9c80e233e9ecc8d64e828b46bb3cfe13.ppt
- Количество слайдов: 53
 Grid Security: What is it? Where is it going? Why? Von Welch vwelch@ncsa. uiuc. edu National Center for Supercomputing Applications Globus Alliance
Grid Security: What is it? Where is it going? Why? Von Welch vwelch@ncsa. uiuc. edu National Center for Supercomputing Applications Globus Alliance
 Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 2
Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 2
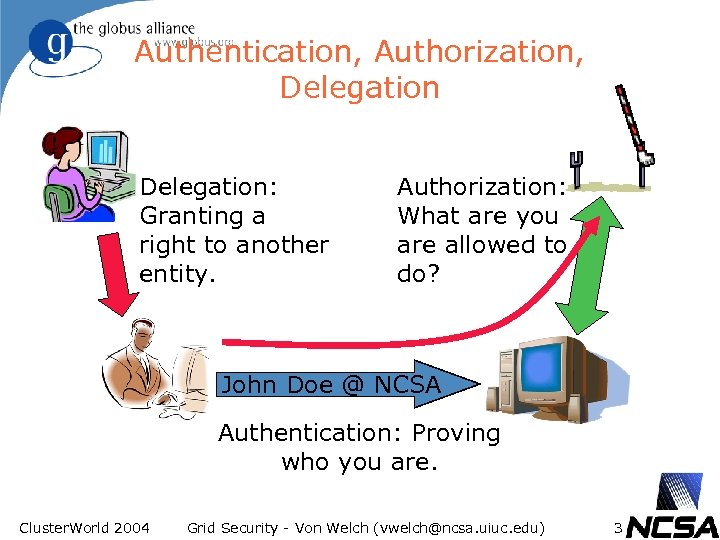 Authentication, Authorization, Delegation: Granting a right to another entity. Authorization: What are you are allowed to do? John Doe @ NCSA Authentication: Proving who you are. Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 3
Authentication, Authorization, Delegation: Granting a right to another entity. Authorization: What are you are allowed to do? John Doe @ NCSA Authentication: Proving who you are. Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 3
 Public Key Infrastructure l Used in almost all Grids today u. Allows for two entities to authenticate with minimal cross-organizational supprt l Based on asymmetric cryptography u. Private and Public Key l Public key is encoded in a Certificate by a Certificate Authority (CA) u. Certificate and Private key are used to establish identity Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 4
Public Key Infrastructure l Used in almost all Grids today u. Allows for two entities to authenticate with minimal cross-organizational supprt l Based on asymmetric cryptography u. Private and Public Key l Public key is encoded in a Certificate by a Certificate Authority (CA) u. Certificate and Private key are used to establish identity Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 4
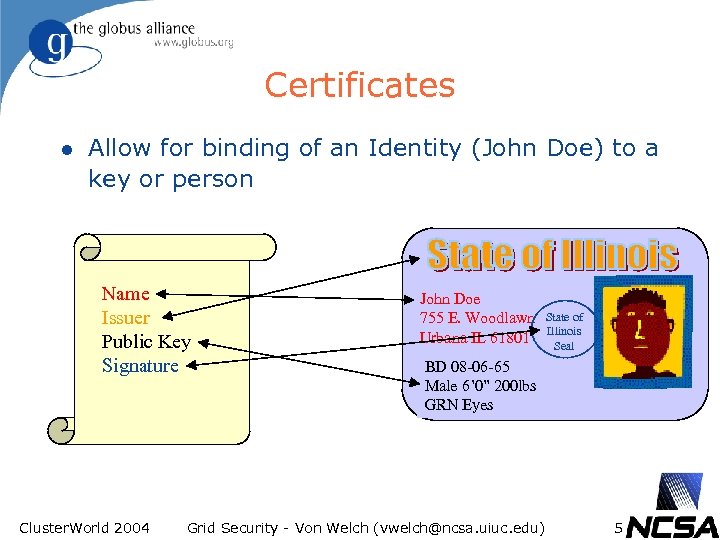 Certificates l Allow for binding of an Identity (John Doe) to a key or person Name Issuer Public Key Signature Cluster. World 2004 John Doe 755 E. Woodlawn Urbana IL 61801 State of Illinois Seal BD 08 -06 -65 Male 6’ 0” 200 lbs GRN Eyes Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 5
Certificates l Allow for binding of an Identity (John Doe) to a key or person Name Issuer Public Key Signature Cluster. World 2004 John Doe 755 E. Woodlawn Urbana IL 61801 State of Illinois Seal BD 08 -06 -65 Male 6’ 0” 200 lbs GRN Eyes Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 5
 Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 6
Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 6
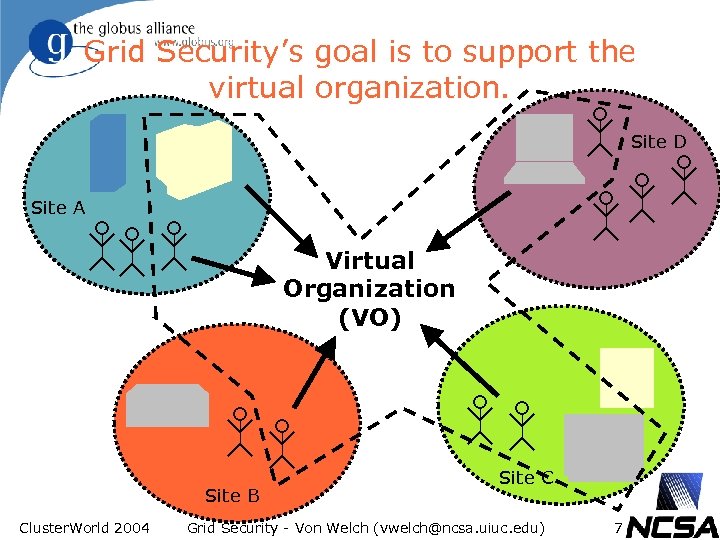 Grid Security’s goal is to support the virtual organization. Site D Site A Virtual Organization (VO) Site B Cluster. World 2004 Site C Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 7
Grid Security’s goal is to support the virtual organization. Site D Site A Virtual Organization (VO) Site B Cluster. World 2004 Site C Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 7
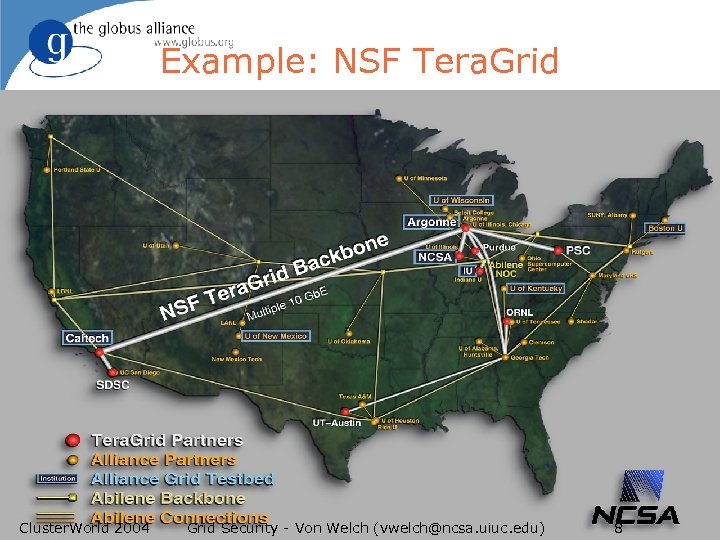 Example: NSF Tera. Grid Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 8
Example: NSF Tera. Grid Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 8
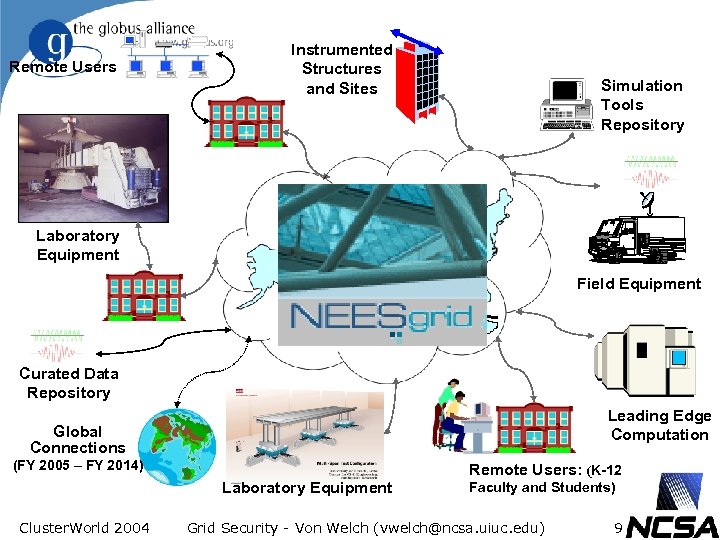 Remote Users Laboratory Equipment Instrumented Structures and Sites Simulation Tools Repository High. Performance Network(s) Field Equipment Curated Data Repository Leading Edge Computation Global Connections (FY 2005 – FY 2014) Remote Users: (K-12 Laboratory Equipment Cluster. World 2004 Faculty and Students) Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 9
Remote Users Laboratory Equipment Instrumented Structures and Sites Simulation Tools Repository High. Performance Network(s) Field Equipment Curated Data Repository Leading Edge Computation Global Connections (FY 2005 – FY 2014) Remote Users: (K-12 Laboratory Equipment Cluster. World 2004 Faculty and Students) Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 9
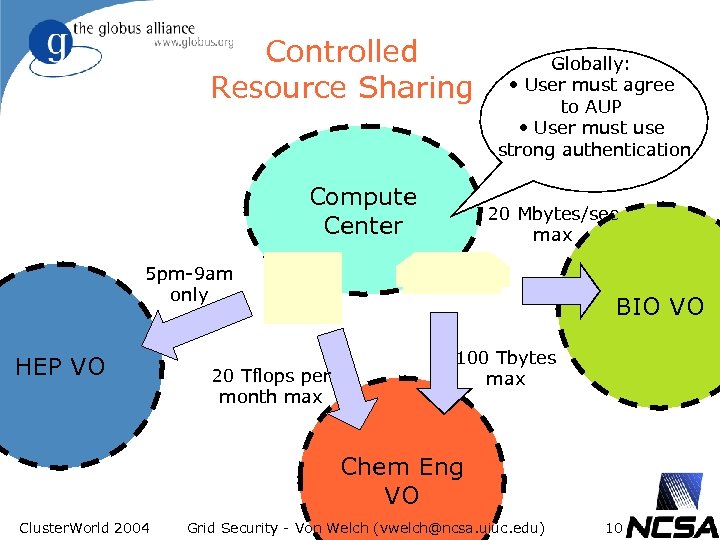 Controlled Resource Sharing Compute Center Globally: • User must agree to AUP • User must use strong authentication 20 Mbytes/sec max 5 pm-9 am only HEP VO 20 Tflops per month max BIO VO 100 Tbytes max Chem Eng VO Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 10
