945a97a8dc0545a2ac0b2504c05e7d83.ppt
- Количество слайдов: 40
 GR 01 E - Electronic Commerce Overview Module 1 Technology: E 1. Security Copyright © 2003 T. Trappenberg Overview E 1
GR 01 E - Electronic Commerce Overview Module 1 Technology: E 1. Security Copyright © 2003 T. Trappenberg Overview E 1
 Data security Hacker resistance Fault Tolerance Intrusion control and detection SSL Policies … Copyright © 2003 T. Trappenberg Overview E 2
Data security Hacker resistance Fault Tolerance Intrusion control and detection SSL Policies … Copyright © 2003 T. Trappenberg Overview E 2
 What is SSL/TSL? • Secure Socket Layer/Transport Layer Security • Runs commonly on top of TCP/IP • A protocol that implements - privacy against eavesdroppers through encryption of messages - message integrity trough hash function - authentication through digital signatures • e. g. , connect to https, ssmtp, spop 3 (each has a unique port number) Copyright © 2003 T. Trappenberg Overview E 3
What is SSL/TSL? • Secure Socket Layer/Transport Layer Security • Runs commonly on top of TCP/IP • A protocol that implements - privacy against eavesdroppers through encryption of messages - message integrity trough hash function - authentication through digital signatures • e. g. , connect to https, ssmtp, spop 3 (each has a unique port number) Copyright © 2003 T. Trappenberg Overview E 3
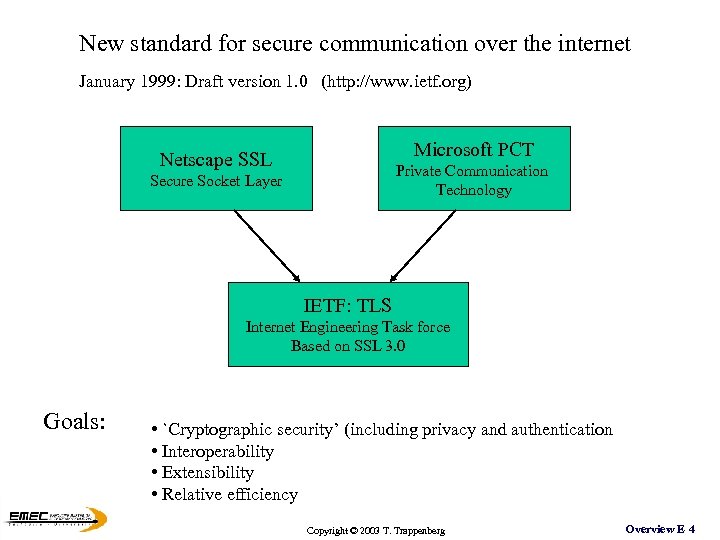 New standard for secure communication over the internet January 1999: Draft version 1. 0 (http: //www. ietf. org) Microsoft PCT Netscape SSL Private Communication Technology Secure Socket Layer IETF: TLS Internet Engineering Task force Based on SSL 3. 0 Goals: • `Cryptographic security’ (including privacy and authentication • Interoperability • Extensibility • Relative efficiency Copyright © 2003 T. Trappenberg Overview E 4
New standard for secure communication over the internet January 1999: Draft version 1. 0 (http: //www. ietf. org) Microsoft PCT Netscape SSL Private Communication Technology Secure Socket Layer IETF: TLS Internet Engineering Task force Based on SSL 3. 0 Goals: • `Cryptographic security’ (including privacy and authentication • Interoperability • Extensibility • Relative efficiency Copyright © 2003 T. Trappenberg Overview E 4
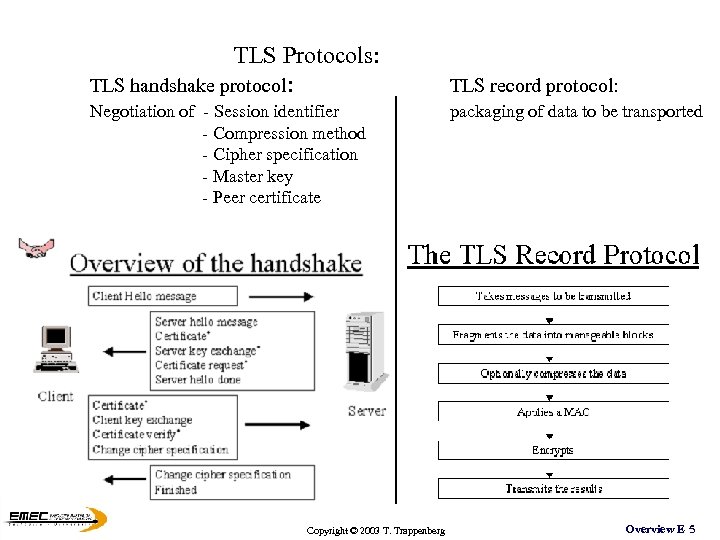 TLS Protocols: TLS handshake protocol: Negotiation of - Session identifier - Compression method - Cipher specification - Master key - Peer certificate Copyright © 2003 T. Trappenberg TLS record protocol: packaging of data to be transported Overview E 5
TLS Protocols: TLS handshake protocol: Negotiation of - Session identifier - Compression method - Cipher specification - Master key - Peer certificate Copyright © 2003 T. Trappenberg TLS record protocol: packaging of data to be transported Overview E 5
 Authetication: either - both parties - server authentication - no authentication Copyright © 2003 T. Trappenberg Overview E 6
