3f3838beae5dcf824a28d33a8a738815.ppt
- Количество слайдов: 38

Grid Security Overview The Globus Project™ http: //www. globus. org/ Copyright (c) 2002 University of Chicago and The University of Southern California. All Rights Reserved. presentation is licensed for use under the terms of the Globus Toolkit Public License. See http: //www. globus. org/toolkit/download/license. html for the full text of this license. Grid School 2004 Security Overview This

Security Terminology Authentication: Establishing identity l Authorization: Establishing rights l Message protection –Message integrity –Message confidentiality l Non-repudiation l Digital signature l Accounting l Delegation l Grid School 2004 Security Overview 2
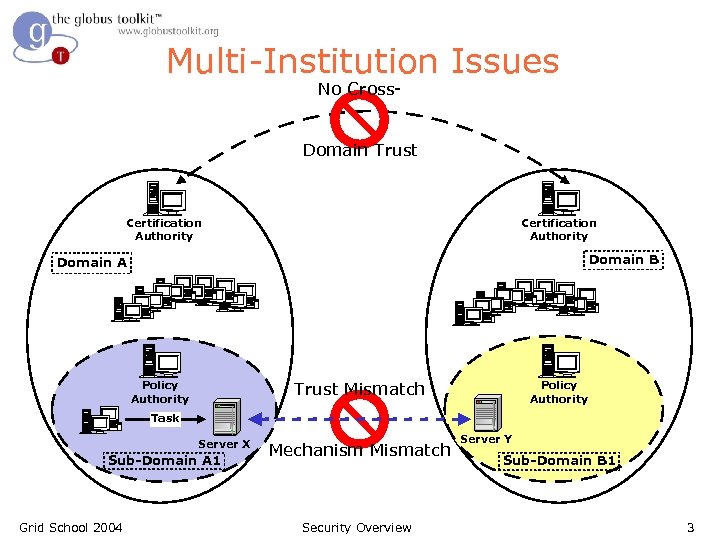
Multi-Institution Issues No Cross- Domain Trust Certification Authority Domain B Domain A Trust Mismatch Policy Authority Task Server X Sub-Domain A 1 Grid School 2004 Mechanism Mismatch Security Overview Server Y Sub-Domain B 1 3
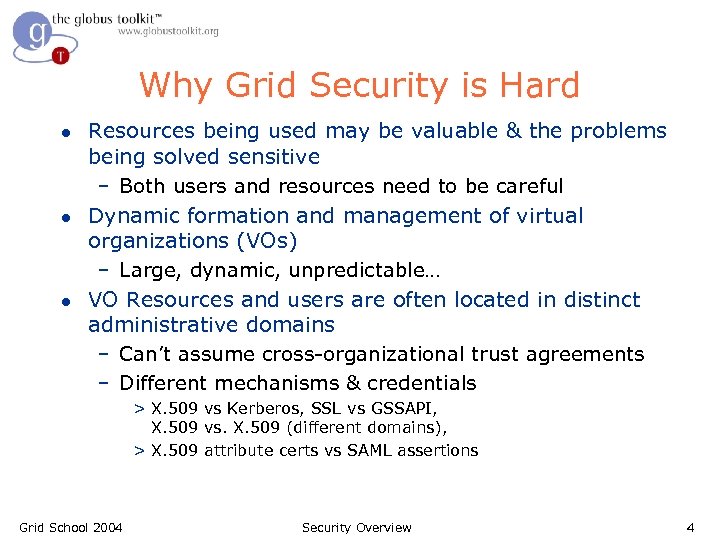
Why Grid Security is Hard l l l Resources being used may be valuable & the problems being solved sensitive – Both users and resources need to be careful Dynamic formation and management of virtual organizations (VOs) – Large, dynamic, unpredictable… VO Resources and users are often located in distinct administrative domains – Can’t assume cross-organizational trust agreements – Different mechanisms & credentials > X. 509 vs Kerberos, SSL vs GSSAPI, X. 509 vs. X. 509 (different domains), > X. 509 attribute certs vs SAML assertions Grid School 2004 Security Overview 4

Why Grid Security is Hard… l l l Interactions are not just client/server, but service-to-service on behalf of the user – Requires delegation of rights by user to service – Services may be dynamically instantiated Standardization of interfaces to allow for discovery, negotiation and use Implementation must be broadly available & applicable – Standard, well-tested, well-understood protocols; integrated with wide variety of tools Policy from sites, VO, users need to be combined – Varying formats Want to hide as much as possible from applications! Grid School 2004 Security Overview 5

