Handler (aka X 509 Sign Handler) l Signs GSI Secure Message secured communications
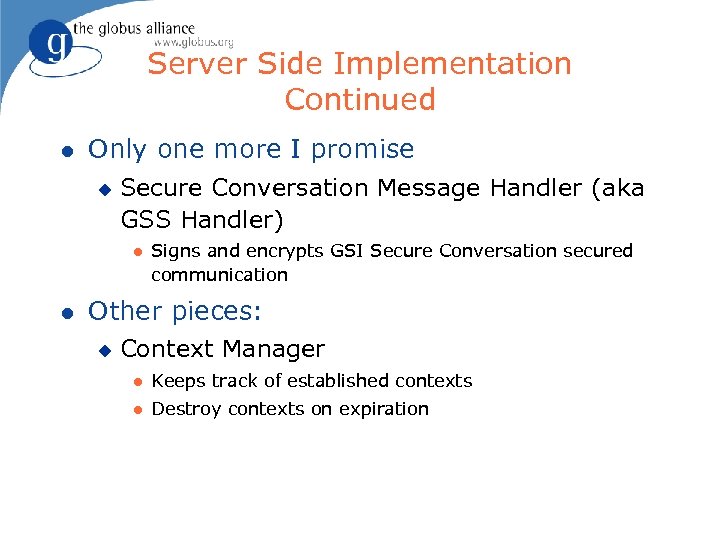 Server Side Implementation Continued l Only one more I promise u Secure Conversation Message Handler (aka GSS Handler) l l Signs and encrypts GSI Secure Conversation secured communication Other pieces: u Context Manager l Keeps track of established contexts l Destroy contexts on expiration
Server Side Implementation Continued l Only one more I promise u Secure Conversation Message Handler (aka GSS Handler) l l Signs and encrypts GSI Secure Conversation secured communication Other pieces: u Context Manager l Keeps track of established contexts l Destroy contexts on expiration
 Server Side Programming l Declarative Model: u u Security properties (for incoming communication) are specified in a deployment descriptor Wrapper handler(s) reads descriptor and populate security parameters Handlers act on security parameters Generally requires no explicit security calls by service implementer
Server Side Programming l Declarative Model: u u Security properties (for incoming communication) are specified in a deployment descriptor Wrapper handler(s) reads descriptor and populate security parameters Handlers act on security parameters Generally requires no explicit security calls by service implementer
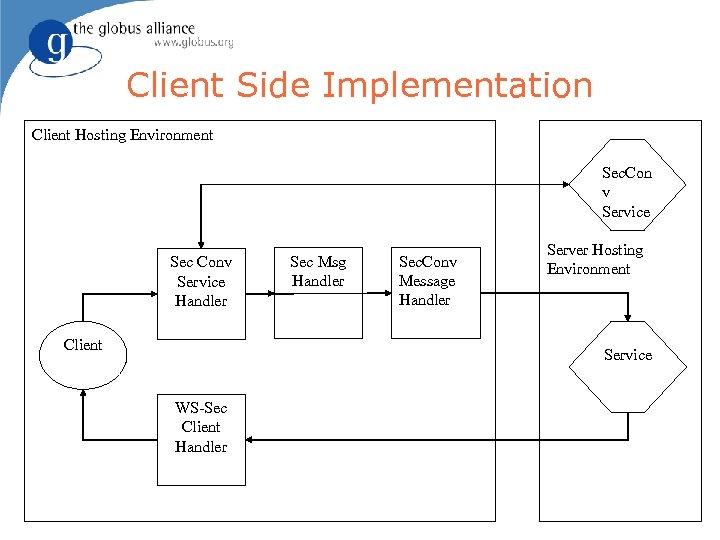 Client Side Implementation Client Hosting Environment Sec. Con v Service Sec Conv Service Handler Client Sec Msg Handler Sec. Conv Message Handler Server Hosting Environment Service WS-Sec Client Handler
Client Side Implementation Client Hosting Environment Sec. Con v Service Sec Conv Service Handler Client Sec Msg Handler Sec. Conv Message Handler Server Hosting Environment Service WS-Sec Client Handler
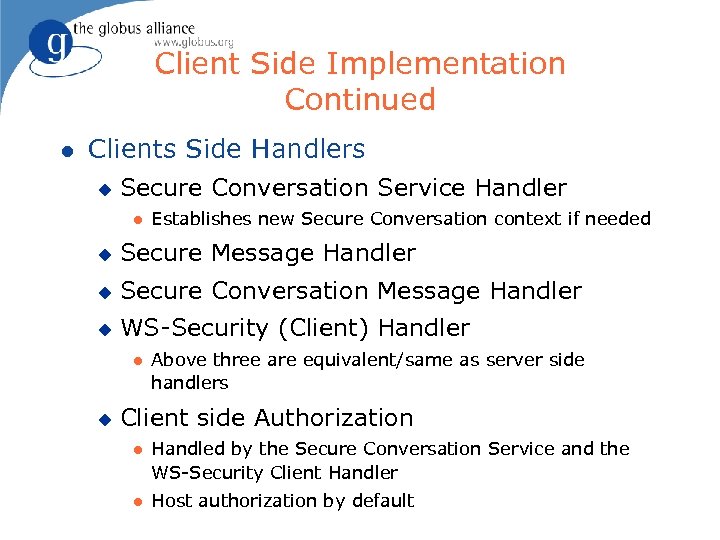 Client Side Implementation Continued l Clients Side Handlers u Secure Conversation Service Handler l Establishes new Secure Conversation context if needed u Secure Message Handler u Secure Conversation Message Handler u WS-Security (Client) Handler l u Above three are equivalent/same as server side handlers Client side Authorization l Handled by the Secure Conversation Service and the WS-Security Client Handler l Host authorization by default
Client Side Implementation Continued l Clients Side Handlers u Secure Conversation Service Handler l Establishes new Secure Conversation context if needed u Secure Message Handler u Secure Conversation Message Handler u WS-Security (Client) Handler l u Above three are equivalent/same as server side handlers Client side Authorization l Handled by the Secure Conversation Service and the WS-Security Client Handler l Host authorization by default
 Client Side Programming l Clients need to set security properties explicitly – programmatic model u l Server/Service acting as client Handlers pick up security properties and act accordingly
Client Side Programming l Clients need to set security properties explicitly – programmatic model u l Server/Service acting as client Handlers pick up security properties and act accordingly
