891223a10268920aaed5cfa2161f967a.ppt
- Количество слайдов: 29

Grid Security Steve Tuecke Argonne National Laboratory

Overview l The Grid Concept l Community Authorization l Implementation Approach

The Grid Concept

Grid Computing l l Enable communities (“virtual organizations”) to share geographically distributed resources as they pursue common goals—in the absence of central control, omniscience, trust relationships Via investigations of – New applications that become possible when resources can be shared in a coordinated way – Protocols, algorithms, persistent infrastructure to facilitate sharing
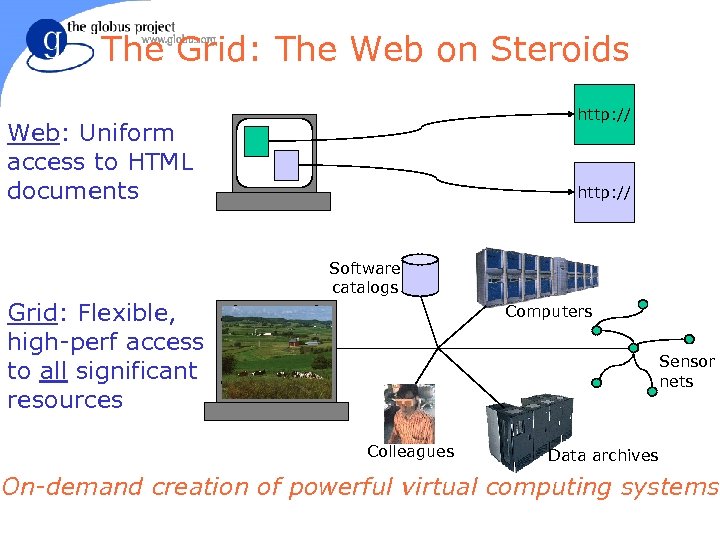
The Grid: The Web on Steroids http: // Web: Uniform access to HTML documents http: // Software catalogs Grid: Flexible, high-perf access to all significant resources Computers Sensor nets Colleagues Data archives On-demand creation of powerful virtual computing systems

Grid Communities and Applications: NSF National Technology Grid
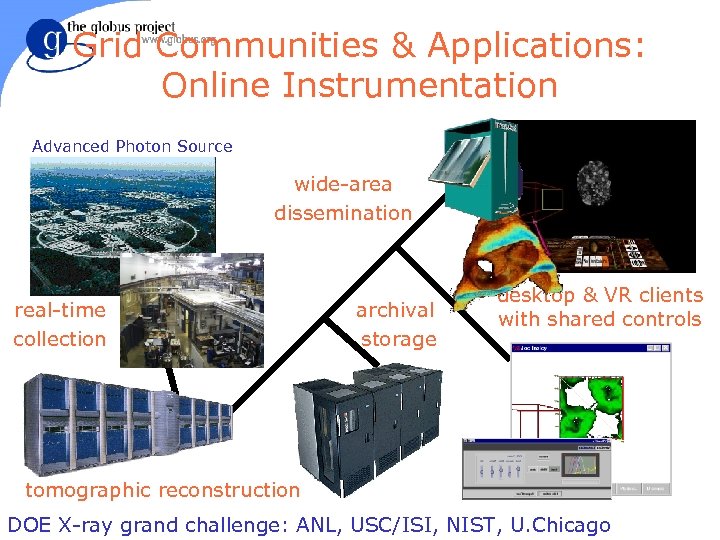
Grid Communities & Applications: Online Instrumentation Advanced Photon Source wide-area dissemination real-time collection archival storage desktop & VR clients with shared controls tomographic reconstruction DOE X-ray grand challenge: ANL, USC/ISI, NIST, U. Chicago
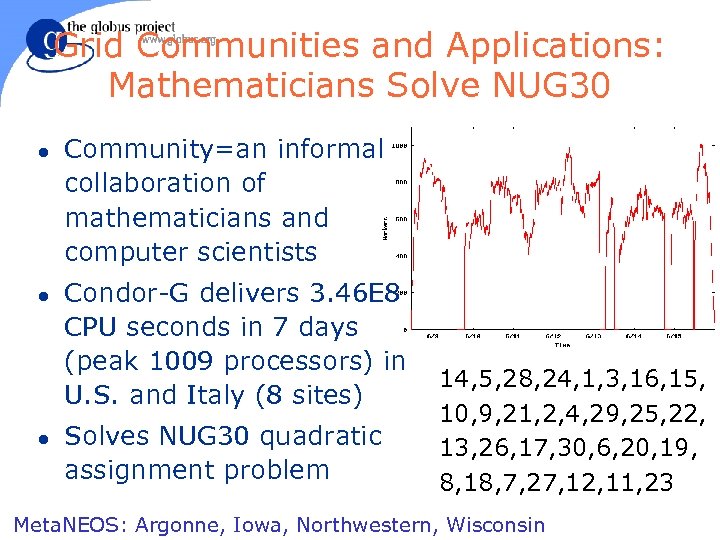
Grid Communities and Applications: Mathematicians Solve NUG 30 l l l Community=an informal collaboration of mathematicians and computer scientists Condor-G delivers 3. 46 E 8 CPU seconds in 7 days (peak 1009 processors) in U. S. and Italy (8 sites) Solves NUG 30 quadratic assignment problem 14, 5, 28, 24, 1, 3, 16, 15, 10, 9, 21, 2, 4, 29, 25, 22, 13, 26, 17, 30, 6, 20, 19, 8, 18, 7, 27, 12, 11, 23 Meta. NEOS: Argonne, Iowa, Northwestern, Wisconsin