The Grid Trust solution l l l Instead of setting up trust relationships at the organizational level (lots of overhead, possible legalities - expensive!) set up trust at the user/resource level Virtual Organizations (VOs) for multi-user collaborations – Federate through mutually trusted services – Local policy authorities rule Users able to set up dynamic trust domains – Personal collection of resources working together based on trust of user Grid School 2004 Security Overview 6
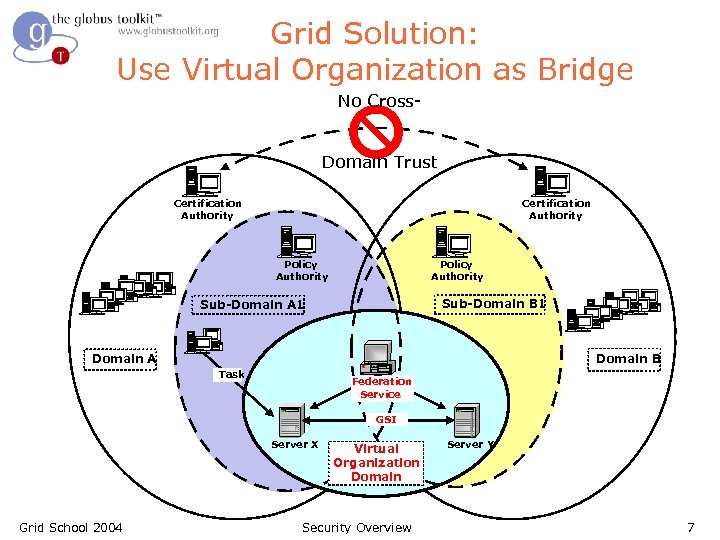
Grid Solution: Use Virtual Organization as Bridge No Cross. Domain Trust Certification Authority Policy Authority Sub-Domain B 1 Sub-Domain A 1 Domain A Domain B Task Federation Service GSI Server X Grid School 2004 Virtual Organization Domain Security Overview Server Y 7
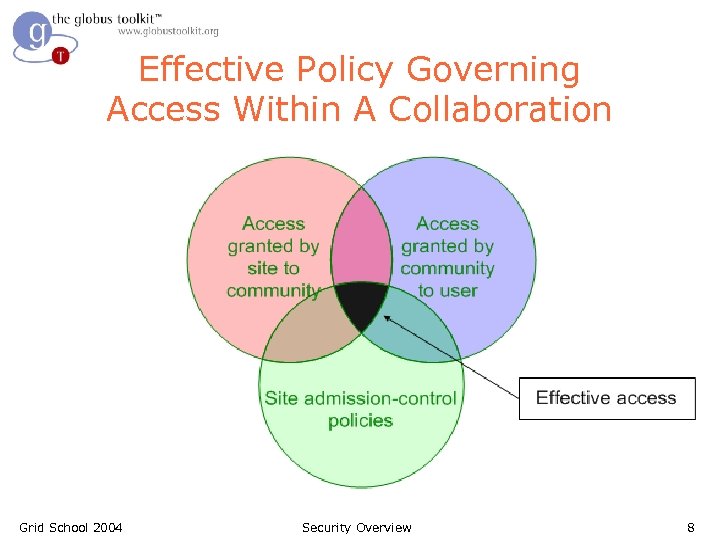
Effective Policy Governing Access Within A Collaboration Grid School 2004 Security Overview 8
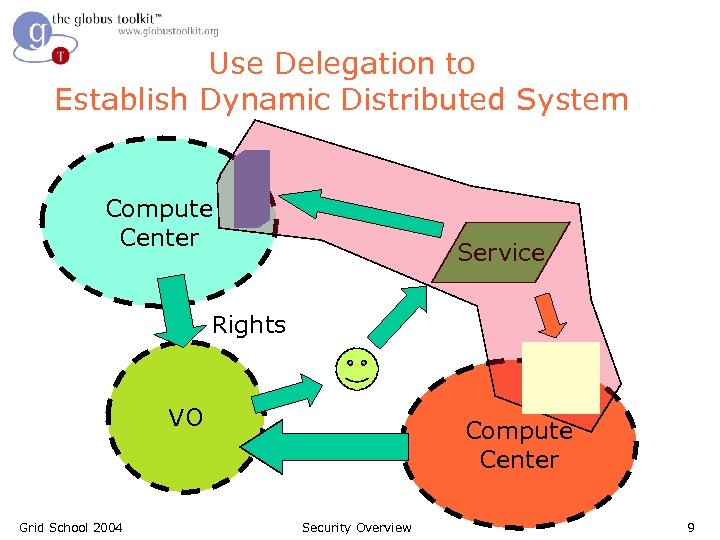
Use Delegation to Establish Dynamic Distributed System Compute Center Service Rights VO Grid School 2004 Compute Center Security Overview 9
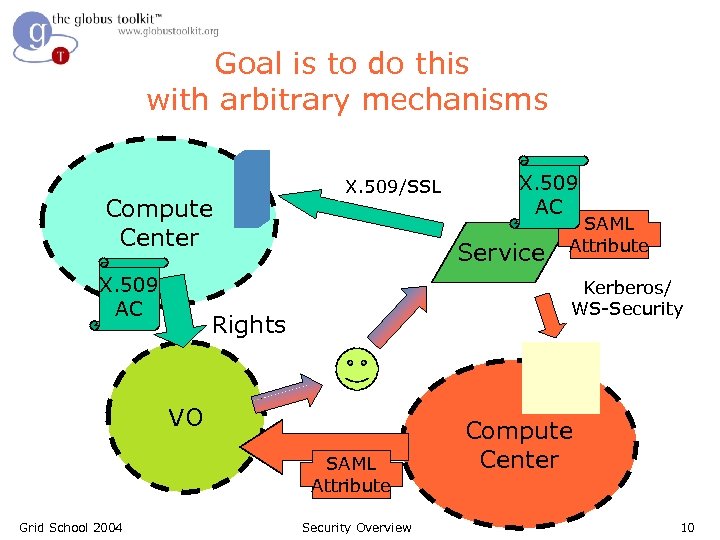
Goal is to do this with arbitrary mechanisms Compute Center X. 509 AC X. 509/SSL Service SAML Attribute Kerberos/ WS-Security Rights VO SAML Attribute Grid School 2004 X. 509 AC Security Overview Compute Center 10