 JAAS l Java Authentication & Authorization Service l Currently (3. 0) only used for managing/storing credentials u JAAS Subject object l l l Authorization checks Outgoing Connections Different Subject Types: u u Container u l System Peer Invocation Subject
JAAS l Java Authentication & Authorization Service l Currently (3. 0) only used for managing/storing credentials u JAAS Subject object l l l Authorization checks Outgoing Connections Different Subject Types: u u Container u l System Peer Invocation Subject
 GRIM (Grid Resource Identity Mapper) l Allows GT 3 components to run without special privileges l Setuid to user with access to (host) credentials u u Reads credentials Creates GRIM Proxy from credentials and configuration information
GRIM (Grid Resource Identity Mapper) l Allows GT 3 components to run without special privileges l Setuid to user with access to (host) credentials u u Reads credentials Creates GRIM Proxy from credentials and configuration information
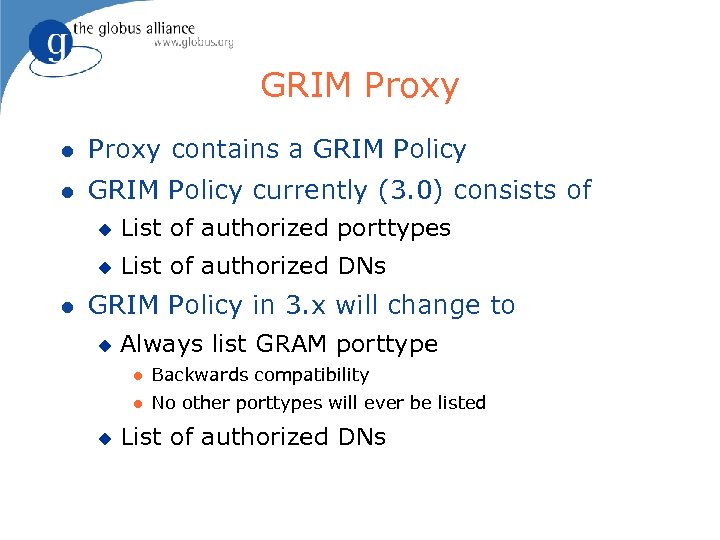 GRIM Proxy l Proxy contains a GRIM Policy l GRIM Policy currently (3. 0) consists of u u l List of authorized porttypes List of authorized DNs GRIM Policy in 3. x will change to u Always list GRAM porttype l l u Backwards compatibility No other porttypes will ever be listed List of authorized DNs
GRIM Proxy l Proxy contains a GRIM Policy l GRIM Policy currently (3. 0) consists of u u l List of authorized porttypes List of authorized DNs GRIM Policy in 3. x will change to u Always list GRAM porttype l l u Backwards compatibility No other porttypes will ever be listed List of authorized DNs
 GRIM Wish List l Make GRIM produce independent proxy l Proxy should contain non-critical extension l Extension should contain SAML assertion on allowed DNs l Does not require special handling of proxy in cases where you don’t care about the extension
GRIM Wish List l Make GRIM produce independent proxy l Proxy should contain non-critical extension l Extension should contain SAML assertion on allowed DNs l Does not require special handling of proxy in cases where you don’t care about the extension
 Authorization – Cooking your own l Replace the Authorization Handler u Check out the current one u Write your own u Build/Compile it u Replace existing handler in serverconfig. wsdd and make sure that handler is available in your CLASSPATH
Authorization – Cooking your own l Replace the Authorization Handler u Check out the current one u Write your own u Build/Compile it u Replace existing handler in serverconfig. wsdd and make sure that handler is available in your CLASSPATH
