3bf922c146c507c3327e0b6a566bad13.ppt
- Количество слайдов: 44
 Grid Security & the EUGrid. PMA EIROforum GG Meeting David Groep, EUGrid. PMA Chair, 2005. 09. 14
Grid Security & the EUGrid. PMA EIROforum GG Meeting David Groep, EUGrid. PMA Chair, 2005. 09. 14
 Outline Grid Security Infrastructure · Virtual Organisations · Authentication vs. Authorisation Authentication Federation · · EUGrid. PMA Trust Basis and Minimum Requirements International Grid Trust Federation Roadmap Authorization Federation … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 2
Outline Grid Security Infrastructure · Virtual Organisations · Authentication vs. Authorisation Authentication Federation · · EUGrid. PMA Trust Basis and Minimum Requirements International Grid Trust Federation Roadmap Authorization Federation … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 2
 Grid Security Requirements · Control access to shared services · Initial focus on high-value resources: supercomputers, large clusters, multi-Peta. Byte storage · Support multi-user collaborations · Composed of individuals acting alone – their home organisation administration may not know about their activities · Allow users/application communities to establish relations · Both personal and community-based aggregation of resources, based on personal or community-mediated trust · Easy to use · single sign-on for users · David Groep – davidg@eugridpma. org Resource Owner Always Stays EIROforum GG meeting – Sept 2005 - 4 in Control
Grid Security Requirements · Control access to shared services · Initial focus on high-value resources: supercomputers, large clusters, multi-Peta. Byte storage · Support multi-user collaborations · Composed of individuals acting alone – their home organisation administration may not know about their activities · Allow users/application communities to establish relations · Both personal and community-based aggregation of resources, based on personal or community-mediated trust · Easy to use · single sign-on for users · David Groep – davidg@eugridpma. org Resource Owner Always Stays EIROforum GG meeting – Sept 2005 - 4 in Control
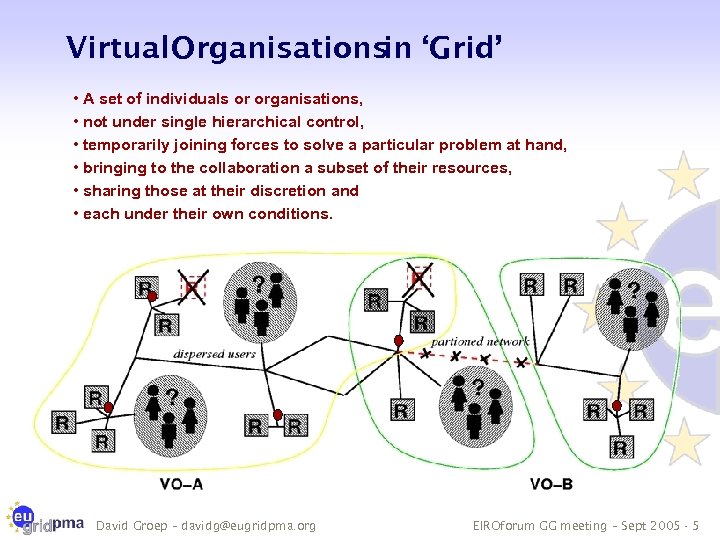 Virtual Organisationsin ‘Grid’ • A set of individuals or organisations, • not under single hierarchical control, • temporarily joining forces to solve a particular problem at hand, • bringing to the collaboration a subset of their resources, • sharing those at their discretion and • each under their own conditions. David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 5
Virtual Organisationsin ‘Grid’ • A set of individuals or organisations, • not under single hierarchical control, • temporarily joining forces to solve a particular problem at hand, • bringing to the collaboration a subset of their resources, • sharing those at their discretion and • each under their own conditions. David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 5
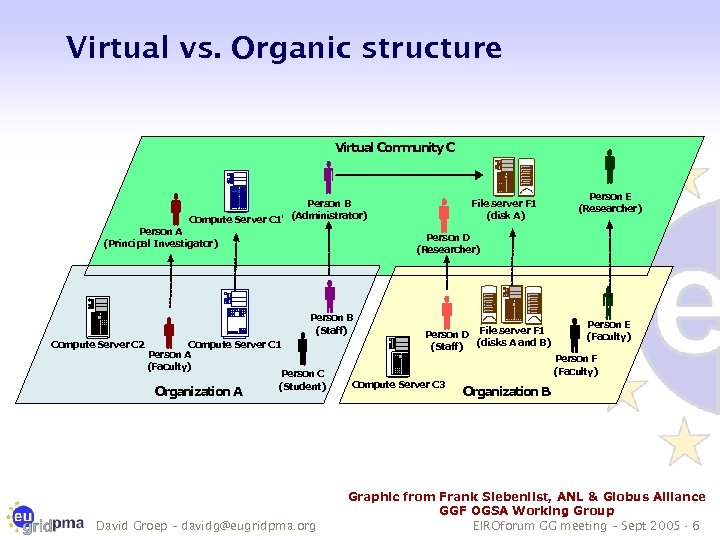 Virtual vs. Organic structure Virtual Com unity C m File server F 1 (disk A) Person B (Administrator) Compute Server C 1' Person A (Principal Investigator) Person D (Researcher) Person B (Staff) Compute Server C 2 Person E (Researcher) Compute Server C 1 Person A (Faculty) Person C (Student) Organization A David Groep – davidg@eugridpma. org Person D File server F 1 (Staff) (disks A and B) Person E (Faculty) Person F (Faculty) Compute Server C 3 Organization B Graphic from Frank Siebenlist, ANL & Globus Alliance GGF OGSA Working Group EIROforum GG meeting – Sept 2005 - 6
Virtual vs. Organic structure Virtual Com unity C m File server F 1 (disk A) Person B (Administrator) Compute Server C 1' Person A (Principal Investigator) Person D (Researcher) Person B (Staff) Compute Server C 2 Person E (Researcher) Compute Server C 1 Person A (Faculty) Person C (Student) Organization A David Groep – davidg@eugridpma. org Person D File server F 1 (Staff) (disks A and B) Person E (Faculty) Person F (Faculty) Compute Server C 3 Organization B Graphic from Frank Siebenlist, ANL & Globus Alliance GGF OGSA Working Group EIROforum GG meeting – Sept 2005 - 6
 Stakeholders in Grid Security · Conceptually, all members of a VO are equal · Users can provide their own services · Resource provider organisations may or may not have personal members (they can just sell resources to a VO) · No a priori trust relationship between members · VO lifetime can vary from hours to decades · People (and resources) usually are members of more than one VO · … but an relation is required · as a basis for authorising access · for traceability and liability · for incident handling, accounting David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 7
Stakeholders in Grid Security · Conceptually, all members of a VO are equal · Users can provide their own services · Resource provider organisations may or may not have personal members (they can just sell resources to a VO) · No a priori trust relationship between members · VO lifetime can vary from hours to decades · People (and resources) usually are members of more than one VO · … but an relation is required · as a basis for authorising access · for traceability and liability · for incident handling, accounting David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 7