Grid Security Infrastructure (GSI) l l l Use GSI as a standard mechanism for bridging disparate security mechanisms – Doesn’t solve trust problem, but now things talk same protocol and understand each other’s identity credentials – Basic support for delegation, policy distribution Translate from other mechanisms to/from GSI as needed Convert from GSI identity to local identity for authorization Grid School 2004 Security Overview 11

GSI l l GSI implements X. 509 Proxy Certificates as extensions to these standards to support dynamic naming of services, delegation of rights and single sign-on After authentication, GSI identity is mapped by administer configuration to a local identity for authorization. – Local identity controls access to local files, job startup rights, etc. Grid School 2004 Security Overview 12

Grid Security Infrastructure (GSI) l Based on standard PKI technologies – SSL protocol for authentication, message protection – CAs allow one-way, light-weight trust relationships (not just site-to-site) l X. 509 Certificates for asserting identity – for users, services, hosts, etc. l Proxy Certificates – GSI extension to X. 509 certificates for delegation, single sign-on Grid School 2004 Security Overview 13
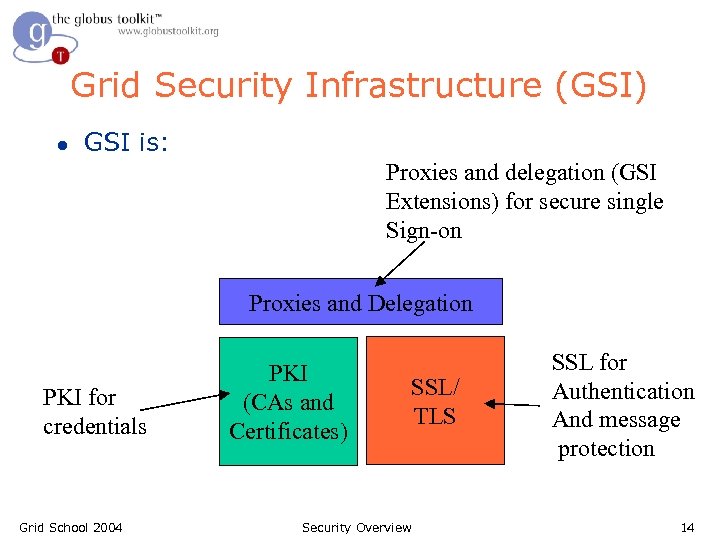
Grid Security Infrastructure (GSI) l GSI is: Proxies and delegation (GSI Extensions) for secure single Sign-on Proxies and Delegation PKI for credentials Grid School 2004 PKI (CAs and Certificates) SSL/ TLS Security Overview SSL for Authentication And message protection 14
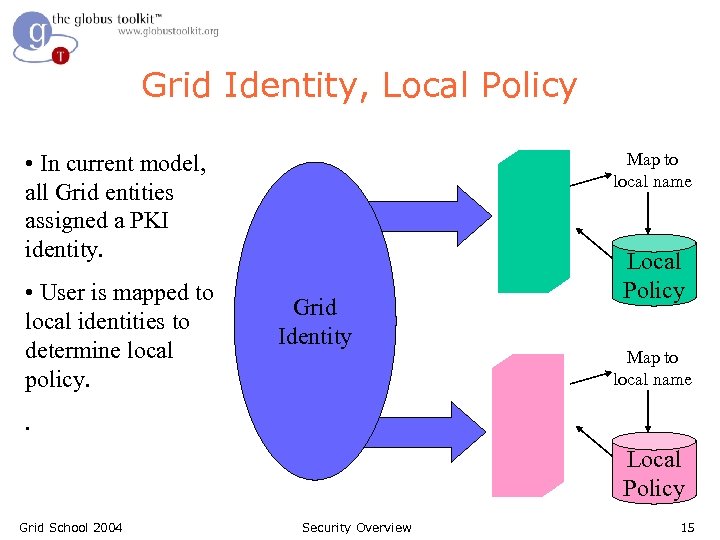
Grid Identity, Local Policy Map to local name • In current model, all Grid entities assigned a PKI identity. • User is mapped to local identities to determine local policy. Grid Identity Local Policy Map to local name . Local Policy Grid School 2004 Security Overview 15
