67d85c7293596b405e6fa58cd646a503.ppt
- Количество слайдов: 13
 Generic AAA model in Grids IRTF - AAAARCH meeting IETF 52 – Dec 14 th Salt Lake City Leon Gommans lgommans@science. uva. nl Advanced Internet Research Group Informatics Institute University of Amsterdam
Generic AAA model in Grids IRTF - AAAARCH meeting IETF 52 – Dec 14 th Salt Lake City Leon Gommans lgommans@science. uva. nl Advanced Internet Research Group Informatics Institute University of Amsterdam
 Goal Show authorization framework concepts of RFC 2904 applied to the Grid ( at FL 300 ) Show current implementation based on Globus Security Infrastructure (www. globus. org) Show possible future authorization concepts.
Goal Show authorization framework concepts of RFC 2904 applied to the Grid ( at FL 300 ) Show current implementation based on Globus Security Infrastructure (www. globus. org) Show possible future authorization concepts.
 Grids • Allow individuals / institutes in science or industry to form virtual organizations as to pool resources (computers, networks, data) and pursue a common goal. • Current GRID Security Infrastructure (GSI): • Allows access to multi-domain resources with a single sign-on • Allows organizations to remain in control of their resources • GSS-API / TLS based More details: http: //www. globus. org/documentation/incoming/butler. pdf
Grids • Allow individuals / institutes in science or industry to form virtual organizations as to pool resources (computers, networks, data) and pursue a common goal. • Current GRID Security Infrastructure (GSI): • Allows access to multi-domain resources with a single sign-on • Allows organizations to remain in control of their resources • GSS-API / TLS based More details: http: //www. globus. org/documentation/incoming/butler. pdf
 • Use of X 509 Certificates and Proxy Certificates to *: Remote login and access control for "standard" services. Client/server and server/client authentication. Authenticated and encrypted messages via GSS. Authenticated and encrypted streams via SSL and TLS. Authenticated and encrypted Web server access via https Impersonate and establish (a chain of) delegation. *) Ref: http: //archive. ncsa. uiuc. edu/General/Grid. Forum/SWG/taxonomy. html and draft-ietf-pkix-proxy-01. txt
• Use of X 509 Certificates and Proxy Certificates to *: Remote login and access control for "standard" services. Client/server and server/client authentication. Authenticated and encrypted messages via GSS. Authenticated and encrypted streams via SSL and TLS. Authenticated and encrypted Web server access via https Impersonate and establish (a chain of) delegation. *) Ref: http: //archive. ncsa. uiuc. edu/General/Grid. Forum/SWG/taxonomy. html and draft-ietf-pkix-proxy-01. txt
