242ad1a6ce0380957899d56122553e7a.ppt
- Количество слайдов: 23
 GSI – Grid Security Infrastructure and the EU Data. Grid Authentication Infrastructure For the EDG CACG: David Groep
GSI – Grid Security Infrastructure and the EU Data. Grid Authentication Infrastructure For the EDG CACG: David Groep
 Outline u The Grid in one line u The Grid Security Infrastructure (from Globus) u EU Data. Grid (EDG) u The EDG CA Coordination Group (CACG) David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 2
Outline u The Grid in one line u The Grid Security Infrastructure (from Globus) u EU Data. Grid (EDG) u The EDG CA Coordination Group (CACG) David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 2
 The Grid: coordinated resource sharing and problem solving in dynamic, multi institutional virtual organizations Carl Kesselman, Ian Foster, The Anatomy of the Grid u Extension of “meta-computing” to ubiquitous resources u Pioneered by the I-WAY, GUSTO and the Globus Project u Vision: getting resources like you get electricity nowadays David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 3
The Grid: coordinated resource sharing and problem solving in dynamic, multi institutional virtual organizations Carl Kesselman, Ian Foster, The Anatomy of the Grid u Extension of “meta-computing” to ubiquitous resources u Pioneered by the I-WAY, GUSTO and the Globus Project u Vision: getting resources like you get electricity nowadays David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 3
 A Quick Refresher Grid Security Infrastructure (GSI) = X. 509 (PKI certificate format)* + proxy certificates (single sign-on & delegation) + TLS/SSL (authentication & msg protection)* + delegation protocol (remote delegation) + GSS-API (standard API)* + GSS-API Extensions (better Grid support) * = Existing IETF standards • Others are GGF & IETF drafts David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 4
A Quick Refresher Grid Security Infrastructure (GSI) = X. 509 (PKI certificate format)* + proxy certificates (single sign-on & delegation) + TLS/SSL (authentication & msg protection)* + delegation protocol (remote delegation) + GSS-API (standard API)* + GSS-API Extensions (better Grid support) * = Existing IETF standards • Others are GGF & IETF drafts David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 4
 X. 509 Proxy Certificates Work u Defines how a short term, restricted credential can be created from a normal, long-term X. 509 credential n n A “proxy certificate” is a special type of X. 509 certificate that is signed by the normal end entity cert, or by another proxy Supports single sign-on & delegation through “impersonation” u ANL, ISI, LBNL David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 5
X. 509 Proxy Certificates Work u Defines how a short term, restricted credential can be created from a normal, long-term X. 509 credential n n A “proxy certificate” is a special type of X. 509 certificate that is signed by the normal end entity cert, or by another proxy Supports single sign-on & delegation through “impersonation” u ANL, ISI, LBNL David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 5
 Restricted Proxies u Q: How to restrict rights of delegated proxy to a subset of those associated with the issuer? u A: Embed restriction policy in proxy cert n Policy is evaluated by resource upon proxy use n Reduces rights available to the proxy to a subset of those held by the user u But n how to avoid policy language wars? Proxy cert just contains a container for a policy specification, without defining the language s n Container = OID + blob Can evolve policy languages over time David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 6
Restricted Proxies u Q: How to restrict rights of delegated proxy to a subset of those associated with the issuer? u A: Embed restriction policy in proxy cert n Policy is evaluated by resource upon proxy use n Reduces rights available to the proxy to a subset of those held by the user u But n how to avoid policy language wars? Proxy cert just contains a container for a policy specification, without defining the language s n Container = OID + blob Can evolve policy languages over time David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 6
 Delegation Tracing u Often want to know through what entities a proxy certificate has been delegated n Audit (retrace footsteps) n Authorization (deny from bad entities) u Solved by adding information to the signed proxy certificate about each entity to which a proxy is delegated. n Does NOT guarantee proper use of proxy n Just tells you which entities were purposely involved in a delegation David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 7