Authetication: either - both parties - server authentication - no authentication Copyright © 2003 T. Trappenberg Overview E 6
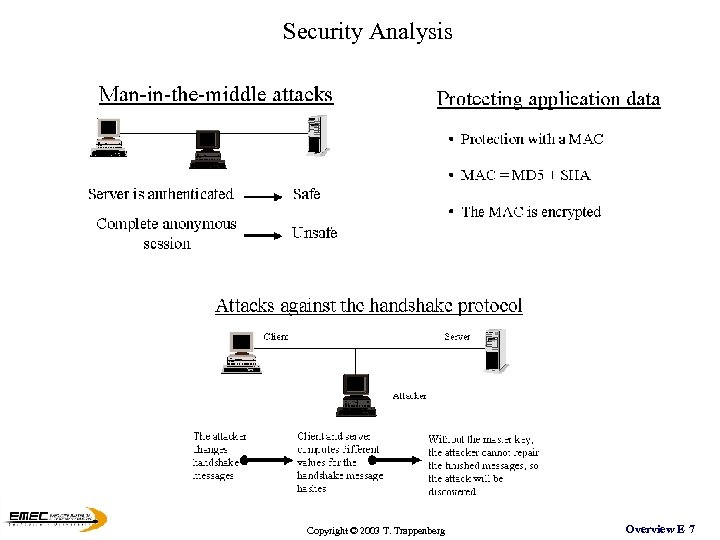 Security Analysis Copyright © 2003 T. Trappenberg Overview E 7
Security Analysis Copyright © 2003 T. Trappenberg Overview E 7
 However: -How secure is the cryptographic protocol? (e. g. key length, …) - How is authentication handled (e. g. switched on? , signature verification, …) - Implementation errors Copyright © 2003 T. Trappenberg Overview E 8
However: -How secure is the cryptographic protocol? (e. g. key length, …) - How is authentication handled (e. g. switched on? , signature verification, …) - Implementation errors Copyright © 2003 T. Trappenberg Overview E 8
 GR 01 E - Electronic Commerce Overview Module 1 Technology: E 2. Cryptography Copyright © 2003 T. Trappenberg Overview E 9
GR 01 E - Electronic Commerce Overview Module 1 Technology: E 2. Cryptography Copyright © 2003 T. Trappenberg Overview E 9
 Dear Jean, I love you George This is $1000 Dollar (US!!) Copyright © 2003 T. Trappenberg Overview E 10
Dear Jean, I love you George This is $1000 Dollar (US!!) Copyright © 2003 T. Trappenberg Overview E 10
 Cryptography Basics • • • Ciphers Symmetric Key Algorithms Public Key Algorithms Message Digests Digital Signatures Trust networks Copyright © 2003 T. Trappenberg Overview E 11
Cryptography Basics • • • Ciphers Symmetric Key Algorithms Public Key Algorithms Message Digests Digital Signatures Trust networks Copyright © 2003 T. Trappenberg Overview E 11
 • Confidentiality (how can I make sure that an eavesdropper can not read my message) • Message integrity (how do I know that the message has not been modified on its travel? ) • Authentication (how do I know that the message is from a particular person? ) Copyright © 2003 T. Trappenberg Overview E 12
• Confidentiality (how can I make sure that an eavesdropper can not read my message) • Message integrity (how do I know that the message has not been modified on its travel? ) • Authentication (how do I know that the message is from a particular person? ) Copyright © 2003 T. Trappenberg Overview E 12
 guvf zrffntr vf frperg __is __ss___ is s_____ Copyright © 2003 T. Trappenberg Overview E 13
guvf zrffntr vf frperg __is __ss___ is s_____ Copyright © 2003 T. Trappenberg Overview E 13
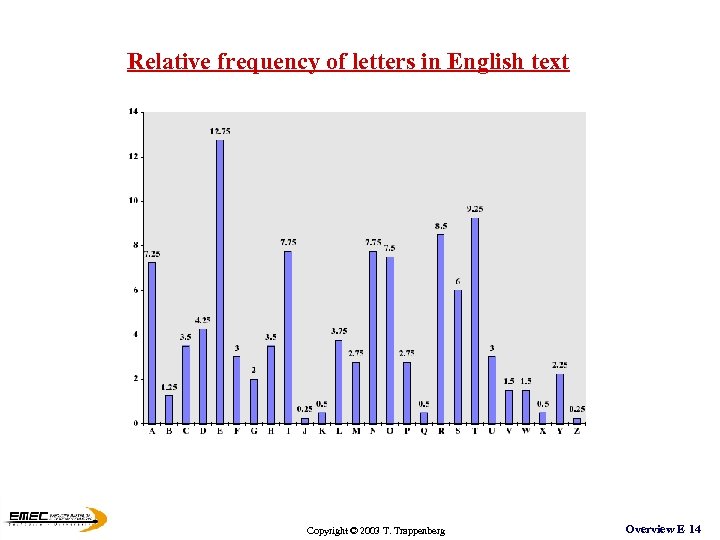 Relative frequency of letters in English text Copyright © 2003 T. Trappenberg Overview E 14
Relative frequency of letters in English text Copyright © 2003 T. Trappenberg Overview E 14
 guvf zrffntr vf frperg __is __ss___ is s_____ __is _ess__e is se__e_ this _ess__e is se__et this message is secret ROT 13 algorithm (cipher): abcdefghijklmnopqrstuvwxyzabcdefghijklm Copyright © 2003 T. Trappenberg Overview E 15
guvf zrffntr vf frperg __is __ss___ is s_____ __is _ess__e is se__e_ this _ess__e is se__et this message is secret ROT 13 algorithm (cipher): abcdefghijklmnopqrstuvwxyzabcdefghijklm Copyright © 2003 T. Trappenberg Overview E 15
