756b4718ec97232b8242b055be9fc86f.ppt
- Количество слайдов: 14
 GPO PKI – Getting Started U. S. Government Publishing Office April 21, 2017
GPO PKI – Getting Started U. S. Government Publishing Office April 21, 2017
 Agenda § About GPO PKI – Using GPO PKI for OFR e. DOCS § GPO PKI Services
Agenda § About GPO PKI – Using GPO PKI for OFR e. DOCS § GPO PKI Services
 About GPO PKI § Shared Service Provider (SSP) certification – July 2007 § Cross-Certified with Federal Bridge Certification Authority since December 2005 § Meets all Federal PKI requirements § In operation at GPO since 2004
About GPO PKI § Shared Service Provider (SSP) certification – July 2007 § Cross-Certified with Federal Bridge Certification Authority since December 2005 § Meets all Federal PKI requirements § In operation at GPO since 2004
 GPO PKI Services § End User Certificates – Medium Assurance Level (federal PKI) – Requires in-person identity proofing for Users • End user must present themselves in person to the RA or LRA – Two options: • At GPO Main Office • Agency Local Registration Authority (LRA) – Agency LRA personnel require a hardware token • LRA personnel (agency) must be identity proofed at GPO • Hardware token required due to sensitive nature of enrollment function performed • LRA enrolls other agency personnel at agency– record keeping requirements – Agency users must present themselves in person to LRA at agency
GPO PKI Services § End User Certificates – Medium Assurance Level (federal PKI) – Requires in-person identity proofing for Users • End user must present themselves in person to the RA or LRA – Two options: • At GPO Main Office • Agency Local Registration Authority (LRA) – Agency LRA personnel require a hardware token • LRA personnel (agency) must be identity proofed at GPO • Hardware token required due to sensitive nature of enrollment function performed • LRA enrolls other agency personnel at agency– record keeping requirements – Agency users must present themselves in person to LRA at agency
 GPO PKI Services § Help Desk — GPO provides technical assistance to users • Email notification by users to GPO — Automatically routed to GPO PKI support — Phone number provided for emergencies — Agency IT Help Desk • Most agency end users to coordinate IT problem reporting and resolution through the agency IT Help Desk • GPO will work with agencies and PKI end users — GPO will always provide technical assistance to resolve end user PKI problems — May involve IT problems at the agency and agency will need to resolve those
GPO PKI Services § Help Desk — GPO provides technical assistance to users • Email notification by users to GPO — Automatically routed to GPO PKI support — Phone number provided for emergencies — Agency IT Help Desk • Most agency end users to coordinate IT problem reporting and resolution through the agency IT Help Desk • GPO will work with agencies and PKI end users — GPO will always provide technical assistance to resolve end user PKI problems — May involve IT problems at the agency and agency will need to resolve those
 Certificate Uses § File signing — e. DOCS, for example § File encryption § Email encryption and signing (S/MIME) — For Outlook email § Other uses are possible, in consultation with GPO PKI
Certificate Uses § File signing — e. DOCS, for example § File encryption § Email encryption and signing (S/MIME) — For Outlook email § Other uses are possible, in consultation with GPO PKI
 OFR e. DOCS PKI § Background – OFR e. DOCS application • Hosted by GPO on behalf of OFR • Allows digital submission of digitally signed files – Saves time and money – Requires official agency submitter to have PKI certificate • Required Medium Assurance PKI certificate – Requires In-Person Identity Proofing – GPO PKI services for the OFR e. DOCS application • In Operation since September 16, 2006 – OFR e. DOCS originally used NFC PKI (pre Sept. 2006)
OFR e. DOCS PKI § Background – OFR e. DOCS application • Hosted by GPO on behalf of OFR • Allows digital submission of digitally signed files – Saves time and money – Requires official agency submitter to have PKI certificate • Required Medium Assurance PKI certificate – Requires In-Person Identity Proofing – GPO PKI services for the OFR e. DOCS application • In Operation since September 16, 2006 – OFR e. DOCS originally used NFC PKI (pre Sept. 2006)
 e. DOCS Document Submission Process Step 1 End user logs into GPO PKI end user software (COTS client software meeting FIPS 140 -2 and Federal PKI standards from Entrust, configured by GPO to interface to the FBCA cross-certified GPO PKI). User enters appropriate password (from certificate issuance process, for initial password). Step 2 End user locates the file to be signed using Windows operating system process. Step 3 End user RIGHT CLICKS on the file to be signed. Step 4 End User selects Digitally Sign File…. Step 5 End User completes prompts to complete signing process. Step 6 GPO PKI software signs the file. Step 7 End user uploads the signed document to the OFR Web Portal. User uploads file selected and signed. Step 8 Process COMPLETE.
