a2b296d67ad12030c5fca29746dfb802.ppt
- Количество слайдов: 53
Grid. Shib A Technical Overview Tom Scavo trscavo@ncsa. uiuc. edu NCSA gridshib-tech-overview-dec 05 1

Overview • • • Grid. Shib project details Grid. Shib use cases Grid. Shib implementation Grid. Shib attribute pull profile Grid. Shib-My. Proxy integration Grid. Shib browser profile gridshib-tech-overview-dec 05 2

What is Grid. Shib? • Grid. Shib enables secure attribute sharing between Grid virtual organizations and higher-educational institutions • The goal of Grid. Shib is to integrate the Globus Toolkit® with Shibboleth® • Grid. Shib adds attribute-based authorization to Globus Toolkit gridshib-tech-overview-dec 05 3
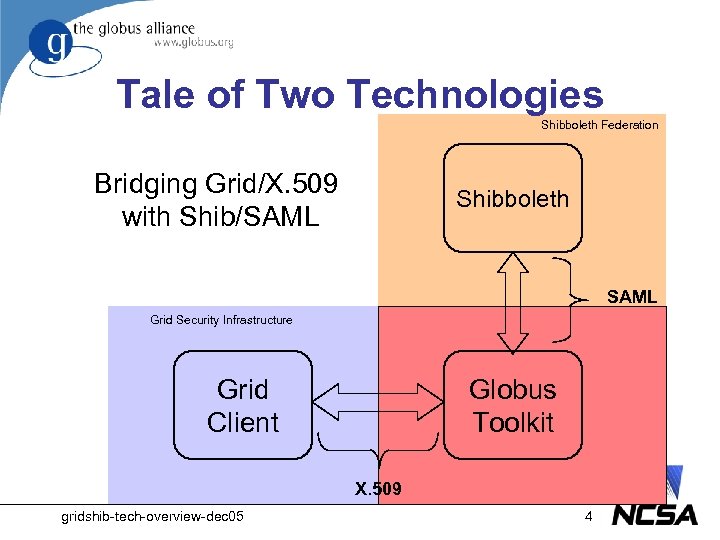
Tale of Two Technologies Shibboleth Federation Bridging Grid/X. 509 with Shib/SAML Shibboleth SAML Grid Security Infrastructure Grid Client Globus Toolkit X. 509 gridshib-tech-overview-dec 05 4

Motivation • Large scientific projects have spawned Virtual Organizations (VOs) • The cyberinfrastructure and software systems to support VOs are called grids • Globus Toolkit is the de facto standard software solution for grids • Grid Security Infrastructure provides basic security services…but does it scale? gridshib-tech-overview-dec 05 5
Why Shibboleth? • What does Shibboleth bring to the table? – A large (and growing) installed base – A standards-based, open source implementation – A standard attribute vocabulary (edu. Person) • A well-developed, federated identity management infrastructure has sprung up around Shibboleth gridshib-tech-overview-dec 05 6
Shibboleth Federations • A federation – Provides a common trust and policy framework – Issues credentials and distributes metadata – Provides discovery services for SPs • Shibboleth-based federations: – – – In. Common (23 members) In. Queue (157 members) SDSS (30 members) SWITCH (23 members) HAKA (8 members) gridshib-tech-overview-dec 05 7
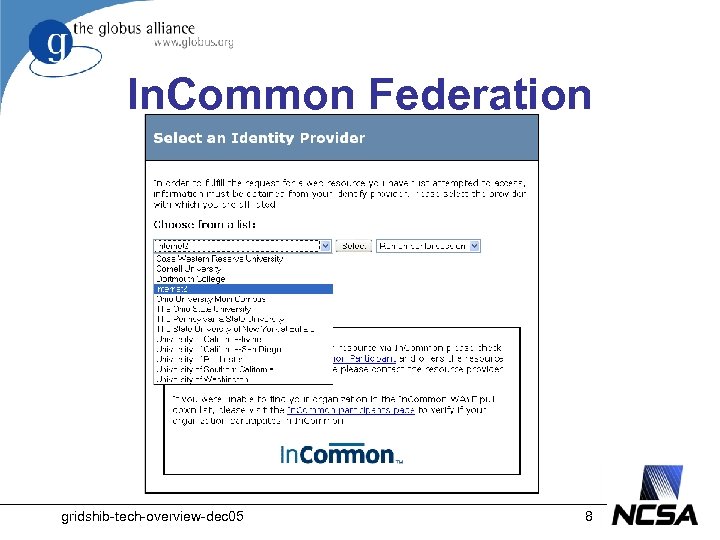
In. Common Federation gridshib-tech-overview-dec 05 8

Introduction gridshib-tech-overview-dec 05 9

Grid. Shib Project • Grid. Shib is a project funded by the NSF Middleware Initiative (NMI awards 0438424 and 0438385) • Grid. Shib is a joint project of NCSA, University of Chicago, and Argonne National Laboratory • Project web site http: //gridshib. globus. org/ gridshib-tech-overview-dec 05 10