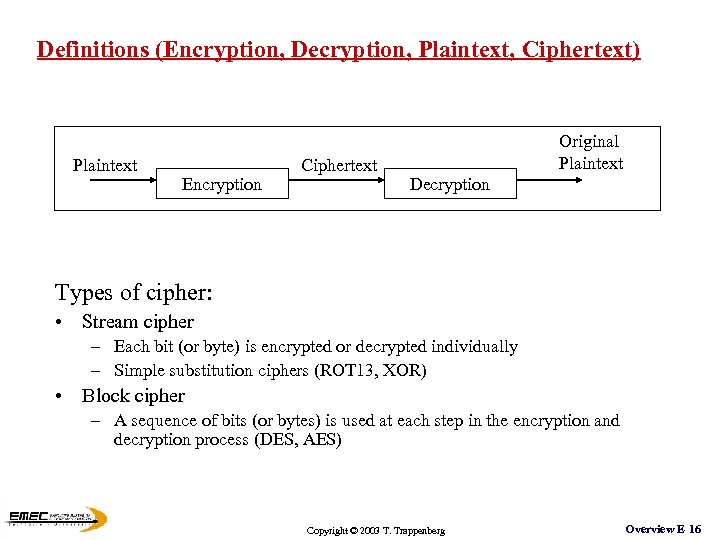 Definitions (Encryption, Decryption, Plaintext, Ciphertext) Plaintext Encryption Ciphertext Original Plaintext Decryption Types of cipher: • Stream cipher – Each bit (or byte) is encrypted or decrypted individually – Simple substitution ciphers (ROT 13, XOR) • Block cipher – A sequence of bits (or bytes) is used at each step in the encryption and decryption process (DES, AES) Copyright © 2003 T. Trappenberg Overview E 16
Definitions (Encryption, Decryption, Plaintext, Ciphertext) Plaintext Encryption Ciphertext Original Plaintext Decryption Types of cipher: • Stream cipher – Each bit (or byte) is encrypted or decrypted individually – Simple substitution ciphers (ROT 13, XOR) • Block cipher – A sequence of bits (or bytes) is used at each step in the encryption and decryption process (DES, AES) Copyright © 2003 T. Trappenberg Overview E 16
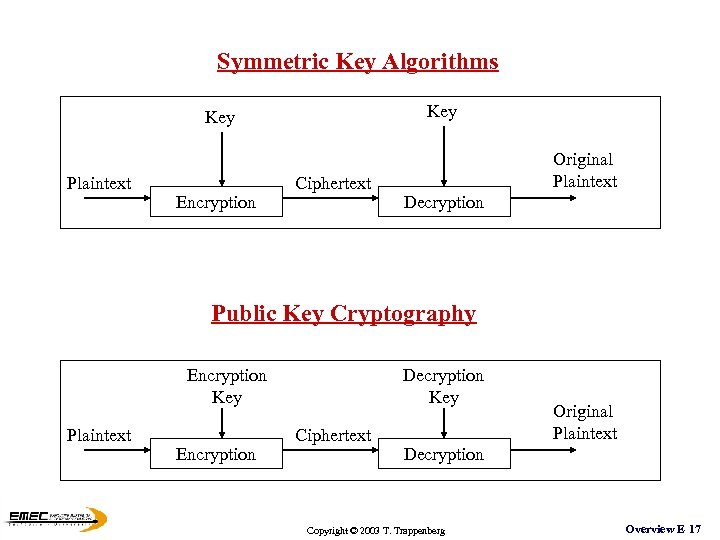 Symmetric Key Algorithms Key Plaintext Encryption Ciphertext Original Plaintext Decryption Public Key Cryptography Encryption Key Plaintext Encryption Decryption Key Ciphertext Original Plaintext Decryption Copyright © 2003 T. Trappenberg Overview E 17
Symmetric Key Algorithms Key Plaintext Encryption Ciphertext Original Plaintext Decryption Public Key Cryptography Encryption Key Plaintext Encryption Decryption Key Ciphertext Original Plaintext Decryption Copyright © 2003 T. Trappenberg Overview E 17
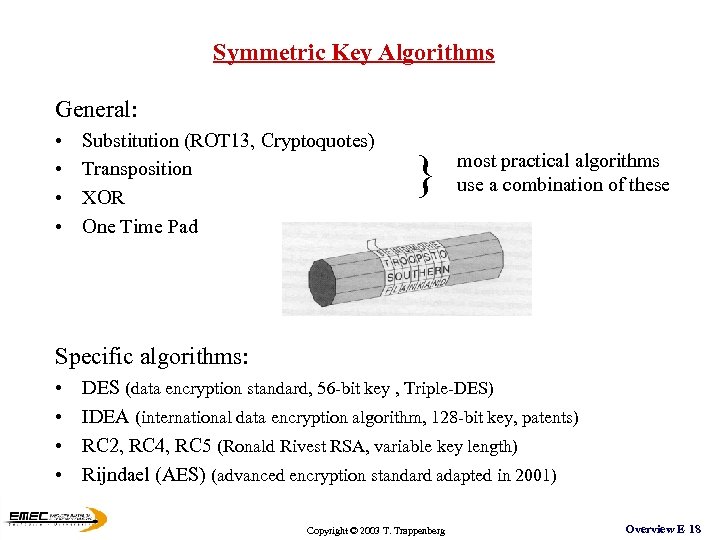 Symmetric Key Algorithms General: • • Substitution (ROT 13, Cryptoquotes) Transposition XOR One Time Pad } most practical algorithms use a combination of these Specific algorithms: • • DES (data encryption standard, 56 -bit key , Triple-DES) IDEA (international data encryption algorithm, 128 -bit key, patents) RC 2, RC 4, RC 5 (Ronald Rivest RSA, variable key length) Rijndael (AES) (advanced encryption standard adapted in 2001) Copyright © 2003 T. Trappenberg Overview E 18
Symmetric Key Algorithms General: • • Substitution (ROT 13, Cryptoquotes) Transposition XOR One Time Pad } most practical algorithms use a combination of these Specific algorithms: • • DES (data encryption standard, 56 -bit key , Triple-DES) IDEA (international data encryption algorithm, 128 -bit key, patents) RC 2, RC 4, RC 5 (Ronald Rivest RSA, variable key length) Rijndael (AES) (advanced encryption standard adapted in 2001) Copyright © 2003 T. Trappenberg Overview E 18
 Rijndael: Iterated Block Cipher • 10/12/14 times applying the same round function • Round function: uniform and parallel, composed of 4 steps • Each step has its own particular function: - Byte. Sub: nonlinearity - Shift. Row: inter-column diffusion - Mix. Column: inter-byte diffusion within columns - Round key addition Copyright © 2003 T. Trappenberg Overview E 19