 Building Virtual Organisations · VOs today are rather long-lived (but not too difficult to set up) · · · HEP physics experiments (10+ yrs) Earth Observation missions (10+ yrs) Earthquake engineering (10+ yrs) LIGO (Gravitational waves) (10+ yrs? ) Projects-based ‘aggregate working groups’ EGEE bio-medical application area (2+ yr), … · Future is likely to bring many shorter-lived VOs · ad-hoc collaborations of scientists (~weeks) · commercial analysis outsourcing (~days) · … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 8
Building Virtual Organisations · VOs today are rather long-lived (but not too difficult to set up) · · · HEP physics experiments (10+ yrs) Earth Observation missions (10+ yrs) Earthquake engineering (10+ yrs) LIGO (Gravitational waves) (10+ yrs? ) Projects-based ‘aggregate working groups’ EGEE bio-medical application area (2+ yr), … · Future is likely to bring many shorter-lived VOs · ad-hoc collaborations of scientists (~weeks) · commercial analysis outsourcing (~days) · … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 8
 VO embedding today · as part of a Grid ‘ecosystem’ where ecosystem takes care of end-to-end solution · Middleware · User support · ‘Infrastructure’ (a collective of Resource Centres) · a single VO per project user groups join up together and participate in a single project · Implicit sharing agreement between users and centres · sharing across all user communities in the project · ‘non-aligned’ VOs · need to build their own hosting environment · maybe supported by a ‘big’ partner from another ecosystem David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 9
VO embedding today · as part of a Grid ‘ecosystem’ where ecosystem takes care of end-to-end solution · Middleware · User support · ‘Infrastructure’ (a collective of Resource Centres) · a single VO per project user groups join up together and participate in a single project · Implicit sharing agreement between users and centres · sharing across all user communities in the project · ‘non-aligned’ VOs · need to build their own hosting environment · maybe supported by a ‘big’ partner from another ecosystem David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 9
 Many Grid Sites Need Interoperation · In Europe · Enabling Grid for E-scienc. E (EGEE) (~160 sites) · Distributed European Infrastructure for Supercomputer Applications (DEISA) (~15 sites) · South East European Grid (SEE-GRID) (~30 sites) · many national projects (VL-e, D-Grid, UK e-Science) · In the US · Open Science Grid (OSG) (~40 sites) · Tera. Grid (~5 sites) · also many others, like NEESGRID, NASA IPG, … · Asia-Pacific · AP Grid (~10? ) · Pacific Rim Applications and Grid Middleware Assembly (~15? ) · … · LHC Computing Grid Project (global) (~160) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 10
Many Grid Sites Need Interoperation · In Europe · Enabling Grid for E-scienc. E (EGEE) (~160 sites) · Distributed European Infrastructure for Supercomputer Applications (DEISA) (~15 sites) · South East European Grid (SEE-GRID) (~30 sites) · many national projects (VL-e, D-Grid, UK e-Science) · In the US · Open Science Grid (OSG) (~40 sites) · Tera. Grid (~5 sites) · also many others, like NEESGRID, NASA IPG, … · Asia-Pacific · AP Grid (~10? ) · Pacific Rim Applications and Grid Middleware Assembly (~15? ) · … · LHC Computing Grid Project (global) (~160) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 10
 Separating. Auth. N from Auth. Z · Single Authentication token (“passport”) · · · issued by a trustworthy third party, recognised by many resource providers, users, and VOs satisfies traceability requirement in itself does not grant any access but provides high-quality unique binding between an identifier and the subject* · X. 509 certificates in a PKI, cryptographically secured · Authorisation (“visa”) · · granted to a person/service or a set of them (a VO) granted by the actual owner (e. g. a site) based on the ‘passport’ name providers define their lists of authorised users & VOs, but can still ban individual users within a VO David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 11
Separating. Auth. N from Auth. Z · Single Authentication token (“passport”) · · · issued by a trustworthy third party, recognised by many resource providers, users, and VOs satisfies traceability requirement in itself does not grant any access but provides high-quality unique binding between an identifier and the subject* · X. 509 certificates in a PKI, cryptographically secured · Authorisation (“visa”) · · granted to a person/service or a set of them (a VO) granted by the actual owner (e. g. a site) based on the ‘passport’ name providers define their lists of authorised users & VOs, but can still ban individual users within a VO David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 11