Milestones • • Dec 2004, Grid. Shib project commences Feb 2005, Developers onboard Apr 2005, Globus Toolkit 4. 0 released May 2005, Grid. Shib Alpha released Jul 2005, Shibboleth 1. 3 released Sep 2005, Grid. Shib Beta released Grid. Shib-My. Proxy integration TBA gridshib-tech-overview-dec 05 11

Related Projects • Globus Toolkit http: //www. globus. org/toolkit/ • Shibboleth http: //shibboleth. internet 2. edu/ • Lion. Share http: //lionshare. its. psu. edu/ • e. SP-grid http: //escience. ox. ac. uk/oesc/projects/index. xml. ID= body. 1_div. 1#esp gridshib-tech-overview-dec 05 12

Leveraged Standards • X. 509 Public Key Infrastructure (RFC 3280) • Proxy certificates (RFC 3820) • OASIS SAML 1. 1 http: //www. oasisopen. org/committees/tc_home. php? wg_abbrev =security#samlv 11 • Internet 2 Shibboleth http: //shibboleth. internet 2. edu/docs/internet 2 mace-shibboleth-arch-protocols-latest. pdf gridshib-tech-overview-dec 05 13

Use Cases • There are three use cases under consideration: 1. Established grid user (non-browser) 2. New grid user (non-browser) 3. Portal grid user (browser) v Initial efforts have concentrated on the established grid user (i. e. , user with existing long-term X. 509 credentials ) gridshib-tech-overview-dec 05 14

Established Grid User • User possesses an X. 509 end entity certificate • User may or may not use My. Proxy Server to manage X. 509 credentials • User authenticates to Grid SP with proxy certificate (grid-proxy-init) • The current Grid. Shib implementation addresses this use case gridshib-tech-overview-dec 05 15

New Grid User • User does not possess an X. 509 end entity certificate • User relies on My. Proxy Online CA to issue short-lived X. 509 certificates • User authenticates to Grid SP using short-lived X. 509 credential • Emerging Grid. Shib Non-Browser Profiles address this use case gridshib-tech-overview-dec 05 16
Portal Grid User • User does not possess an X. 509 cert • User accesses Grid SP via a browser interface, that is, the client delegates a web application to request a service at the Grid SP • My. Proxy issues a short-lived X. 509 certificate via a back-channel exchange • Grid. Shib Browser Profiles apply gridshib-tech-overview-dec 05 17

Grid. Shib Implementation gridshib-tech-overview-dec 05 18
Software Components • Grid. Shib for Globus Toolkit – A plugin for GT 4. 0 • Grid. Shib for Shibboleth – A plugin for Shibboleth 1. 3 Id. P • Shibboleth Id. P Tester – A test application for Shibboleth 1. 3 Id. P • Visit the Grid. Shib Download page: http: //gridshib. globus. org/download. html gridshib-tech-overview-dec 05 19
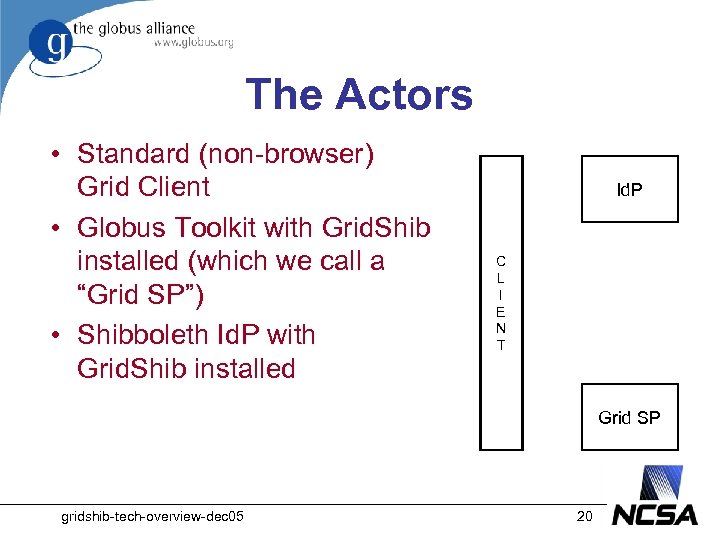
The Actors • Standard (non-browser) Grid Client • Globus Toolkit with Grid. Shib installed (which we call a “Grid SP”) • Shibboleth Id. P with Grid. Shib installed Id. P C L I E N T Grid SP gridshib-tech-overview-dec 05 20