Rijndael: Iterated Block Cipher • 10/12/14 times applying the same round function • Round function: uniform and parallel, composed of 4 steps • Each step has its own particular function: - Byte. Sub: nonlinearity - Shift. Row: inter-column diffusion - Mix. Column: inter-byte diffusion within columns - Round key addition Copyright © 2003 T. Trappenberg Overview E 19
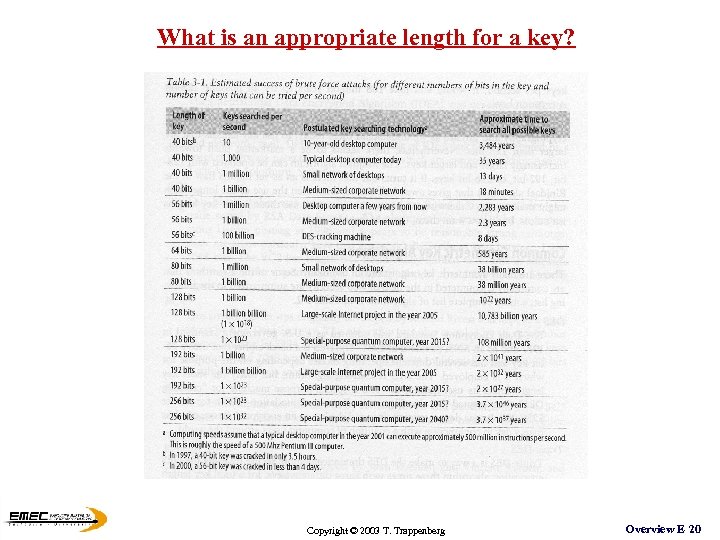 What is an appropriate length for a key? Copyright © 2003 T. Trappenberg Overview E 20
What is an appropriate length for a key? Copyright © 2003 T. Trappenberg Overview E 20
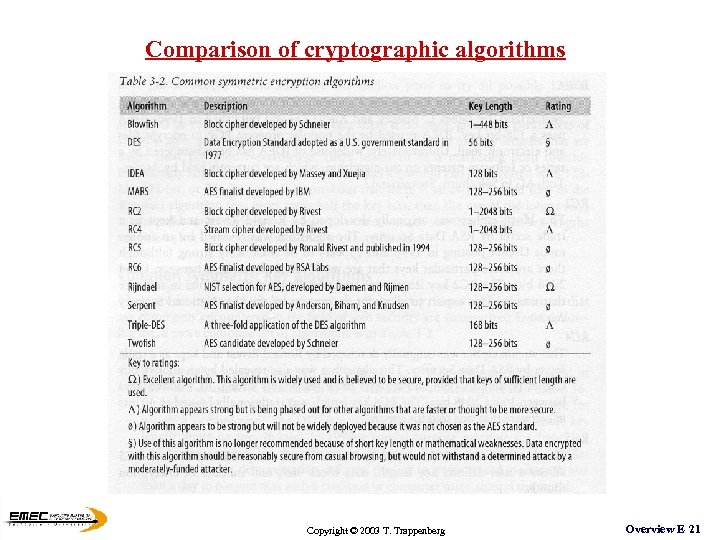 Comparison of cryptographic algorithms Copyright © 2003 T. Trappenberg Overview E 21
Comparison of cryptographic algorithms Copyright © 2003 T. Trappenberg Overview E 21
 Key distribution problem Solutions: • Doubly padlocked box exchange • Diffie-Hellman key exchange • Public-key cryptography (RSA, elliptic curve cryptography) Copyright © 2003 T. Trappenberg Overview E 22
Key distribution problem Solutions: • Doubly padlocked box exchange • Diffie-Hellman key exchange • Public-key cryptography (RSA, elliptic curve cryptography) Copyright © 2003 T. Trappenberg Overview E 22
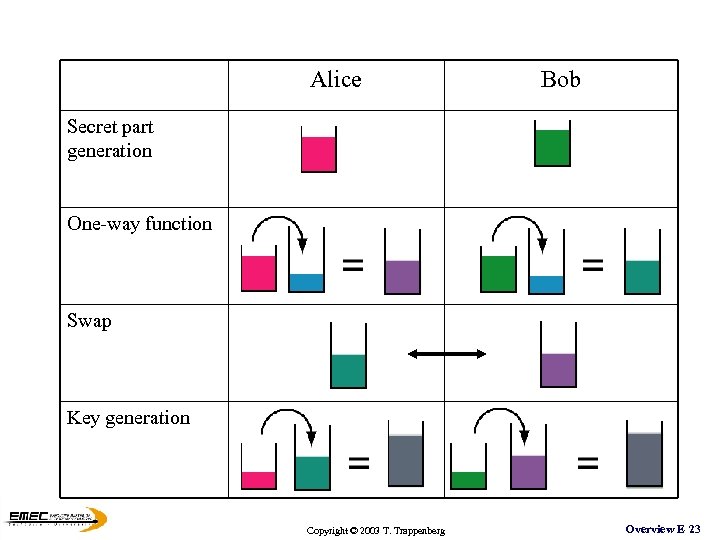 Alice Bob Secret part generation One-way function Swap Key generation Copyright © 2003 T. Trappenberg Overview E 23
Alice Bob Secret part generation One-way function Swap Key generation Copyright © 2003 T. Trappenberg Overview E 23
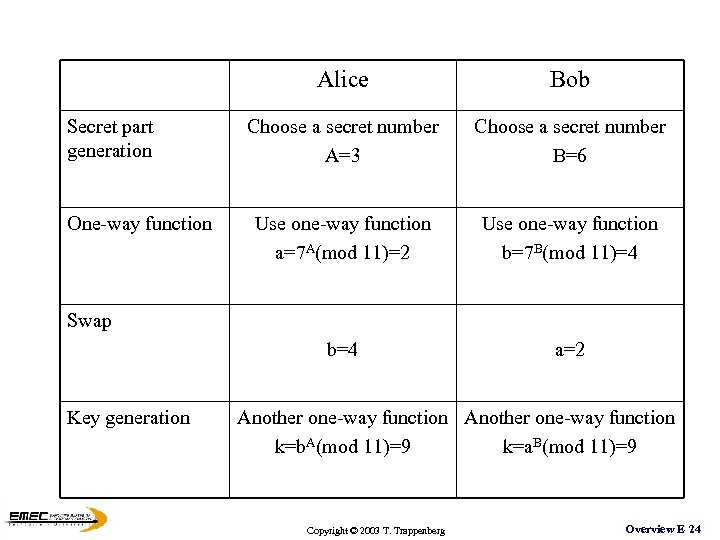 Alice One-way function Choose a secret number A=3 Choose a secret number B=6 Use one-way function a=7 A(mod 11)=2 Use one-way function b=7 B(mod 11)=4 b=4 Secret part generation Bob a=2 Swap Key generation Another one-way function k=b. A(mod 11)=9 k=a. B(mod 11)=9 Copyright © 2003 T. Trappenberg Overview E 24
Alice One-way function Choose a secret number A=3 Choose a secret number B=6 Use one-way function a=7 A(mod 11)=2 Use one-way function b=7 B(mod 11)=4 b=4 Secret part generation Bob a=2 Swap Key generation Another one-way function k=b. A(mod 11)=9 k=a. B(mod 11)=9 Copyright © 2003 T. Trappenberg Overview E 24
 • The Diffie-Hellman key exchange was the first widely recognized solution to the key exchange problem • Can only be used to exchange key. Symmetric key cryptographic methods can be used to exchange secret messages • Fairly elaborate exchange of messages Copyright © 2003 T. Trappenberg Overview E 25
• The Diffie-Hellman key exchange was the first widely recognized solution to the key exchange problem • Can only be used to exchange key. Symmetric key cryptographic methods can be used to exchange secret messages • Fairly elaborate exchange of messages Copyright © 2003 T. Trappenberg Overview E 25
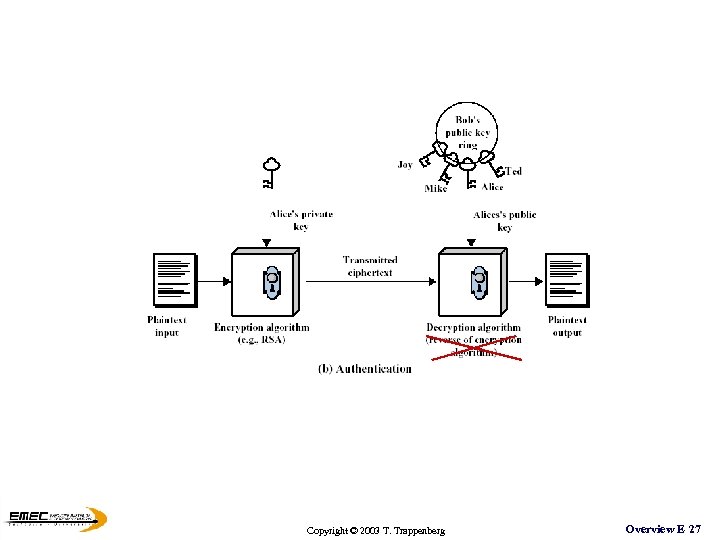
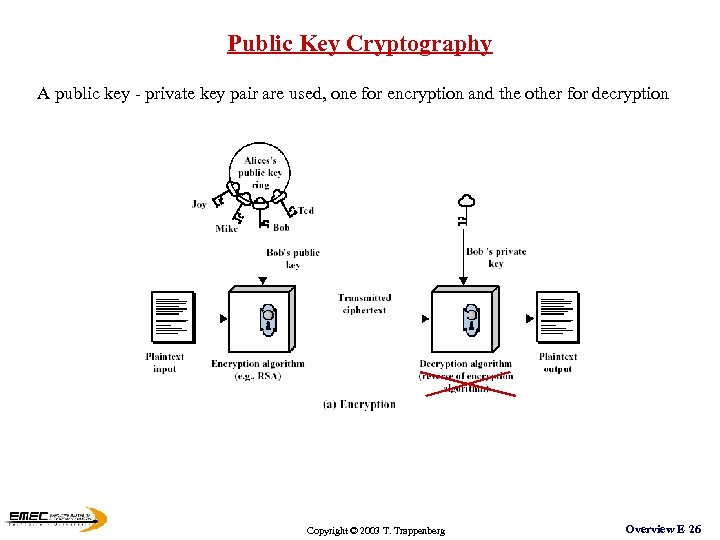 Public Key Cryptography A public key - private key pair are used, one for encryption and the other for decryption Copyright © 2003 T. Trappenberg Overview E 26