 Grid Authorization today · Leverages authentication provided by PKI · Identity management decoupled from access control · Creation of short-lived ‘tokens’ (‘proxy’ certificates) for single sign-on based on these identities But: · Variety of mechanisms · Per-resource list of authorized users (“grid-mapfile”) · Directories of authorized users (VO-LDAP) · Embedded assertions (VOMS, CAS) · Variety of sources of authority · Semantics to describe roles and rights differs · No common namespace · Not integrated with other (site) AA mechanisms yet David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 12
Grid Authorization today · Leverages authentication provided by PKI · Identity management decoupled from access control · Creation of short-lived ‘tokens’ (‘proxy’ certificates) for single sign-on based on these identities But: · Variety of mechanisms · Per-resource list of authorized users (“grid-mapfile”) · Directories of authorized users (VO-LDAP) · Embedded assertions (VOMS, CAS) · Variety of sources of authority · Semantics to describe roles and rights differs · No common namespace · Not integrated with other (site) AA mechanisms yet David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 12
 Authentication
Authentication
 Well known X. 509 PKIs · Secure web servers (‘https’) based on PKI · Various commercial providers · Entrust, Thawte, Verisign, Swiss. Sign, … · Usually expensive but don’t actually subsume liability … … a rogue person obtained a certificate from Verisign asserting he was from Microsoft … · Are implicitly trusted by many, since web browsers pre-install the roots of trust … but did you ever check the policies of all those CAs? · But use of commercial CAs solves the ‘pop-up’ problem. . . so for (web) servers we would still need a pop-up free service · National (government) PKIs · Slow in the uptake of the 1999/93/EC for the average citizen (but Estonia is now there!) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 14
Well known X. 509 PKIs · Secure web servers (‘https’) based on PKI · Various commercial providers · Entrust, Thawte, Verisign, Swiss. Sign, … · Usually expensive but don’t actually subsume liability … … a rogue person obtained a certificate from Verisign asserting he was from Microsoft … · Are implicitly trusted by many, since web browsers pre-install the roots of trust … but did you ever check the policies of all those CAs? · But use of commercial CAs solves the ‘pop-up’ problem. . . so for (web) servers we would still need a pop-up free service · National (government) PKIs · Slow in the uptake of the 1999/93/EC for the average citizen (but Estonia is now there!) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 14
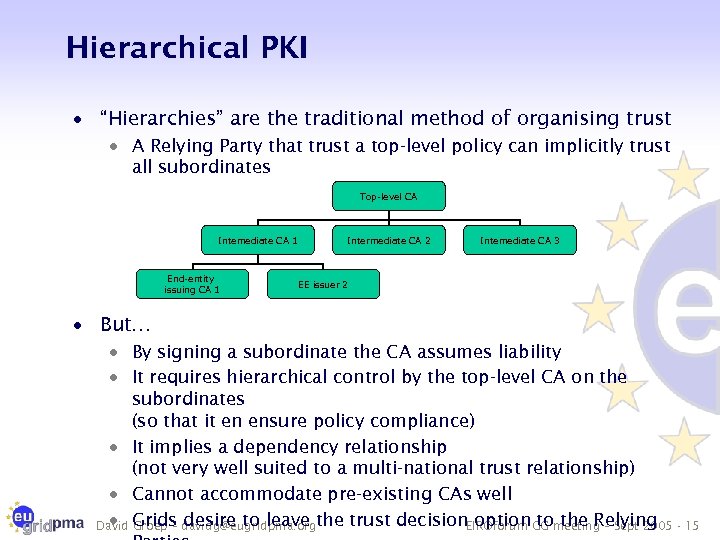 Hierarchical PKI · “Hierarchies” are the traditional method of organising trust · A Relying Party that trust a top-level policy can implicitly trust all subordinates Top-level CA Intemediate CA 1 End-entity issuing CA 1 Intermediate CA 2 Intemediate CA 3 EE issuer 2 · But… · By signing a subordinate the CA assumes liability · It requires hierarchical control by the top-level CA on the subordinates (so that it en ensure policy compliance) · It implies a dependency relationship (not very well suited to a multi-national trust relationship) · Cannot accommodate pre-existing CAs well · Groep – desire to leave David Grids davidg@eugridpma. orgthe trust decision option GG meeting – Sept 2005 - 15 EIROforum to the Relying
Hierarchical PKI · “Hierarchies” are the traditional method of organising trust · A Relying Party that trust a top-level policy can implicitly trust all subordinates Top-level CA Intemediate CA 1 End-entity issuing CA 1 Intermediate CA 2 Intemediate CA 3 EE issuer 2 · But… · By signing a subordinate the CA assumes liability · It requires hierarchical control by the top-level CA on the subordinates (so that it en ensure policy compliance) · It implies a dependency relationship (not very well suited to a multi-national trust relationship) · Cannot accommodate pre-existing CAs well · Groep – desire to leave David Grids davidg@eugridpma. orgthe trust decision option GG meeting – Sept 2005 - 15 EIROforum to the Relying
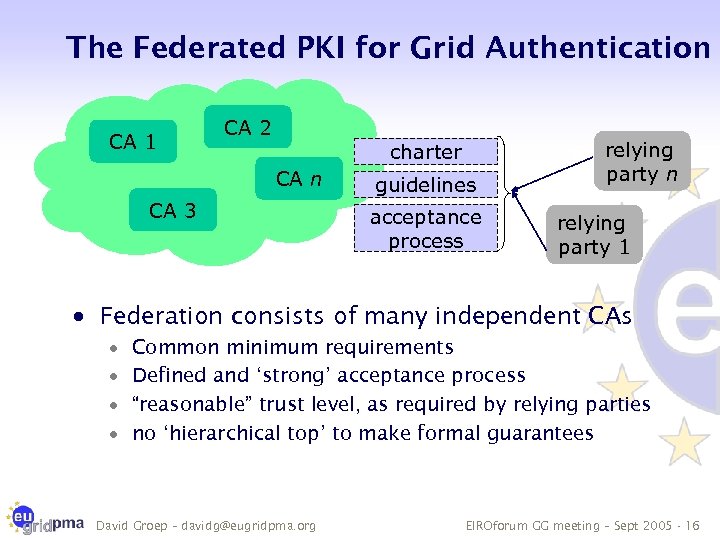 The Federated PKI for Grid Authentication CA 1 CA 2 charter CA n CA 3 guidelines acceptance process relying party n relying party 1 · Federation consists of many independent CAs · · Common minimum requirements Defined and ‘strong’ acceptance process “reasonable” trust level, as required by relying parties no ‘hierarchical top’ to make formal guarantees David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 16
The Federated PKI for Grid Authentication CA 1 CA 2 charter CA n CA 3 guidelines acceptance process relying party n relying party 1 · Federation consists of many independent CAs · · Common minimum requirements Defined and ‘strong’ acceptance process “reasonable” trust level, as required by relying parties no ‘hierarchical top’ to make formal guarantees David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 16