Grid. Shib Attribute Pull Profile • In the current implementation, a Grid SP “pulls” attributes from a Shib Id. P • The Client is assumed to have an account (i. e. , local principal name) at the Id. P • The Grid SP and the Id. P have been assigned a unique identifier (provider. Id) gridshib-tech-overview-dec 05 Id. P C L I E N T 2 3 1 Grid SP 4 21
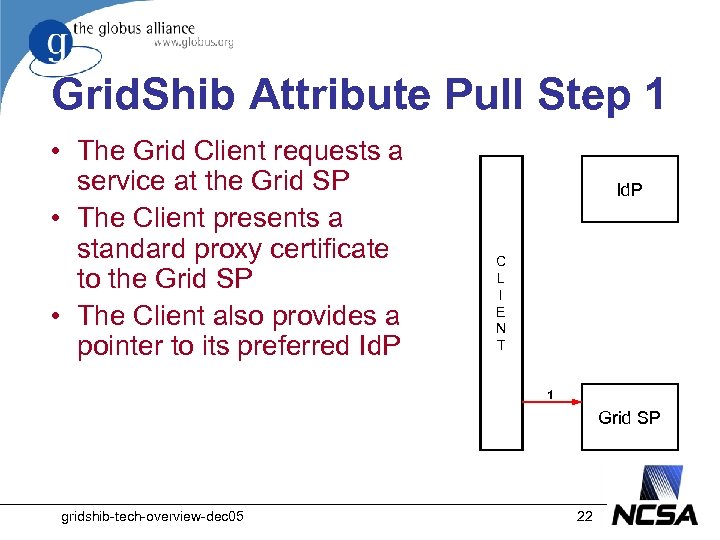
Grid. Shib Attribute Pull Step 1 • The Grid Client requests a service at the Grid SP • The Client presents a standard proxy certificate to the Grid SP • The Client also provides a pointer to its preferred Id. P C L I E N T 1 Grid SP gridshib-tech-overview-dec 05 22

Id. P Discovery • The Grid SP needs to know the Client’s preferred Id. P • One approach is to embed the Id. P provider. Id in the proxy certificate • This requires modifications to the My. Proxy client software, however • Currently the Id. P provider. Id is configured into the Grid SP gridshib-tech-overview-dec 05 23
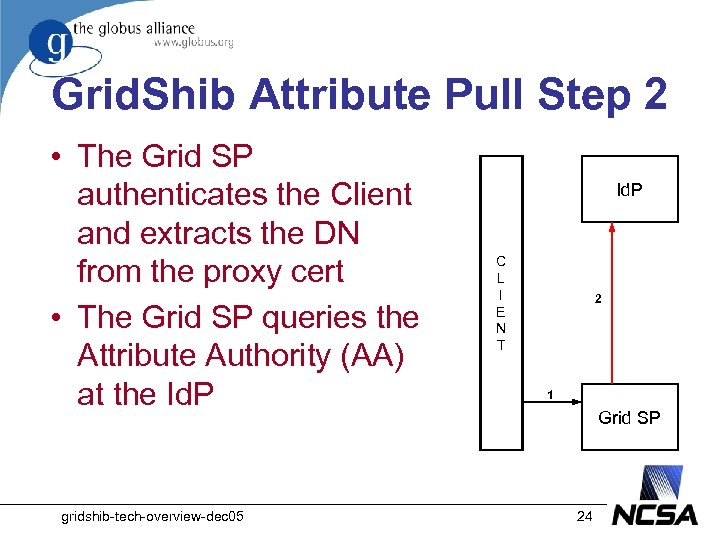
Grid. Shib Attribute Pull Step 2 • The Grid SP authenticates the Client and extracts the DN from the proxy cert • The Grid SP queries the Attribute Authority (AA) at the Id. P gridshib-tech-overview-dec 05 Id. P C L I E N T 2 1 Grid SP 24

Attribute Query • The Grid SP formulates a SAML attribute query: • • <samlp: Attribute. Query Resource="https: //globus. org/gridshib"> <saml: Subject> <saml: Name. Identifier Format="urn: oasis: names: tc: SAML: 1. 1: nameidformat: X 509 Subject. Name" Name. Qualifier="http: //idp. uchicago. edu/shibboleth"> CN=Grid. Shib, OU=NCSA, O=UIUC </saml: Name. Identifier> </saml: Subject> <!-- Attribute. Designator here --> </samlp: Attribute. Query> The Resource attribute is the Grid SP provider. Id The Name. Qualifier attribute is the Id. P provider. Id The Name. Identifier is the DN from the proxy cert Zero or more Attribute. Designator elements call out the desired attributes gridshib-tech-overview-dec 05 25
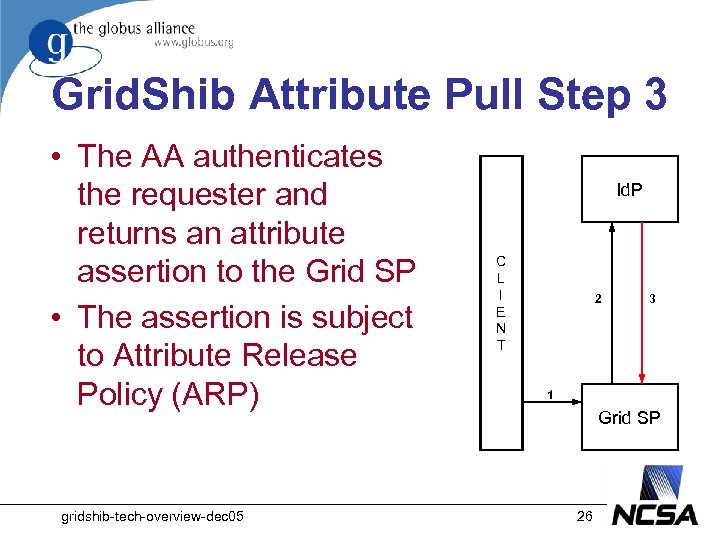
Grid. Shib Attribute Pull Step 3 • The AA authenticates the requester and returns an attribute assertion to the Grid SP • The assertion is subject to Attribute Release Policy (ARP) gridshib-tech-overview-dec 05 Id. P C L I E N T 2 3 1 Grid SP 26