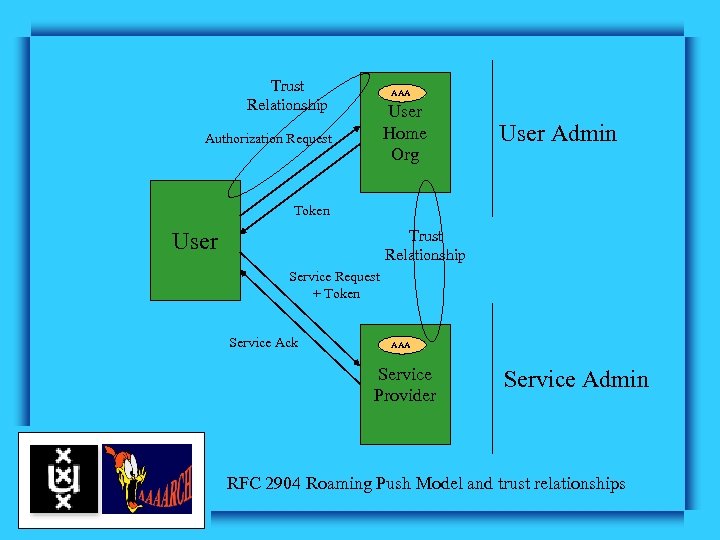 Trust Relationship AAA User Home Org Authorization Request User Admin Token Trust Relationship User Service Request + Token Service Ack AAA Service Provider Service Admin RFC 2904 Roaming Push Model and trust relationships
Trust Relationship AAA User Home Org Authorization Request User Admin Token Trust Relationship User Service Request + Token Service Ack AAA Service Provider Service Admin RFC 2904 Roaming Push Model and trust relationships
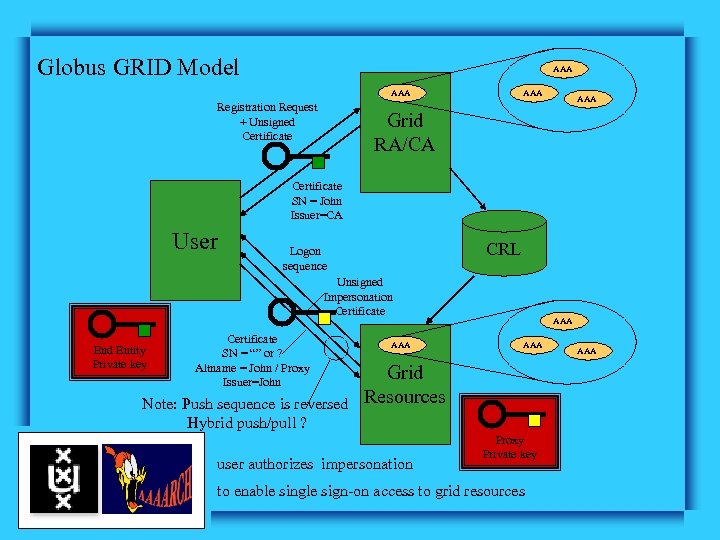 Globus GRID Model AAA Registration Request + Unsigned Certificate AAA Grid RA/CA Certificate SN = John Issuer=CA User CRL Logon sequence Unsigned Impersonation Certificate End Entity Private key Certificate SN = “” or ? Altname = John / Proxy Issuer=John Note: Push sequence is reversed Hybrid push/pull ? AAA AAA Grid Resources user authorizes impersonation Proxy Private key to enable single sign-on access to grid resources AAA
Globus GRID Model AAA Registration Request + Unsigned Certificate AAA Grid RA/CA Certificate SN = John Issuer=CA User CRL Logon sequence Unsigned Impersonation Certificate End Entity Private key Certificate SN = “” or ? Altname = John / Proxy Issuer=John Note: Push sequence is reversed Hybrid push/pull ? AAA AAA Grid Resources user authorizes impersonation Proxy Private key to enable single sign-on access to grid resources AAA
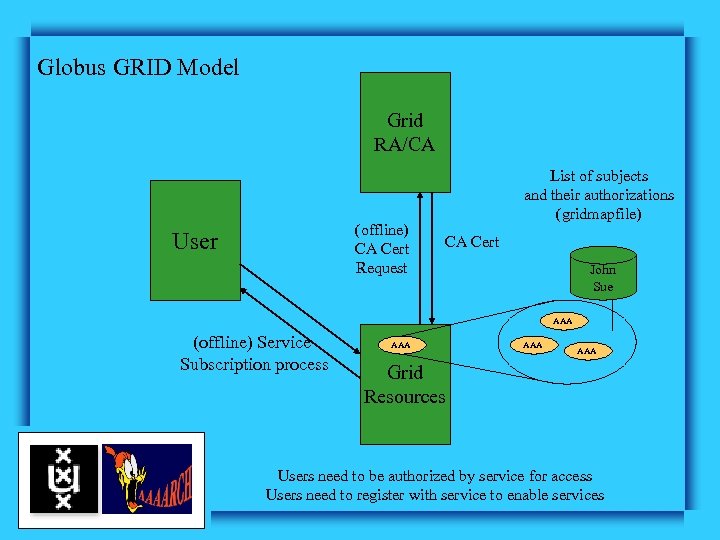 Globus GRID Model Grid RA/CA (offline) CA Cert Request User List of subjects and their authorizations (gridmapfile) CA Cert John Sue AAA (offline) Service Subscription process AAA AAA Grid Resources Users need to be authorized by service for access Users need to register with service to enable services
Globus GRID Model Grid RA/CA (offline) CA Cert Request User List of subjects and their authorizations (gridmapfile) CA Cert John Sue AAA (offline) Service Subscription process AAA AAA Grid Resources Users need to be authorized by service for access Users need to register with service to enable services
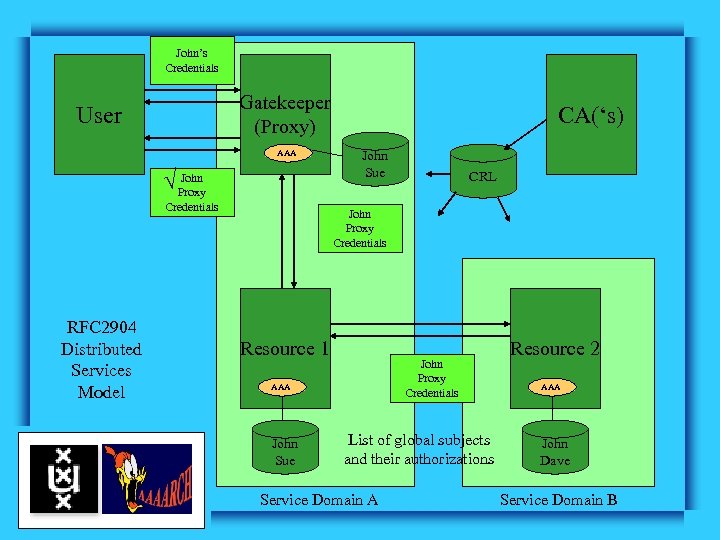 John’s Credentials Gatekeeper (Proxy) User AAA John Proxy Credentials RFC 2904 Distributed Services Model CA(‘s) John Sue CRL John Proxy Credentials Resource 1 John Proxy Credentials AAA John Sue List of global subjects and their authorizations Service Domain A Resource 2 AAA John Dave Service Domain B