Delegation Tracing u Often want to know through what entities a proxy certificate has been delegated n Audit (retrace footsteps) n Authorization (deny from bad entities) u Solved by adding information to the signed proxy certificate about each entity to which a proxy is delegated. n Does NOT guarantee proper use of proxy n Just tells you which entities were purposely involved in a delegation David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 7
 Proxy Certificate Standards Work u “Internet n draft-ietf-pkix-proxy-00. txt s n Public Key Infrastructure X. 509 Proxy Certificate Profile” Draft being considered by IETF PKIX working group, and by GGF GSI working group Defines proxy certificate format, including restricted rights and delegation tracing u LBNL student is implementing into Open. SSL u Demonstrated CAS demo a prototype of restricted proxies at HPDC as part of David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 8
Proxy Certificate Standards Work u “Internet n draft-ietf-pkix-proxy-00. txt s n Public Key Infrastructure X. 509 Proxy Certificate Profile” Draft being considered by IETF PKIX working group, and by GGF GSI working group Defines proxy certificate format, including restricted rights and delegation tracing u LBNL student is implementing into Open. SSL u Demonstrated CAS demo a prototype of restricted proxies at HPDC as part of David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 8
 Delegation Protocol Work u “TLS n draft-ietf-tls-delegation-01. txt s n Delegation Protocol” Draft being considered by IETF TLS working group, and by GGF GSI working group Defines how to remotely delegate an X. 509 Proxy Certificate using extensions to the TLS (SSL) protocol David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 9
Delegation Protocol Work u “TLS n draft-ietf-tls-delegation-01. txt s n Delegation Protocol” Draft being considered by IETF TLS working group, and by GGF GSI working group Defines how to remotely delegate an X. 509 Proxy Certificate using extensions to the TLS (SSL) protocol David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 9
 Community Authorization Service u Question: How does a large community grant its users access to a large set of resources? n u Should minimize burden on both the users and resource providers Solution: Community Authorization Service (CAS) n Community negotiates access to resources n Resource outsources fine-grain authorization to CAS n Resource only needs to know about “CAS user” credential s n CAS handles user registration, group membership… User who wants access to resource asks CAS for a capability credential s Restricted proxy of the “CAS user” credential, checked by resource David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 10
Community Authorization Service u Question: How does a large community grant its users access to a large set of resources? n u Should minimize burden on both the users and resource providers Solution: Community Authorization Service (CAS) n Community negotiates access to resources n Resource outsources fine-grain authorization to CAS n Resource only needs to know about “CAS user” credential s n CAS handles user registration, group membership… User who wants access to resource asks CAS for a capability credential s Restricted proxy of the “CAS user” credential, checked by resource David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 10
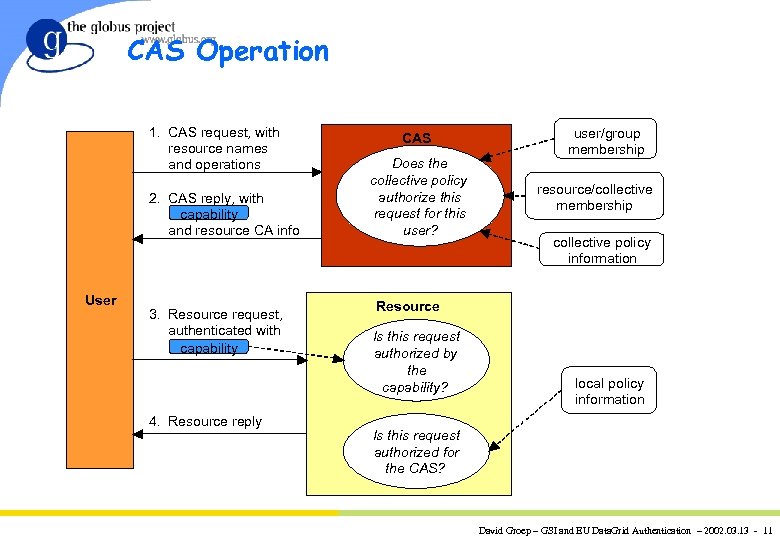 CAS Operation 1. CAS request, with resource names and operations 2. CAS reply, with capability and resource CA info User 3. Resource request, authenticated with capability 4. Resource reply CAS Does the collective policy authorize this request for this user? user/group membership resource/collective membership collective policy information Resource Is this request authorized by the capability? local policy information Is this request authorized for the CAS? David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 11
CAS Operation 1. CAS request, with resource names and operations 2. CAS reply, with capability and resource CA info User 3. Resource request, authenticated with capability 4. Resource reply CAS Does the collective policy authorize this request for this user? user/group membership resource/collective membership collective policy information Resource Is this request authorized by the capability? local policy information Is this request authorized for the CAS? David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 11
 Community Authorization Service u CAS provides user community with information needed to authenticate resources n Sent with capability credential, used on connection with resource n Resource identity (DN), CA u This allows new resources/users (and their CAs) to be made available to a community through the CAS without action on the other user’s/resource’s part David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 12