Attribute Assertion • The assertion contains an attribute statement: <saml: Attribute. Statement> <saml: Subject> <saml: Name. Identifier Format="urn: oasis: names: tc: SAML: 1. 1: nameid-format: X 509 Subject. Name" Name. Qualifier="http: //idp. uchicago. edu/shibboleth"> CN=Grid. Shib, OU=NCSA, O=UIUC </saml: Name. Identifier> </saml: Subject> <saml: Attribute. Name="urn: mace: dir: attribute-def: edu. Person. Affiliation" Attribute. Namespace="urn: mace: shibboleth: 1. 0: attribute. Namespace: uri"> <saml: Attribute. Value> member </saml: Attribute. Value> <saml: Attribute. Value> student </saml: Attribute. Value> </saml: Attribute. Statement> • The Subject is identical to the Subject of the query • Attributes may be single-valued or multi-valued • Attributes may be scoped (e. g. , member@uchicago. edu) gridshib-tech-overview-dec 05 27
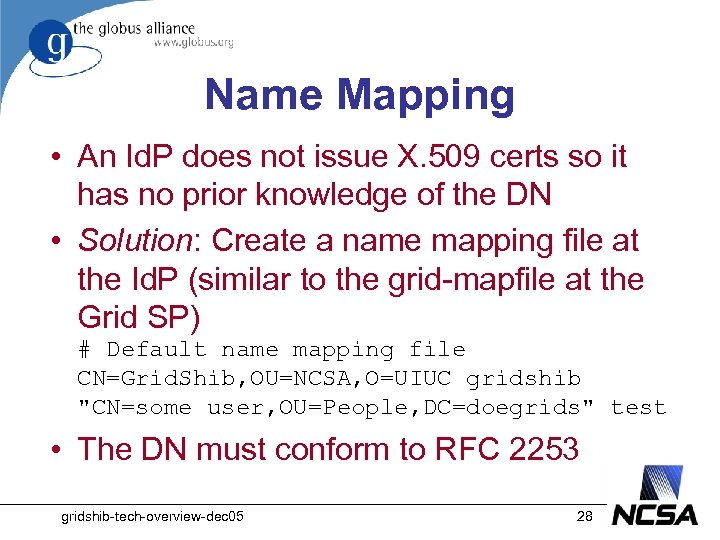
Name Mapping • An Id. P does not issue X. 509 certs so it has no prior knowledge of the DN • Solution: Create a name mapping file at the Id. P (similar to the grid-mapfile at the Grid SP) # Default name mapping file CN=Grid. Shib, OU=NCSA, O=UIUC gridshib "CN=some user, OU=People, DC=doegrids" test • The DN must conform to RFC 2253 gridshib-tech-overview-dec 05 28
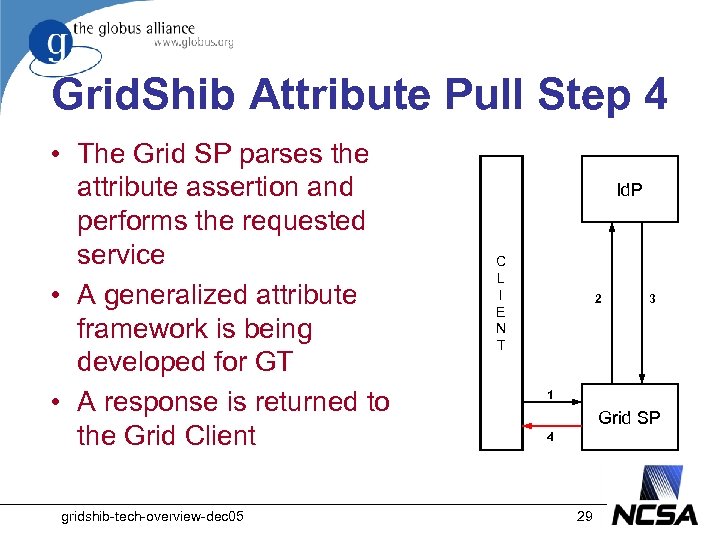
Grid. Shib Attribute Pull Step 4 • The Grid SP parses the attribute assertion and performs the requested service • A generalized attribute framework is being developed for GT • A response is returned to the Grid Client gridshib-tech-overview-dec 05 Id. P C L I E N T 2 3 1 Grid SP 4 29
Future Work • Solve the Id. P Discovery problem – Implement shib-proxy-init • Implement DB-based name mapping • Provide name mapping maintenance tools (for administrators) • Design an interactive name registry service (for users) • Devise metadata repositories and tools gridshib-tech-overview-dec 05 30