e. DOCS Document Submission Process Step 1 End user logs into GPO PKI end user software (COTS client software meeting FIPS 140 -2 and Federal PKI standards from Entrust, configured by GPO to interface to the FBCA cross-certified GPO PKI). User enters appropriate password (from certificate issuance process, for initial password). Step 2 End user locates the file to be signed using Windows operating system process. Step 3 End user RIGHT CLICKS on the file to be signed. Step 4 End User selects Digitally Sign File…. Step 5 End User completes prompts to complete signing process. Step 6 GPO PKI software signs the file. Step 7 End user uploads the signed document to the OFR Web Portal. User uploads file selected and signed. Step 8 Process COMPLETE.
 GPO PKI Services – Cost Structure § Cost Structure – End User Certificates • $150. 00 per user per year – NOTE: Software certificate (does not apply to smartcard certificate) – LRA Users • $350. 00 per LRA per year (includes hardware token) • LRA’s perform enrollment of agency users for GPO PKI – Costs documented in GPO Circular Letter 943 • URL: https: //beta. gpo. gov/docs/default-source/circular-letters-pdffiles/2015/cir 943. pdf § Business Enablement – SF-1 Form executed for GPO • Printing Officers at each federal agency – liaison to GPO – Memorandum of Agreement • Spells out roles and responsibilities
GPO PKI Services – Cost Structure § Cost Structure – End User Certificates • $150. 00 per user per year – NOTE: Software certificate (does not apply to smartcard certificate) – LRA Users • $350. 00 per LRA per year (includes hardware token) • LRA’s perform enrollment of agency users for GPO PKI – Costs documented in GPO Circular Letter 943 • URL: https: //beta. gpo. gov/docs/default-source/circular-letters-pdffiles/2015/cir 943. pdf § Business Enablement – SF-1 Form executed for GPO • Printing Officers at each federal agency – liaison to GPO – Memorandum of Agreement • Spells out roles and responsibilities
 GPO PKI Services – Getting Started Step 1: Execute a Standard Form 1 (SF-1) and send to GPO § § Send to: Bobbie Mc. Koy at GPO (contact information on last slide) Sample SF-1 shown on a later slide Identify the Number of End Users that will have Certificates Decide if Agency will use Local Registration Authority (LRA) function Step 2: Execute Memorandum of Agreement and send to GPO § § Spells out Roles and Responsibilities Send to: John Hannan at GPO at jhannon@gpo. gov Step 3: Ensure Agency IT Support staff know about: § A: Entrust Software installation on end user computers • Agencies normally review and certify software for use on Agency computers § B: Firewall Settings Required (see next slide) § C: Help Desk Notification for End User Problems • • • Firewall changes may be needed at some Agencies (depends on Agency controls) Decide how Agency End Users will request Help Desk support for PKI problems Most common model: End Users notify Agency Help Desk (using standard agency procedures) – Agency Help Desk notifies GPO PKI Help Desk, if needed Step 4: Install Entrust software on end user computers at Agency § § Entrust software provided by GPO as part of fee per user Available for download at URL: https: //beta. gpo. gov/how-to-work-with-us/agency/services-foragencies/public-key-infrastructure Step 5: Arrange a date and time for End Users to come to GPO for in-person Identity Proofing (federal PKI requirement) § Contact John Hannan at GPO at jhannon@gpo. gov.