Controlled Resource Sharing Compute Center Globally: • User must agree to AUP • User must use strong authentication 20 Mbytes/sec max 5 pm-9 am only HEP VO 20 Tflops per month max BIO VO 100 Tbytes max Chem Eng VO Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 10
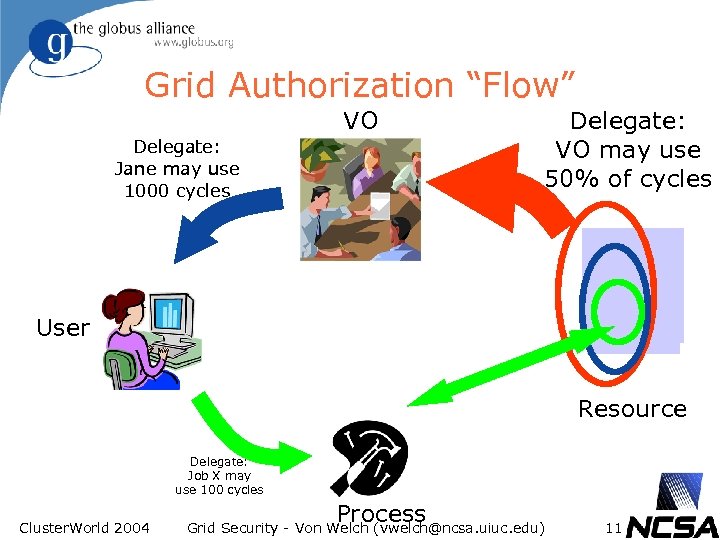 Grid Authorization “Flow” VO Delegate: Jane may use 1000 cycles Delegate: VO may use 50% of cycles User Resource Delegate: Job X may use 100 cycles Cluster. World 2004 Process Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 11
Grid Authorization “Flow” VO Delegate: Jane may use 1000 cycles Delegate: VO may use 50% of cycles User Resource Delegate: Job X may use 100 cycles Cluster. World 2004 Process Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 11
 So, what are the challenges? l Resources being used may be valuable & the problems being solved sensitive u l VOs aren’t static u l Both users and resources need to be careful Large, dynamic, unpredictable… VO Resources and users are often located in distinct administrative domains u u Can’t assume cross-organizational trust agreements Different mechanisms, trust roots & credentials l l l Cluster. World 2004 X. 509 vs Kerberos Different CAs X. 509 attribute certs vs SAML assertions Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 12
So, what are the challenges? l Resources being used may be valuable & the problems being solved sensitive u l VOs aren’t static u l Both users and resources need to be careful Large, dynamic, unpredictable… VO Resources and users are often located in distinct administrative domains u u Can’t assume cross-organizational trust agreements Different mechanisms, trust roots & credentials l l l Cluster. World 2004 X. 509 vs Kerberos Different CAs X. 509 attribute certs vs SAML assertions Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 12
 More challenges… l Interactions are not just client/server, but service-to-service on behalf of the user u u l l Standardization of interfaces to allow for discovery, negotiation and use Implementation must be broadly available & applicable u l Standard, well-tested, well-understood protocols; integrated with wide variety of tools Policy from sites, VO, users need to be combined u l Requires delegation of rights by user to service Services may be dynamically instantiated Varying formats: SAML, XACML, local custom, etc. Want to hide as much as possible from applications! Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 13
More challenges… l Interactions are not just client/server, but service-to-service on behalf of the user u u l l Standardization of interfaces to allow for discovery, negotiation and use Implementation must be broadly available & applicable u l Standard, well-tested, well-understood protocols; integrated with wide variety of tools Policy from sites, VO, users need to be combined u l Requires delegation of rights by user to service Services may be dynamically instantiated Varying formats: SAML, XACML, local custom, etc. Want to hide as much as possible from applications! Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 13
 Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 14
Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 14
 Grid Security Infrastructure (GSI) l Open source libraries, tools and standards which provide security functionality of the Globus Toolkit l Provides for cross-organizational: u Authentication u Message protection u Authorization u Single sign-on Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 15
Grid Security Infrastructure (GSI) l Open source libraries, tools and standards which provide security functionality of the Globus Toolkit l Provides for cross-organizational: u Authentication u Message protection u Authorization u Single sign-on Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 15