Grid. Shib-My. Proxy Integration gridshib-tech-overview-dec 05 31
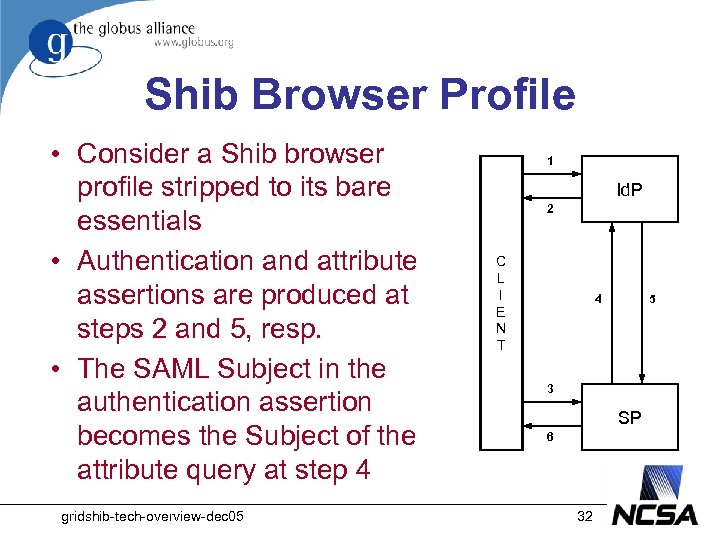
Shib Browser Profile • Consider a Shib browser profile stripped to its bare essentials • Authentication and attribute assertions are produced at steps 2 and 5, resp. • The SAML Subject in the authentication assertion becomes the Subject of the attribute query at step 4 gridshib-tech-overview-dec 05 1 Id. P 2 C L I E N T 4 5 3 SP 6 32
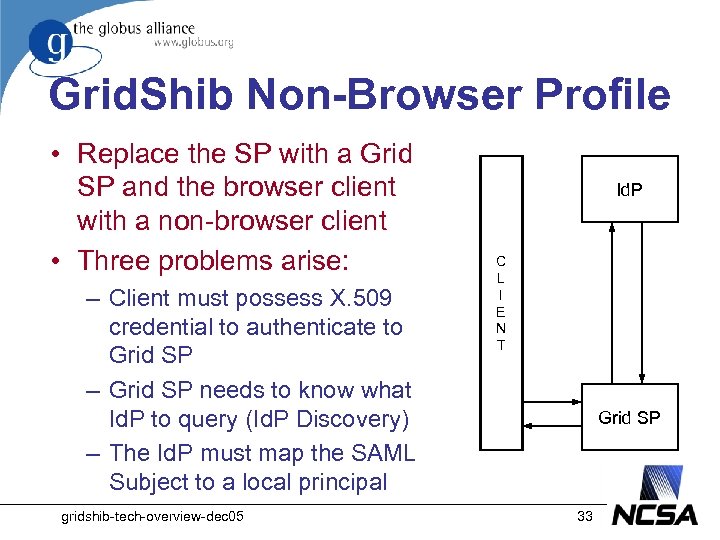
Grid. Shib Non-Browser Profile • Replace the SP with a Grid SP and the browser client with a non-browser client • Three problems arise: – Client must possess X. 509 credential to authenticate to Grid SP – Grid SP needs to know what Id. P to query (Id. P Discovery) – The Id. P must map the SAML Subject to a local principal gridshib-tech-overview-dec 05 Id. P C L I E N T Grid SP 33