Public Key Cryptography A public key - private key pair are used, one for encryption and the other for decryption Copyright © 2003 T. Trappenberg Overview E 26
 Copyright © 2003 T. Trappenberg Overview E 27
Copyright © 2003 T. Trappenberg Overview E 27
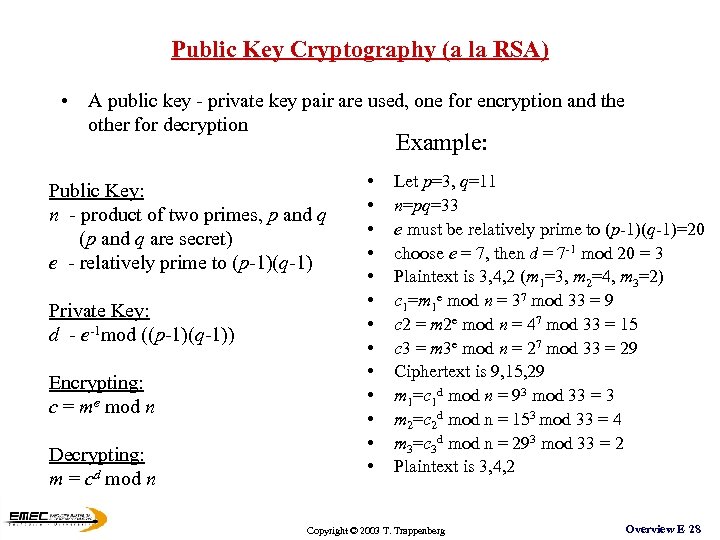 Public Key Cryptography (a la RSA) • A public key - private key pair are used, one for encryption and the other for decryption Example: Public Key: n - product of two primes, p and q (p and q are secret) e - relatively prime to (p-1)(q-1) Private Key: d - e-1 mod ((p-1)(q-1)) Encrypting: c = me mod n Decrypting: m = cd mod n • • • • Let p=3, q=11 n=pq=33 e must be relatively prime to (p-1)(q-1)=20 choose e = 7, then d = 7 -1 mod 20 = 3 Plaintext is 3, 4, 2 (m 1=3, m 2=4, m 3=2) c 1=m 1 e mod n = 37 mod 33 = 9 c 2 = m 2 e mod n = 47 mod 33 = 15 c 3 = m 3 e mod n = 27 mod 33 = 29 Ciphertext is 9, 15, 29 m 1=c 1 d mod n = 93 mod 33 = 3 m 2=c 2 d mod n = 153 mod 33 = 4 m 3=c 3 d mod n = 293 mod 33 = 2 Plaintext is 3, 4, 2 Copyright © 2003 T. Trappenberg Overview E 28
Public Key Cryptography (a la RSA) • A public key - private key pair are used, one for encryption and the other for decryption Example: Public Key: n - product of two primes, p and q (p and q are secret) e - relatively prime to (p-1)(q-1) Private Key: d - e-1 mod ((p-1)(q-1)) Encrypting: c = me mod n Decrypting: m = cd mod n • • • • Let p=3, q=11 n=pq=33 e must be relatively prime to (p-1)(q-1)=20 choose e = 7, then d = 7 -1 mod 20 = 3 Plaintext is 3, 4, 2 (m 1=3, m 2=4, m 3=2) c 1=m 1 e mod n = 37 mod 33 = 9 c 2 = m 2 e mod n = 47 mod 33 = 15 c 3 = m 3 e mod n = 27 mod 33 = 29 Ciphertext is 9, 15, 29 m 1=c 1 d mod n = 93 mod 33 = 3 m 2=c 2 d mod n = 153 mod 33 = 4 m 3=c 3 d mod n = 293 mod 33 = 2 Plaintext is 3, 4, 2 Copyright © 2003 T. Trappenberg Overview E 28
 PGP: Pretty Good Privacy • Implementation of best available cryptographic algorithms for confidentiality and authentication and integration into a freely available general-purpose application Philip Zimmermann • Package, source code, and documentation available on the web • Low-cost commercial version from Network Associates • Includes AES, 3 DES, CAST, IDEA; RSA DSS, Diffie-Hellman; SHA 1; key management, … Copyright © 2003 T. Trappenberg Overview E 29
PGP: Pretty Good Privacy • Implementation of best available cryptographic algorithms for confidentiality and authentication and integration into a freely available general-purpose application Philip Zimmermann • Package, source code, and documentation available on the web • Low-cost commercial version from Network Associates • Includes AES, 3 DES, CAST, IDEA; RSA DSS, Diffie-Hellman; SHA 1; key management, … Copyright © 2003 T. Trappenberg Overview E 29