 Building the federation · PKI providers (‘CAs’) and Relying Parties (‘sites’) together shape minimum requirements (‘guidelines’) · Authorities testify compliance with these guidelines · Peer-review process within the federation to (re) evaluate members on entry & periodically · Reduce effort on the relying parties · single document to review and assess for all CAs · Reduce cost on the CAs: · no audit statement needed by certified accountants · but participation in the federation does come with a price · Requires that the federation remains manageable in size · David Groep – davidg@eugridpma. org Ultimate decision always remains with meeting. RP 2005 - 17 EIROforum GG the – Sept
Building the federation · PKI providers (‘CAs’) and Relying Parties (‘sites’) together shape minimum requirements (‘guidelines’) · Authorities testify compliance with these guidelines · Peer-review process within the federation to (re) evaluate members on entry & periodically · Reduce effort on the relying parties · single document to review and assess for all CAs · Reduce cost on the CAs: · no audit statement needed by certified accountants · but participation in the federation does come with a price · Requires that the federation remains manageable in size · David Groep – davidg@eugridpma. org Ultimate decision always remains with meeting. RP 2005 - 17 EIROforum GG the – Sept
 Relying Party issues to be addressed Relying Party requests: 1. standard accreditation profiles sufficient to assure approximate parity in CAs 2. monitor [] signing namespaces for name overlaps 3. a forum [to] participate and raise issues 4. [operation of] a secure collection point for information about CAs which you accredit 5. common practices where possible [list courtesy of the Open Science Grid] David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 18
Relying Party issues to be addressed Relying Party requests: 1. standard accreditation profiles sufficient to assure approximate parity in CAs 2. monitor [] signing namespaces for name overlaps 3. a forum [to] participate and raise issues 4. [operation of] a secure collection point for information about CAs which you accredit 5. common practices where possible [list courtesy of the Open Science Grid] David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 18
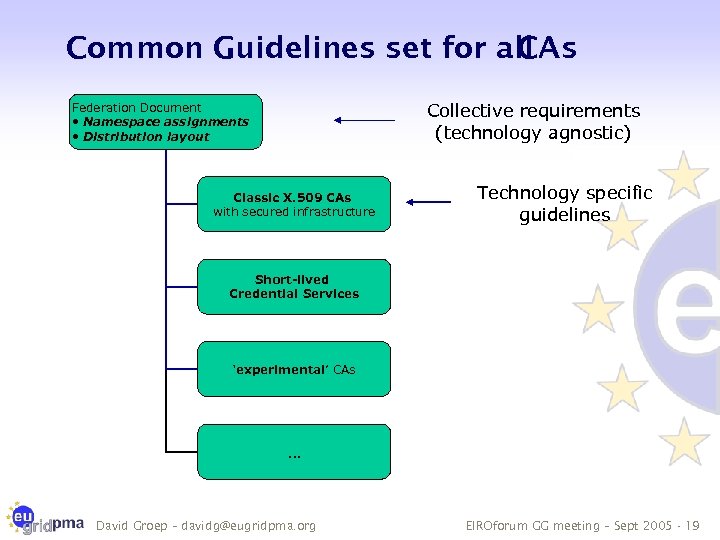 Common Guidelines set for all CAs Collective requirements (technology agnostic) Federation Document • Namespace assignments • Distribution layout Classic X. 509 CAs with secured infrastructure Technology specific guidelines Short-lived Credential Services ‘experimental’ CAs … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 19
Common Guidelines set for all CAs Collective requirements (technology agnostic) Federation Document • Namespace assignments • Distribution layout Classic X. 509 CAs with secured infrastructure Technology specific guidelines Short-lived Credential Services ‘experimental’ CAs … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 19
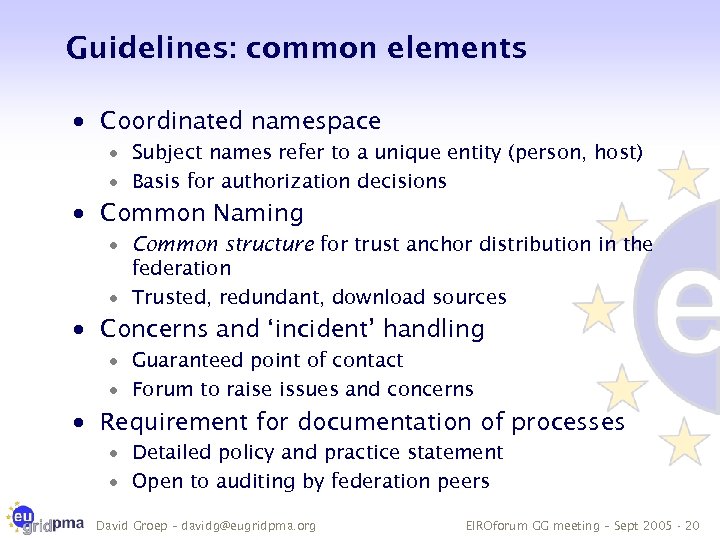 Guidelines: common elements · Coordinated namespace · Subject names refer to a unique entity (person, host) · Basis for authorization decisions · Common Naming · Common structure for trust anchor distribution in the federation · Trusted, redundant, download sources · Concerns and ‘incident’ handling · Guaranteed point of contact · Forum to raise issues and concerns · Requirement for documentation of processes · Detailed policy and practice statement · Open to auditing by federation peers David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 20
Guidelines: common elements · Coordinated namespace · Subject names refer to a unique entity (person, host) · Basis for authorization decisions · Common Naming · Common structure for trust anchor distribution in the federation · Trusted, redundant, download sources · Concerns and ‘incident’ handling · Guaranteed point of contact · Forum to raise issues and concerns · Requirement for documentation of processes · Detailed policy and practice statement · Open to auditing by federation peers David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 20
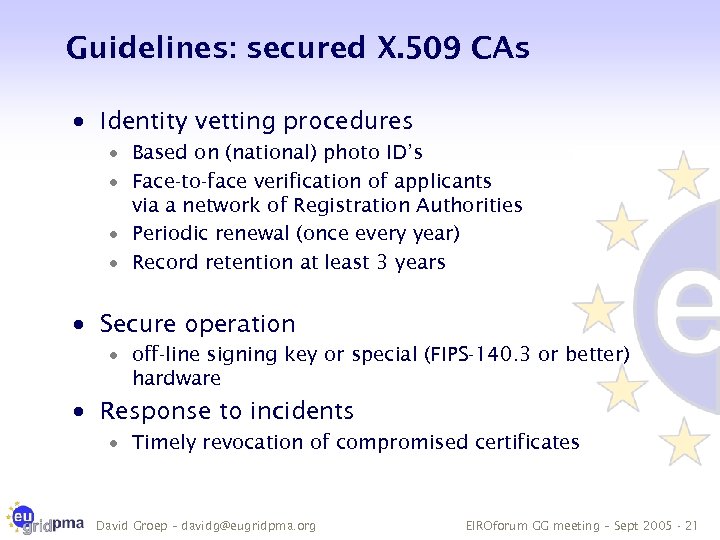 Guidelines: secured X. 509 CAs · Identity vetting procedures · Based on (national) photo ID’s · Face-to-face verification of applicants via a network of Registration Authorities · Periodic renewal (once every year) · Record retention at least 3 years · Secure operation · off-line signing key or special (FIPS-140. 3 or better) hardware · Response to incidents · Timely revocation of compromised certificates David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 21
Guidelines: secured X. 509 CAs · Identity vetting procedures · Based on (national) photo ID’s · Face-to-face verification of applicants via a network of Registration Authorities · Periodic renewal (once every year) · Record retention at least 3 years · Secure operation · off-line signing key or special (FIPS-140. 3 or better) hardware · Response to incidents · Timely revocation of compromised certificates David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 21