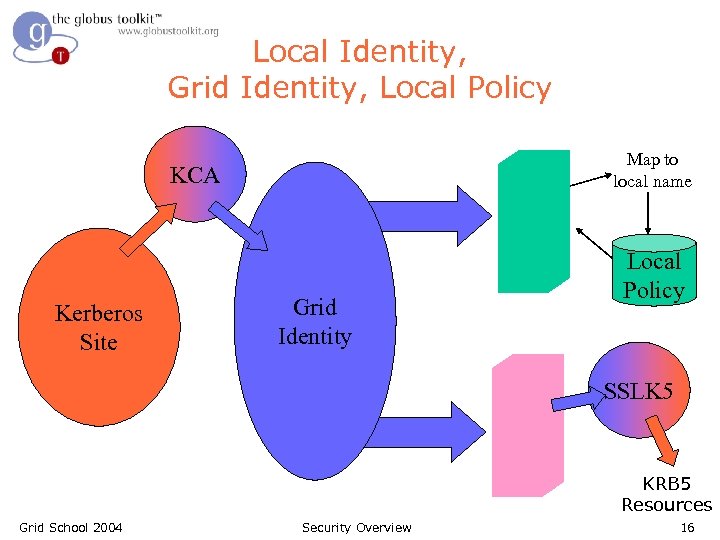
Local Identity, Grid Identity, Local Policy Map to local name KCA Kerberos Site Grid Identity Local Policy SSLK 5 KRB 5 Resources Grid School 2004 Security Overview 16
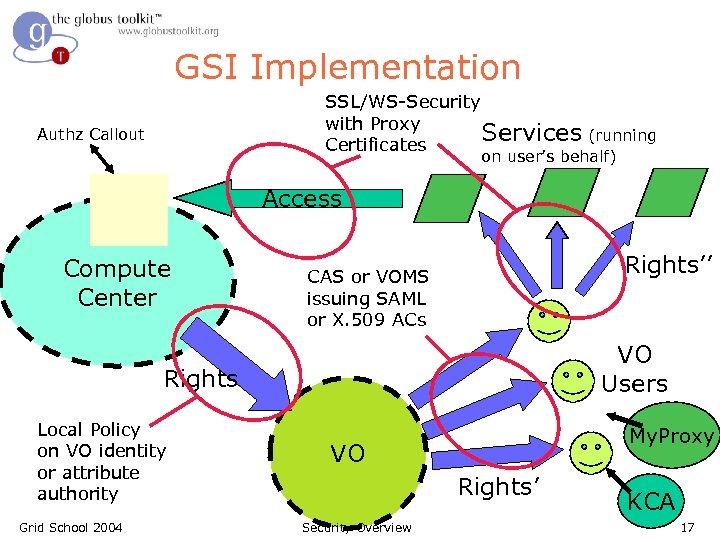
GSI Implementation SSL/WS-Security with Proxy Services (running Certificates Authz Callout on user’s behalf) Access Compute Center Rights’’ CAS or VOMS issuing SAML or X. 509 ACs VO Users Rights Local Policy on VO identity or attribute authority Grid School 2004 My. Proxy VO Rights’ Security Overview KCA 17
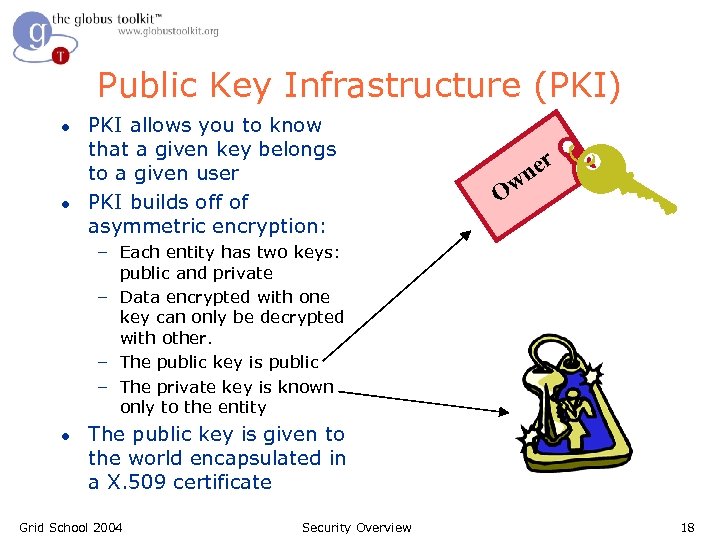
Public Key Infrastructure (PKI) l l PKI allows you to know that a given key belongs to a given user PKI builds off of asymmetric encryption: er wn O – Each entity has two keys: public and private – Data encrypted with one key can only be decrypted with other. – The public key is public – The private key is known only to the entity l The public key is given to the world encapsulated in a X. 509 certificate Grid School 2004 Security Overview 18
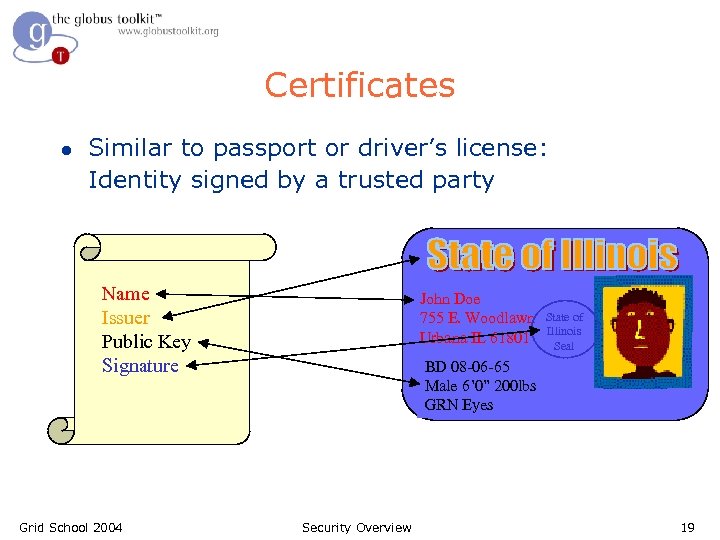
Certificates l Similar to passport or driver’s license: Identity signed by a trusted party Name Issuer Public Key Signature Grid School 2004 John Doe 755 E. Woodlawn Urbana IL 61801 State of Illinois Seal BD 08 -06 -65 Male 6’ 0” 200 lbs GRN Eyes Security Overview 19
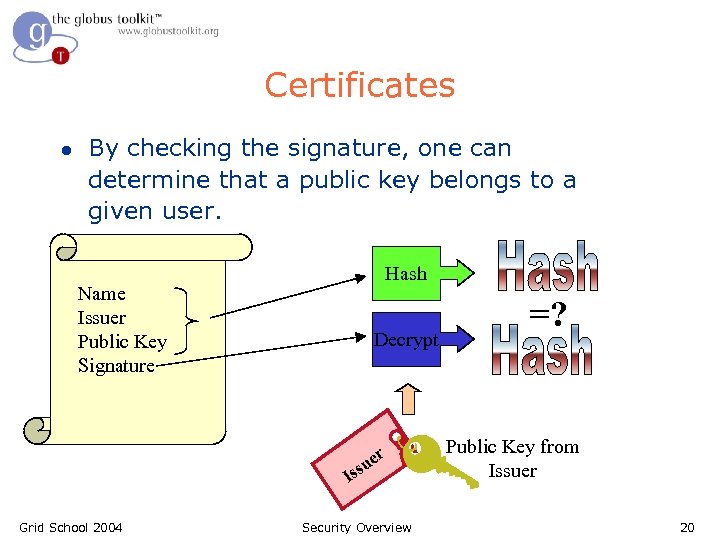
Certificates l By checking the signature, one can determine that a public key belongs to a given user. Hash Name Issuer Public Key Signature Decrypt er su s I Grid School 2004 Security Overview =? Public Key from Issuer 20