Grid Communities and Applications: Network for Earthquake Eng. Simulation l l NEESgrid: national infrastructure to couple earthquake engineers with experimental facilities, databases, computers, & each other On-demand access to experiments, data streams, computing, archives, collaboration NEESgrid: Argonne, Michigan, NCSA, UIUC, USC
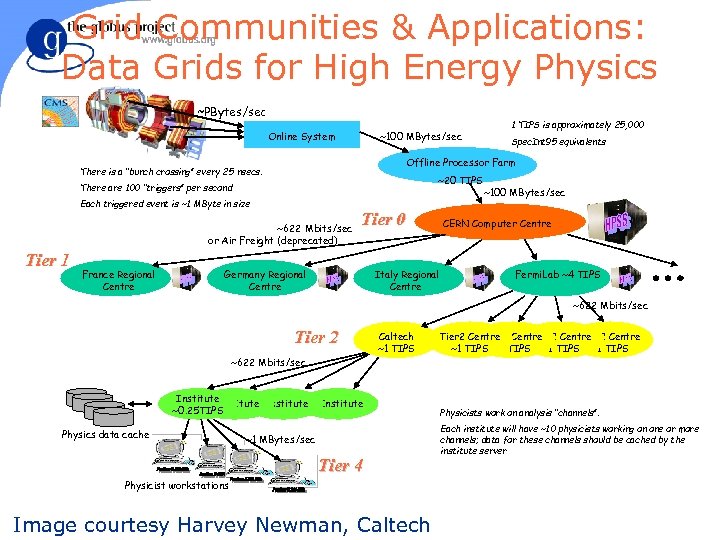
Grid Communities & Applications: Data Grids for High Energy Physics ~PBytes/sec Online System ~100 MBytes/sec ~20 TIPS There are 100 “triggers” per second Each triggered event is ~1 MByte in size ~622 Mbits/sec or Air Freight (deprecated) France Regional Centre Spec. Int 95 equivalents Offline Processor Farm There is a “bunch crossing” every 25 nsecs. Tier 1 1 TIPS is approximately 25, 000 Tier 0 Germany Regional Centre Italy Regional Centre ~100 MBytes/sec CERN Computer Centre Fermi. Lab ~4 TIPS ~622 Mbits/sec Tier 2 ~622 Mbits/sec Institute ~0. 25 TIPS Physics data cache Caltech ~1 TIPS Institute ~1 MBytes/sec Tier 4 Physicist workstations Image courtesy Harvey Newman, Caltech Tier 2 Centre Tier 2 Centre ~1 TIPS Physicists work on analysis “channels”. Each institute will have ~10 physicists working on one or more channels; data for these channels should be cached by the institute server

Grid Communities and Applications: Home Computers Evaluate AIDS Drugs l Community = – 1000 s of home computer users – Philanthropic computing vendor (Entropia) – Research group (Scripps) l Common goal= advance AIDS research

Broader Context l “Grid Computing” has much in common with major industrial thrusts – Business-to-business, Peer-to-peer, Application Service Providers, Internet Computing, … l Distinguished primarily by more sophisticated sharing modalities – E. g. , “run program X at site Y subject to community policy P, providing access to data at Z according to policy Q” – Secondarily by unique demands of advanced & high-performance systems
The Globus Project l Started in 1995 (I-WAY software) l Globus R&D – Definition of Grid architecture – Grid protocols, services, APIs > Security, resource mgmt, data access, information, communication, etc. – Development of Globus Toolkit > Large user base among tool developers & in production Grids > Open source l Numerous application projects l Outreach & leadership