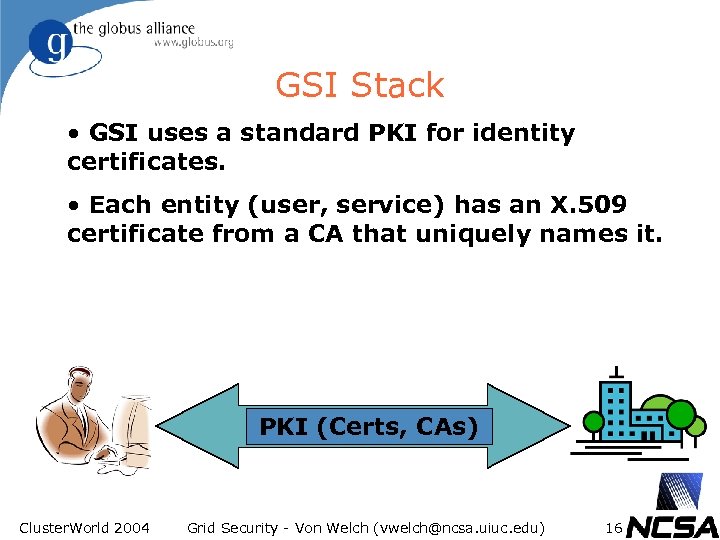 GSI Stack • GSI uses a standard PKI for identity certificates. • Each entity (user, service) has an X. 509 certificate from a CA that uniquely names it. PKI (Certs, CAs) Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 16
GSI Stack • GSI uses a standard PKI for identity certificates. • Each entity (user, service) has an X. 509 certificate from a CA that uniquely names it. PKI (Certs, CAs) Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 16
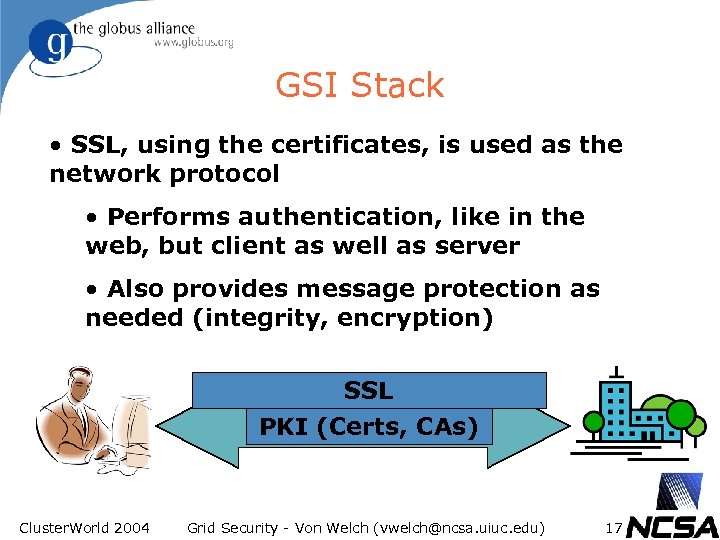 GSI Stack • SSL, using the certificates, is used as the network protocol • Performs authentication, like in the web, but client as well as server • Also provides message protection as needed (integrity, encryption) SSL PKI (Certs, CAs) Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 17
GSI Stack • SSL, using the certificates, is used as the network protocol • Performs authentication, like in the web, but client as well as server • Also provides message protection as needed (integrity, encryption) SSL PKI (Certs, CAs) Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 17
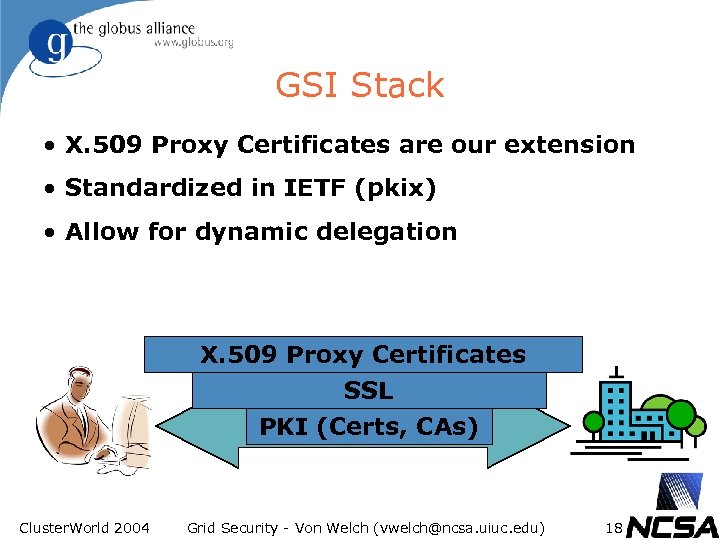 GSI Stack • X. 509 Proxy Certificates are our extension • Standardized in IETF (pkix) • Allow for dynamic delegation X. 509 Proxy Certificates SSL PKI (Certs, CAs) Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 18
GSI Stack • X. 509 Proxy Certificates are our extension • Standardized in IETF (pkix) • Allow for dynamic delegation X. 509 Proxy Certificates SSL PKI (Certs, CAs) Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 18
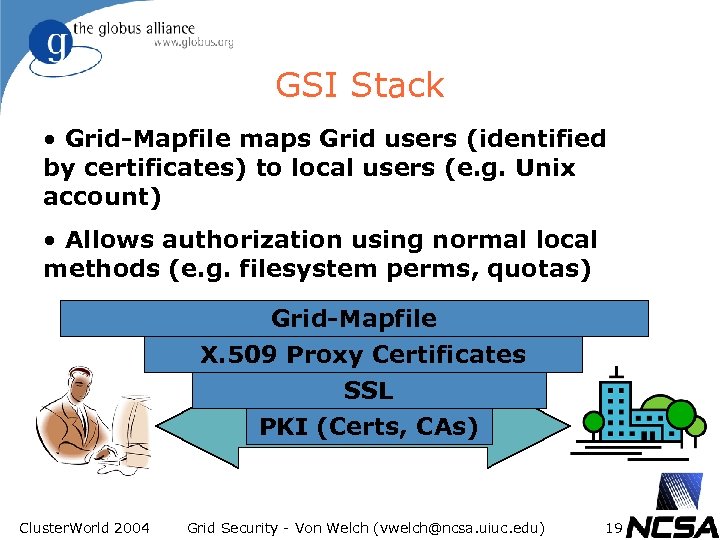 GSI Stack • Grid-Mapfile maps Grid users (identified by certificates) to local users (e. g. Unix account) • Allows authorization using normal local methods (e. g. filesystem perms, quotas) Grid-Mapfile X. 509 Proxy Certificates SSL PKI (Certs, CAs) Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 19
GSI Stack • Grid-Mapfile maps Grid users (identified by certificates) to local users (e. g. Unix account) • Allows authorization using normal local methods (e. g. filesystem perms, quotas) Grid-Mapfile X. 509 Proxy Certificates SSL PKI (Certs, CAs) Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 19
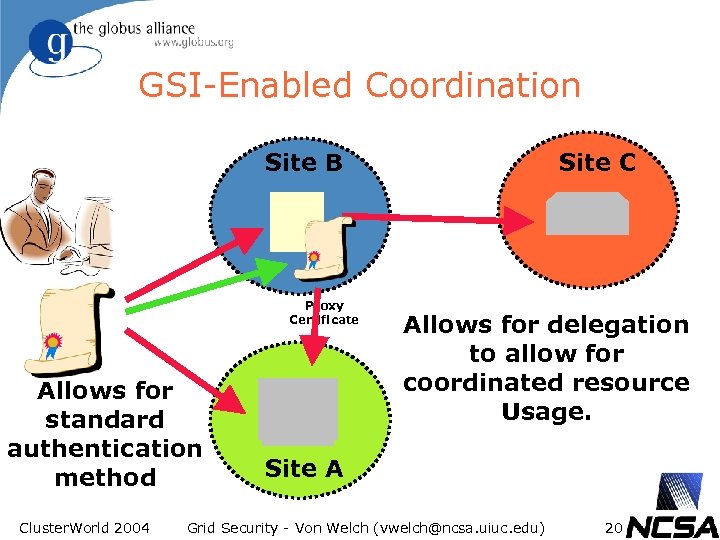 GSI-Enabled Coordination Site B Proxy Certificate Allows for standard authentication method Cluster. World 2004 Site C Allows for delegation to allow for coordinated resource Usage. Site A Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 20
GSI-Enabled Coordination Site B Proxy Certificate Allows for standard authentication method Cluster. World 2004 Site C Allows for delegation to allow for coordinated resource Usage. Site A Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 20
 Grid Security Services l How does a site with an existing sophisticated security infrastructure leverage that for Grids? u l How do I carry X. 509 credentials around with me? How do I use with non-GSI aware applications? u l E. g. Kerberos E. g. Web portals? How does a VO manage the resources contributed to it? Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 21
Grid Security Services l How does a site with an existing sophisticated security infrastructure leverage that for Grids? u l How do I carry X. 509 credentials around with me? How do I use with non-GSI aware applications? u l E. g. Kerberos E. g. Web portals? How does a VO manage the resources contributed to it? Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 21
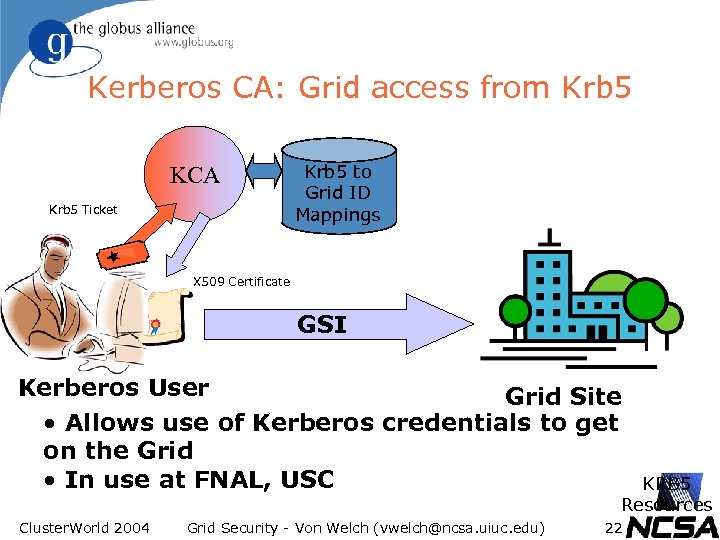 Kerberos CA: Grid access from Krb 5 KCA Krb 5 Ticket Krb 5 to Grid ID Mappings X 509 Certificate GSI Kerberos User Grid Site • Allows use of Kerberos credentials to get on the Grid • In use at FNAL, USC KRB 5 Resources Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 22
Kerberos CA: Grid access from Krb 5 KCA Krb 5 Ticket Krb 5 to Grid ID Mappings X 509 Certificate GSI Kerberos User Grid Site • Allows use of Kerberos credentials to get on the Grid • In use at FNAL, USC KRB 5 Resources Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 22