Certificate Authorities (CAs) l l l A small set of trusted entities known as Certificate Authorities (CAs) are established to sign certificates A Certificate Authority is an entity that exists only to sign user certificates Name: CA Issuer: CA CA’s Public Key CA’s Signature The CA signs it’s own certificate which is distributed in a trusted manner Grid School 2004 Security Overview 21
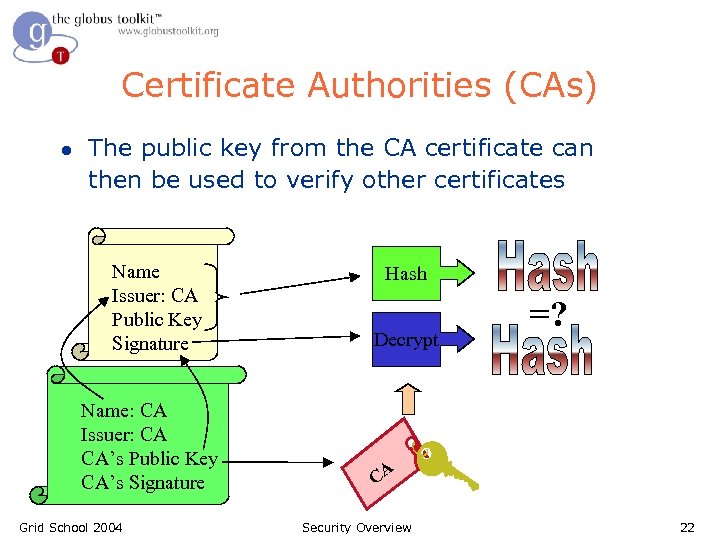
Certificate Authorities (CAs) l The public key from the CA certificate can then be used to verify other certificates Name Issuer: CA Public Key Signature Name: CA Issuer: CA CA’s Public Key CA’s Signature Grid School 2004 Hash Decrypt =? CA Security Overview 22
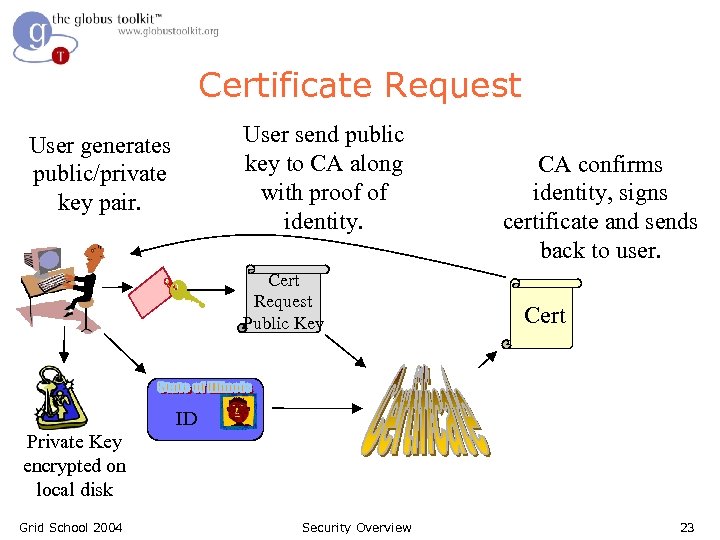
Certificate Request User send public key to CA along with proof of identity. User generates public/private key pair. Cert Request Public Key CA confirms identity, signs certificate and sends back to user. Cert ID Private Key encrypted on local disk Grid School 2004 Security Overview 23