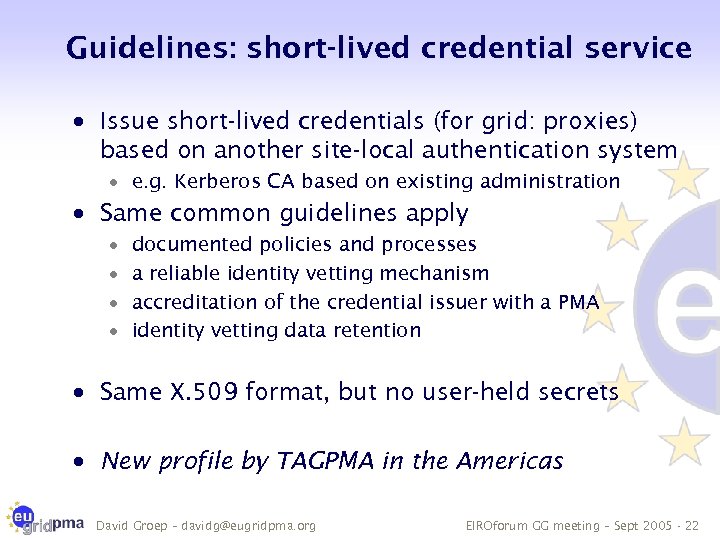 Guidelines: short-lived credential service · Issue short-lived credentials (for grid: proxies) based on another site-local authentication system · e. g. Kerberos CA based on existing administration · Same common guidelines apply · · documented policies and processes a reliable identity vetting mechanism accreditation of the credential issuer with a PMA identity vetting data retention · Same X. 509 format, but no user-held secrets · New profile by TAGPMA in the Americas David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 22
Guidelines: short-lived credential service · Issue short-lived credentials (for grid: proxies) based on another site-local authentication system · e. g. Kerberos CA based on existing administration · Same common guidelines apply · · documented policies and processes a reliable identity vetting mechanism accreditation of the credential issuer with a PMA identity vetting data retention · Same X. 509 format, but no user-held secrets · New profile by TAGPMA in the Americas David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 22
 Guidelines: ‘Active Certificate Stores’ · Secure key/cert storage for end-users · Protected by alternative means · by checking identity with the home organisation · via one-time pads issued by the credential store · … · Backed by a “traditional” CA · Releases short-lived tokens (RFC 3820 “proxy” certs) · ACS hosted by a trusted party (CA, NREN, Operations Center, …) Profile yet to be written David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 23
Guidelines: ‘Active Certificate Stores’ · Secure key/cert storage for end-users · Protected by alternative means · by checking identity with the home organisation · via one-time pads issued by the credential store · … · Backed by a “traditional” CA · Releases short-lived tokens (RFC 3820 “proxy” certs) · ACS hosted by a trusted party (CA, NREN, Operations Center, …) Profile yet to be written David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 23
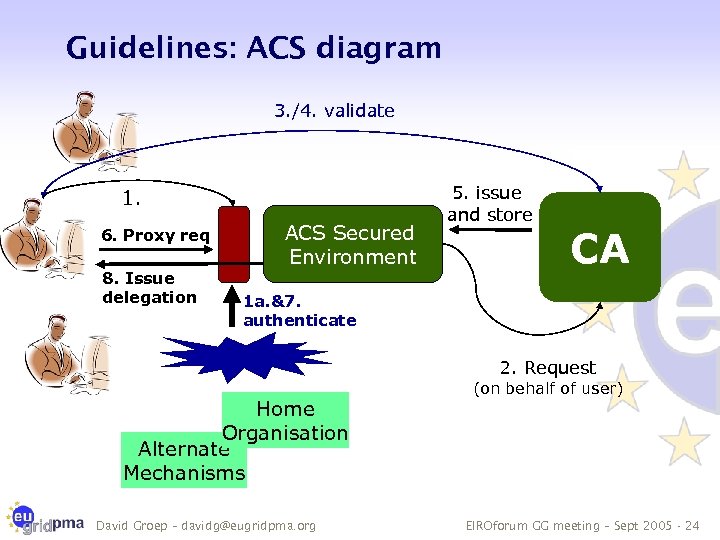 Guidelines: ACS diagram 3. /4. validate 1. 6. Proxy req 8. Issue delegation ACS Secured Environment 5. issue and store CA 1 a. &7. authenticate 2. Request Home Organisation Alternate Mechanisms David Groep – davidg@eugridpma. org (on behalf of user) EIROforum GG meeting – Sept 2005 - 24
Guidelines: ACS diagram 3. /4. validate 1. 6. Proxy req 8. Issue delegation ACS Secured Environment 5. issue and store CA 1 a. &7. authenticate 2. Request Home Organisation Alternate Mechanisms David Groep – davidg@eugridpma. org (on behalf of user) EIROforum GG meeting – Sept 2005 - 24
 History The EUGrid. PMAorigins: the EDG CACG The EU Data. Grid in 2000 needed a PKI for the test bed Both end-user and service/host PKI CACG had the task of creating this PKI Single CA was not considered acceptable Single point of attack or failure One CA per country, large region or international organization for Grid Authentication only no support for long-term encryption or digital signatures CA must have strong relationship with RAs Some pre-existing CAs A single hierarchy would have excluded existing CAs and was not convenient to support with existing software Coordinated group of peer CAs was most suitable choice Based on “reasonable procedures” and “acceptable methods” David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 25
History The EUGrid. PMAorigins: the EDG CACG The EU Data. Grid in 2000 needed a PKI for the test bed Both end-user and service/host PKI CACG had the task of creating this PKI Single CA was not considered acceptable Single point of attack or failure One CA per country, large region or international organization for Grid Authentication only no support for long-term encryption or digital signatures CA must have strong relationship with RAs Some pre-existing CAs A single hierarchy would have excluded existing CAs and was not convenient to support with existing software Coordinated group of peer CAs was most suitable choice Based on “reasonable procedures” and “acceptable methods” David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 25
 The EUGrid. PMA “constitution” EUGrid. PMA founded April 2004 as a successor to the CACG The European Policy Management Authority for Grid Authentication in e-Science (hereafter called EUGrid. PMA) is a body • to establish requirements and best practices for grid identity providers • to enable a common trust domain applicable to authentication of end-entities in inter-organisational access to distributed resources. As its main activity the EUGrid. PMA • coordinates a Public Key Infrastructure (PKI) for use with Grid authentication middleware. The EUGrid. PMA itself does not provide identity assertions, but instead asserts that - within the scope of this charter – the certificates issued by the Accredited Authorities meet or exceed the relevant guidelines. David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 26