 public class Authorization. Handler extends Basic. Handler {. . . public void invoke(Message. Context message. Context) throws Axis. Fault { Subject subject = (Subject) message. Context. get. Property(Constants. PEER_SUBJECT); Service. Properties props = Descriptor. Handler. get. Service(message. Context); Service. Authorization auth = null; String tmp = (String)props. get. Property(Authorization. AUTHORIZATION); if (tmp == null) { auth = Default. Authorization. get. Instance(); } else if (tmp. equals. Ignore. Case("none")) { auth = No. Authorization. get. Instance(); } else if (tmp. equals. Ignore. Case("self")) { auth = Self. Authorization. get. Instance(); } else if (tmp. equals. Ignore. Case("gridmap")) { auth = Grid. Map. Authorization. get. Instance(); } else { Exception e = new Authorization. Exception( i 18 n. get. Message("bad. Auth. Method", new Object[] { tmp})); throw Axis. Fault. make. Fault(e); } } } try { authorize(subject, props, message. Context); } catch (Authorization. Exception e) { throw Axis. Fault. make. Fault(e); }
public class Authorization. Handler extends Basic. Handler {. . . public void invoke(Message. Context message. Context) throws Axis. Fault { Subject subject = (Subject) message. Context. get. Property(Constants. PEER_SUBJECT); Service. Properties props = Descriptor. Handler. get. Service(message. Context); Service. Authorization auth = null; String tmp = (String)props. get. Property(Authorization. AUTHORIZATION); if (tmp == null) { auth = Default. Authorization. get. Instance(); } else if (tmp. equals. Ignore. Case("none")) { auth = No. Authorization. get. Instance(); } else if (tmp. equals. Ignore. Case("self")) { auth = Self. Authorization. get. Instance(); } else if (tmp. equals. Ignore. Case("gridmap")) { auth = Grid. Map. Authorization. get. Instance(); } else { Exception e = new Authorization. Exception( i 18 n. get. Message("bad. Auth. Method", new Object[] { tmp})); throw Axis. Fault. make. Fault(e); } } } try { authorize(subject, props, message. Context); } catch (Authorization. Exception e) { throw Axis. Fault. make. Fault(e); }
 GSI Secure Conversation l Based on GSSAPI, WS-Security, XML-Signature and XML-Encryption l Session based l Support for delegation u l Automatic refresh of delegated proxy on redelegation Uses our SSL based GSSAPI mechanism u Protocol is driven by gss_init/accept_sec_context u get_mic/verify_mic and wrap/unwrap
GSI Secure Conversation l Based on GSSAPI, WS-Security, XML-Signature and XML-Encryption l Session based l Support for delegation u l Automatic refresh of delegated proxy on redelegation Uses our SSL based GSSAPI mechanism u Protocol is driven by gss_init/accept_sec_context u get_mic/verify_mic and wrap/unwrap
 Secure Conversation Messages Recap l Context establishment messages contain: u Base 64 encoded GSS token u Context Identifier u Continue Needed indicator u Mechanism OID – initial message only
Secure Conversation Messages Recap l Context establishment messages contain: u Base 64 encoded GSS token u Context Identifier u Continue Needed indicator u Mechanism OID – initial message only
 GSI Secure Conversation & XML-Encryption
GSI Secure Conversation & XML-Encryption
 GSI Secure Conversation & XML-Signature
GSI Secure Conversation & XML-Signature