X. 509 Proxy Certificates l GSI Extension to X. 509 Identity Certificates – RFC l l Enables single sign-on Allow user to dynamically assign identity and rights to service – Can name services created on the fly and give them rights (i. e. set policy) l What is effectively happening is the user is creating their own trust domain of services – Services trust each other with user acting as the trust root Grid School 2004 Security Overview 24
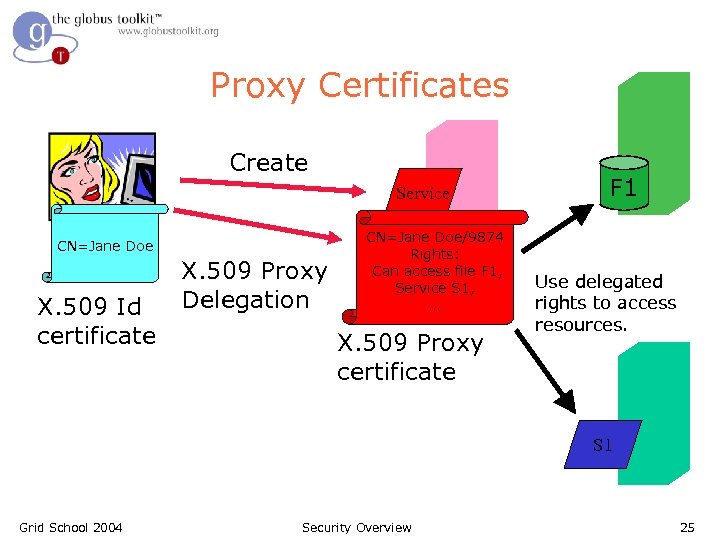
Proxy Certificates Create Service CN=Jane Doe X. 509 Id certificate X. 509 Proxy Delegation CN=Jane Doe/9874 Rights: Can access file F 1, Service S 1, … X. 509 Proxy certificate F 1 Use delegated rights to access resources. S 1 Grid School 2004 Security Overview 25