The Role of My. Proxy • Consider a new grid user instead of the established grid user • For a new grid user, we are led to a significantly different solution • Obviously, we must issue an X. 509 credential to a new grid user • A short-lived credential is preferred • Enter My. Proxy Online CA… gridshib-tech-overview-dec 05 34
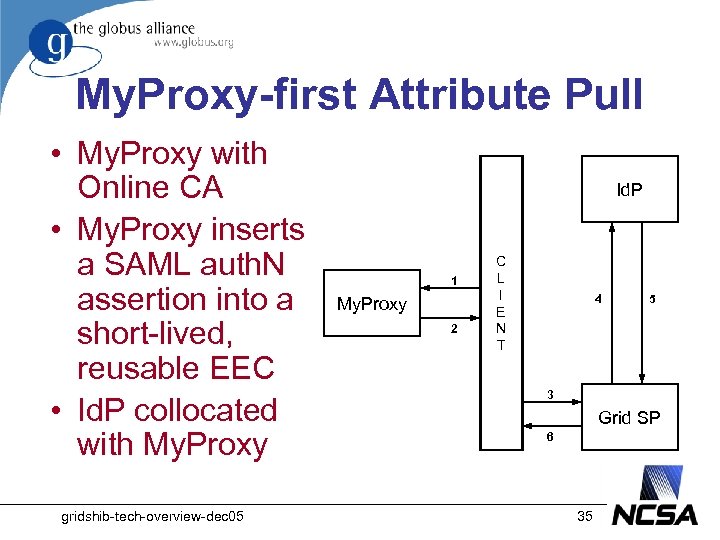
My. Proxy-first Attribute Pull • My. Proxy with Online CA • My. Proxy inserts a SAML auth. N assertion into a short-lived, reusable EEC • Id. P collocated with My. Proxy gridshib-tech-overview-dec 05 Id. P 1 My. Proxy 2 C L I E N T 4 5 3 Grid SP 6 35
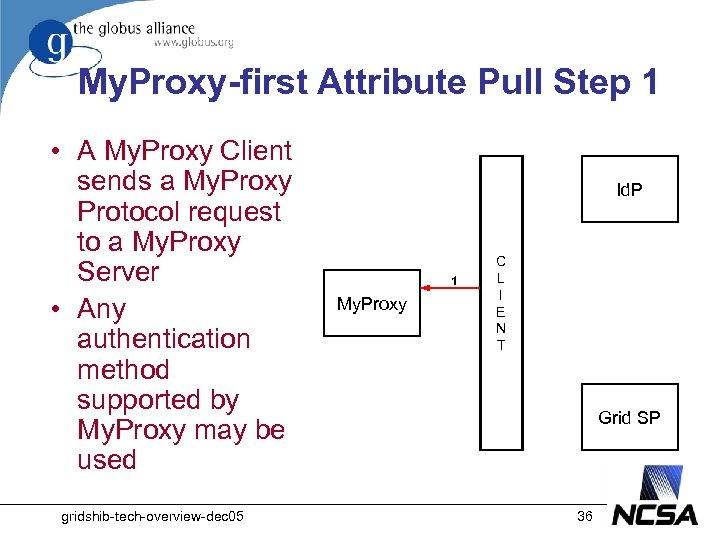
My. Proxy-first Attribute Pull Step 1 • A My. Proxy Client sends a My. Proxy Protocol request to a My. Proxy Server • Any authentication method supported by My. Proxy may be used gridshib-tech-overview-dec 05 Id. P 1 My. Proxy C L I E N T Grid SP 36

My. Proxy-first Attribute Pull Step 2 • The My. Proxy Server authenticates the requester • My. Proxy issues an X. 509 credential with embedded auth. N assertion • The credential is returned in a My. Proxy Protocol response gridshib-tech-overview-dec 05 Id. P 1 My. Proxy 2 C L I E N T Grid SP 37
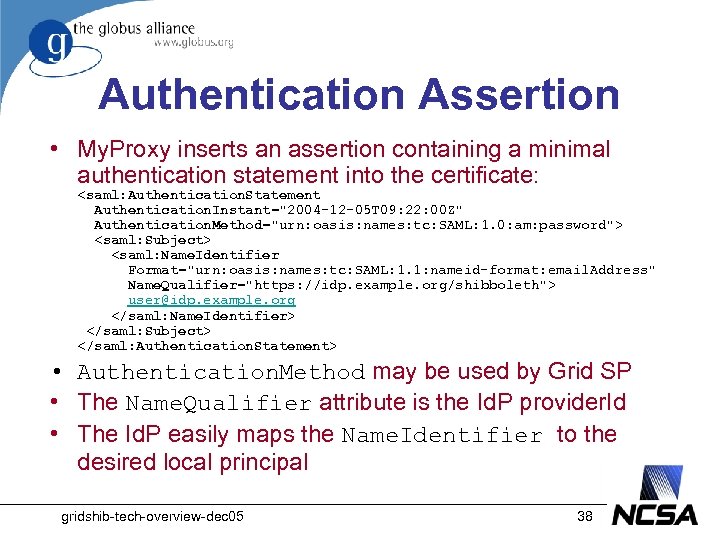
Authentication Assertion • My. Proxy inserts an assertion containing a minimal authentication statement into the certificate: <saml: Authentication. Statement Authentication. Instant="2004 -12 -05 T 09: 22: 00 Z" Authentication. Method="urn: oasis: names: tc: SAML: 1. 0: am: password"> <saml: Subject> <saml: Name. Identifier Format="urn: oasis: names: tc: SAML: 1. 1: nameid-format: email. Address" Name. Qualifier="https: //idp. example. org/shibboleth"> user@idp. example. org </saml: Name. Identifier> </saml: Subject> </saml: Authentication. Statement> • Authentication. Method may be used by Grid SP • The Name. Qualifier attribute is the Id. P provider. Id • The Id. P easily maps the Name. Identifier to the desired local principal gridshib-tech-overview-dec 05 38
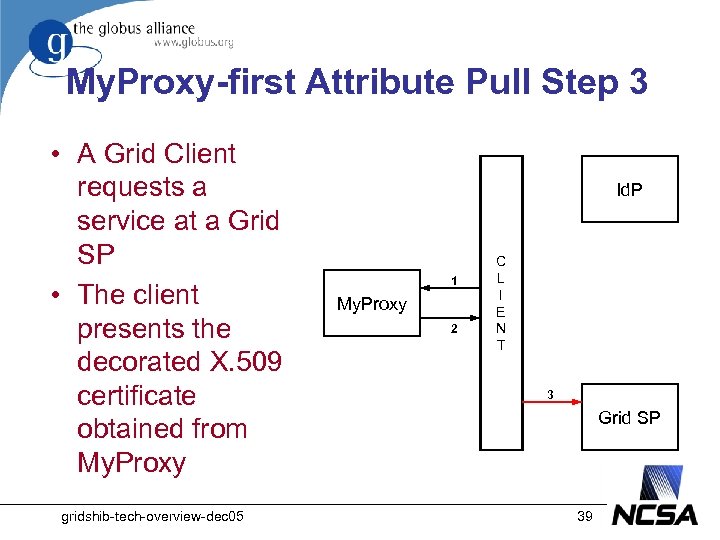
My. Proxy-first Attribute Pull Step 3 • A Grid Client requests a service at a Grid SP • The client presents the decorated X. 509 certificate obtained from My. Proxy gridshib-tech-overview-dec 05 Id. P 1 My. Proxy 2 C L I E N T 3 Grid SP 39