The EUGrid. PMA “constitution” EUGrid. PMA founded April 2004 as a successor to the CACG The European Policy Management Authority for Grid Authentication in e-Science (hereafter called EUGrid. PMA) is a body • to establish requirements and best practices for grid identity providers • to enable a common trust domain applicable to authentication of end-entities in inter-organisational access to distributed resources. As its main activity the EUGrid. PMA • coordinates a Public Key Infrastructure (PKI) for use with Grid authentication middleware. The EUGrid. PMA itself does not provide identity assertions, but instead asserts that - within the scope of this charter – the certificates issued by the Accredited Authorities meet or exceed the relevant guidelines. David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 26
 EUGrid. PMA Membership EUGrid. PMA membership for (classic) CAs: · A single Certification Authority (CA) · per country, · large region (e. g. the Nordic Countries), or · international treaty organization. · The goal is to serve the largest possible community with a small number of stable CAs · operated as a long-term commitment Many CAs are operated by the (national) NREN (CESNET, ESnet, Belnet, NIIF, EEnet, SWITCH, DFN, … ) or by the e-Science programme/science foundation (UK e. Science, VL-e, CNRS, … ) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 27
EUGrid. PMA Membership EUGrid. PMA membership for (classic) CAs: · A single Certification Authority (CA) · per country, · large region (e. g. the Nordic Countries), or · international treaty organization. · The goal is to serve the largest possible community with a small number of stable CAs · operated as a long-term commitment Many CAs are operated by the (national) NREN (CESNET, ESnet, Belnet, NIIF, EEnet, SWITCH, DFN, … ) or by the e-Science programme/science foundation (UK e. Science, VL-e, CNRS, … ) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 27
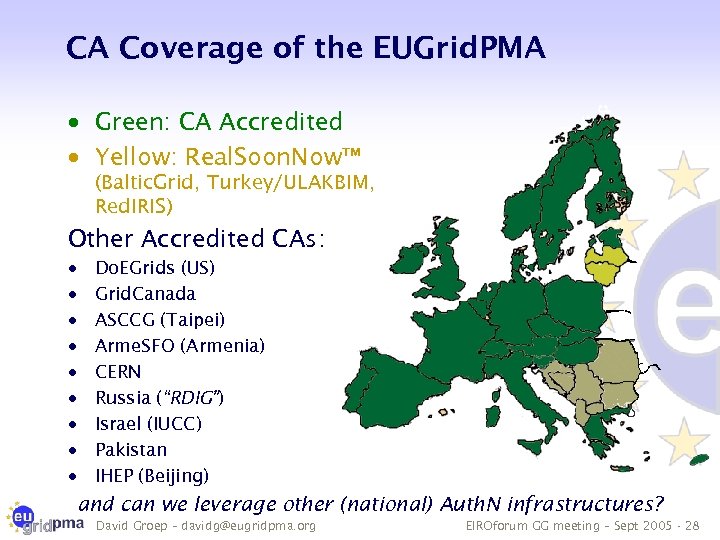 CA Coverage of the EUGrid. PMA · Green: CA Accredited · Yellow: Real. Soon. Now™ (Baltic. Grid, Turkey/ULAKBIM, Red. IRIS) Other Accredited CAs: · · · · · Do. EGrids (US) Grid. Canada ASCCG (Taipei) Arme. SFO (Armenia) CERN Russia (“RDIG”) Israel (IUCC) Pakistan IHEP (Beijing) and can we leverage other (national) Auth. N infrastructures? David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 28
CA Coverage of the EUGrid. PMA · Green: CA Accredited · Yellow: Real. Soon. Now™ (Baltic. Grid, Turkey/ULAKBIM, Red. IRIS) Other Accredited CAs: · · · · · Do. EGrids (US) Grid. Canada ASCCG (Taipei) Arme. SFO (Armenia) CERN Russia (“RDIG”) Israel (IUCC) Pakistan IHEP (Beijing) and can we leverage other (national) Auth. N infrastructures? David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 28
 EUGrid. PMAmajor relying parties · All EU 6 th framework e-Infrastructure projects · EGEE · DEISA · SEE-GRID · LHC Computing Grid Project (“LCG”) · Open Science Grid (US) · National projects, like (non-exhaustive): · UK e. Science programme · Virtual Lab e-Science, NL · … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 29
EUGrid. PMAmajor relying parties · All EU 6 th framework e-Infrastructure projects · EGEE · DEISA · SEE-GRID · LHC Computing Grid Project (“LCG”) · Open Science Grid (US) · National projects, like (non-exhaustive): · UK e. Science programme · Virtual Lab e-Science, NL · … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 29
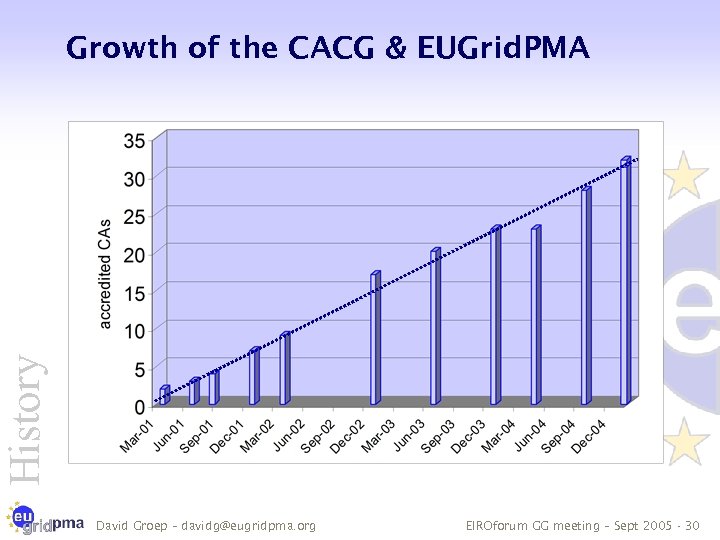 History Growth of the CACG & EUGrid. PMA David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 30
History Growth of the CACG & EUGrid. PMA David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 30
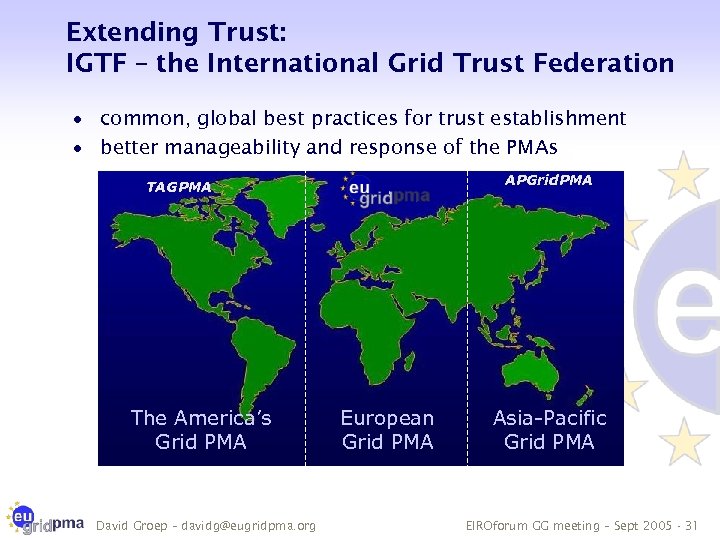 Extending Trust: IGTF – the International Grid Trust Federation · common, global best practices for trust establishment · better manageability and response of the PMAs APGrid. PMA TAGPMA The America’s Grid PMA David Groep – davidg@eugridpma. org European Grid PMA Asia-Pacific Grid PMA EIROforum GG meeting – Sept 2005 - 31
Extending Trust: IGTF – the International Grid Trust Federation · common, global best practices for trust establishment · better manageability and response of the PMAs APGrid. PMA TAGPMA The America’s Grid PMA David Groep – davidg@eugridpma. org European Grid PMA Asia-Pacific Grid PMA EIROforum GG meeting – Sept 2005 - 31
 APGrid. PMA · 13 members from the Asia-Pacific Region, chaired by Yoshio Tanaka (AIST) • AIST (. jp) • APAC (. au) • BMG (. sg) • CMSD (. in) • HKU CS SRG (. hk) • KISTI (. kr) • NCHC (. tw) • NPACI (. us) • Osaka U. (. jp) • SDG (. cn) • USM (. my) • IHEP Beijing (. cn) • ASGCC (. tw) · Launched June 1 st, 2004 · 4 ‘production-quality’ CAs · Pioneered ‘experimental’ profile David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 32
APGrid. PMA · 13 members from the Asia-Pacific Region, chaired by Yoshio Tanaka (AIST) • AIST (. jp) • APAC (. au) • BMG (. sg) • CMSD (. in) • HKU CS SRG (. hk) • KISTI (. kr) • NCHC (. tw) • NPACI (. us) • Osaka U. (. jp) • SDG (. cn) • USM (. my) • IHEP Beijing (. cn) • ASGCC (. tw) · Launched June 1 st, 2004 · 4 ‘production-quality’ CAs · Pioneered ‘experimental’ profile David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 32