John’s Credentials Gatekeeper (Proxy) User AAA John Proxy Credentials RFC 2904 Distributed Services Model CA(‘s) John Sue CRL John Proxy Credentials Resource 1 John Proxy Credentials AAA John Sue List of global subjects and their authorizations Service Domain A Resource 2 AAA John Dave Service Domain B
 “Industrializing” the Grid • Allow commercial organizations to collaborate in easy to use, secure and reliable fashion • interoperability, confidentiality, privacy, availability, integrity etc. • Ad hoc usage of Grid available resources need to be converted in units that can be settled as subscribed services do not scale. • resource usage, storage, digital rights etc. • Grid resources need procurement, user in driving seat. • user authorizes usage up to a certain limit.
“Industrializing” the Grid • Allow commercial organizations to collaborate in easy to use, secure and reliable fashion • interoperability, confidentiality, privacy, availability, integrity etc. • Ad hoc usage of Grid available resources need to be converted in units that can be settled as subscribed services do not scale. • resource usage, storage, digital rights etc. • Grid resources need procurement, user in driving seat. • user authorizes usage up to a certain limit.
 Workflow • create relationship with home organization that can authorize a usage limit. • create relationship with organization that represents a community and authorizes access to and usage of resources belonging to a Virtual Organization based on authorized usage limit. • use resources based on authorization from Virtual Organization
Workflow • create relationship with home organization that can authorize a usage limit. • create relationship with organization that represents a community and authorizes access to and usage of resources belonging to a Virtual Organization based on authorized usage limit. • use resources based on authorization from Virtual Organization
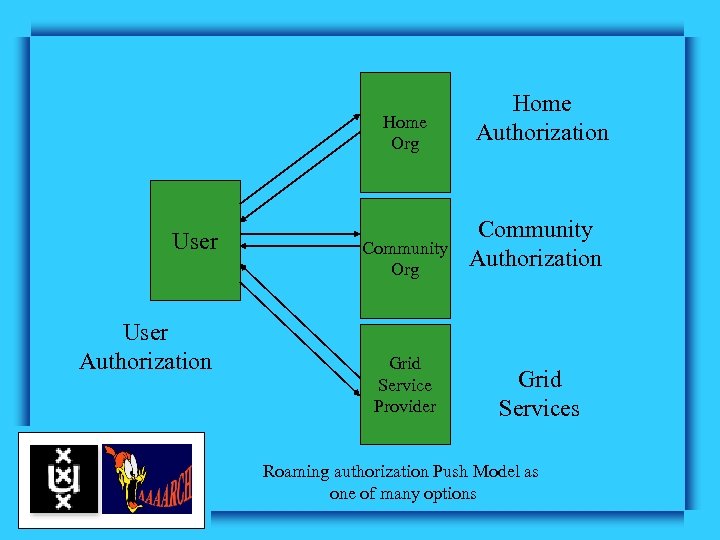 Home Org User Authorization Home Authorization Community Org Community Authorization Grid Service Provider Grid Services Roaming authorization Push Model as one of many options
Home Org User Authorization Home Authorization Community Org Community Authorization Grid Service Provider Grid Services Roaming authorization Push Model as one of many options
 Thank you More info draft-ietf-pkix-proxy-01. txt www. globus. org www. ggf. org www. aaaarch. org
Thank you More info draft-ietf-pkix-proxy-01. txt www. globus. org www. ggf. org www. aaaarch. org