 Message Digests & Hash function • A message digest is a one-way function which maps the information contained in a (small or large) file to a single large number, typically between 128 bits and 256 bits in length. • A good message digest function should have the following properties: – Every bit of the output is influenced by every bit of the input – Changing a single bit in the input results in every output bit having a 50% chance of changing – Given an input file, its corresponding digest, and the digest function, it is computationally infeasible to produce another input file which maps to the same digest Copyright © 2003 T. Trappenberg Overview E 30
Message Digests & Hash function • A message digest is a one-way function which maps the information contained in a (small or large) file to a single large number, typically between 128 bits and 256 bits in length. • A good message digest function should have the following properties: – Every bit of the output is influenced by every bit of the input – Changing a single bit in the input results in every output bit having a 50% chance of changing – Given an input file, its corresponding digest, and the digest function, it is computationally infeasible to produce another input file which maps to the same digest Copyright © 2003 T. Trappenberg Overview E 30
 http: //ciips. ee. uwa. edu. au/~morris/Year 2/PLDS 210/hash_tables. html Copyright © 2003 T. Trappenberg Overview E 31
http: //ciips. ee. uwa. edu. au/~morris/Year 2/PLDS 210/hash_tables. html Copyright © 2003 T. Trappenberg Overview E 31
 Message Digests (continued) • Standard encryption algorithm • e. g. use last block in cipher feedback mode • Provide good message digest code • Computationally more demanding than other specialized functions • MD 5 • One widely used message digest algorithm from a series of algorithms developed by Ronald Rivest • Does not rely on a secrete key and is therefore not suitable as MAC without further provisions • HMAC • The Hashed Message Authentication Code uses a shared secret key in combination with a message digest function to produce a secret message authentication code • Since an attacker doesn’t know the secret, the attacker cannot produce a correct authentication code if they alter the message • Fast to calculate, can be used as digital signature. However, a shared secret key is used. • SHA-1 • Developed by the NSA for use with the Digital Signature Standard Copyright © 2003 T. Trappenberg Overview E 32
Message Digests (continued) • Standard encryption algorithm • e. g. use last block in cipher feedback mode • Provide good message digest code • Computationally more demanding than other specialized functions • MD 5 • One widely used message digest algorithm from a series of algorithms developed by Ronald Rivest • Does not rely on a secrete key and is therefore not suitable as MAC without further provisions • HMAC • The Hashed Message Authentication Code uses a shared secret key in combination with a message digest function to produce a secret message authentication code • Since an attacker doesn’t know the secret, the attacker cannot produce a correct authentication code if they alter the message • Fast to calculate, can be used as digital signature. However, a shared secret key is used. • SHA-1 • Developed by the NSA for use with the Digital Signature Standard Copyright © 2003 T. Trappenberg Overview E 32