Community Authorization Service u CAS provides user community with information needed to authenticate resources n Sent with capability credential, used on connection with resource n Resource identity (DN), CA u This allows new resources/users (and their CAs) to be made available to a community through the CAS without action on the other user’s/resource’s part David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 12
 The EU Data. Grid (EDG) Project u Data. Grid: generic Grid middleware and test bed for n High Energy Physics n Earth Observation and ozone modelling n Bio-informatics & bio-medicine u Middleware components (on top of Globus): n scheduling and accounting n data replication and management n monitoring n data storage n fabric and farm management David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 13
The EU Data. Grid (EDG) Project u Data. Grid: generic Grid middleware and test bed for n High Energy Physics n Earth Observation and ozone modelling n Bio-informatics & bio-medicine u Middleware components (on top of Globus): n scheduling and accounting n data replication and management n monitoring n data storage n fabric and farm management David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 13
 The EDG Test Bed u Started end 2000 – beginning 2001 with “Test Bed 0” n Globus installations in several countries n Implement core infrastructure to get this to work u Test Bed 1, deployed Nov 2001, successful demo in March 1 st u Continuous upgrades till December 2003 David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 15
The EDG Test Bed u Started end 2000 – beginning 2001 with “Test Bed 0” n Globus installations in several countries n Implement core infrastructure to get this to work u Test Bed 1, deployed Nov 2001, successful demo in March 1 st u Continuous upgrades till December 2003 David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 15
 The first Grid CA’s u The Globus Project has been running a “worthless” CA n authentication based on non-bouncing e-mail address only n not accepted by many of the participating sites u For EDG “production” test bed need for just a bit stronger auth n grass-roots effort by volunteers in various countries n policies and practices all different n various degrees of subject authentication n a (very) few CA’s are still in need of a written policy David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 16
The first Grid CA’s u The Globus Project has been running a “worthless” CA n authentication based on non-bouncing e-mail address only n not accepted by many of the participating sites u For EDG “production” test bed need for just a bit stronger auth n grass-roots effort by volunteers in various countries n policies and practices all different n various degrees of subject authentication n a (very) few CA’s are still in need of a written policy David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 16
 Current EDG Certification Authorities u CERN (HEP-only, Grid-only) u Do. ESG u Czech Republic (CESNET) u Germany u France u Spain (FZK, Grid-only) (CNRS) (IFCA, HEP-only, Grid-only) u Netherlands u Italy CA (ESnet, Grid-only) (NIKHEF/Dutch. Grid, Grid-only) (INFN, HEP-only, Grid-only) u Portugal u Nordic u Russia (LIP, HEP-only, Grid-only) Countries (NBI, Grid-only) (Moscow State Uni, HEP-only, Grid-only) u Grid. PP/UKHEP some EDG CA stats: u 11 CAs u 1 year in operation u~ 1000 certs issued u potential community: 10000– 40000–? ? ? (CLRC/RAL, Grid-only) David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 17
Current EDG Certification Authorities u CERN (HEP-only, Grid-only) u Do. ESG u Czech Republic (CESNET) u Germany u France u Spain (FZK, Grid-only) (CNRS) (IFCA, HEP-only, Grid-only) u Netherlands u Italy CA (ESnet, Grid-only) (NIKHEF/Dutch. Grid, Grid-only) (INFN, HEP-only, Grid-only) u Portugal u Nordic u Russia (LIP, HEP-only, Grid-only) Countries (NBI, Grid-only) (Moscow State Uni, HEP-only, Grid-only) u Grid. PP/UKHEP some EDG CA stats: u 11 CAs u 1 year in operation u~ 1000 certs issued u potential community: 10000– 40000–? ? ? (CLRC/RAL, Grid-only) David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 17
 EDG CA “Minimum Requirements” (1) u Still largely defined by common practice … “An acceptable procedure for confirming the identity of the requestor […] e. g. by personal contact or some other rigorous method” n One CA per country → basic trust in personal authentication by CA/RA n Subject name includes full given name and affiliation n Specific nameforms per CA (but all different) n Most use personal voice recognition of known persons, or check official ID papers via an RA-to-CA communications by integrity-protected e-mail n Affiliation usually checked by looking in “public” directories n “Host certificates” introduced by a pre-certified administrator David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 18