 Performance l Needs to be improved u Currently about 10 x slower than insecure u Initialization is very slow l Apache XML security libraries add large overhead (3 x/message processed) l JSR 105/106 are moving along u Apache will adopt u We don’t want to make major changes now l Concentrate on low cost high impact improvements l Move some interactions to Secure Message u Fewer roundtrips
Performance l Needs to be improved u Currently about 10 x slower than insecure u Initialization is very slow l Apache XML security libraries add large overhead (3 x/message processed) l JSR 105/106 are moving along u Apache will adopt u We don’t want to make major changes now l Concentrate on low cost high impact improvements l Move some interactions to Secure Message u Fewer roundtrips
 New Secure Conversation Features (3. x) l Support for anonymous authentication l Support for specifying context lifetime l Some performance improvements
New Secure Conversation Features (3. x) l Support for anonymous authentication l Support for specifying context lifetime l Some performance improvements
 GSI Secure Message l Supports integrity protection with X 509 certificates u l l Support for proxy certificates Can be combined with GSI Secure Conversation Not fully featured No replay attack prevention u No encryption support u l Missing features slated for 3. x
GSI Secure Message l Supports integrity protection with X 509 certificates u l l Support for proxy certificates Can be combined with GSI Secure Conversation Not fully featured No replay attack prevention u No encryption support u l Missing features slated for 3. x
 GSI Secure Message Example
GSI Secure Message Example
 Username/Password l Not clear which release this will show up in l Potential mechanisms: u WS-Security Username/Password token l u Should be used in combination with anonymous Secure Conversation More advanced/secure Username/Password schemes - Auth. A
Username/Password l Not clear which release this will show up in l Potential mechanisms: u WS-Security Username/Password token l u Should be used in combination with anonymous Secure Conversation More advanced/secure Username/Password schemes - Auth. A
 The Auth. A Protocol l l Client has password Server has secret = f(servername|username|password) u f is a secure one way function u l l Client & Server created Session Key using a encrypted Diffie-Hellman exchange Client & Server authenticate each other Security Proof Exists Details at http: //grouper. ieee. org/groups/1363/passwd. PK/ contributions/autha. pdf
The Auth. A Protocol l l Client has password Server has secret = f(servername|username|password) u f is a secure one way function u l l Client & Server created Session Key using a encrypted Diffie-Hellman exchange Client & Server authenticate each other Security Proof Exists Details at http: //grouper. ieee. org/groups/1363/passwd. PK/ contributions/autha. pdf
 Discussion l WS-Resource Impact l One time passwords l Smart Card support l Kerberos l Other authentication mechanisms? l …
Discussion l WS-Resource Impact l One time passwords l Smart Card support l Kerberos l Other authentication mechanisms? l …