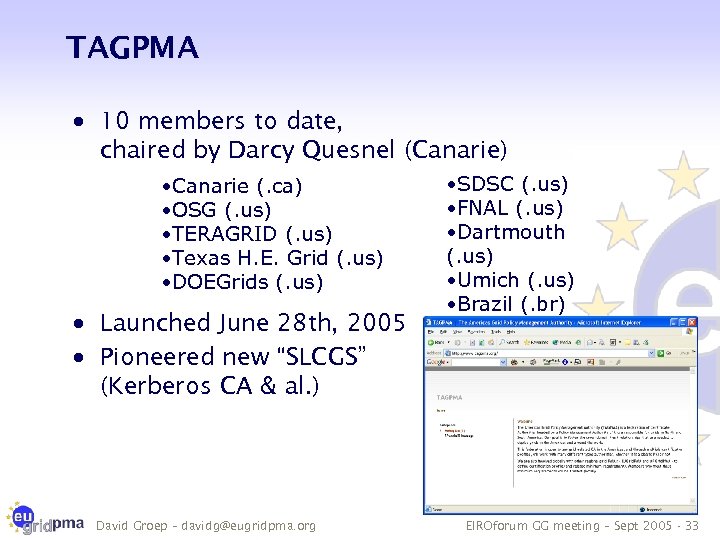 TAGPMA · 10 members to date, chaired by Darcy Quesnel (Canarie) • Canarie (. ca) • OSG (. us) • TERAGRID (. us) • Texas H. E. Grid (. us) • DOEGrids (. us) · Launched June 28 th, 2005 · Pioneered new “SLCGS” (Kerberos CA & al. ) David Groep – davidg@eugridpma. org • SDSC (. us) • FNAL (. us) • Dartmouth (. us) • Umich (. us) • Brazil (. br) EIROforum GG meeting – Sept 2005 - 33
TAGPMA · 10 members to date, chaired by Darcy Quesnel (Canarie) • Canarie (. ca) • OSG (. us) • TERAGRID (. us) • Texas H. E. Grid (. us) • DOEGrids (. us) · Launched June 28 th, 2005 · Pioneered new “SLCGS” (Kerberos CA & al. ) David Groep – davidg@eugridpma. org • SDSC (. us) • FNAL (. us) • Dartmouth (. us) • Umich (. us) • Brazil (. br) EIROforum GG meeting – Sept 2005 - 33
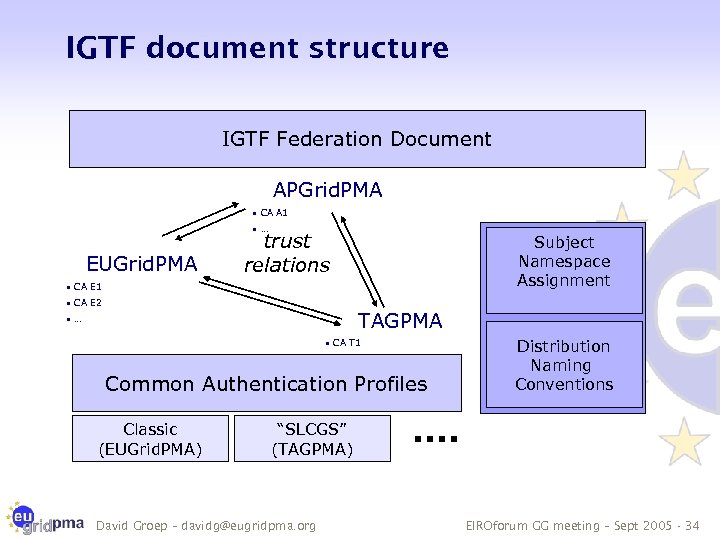 IGTF document structure IGTF Federation Document APGrid. PMA • CA A 1 • … EUGrid. PMA trust relations Subject Namespace Assignment • CA E 1 • CA E 2 TAGPMA • … • CA T 1 • … Common Authentication Profiles Classic (EUGrid. PMA) Distribution Naming Conventions “SLCGS” (TAGPMA) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 34
IGTF document structure IGTF Federation Document APGrid. PMA • CA A 1 • … EUGrid. PMA trust relations Subject Namespace Assignment • CA E 1 • CA E 2 TAGPMA • … • CA T 1 • … Common Authentication Profiles Classic (EUGrid. PMA) Distribution Naming Conventions “SLCGS” (TAGPMA) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 34
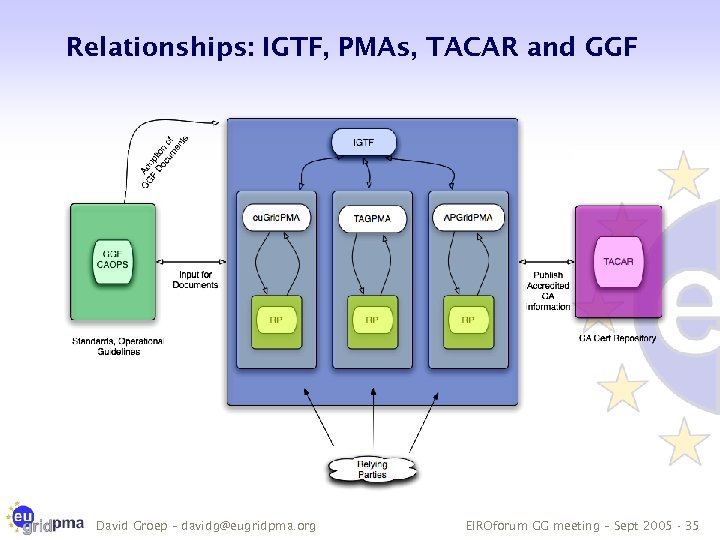 Relationships: IGTF, PMAs, TACAR and GGF David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 35
Relationships: IGTF, PMAs, TACAR and GGF David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 35
 Timeline · March 2005: IGTF Draft Federation Document GGF 13 · June 28 th: TAGPMA founded at GGF 14 · July 27 th : APGrid. PMA approved draft 0. 7 · September: EUGrid. PMA meeting on approval · October 3 -4 (planned): formal foundation of the IGTF David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 36
Timeline · March 2005: IGTF Draft Federation Document GGF 13 · June 28 th: TAGPMA founded at GGF 14 · July 27 th : APGrid. PMA approved draft 0. 7 · September: EUGrid. PMA meeting on approval · October 3 -4 (planned): formal foundation of the IGTF David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 36
 TACAR A trusted repository which can contain verified root-CA certificates The certificates to be collected are those directly managed by the member NRENs, or belonging either to a National Academic PKI in the TERENA member countries (NPKIs), or to non-profit research projects directly involving the academic community. · Authoritative source for validation of trust anchors · independent web administration makes for stronger trust · TACAR certificate itself published in paper/journals · over 20 CA root certificates collected (not only for grid use) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 37
TACAR A trusted repository which can contain verified root-CA certificates The certificates to be collected are those directly managed by the member NRENs, or belonging either to a National Academic PKI in the TERENA member countries (NPKIs), or to non-profit research projects directly involving the academic community. · Authoritative source for validation of trust anchors · independent web administration makes for stronger trust · TACAR certificate itself published in paper/journals · over 20 CA root certificates collected (not only for grid use) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 37
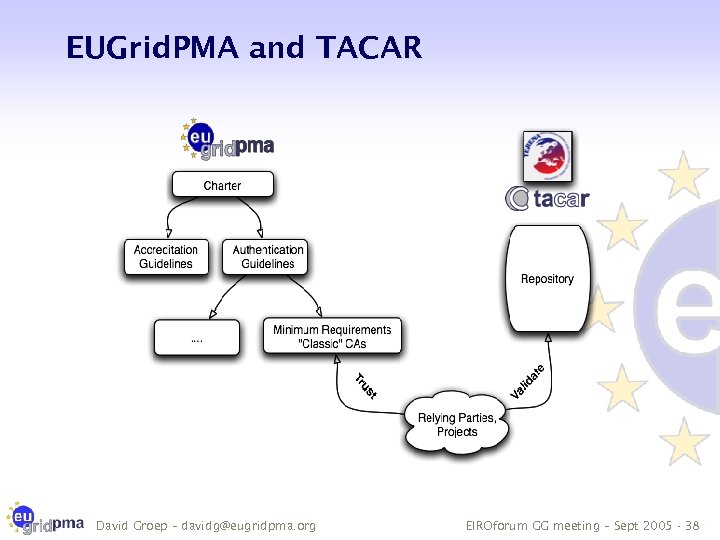 EUGrid. PMA and TACAR David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 38
EUGrid. PMA and TACAR David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 38
 Along the e-IRG Roadmap e-IRG: e-Infrastructure Reflection Group Roadmap for i 2010: · commitment to the federated approach · vision of an integrated AA infrastructure for e. Europe Towards an integrated AAI for academia in Europe and beyond · The e-IRG notes the timely operation of the EUGrid. PMA in conjunction with the TACAR CA Repository and it expresses its satisfaction for a European initiative that serves e-Science Grid projects. […] The e-IRG strongly encourages the EUGrid. PMA / TACAR to continue their valuable work […] (Dublin, 2004) · The e-IRG encourages work towards a common federation for academia and research institutes that ensures mutual recognition of the strength and validity of their authorization assertions. (The Hague, 2005) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 39
Along the e-IRG Roadmap e-IRG: e-Infrastructure Reflection Group Roadmap for i 2010: · commitment to the federated approach · vision of an integrated AA infrastructure for e. Europe Towards an integrated AAI for academia in Europe and beyond · The e-IRG notes the timely operation of the EUGrid. PMA in conjunction with the TACAR CA Repository and it expresses its satisfaction for a European initiative that serves e-Science Grid projects. […] The e-IRG strongly encourages the EUGrid. PMA / TACAR to continue their valuable work […] (Dublin, 2004) · The e-IRG encourages work towards a common federation for academia and research institutes that ensures mutual recognition of the strength and validity of their authorization assertions. (The Hague, 2005) David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 39