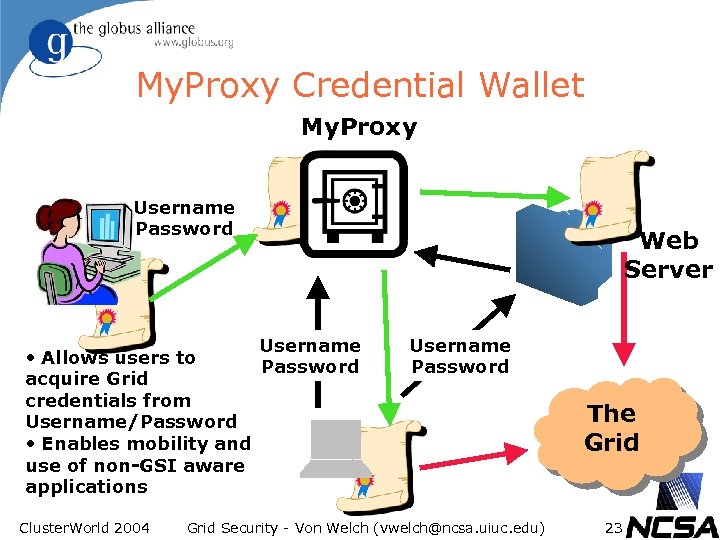 My. Proxy Credential Wallet My. Proxy Username Password Username • Allows users to Password acquire Grid credentials from Username/Password • Enables mobility and use of non-GSI aware applications Cluster. World 2004 Web Server Username Password Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) The Grid 23
My. Proxy Credential Wallet My. Proxy Username Password Username • Allows users to Password acquire Grid credentials from Username/Password • Enables mobility and use of non-GSI aware applications Cluster. World 2004 Web Server Username Password Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) The Grid 23
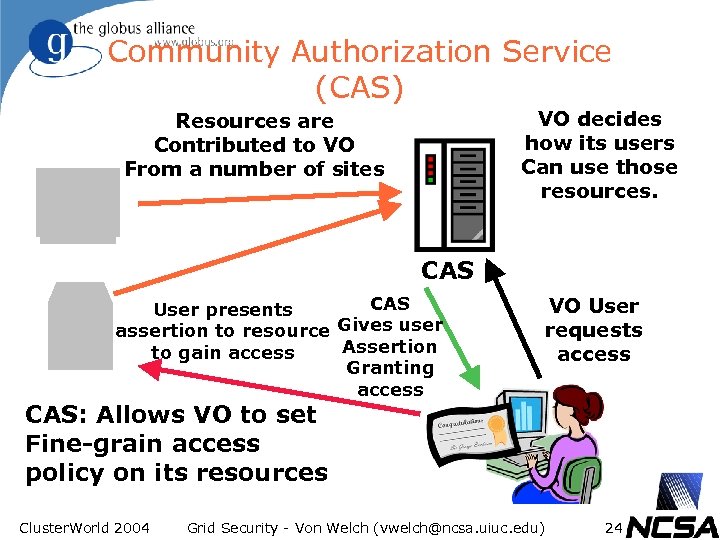 Community Authorization Service (CAS) VO decides how its users Can use those resources. Resources are Contributed to VO From a number of sites CAS User presents assertion to resource Gives user Assertion to gain access Granting access VO User requests access CAS: Allows VO to set Fine-grain access policy on its resources Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 24
Community Authorization Service (CAS) VO decides how its users Can use those resources. Resources are Contributed to VO From a number of sites CAS User presents assertion to resource Gives user Assertion to gain access Granting access VO User requests access CAS: Allows VO to set Fine-grain access policy on its resources Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 24
 Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 25
Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 25
 Grid Evolution: Open Grid Services Architecture l Goals u u u l Refactor Globus protocol suite to enable common base and expose key capabilities Service orientation to virtualize resources and unify resources/services/information Embrace key Web services technologies for standard IDL, leverage commercial efforts Result = standard interfaces & behaviors for distributed system mgmt: the Grid service u Standardization within Global Grid Forum and OASIS u Open source & commercial implementations Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 26
Grid Evolution: Open Grid Services Architecture l Goals u u u l Refactor Globus protocol suite to enable common base and expose key capabilities Service orientation to virtualize resources and unify resources/services/information Embrace key Web services technologies for standard IDL, leverage commercial efforts Result = standard interfaces & behaviors for distributed system mgmt: the Grid service u Standardization within Global Grid Forum and OASIS u Open source & commercial implementations Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 26
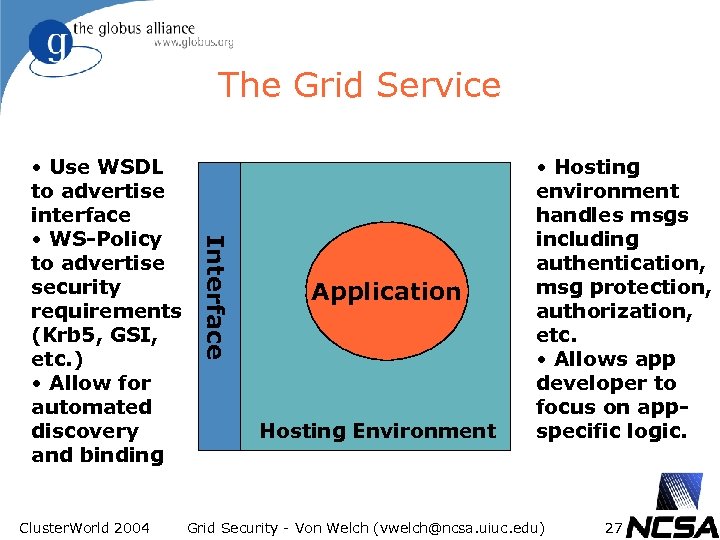 The Grid Service Cluster. World 2004 Interface • Use WSDL to advertise interface • WS-Policy to advertise security requirements (Krb 5, GSI, etc. ) • Allow for automated discovery and binding Application Hosting Environment • Hosting environment handles msgs including authentication, msg protection, authorization, etc. • Allows app developer to focus on appspecific logic. Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 27
The Grid Service Cluster. World 2004 Interface • Use WSDL to advertise interface • WS-Policy to advertise security requirements (Krb 5, GSI, etc. ) • Allow for automated discovery and binding Application Hosting Environment • Hosting environment handles msgs including authentication, msg protection, authorization, etc. • Allows app developer to focus on appspecific logic. Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 27
 Based on Standards l Web Services u u l SOAP WSDL Extensions (follow-on to OGSI) u WSRF l u Lifetime control WS-Resource. Properties l Expose state u WS-Notification u WS-Service. Group u WS-Renewable. Reference Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 28
Based on Standards l Web Services u u l SOAP WSDL Extensions (follow-on to OGSI) u WSRF l u Lifetime control WS-Resource. Properties l Expose state u WS-Notification u WS-Service. Group u WS-Renewable. Reference Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 28
 Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 29
Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 29
 Leverage existing/emerging Security Standards l l l WS-Security/Policy/Trust/Federation/ Authorization/Secure. Conversation/Privacy XKMS, XML-Signature/Encryption, SAML, XACML, Xr. ML But… u u u Need to OGSA’fy Need to define Profile/Mechanisms Need to define Naming conventions Need to address late/missing specs Support for delegation, transient services Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 30
Leverage existing/emerging Security Standards l l l WS-Security/Policy/Trust/Federation/ Authorization/Secure. Conversation/Privacy XKMS, XML-Signature/Encryption, SAML, XACML, Xr. ML But… u u u Need to OGSA’fy Need to define Profile/Mechanisms Need to define Naming conventions Need to address late/missing specs Support for delegation, transient services Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 30
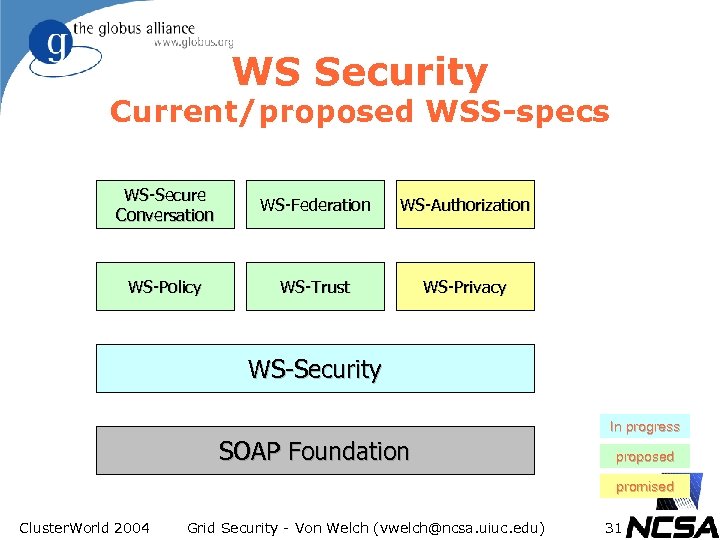 WS Security Current/proposed WSS-specs WS-Secure Conversation WS-Federation WS-Authorization WS-Policy WS-Trust WS-Privacy WS-Security In progress SOAP Foundation proposed promised Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 31
WS Security Current/proposed WSS-specs WS-Secure Conversation WS-Federation WS-Authorization WS-Policy WS-Trust WS-Privacy WS-Security In progress SOAP Foundation proposed promised Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 31
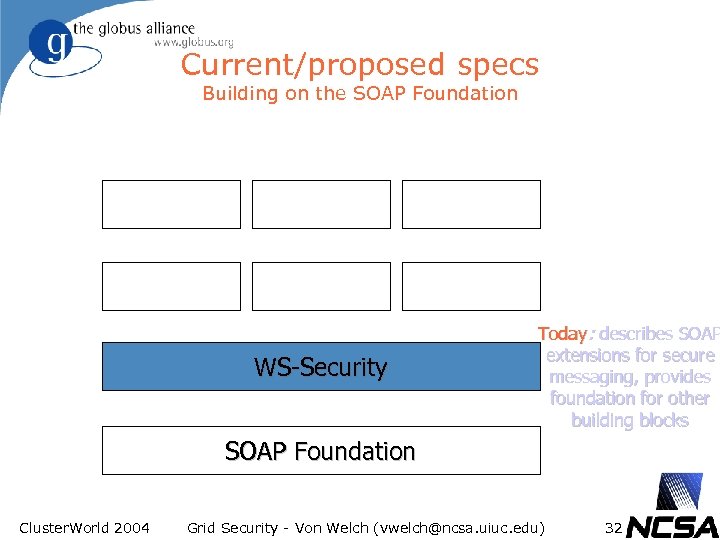 Current/proposed specs Building on the SOAP Foundation WS-Security Today: describes SOAP extensions for secure messaging, provides foundation for other building blocks SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 32
Current/proposed specs Building on the SOAP Foundation WS-Security Today: describes SOAP extensions for secure messaging, provides foundation for other building blocks SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 32
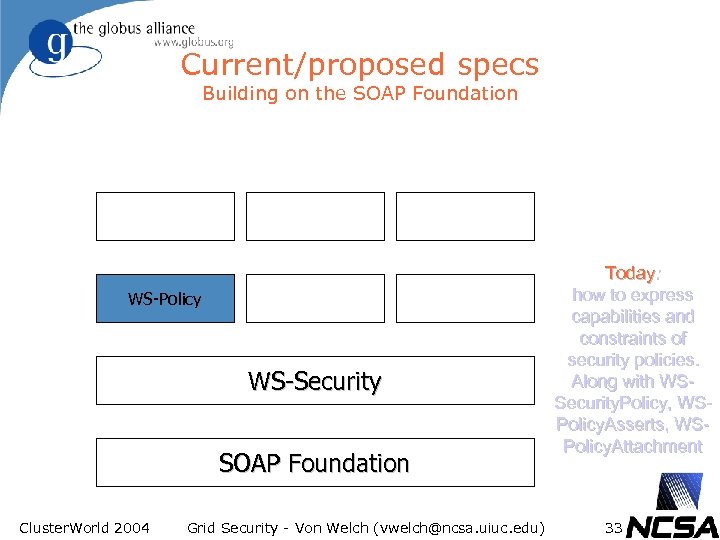 Current/proposed specs Building on the SOAP Foundation WS-Policy WS-Security SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) Today: how to express capabilities and constraints of security policies. Along with WSSecurity. Policy, WSPolicy. Asserts, WSPolicy. Attachment 33
Current/proposed specs Building on the SOAP Foundation WS-Policy WS-Security SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) Today: how to express capabilities and constraints of security policies. Along with WSSecurity. Policy, WSPolicy. Asserts, WSPolicy. Attachment 33
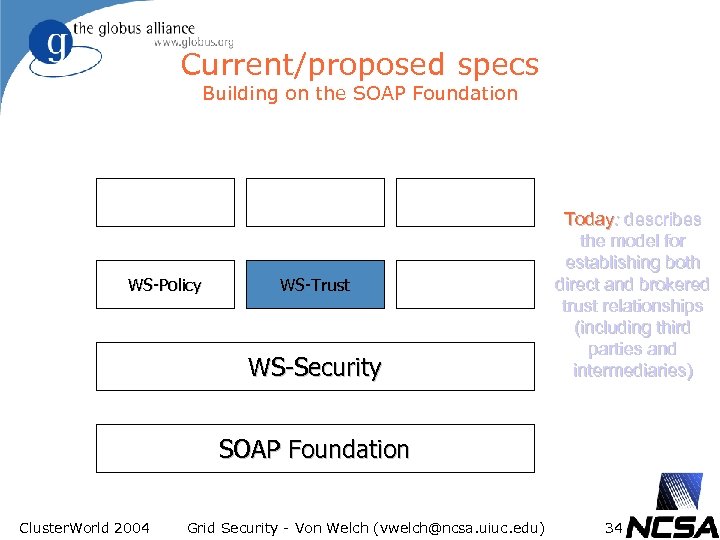 Current/proposed specs Building on the SOAP Foundation WS-Policy WS-Trust WS-Security Today: describes the model for establishing both direct and brokered trust relationships (including third parties and intermediaries) SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 34
Current/proposed specs Building on the SOAP Foundation WS-Policy WS-Trust WS-Security Today: describes the model for establishing both direct and brokered trust relationships (including third parties and intermediaries) SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 34
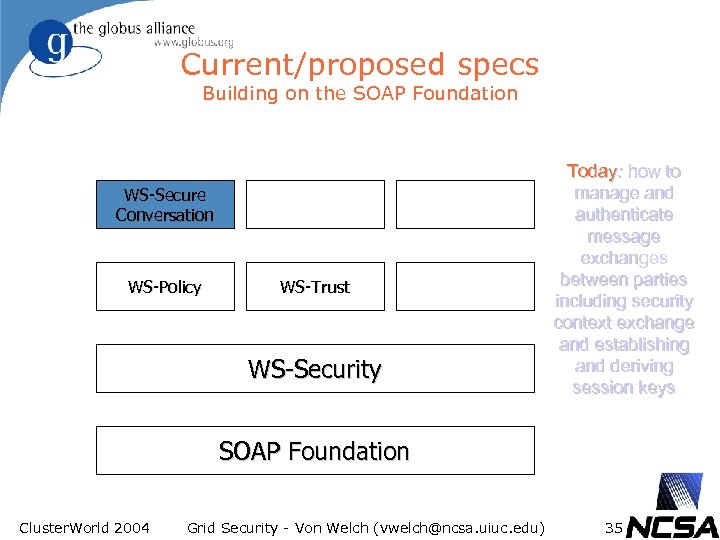 Current/proposed specs Building on the SOAP Foundation WS-Secure Conversation WS-Policy WS-Trust WS-Security Today: how to manage and authenticate message exchanges between parties including security context exchange and establishing and deriving session keys SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 35
Current/proposed specs Building on the SOAP Foundation WS-Secure Conversation WS-Policy WS-Trust WS-Security Today: how to manage and authenticate message exchanges between parties including security context exchange and establishing and deriving session keys SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 35
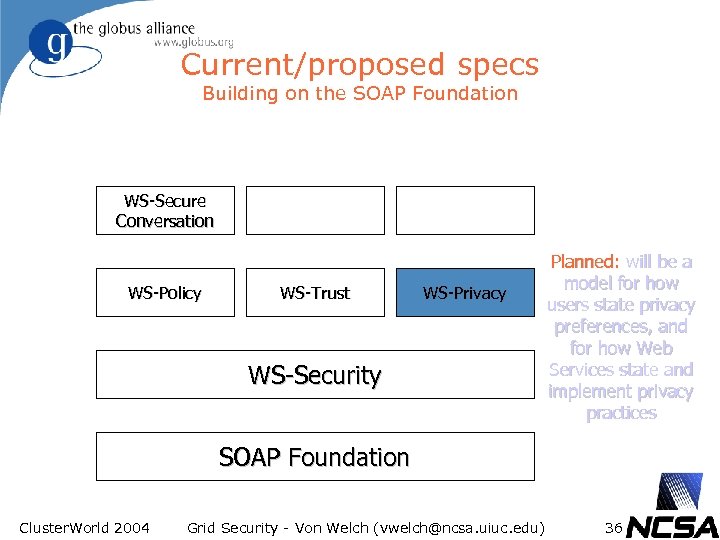 Current/proposed specs Building on the SOAP Foundation WS-Secure Conversation WS-Policy WS-Trust WS-Privacy WS-Security Planned: will be a model for how users state privacy preferences, and for how Web Services state and implement privacy practices SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 36