More Details l l www. globus. org “The Anatomy of the Grid: Enabling Scalable Virtual Organizations” – Foster, Kesselman, Tuecke – www. globus. org/research/papers/anatomy. pdf

Community Authorization

Community Properties l 100 s of resource providers, 1000 s of users – N users from many institutions, worldwide – M independent resource providers which contribute resources to one or more communities – How to avoid N X M trust relationships? l Resource providers grant/sell to communities – Grant bulk access to community – Community representative handles fine grained authorization and prioritization within bulk grants l l Users may combine community resources with own resources to solve problems Various services carrying out requests of users

Capability Based Solution l A community service & administrator, which: – Maintains user membership to the community. – Maintains resource service agreements to community. – Maintains access control database, granting users access to (part of) resources, based on community policies and priorities. > May employ groups, roles, etc. – Issues capabilities to community members (users) to grant them access to resources. > User presents capability directly to resource to claim service. l AAAArch “push” model
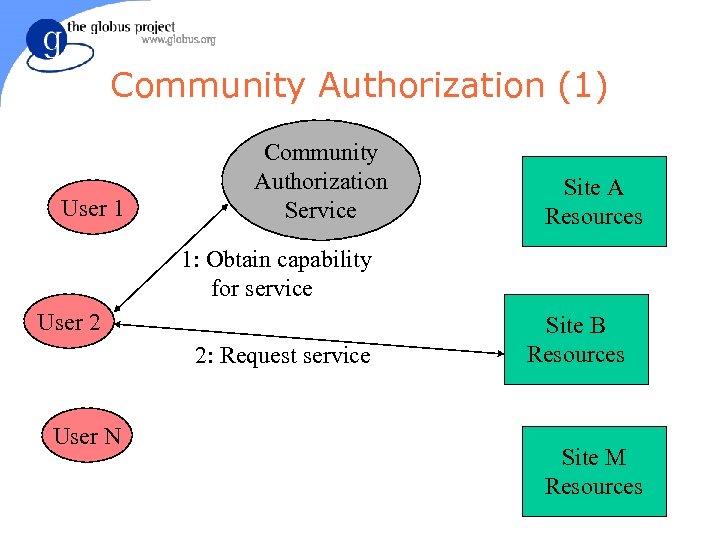
Community Authorization (1) User 1 Community Authorization Service Site A Resources 1: Obtain capability for service User 2 2: Request service User N Site B Resources Site M Resources
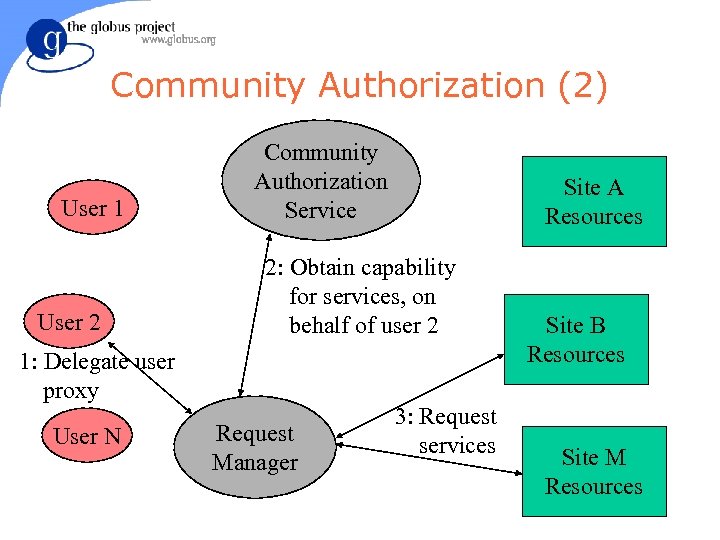
Community Authorization (2) User 1 User 2 Community Authorization Service 2: Obtain capability for services, on behalf of user 2 1: Delegate user proxy User N Site A Resources Request Manager 3: Request services Site B Resources Site M Resources
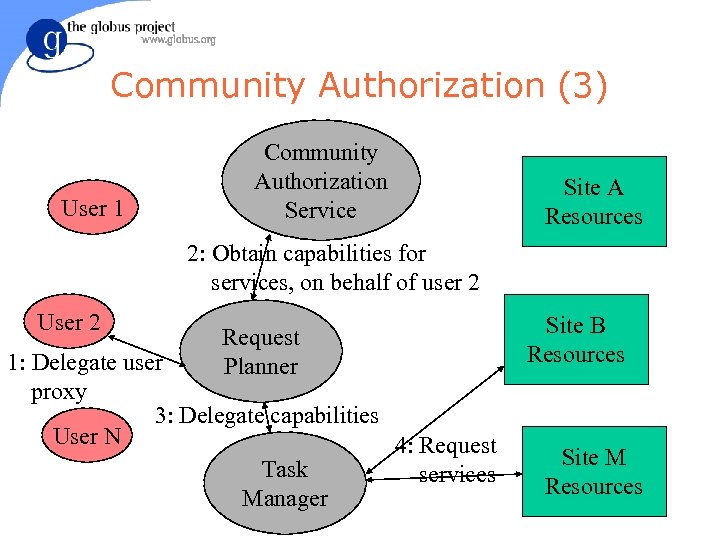
Community Authorization (3) User 1 Community Authorization Service Site A Resources 2: Obtain capabilities for services, on behalf of user 2 User 2 Request Planner 1: Delegate user proxy 3: Delegate capabilities User N 4: Request Task services Manager Site B Resources Site M Resources