My. Proxy-first Attribute Pull Step 4 • The Grid SP authenticates the Client and processes the assertion • The Grid SP queries the Shib Attribute Authority (AA) referred to in the assertion gridshib-tech-overview-dec 05 Id. P 1 My. Proxy 2 C L I E N T 4 3 Grid SP 40

My. Proxy-first Attribute Pull Step 5 • The AA authenticates the requester and returns an attribute assertion to the Grid SP • The assertion is subject to policy gridshib-tech-overview-dec 05 Id. P 1 My. Proxy 2 C L I E N T 4 5 3 Grid SP 41
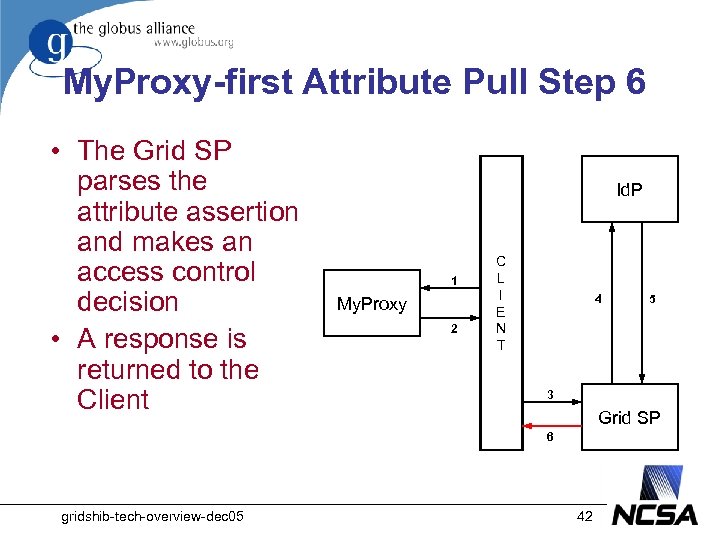
My. Proxy-first Attribute Pull Step 6 • The Grid SP parses the attribute assertion and makes an access control decision • A response is returned to the Client Id. P 1 My. Proxy 2 C L I E N T 4 3 Grid SP 6 gridshib-tech-overview-dec 05 5 42

My. Proxy-first Advantages • • • Relatively easy to implement Requires only one round trip by the client Requires no modifications to the Shib Id. P Requires no modifications to the Client Supports multiple authentication mechanisms out-of-the-box • Uses transparent, persistent identifiers: – No coordination of timeouts necessary – Mapping to local principal is straightforward gridshib-tech-overview-dec 05 43

Id. P-first Non-Browser Profiles • The Id. P-first profiles require no shared state between My. Proxy and the Id. P • Supports separate security domains • Leverages existing name identifier mappings at the Id. P • Id. P-first profiles may be used with either Attribute Pull or Attribute Push gridshib-tech-overview-dec 05 44