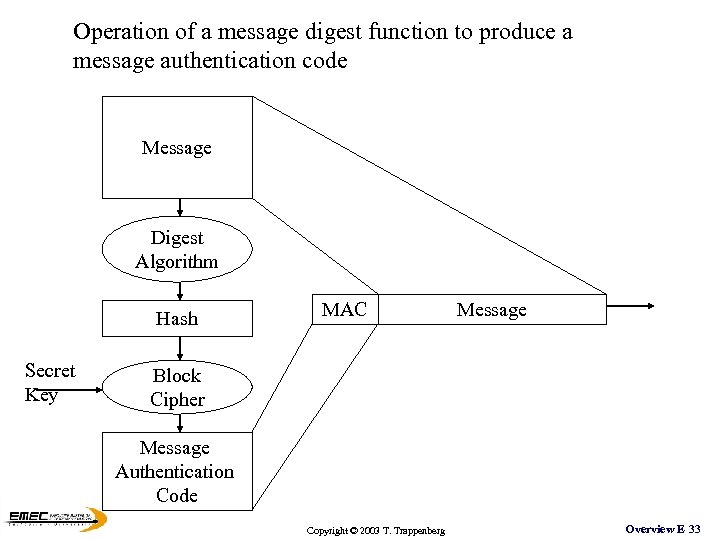 Operation of a message digest function to produce a message authentication code Message Digest Algorithm Hash Secret Key MAC Message Block Cipher Message Authentication Code Copyright © 2003 T. Trappenberg Overview E 33
Operation of a message digest function to produce a message authentication code Message Digest Algorithm Hash Secret Key MAC Message Block Cipher Message Authentication Code Copyright © 2003 T. Trappenberg Overview E 33
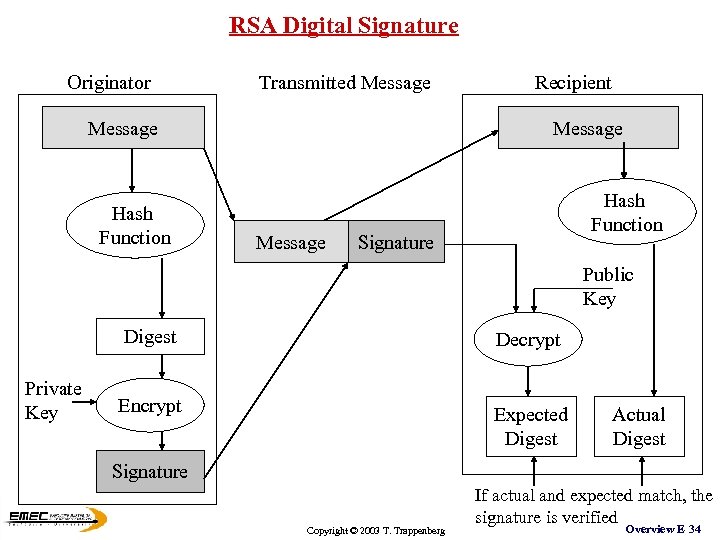 RSA Digital Signature Originator Transmitted Message Hash Function Recipient Message Hash Function Signature Public Key Digest Private Key Decrypt Encrypt Expected Digest Actual Digest Signature Copyright © 2003 T. Trappenberg If actual and expected match, the signature is verified Overview E 34
RSA Digital Signature Originator Transmitted Message Hash Function Recipient Message Hash Function Signature Public Key Digest Private Key Decrypt Encrypt Expected Digest Actual Digest Signature Copyright © 2003 T. Trappenberg If actual and expected match, the signature is verified Overview E 34
 Types of authentication • • What you know (username and password) What you have (token, smart card) What you are (biometrics) Where you are (location security) Copyright © 2003 T. Trappenberg Overview E 35
Types of authentication • • What you know (username and password) What you have (token, smart card) What you are (biometrics) Where you are (location security) Copyright © 2003 T. Trappenberg Overview E 35
 Digital Certificates • Need a system for pairing public keys to identification information • Certification authority (or trusted third party) issues a certificate which pairs identification information with a public key, signed with the certification authority’s private key • User must trust the certification authority, and have a valid copy of the certification authority’s public key Copyright © 2003 T. Trappenberg Overview E 36
Digital Certificates • Need a system for pairing public keys to identification information • Certification authority (or trusted third party) issues a certificate which pairs identification information with a public key, signed with the certification authority’s private key • User must trust the certification authority, and have a valid copy of the certification authority’s public key Copyright © 2003 T. Trappenberg Overview E 36
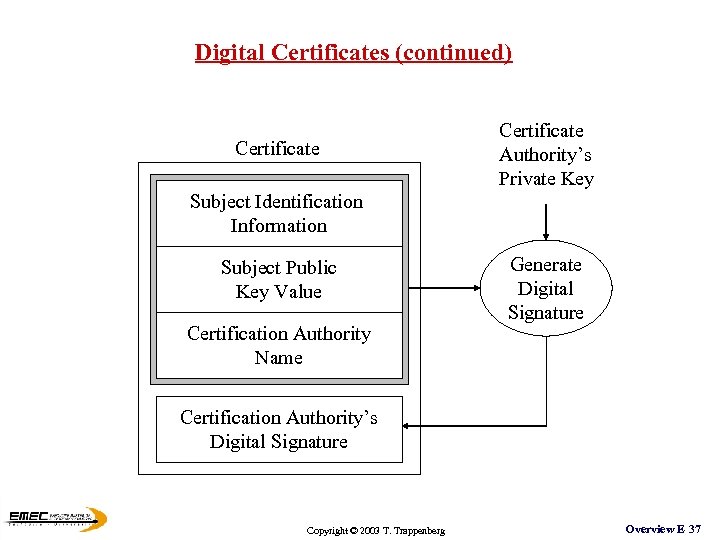 Digital Certificates (continued) Certificate Authority’s Private Key Subject Identification Information Subject Public Key Value Certification Authority Name Generate Digital Signature Certification Authority’s Digital Signature Copyright © 2003 T. Trappenberg Overview E 37