Obtaining a Certificate l The program grid-cert-request is used to create a public/private key pair and unsigned certificate in ~/. globus/: – usercert_request. pem: Unsigned certificate file – userkey. pem: Encrypted private key file > Must be readable only by the owner l l l Mail usercert_request. pem to ca@globus. org Receive a Globus-signed certificate Place in ~/. globus/usercert. pem Other organizations use different approaches – NCSA, NPACI, NASA, etc. have their own CA Grid School 2004 Security Overview 26

Certificate Information l To get cert information run grid-cert-info % grid-cert-info -subject /C=US/O=Globus/O=ANL/OU=MCS/CN=Ian Foster l Options for printing cert information -all -subject -issuer Grid School 2004 -startdate -enddate -help Security Overview 27

“Logging on” to the Grid l To run programs, authenticate to Globus: % grid-proxy-init Enter PEM pass phrase: ****** l l Creates a temporary, local, short-lived proxy credential for use by our computations Options for grid-proxy-init: -hours <lifetime of credential> -bits <length of key> -help Grid School 2004 Security Overview 28
grid-proxy-init Details l l l grid-proxy-init creates the local proxy file. User enters pass phrase, which is used to decrypt private key. Private key is used to sign a proxy certificate with its own, new public/private key pair. – User’s private key not exposed after proxy has been signed Proxy placed in /tmp, read-only by user NOTE: No network traffic! grid-proxy-info displays proxy details Grid School 2004 Security Overview 29
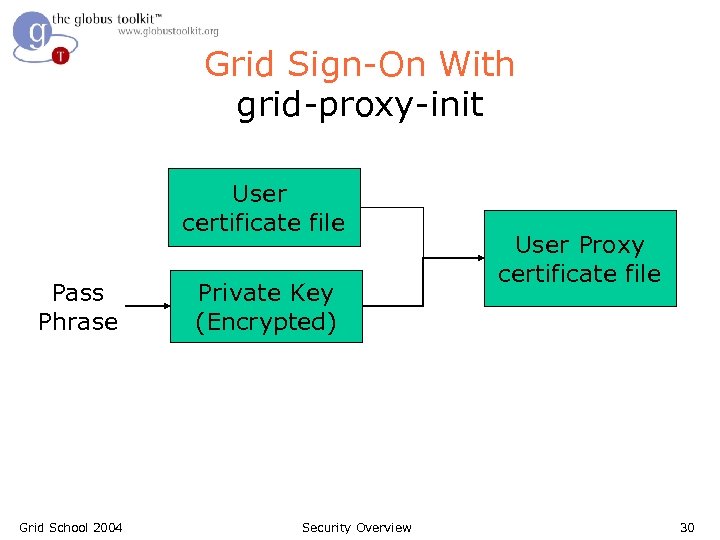
Grid Sign-On With grid-proxy-init User certificate file Pass Phrase Grid School 2004 Private Key (Encrypted) Security Overview User Proxy certificate file 30