Current/proposed specs Building on the SOAP Foundation WS-Secure Conversation WS-Policy WS-Trust WS-Privacy WS-Security Planned: will be a model for how users state privacy preferences, and for how Web Services state and implement privacy practices SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 36
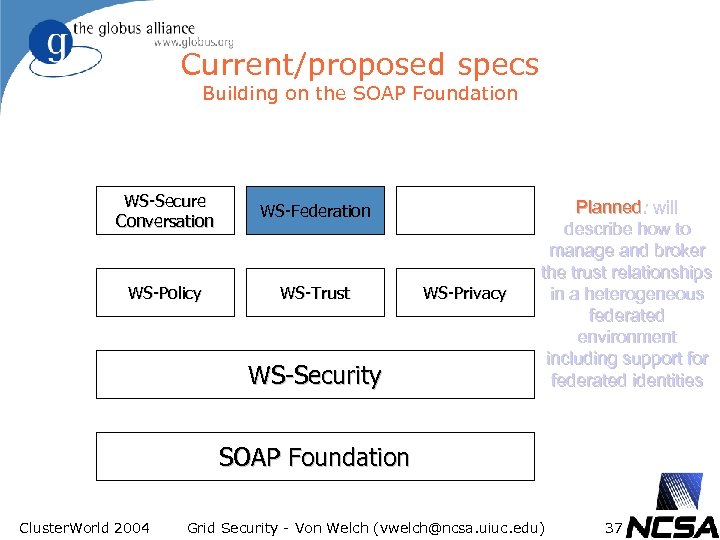 Current/proposed specs Building on the SOAP Foundation WS-Secure Conversation WS-Federation WS-Policy WS-Trust WS-Security WS-Privacy Planned: will describe how to manage and broker the trust relationships in a heterogeneous federated environment including support for federated identities SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 37
Current/proposed specs Building on the SOAP Foundation WS-Secure Conversation WS-Federation WS-Policy WS-Trust WS-Security WS-Privacy Planned: will describe how to manage and broker the trust relationships in a heterogeneous federated environment including support for federated identities SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 37
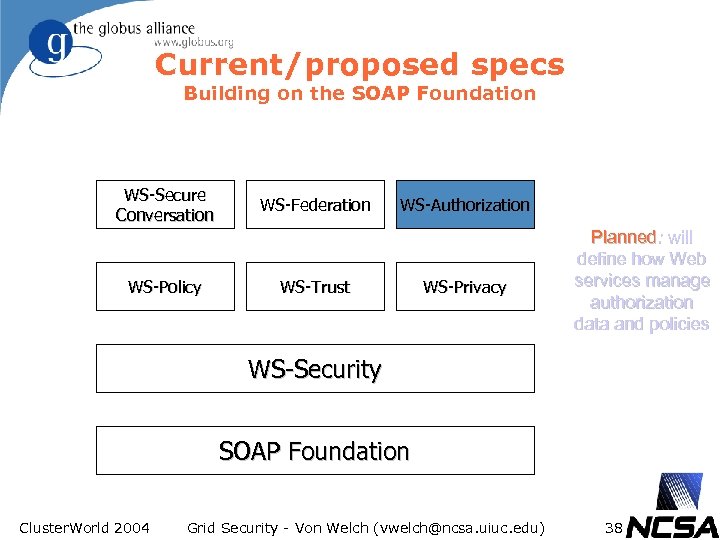 Current/proposed specs Building on the SOAP Foundation WS-Secure Conversation WS-Policy WS-Federation WS-Authorization WS-Trust WS-Privacy Planned: will define how Web services manage authorization data and policies WS-Security SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 38
Current/proposed specs Building on the SOAP Foundation WS-Secure Conversation WS-Policy WS-Federation WS-Authorization WS-Trust WS-Privacy Planned: will define how Web services manage authorization data and policies WS-Security SOAP Foundation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 38
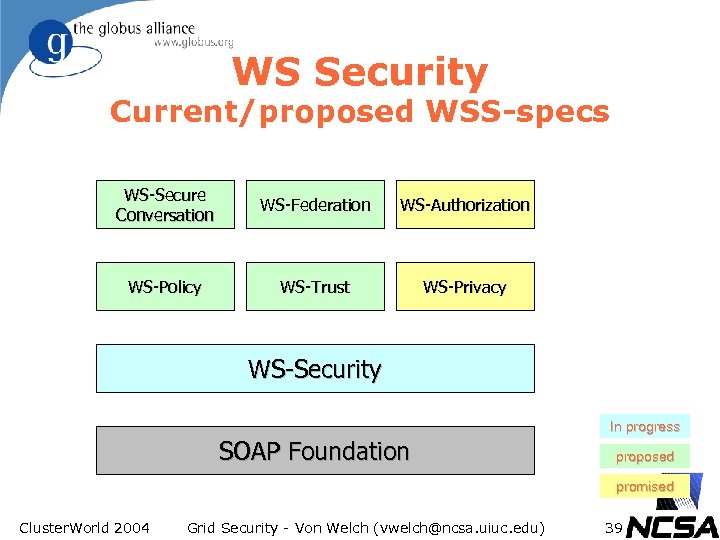 WS Security Current/proposed WSS-specs WS-Secure Conversation WS-Federation WS-Authorization WS-Policy WS-Trust WS-Privacy WS-Security In progress SOAP Foundation proposed promised Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 39
WS Security Current/proposed WSS-specs WS-Secure Conversation WS-Federation WS-Authorization WS-Policy WS-Trust WS-Privacy WS-Security In progress SOAP Foundation proposed promised Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 39
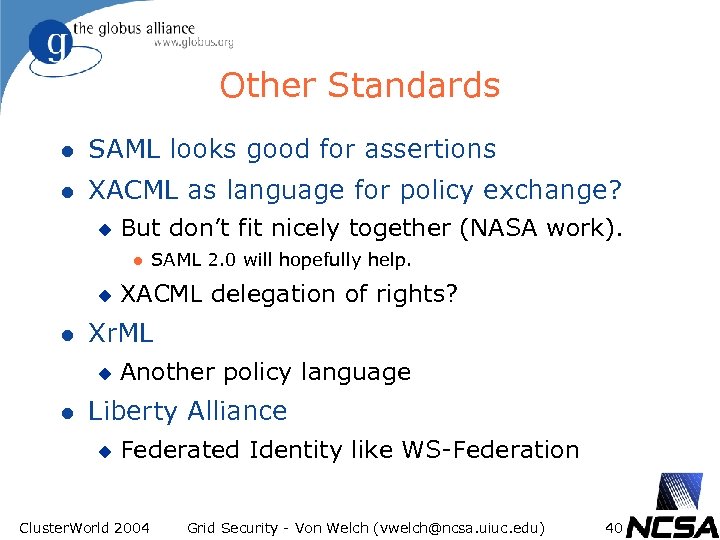 Other Standards l SAML looks good for assertions l XACML as language for policy exchange? u But don’t fit nicely together (NASA work). l u l XACML delegation of rights? Xr. ML u l SAML 2. 0 will hopefully help. Another policy language Liberty Alliance u Federated Identity like WS-Federation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 40
Other Standards l SAML looks good for assertions l XACML as language for policy exchange? u But don’t fit nicely together (NASA work). l u l XACML delegation of rights? Xr. ML u l SAML 2. 0 will hopefully help. Another policy language Liberty Alliance u Federated Identity like WS-Federation Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 40
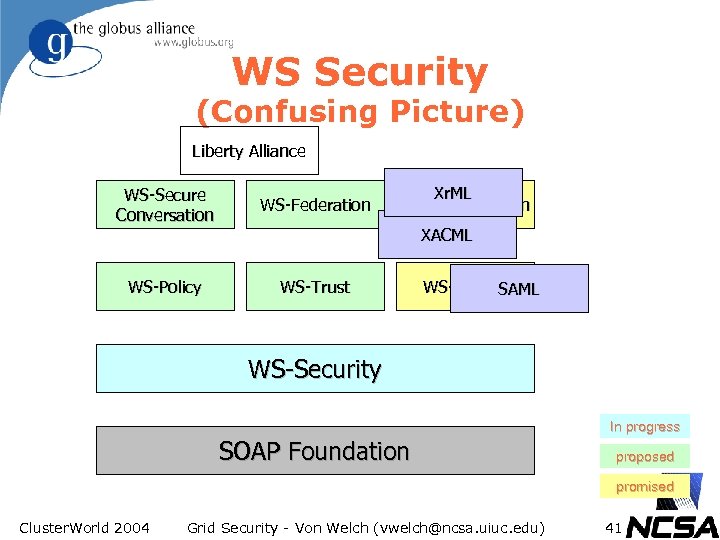 WS Security (Confusing Picture) Liberty Alliance WS-Secure Conversation WS-Federation WS-Policy Xr. ML WS-Authorization WS-Trust XACML WS-Privacy SAML WS-Security In progress SOAP Foundation proposed promised Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 41
WS Security (Confusing Picture) Liberty Alliance WS-Secure Conversation WS-Federation WS-Policy Xr. ML WS-Authorization WS-Trust XACML WS-Privacy SAML WS-Security In progress SOAP Foundation proposed promised Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 41
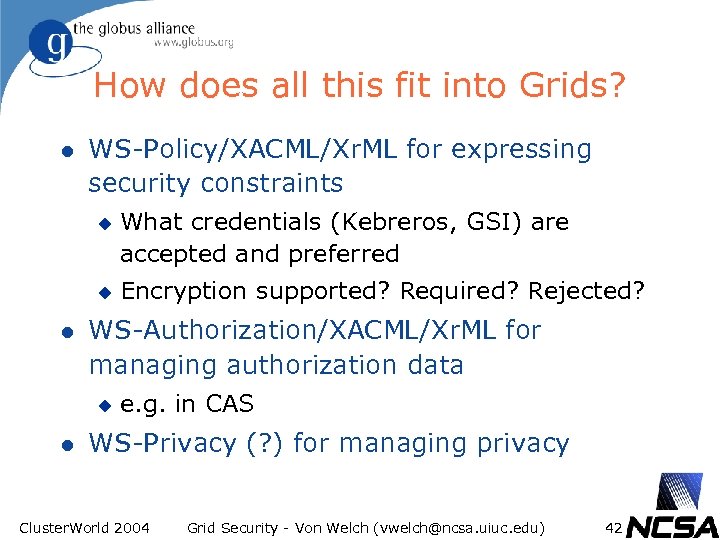 How does all this fit into Grids? l WS-Policy/XACML/Xr. ML for expressing security constraints u u l Encryption supported? Required? Rejected? WS-Authorization/XACML/Xr. ML for managing authorization data u l What credentials (Kebreros, GSI) are accepted and preferred e. g. in CAS WS-Privacy (? ) for managing privacy Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 42