Digital Certificates (continued) Certificate Authority’s Private Key Subject Identification Information Subject Public Key Value Certification Authority Name Generate Digital Signature Certification Authority’s Digital Signature Copyright © 2003 T. Trappenberg Overview E 37
 Certification Paths • More than one Certification Authority will be required • If CAs trust one another, they can issue certificates for each other’s public keys • This leads to a recursively defined path from a user under one CA to a user under another CA Copyright © 2003 T. Trappenberg Overview E 38
Certification Paths • More than one Certification Authority will be required • If CAs trust one another, they can issue certificates for each other’s public keys • This leads to a recursively defined path from a user under one CA to a user under another CA Copyright © 2003 T. Trappenberg Overview E 38
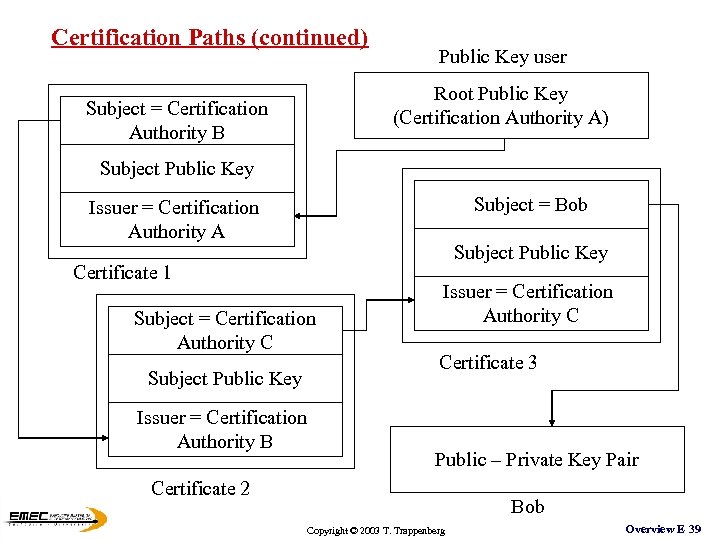 Certification Paths (continued) Public Key user Root Public Key (Certification Authority A) Subject = Certification Authority B Subject Public Key Subject = Bob Issuer = Certification Authority A Subject Public Key Certificate 1 Subject = Certification Authority C Subject Public Key Issuer = Certification Authority B Issuer = Certification Authority C Certificate 3 Public – Private Key Pair Certificate 2 Bob Copyright © 2003 T. Trappenberg Overview E 39
Certification Paths (continued) Public Key user Root Public Key (Certification Authority A) Subject = Certification Authority B Subject Public Key Subject = Bob Issuer = Certification Authority A Subject Public Key Certificate 1 Subject = Certification Authority C Subject Public Key Issuer = Certification Authority B Issuer = Certification Authority C Certificate 3 Public – Private Key Pair Certificate 2 Bob Copyright © 2003 T. Trappenberg Overview E 39
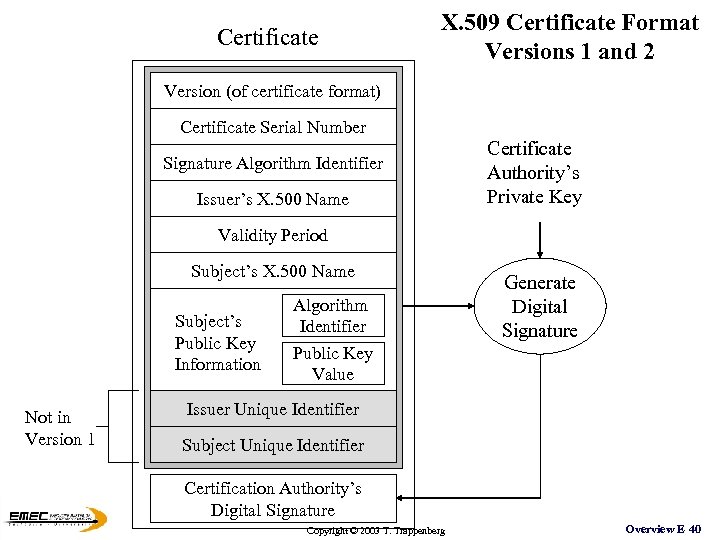 Certificate X. 509 Certificate Format Versions 1 and 2 Version (of certificate format) Certificate Serial Number Signature Algorithm Identifier Issuer’s X. 500 Name Certificate Authority’s Private Key Validity Period Subject’s X. 500 Name Subject’s Public Key Information Not in Version 1 Algorithm Identifier Public Key Value Generate Digital Signature Issuer Unique Identifier Subject Unique Identifier Certification Authority’s Digital Signature Copyright © 2003 T. Trappenberg Overview E 40
Certificate X. 509 Certificate Format Versions 1 and 2 Version (of certificate format) Certificate Serial Number Signature Algorithm Identifier Issuer’s X. 500 Name Certificate Authority’s Private Key Validity Period Subject’s X. 500 Name Subject’s Public Key Information Not in Version 1 Algorithm Identifier Public Key Value Generate Digital Signature Issuer Unique Identifier Subject Unique Identifier Certification Authority’s Digital Signature Copyright © 2003 T. Trappenberg Overview E 40