Attribute Pull or Push? Pull Push user request Grid SP attributes AA gridshib-tech-overview-dec 05 request attributes AA 45
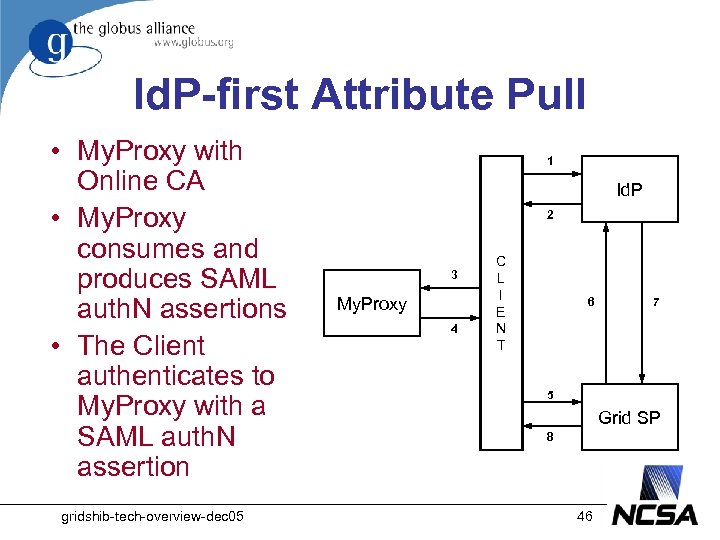
Id. P-first Attribute Pull • My. Proxy with Online CA • My. Proxy consumes and produces SAML auth. N assertions • The Client authenticates to My. Proxy with a SAML auth. N assertion gridshib-tech-overview-dec 05 1 Id. P 2 3 My. Proxy 4 C L I E N T 6 7 5 Grid SP 8 46
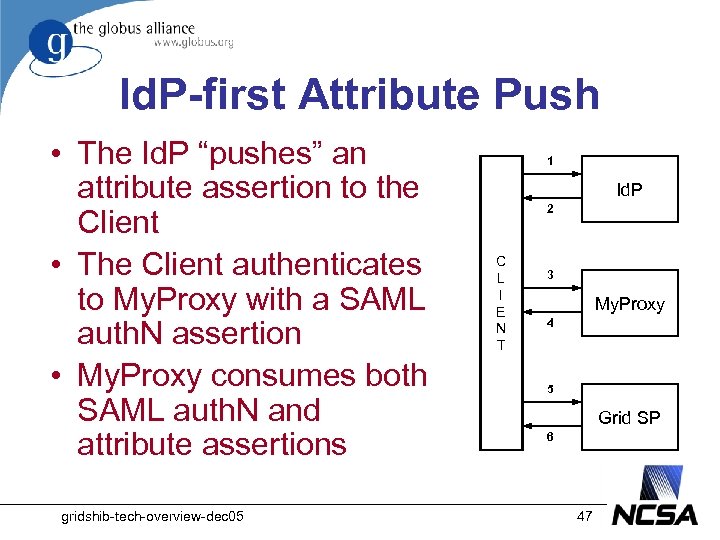
Id. P-first Attribute Push • The Id. P “pushes” an attribute assertion to the Client • The Client authenticates to My. Proxy with a SAML auth. N assertion • My. Proxy consumes both SAML auth. N and attribute assertions gridshib-tech-overview-dec 05 1 Id. P 2 C L I E N T 3 My. Proxy 4 5 Grid SP 6 47
Id. P-first Advantages • Since Id. P controls both ends of the flow: – Mapping Name. Identifier to a local principal is straightforward – Choice of Name. Identifier format is left to the Id. P • Attribute push simplifies Id. P config and trust relationships • Reusable by grid portal use case gridshib-tech-overview-dec 05 48
Grid. Shib Browser Profiles gridshib-tech-overview-dec 05 49

Id. P-first Browser Profiles • As a consequence of the Id. P-first Non. Browser profiles, My. Proxy gains the ability to consumes SAML assertions • If we replace the non-browser client with a web component, we can reuse that functionality in the following Grid. Shib Browser Profile gridshib-tech-overview-dec 05 50

Id. P-first Attribute Pull • The first three steps are normal Shib Browser/POST • A Shib SP is protecting a web version of My. Proxy Client gridshib-tech-overview-dec 05 1 Id. P 2 C L I E N T 7 My. Proxy 4 5 3 6 SP 10 8 Grid SP 9 51

The 3 -tier Problem • How does the browser user delegate authority to the web component to retrieve an X. 509 credential on its behalf? • This problem is an instance of the socalled n-tier problem gridshib-tech-overview-dec 05 52
Delegation Profile • No widely accepted solution to this problem exists today • The Shib dev team has proposed a SAML 2 -based solution: http: //shibboleth. internet 2. edu/docs/draft -cantor-saml-sso-delegation-01. pdf • The implications for Grid. Shib are not clear at this point gridshib-tech-overview-dec 05 53
a2b296d67ad12030c5fca29746dfb802.ppt