Implementation Approach
Grid Security Infrastructure (GSI) l Authentication and message protection l Extensions to existing standard protocols & APIs – Standards: SSL/TLS, X. 509, GSS-API – Extensions for single sign-on and delegation > Internet X. 509 PKI Impersonation Proxy Certificate Profile > TLS Delegation Protocol l Globus Toolkit reference implementation of GSI – Open. SSL + GSS-API + delegation – Tools and services to interface to local security > Simple ACLs; SSLK 5 & PKINIT for access to K 5, AFS, etc. – Tools for credential management > Login, logout, cert request, smartcards, cred repository, etc.

X. 509 Proxy Certificate Overview l l To support single sign-on and delegation Proxy Certificate (PC) is signed by End Entity Certificate (EEC) or another Proxy Certificate – We are NOT using an EEC to as if it were a CA > CA performs two functions: 1) Assigns a name (or identity), and 2) Binds the name to the a key. > PC only does #2. It binds the name to an proxy key. – PC inherits name from its signing EEC > Subject name used for two purposes: 1) Path discovery & validation, and 2) To hold the assigned name. > In a PC, the subject is used only for #1, path discovery l “TLS Delegation Protocol” draft defines how to create a remote Proxy Certificate
Features Of This Approach l Ease of integration – Requires only a small change to path validation > SSL/TLS requires no protocol change to use PC – Authorization based on identity still works l Ease of use – Enables single sign-on & credential repositories l Protection of EEC private key – Single sign-on & delegation w/o sharing EEC keys l Limits consequences of a compromised key – Can restrict PC (e. g. lifetime, uses, etc. ) – Compromised PC does not compromise EEC
Implementation Status l Globus Toolkit’s Grid Security Infrastructure (GSI) has used similar approach for ~4 years – GSI = GSS-API + X. 509 + PC + SSL + delegation – Integrated into numerous “Grid” tools (C & Java) > Globus Toolkit, Condor, SRB, MPI, ssh/Secure. CRT, FTP, etc. – Adopted by 100 s of sites, 1000 s of users > NCSA, NPACI, NASA IPG, DOE Science Grid, European Datagrid, Gri. Phy. N (Phyics Grids), NEESgrid (Earthquake Engineering Grid) l Global Grid Forum & IETF effort to move GSI forward through cleanup, better integration with standards, technical specifications, etc. – http: //www. gridforum. org/security/gsi

Capabilities l By extending a Proxy Certificate to hold a restriction policy, one can build a form of capability – Currently, the holder of a user’s proxy credential allows that holder to impersonate the user, to access any resources available to the user – But can extend the proxy credential to contain a restriction policy > E. g. “Holder of this proxy can only start a process on resource X, and read user’s file Y. ”

Community Authorization Service l CAS has its own identity certificate – It is this CAS identity that is known to resources l l User authenticates with CAS using user’s identity certificates (or proxy of identity certificate) User requests access to a community resource(s) CAS delegates back to user a restricted proxy credential from the CAS identity credential User authenticates with resource using this CAS identity

Resource Checking of Capability l Authentication from client is with the CAS identity – Resource sees the “community” identity – Though an X. 509 extension in the capability may include user’s identity, etc. for audit purposes l Resource maps CAS identity to local account and privileges – E. g. A Unix account, with a given file system quota – Different communities map to different accounts l For each request, resource evaluates the request against the policy contained in the CAS restricted proxy certificate that was used to authenticate.

Accounting l CAS inserts GUID into capability, which is used for: – Accounting: Resources can log consumption using this GUID. CAS can recombine with log of issued capabilities to reconstruct full accounting info. > Requires protocol for propagation of accounting info – Usage enforcement: Restriction policy in capability may include usage constraints. Resource can track and enforce such constraints using the GUID, including across multiple requests using the same capability.
891223a10268920aaed5cfa2161f967a.ppt