Destroying Your Proxy (logout) l To destroy your local proxy that was created by grid-proxy-init: % grid-proxy-destroy l This does NOT destroy any proxies that were delegated from this proxy. – You cannot revoke a remote proxy – Usually create proxies with short lifetimes Grid School 2004 Security Overview 31

Proxy Information l To get proxy information run grid-proxy-info % grid-proxy-info -subject /C=US/O=Globus/O=ANL/OU=MCS/CN=Ian Foster l Options for printing proxy information -subject -type -strength l -issuer -timeleft -help Options for scripting proxy queries -exists -hours <lifetime of credential> -exists -bits <length of key> – Returns 0 status for true, 1 for false: Grid School 2004 Security Overview 32
Delegation l Delegation = remote creation of a (second level) proxy credential – New key pair generated remotely on server – Proxy cert and public key sent to client – Clients signs proxy cert and returns it – Server (usually) puts proxy in /tmp l Allows remote process to authenticate on behalf of the user – Remote process “impersonates” the user Grid School 2004 Security Overview 33

Limited Proxy l During delegation, the client can elect to delegate only a “limited proxy”, rather than a “full” proxy – GRAM (job submission) client does this l Each service decides whether it will allow authentication with a limited proxy – Job manager service requires a full proxy – Grid. FTP server allows either full or limited proxy to be used Grid School 2004 Security Overview 34

Secure Services l l On most unix machines, inetd listens for incoming service connections and passes connections to daemons for processing. On Grid servers, the gatekeeper securely performs the same function for many services – It handles mutual authentication using files in /etc/grid-security – It maps to local users via the gridmap file Grid School 2004 Security Overview 35
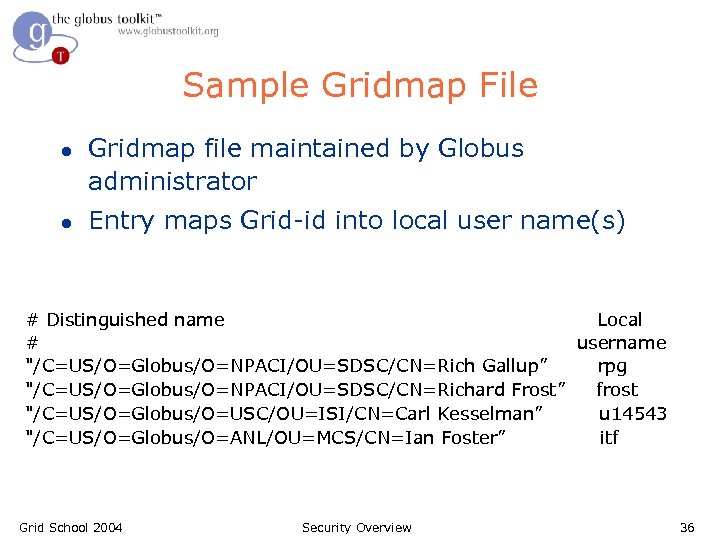
Sample Gridmap File l l Gridmap file maintained by Globus administrator Entry maps Grid-id into local user name(s) # Distinguished name Local # username "/C=US/O=Globus/O=NPACI/OU=SDSC/CN=Rich Gallup” rpg "/C=US/O=Globus/O=NPACI/OU=SDSC/CN=Richard Frost” frost "/C=US/O=Globus/O=USC/OU=ISI/CN=Carl Kesselman” u 14543 "/C=US/O=Globus/O=ANL/OU=MCS/CN=Ian Foster” itf Grid School 2004 Security Overview 36

Authorization l l GSI handles authentication, but authorization is a separate issue Authorization issues: – Management of authorization on a multi-organization grid is still an interesting problem. – The grid-mapfile doesn’t scale well, and works only at the resource level, not the collective level. – Large communities that share resources exacerbates authorization issues, which has led us to CAS… Grid School 2004 Security Overview 37
Security Summary l Programs for credential management – grid-cert-info, grid-proxy-init, grid-proxydestroy, grid-proxy-info l l GSS-API: The Globus Toolkit Grid Security Infrastructure (GSI) uses this API, which allows programs to easily add security globus_gss_assist: This is a simple wrapper around GSS-API, making it easier to use Grid School 2004 Security Overview 38
3f3838beae5dcf824a28d33a8a738815.ppt