How does all this fit into Grids? l WS-Policy/XACML/Xr. ML for expressing security constraints u u l Encryption supported? Required? Rejected? WS-Authorization/XACML/Xr. ML for managing authorization data u l What credentials (Kebreros, GSI) are accepted and preferred e. g. in CAS WS-Privacy (? ) for managing privacy Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 42
 OGSA Security Roadmap Goal l l Address the Grid Security Architecture Requirements Make Implementations Possible Address Interoperability Address Pluggability/Replaceability Address missing/late/insufficient Standards “OGSA Security Roadmap” submitted to GGF – co-authored with IBM Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 43
OGSA Security Roadmap Goal l l Address the Grid Security Architecture Requirements Make Implementations Possible Address Interoperability Address Pluggability/Replaceability Address missing/late/insufficient Standards “OGSA Security Roadmap” submitted to GGF – co-authored with IBM Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 43
 OGSA Security l Security implemented by pluggable security services u l Usable by clients and services Allow for more agnostic approach to security mechanisms u u As implementations are created for a mechanism they can be plugged into existing tools to enable use. Applications and services can examine published security policies and convert/acquire credentials as needed Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 44
OGSA Security l Security implemented by pluggable security services u l Usable by clients and services Allow for more agnostic approach to security mechanisms u u As implementations are created for a mechanism they can be plugged into existing tools to enable use. Applications and services can examine published security policies and convert/acquire credentials as needed Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 44
 Remove Security from Applications l l l Allow deployment-time selection of supported mechanisms and policies OGSA resource virtualization allows for policy on application-independent operation invocation Place as much security functionality as possible into sophisticated hosting environments Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 45
Remove Security from Applications l l l Allow deployment-time selection of supported mechanisms and policies OGSA resource virtualization allows for policy on application-independent operation invocation Place as much security functionality as possible into sophisticated hosting environments Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 45
 Transparent Call-outs from WS-Stubs Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 46
Transparent Call-outs from WS-Stubs Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 46
 Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 47
Outline l Some quick terminology l What is Grid Security? l Current State of the Art l OGSA Grid Evolution l OGSA Security and Web Services Security l Globus Toolkit Implementation and Futures Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 47
 What’s actually in GT 3? l SOAP-based wire protocol l WS-Security (XML-Signature, XML-Encryption) for authentication, message protection l GSI-Secure. Conversation u u u Based on GT 2’s TLS/GSSAPI implementation Based on a poor-man’s “interpretation” of WS-Trust/WS-Secure. Conversation specs plus XML-Signature/XML-Encryption/WS-Security Waiting for WS-Trust & WS-Secure. Conversation & WS-Kerberos specs to be submitted to standards body Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 48
What’s actually in GT 3? l SOAP-based wire protocol l WS-Security (XML-Signature, XML-Encryption) for authentication, message protection l GSI-Secure. Conversation u u u Based on GT 2’s TLS/GSSAPI implementation Based on a poor-man’s “interpretation” of WS-Trust/WS-Secure. Conversation specs plus XML-Signature/XML-Encryption/WS-Security Waiting for WS-Trust & WS-Secure. Conversation & WS-Kerberos specs to be submitted to standards body Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 48
 What’s Actually in GT 3? l SAML assertions in Community Authorization Service (GT 3. 2) u Allow VOs to set and distribute policy on file access l Standardized Proxy Certificates l Java and C implementations l Java based on Axis with security implemented in handlers Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 49