GPO PKI Services – Getting Started Step 1: Execute a Standard Form 1 (SF-1) and send to GPO § § Send to: Bobbie Mc. Koy at GPO (contact information on last slide) Sample SF-1 shown on a later slide Identify the Number of End Users that will have Certificates Decide if Agency will use Local Registration Authority (LRA) function Step 2: Execute Memorandum of Agreement and send to GPO § § Spells out Roles and Responsibilities Send to: John Hannan at GPO at jhannon@gpo. gov Step 3: Ensure Agency IT Support staff know about: § A: Entrust Software installation on end user computers • Agencies normally review and certify software for use on Agency computers § B: Firewall Settings Required (see next slide) § C: Help Desk Notification for End User Problems • • • Firewall changes may be needed at some Agencies (depends on Agency controls) Decide how Agency End Users will request Help Desk support for PKI problems Most common model: End Users notify Agency Help Desk (using standard agency procedures) – Agency Help Desk notifies GPO PKI Help Desk, if needed Step 4: Install Entrust software on end user computers at Agency § § Entrust software provided by GPO as part of fee per user Available for download at URL: https: //beta. gpo. gov/how-to-work-with-us/agency/services-foragencies/public-key-infrastructure Step 5: Arrange a date and time for End Users to come to GPO for in-person Identity Proofing (federal PKI requirement) § Contact John Hannan at GPO at jhannon@gpo. gov.
 Example SF-1 Form
Example SF-1 Form
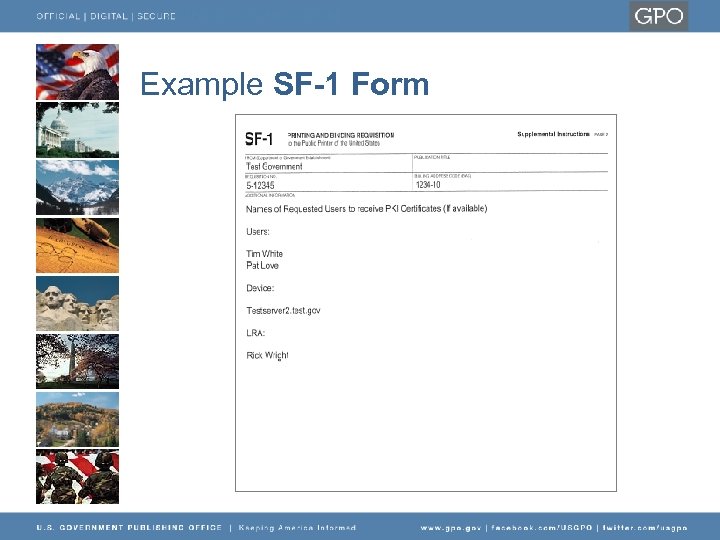 Example SF-1 Form
Example SF-1 Form
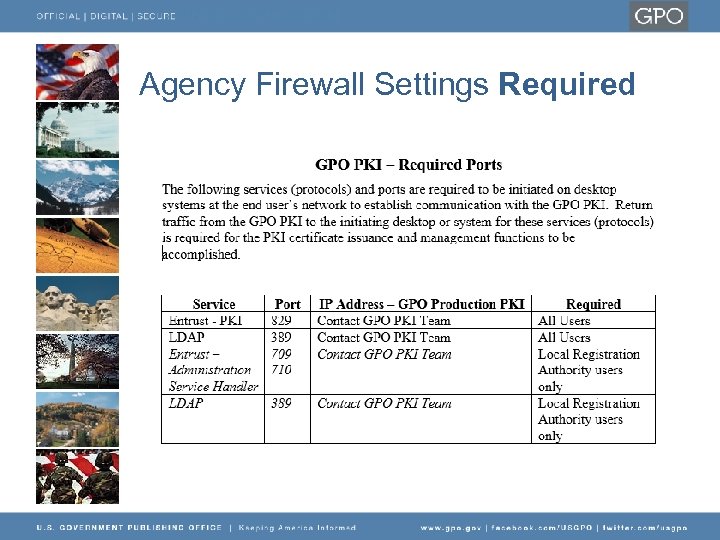 Agency Firewall Settings Required
Agency Firewall Settings Required
 Contact Information Technical John Hannan, CISSP Chief Information Security Officer U. S. Government Publishing Office 202. 512. 1021 jhannan@gpo. gov Business Official Journals of Government Office U. S. Government Publishing Office 202. 512. 2100
Contact Information Technical John Hannan, CISSP Chief Information Security Officer U. S. Government Publishing Office 202. 512. 1021 jhannan@gpo. gov Business Official Journals of Government Office U. S. Government Publishing Office 202. 512. 2100