EDG CA “Minimum Requirements” (1) u Still largely defined by common practice … “An acceptable procedure for confirming the identity of the requestor […] e. g. by personal contact or some other rigorous method” n One CA per country → basic trust in personal authentication by CA/RA n Subject name includes full given name and affiliation n Specific nameforms per CA (but all different) n Most use personal voice recognition of known persons, or check official ID papers via an RA-to-CA communications by integrity-protected e-mail n Affiliation usually checked by looking in “public” directories n “Host certificates” introduced by a pre-certified administrator David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 18
 EDG CA “Minimum Requirements” (2) u Technical controls better specified n machine with CA private key not connected to any network n CA RSA key length 2048 bits → lifetime 5 years n Subscriber key length > 1024 bits → 1 year n All CA’s issue a CRL with a 30 -day lifetime (updated ~ weekly) n Relying parties must update every 24 hrs n Audit logs must be kept n but no auditing is done! (no funding) u Strongly recommends running a directory service David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 19
EDG CA “Minimum Requirements” (2) u Technical controls better specified n machine with CA private key not connected to any network n CA RSA key length 2048 bits → lifetime 5 years n Subscriber key length > 1024 bits → 1 year n All CA’s issue a CRL with a 30 -day lifetime (updated ~ weekly) n Relying parties must update every 24 hrs n Audit logs must be kept n but no auditing is done! (no funding) u Strongly recommends running a directory service David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 19
 EDG CA CP/CPS and the Matrices u Every EDG CA must provide a CP/CPS (combined) n RFC 2527 preferred n a per-CA “feature matrix” is made u Cross-evaluation of CP/CPS by every CA Manager n tries to make up for lack of auditing n provide trust guidelines for “local” site administrators n Every CA Manager should inspect all other CP/CPSs n Yields the Acceptance Matrix David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 20
EDG CA CP/CPS and the Matrices u Every EDG CA must provide a CP/CPS (combined) n RFC 2527 preferred n a per-CA “feature matrix” is made u Cross-evaluation of CP/CPS by every CA Manager n tries to make up for lack of auditing n provide trust guidelines for “local” site administrators n Every CA Manager should inspect all other CP/CPSs n Yields the Acceptance Matrix David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 20
 CA Feature Matrix by Brian Coghlan, TCD, Ireland David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 21
CA Feature Matrix by Brian Coghlan, TCD, Ireland David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 21
 CA Acceptance Matrix The Acceptance Matrix Problem: This does not scale u Already 12 CA’s u Numbers growing rapidly u Cross. Grid Project: + 7 countries u CERN/LHC: +120 countries u. . u Automate u move the evaluation work to proper forums David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 22
CA Acceptance Matrix The Acceptance Matrix Problem: This does not scale u Already 12 CA’s u Numbers growing rapidly u Cross. Grid Project: + 7 countries u CERN/LHC: +120 countries u. . u Automate u move the evaluation work to proper forums David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 22
 Grid CA Standardization Efforts u Global Grid Forum (GGF) n standardization body modeled like IETF/IRTF n 2 working groups in security area: n Grid Security Infrastructure wg n Grid. CP wg n http: //www. globalgridforum. org/ u Grid. CP working group n define a reference CP (with four? levels) n every compliant CA should add own appendix with CPS (few pages) n not clear on: cross-certifying, root, or bridge CA David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 23
Grid CA Standardization Efforts u Global Grid Forum (GGF) n standardization body modeled like IETF/IRTF n 2 working groups in security area: n Grid Security Infrastructure wg n Grid. CP wg n http: //www. globalgridforum. org/ u Grid. CP working group n define a reference CP (with four? levels) n every compliant CA should add own appendix with CPS (few pages) n not clear on: cross-certifying, root, or bridge CA David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 23
 EDG and GGF CA References u The EU Data. Grid http: //www. eu-datagrid. org/ u The Globus Project http: //www. globus. org/security/ u EDG CACG site http: //marianne. in 2 p 3. fr/datagrid/ca/ u GGF Grid. CP wg http: //www. gridcp. es. net/ u Do. ESG site http: //envisage. es. net/ David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 24
EDG and GGF CA References u The EU Data. Grid http: //www. eu-datagrid. org/ u The Globus Project http: //www. globus. org/security/ u EDG CACG site http: //marianne. in 2 p 3. fr/datagrid/ca/ u GGF Grid. CP wg http: //www. gridcp. es. net/ u Do. ESG site http: //envisage. es. net/ David Groep – GSI and EU Data. Grid Authentication – 2002. 03. 13 - 24