What’s Actually in GT 3? l SAML assertions in Community Authorization Service (GT 3. 2) u Allow VOs to set and distribute policy on file access l Standardized Proxy Certificates l Java and C implementations l Java based on Axis with security implemented in handlers Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 49
 GT Security Futures (1) l Authorization is “KEY” for the coming year u Includes communicating/sharing/matching of authz-policies and capabilities u u Standards for authorization services u l Profiles for Attributes GGF OGSA Authorization WG Restricted Delegation u By service and operation u By “domains” Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 50
GT Security Futures (1) l Authorization is “KEY” for the coming year u Includes communicating/sharing/matching of authz-policies and capabilities u u Standards for authorization services u l Profiles for Attributes GGF OGSA Authorization WG Restricted Delegation u By service and operation u By “domains” Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 50
 GT Security Futures (2) l Securely route through firewalls/networkhurdles u l Integration of Group authentication/keyexchange protocols u l Tackle the firewall/NAT traversal issues transparently in the runtime Going from 2 parties to N parties should be “seamless” Secure Logging and Audit u Another undefined, unstandardized missing link… while the requirements are there! Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 51
GT Security Futures (2) l Securely route through firewalls/networkhurdles u l Integration of Group authentication/keyexchange protocols u l Tackle the firewall/NAT traversal issues transparently in the runtime Going from 2 parties to N parties should be “seamless” Secure Logging and Audit u Another undefined, unstandardized missing link… while the requirements are there! Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 51
 Conclusion l Grid’s requirements maybe few years ahead, but industry will face same challenges soon u l Our security requirements are conceptually 1 -2 levels above what is available now as specifications, standards and open source u l And distracting and time consuming… Come help us at the Global Grid Forum u u l Ideally, we want to be end-users of WSS not plumbers… The standards circus is very worrisome u l Few “new” distributed computing requirements… Exciting security stuff! We need your help… (www. ggf. org) Play with the Globus Toolkit (GT 3. 2) u Downloaded 100 k+ times already Cluster. World 2004 (www. globus. org) Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 52
Conclusion l Grid’s requirements maybe few years ahead, but industry will face same challenges soon u l Our security requirements are conceptually 1 -2 levels above what is available now as specifications, standards and open source u l And distracting and time consuming… Come help us at the Global Grid Forum u u l Ideally, we want to be end-users of WSS not plumbers… The standards circus is very worrisome u l Few “new” distributed computing requirements… Exciting security stuff! We need your help… (www. ggf. org) Play with the Globus Toolkit (GT 3. 2) u Downloaded 100 k+ times already Cluster. World 2004 (www. globus. org) Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 52
 Thanks l Many colleagues at Argonne, NCSA, ISI & PDC: u l Frank Siebenlist, Sam Meder, Olle Mulmo, Leaur Pearlman, Jarek Garow, Jim Basney, Steve Tuecke, Ian Foster, Carl Kesselman, Rachana Ananthakrishnan and many others. Funding from DOE, NSF and IBM Questions? Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 53
Thanks l Many colleagues at Argonne, NCSA, ISI & PDC: u l Frank Siebenlist, Sam Meder, Olle Mulmo, Leaur Pearlman, Jarek Garow, Jim Basney, Steve Tuecke, Ian Foster, Carl Kesselman, Rachana Ananthakrishnan and many others. Funding from DOE, NSF and IBM Questions? Cluster. World 2004 Grid Security - Von Welch (vwelch@ncsa. uiuc. edu) 53