 Authorization
Authorization
 Next: Authorization Interoperation? · Interoperation requirements for authorization · common semantics of attributes · honour ultimate source of authority: but where is that source? what is the authorization language? Variety of different mechanisms · different target audience leads to different approaches · (wireless) network roaming · Access to supercomputers, large clusters, storage · Access to licensed database content (e. g. genomics, libraries) · Existing community organisation differences David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 41
Next: Authorization Interoperation? · Interoperation requirements for authorization · common semantics of attributes · honour ultimate source of authority: but where is that source? what is the authorization language? Variety of different mechanisms · different target audience leads to different approaches · (wireless) network roaming · Access to supercomputers, large clusters, storage · Access to licensed database content (e. g. genomics, libraries) · Existing community organisation differences David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 41
 Authorization Attributes · Various mechanisms need glue · VO directory/VOMS mechanisms, Shibboleth, Géant 2 AAI, … · developments are getting under way · Variety in semantics · different names for roles and attributes · incompatible (policy) languages · Federations like the PMA needed for Authorization · coordinate semantics · secure collection of Authorization trust anchors · mutual recognition of authorization “value” (not authorization itself, of course) concertation via TERENA TF-EMC 2, JSPG, … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 42
Authorization Attributes · Various mechanisms need glue · VO directory/VOMS mechanisms, Shibboleth, Géant 2 AAI, … · developments are getting under way · Variety in semantics · different names for roles and attributes · incompatible (policy) languages · Federations like the PMA needed for Authorization · coordinate semantics · secure collection of Authorization trust anchors · mutual recognition of authorization “value” (not authorization itself, of course) concertation via TERENA TF-EMC 2, JSPG, … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 42
 Making a Grid Community Actually Work · VOs need services to manage membership · directory service, attribute issuing · not so much ‘machines’, but ‘people’ and ‘time’ · Operational problems and incidents · where can users go with their problems? · how to stop and prevent incidents? · contact management? · Central services · information services (where are my resources? ) · brokering? Cataloguing? · Hosting provided by the “native” organisation or home organisation of the PI? or … A grid Ecosystem can help significantly here David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 43
Making a Grid Community Actually Work · VOs need services to manage membership · directory service, attribute issuing · not so much ‘machines’, but ‘people’ and ‘time’ · Operational problems and incidents · where can users go with their problems? · how to stop and prevent incidents? · contact management? · Central services · information services (where are my resources? ) · brokering? Cataloguing? · Hosting provided by the “native” organisation or home organisation of the PI? or … A grid Ecosystem can help significantly here David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 43
 Summary · Grid Security: Authentication and Authorization · Who am I: · · Common trust domain exists via EUGrid. PMA and IGTF Coordinated minimum requirements different authentication profiles Recognised by many projects & supported the e-IRG · What can I do: · no unified scheme for authorization (yet) · coordination under way in TF-EMC 2 and EGEE · Authorisation Federations are the next big challenge for Grid an e. Europe · How can I do it: · who runs the actual services: Ecosystem, VO, PI home organisation, … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 44
Summary · Grid Security: Authentication and Authorization · Who am I: · · Common trust domain exists via EUGrid. PMA and IGTF Coordinated minimum requirements different authentication profiles Recognised by many projects & supported the e-IRG · What can I do: · no unified scheme for authorization (yet) · coordination under way in TF-EMC 2 and EGEE · Authorisation Federations are the next big challenge for Grid an e. Europe · How can I do it: · who runs the actual services: Ecosystem, VO, PI home organisation, … David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 44
 http: //www. eugridpma. org / David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 45
http: //www. eugridpma. org / David Groep – davidg@eugridpma. org EIROforum GG meeting – Sept 2005 - 45


